7388e6d66d8242d806466161b89e364c.ppt
- Количество слайдов: 25
 EE 122: Layering and the Internet Architecture Kevin Lai September 4, 2002 laik@cs. berkeley. edu
EE 122: Layering and the Internet Architecture Kevin Lai September 4, 2002 laik@cs. berkeley. edu
 Organizing Network Functionality § Many kinds of networking functionality - e. g. , encoding, framing, routing, addressing, reliability, etc. § § § How should they be organized? How should they interact? Layering is one answer to these questions laik@cs. berkeley. edu 2
Organizing Network Functionality § Many kinds of networking functionality - e. g. , encoding, framing, routing, addressing, reliability, etc. § § § How should they be organized? How should they interact? Layering is one answer to these questions laik@cs. berkeley. edu 2
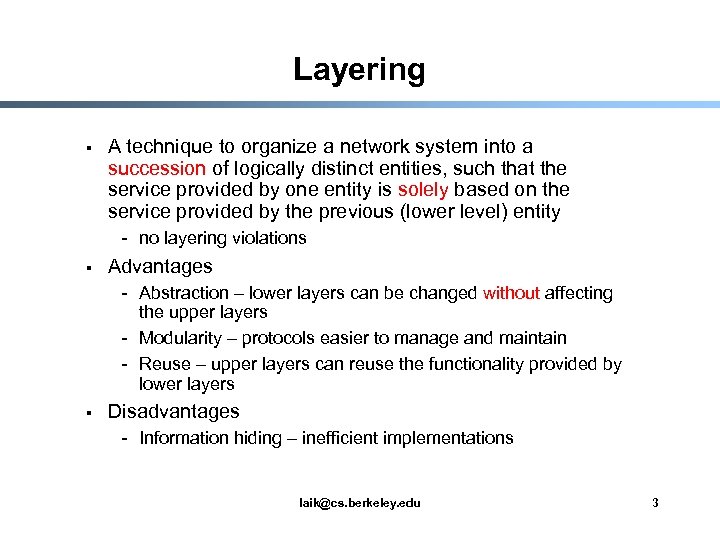 Layering § A technique to organize a network system into a succession of logically distinct entities, such that the service provided by one entity is solely based on the service provided by the previous (lower level) entity - no layering violations § Advantages - Abstraction – lower layers can be changed without affecting the upper layers - Modularity – protocols easier to manage and maintain - Reuse – upper layers can reuse the functionality provided by lower layers § Disadvantages - Information hiding – inefficient implementations laik@cs. berkeley. edu 3
Layering § A technique to organize a network system into a succession of logically distinct entities, such that the service provided by one entity is solely based on the service provided by the previous (lower level) entity - no layering violations § Advantages - Abstraction – lower layers can be changed without affecting the upper layers - Modularity – protocols easier to manage and maintain - Reuse – upper layers can reuse the functionality provided by lower layers § Disadvantages - Information hiding – inefficient implementations laik@cs. berkeley. edu 3
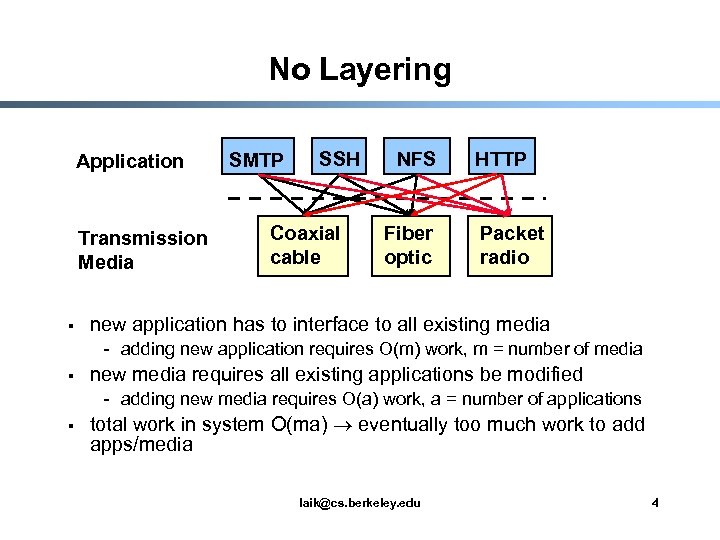 No Layering Application Transmission Media § SMTP SSH Coaxial cable NFS Fiber optic HTTP Packet radio new application has to interface to all existing media - adding new application requires O(m) work, m = number of media § new media requires all existing applications be modified - adding new media requires O(a) work, a = number of applications § total work in system O(ma) eventually too much work to add apps/media laik@cs. berkeley. edu 4
No Layering Application Transmission Media § SMTP SSH Coaxial cable NFS Fiber optic HTTP Packet radio new application has to interface to all existing media - adding new application requires O(m) work, m = number of media § new media requires all existing applications be modified - adding new media requires O(a) work, a = number of applications § total work in system O(ma) eventually too much work to add apps/media laik@cs. berkeley. edu 4
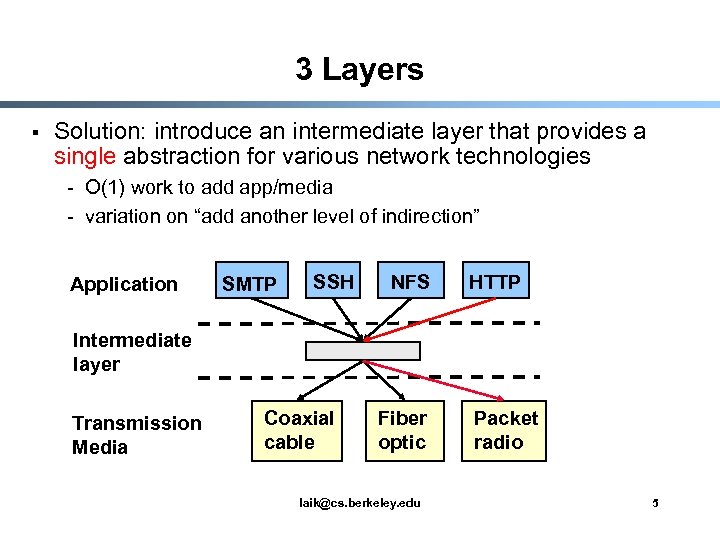 3 Layers § Solution: introduce an intermediate layer that provides a single abstraction for various network technologies - O(1) work to add app/media - variation on “add another level of indirection” Application SMTP SSH NFS HTTP Intermediate layer Transmission Media Coaxial cable Fiber optic laik@cs. berkeley. edu Packet radio 5
3 Layers § Solution: introduce an intermediate layer that provides a single abstraction for various network technologies - O(1) work to add app/media - variation on “add another level of indirection” Application SMTP SSH NFS HTTP Intermediate layer Transmission Media Coaxial cable Fiber optic laik@cs. berkeley. edu Packet radio 5
 ISO OSI Reference Model § § § ISO – International Standard Organization OSI – Open System Interconnection Started to 1978; first standard 1979 - ARPANET started in 1969; TCP/IP protocols ready by 1974 § Goal: a general open standard - allow vendors to enter the market by using their own implementation and protocols laik@cs. berkeley. edu 6
ISO OSI Reference Model § § § ISO – International Standard Organization OSI – Open System Interconnection Started to 1978; first standard 1979 - ARPANET started in 1969; TCP/IP protocols ready by 1974 § Goal: a general open standard - allow vendors to enter the market by using their own implementation and protocols laik@cs. berkeley. edu 6
 ISO OSI Reference Model § Seven layers - Lower three layers are peer-to-peer - Next four layers are end-to-end Application Presentation Session Transport Network Datalink Physical medium laik@cs. berkeley. edu Application Presentation Session Transport Network Datalink Physical 7
ISO OSI Reference Model § Seven layers - Lower three layers are peer-to-peer - Next four layers are end-to-end Application Presentation Session Transport Network Datalink Physical medium laik@cs. berkeley. edu Application Presentation Session Transport Network Datalink Physical 7
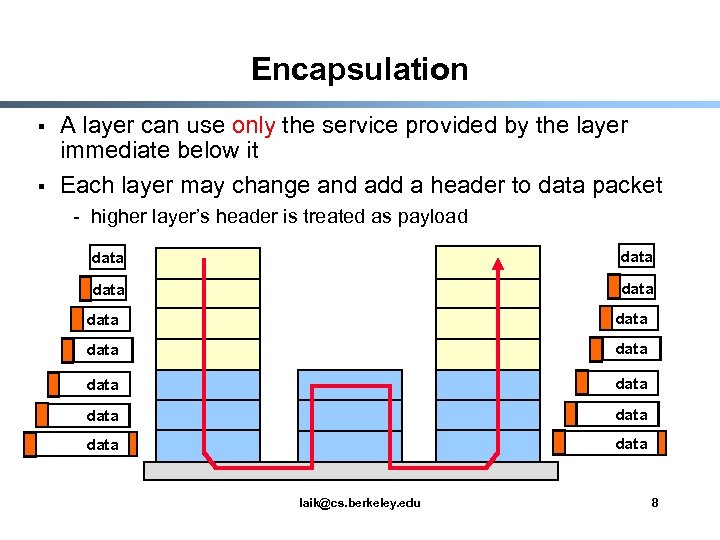 Encapsulation § § A layer can use only the service provided by the layer immediate below it Each layer may change and add a header to data packet - higher layer’s header is treated as payload data data data data laik@cs. berkeley. edu 8
Encapsulation § § A layer can use only the service provided by the layer immediate below it Each layer may change and add a header to data packet - higher layer’s header is treated as payload data data data data laik@cs. berkeley. edu 8
 OSI Model Concepts § § § Service – says what a layer does Interface – says how to access the service Protocol – says how is the service implemented - a set of rules and formats that govern the communication between two peers laik@cs. berkeley. edu 9
OSI Model Concepts § § § Service – says what a layer does Interface – says how to access the service Protocol – says how is the service implemented - a set of rules and formats that govern the communication between two peers laik@cs. berkeley. edu 9
 Physical Layer (1) § § Service: move the information between two systems connected by a physical link Interface: specifies how to send a bit Protocols: coding scheme used to represent a bit, voltage levels, duration of a bit Examples: coaxial cable, optical fiber links; transmitters, receivers laik@cs. berkeley. edu 10
Physical Layer (1) § § Service: move the information between two systems connected by a physical link Interface: specifies how to send a bit Protocols: coding scheme used to represent a bit, voltage levels, duration of a bit Examples: coaxial cable, optical fiber links; transmitters, receivers laik@cs. berkeley. edu 10
 Datalink Layer (2) § Service: - framing, i. e. , attach frame separators - send data frames between peers - others: • arbitrate the access to common physical media • ensure reliable transmission • provide flow control § § Interface: send a data unit (packet) to a machine connected to the same physical media Protocols: layer addresses, implement Medium Access Control (MAC) (e. g. , CSMA/CD)… laik@cs. berkeley. edu 11
Datalink Layer (2) § Service: - framing, i. e. , attach frame separators - send data frames between peers - others: • arbitrate the access to common physical media • ensure reliable transmission • provide flow control § § Interface: send a data unit (packet) to a machine connected to the same physical media Protocols: layer addresses, implement Medium Access Control (MAC) (e. g. , CSMA/CD)… laik@cs. berkeley. edu 11
 Network Layer (3) § Service: - deliver a packet to specified destination - perform segmentation/reassemble - others: • packet scheduling • buffer management § § Interface: send a packet to a specified destination Protocols: define global unique addresses; construct routing tables laik@cs. berkeley. edu 12
Network Layer (3) § Service: - deliver a packet to specified destination - perform segmentation/reassemble - others: • packet scheduling • buffer management § § Interface: send a packet to a specified destination Protocols: define global unique addresses; construct routing tables laik@cs. berkeley. edu 12
 Transport Layer (4) § Services: - provide an error-free and flow-controlled end-to-end connection - multiplex multiple transport connections to one network connection - split one transport connection in multiple network connections § § § Interface: send a packet to specify destination Protocols: implement reliability and flow control Examples: TCP and UDP laik@cs. berkeley. edu 13
Transport Layer (4) § Services: - provide an error-free and flow-controlled end-to-end connection - multiplex multiple transport connections to one network connection - split one transport connection in multiple network connections § § § Interface: send a packet to specify destination Protocols: implement reliability and flow control Examples: TCP and UDP laik@cs. berkeley. edu 13
 Session Layer (5) § Service: - full-duplex - access management, e. g. , token control - synchronization, e. g. , provide check points for long transfers § § Interface: depends on service Protocols: token management; insert checkpoints, implement roll-back functions laik@cs. berkeley. edu 14
Session Layer (5) § Service: - full-duplex - access management, e. g. , token control - synchronization, e. g. , provide check points for long transfers § § Interface: depends on service Protocols: token management; insert checkpoints, implement roll-back functions laik@cs. berkeley. edu 14
 Presentation Layer (6) § § § Service: convert data between various representations Interface: depends on service Protocol: define data formats, and rules to convert from one format to another laik@cs. berkeley. edu 15
Presentation Layer (6) § § § Service: convert data between various representations Interface: depends on service Protocol: define data formats, and rules to convert from one format to another laik@cs. berkeley. edu 15
 Application Layer (7) § § Service: any service provided to the end user Interface: depends on the application Protocol: depends on the application Examples: Kazaa, SMTP, ssh, NFS, WWW browser laik@cs. berkeley. edu 16
Application Layer (7) § § Service: any service provided to the end user Interface: depends on the application Protocol: depends on the application Examples: Kazaa, SMTP, ssh, NFS, WWW browser laik@cs. berkeley. edu 16
 OSI vs. TCP/IP § OSI: conceptually define services, interfaces, protocols - more layers less efficient § Internet: provide a successful implementation - don’t need so many layers in practice Application Presentation Session Transport Network Datalink Physical OSI Application Transport Internet Host-tonetwork SMTP SSH DNS TCP UDP IP LAN Packet radio TCP/IP laik@cs. berkeley. edu 17
OSI vs. TCP/IP § OSI: conceptually define services, interfaces, protocols - more layers less efficient § Internet: provide a successful implementation - don’t need so many layers in practice Application Presentation Session Transport Network Datalink Physical OSI Application Transport Internet Host-tonetwork SMTP SSH DNS TCP UDP IP LAN Packet radio TCP/IP laik@cs. berkeley. edu 17
 Layer Violations and Not § Types of violations - Higher layer interacts with layer below previous layer • e. g. , application has special behavior when running on wireless link • sometimes provides useful performance enhancement - Lower layer interacts with higher layer • e. g. , router (network layer device) routes based on transport or application data in packet • usually a very bad idea (see end-to-end argument) § Not violations - Reducing copying of packets laik@cs. berkeley. edu 18
Layer Violations and Not § Types of violations - Higher layer interacts with layer below previous layer • e. g. , application has special behavior when running on wireless link • sometimes provides useful performance enhancement - Lower layer interacts with higher layer • e. g. , router (network layer device) routes based on transport or application data in packet • usually a very bad idea (see end-to-end argument) § Not violations - Reducing copying of packets laik@cs. berkeley. edu 18
 End-to-End Argument § How do you divide functionality across layers? - One answer: the end-to-end argument - Push as much functionality to higher layers as possible while still maintaining correctness and performance [J. H. Saltzer, D. P. Reed, D. D. Clark, “End-to-End Arguments in System Design”, ACM Transactions on Computer Systems, Vol. 2, No. 4, 1984, pp. 277 -288] laik@cs. berkeley. edu 19
End-to-End Argument § How do you divide functionality across layers? - One answer: the end-to-end argument - Push as much functionality to higher layers as possible while still maintaining correctness and performance [J. H. Saltzer, D. P. Reed, D. D. Clark, “End-to-End Arguments in System Design”, ACM Transactions on Computer Systems, Vol. 2, No. 4, 1984, pp. 277 -288] laik@cs. berkeley. edu 19
 Example: Reliable File Transfer Host A Host B Appl. OS § § § Appl. OK OS Problem: transfer a file composed of blocks Solution 1: transfer each block and retry if necessary, and then concatenate them Solution 2: transfer the blocks, verify the entire file and retry the entire file if necessary laik@cs. berkeley. edu 20
Example: Reliable File Transfer Host A Host B Appl. OS § § § Appl. OK OS Problem: transfer a file composed of blocks Solution 1: transfer each block and retry if necessary, and then concatenate them Solution 2: transfer the blocks, verify the entire file and retry the entire file if necessary laik@cs. berkeley. edu 20
 Discussion § Solution 1 not complete - e. g. , disk fills up after block is verified, but before block is written to disk § § § The receiver has to check the entire file anyway Thus, full functionality can be entirely implemented at application layer; no need for reliability from lower layers However, verifying and retrying the individual blocks improves performance - e. g. , high probability of lost block retrying the entire file on error is very inefficient § End-to-end argument says implement reliability in both layers in this case laik@cs. berkeley. edu 21
Discussion § Solution 1 not complete - e. g. , disk fills up after block is verified, but before block is written to disk § § § The receiver has to check the entire file anyway Thus, full functionality can be entirely implemented at application layer; no need for reliability from lower layers However, verifying and retrying the individual blocks improves performance - e. g. , high probability of lost block retrying the entire file on error is very inefficient § End-to-end argument says implement reliability in both layers in this case laik@cs. berkeley. edu 21
 Intuitive Justification § § § Application has more information about the data and the semantics of the service it requires (e. g. , level of reliability) A lower layer has more information about constraints in data transmission (e. g. , packet size, error rate) implementing a functionality at a lower level should have minimum performance impact on applications that do not use the functionality - otherwise, network service model becomes cluttered with demands of unpopular applications - do add functionality to lower layers that improves the performance of many applications laik@cs. berkeley. edu 22
Intuitive Justification § § § Application has more information about the data and the semantics of the service it requires (e. g. , level of reliability) A lower layer has more information about constraints in data transmission (e. g. , packet size, error rate) implementing a functionality at a lower level should have minimum performance impact on applications that do not use the functionality - otherwise, network service model becomes cluttered with demands of unpopular applications - do add functionality to lower layers that improves the performance of many applications laik@cs. berkeley. edu 22
 Internet Embodies End-to-End Argument § § Network layer provides simple service model: best effort datagram (packet) delivery Only one higher level service implemented at transport layer: reliable, in order data delivery (TCP) - performance enhancement; used by a large variety of applications (Gnutella, ssh, SMTP, HTTP) - does not impact other applications (can use UDP) § Everything else implemented at application level laik@cs. berkeley. edu 23
Internet Embodies End-to-End Argument § § Network layer provides simple service model: best effort datagram (packet) delivery Only one higher level service implemented at transport layer: reliable, in order data delivery (TCP) - performance enhancement; used by a large variety of applications (Gnutella, ssh, SMTP, HTTP) - does not impact other applications (can use UDP) § Everything else implemented at application level laik@cs. berkeley. edu 23
 Properties § Advantages - Service model can be implemented by a large variety of network technologies - No per flow state in network • Robust to failure • Scalable to large numbers of flows, nodes § Disadvantages - no differentiation of quality of service • vulnerable to selfish users • vulnerable to malicious users - only unicast routing • no multicast, anycast laik@cs. berkeley. edu 24
Properties § Advantages - Service model can be implemented by a large variety of network technologies - No per flow state in network • Robust to failure • Scalable to large numbers of flows, nodes § Disadvantages - no differentiation of quality of service • vulnerable to selfish users • vulnerable to malicious users - only unicast routing • no multicast, anycast laik@cs. berkeley. edu 24
 Summary § Layering is way to organize communication functionality; provides - Abstraction - Modularity - Reuse § End-to-end argument - Push as much functionality to higher layers as possible while still maintaining correctness and performance § Internet embodies end-to-end argument laik@cs. berkeley. edu 25
Summary § Layering is way to organize communication functionality; provides - Abstraction - Modularity - Reuse § End-to-end argument - Push as much functionality to higher layers as possible while still maintaining correctness and performance § Internet embodies end-to-end argument laik@cs. berkeley. edu 25


