abbcab1c7a03e47995f0f2763f5f031b.ppt
- Количество слайдов: 35
 Educational Solutions National INFOSEC Education and Training Program for a Safer World http//www. nsa. gov: 8080/isso/programs/nietp/index. htm
Educational Solutions National INFOSEC Education and Training Program for a Safer World http//www. nsa. gov: 8080/isso/programs/nietp/index. htm
 Introduction to Information Assurance (IA) 07 July 1999
Introduction to Information Assurance (IA) 07 July 1999
 The Course Objective is · To introduce the student to Information Assurance, · Present the macro problem facing the global information network infrastructure and, · Define Information Assurance and what is being done to protect infrastructures.
The Course Objective is · To introduce the student to Information Assurance, · Present the macro problem facing the global information network infrastructure and, · Define Information Assurance and what is being done to protect infrastructures.
 What is Information Assurance and. . . why should I care?
What is Information Assurance and. . . why should I care?
 Information Assurance is. . . l Information Operations (IO) that protect and defend information and information systems by ensuring their confidentiality, Ü authentication, Ü integrity, Ü availability, and Ü non-repudiation. Ü l This includes providing for restoration of information systems by incorporating protection, Ü detection, and Ü reaction capabilities. Ü (Definition from National Information Systems Security (INFOSEC) Glossary, NSTISSI No. 4009, Aug 1997)
Information Assurance is. . . l Information Operations (IO) that protect and defend information and information systems by ensuring their confidentiality, Ü authentication, Ü integrity, Ü availability, and Ü non-repudiation. Ü l This includes providing for restoration of information systems by incorporating protection, Ü detection, and Ü reaction capabilities. Ü (Definition from National Information Systems Security (INFOSEC) Glossary, NSTISSI No. 4009, Aug 1997)
 National Infrastructures At Risk u Landscape is changing u PCCIP/PDD 63 In the cyber era, our traditional lines of defense no longer provide a wall between citizens and those who would do harm.
National Infrastructures At Risk u Landscape is changing u PCCIP/PDD 63 In the cyber era, our traditional lines of defense no longer provide a wall between citizens and those who would do harm.
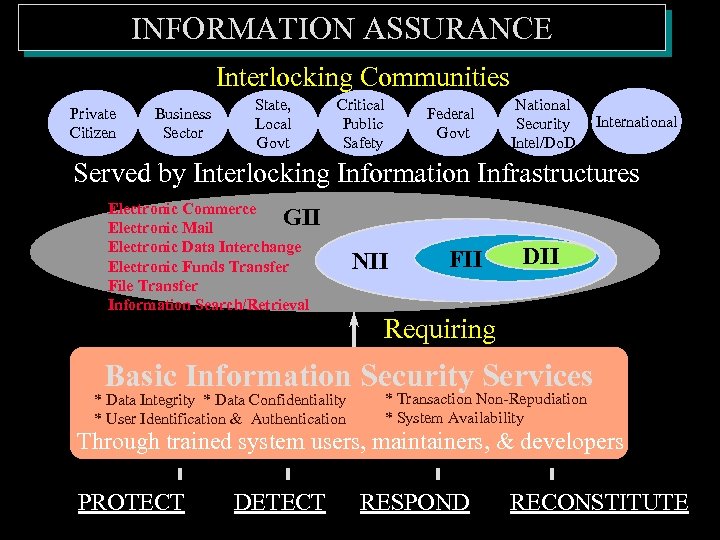 INFORMATION ASSURANCE Interlocking Communities Private Citizen Business Sector State, Local Govt Critical Public Safety Federal Govt National Security Intel/Do. D International Served by Interlocking Information Infrastructures Electronic Commerce GII Electronic Mail Electronic Data Interchange Electronic Funds Transfer File Transfer Information Search/Retrieval NII FII DII Requiring Basic Information Security Services * Data Integrity * Data Confidentiality * User Identification & Authentication * Transaction Non-Repudiation * System Availability Through trained system users, maintainers, & developers PROTECT DETECT Validated Certificates RESPOND Assured. RECONSTITUTE Services
INFORMATION ASSURANCE Interlocking Communities Private Citizen Business Sector State, Local Govt Critical Public Safety Federal Govt National Security Intel/Do. D International Served by Interlocking Information Infrastructures Electronic Commerce GII Electronic Mail Electronic Data Interchange Electronic Funds Transfer File Transfer Information Search/Retrieval NII FII DII Requiring Basic Information Security Services * Data Integrity * Data Confidentiality * User Identification & Authentication * Transaction Non-Repudiation * System Availability Through trained system users, maintainers, & developers PROTECT DETECT Validated Certificates RESPOND Assured. RECONSTITUTE Services
 You Are Here! The number of internet users will quadruple from 36. 0 million in 1997 to 142. 0 million by the year 2002: Avg. annual growth rate = 53%
You Are Here! The number of internet users will quadruple from 36. 0 million in 1997 to 142. 0 million by the year 2002: Avg. annual growth rate = 53%
 HISTORY Evolution of Information Assurance In the 20 th Century
HISTORY Evolution of Information Assurance In the 20 th Century
 In the Beginning. . . There was COMSEC (Communications Security ) “Measurement and controls taken to deny unauthorized persons information derived from telecommunications and to ensure the authenticity of such telecommunications. COMSEC includes: cryptosecurity, transmission security, emissions security, & physical security of COMSEC material. ”
In the Beginning. . . There was COMSEC (Communications Security ) “Measurement and controls taken to deny unauthorized persons information derived from telecommunications and to ensure the authenticity of such telecommunications. COMSEC includes: cryptosecurity, transmission security, emissions security, & physical security of COMSEC material. ”
 Confidentiality Assurance that information is not disclosed to unauthorized persons, processes, or devices. * l l In condensed form. . . Protection from unauthorized disclosure or No one but you and the sender knows *(Definition from National Information Systems Security (INFOSEC) Glossary, NSTISSI No. 4009, Aug 1997)
Confidentiality Assurance that information is not disclosed to unauthorized persons, processes, or devices. * l l In condensed form. . . Protection from unauthorized disclosure or No one but you and the sender knows *(Definition from National Information Systems Security (INFOSEC) Glossary, NSTISSI No. 4009, Aug 1997)
 Authentication Security measure designed to establish the validity of a transmission, message, or originator, or a means of verifying an individual’s authorization to receive specific categories of information. * l l In condensed form. . . Verification of originator or Knowing for sure who sent the message *(Definition from National Information Systems Security (INFOSEC) Glossary, NSTISSI No. 4009, Aug 1997)
Authentication Security measure designed to establish the validity of a transmission, message, or originator, or a means of verifying an individual’s authorization to receive specific categories of information. * l l In condensed form. . . Verification of originator or Knowing for sure who sent the message *(Definition from National Information Systems Security (INFOSEC) Glossary, NSTISSI No. 4009, Aug 1997)
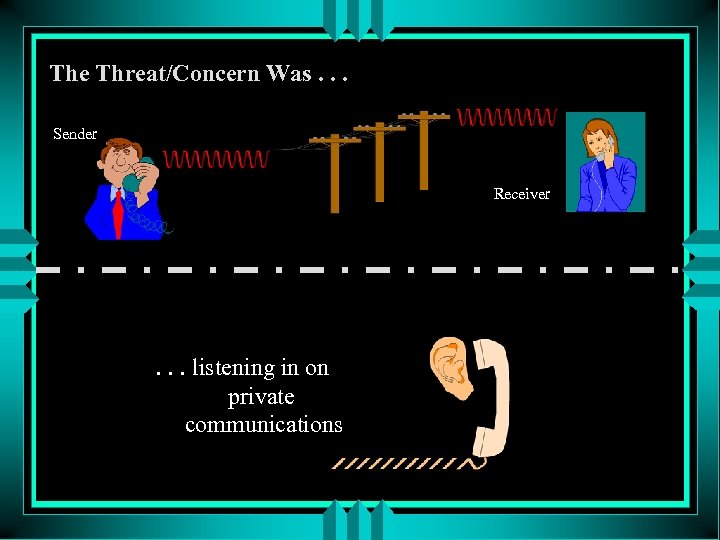 The Threat/Concern Was. . . Sender Receiver . . . listening in on private communications
The Threat/Concern Was. . . Sender Receiver . . . listening in on private communications
 Then there was. . . COMPUSEC (80/90’s) “ Measures and controls that ensure confidentiality, integrity, and availability of information system assets including hardware, software, firmware, and information being processed, stored, and communicated. ” (Computer Security)
Then there was. . . COMPUSEC (80/90’s) “ Measures and controls that ensure confidentiality, integrity, and availability of information system assets including hardware, software, firmware, and information being processed, stored, and communicated. ” (Computer Security)
 Integrity Quality of an Information System (IS) reflecting the local correctness and reliability of the operating system; the logical completeness of the hardware and software implementing the protection mechanisms; and the consistency of the data structures and occurrence of the stored data. * l l In condensed form. . . Protection from unauthorized change or Person hearing/receiving exactly what you said/sent *(Definition from National Information Systems Security (INFOSEC) Glossary, NSTISSI No. 4009, Aug 1997)
Integrity Quality of an Information System (IS) reflecting the local correctness and reliability of the operating system; the logical completeness of the hardware and software implementing the protection mechanisms; and the consistency of the data structures and occurrence of the stored data. * l l In condensed form. . . Protection from unauthorized change or Person hearing/receiving exactly what you said/sent *(Definition from National Information Systems Security (INFOSEC) Glossary, NSTISSI No. 4009, Aug 1997)
 Availability l Timely, reliable access to data and information services for authorized users. * l In condensed form. . . Assured access by authorized users or Having a dial tone when you want one *(Definition from National Information Systems Security (INFOSEC) Glossary, NSTISSI No. 4009, Aug 1997)
Availability l Timely, reliable access to data and information services for authorized users. * l In condensed form. . . Assured access by authorized users or Having a dial tone when you want one *(Definition from National Information Systems Security (INFOSEC) Glossary, NSTISSI No. 4009, Aug 1997)
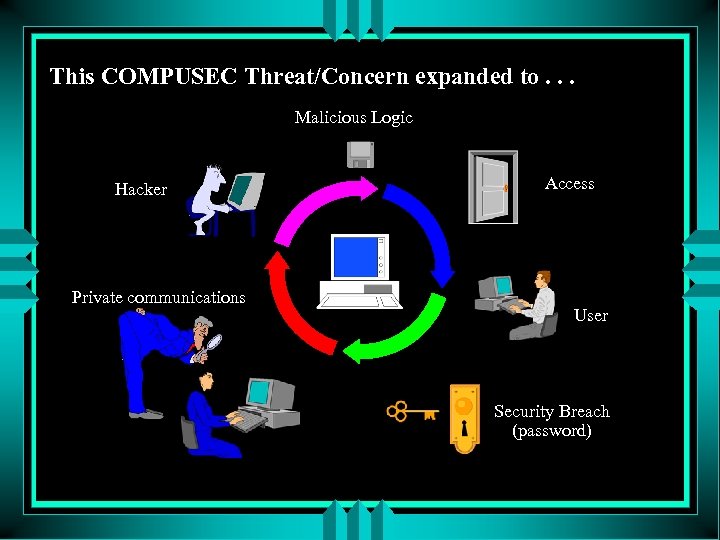 This COMPUSEC Threat/Concern expanded to. . . Malicious Logic Hacker Private communications Access User Security Breach (password)
This COMPUSEC Threat/Concern expanded to. . . Malicious Logic Hacker Private communications Access User Security Breach (password)
 The Concern later increased to include both. . . • COMSEC. . . and. . . • COMPUSEC
The Concern later increased to include both. . . • COMSEC. . . and. . . • COMPUSEC
 This COMSEC/COMPUSEC merger formed. . . INFOSEC (Information Systems Security) (90’s) “Protection of information systems against unauthorized access to or modification of information, whether in storage, processing, or transit, and against the denial of services to authorized users, including those measures necessary to detect, document, and counter such threats. ”
This COMSEC/COMPUSEC merger formed. . . INFOSEC (Information Systems Security) (90’s) “Protection of information systems against unauthorized access to or modification of information, whether in storage, processing, or transit, and against the denial of services to authorized users, including those measures necessary to detect, document, and counter such threats. ”
 Non-Repudiation l Assurance the sender of data is provided with proof of delivery and the recipient is provided with proof of the sender’s identity, so neither can later deny having processed the data. * l In condensed form. . . Undeniable proof of participation or Like receipt-requested mail - each knows the other got it *(Definition from National Information Systems Security (INFOSEC) Glossary, NSTISSI No. 4009, Aug 1997)
Non-Repudiation l Assurance the sender of data is provided with proof of delivery and the recipient is provided with proof of the sender’s identity, so neither can later deny having processed the data. * l In condensed form. . . Undeniable proof of participation or Like receipt-requested mail - each knows the other got it *(Definition from National Information Systems Security (INFOSEC) Glossary, NSTISSI No. 4009, Aug 1997)
 Today. . . we speak “Information Assurance” (Now/Future) “Information Operations that protect and defend information and information systems by ensuring their confidentiality, authentication, integrity, availability, and non-repudiation. This includes providing for restoration of information systems by incorporating protection, detection and reaction capabilities. ”
Today. . . we speak “Information Assurance” (Now/Future) “Information Operations that protect and defend information and information systems by ensuring their confidentiality, authentication, integrity, availability, and non-repudiation. This includes providing for restoration of information systems by incorporating protection, detection and reaction capabilities. ”
 The Concern NOW is. . . Protect, Defend. . . Authentication Integrity Confidentiality Availability Non-Repudiation. . . & Restoration of Info
The Concern NOW is. . . Protect, Defend. . . Authentication Integrity Confidentiality Availability Non-Repudiation. . . & Restoration of Info
 New Direction New Challenges Information Assurance (IA) Leadership for the Nation Provide - - solutions, products and services, and conduct defensive information operations, to achieve - - IA for U. S. Critical Information Infrastructures operating in a global network environment
New Direction New Challenges Information Assurance (IA) Leadership for the Nation Provide - - solutions, products and services, and conduct defensive information operations, to achieve - - IA for U. S. Critical Information Infrastructures operating in a global network environment
 Get Engaged. . . Move from INFOSEC. . . to. . . Information Assurance Protect Detect IA Restore React
Get Engaged. . . Move from INFOSEC. . . to. . . Information Assurance Protect Detect IA Restore React
 Why is Information Assurance important?
Why is Information Assurance important?
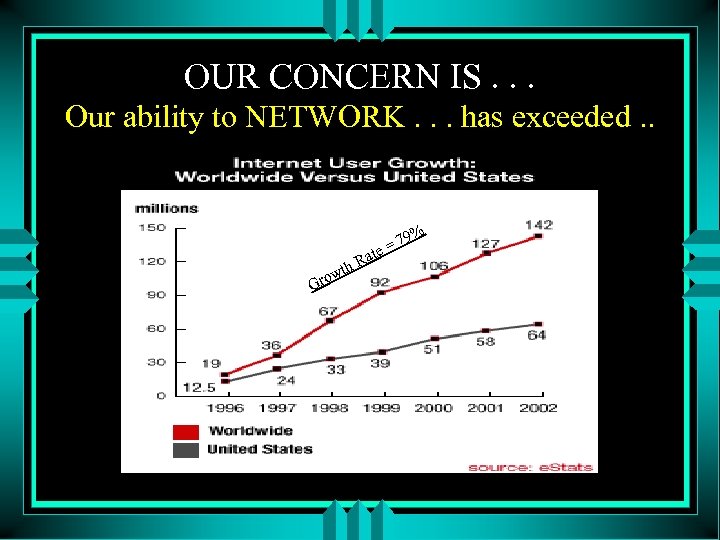 OUR CONCERN IS. . . Our ability to NETWORK. . . has exceeded. . te Gro w a th R 79% =
OUR CONCERN IS. . . Our ability to NETWORK. . . has exceeded. . te Gro w a th R 79% =
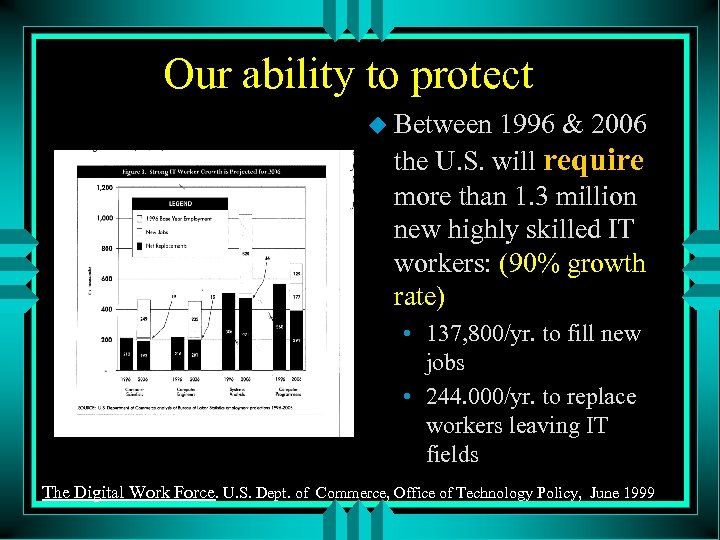 Our ability to protect u Between 1996 & 2006 the U. S. will require more than 1. 3 million new highly skilled IT workers: (90% growth rate) • 137, 800/yr. to fill new jobs • 244. 000/yr. to replace workers leaving IT fields The Digital Work Force. U. S. Dept. of Commerce, Office of Technology Policy, June 1999
Our ability to protect u Between 1996 & 2006 the U. S. will require more than 1. 3 million new highly skilled IT workers: (90% growth rate) • 137, 800/yr. to fill new jobs • 244. 000/yr. to replace workers leaving IT fields The Digital Work Force. U. S. Dept. of Commerce, Office of Technology Policy, June 1999
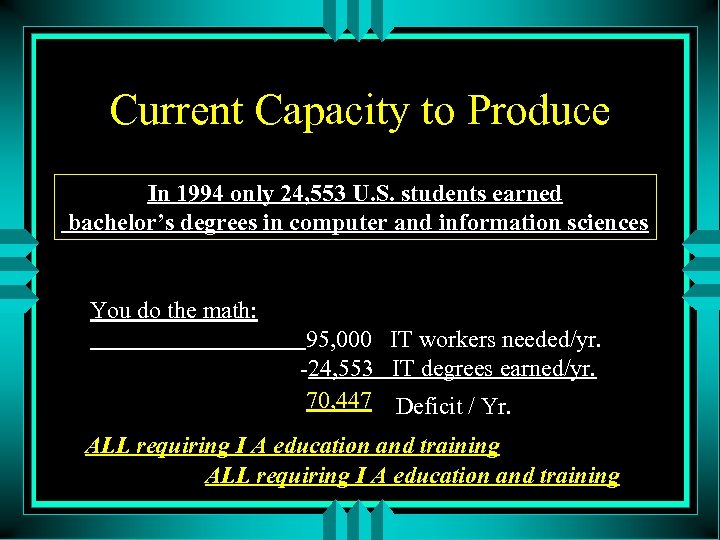 Current Capacity to Produce In 1994 only 24, 553 U. S. students earned bachelor’s degrees in computer and information sciences You do the math: 95, 000 IT workers needed/yr. -24, 553 IT degrees earned/yr. 70, 447 Deficit / Yr. ALL requiring I A education and training
Current Capacity to Produce In 1994 only 24, 553 U. S. students earned bachelor’s degrees in computer and information sciences You do the math: 95, 000 IT workers needed/yr. -24, 553 IT degrees earned/yr. 70, 447 Deficit / Yr. ALL requiring I A education and training
 President’s Commission (October 1997) l President’s Commission on Critical Information Infrastructure Protection (PCCIIP) l http: //www. pccip. gov/ National Goal l Achieve & maintain ability to protect critical infrastructure. . .
President’s Commission (October 1997) l President’s Commission on Critical Information Infrastructure Protection (PCCIIP) l http: //www. pccip. gov/ National Goal l Achieve & maintain ability to protect critical infrastructure. . .
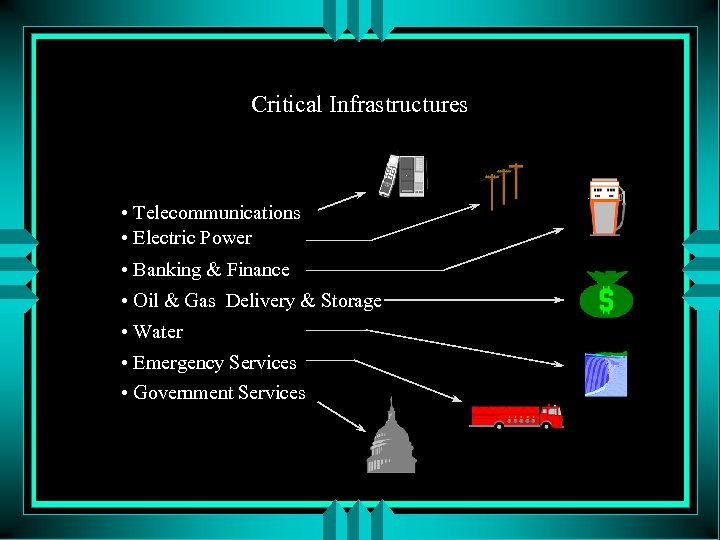 Critical Infrastructures • Telecommunications • Electric Power • Banking & Finance • Oil & Gas Delivery & Storage • Water • Emergency Services • Government Services
Critical Infrastructures • Telecommunications • Electric Power • Banking & Finance • Oil & Gas Delivery & Storage • Water • Emergency Services • Government Services
 What’s being done? Presidential Decision Directive 63 (1998) “It has long been the Policy of the United States to assure the continuity and viability of critical infrastructures. I intend that the United States will take all necessary measures to swiftly eliminate any significant vulnerability to both physical and cyber attacks on our critical infrastructures, including especially our cyber systems. ” www. ciao. gov
What’s being done? Presidential Decision Directive 63 (1998) “It has long been the Policy of the United States to assure the continuity and viability of critical infrastructures. I intend that the United States will take all necessary measures to swiftly eliminate any significant vulnerability to both physical and cyber attacks on our critical infrastructures, including especially our cyber systems. ” www. ciao. gov
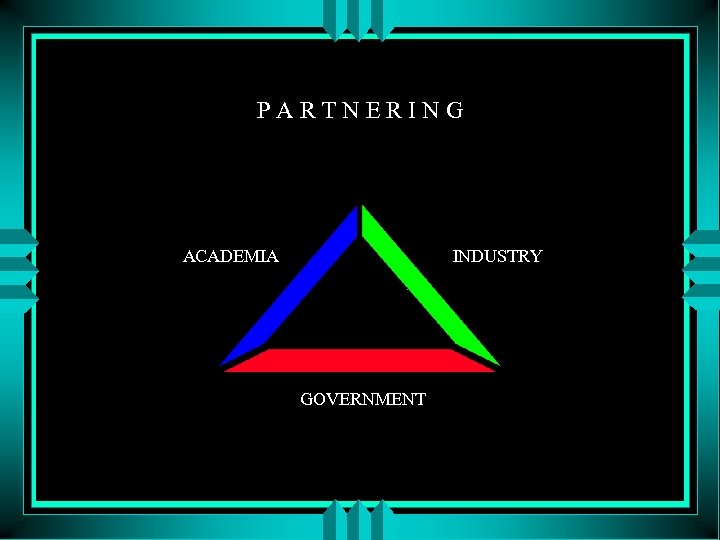 PARTNERING ACADEMIA INDUSTRY GOVERNMENT
PARTNERING ACADEMIA INDUSTRY GOVERNMENT
 Partners - Provide IA through Cyber Defense by moving from the. . . l Protect mode of securing l l Servers l l Networks Workstations, . . . to the. . . Detect & Report modes l l Data fusion & analysis l l Improve attack sensing & warning Determine source, intent, impact, then report it, and. . . finally to the. . . Respond mode l Restore - damage, recover, and verify operations l Pursue - contact appropriate legal authorities
Partners - Provide IA through Cyber Defense by moving from the. . . l Protect mode of securing l l Servers l l Networks Workstations, . . . to the. . . Detect & Report modes l l Data fusion & analysis l l Improve attack sensing & warning Determine source, intent, impact, then report it, and. . . finally to the. . . Respond mode l Restore - damage, recover, and verify operations l Pursue - contact appropriate legal authorities
 The Bottom Line Be aware of the complexity of and the threats to business and government infrastructures and understand the security procedures designed to protect networks from information attacks
The Bottom Line Be aware of the complexity of and the threats to business and government infrastructures and understand the security procedures designed to protect networks from information attacks
 For more information on IA. . . l PDD-63 and the Presidential Commission Report on Critical Infrastructure Protection: http: //www. pccip. gov/info. html l Defense Information Systems Agency (DISA) Awareness and Training Facility: http: //www. disa. mil/cissitf. html l National Security Telecommunications and Information Systems Security Training Standards: http: //www. . nstissc. gov l National INFOSEC Education Colloquium: http: //www. infosec. jmu. edu/ncisse l National Institute for Standards and Technology (NIST) Computer Security Clearing House: http: //csrc. nist. gov/welcome. html l National Security Agency INFOSEC Page - National INFOSEC Education and Training Program: http: //www. nsa. gov: 8080/isso/programs/nietp/index. htm
For more information on IA. . . l PDD-63 and the Presidential Commission Report on Critical Infrastructure Protection: http: //www. pccip. gov/info. html l Defense Information Systems Agency (DISA) Awareness and Training Facility: http: //www. disa. mil/cissitf. html l National Security Telecommunications and Information Systems Security Training Standards: http: //www. . nstissc. gov l National INFOSEC Education Colloquium: http: //www. infosec. jmu. edu/ncisse l National Institute for Standards and Technology (NIST) Computer Security Clearing House: http: //csrc. nist. gov/welcome. html l National Security Agency INFOSEC Page - National INFOSEC Education and Training Program: http: //www. nsa. gov: 8080/isso/programs/nietp/index. htm


