1b6fe7acef8d7ea8380ba7e8e2a38d61.ppt
- Количество слайдов: 77
 EE 515/IS 523 Think Like an Adversary Lecture 7 Usability/Software Failures Yongdae Kim
EE 515/IS 523 Think Like an Adversary Lecture 7 Usability/Software Failures Yongdae Kim
![Recap ^http: //security 101. kr ^E-mail policy 4 Include [ee 515] or [is 523] Recap ^http: //security 101. kr ^E-mail policy 4 Include [ee 515] or [is 523]](https://present5.com/presentation/1b6fe7acef8d7ea8380ba7e8e2a38d61/image-2.jpg) Recap ^http: //security 101. kr ^E-mail policy 4 Include [ee 515] or [is 523] in the subject of your e-mail ^Student Survey 4 http: //bit. ly/Si. K 9 M 3 ^Student Presentation 4 Send me email. ^Preproposal meeting: Today after class
Recap ^http: //security 101. kr ^E-mail policy 4 Include [ee 515] or [is 523] in the subject of your e-mail ^Student Survey 4 http: //bit. ly/Si. K 9 M 3 ^Student Presentation 4 Send me email. ^Preproposal meeting: Today after class
 Definitions ^ Identification - a claim about identity 4 Who or what I am (global or local) ^ Authentication - confirming that claims are true 4 I am who I say I am 4 I have a valid credential ^ Authorization - granting permission based on a valid claim 4 Now that I have been validated, I am allowed to access certain resources or take certain actions ^ Access control system - a system that authenticates users and gives them access to resources based on their authorizations 4 Includes or relies upon an authentication mechanism 4 May include the ability to grant course or fine-grained authorizations, revoke or delegate authorizations 4 Also includes an interface for policy configuration and management
Definitions ^ Identification - a claim about identity 4 Who or what I am (global or local) ^ Authentication - confirming that claims are true 4 I am who I say I am 4 I have a valid credential ^ Authorization - granting permission based on a valid claim 4 Now that I have been validated, I am allowed to access certain resources or take certain actions ^ Access control system - a system that authenticates users and gives them access to resources based on their authorizations 4 Includes or relies upon an authentication mechanism 4 May include the ability to grant course or fine-grained authorizations, revoke or delegate authorizations 4 Also includes an interface for policy configuration and management
 Building blocks of authentication ^Factors 4 Something you know (or recognize) 4 Something you have 4 Something you are ^Two factors are better than one 4 Especially two factors from different categories ^What are some examples of each of these factors? ^What are some examples of two-factor authentication?
Building blocks of authentication ^Factors 4 Something you know (or recognize) 4 Something you have 4 Something you are ^Two factors are better than one 4 Especially two factors from different categories ^What are some examples of each of these factors? ^What are some examples of two-factor authentication?
 Authentication mechanisms ^Text-based passwords ^Graphical passwords ^Hardware tokens ^Public key crypto protocols ^Biometrics
Authentication mechanisms ^Text-based passwords ^Graphical passwords ^Hardware tokens ^Public key crypto protocols ^Biometrics
 Evaluation ^Accessibility ^Memorability ^Security ^Cost ^Environmental considerations
Evaluation ^Accessibility ^Memorability ^Security ^Cost ^Environmental considerations
 Typical password advice
Typical password advice
 Typical password advice ^Pick a hard to guess password ^Don’t use it anywhere else ^Change it often ^Don’t write it down So what do you do when every web site you visit asks for a password?
Typical password advice ^Pick a hard to guess password ^Don’t use it anywhere else ^Change it often ^Don’t write it down So what do you do when every web site you visit asks for a password?
 Bank = b 3 a. YZ Amazon = aa 66 x! Phonebill = p$2$ta 1
Bank = b 3 a. YZ Amazon = aa 66 x! Phonebill = p$2$ta 1

 Problems with Passwords ^Selection – Difficult to think of a good password – Passwords people think of first are easy to guess ^Memorability – Easy to forget passwords that aren’t frequently used – Difficult to remember “secure” passwords with a mix of upper & lower case letters, numbers, and special characters ^Reuse – Too many passwords to remember – A previously used password is memorable ^Sharing – Often unintentional through reuse – Systems aren’t designed to support the way people work together and share information
Problems with Passwords ^Selection – Difficult to think of a good password – Passwords people think of first are easy to guess ^Memorability – Easy to forget passwords that aren’t frequently used – Difficult to remember “secure” passwords with a mix of upper & lower case letters, numbers, and special characters ^Reuse – Too many passwords to remember – A previously used password is memorable ^Sharing – Often unintentional through reuse – Systems aren’t designed to support the way people work together and share information
 Mnemonic Passwords F Four s score and s seven y years a ago , o our First letter of each word (with punctuation) Substitute numbers for words or similar-looking letters Substitute symbols for words or similar-looking letters Source: Cynthia Kuo, SOUPS 2006 4 sa 7 ya, o. F 4 sasya, o. F fsasya, o. F 4 sa 7 ya, o. F 4 s&7 ya, o. F F Fathers
Mnemonic Passwords F Four s score and s seven y years a ago , o our First letter of each word (with punctuation) Substitute numbers for words or similar-looking letters Substitute symbols for words or similar-looking letters Source: Cynthia Kuo, SOUPS 2006 4 sa 7 ya, o. F 4 sasya, o. F fsasya, o. F 4 sa 7 ya, o. F 4 s&7 ya, o. F F Fathers
 The Promise? ^Phrases help users incorporate different character classes in passwords 4 Easier to think of character-for-word substitutions ^Virtually infinite number of phrases ^Dictionaries do not contain mnemonics Source: Cynthia Kuo, SOUPS 2006
The Promise? ^Phrases help users incorporate different character classes in passwords 4 Easier to think of character-for-word substitutions ^Virtually infinite number of phrases ^Dictionaries do not contain mnemonics Source: Cynthia Kuo, SOUPS 2006
 Mnemonic password evaluation ^Mnemonic passwords are not a panacea for password creation ^No comprehensive dictionary today ^May become more vulnerable in future – Many people start to use them – Attackers incentivized to build dictionaries ^Publicly available phrases should be avoided! Source: Cynthia Kuo, SOUPS 2006
Mnemonic password evaluation ^Mnemonic passwords are not a panacea for password creation ^No comprehensive dictionary today ^May become more vulnerable in future – Many people start to use them – Attackers incentivized to build dictionaries ^Publicly available phrases should be avoided! Source: Cynthia Kuo, SOUPS 2006
 Password keeper software ^Run on PC or handheld ^Only remember one password
Password keeper software ^Run on PC or handheld ^Only remember one password
 Single sign-on ^Login once to get access to all your passwords
Single sign-on ^Login once to get access to all your passwords
 Biometrics
Biometrics
 Fingerprint Spoofing ^Devices 4 Microsoft Fingerprint Reader 4 APC Biometric Security device ^Success! 4 Very soft piece of wax flattened against hard surface 4 Press the finger to be molded for 5 minutes 4 Transfer wax to freezer for 10 -15 minutes 4 Firmly press modeling material into cast 4 Press against the fingerprint reader ^Replicated several times
Fingerprint Spoofing ^Devices 4 Microsoft Fingerprint Reader 4 APC Biometric Security device ^Success! 4 Very soft piece of wax flattened against hard surface 4 Press the finger to be molded for 5 minutes 4 Transfer wax to freezer for 10 -15 minutes 4 Firmly press modeling material into cast 4 Press against the fingerprint reader ^Replicated several times
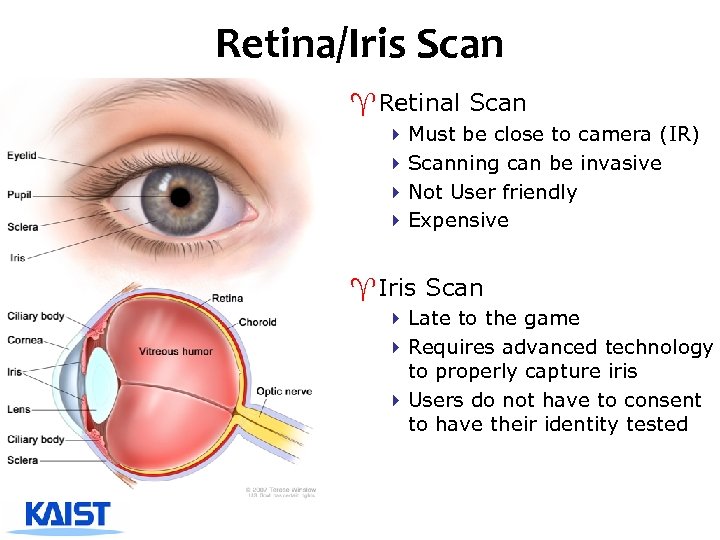 Retina/Iris Scan ^Retinal Scan 4 Must be close to camera (IR) 4 Scanning can be invasive 4 Not User friendly 4 Expensive ^Iris Scan 4 Late to the game 4 Requires advanced technology to properly capture iris 4 Users do not have to consent to have their identity tested
Retina/Iris Scan ^Retinal Scan 4 Must be close to camera (IR) 4 Scanning can be invasive 4 Not User friendly 4 Expensive ^Iris Scan 4 Late to the game 4 Requires advanced technology to properly capture iris 4 Users do not have to consent to have their identity tested
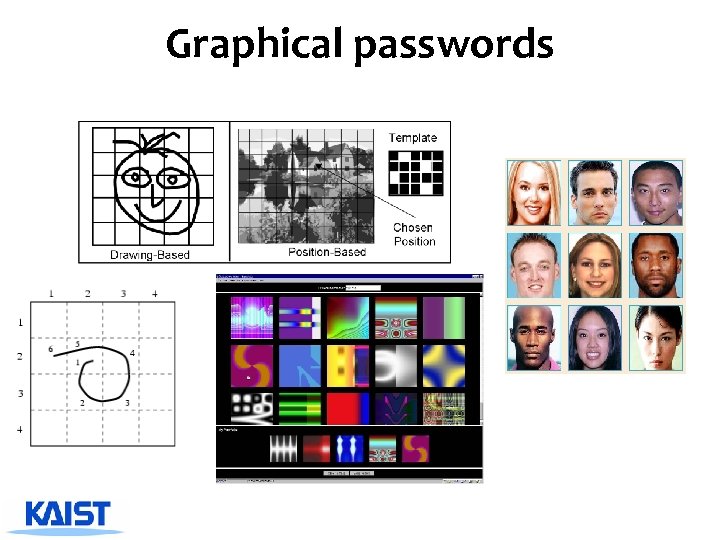 Graphical passwords
Graphical passwords
 “Forgotten password” mechanism ^Email password or magic URL to address on file ^Challenge questions ^Why not make this the normal way to access infrequently used sites?
“Forgotten password” mechanism ^Email password or magic URL to address on file ^Challenge questions ^Why not make this the normal way to access infrequently used sites?
 Convenient Secure. ID 1 ^What problems does this approach solve? ^What problems does it create? Source: http: //worsethanfailure. com/Articles/Security_by_Oblivity. aspx
Convenient Secure. ID 1 ^What problems does this approach solve? ^What problems does it create? Source: http: //worsethanfailure. com/Articles/Security_by_Oblivity. aspx
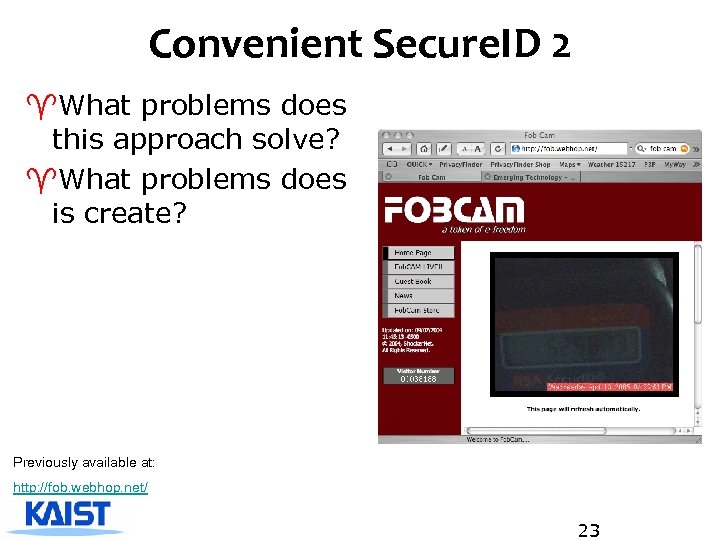 Convenient Secure. ID 2 ^What problems does this approach solve? ^What problems does is create? Previously available at: http: //fob. webhop. net/ 23
Convenient Secure. ID 2 ^What problems does this approach solve? ^What problems does is create? Previously available at: http: //fob. webhop. net/ 23
 Browser-based mutual authentication ^ Chris Drake’s “Magic Bullet” proposal ^ http: //lists. w 3. org/Archives/Public/public-usableauthentication/2007 Mar/0004. html – User gets ID, password (or alternative), image, hotspot at enrollment – Before user is allowed to login they are asked to confirm URL and SSL cert and click buttons – Then login box appears and user enters username and password (or alternative) – Server displays set of images, including user’s image (or if user entered incorrect password, random set of images appear) – User finds their image and clicks on hotspot • Image manipulation can help prevent replay attacks ^ What problems does this solve? ^ What problems doesn’t it solve? ^ What kind of testing is needed
Browser-based mutual authentication ^ Chris Drake’s “Magic Bullet” proposal ^ http: //lists. w 3. org/Archives/Public/public-usableauthentication/2007 Mar/0004. html – User gets ID, password (or alternative), image, hotspot at enrollment – Before user is allowed to login they are asked to confirm URL and SSL cert and click buttons – Then login box appears and user enters username and password (or alternative) – Server displays set of images, including user’s image (or if user entered incorrect password, random set of images appear) – User finds their image and clicks on hotspot • Image manipulation can help prevent replay attacks ^ What problems does this solve? ^ What problems doesn’t it solve? ^ What kind of testing is needed
 Phishing
Phishing
 Spear Phishing (Targeted Phishing) ^Personalized mail for a (small) group of targeted users 4 Employees, Facebook friends, Alumni, e. Commerce Customers 4 These groups can be obtained through identity theft! ^Content of the email is personalized. 4 Different from Viagra phishing/spam ^Combined with other attacks 4 Zero-day vulnerability: unpatched 4 Rootkit: Below OS kernel, impossible to detect with AV software 4 Key logger: Further obtain ID/password 4 APT (Advanced Persistent Threat): long-term surveillance 26
Spear Phishing (Targeted Phishing) ^Personalized mail for a (small) group of targeted users 4 Employees, Facebook friends, Alumni, e. Commerce Customers 4 These groups can be obtained through identity theft! ^Content of the email is personalized. 4 Different from Viagra phishing/spam ^Combined with other attacks 4 Zero-day vulnerability: unpatched 4 Rootkit: Below OS kernel, impossible to detect with AV software 4 Key logger: Further obtain ID/password 4 APT (Advanced Persistent Threat): long-term surveillance 26
 Examples of Spear Phishing 27
Examples of Spear Phishing 27
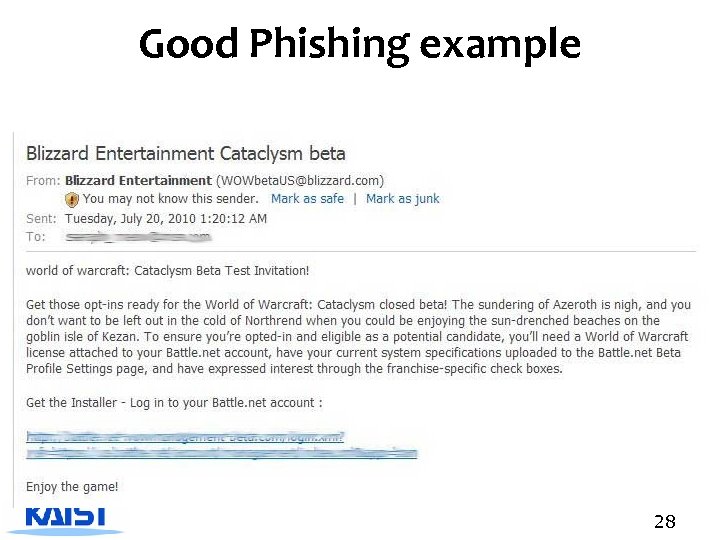 Good Phishing example 28
Good Phishing example 28
 Policy and Usability
Policy and Usability

 Cost of Reading Policy Cranor et al. ^TR= p x R x n 4 p is the population of all Internet users 4 R is the average time to read one policy 4 n is the average number of unique sites Internet users visit annually ^p = 221 million Americans online (Nielsen, May 2008) ^R = avg time to read a policy = # words in policy / reading rate 4 To estimate words per policy: - Measured the policy length of the 75 most visited websites - Reflects policies people are most likely to visit ^Reading rate = 250 WPM Mid estimate: 2, 514 words / 250 WPM = 10 minutes
Cost of Reading Policy Cranor et al. ^TR= p x R x n 4 p is the population of all Internet users 4 R is the average time to read one policy 4 n is the average number of unique sites Internet users visit annually ^p = 221 million Americans online (Nielsen, May 2008) ^R = avg time to read a policy = # words in policy / reading rate 4 To estimate words per policy: - Measured the policy length of the 75 most visited websites - Reflects policies people are most likely to visit ^Reading rate = 250 WPM Mid estimate: 2, 514 words / 250 WPM = 10 minutes
 ^n = number of unique sites per year 4 Nielsen estimates Americans visit 185 unique sites in a month: 4 but that doesn’t quite scale x 12, so 1462 unique sites per year. ^TR= p x R x n = 221 million x 10 minutes x 1462 sites ^R x n = 244 hours per year person
^n = number of unique sites per year 4 Nielsen estimates Americans visit 185 unique sites in a month: 4 but that doesn’t quite scale x 12, so 1462 unique sites per year. ^TR= p x R x n = 221 million x 10 minutes x 1462 sites ^R x n = 244 hours per year person
 P 3 P: Platform for Privacy Preferences ^A framework for automated privacy discussions 4 Web sites disclose their privacy practices in standard machine-readable formats 4 Web browsers automatically retrieve P 3 P privacy policies and compare them to users’ privacy preferences 4 Sites and browsers can then negotiate about privacy terms
P 3 P: Platform for Privacy Preferences ^A framework for automated privacy discussions 4 Web sites disclose their privacy practices in standard machine-readable formats 4 Web browsers automatically retrieve P 3 P privacy policies and compare them to users’ privacy preferences 4 Sites and browsers can then negotiate about privacy terms


 Why Johnny Can’t Encrypt - A Usability Evaluation of PGP 5. 0 - Alma Whitten and J. D. Tygar Usenix Sec’ 99 Presented by Yongdae Kim Some of the Slides borrowed from Jeremy Hyland
Why Johnny Can’t Encrypt - A Usability Evaluation of PGP 5. 0 - Alma Whitten and J. D. Tygar Usenix Sec’ 99 Presented by Yongdae Kim Some of the Slides borrowed from Jeremy Hyland
 Defining Usable Security Software ^Security software is usable if the people who are expected to use it: 4 are reliably made aware of the security tasks they need to perform. 4 are able to figure out how to successfully perform those tasks 4 don't make dangerous errors 4 are sufficiently comfortable with the interface to continue using it.
Defining Usable Security Software ^Security software is usable if the people who are expected to use it: 4 are reliably made aware of the security tasks they need to perform. 4 are able to figure out how to successfully perform those tasks 4 don't make dangerous errors 4 are sufficiently comfortable with the interface to continue using it.
 Why is usable security hard? 1. The unmotivated users 4“Security is usually a secondary goal” 2. Policy Abstraction 4 Programmers understand the representation but normal users have no background knowledge. 3. The lack of feedback 4 We can’t predict every situation. 4. The proverbial “barn door” 4 Need to focus on error prevention. 5. The weakest link 4 Attacker only needs to find one vulnerability
Why is usable security hard? 1. The unmotivated users 4“Security is usually a secondary goal” 2. Policy Abstraction 4 Programmers understand the representation but normal users have no background knowledge. 3. The lack of feedback 4 We can’t predict every situation. 4. The proverbial “barn door” 4 Need to focus on error prevention. 5. The weakest link 4 Attacker only needs to find one vulnerability
 Why Johnny can’t encrypt? ^PGP 5. 0 4 Pretty Good Privacy 4 Software for encrypting and signing data 4 Plug-in provides “easy” use with email clients 4 Modern GUI, well designed by most standards ^Usability Evaluation following their definition If an average user of email feels the need for privacy and authentication, and acquires PGP with that purpose in mind, will PGP's current design allow that person to realize what needs to be done, figure out how to do it, and avoid dangerous errors, without becoming so frustrated that he or she decides to give up on using PGP after all?
Why Johnny can’t encrypt? ^PGP 5. 0 4 Pretty Good Privacy 4 Software for encrypting and signing data 4 Plug-in provides “easy” use with email clients 4 Modern GUI, well designed by most standards ^Usability Evaluation following their definition If an average user of email feels the need for privacy and authentication, and acquires PGP with that purpose in mind, will PGP's current design allow that person to realize what needs to be done, figure out how to do it, and avoid dangerous errors, without becoming so frustrated that he or she decides to give up on using PGP after all?
 Usability Evaluation Methods ^Cognitive walk through 4 Mentally step through the software as if we were a new user. Attempt to identify the usability pitfalls. 4 Focus on interface learnablity. ^Results
Usability Evaluation Methods ^Cognitive walk through 4 Mentally step through the software as if we were a new user. Attempt to identify the usability pitfalls. 4 Focus on interface learnablity. ^Results
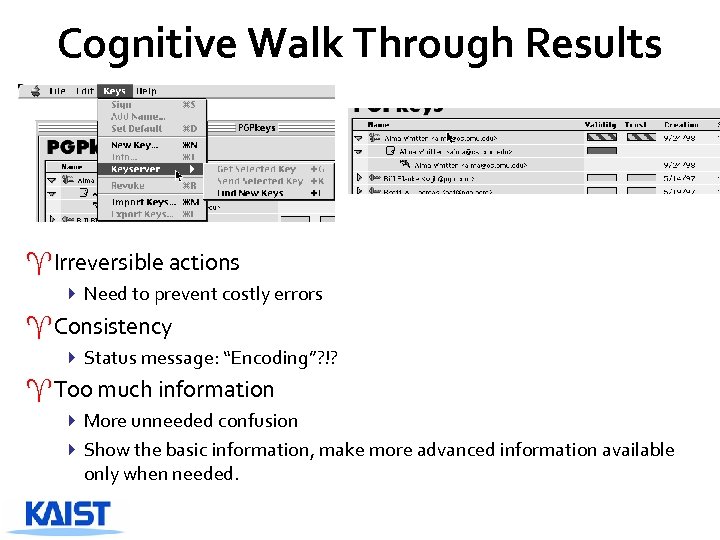 Cognitive Walk Through Results ^Irreversible actions 4 Need to prevent costly errors ^Consistency 4 Status message: “Encoding”? !? ^Too much information 4 More unneeded confusion 4 Show the basic information, make more advanced information available only when needed.
Cognitive Walk Through Results ^Irreversible actions 4 Need to prevent costly errors ^Consistency 4 Status message: “Encoding”? !? ^Too much information 4 More unneeded confusion 4 Show the basic information, make more advanced information available only when needed.
 User Test ^User Test 4 PGP 5. 0 with Eudora 412 participants all with at least some college and none with advanced knowledge of encryption 4 Participants were given a scenario with tasks to complete within 90 min 4 Tasks built on each other 4 Participants could ask some questions through email
User Test ^User Test 4 PGP 5. 0 with Eudora 412 participants all with at least some college and none with advanced knowledge of encryption 4 Participants were given a scenario with tasks to complete within 90 min 4 Tasks built on each other 4 Participants could ask some questions through email
 User Test Results ^3 users accidentally sent the message in clear text ^7 users used their public key to encrypt and only 2 of the 7 figured out how to correct the problem ^Only 2 users were able to decrypt without problems ^Only 1 user figured out how to deal with RSA keys correctly. ^A total of 3 users were able to successfully complete the basic process of sending and receiving encrypted emails. ^One user was not able to encrypt at all
User Test Results ^3 users accidentally sent the message in clear text ^7 users used their public key to encrypt and only 2 of the 7 figured out how to correct the problem ^Only 2 users were able to decrypt without problems ^Only 1 user figured out how to deal with RSA keys correctly. ^A total of 3 users were able to successfully complete the basic process of sending and receiving encrypted emails. ^One user was not able to encrypt at all
 Conclusion ^Reminder If an average user of email feels the need for privacy and authentication, and acquires PGP with that purpose in mind, will PGP's current design allow that person to realize what needs to be done, figure out how to do it, and avoid dangerous errors, without becoming so frustrated that he or she decides to give up on using PGP after all? ^Is this a failure in the design of the PGP 5. 0 interface or is it a function of the problem of traditional usable design vs. design for usable secure systems? ^What other issues? What kind of similar security issues? What do we learn from this paper?
Conclusion ^Reminder If an average user of email feels the need for privacy and authentication, and acquires PGP with that purpose in mind, will PGP's current design allow that person to realize what needs to be done, figure out how to do it, and avoid dangerous errors, without becoming so frustrated that he or she decides to give up on using PGP after all? ^Is this a failure in the design of the PGP 5. 0 interface or is it a function of the problem of traditional usable design vs. design for usable secure systems? ^What other issues? What kind of similar security issues? What do we learn from this paper?
 Analysis of an Electronic Voting System TADAYOSHI KOHNO ADAM STUBBLEFIELD† AVIEL D. RUBIN‡ DAN S. WALLACH§ February 27, 2004 Presented by: Aldo Villanueva
Analysis of an Electronic Voting System TADAYOSHI KOHNO ADAM STUBBLEFIELD† AVIEL D. RUBIN‡ DAN S. WALLACH§ February 27, 2004 Presented by: Aldo Villanueva
 Outline ^Palm Beach Fiasco ^Introducing DRE ^History of Diebold ^Vulnerabilities of Diebold DRE ^Summary 46
Outline ^Palm Beach Fiasco ^Introducing DRE ^History of Diebold ^Vulnerabilities of Diebold DRE ^Summary 46
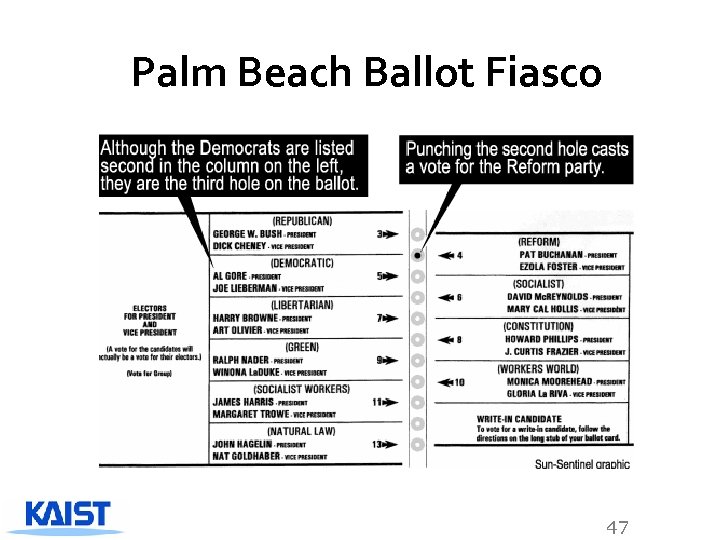 Palm Beach Ballot Fiasco 47
Palm Beach Ballot Fiasco 47
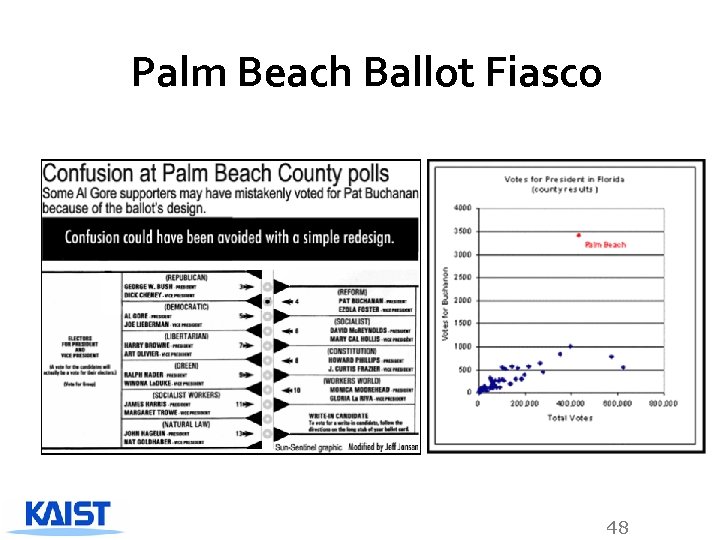 Palm Beach Ballot Fiasco 48
Palm Beach Ballot Fiasco 48
 DRE “Direct Recording Electronic” ^Eliminate paper ballots from the voting process. ^Process: 4 The voter arrives to the voting place and prove he’s allowed to vote there. 4 He gets a token (PIN or smartcard). 4 Enters the token in the voting terminal and votes for its candidate. 4 DRE System presents the voter’s election and gives a final chance to make changes.
DRE “Direct Recording Electronic” ^Eliminate paper ballots from the voting process. ^Process: 4 The voter arrives to the voting place and prove he’s allowed to vote there. 4 He gets a token (PIN or smartcard). 4 Enters the token in the voting terminal and votes for its candidate. 4 DRE System presents the voter’s election and gives a final chance to make changes.
 History • 1995: I-Mark Systems • 1997: Global Election Systems acquired I-Mark • 2002: Diebold acquired GES and change the name to Diebold Election System • 2006: Diebold removed its name from the voting machines for “strategic” reasons • 2007: Diebold changed its name to "Premier Election Solutions"
History • 1995: I-Mark Systems • 1997: Global Election Systems acquired I-Mark • 2002: Diebold acquired GES and change the name to Diebold Election System • 2006: Diebold removed its name from the voting machines for “strategic” reasons • 2007: Diebold changed its name to "Premier Election Solutions"
 Analysis of the Diebold’s Accu. Vote-TS DRE voting system ^The source code for Diebold’s Accu. Vote-TS DRE voting system was analyzed. ^There were several vulnerabilities found.
Analysis of the Diebold’s Accu. Vote-TS DRE voting system ^The source code for Diebold’s Accu. Vote-TS DRE voting system was analyzed. ^There were several vulnerabilities found.
 Vulnerability No. 1: Smartcards ^The smartcards used in the voting process are very easy to fake since they don’t perform any cryptographic operations. ^Attacker could: 4 Cast multiple votes 4 End the elections early
Vulnerability No. 1: Smartcards ^The smartcards used in the voting process are very easy to fake since they don’t perform any cryptographic operations. ^Attacker could: 4 Cast multiple votes 4 End the elections early
 Vulnerability No. 2: Tampering ^System configuration : impersonating any other voting terminal. ^Ballot definitions: changing the order of the candidates only in the interface ^Election results: modifying the voting records file stored on the device
Vulnerability No. 2: Tampering ^System configuration : impersonating any other voting terminal. ^Ballot definitions: changing the order of the candidates only in the interface ^Election results: modifying the voting records file stored on the device
 Vulnerability No. 3: Impersonating legitimate voting terminals ^Voting terminals are configured to upload voting totals to a system after an election. ^An adversary able to pose as a legitimate voting terminal to the tabulating authority could report false vote counts.
Vulnerability No. 3: Impersonating legitimate voting terminals ^Voting terminals are configured to upload voting totals to a system after an election. ^An adversary able to pose as a legitimate voting terminal to the tabulating authority could report false vote counts.
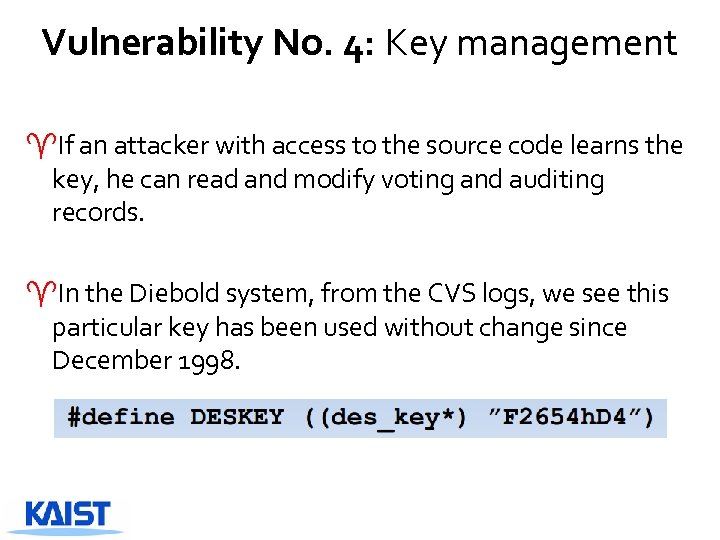 Vulnerability No. 4: Key management ^If an attacker with access to the source code learns the key, he can read and modify voting and auditing records. ^In the Diebold system, from the CVS logs, we see this particular key has been used without change since December 1998.
Vulnerability No. 4: Key management ^If an attacker with access to the source code learns the key, he can read and modify voting and auditing records. ^In the Diebold system, from the CVS logs, we see this particular key has been used without change since December 1998.
 Vulnerability No. 5: Linking voters to their votes ^Each vote is written sequentially to the file recording the votes. ^It’s easy for the attacker (poll worker) to access the voting records, to link voters with their votes.
Vulnerability No. 5: Linking voters to their votes ^Each vote is written sequentially to the file recording the votes. ^It’s easy for the attacker (poll worker) to access the voting records, to link voters with their votes.
 Vulnerability No. 6: Audit logs ^The whole audit log is encrypted using an insecure method. ^At the time that the logging occurs, the log can also be printed to an attached printer. ^An attacker could create discrepancies between the printed log and the log stored on the terminal by unplugging the printer (or, by simply cutting the cable).
Vulnerability No. 6: Audit logs ^The whole audit log is encrypted using an insecure method. ^At the time that the logging occurs, the log can also be printed to an attached printer. ^An attacker could create discrepancies between the printed log and the log stored on the terminal by unplugging the printer (or, by simply cutting the cable).

 Other vulnerabilities ^An attacker can delay the start of an election: 4 Do. S attack against the election management’s server preventing the voting terminals from acquiring their ballot definition in time. ^Poor software engineering: 4 Uses C++ 4 No documentation Top-to-bottom code review would be nearly impossible.
Other vulnerabilities ^An attacker can delay the start of an election: 4 Do. S attack against the election management’s server preventing the voting terminals from acquiring their ballot definition in time. ^Poor software engineering: 4 Uses C++ 4 No documentation Top-to-bottom code review would be nearly impossible.
 Summary ^Significant security flaws: 4 Voters can trivially cast multiple ballots 4 Administrative functions can be performed by regular voters 4 Threats posed by insiders such as poll workers, software developers, etc.
Summary ^Significant security flaws: 4 Voters can trivially cast multiple ballots 4 Administrative functions can be performed by regular voters 4 Threats posed by insiders such as poll workers, software developers, etc.
 SECURITY ANALYSIS OF THE DIEBOLD ACCUVOTE – TS VOTING MACHINE Ariel J. Feldman J. Alex Halderman Edward W. Felten September 13, 2006 Presented by: Jiseong Noh
SECURITY ANALYSIS OF THE DIEBOLD ACCUVOTE – TS VOTING MACHINE Ariel J. Feldman J. Alex Halderman Edward W. Felten September 13, 2006 Presented by: Jiseong Noh
 Outline ^Overview of Diebold Accu. Vote-TS Voting Machine ^Design Points ^Boot Processes ^Vulnerability Points ^Attack Scenarios ^Mitigation of the vulnerabilities ^Conclusion 62
Outline ^Overview of Diebold Accu. Vote-TS Voting Machine ^Design Points ^Boot Processes ^Vulnerability Points ^Attack Scenarios ^Mitigation of the vulnerabilities ^Conclusion 62
 Diebold Accu. Vote-TS ^Manufactured by Diebold Election Systems 4 Sold to Election Systems & Software in 2009 ^DRE – Direct Recording Electronic Voting Machine 4 Voters use machine to cast vote 4 Machine is used to record the votes 4(*) 32% of the USA registered voters used DRE in 2008 4 About 16 Million voters used Accuvote-TS in 2010 ^Custom election software runs on top of Windows CE (*)http: //www. electiondataservices. com/images/File/NR_Vote. Equip_Nov-2008 w. Appendix 2. pdf) 63
Diebold Accu. Vote-TS ^Manufactured by Diebold Election Systems 4 Sold to Election Systems & Software in 2009 ^DRE – Direct Recording Electronic Voting Machine 4 Voters use machine to cast vote 4 Machine is used to record the votes 4(*) 32% of the USA registered voters used DRE in 2008 4 About 16 Million voters used Accuvote-TS in 2010 ^Custom election software runs on top of Windows CE (*)http: //www. electiondataservices. com/images/File/NR_Vote. Equip_Nov-2008 w. Appendix 2. pdf) 63
 Design Points Serial port Touch Screen Smart Card Reader Open to Public Audio jack Processor Removable Flash Key Access Printer On-board Flash RAM EPROM Inside Box http: //web. cecs. pdx. edu/~hook/cs 491 sp 08/Access. Control. Sp 08. pdf 64
Design Points Serial port Touch Screen Smart Card Reader Open to Public Audio jack Processor Removable Flash Key Access Printer On-board Flash RAM EPROM Inside Box http: //web. cecs. pdx. edu/~hook/cs 491 sp 08/Access. Control. Sp 08. pdf 64
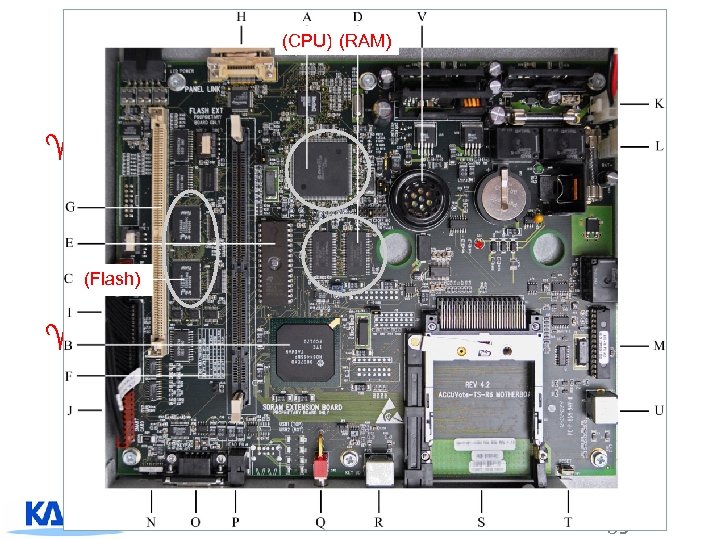 (CPU) (RAM) Design Points ^Similar to a general-purpose hand-held PC 4 A CPU, 32 MB RAM, 16 MB internal flash storage 4 Touchscreen LCD display 4 Two PC card slots – one for memory card, other for modem card (Flash) ^OS uses a customized software 4 Automatically runs Voting Program 4 Searches for special files in memory card to administer or update the system 4 Searches for script files with user confirmation 65
(CPU) (RAM) Design Points ^Similar to a general-purpose hand-held PC 4 A CPU, 32 MB RAM, 16 MB internal flash storage 4 Touchscreen LCD display 4 Two PC card slots – one for memory card, other for modem card (Flash) ^OS uses a customized software 4 Automatically runs Voting Program 4 Searches for special files in memory card to administer or update the system 4 Searches for script files with user confirmation 65
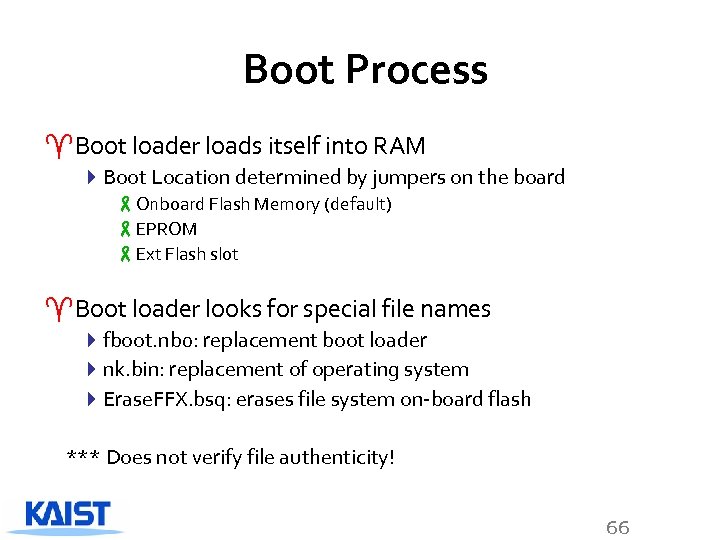 Boot Process ^Boot loader loads itself into RAM 4 Boot Location determined by jumpers on the board -Onboard Flash Memory (default) -EPROM -Ext Flash slot ^Boot loader looks for special file names 4 fboot. nb 0: replacement boot loader 4 nk. bin: replacement of operating system 4 Erase. FFX. bsq: erases file system on-board flash *** Does not verify file authenticity! 66
Boot Process ^Boot loader loads itself into RAM 4 Boot Location determined by jumpers on the board -Onboard Flash Memory (default) -EPROM -Ext Flash slot ^Boot loader looks for special file names 4 fboot. nb 0: replacement boot loader 4 nk. bin: replacement of operating system 4 Erase. FFX. bsq: erases file system on-board flash *** Does not verify file authenticity! 66
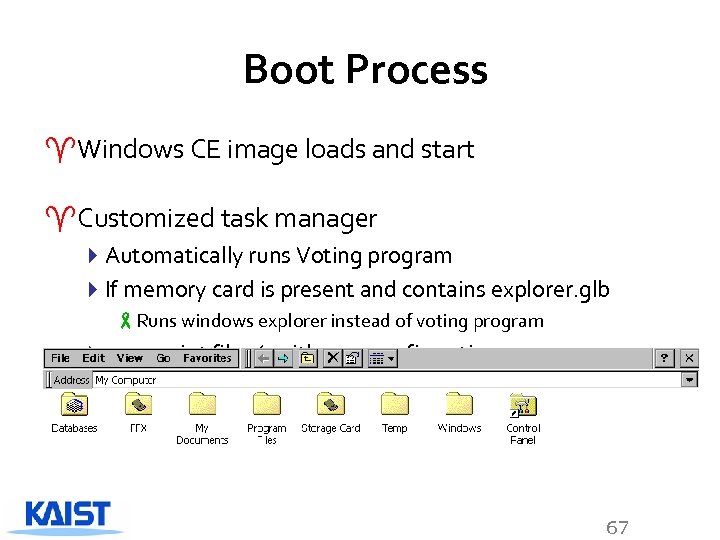 Boot Process ^Windows CE image loads and start ^Customized task manager 4 Automatically runs Voting program 4 If memory card is present and contains explorer. glb -Runs windows explorer instead of voting program 4 runs script files (. with user confirmation 67
Boot Process ^Windows CE image loads and start ^Customized task manager 4 Automatically runs Voting program 4 If memory card is present and contains explorer. glb -Runs windows explorer instead of voting program 4 runs script files (. with user confirmation 67
 Vulnerability Points (H/W) ^Lightweight Lock: easily picked up without a key Easy Access to Memory Card 68
Vulnerability Points (H/W) ^Lightweight Lock: easily picked up without a key Easy Access to Memory Card 68
 Vulnerability Points (H/W) ^EPROM(E): Replace EPROM with malware ^PC Card Slot(S): Used to replace existing software with malware using Memory Card ^Serial Keypad Connector(O): open communication port ^Infrared Port(N): open communication port 69
Vulnerability Points (H/W) ^EPROM(E): Replace EPROM with malware ^PC Card Slot(S): Used to replace existing software with malware using Memory Card ^Serial Keypad Connector(O): open communication port ^Infrared Port(N): open communication port 69
 Vulnerability Points (S/W) ^Authenticity problem -Never checks to validate the authenticity of files on the memory card on booting or updating software ^Buffer Overflow -malformed script files could bypass the confirmation http: //www. cyberdin. com/images/stories/pict 5. jpg 70
Vulnerability Points (S/W) ^Authenticity problem -Never checks to validate the authenticity of files on the memory card on booting or updating software ^Buffer Overflow -malformed script files could bypass the confirmation http: //www. cyberdin. com/images/stories/pict 5. jpg 70
 Attack Types • Stealing Votes • Malicious processes runs in parallel with voting program • Change votes for a favored candidate • Total count of votes does not change • Denial-of-Service • Destroys all records of the election • Makes the voting machine inoperable 71
Attack Types • Stealing Votes • Malicious processes runs in parallel with voting program • Change votes for a favored candidate • Total count of votes does not change • Denial-of-Service • Destroys all records of the election • Makes the voting machine inoperable 71
 Delivery of Malicious Code ^EPROM -Attack code is placed on an EPROM chip -Attacker replaces the EPROM chip and changes the jumper settings to boot from EPROM ^Memory card on PC Card Slot -Attack code is placed on the memory card -Memory card is inserted before voting machine booted -Malicious boot loader containing virus is installed on the machine -The machine is now infected 72
Delivery of Malicious Code ^EPROM -Attack code is placed on an EPROM chip -Attacker replaces the EPROM chip and changes the jumper settings to boot from EPROM ^Memory card on PC Card Slot -Attack code is placed on the memory card -Memory card is inserted before voting machine booted -Malicious boot loader containing virus is installed on the machine -The machine is now infected 72
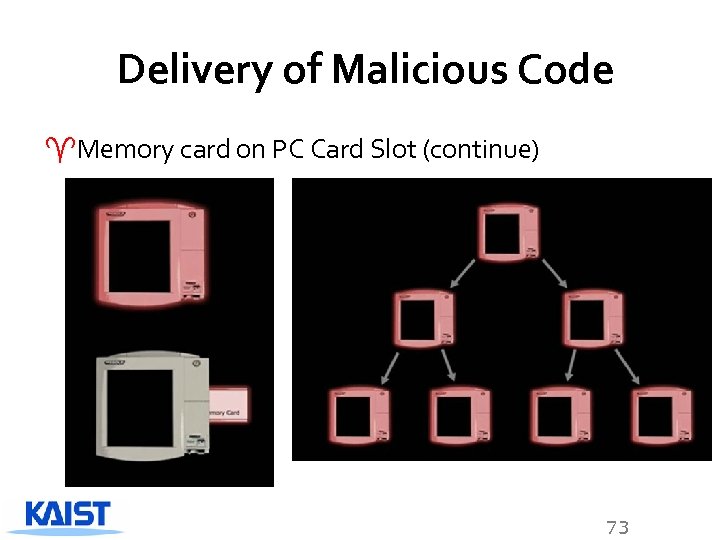 Delivery of Malicious Code ^Memory card on PC Card Slot (continue) 73
Delivery of Malicious Code ^Memory card on PC Card Slot (continue) 73
 Mitigation of Vulnerabilities ^Modifications to DRE Software and Hardware -Digitally sign all software updates -Verify the signature of software updates before installing them -Ask user confirmation of any software updates -Use specialized hardware to maintain tamper-proof logs 4 Physical Access Controls -Sealing the machine and memory card with tamper-evident seals 74
Mitigation of Vulnerabilities ^Modifications to DRE Software and Hardware -Digitally sign all software updates -Verify the signature of software updates before installing them -Ask user confirmation of any software updates -Use specialized hardware to maintain tamper-proof logs 4 Physical Access Controls -Sealing the machine and memory card with tamper-evident seals 74
 Summary ^DREs are like desktop PC, in the security point of view ^Diebold Accu. Vote-TS has many serious vulnerabilities 4 Weak physical security 4 Runs on general-purpose H/W and OS 4 No way to check if an attack occurred 4 Virus attack possible – no need for distributed attack ^DREs have their advantages; however, they should overcome these problems to make reliable votes 75
Summary ^DREs are like desktop PC, in the security point of view ^Diebold Accu. Vote-TS has many serious vulnerabilities 4 Weak physical security 4 Runs on general-purpose H/W and OS 4 No way to check if an attack occurred 4 Virus attack possible – no need for distributed attack ^DREs have their advantages; however, they should overcome these problems to make reliable votes 75
 Bankruptcy of Diebold ^ Papers which criticize DRE, particularly Diebold Systems ^ 2003: Analysis of an Electronic Voting System ^ 2004: Trusted Agent Report Diebold Accu. Vote-TS Voting System ^ 2006: Security Analysis Of The Diebold Accu. Vote - TS Voting Machine ^ Bad Reputation Changed the name multiple times ^ May 19, 2010 Dominion Voting Systems acquired Premier Elections Solutions.
Bankruptcy of Diebold ^ Papers which criticize DRE, particularly Diebold Systems ^ 2003: Analysis of an Electronic Voting System ^ 2004: Trusted Agent Report Diebold Accu. Vote-TS Voting System ^ 2006: Security Analysis Of The Diebold Accu. Vote - TS Voting Machine ^ Bad Reputation Changed the name multiple times ^ May 19, 2010 Dominion Voting Systems acquired Premier Elections Solutions.
 Conclusions ^Voting equipment vendors say closed-source nature of the systems makes them more secure. ^Authors think that an open process would result better. ^The best solution will be a computerized voting system with ballot paper.
Conclusions ^Voting equipment vendors say closed-source nature of the systems makes them more secure. ^Authors think that an open process would result better. ^The best solution will be a computerized voting system with ballot paper.


