cd8cf7600b38b4bb17237b93e5717462.ppt
- Количество слайдов: 43

EEC-484/584 Computer Networks Lecture 8 Wenbing Zhao wenbing@ieee. org (Part of the slides are based on materials supplied by Dr. Louise Moser at UCSB and Prentice-Hall) Spring Semester 2006 EEC-484/584: Computer Networks
2 Outline • Error detection and correction • Elementary Data Link Protocols • Example protocols (not required for quiz) Spring Semester 2006 EEC-484/584: Computer Networks 2
3 Error-Correcting Codes • n-bit codeword – an n-bit unit containing data and check bits – m bits of data, r bits redundant/check bits (n = m+r) • How to measure the differences between two codewords (num of different bits) – Using exclusive OR and counting number of 1 bits in the result Spring Semester 2006 EEC-484/584: Computer Networks 3

4 Error-Correcting Codes • Hamming distance – number of bit positions in which two codewords differ • If two codewords are a Hamming distance d apart, it will require d single-bit errors to convert one into the other Spring Semester 2006 EEC-484/584: Computer Networks 4

5 Error-Correcting Codes • Complete code – Complete list of all legal codewords: 2 m possible data messages – Recall that there are m bits of data • Hamming distance of the complete code – Find two codewords whose Hamming distance is minimum Spring Semester 2006 EEC-484/584: Computer Networks 5

6 Error-Detection Codes • A distance d+1 code can detect up to d errors, why? – If there are d+1 errors, one valid codeword might be turned into another valid codeword – ≤ d errors will change a valid codeword into an illegal codeword can be detected! Spring Semester 2006 EEC-484/584: Computer Networks 6

7 Error-Correcting Codes • To correct d errors, need a distance 2 d+1 code – Legal codewords are so far part that even with d changes, original codeword is still closer than any other codeword, so it can be uniquely determined Spring Semester 2006 EEC-484/584: Computer Networks 7
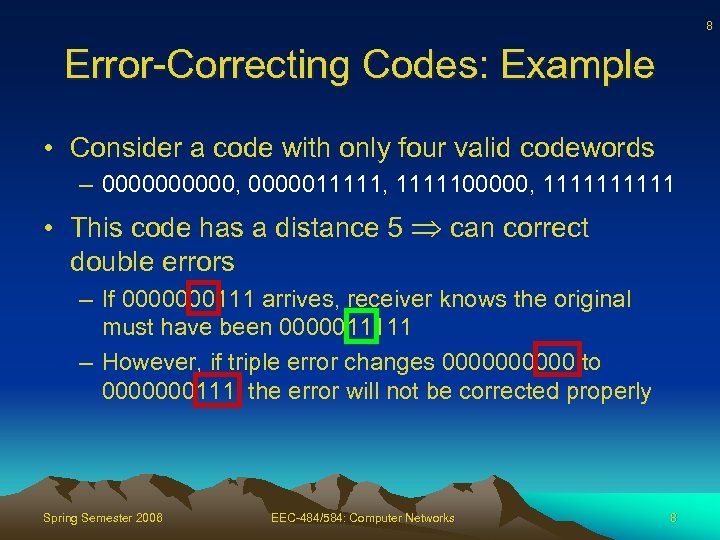
8 Error-Correcting Codes: Example • Consider a code with only four valid codewords – 00000, 0000011111, 1111100000, 11111 • This code has a distance 5 can correct double errors – If 0000000111 arrives, receiver knows the original must have been 0000011111 – However, if triple error changes 00000 to 0000000111, the error will not be corrected properly Spring Semester 2006 EEC-484/584: Computer Networks 8

9 Parity Bit • Parity bit – a single bit is appended to the data • Parity bit is chosen so that number of 1 bits in the codeword is even or odd • Example: Given 1011010 – With even parity 10110100 – With odd parity 10110101 • A code with a single parity bit has a distance 2 – Since any single-bit error produces a codeword with wrong parity can be used to detect single bit errors Spring Semester 2006 EEC-484/584: Computer Networks 9
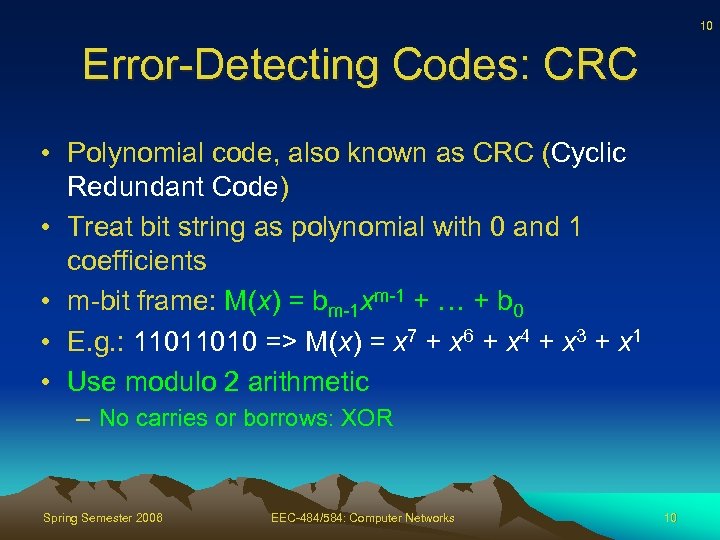
10 Error-Detecting Codes: CRC • Polynomial code, also known as CRC (Cyclic Redundant Code) • Treat bit string as polynomial with 0 and 1 coefficients • m-bit frame: M(x) = bm-1 xm-1 + … + b 0 • E. g. : 11011010 => M(x) = x 7 + x 6 + x 4 + x 3 + x 1 • Use modulo 2 arithmetic – No carries or borrows: XOR Spring Semester 2006 EEC-484/584: Computer Networks 10
11 Cyclic Redundant Code • Sender and receiver agree on generator polynomial G(x) (High & low order bits must be 1) • For a frame with m bits corresponding to M(x), m > deg G(x) = r • Append checksum to end of frame so polynomial T(x) corresponding to checksummed frame is divisible by G(x) • When receiver gets checksummed frame, divides T(x) by G(x) • If remainder R(x) != 0, then transmission error Spring Semester 2006 EEC-484/584: Computer Networks 11
12 Algorithm to Compute CRC Checksum • Let m = deg M(x), r = deg G(x) • Append r 0 bits to lower-order end of frame: xr. M(x) • Divide bit string corresponding to xr. M(x) by bit string corresponding to G(x) • Subtract remainder R(x) from bit string corresponding to xr. M(x), result is checksummed frame. Let T(x) be its polynomial – xr. M(x) = Q(x)G(x) + R(x) – xr. M(x) – R(x) = Q(x)G(x) = T(x) Spring Semester 2006 EEC-484/584: Computer Networks 12
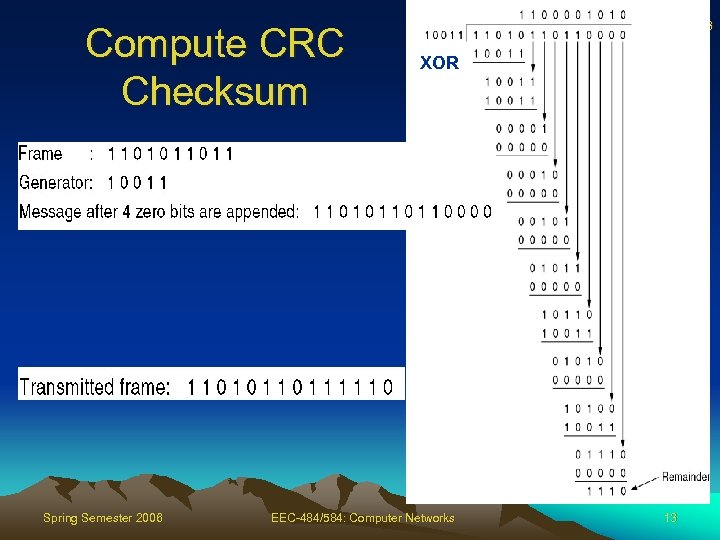
Compute CRC Checksum Spring Semester 2006 13 XOR EEC-484/584: Computer Networks 13
14 International Standard Polynomials • CRC-12 G(x) = x 12 + x 11 + x 3 + x 2 + x 1 + 1 – Used for 6 -bit characters • CRC-16 G(x) = x 16 + x 15 + x 2 + 1 CRC-CCITT G(x) = x 16 + x 12 + x 5 + 1 – Used for 8 -bit characters • CRC-32 G(x) = x 32 + x 26 + x 23 + x 22 + x 16 + x 11 + x 10 + x 8 + x 7 + x 5 + x 4 + x 2 + x 1 + 1 – Used in IEEE 802 – Detects all bursts of length 32 or less and all bursts affecting an odd number of bits Spring Semester 2006 EEC-484/584: Computer Networks 14

15 Exercise • Given 1011011, calculate the parity bit to be appended to the bit string – If even parity is used – If odd parity is used – If the highest order bit is inverted to 0, show the error can be detected Spring Semester 2006 EEC-484/584: Computer Networks 15

16 Exercise • To provide more reliability than a single parity bit can give, an error-detecting coding scheme uses one parity bit for checking all the odd-numbered bits and a second parity bit for all the evennumbered bits. What is the Hamming distance of this code? Spring Semester 2006 EEC-484/584: Computer Networks 16

17 Exercise • A bit stream 10011101 is transmitted using the standard CRC method described in the text. The generator polynomial is x 3 + 1. Show the actual bit string transmitted. Suppose third bit from the left is inverted during transmission. Show that this error is detected at the receiver's end. Spring Semester 2006 EEC-484/584: Computer Networks 17
18 Elementary Data Link Protocols • An Unrestricted Simplex Protocol • A Simplex Stop-and-Wait Protocol • A Simplex Protocol for a Noisy Channel Spring Semester 2006 EEC-484/584: Computer Networks 18
19 Initial Assumptions • Physical, data link, network layers are independent processes • Sender has infinite amount of data ready to send, supplied by network layer • “wire-like” service: DLL provides reliable, source ordered delivery service to NL • Packet from NL is treated as pure data • When sender accepts packet from NL, it encapsulates in a frame with a header and trailer Spring Semester 2006 EEC-484/584: Computer Networks 19
20 Initial Assumptions • Receiver waits for arrived of frame, which generates an interrupt • When frame arrives at receiver, hardware computes checksum – If error then DLL informed event = chksum_err – Else DLL informed event = frame_arrival • DLL acquires frame from physical layer, checks control info in header • If ok then passes packet to NL Spring Semester 2006 EEC-484/584: Computer Networks 20
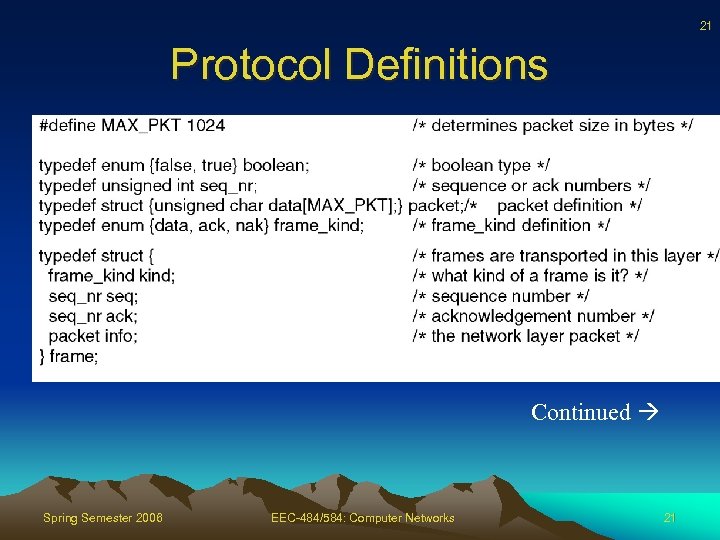
21 Protocol Definitions Continued Spring Semester 2006 EEC-484/584: Computer Networks 21
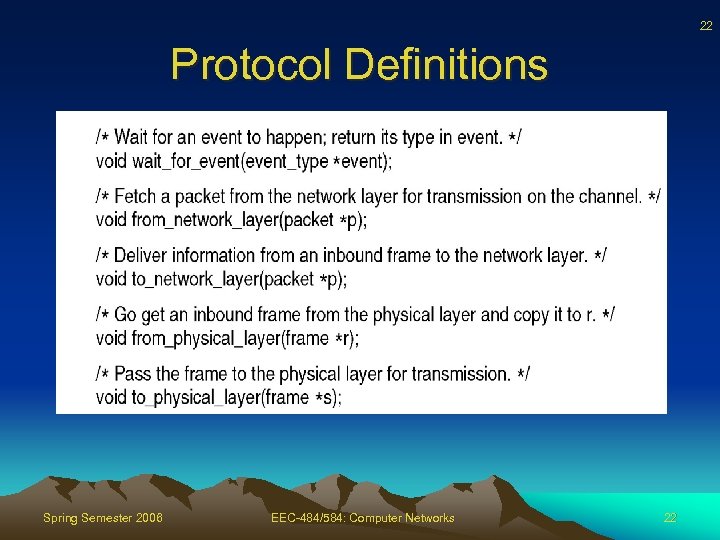
22 Protocol Definitions Spring Semester 2006 EEC-484/584: Computer Networks 22

23 Protocol Definitions Spring Semester 2006 EEC-484/584: Computer Networks 23

24 Unrestricted Simplex Protocol • Additional assumptions – Processing time insignificant – Infinite buffer space – Communication channel never loses or damages frames • Uses no sequence numbers or acks – Only event type frame_arrival Spring Semester 2006 EEC-484/584: Computer Networks 24
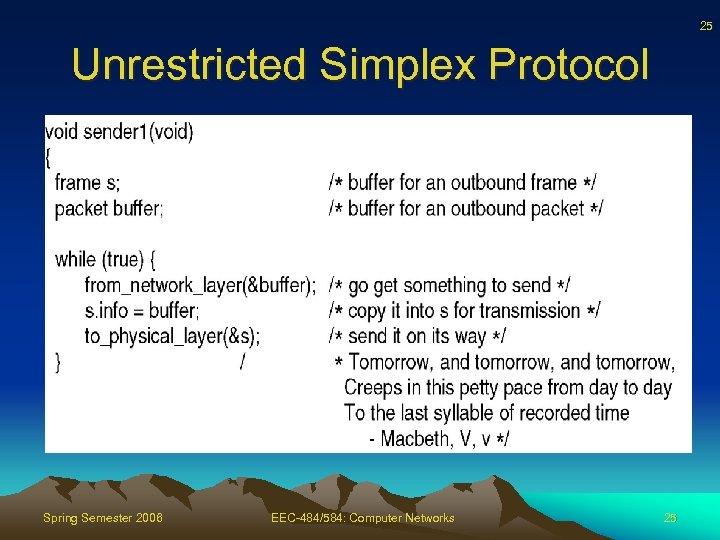
25 Unrestricted Simplex Protocol Spring Semester 2006 EEC-484/584: Computer Networks 25
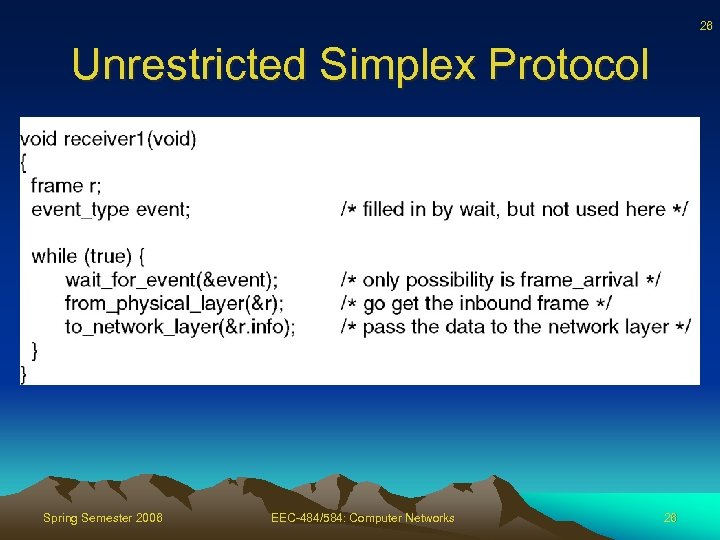
26 Unrestricted Simplex Protocol Spring Semester 2006 EEC-484/584: Computer Networks 26
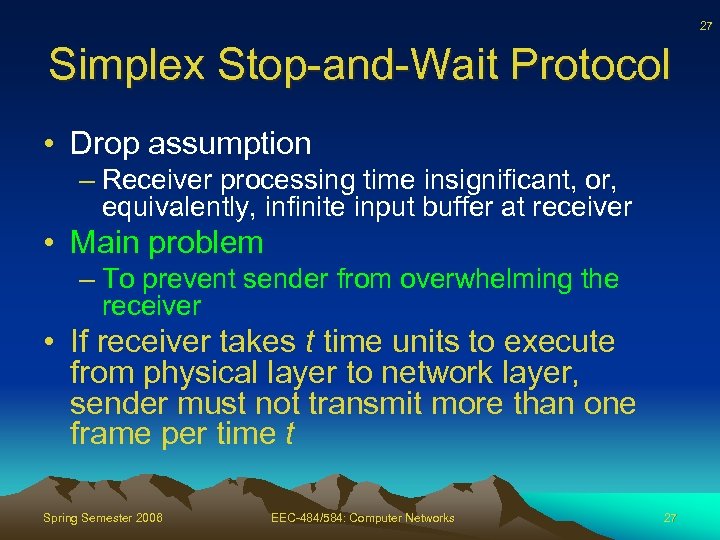
27 Simplex Stop-and-Wait Protocol • Drop assumption – Receiver processing time insignificant, or, equivalently, infinite input buffer at receiver • Main problem – To prevent sender from overwhelming the receiver • If receiver takes t time units to execute from physical layer to network layer, sender must not transmit more than one frame per time t Spring Semester 2006 EEC-484/584: Computer Networks 27

28 Simplex Stop-and-Wait Protocol • One solution – too conservative – Restrict sender so transmits so slowly that even if frame undergoes max delay no buffer overflows • Better solution – Receiver provides feedback to sender and gives sender permission to send next frame • Sender sends frame, stop and wait for ack • Alternates between sender and receiver – Half-duplex Spring Semester 2006 EEC-484/584: Computer Networks 28
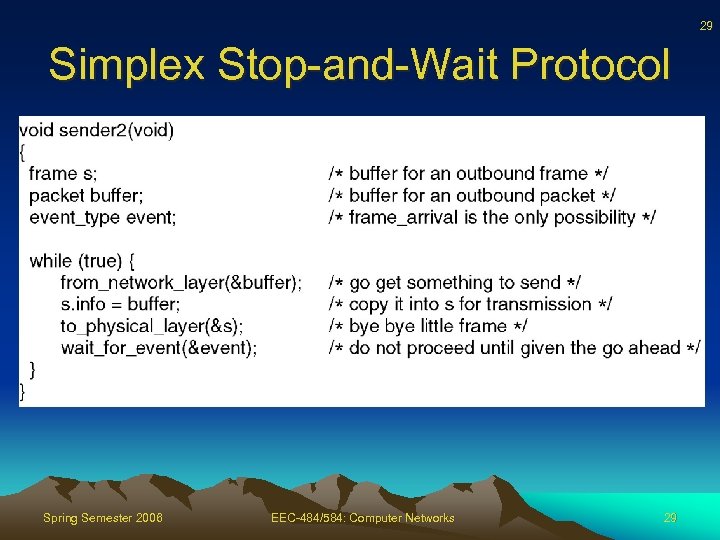
29 Simplex Stop-and-Wait Protocol Spring Semester 2006 EEC-484/584: Computer Networks 29
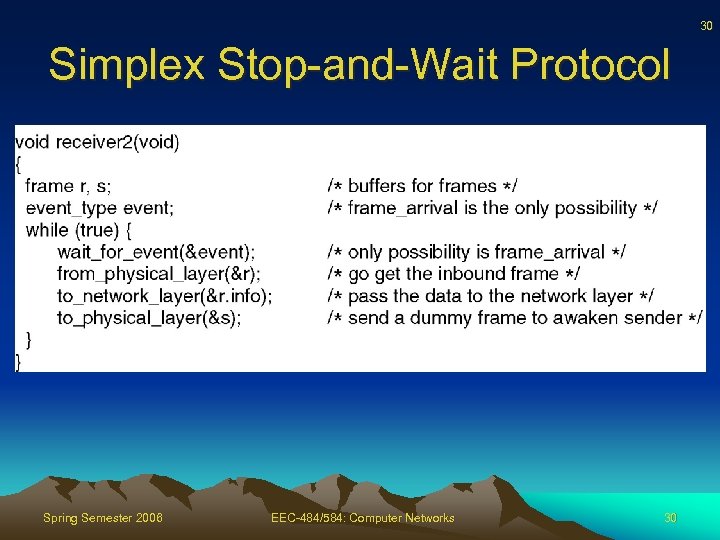
30 Simplex Stop-and-Wait Protocol Spring Semester 2006 EEC-484/584: Computer Networks 30
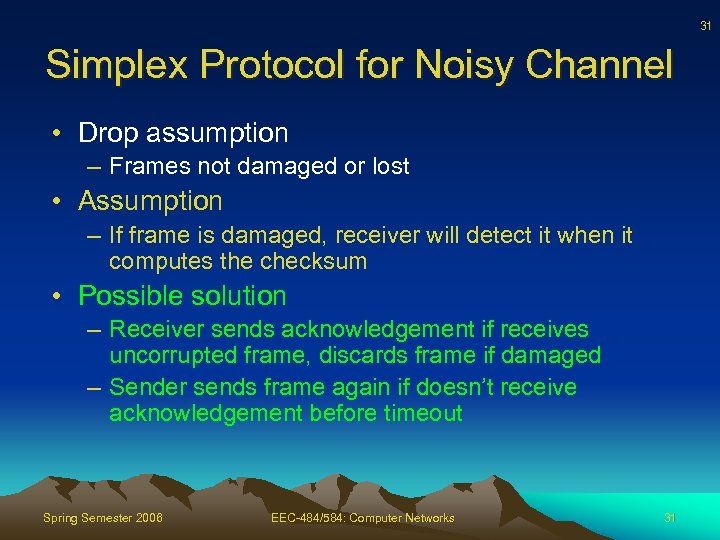
31 Simplex Protocol for Noisy Channel • Drop assumption – Frames not damaged or lost • Assumption – If frame is damaged, receiver will detect it when it computes the checksum • Possible solution – Receiver sends acknowledgement if receives uncorrupted frame, discards frame if damaged – Sender sends frame again if doesn’t receive acknowledgement before timeout Spring Semester 2006 EEC-484/584: Computer Networks 31

32 Simplex Protocol for Noisy Channel • Problem: duplicate messages – Receiver receives uncorrupted frame, sends acknowledgement – Sender times out before receiving acknowledgement, sends frame again – Receiver receives second copy uncorrupted – has duplicate copies • Solution – Use sequence numbers: 1 bit suffices Spring Semester 2006 EEC-484/584: Computer Networks 32
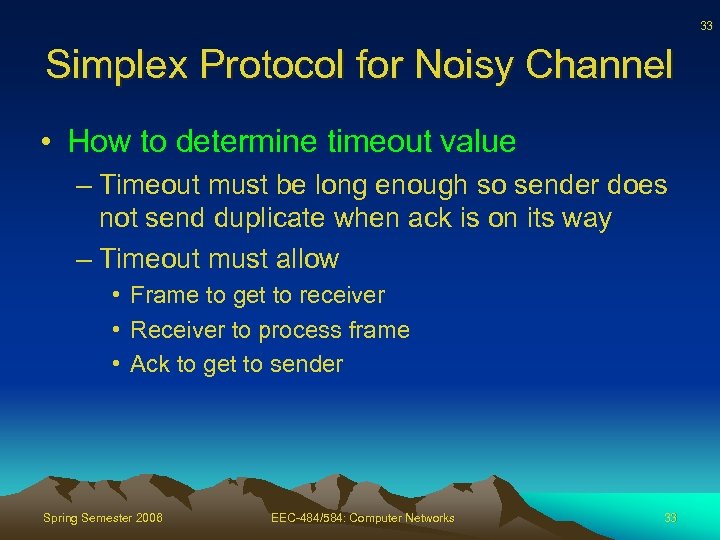
33 Simplex Protocol for Noisy Channel • How to determine timeout value – Timeout must be long enough so sender does not send duplicate when ack is on its way – Timeout must allow • Frame to get to receiver • Receiver to process frame • Ack to get to sender Spring Semester 2006 EEC-484/584: Computer Networks 33
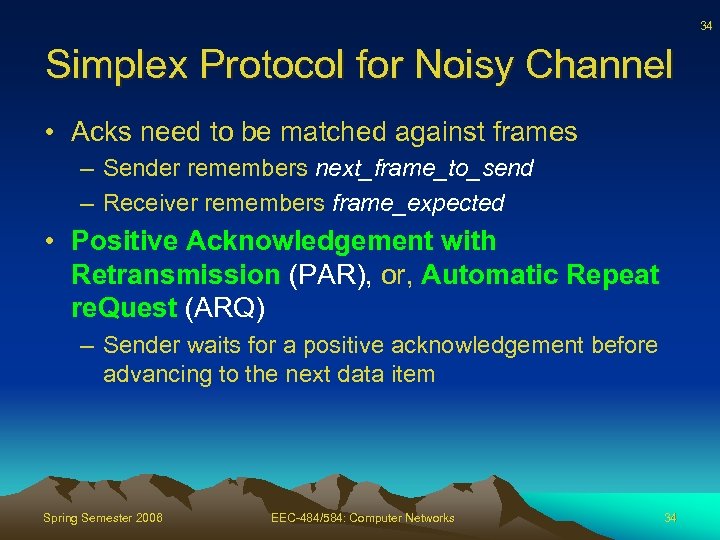
34 Simplex Protocol for Noisy Channel • Acks need to be matched against frames – Sender remembers next_frame_to_send – Receiver remembers frame_expected • Positive Acknowledgement with Retransmission (PAR), or, Automatic Repeat re. Quest (ARQ) – Sender waits for a positive acknowledgement before advancing to the next data item Spring Semester 2006 EEC-484/584: Computer Networks 34
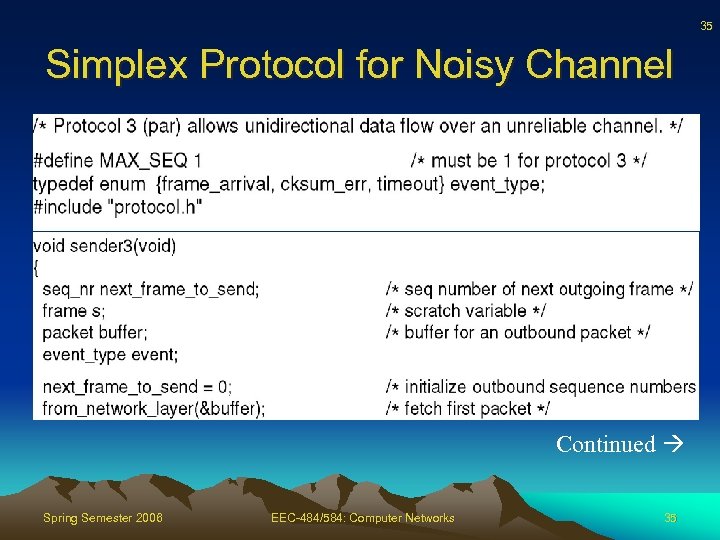
35 Simplex Protocol for Noisy Channel Continued Spring Semester 2006 EEC-484/584: Computer Networks 35
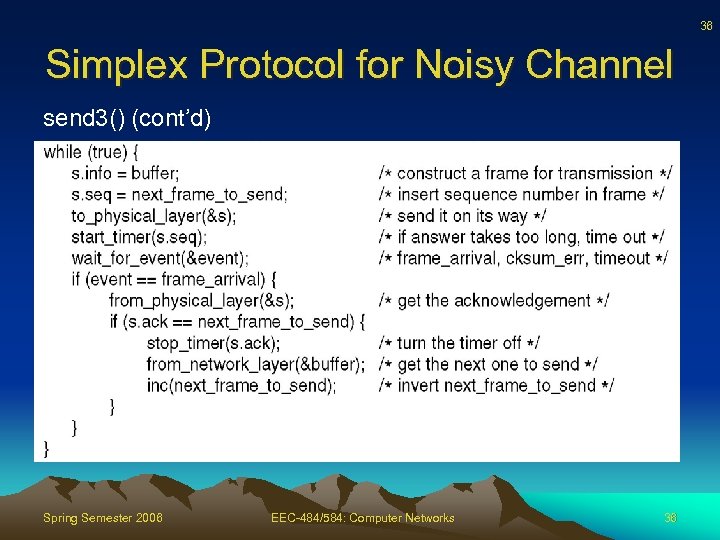
36 Simplex Protocol for Noisy Channel send 3() (cont’d) Spring Semester 2006 EEC-484/584: Computer Networks 36
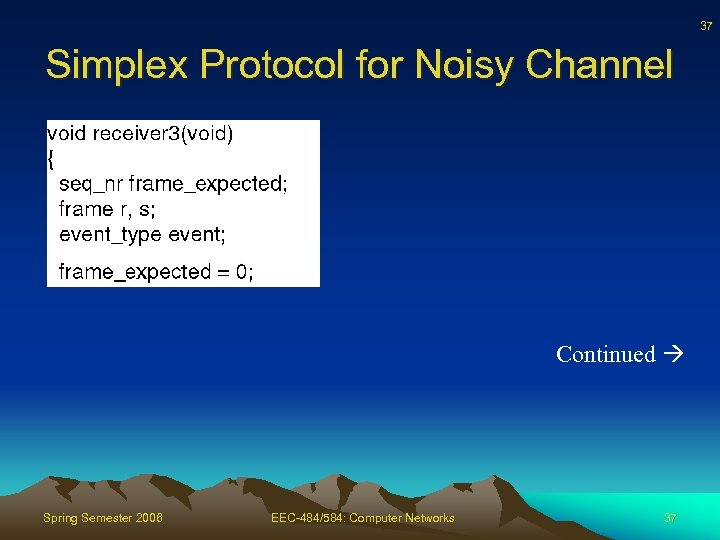
37 Simplex Protocol for Noisy Channel Continued Spring Semester 2006 EEC-484/584: Computer Networks 37
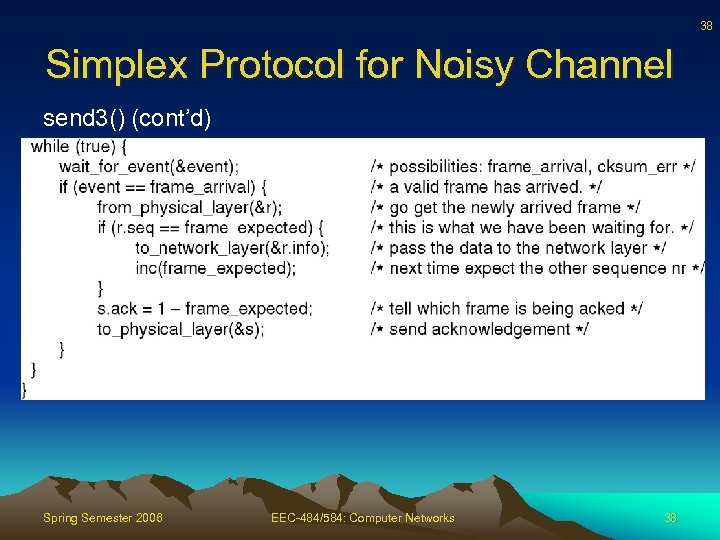
38 Simplex Protocol for Noisy Channel send 3() (cont’d) Spring Semester 2006 EEC-484/584: Computer Networks 38
39 Example Data Link Protocols • High-Level Data Link Control • PPP • Included for completeness, not required for quiz Spring Semester 2006 EEC-484/584: Computer Networks 39
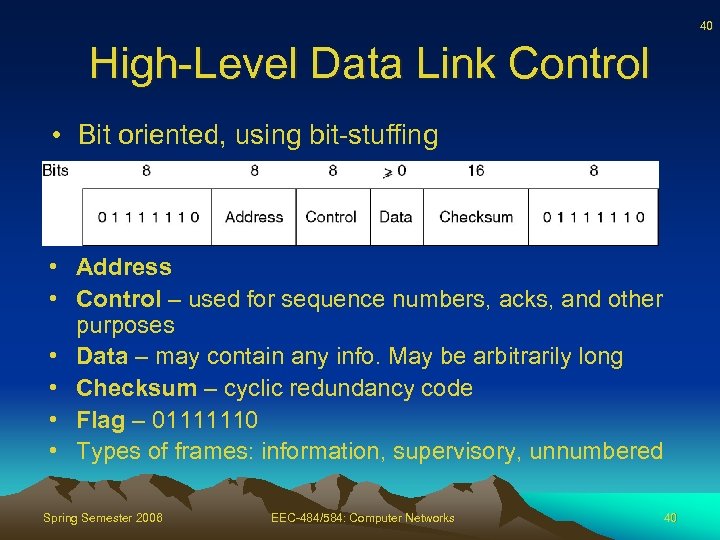
40 High-Level Data Link Control • Bit oriented, using bit-stuffing • Address • Control – used for sequence numbers, acks, and other purposes • Data – may contain any info. May be arbitrarily long • Checksum – cyclic redundancy code • Flag – 01111110 • Types of frames: information, supervisory, unnumbered Spring Semester 2006 EEC-484/584: Computer Networks 40
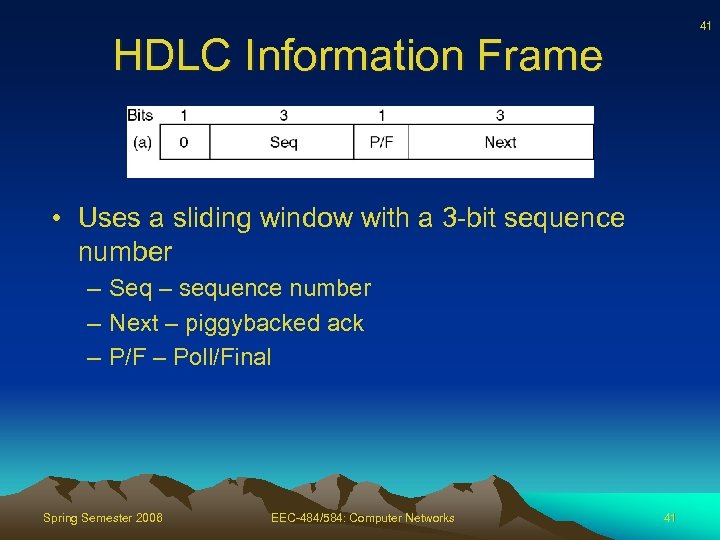
41 HDLC Information Frame • Uses a sliding window with a 3 -bit sequence number – Seq – sequence number – Next – piggybacked ack – P/F – Poll/Final Spring Semester 2006 EEC-484/584: Computer Networks 41
42 Point-to-Point Protocol • A framing method (using byte stuffing) • LCP (link control protocol) – for bringing lines up, testing them, negotiating options and bringing them down again • NCP (network control protocol) – to negotiate network-layer options in a way that is independent of the network layer protocol to be used Spring Semester 2006 EEC-484/584: Computer Networks 42
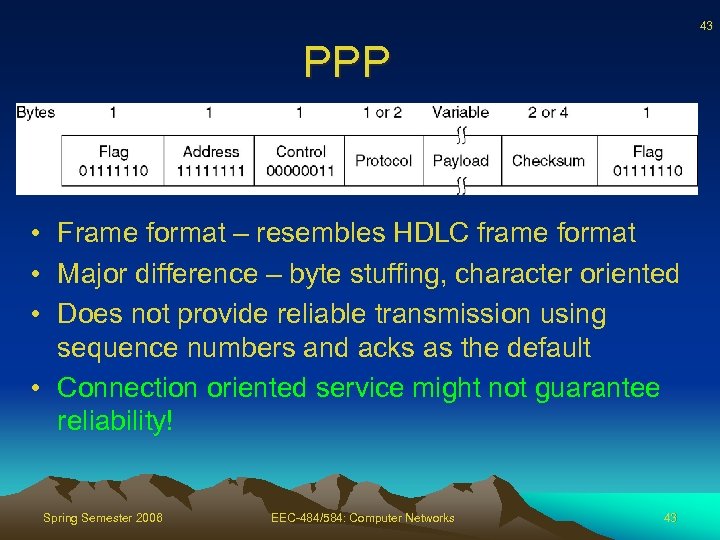
43 PPP • Frame format – resembles HDLC frame format • Major difference – byte stuffing, character oriented • Does not provide reliable transmission using sequence numbers and acks as the default • Connection oriented service might not guarantee reliability! Spring Semester 2006 EEC-484/584: Computer Networks 43
cd8cf7600b38b4bb17237b93e5717462.ppt