b3c67ca342b2e9ea008db05850fe10a1.ppt
- Количество слайдов: 23
 ECE-6612 http: //www. ece. gatech. edu/~copeland/jac/6612/ Prof. John A. Copeland john. copeland@ece. gatech. edu 404 894 -5177 fax 404 894 -0035 Office: Centergy 5138 (VL W 315 MWF a. m. ) email or call for office visit, or call Kathy Cheek, 404 894 -5696 Chapter 5 a - Pretty Good Privacy (PGP) Email
ECE-6612 http: //www. ece. gatech. edu/~copeland/jac/6612/ Prof. John A. Copeland john. copeland@ece. gatech. edu 404 894 -5177 fax 404 894 -0035 Office: Centergy 5138 (VL W 315 MWF a. m. ) email or call for office visit, or call Kathy Cheek, 404 894 -5696 Chapter 5 a - Pretty Good Privacy (PGP) Email
 Electronic Mail In 1982, ARPANET email proposals were published as RFC 821 (www. ietf. org/rfc 0821. txt) and RFC 822 • Email services since are based on these RFC's (+ many later) • CCITT X. 400 & ISO MOTIS grew and waned as competitors • "User Agents" UA, and "Message Transfer Agents" MTA Three parts to an email message: • Envelope - information used to forward the contents • Header - standard strings, some added in route. > To: Cc: Bcc: From: Sender: > Received: (added in route), Return-Path: (by final MTA) > MIME headers added by RFC 1341 and 1521 > A. S. Tanenbaum, "Computer Networks, " (3 rd ed. ) p. 651 2
Electronic Mail In 1982, ARPANET email proposals were published as RFC 821 (www. ietf. org/rfc 0821. txt) and RFC 822 • Email services since are based on these RFC's (+ many later) • CCITT X. 400 & ISO MOTIS grew and waned as competitors • "User Agents" UA, and "Message Transfer Agents" MTA Three parts to an email message: • Envelope - information used to forward the contents • Header - standard strings, some added in route. > To: Cc: Bcc: From: Sender: > Received: (added in route), Return-Path: (by final MTA) > MIME headers added by RFC 1341 and 1521 > A. S. Tanenbaum, "Computer Networks, " (3 rd ed. ) p. 651 2
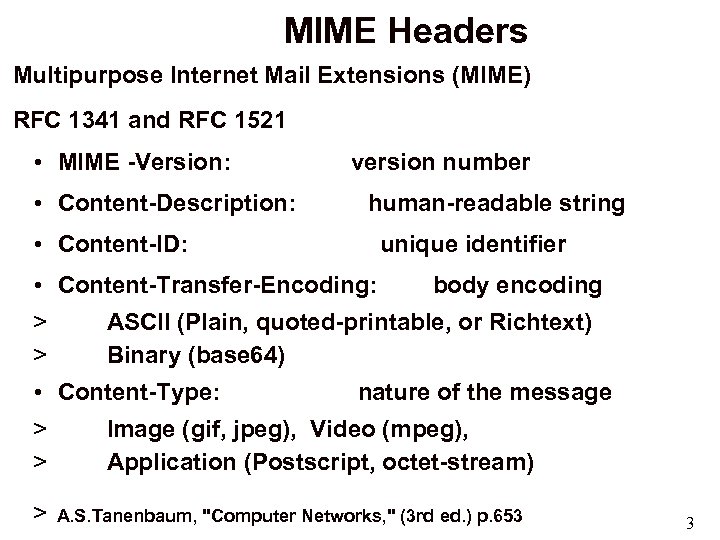 MIME Headers Multipurpose Internet Mail Extensions (MIME) RFC 1341 and RFC 1521 • MIME -Version: • Content-Description: version number human-readable string • Content-ID: unique identifier • Content-Transfer-Encoding: > > ASCII (Plain, quoted-printable, or Richtext) Binary (base 64) • Content-Type: > > > body encoding nature of the message Image (gif, jpeg), Video (mpeg), Application (Postscript, octet-stream) A. S. Tanenbaum, "Computer Networks, " (3 rd ed. ) p. 653 3
MIME Headers Multipurpose Internet Mail Extensions (MIME) RFC 1341 and RFC 1521 • MIME -Version: • Content-Description: version number human-readable string • Content-ID: unique identifier • Content-Transfer-Encoding: > > ASCII (Plain, quoted-printable, or Richtext) Binary (base 64) • Content-Type: > > > body encoding nature of the message Image (gif, jpeg), Video (mpeg), Application (Postscript, octet-stream) A. S. Tanenbaum, "Computer Networks, " (3 rd ed. ) p. 653 3
![Received: from didier. ee. gatech. edu (didier. ee. gatech. edu [130. 207. 230. 10]) Received: from didier. ee. gatech. edu (didier. ee. gatech. edu [130. 207. 230. 10])](https://present5.com/presentation/b3c67ca342b2e9ea008db05850fe10a1/image-4.jpg) Received: from didier. ee. gatech. edu (didier. ee. gatech. edu [130. 207. 230. 10]) by eagle. gcatt. gatech. edu (8. 8. 8+Sun/8. 7. 1) with ESMTP id UAA 00818 for
Received: from didier. ee. gatech. edu (didier. ee. gatech. edu [130. 207. 230. 10]) by eagle. gcatt. gatech. edu (8. 8. 8+Sun/8. 7. 1) with ESMTP id UAA 00818 for
 $ nslookup -q=MX ee. gatech. edu (nslookup -> host) ee. gatech. edu preference = 10, mail exchanger = mail. ee. gatech. edu nameserver = eeserv. ee. gatech. edu nameserver = duchess. ee. gatech. edu nameserver = didier. ee. gatech. edu mail. ee. gatech. edu eeserv. ee. gatech. edu internet address = 130. 207. 230. 10 internet address = 130. 207. 230. 5 duchess. ee. gatech. edu internet address = 130. 207. 230. 13 didier. ee. gatech. edu internet address = 130. 207. 230. 10 5
$ nslookup -q=MX ee. gatech. edu (nslookup -> host) ee. gatech. edu preference = 10, mail exchanger = mail. ee. gatech. edu nameserver = eeserv. ee. gatech. edu nameserver = duchess. ee. gatech. edu nameserver = didier. ee. gatech. edu mail. ee. gatech. edu eeserv. ee. gatech. edu internet address = 130. 207. 230. 10 internet address = 130. 207. 230. 5 duchess. ee. gatech. edu internet address = 130. 207. 230. 13 didier. ee. gatech. edu internet address = 130. 207. 230. 10 5
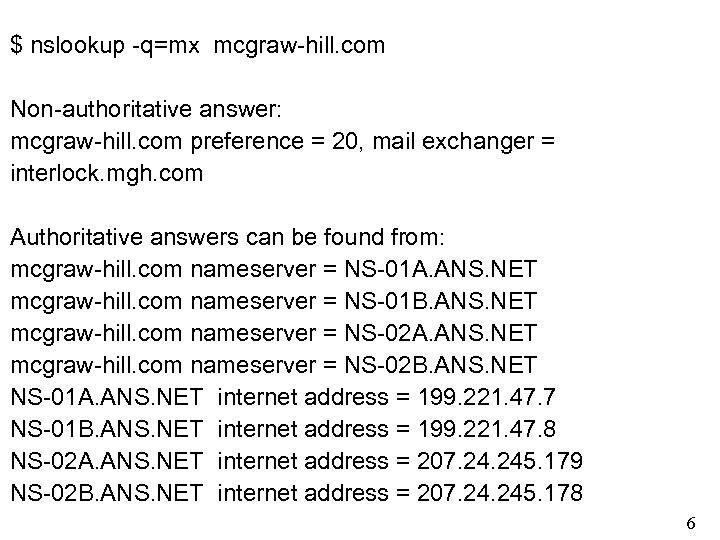 $ nslookup -q=mx mcgraw-hill. com Non-authoritative answer: mcgraw-hill. com preference = 20, mail exchanger = interlock. mgh. com Authoritative answers can be found from: mcgraw-hill. com nameserver = NS-01 A. ANS. NET mcgraw-hill. com nameserver = NS-01 B. ANS. NET mcgraw-hill. com nameserver = NS-02 A. ANS. NET mcgraw-hill. com nameserver = NS-02 B. ANS. NET NS-01 A. ANS. NET internet address = 199. 221. 47. 7 NS-01 B. ANS. NET internet address = 199. 221. 47. 8 NS-02 A. ANS. NET internet address = 207. 245. 179 NS-02 B. ANS. NET internet address = 207. 245. 178 6
$ nslookup -q=mx mcgraw-hill. com Non-authoritative answer: mcgraw-hill. com preference = 20, mail exchanger = interlock. mgh. com Authoritative answers can be found from: mcgraw-hill. com nameserver = NS-01 A. ANS. NET mcgraw-hill. com nameserver = NS-01 B. ANS. NET mcgraw-hill. com nameserver = NS-02 A. ANS. NET mcgraw-hill. com nameserver = NS-02 B. ANS. NET NS-01 A. ANS. NET internet address = 199. 221. 47. 7 NS-01 B. ANS. NET internet address = 199. 221. 47. 8 NS-02 A. ANS. NET internet address = 207. 245. 179 NS-02 B. ANS. NET internet address = 207. 245. 178 6
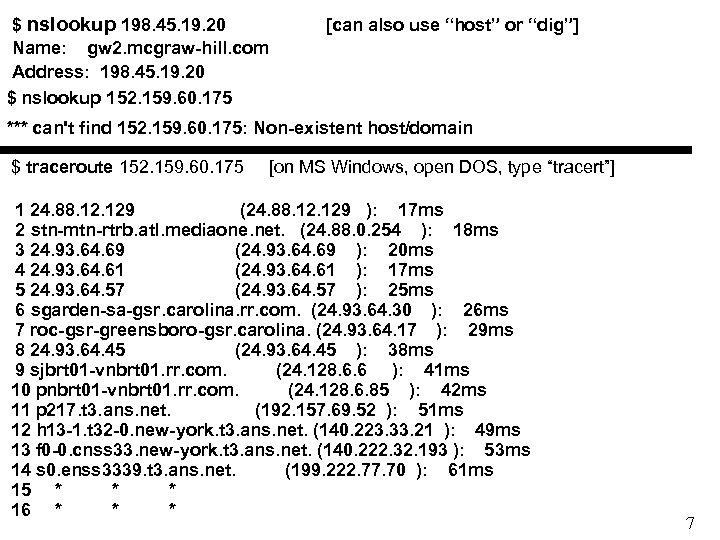 $ nslookup 198. 45. 19. 20 Name: gw 2. mcgraw-hill. com Address: 198. 45. 19. 20 $ nslookup 152. 159. 60. 175 [can also use “host” or “dig”] *** can't find 152. 159. 60. 175: Non-existent host/domain $ traceroute 152. 159. 60. 175 [on MS Windows, open DOS, type “tracert”] 1 24. 88. 129 (24. 88. 129 ): 17 ms 2 stn-mtn-rtrb. atl. mediaone. net. (24. 88. 0. 254 ): 18 ms 3 24. 93. 64. 69 (24. 93. 64. 69 ): 20 ms 4 24. 93. 64. 61 (24. 93. 64. 61 ): 17 ms 5 24. 93. 64. 57 (24. 93. 64. 57 ): 25 ms 6 sgarden-sa-gsr. carolina. rr. com. (24. 93. 64. 30 ): 26 ms 7 roc-gsr-greensboro-gsr. carolina. (24. 93. 64. 17 ): 29 ms 8 24. 93. 64. 45 (24. 93. 64. 45 ): 38 ms 9 sjbrt 01 -vnbrt 01. rr. com. (24. 128. 6. 6 ): 41 ms 10 pnbrt 01 -vnbrt 01. rr. com. (24. 128. 6. 85 ): 42 ms 11 p 217. t 3. ans. net. (192. 157. 69. 52 ): 51 ms 12 h 13 -1. t 32 -0. new-york. t 3. ans. net. (140. 223. 33. 21 ): 49 ms 13 f 0 -0. cnss 33. new-york. t 3. ans. net. (140. 222. 32. 193 ): 53 ms 14 s 0. enss 3339. t 3. ans. net. (199. 222. 77. 70 ): 61 ms 15 * * * 16 * * * 7
$ nslookup 198. 45. 19. 20 Name: gw 2. mcgraw-hill. com Address: 198. 45. 19. 20 $ nslookup 152. 159. 60. 175 [can also use “host” or “dig”] *** can't find 152. 159. 60. 175: Non-existent host/domain $ traceroute 152. 159. 60. 175 [on MS Windows, open DOS, type “tracert”] 1 24. 88. 129 (24. 88. 129 ): 17 ms 2 stn-mtn-rtrb. atl. mediaone. net. (24. 88. 0. 254 ): 18 ms 3 24. 93. 64. 69 (24. 93. 64. 69 ): 20 ms 4 24. 93. 64. 61 (24. 93. 64. 61 ): 17 ms 5 24. 93. 64. 57 (24. 93. 64. 57 ): 25 ms 6 sgarden-sa-gsr. carolina. rr. com. (24. 93. 64. 30 ): 26 ms 7 roc-gsr-greensboro-gsr. carolina. (24. 93. 64. 17 ): 29 ms 8 24. 93. 64. 45 (24. 93. 64. 45 ): 38 ms 9 sjbrt 01 -vnbrt 01. rr. com. (24. 128. 6. 6 ): 41 ms 10 pnbrt 01 -vnbrt 01. rr. com. (24. 128. 6. 85 ): 42 ms 11 p 217. t 3. ans. net. (192. 157. 69. 52 ): 51 ms 12 h 13 -1. t 32 -0. new-york. t 3. ans. net. (140. 223. 33. 21 ): 49 ms 13 f 0 -0. cnss 33. new-york. t 3. ans. net. (140. 222. 32. 193 ): 53 ms 14 s 0. enss 3339. t 3. ans. net. (199. 222. 77. 70 ): 61 ms 15 * * * 16 * * * 7
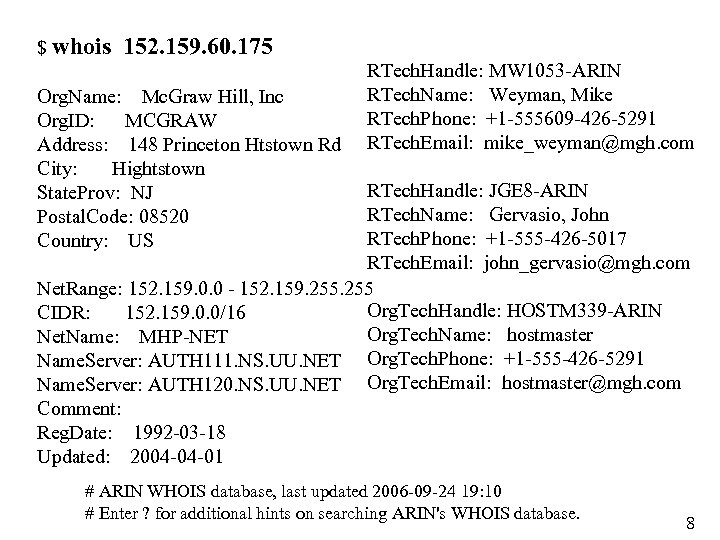 $ whois 152. 159. 60. 175 Org. Name: Mc. Graw Hill, Inc Org. ID: MCGRAW Address: 148 Princeton Htstown Rd City: Hightstown State. Prov: NJ Postal. Code: 08520 Country: US RTech. Handle: MW 1053 -ARIN RTech. Name: Weyman, Mike RTech. Phone: +1 -555609 -426 -5291 RTech. Email: mike_weyman@mgh. com RTech. Handle: JGE 8 -ARIN RTech. Name: Gervasio, John RTech. Phone: +1 -555 -426 -5017 RTech. Email: john_gervasio@mgh. com Net. Range: 152. 159. 0. 0 - 152. 159. 255 Org. Tech. Handle: HOSTM 339 -ARIN CIDR: 152. 159. 0. 0/16 Org. Tech. Name: hostmaster Net. Name: MHP-NET Name. Server: AUTH 111. NS. UU. NET Org. Tech. Phone: +1 -555 -426 -5291 Name. Server: AUTH 120. NS. UU. NET Org. Tech. Email: hostmaster@mgh. com Comment: Reg. Date: 1992 -03 -18 Updated: 2004 -04 -01 # ARIN WHOIS database, last updated 2006 -09 -24 19: 10 # Enter ? for additional hints on searching ARIN's WHOIS database. 8
$ whois 152. 159. 60. 175 Org. Name: Mc. Graw Hill, Inc Org. ID: MCGRAW Address: 148 Princeton Htstown Rd City: Hightstown State. Prov: NJ Postal. Code: 08520 Country: US RTech. Handle: MW 1053 -ARIN RTech. Name: Weyman, Mike RTech. Phone: +1 -555609 -426 -5291 RTech. Email: mike_weyman@mgh. com RTech. Handle: JGE 8 -ARIN RTech. Name: Gervasio, John RTech. Phone: +1 -555 -426 -5017 RTech. Email: john_gervasio@mgh. com Net. Range: 152. 159. 0. 0 - 152. 159. 255 Org. Tech. Handle: HOSTM 339 -ARIN CIDR: 152. 159. 0. 0/16 Org. Tech. Name: hostmaster Net. Name: MHP-NET Name. Server: AUTH 111. NS. UU. NET Org. Tech. Phone: +1 -555 -426 -5291 Name. Server: AUTH 120. NS. UU. NET Org. Tech. Email: hostmaster@mgh. com Comment: Reg. Date: 1992 -03 -18 Updated: 2004 -04 -01 # ARIN WHOIS database, last updated 2006 -09 -24 19: 10 # Enter ? for additional hints on searching ARIN's WHOIS database. 8
 Security Services for Email Privacy - only for intended recipient Authentication - confidence in ID of sender Integrity - assurance of no data alteration Non-repudiation - proof that sender sent it Proof of submission - was sent to email server Proof of delivery - was received by addressee Message flow confidentiality - no one can know a message was sent (anti-traffic analysis) 9
Security Services for Email Privacy - only for intended recipient Authentication - confidence in ID of sender Integrity - assurance of no data alteration Non-repudiation - proof that sender sent it Proof of submission - was sent to email server Proof of delivery - was received by addressee Message flow confidentiality - no one can know a message was sent (anti-traffic analysis) 9
 Anonymity - sender's ID hidden Containment - message forwards to limited area Audit - events recorded Accounting - user statistics for allocating costs Self-destruct - can not forward or store Message sequence integrity - all messages arrived in correct order 10
Anonymity - sender's ID hidden Containment - message forwards to limited area Audit - events recorded Accounting - user statistics for allocating costs Self-destruct - can not forward or store Message sequence integrity - all messages arrived in correct order 10
 Privacy Establishing Keys • Public Key Certification • Exchange Public Keys Multiple Recipients • Encrypt message m with session key, S • Encrypt S with each recipient's key • Send: {S; Kbob}, {S; Kann}, . . . , {m; S} Authentication of Source • Hash (MD 4, MD 5, SHA 1) of message, encrypt with private key (provides ciphertext/plaintext pair) • Secret Key K: MIC is hash of K+m, or CBC residue with K (assuming message not encrypted with K). 11
Privacy Establishing Keys • Public Key Certification • Exchange Public Keys Multiple Recipients • Encrypt message m with session key, S • Encrypt S with each recipient's key • Send: {S; Kbob}, {S; Kann}, . . . , {m; S} Authentication of Source • Hash (MD 4, MD 5, SHA 1) of message, encrypt with private key (provides ciphertext/plaintext pair) • Secret Key K: MIC is hash of K+m, or CBC residue with K (assuming message not encrypted with K). 11
 Message Integrity The source authentication methods that include a hash of the message provide MIC Non-repudiation Public-key signing provides non-repudiation. Secret-key method requires a "Notary" to "Sign" a time-stamp + hash of the message Proof of Delivery Acknowledge before reading - can't prove m was read. Acknowledge after - may have read without signing. 12
Message Integrity The source authentication methods that include a hash of the message provide MIC Non-repudiation Public-key signing provides non-repudiation. Secret-key method requires a "Notary" to "Sign" a time-stamp + hash of the message Proof of Delivery Acknowledge before reading - can't prove m was read. Acknowledge after - may have read without signing. 12
 Proof of Submission • CC yourself (unfortunately headers easily modified) - CC Notary (if recipient not in Bcc) Flow Confidentiality • Encrypt message and headers, to third party. • Send from the corner Cyber Cafe, fake Hot. Mail account Anonymity • Several Web site services available Containment • Network Admin can set up filter tables on routers. 13
Proof of Submission • CC yourself (unfortunately headers easily modified) - CC Notary (if recipient not in Bcc) Flow Confidentiality • Encrypt message and headers, to third party. • Send from the corner Cyber Cafe, fake Hot. Mail account Anonymity • Several Web site services available Containment • Network Admin can set up filter tables on routers. 13
 Names and Addresses X. 500 Name (ISO standard) • ? /C=US/O=CIA/OU=drugs/PN='Manny Norriega' Internet Name • m_noriega@mail. drugpc. cia. gov or manny@cia. gov •
Names and Addresses X. 500 Name (ISO standard) • ? /C=US/O=CIA/OU=drugs/PN='Manny Norriega' Internet Name • m_noriega@mail. drugpc. cia. gov or manny@cia. gov •
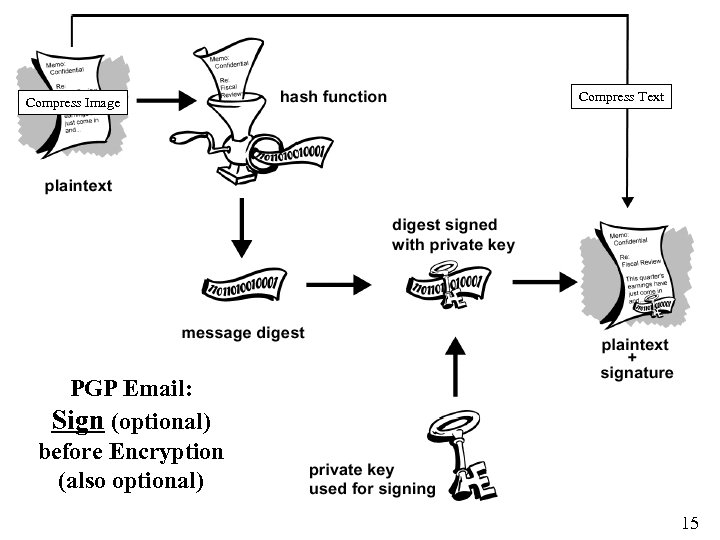 Compress Image Compress Text PGP Email: Sign (optional) before Encryption (also optional) 15
Compress Image Compress Text PGP Email: Sign (optional) before Encryption (also optional) 15
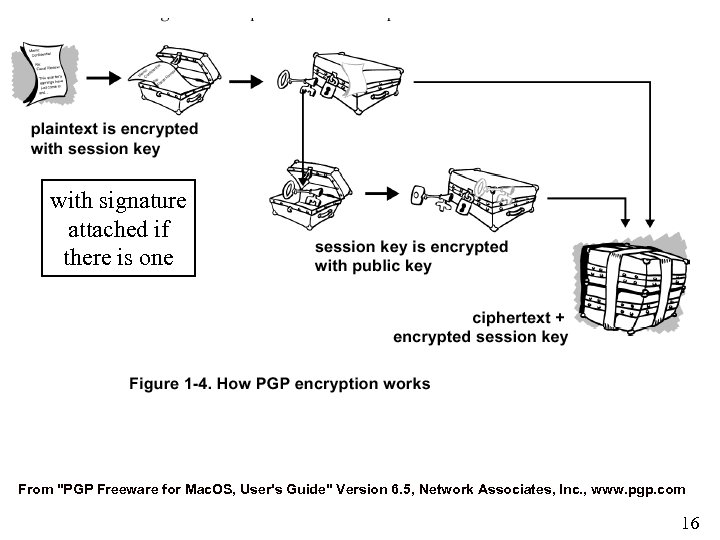 with signature attached if there is one From "PGP Freeware for Mac. OS, User's Guide" Version 6. 5, Network Associates, Inc. , www. pgp. com 16
with signature attached if there is one From "PGP Freeware for Mac. OS, User's Guide" Version 6. 5, Network Associates, Inc. , www. pgp. com 16
 Private Key Ring PGP Email Receiver Public Key Ring compressed, PGP Email Sender p. 144 -145 ed. 3 17
Private Key Ring PGP Email Receiver Public Key Ring compressed, PGP Email Sender p. 144 -145 ed. 3 17
 18
18
 Every 3 bytes split into 4 6 -bit numbers n = 0 to 63 printable characters a-z A-Z 0 -9 + in a received message, “=“, “>”, CR, LF, . . . are ignored 19
Every 3 bytes split into 4 6 -bit numbers n = 0 to 63 printable characters a-z A-Z 0 -9 + in a received message, “=“, “>”, CR, LF, . . . are ignored 19
From: John Copeland
 21
21
 PGP Certificates Anyone can issue a Certificate to anyone else Certificates can be revoked by the issuer Privacy Enhanced Mail, another standard Where PEM expands data into canonical form, • (+33% for text, +78% after encryption) PGP compresses data using ZIP(-50%), encrypts, then (optionally) converts to base 64 (+33%) 22
PGP Certificates Anyone can issue a Certificate to anyone else Certificates can be revoked by the issuer Privacy Enhanced Mail, another standard Where PEM expands data into canonical form, • (+33% for text, +78% after encryption) PGP compresses data using ZIP(-50%), encrypts, then (optionally) converts to base 64 (+33%) 22
 Things of which to be aware Neither PEM nor PGP encodes mail headers • Subject can give away useful info • To and From give an intruder traffic analysis info PGP gives recipient the original file name and modification date PEM may be used in a local system with unknown trustworthyness of certificates Certificates often verify that sender is "John Smith" but he may not be the "John Smith" you think (PGP allows pictures in certificates) 23
Things of which to be aware Neither PEM nor PGP encodes mail headers • Subject can give away useful info • To and From give an intruder traffic analysis info PGP gives recipient the original file name and modification date PEM may be used in a local system with unknown trustworthyness of certificates Certificates often verify that sender is "John Smith" but he may not be the "John Smith" you think (PGP allows pictures in certificates) 23


