acdbab48348c13897e385581c7d9746f.ppt
- Количество слайдов: 40
 ECE 646 Cryptography and Computer Network Security Course web page: ECE web page Courses Course web pages ECE 646
ECE 646 Cryptography and Computer Network Security Course web page: ECE web page Courses Course web pages ECE 646
 Kris Gaj Research and teaching interests: • cryptography • network security • computer arithmetic • FPGA & ASIC design and testing Contact: The Engineering Building, room 3225 kgaj@gmu. edu Office hours: Monday, Tuesday, Wednesday 6: 00 -7: 00 PM
Kris Gaj Research and teaching interests: • cryptography • network security • computer arithmetic • FPGA & ASIC design and testing Contact: The Engineering Building, room 3225 kgaj@gmu. edu Office hours: Monday, Tuesday, Wednesday 6: 00 -7: 00 PM
 ECE 646 Part of: MS in Cp. E Network and System Security (required) Computer Networks (elective) MS in EE Communications & Networks (elective) Ph. D. in Electrical and Computer Engineering MS in Information Security & Assurance MS in E-Commerce Certificate in Information Systems Security Ph. D. in Information Technology
ECE 646 Part of: MS in Cp. E Network and System Security (required) Computer Networks (elective) MS in EE Communications & Networks (elective) Ph. D. in Electrical and Computer Engineering MS in Information Security & Assurance MS in E-Commerce Certificate in Information Systems Security Ph. D. in Information Technology
 NETWORK AND SYSTEM SECURITY Concentration advisors: Kris Gaj, Jens-Peter Kaps 1. ECE 542 Computer Network Architectures and Protocols – S. -C. Chang, et al. 2. ECE 646 Cryptography and Computer Network Security – K. Gaj, J-P. Kaps – lab, project 3. ECE 746 Advanced Applied Cryptography – K. Gaj – lab, project: C/C++, VHDL, or analytical 4. ISA 656 Network Security – A. Stavrou 5. ECE 699 Cryptographic Engineering – J. -P. Kaps, K. Gaj
NETWORK AND SYSTEM SECURITY Concentration advisors: Kris Gaj, Jens-Peter Kaps 1. ECE 542 Computer Network Architectures and Protocols – S. -C. Chang, et al. 2. ECE 646 Cryptography and Computer Network Security – K. Gaj, J-P. Kaps – lab, project 3. ECE 746 Advanced Applied Cryptography – K. Gaj – lab, project: C/C++, VHDL, or analytical 4. ISA 656 Network Security – A. Stavrou 5. ECE 699 Cryptographic Engineering – J. -P. Kaps, K. Gaj
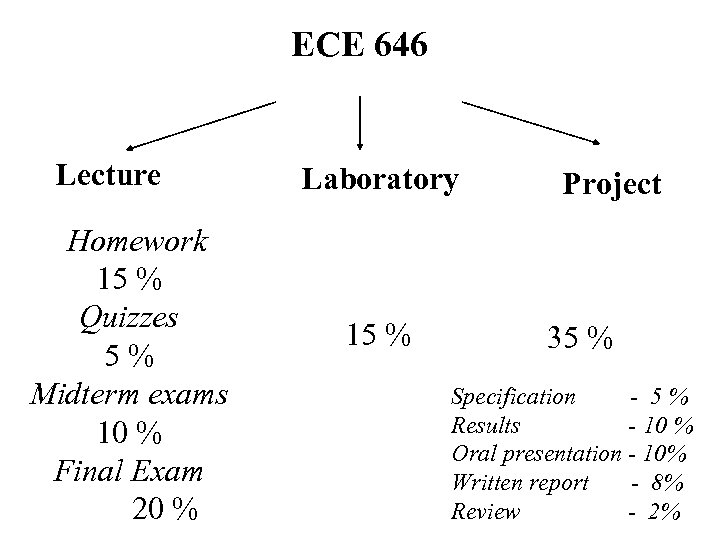 ECE 646 Lecture Homework 15 % Quizzes 5% Midterm exams 10 % Final Exam 20 % Laboratory 15 % Project 35 % Specification - 5% Results - 10 % Oral presentation - 10% Written report - 8% Review - 2%
ECE 646 Lecture Homework 15 % Quizzes 5% Midterm exams 10 % Final Exam 20 % Laboratory 15 % Project 35 % Specification - 5% Results - 10 % Oral presentation - 10% Written report - 8% Review - 2%
 deapth
deapth
 Lecture • viewgraphs / whiteboard • viewgraphs available on the web (please, extend with your notes) • books 1 required (Stallings) 1 optional (all chapters available on the book web page) • articles (Crypto. Bytes, RSA Data Security Conf. , CHES, CRYPTO, etc. ) • web sites - Crypto Resources standards, FAQs, surveys
Lecture • viewgraphs / whiteboard • viewgraphs available on the web (please, extend with your notes) • books 1 required (Stallings) 1 optional (all chapters available on the book web page) • articles (Crypto. Bytes, RSA Data Security Conf. , CHES, CRYPTO, etc. ) • web sites - Crypto Resources standards, FAQs, surveys
 Distance Learning Mode (1) • pilot project introduced for the first time this year • lectures delivered simultaneously in class and on-line • students joining on-line can actively participate in the class (raise a hand, ask questions, etc. ) • minimum preparation required (setting options of a browser, login to Blackboard, etc. ) • on-line sessions can be recorded and replayed outside of the class time (in the asynchronous mode)
Distance Learning Mode (1) • pilot project introduced for the first time this year • lectures delivered simultaneously in class and on-line • students joining on-line can actively participate in the class (raise a hand, ask questions, etc. ) • minimum preparation required (setting options of a browser, login to Blackboard, etc. ) • on-line sessions can be recorded and replayed outside of the class time (in the asynchronous mode)
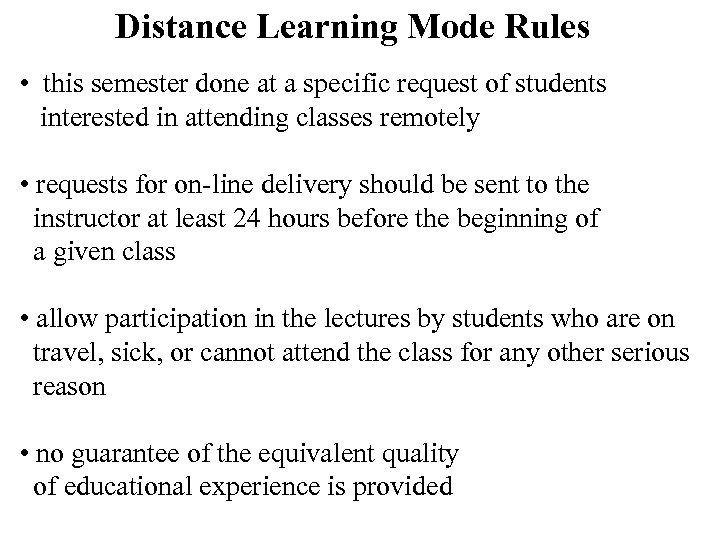 Distance Learning Mode Rules • this semester done at a specific request of students interested in attending classes remotely • requests for on-line delivery should be sent to the instructor at least 24 hours before the beginning of a given class • allow participation in the lectures by students who are on travel, sick, or cannot attend the class for any other serious reason • no guarantee of the equivalent quality of educational experience is provided
Distance Learning Mode Rules • this semester done at a specific request of students interested in attending classes remotely • requests for on-line delivery should be sent to the instructor at least 24 hours before the beginning of a given class • allow participation in the lectures by students who are on travel, sick, or cannot attend the class for any other serious reason • no guarantee of the equivalent quality of educational experience is provided
 Important Announcement There will be no class next Tuesday, September 8 (the instructor attending a conference in Europe). Instead, we will hold a make-up lecture in class: Columbus Day, Monday, Oct. 12 on-line: per your request
Important Announcement There will be no class next Tuesday, September 8 (the instructor attending a conference in Europe). Instead, we will hold a make-up lecture in class: Columbus Day, Monday, Oct. 12 on-line: per your request
 Homework (1) • reading assignments • theoretical problems (may require basics of number theory or probability theory) • problems from the main textbook • short programs • literature surveys
Homework (1) • reading assignments • theoretical problems (may require basics of number theory or probability theory) • problems from the main textbook • short programs • literature surveys
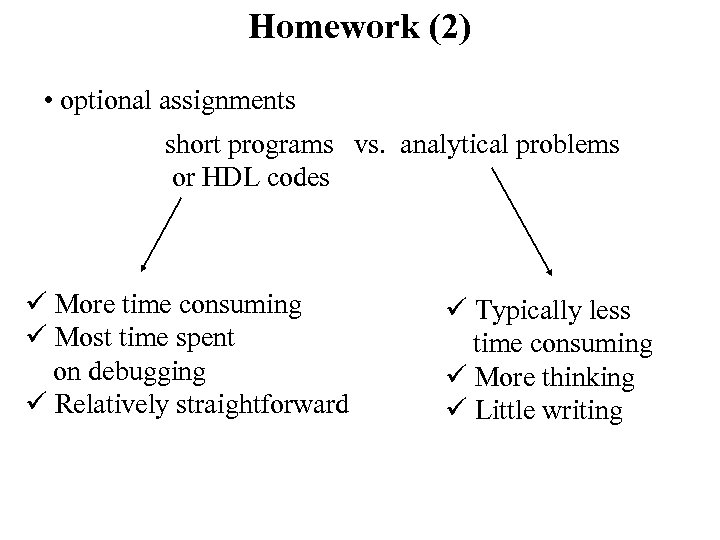 Homework (2) • optional assignments short programs vs. analytical problems or HDL codes ü More time consuming ü Most time spent on debugging ü Relatively straightforward ü Typically less time consuming ü More thinking ü Little writing
Homework (2) • optional assignments short programs vs. analytical problems or HDL codes ü More time consuming ü Most time spent on debugging ü Relatively straightforward ü Typically less time consuming ü More thinking ü Little writing
 Midterm exam ü 2 hours 30 minutes ü multiple choice test + short problems ü open-books, open-notes ü practice exams available on the web ü midterm exam review session - optional Tentative date: Tuesday, October 27 th
Midterm exam ü 2 hours 30 minutes ü multiple choice test + short problems ü open-books, open-notes ü practice exams available on the web ü midterm exam review session - optional Tentative date: Tuesday, October 27 th
 Quizzes ü 10 -15 minutes ü one-two questions related to the most recent lectures ü closed-books, closed-notes ü announced
Quizzes ü 10 -15 minutes ü one-two questions related to the most recent lectures ü closed-books, closed-notes ü announced
 Final exam 2 hours 45 minutes Multiple choice + several problems Tuesday, December 15 7: 30 – 10: 15 PM
Final exam 2 hours 45 minutes Multiple choice + several problems Tuesday, December 15 7: 30 – 10: 15 PM
 Laboratory • 4 labs based on three major software packages ü Cryp. Tool ü Gnu. PG for Linux or Gnu. PG for Windows ü MAGMA Computational Algebra System • done at home or in the ECE labs: software downloaded from the web • based on detailed instructions • grading based on written reports (answers to questions included in the instructions)
Laboratory • 4 labs based on three major software packages ü Cryp. Tool ü Gnu. PG for Linux or Gnu. PG for Windows ü MAGMA Computational Algebra System • done at home or in the ECE labs: software downloaded from the web • based on detailed instructions • grading based on written reports (answers to questions included in the instructions)
 Tentative list of laboratory topics 1. Secure e-mail: Pretty Good Privacy - Gnu. PG 2. Historical ciphers - Cryp. Tool 3. Properties of classical cryptosystems - Cryp. Tool 4. Properties of public key cryptosystems - Magma
Tentative list of laboratory topics 1. Secure e-mail: Pretty Good Privacy - Gnu. PG 2. Historical ciphers - Cryp. Tool 3. Properties of classical cryptosystems - Cryp. Tool 4. Properties of public key cryptosystems - Magma
 Project (1) • original • useful • depth, originality • based on additional literature • you can start at the point where former students ended • based on something you know and are interested in • software or hardware • may involve experiments • teams of 1 -3 students
Project (1) • original • useful • depth, originality • based on additional literature • you can start at the point where former students ended • based on something you know and are interested in • software or hardware • may involve experiments • teams of 1 -3 students
 Project (2) • about three weeks to choose a topic and write the corresponding specification • regular meetings with the instructor • a few oral progress reports based on Power Point slides • draft final presentation due at the last progress report • written report/article, IEEE style due Tuesday December 1 • short conference-style oral presentations Tuesday, December 8 • contest for the best presentation • publication of reports and viewgraphs on the web
Project (2) • about three weeks to choose a topic and write the corresponding specification • regular meetings with the instructor • a few oral progress reports based on Power Point slides • draft final presentation due at the last progress report • written report/article, IEEE style due Tuesday December 1 • short conference-style oral presentations Tuesday, December 8 • contest for the best presentation • publication of reports and viewgraphs on the web
 Project (3) • Project reports/articles requirements - IEEE style - 15 pages maximum - appendices possible but do not influence the evaluation • Review of project reports - reviews done by your fellow students - reviews due, Saturday, December 5, midnight - final version of the report due Monday, December 7, midnight
Project (3) • Project reports/articles requirements - IEEE style - 15 pages maximum - appendices possible but do not influence the evaluation • Review of project reports - reviews done by your fellow students - reviews due, Saturday, December 5, midnight - final version of the report due Monday, December 7, midnight
 Project (4) • Project presentations (Tuesday, December 8, 7: 30 -10: 00 PM) - conference style - open to general public (in particular, students from previous years), ECE seminar credit - 10 minutes for the presentation + 5 minutes for Q&A - time strictly enforced
Project (4) • Project presentations (Tuesday, December 8, 7: 30 -10: 00 PM) - conference style - open to general public (in particular, students from previous years), ECE seminar credit - 10 minutes for the presentation + 5 minutes for Q&A - time strictly enforced
 This Year’s Project Theme Benchmarking (comparing) • cryptographic algorithms • cryptographic libraries and open-source implementations (software and hardware) • platforms • tools
This Year’s Project Theme Benchmarking (comparing) • cryptographic algorithms • cryptographic libraries and open-source implementations (software and hardware) • platforms • tools
 Motivation (1) • multitude of implementations of cryptographic algorithms available in public domain (~50 open-source software libraries, >20 open-source hardware cryptographic cores) How do they compare against each other? Which one to use when implementing a particular cryptographic system?
Motivation (1) • multitude of implementations of cryptographic algorithms available in public domain (~50 open-source software libraries, >20 open-source hardware cryptographic cores) How do they compare against each other? Which one to use when implementing a particular cryptographic system?
 Motivation (2) • multitude of platforms ü general-purpose microprocessors (e. g. , Pentium 4, Core i 7, etc. ) ü microcontrollers (TI MSP 430, Micro. Chip PIC 18) ü Digital Signal Processors ü FPGAs (from Xilinx, Altera, Actel, etc. ) ü ASICs (based on various libraries of standard cells) ü processors embedded in FPGAs (Pico. Blaze, Micro. Blaze, Nios II)
Motivation (2) • multitude of platforms ü general-purpose microprocessors (e. g. , Pentium 4, Core i 7, etc. ) ü microcontrollers (TI MSP 430, Micro. Chip PIC 18) ü Digital Signal Processors ü FPGAs (from Xilinx, Altera, Actel, etc. ) ü ASICs (based on various libraries of standard cells) ü processors embedded in FPGAs (Pico. Blaze, Micro. Blaze, Nios II)
 Motivation (3) • multitude of languages and tools ü C, C++, Java, Python, C#, assembly language, etc. ü VHDL, Verilog, AHDL, etc. ü multiple compilers for software codes ü multiple synthesis tools for hardware codes
Motivation (3) • multitude of languages and tools ü C, C++, Java, Python, C#, assembly language, etc. ü VHDL, Verilog, AHDL, etc. ü multiple compilers for software codes ü multiple synthesis tools for hardware codes
 Motivation (4) • multitude of cryptographic algorithms ü secret-key block ciphers ü secret-key stream ciphers ü public-key ciphers ü hash functions ü message authentication codes ü digital signature schemes ü key agreement schemes
Motivation (4) • multitude of cryptographic algorithms ü secret-key block ciphers ü secret-key stream ciphers ü public-key ciphers ü hash functions ü message authentication codes ü digital signature schemes ü key agreement schemes
 Common benchmarking pitfalls • • • taking credit for improvements in technology e. g. comparing Bob's AES in Virtex 5 vs. Alice's AES in Virtex 2 Pro choosing a convenient performance measure comparing designs with different functionality e. g. , encryption+decryption vs. encryption only comparing the speed of different operations e. g. , comparing the combined speed of encrypting 8 messages in parallel vs. the speed of encrypting a single long message designs optimized using different optimization criteria e. g. , speed only or the ratio of speed to cost using different input/output interfaces 27
Common benchmarking pitfalls • • • taking credit for improvements in technology e. g. comparing Bob's AES in Virtex 5 vs. Alice's AES in Virtex 2 Pro choosing a convenient performance measure comparing designs with different functionality e. g. , encryption+decryption vs. encryption only comparing the speed of different operations e. g. , comparing the combined speed of encrypting 8 messages in parallel vs. the speed of encrypting a single long message designs optimized using different optimization criteria e. g. , speed only or the ratio of speed to cost using different input/output interfaces 27
 Previous Work Comparative Analysis of Software Multi-precision Arithmetic Libraries for Public Key Cryptography Ashraf Abu. Sharekh MS Thesis, April 2004
Previous Work Comparative Analysis of Software Multi-precision Arithmetic Libraries for Public Key Cryptography Ashraf Abu. Sharekh MS Thesis, April 2004
 Previous work e. BACS: ECRYPT Benchmarking of Cryptographic Systems http: //bench. cr. yp. to Project to compare software implementations of cryptographic algorithms Developed by: Daniel J. Bernstein and Tanja Lange (2006 -present) Activity of: VAMPIRE: Virtual Application and Implementation REsearch Lab Integrates: e. BATS: ECRYPT Benchmarking of Asymmetric Systems e. BASC: ECRYPT Benchmarking of Stream Ciphers e. BASH: ECRYPT Benchmarking of All Submitted Hashes Extends earlier software evaluation projects developed by different groups 29
Previous work e. BACS: ECRYPT Benchmarking of Cryptographic Systems http: //bench. cr. yp. to Project to compare software implementations of cryptographic algorithms Developed by: Daniel J. Bernstein and Tanja Lange (2006 -present) Activity of: VAMPIRE: Virtual Application and Implementation REsearch Lab Integrates: e. BATS: ECRYPT Benchmarking of Asymmetric Systems e. BASC: ECRYPT Benchmarking of Stream Ciphers e. BASH: ECRYPT Benchmarking of All Submitted Hashes Extends earlier software evaluation projects developed by different groups 29
 SUPERCOP System for Unified Performance Evaluation Related to Cryptographic Operations and Primitives • toolkit developed by the VAMPIRE lab for measuring the performance of cryptographic software • measures the performance of – – secret-key stream ciphers – public-key encryption systems – public-key signature systems – • hash functions public-key secret-sharing systems output is an extensive set of measurements in a form suitable for easy computer processing 30
SUPERCOP System for Unified Performance Evaluation Related to Cryptographic Operations and Primitives • toolkit developed by the VAMPIRE lab for measuring the performance of cryptographic software • measures the performance of – – secret-key stream ciphers – public-key encryption systems – public-key signature systems – • hash functions public-key secret-sharing systems output is an extensive set of measurements in a form suitable for easy computer processing 30
 SUPERCOP • measurements on multiple machines (currently over 70) and machine-ABI (application binary interface) combinations (currently over 100) • each implementation is recompiled multiple times (currently over 1200 times) with various compiler options to identify best working options for implementation, machine • time measured in clock cycles/byte for multiple input/output sizes • median, lower quartile (25 th percentile), and upper quartile (75 th percentile) reported • standardized function arguments (may be implemented using wrappers) 31
SUPERCOP • measurements on multiple machines (currently over 70) and machine-ABI (application binary interface) combinations (currently over 100) • each implementation is recompiled multiple times (currently over 1200 times) with various compiler options to identify best working options for implementation, machine • time measured in clock cycles/byte for multiple input/output sizes • median, lower quartile (25 th percentile), and upper quartile (75 th percentile) reported • standardized function arguments (may be implemented using wrappers) 31
 GMU Tool ATHENa – Automated Tool for Hardware Evaluatio. N Set of scripts written in Perl aimed at an AUTOMATED generation of OPTIMIZED results for MULTIPLE hardware platforms Currently under development at George Mason University. First version to be released this Fall. 32
GMU Tool ATHENa – Automated Tool for Hardware Evaluatio. N Set of scripts written in Perl aimed at an AUTOMATED generation of OPTIMIZED results for MULTIPLE hardware platforms Currently under development at George Mason University. First version to be released this Fall. 32
 ATHENa Major Features • running all steps of synthesis, implementation, and timing analysis in the batch mode • support for devices and tools of multiple FPGA vendors: Xilinx, Altera, Actel • generation of results for multiple families of FPGAs of a given vendor • automated choice of a device within a given family of FPGAa assuming that the resource utilization does not exceed a certain limit, e. g. , 80% of CLB slices, or 70% of BRAM • choice of multiple optimization criteria (speed, area, ratio speed/area) • heuristic optimization algorithms aimed at maximizing the performance measures (e. g. , speed) based on checking multiple 33 options, and multiple target clock frequencies
ATHENa Major Features • running all steps of synthesis, implementation, and timing analysis in the batch mode • support for devices and tools of multiple FPGA vendors: Xilinx, Altera, Actel • generation of results for multiple families of FPGAs of a given vendor • automated choice of a device within a given family of FPGAa assuming that the resource utilization does not exceed a certain limit, e. g. , 80% of CLB slices, or 70% of BRAM • choice of multiple optimization criteria (speed, area, ratio speed/area) • heuristic optimization algorithms aimed at maximizing the performance measures (e. g. , speed) based on checking multiple 33 options, and multiple target clock frequencies
 ATHENa Additional Features • automated verification of the design through simulation, run in the batch mode based on the provided testbench (optional): – Functional – Post-synthesis – Timing • support for Windows and Linux • Graphical User Interface Requirements: – interpreter of Perl – FPGA tools: free, educational, or commercial versions 34
ATHENa Additional Features • automated verification of the design through simulation, run in the batch mode based on the provided testbench (optional): – Functional – Post-synthesis – Timing • support for Windows and Linux • Graphical User Interface Requirements: – interpreter of Perl – FPGA tools: free, educational, or commercial versions 34
 ATHENa Input/Output Input: – synthesizable source files – configuration files (text files) – testbench (optional) – constraint files (optional) Output: – result summary (human readable) – database entries (suitable for computer postprocessing) 35
ATHENa Input/Output Input: – synthesizable source files – configuration files (text files) – testbench (optional) – constraint files (optional) Output: – result summary (human readable) – database entries (suitable for computer postprocessing) 35
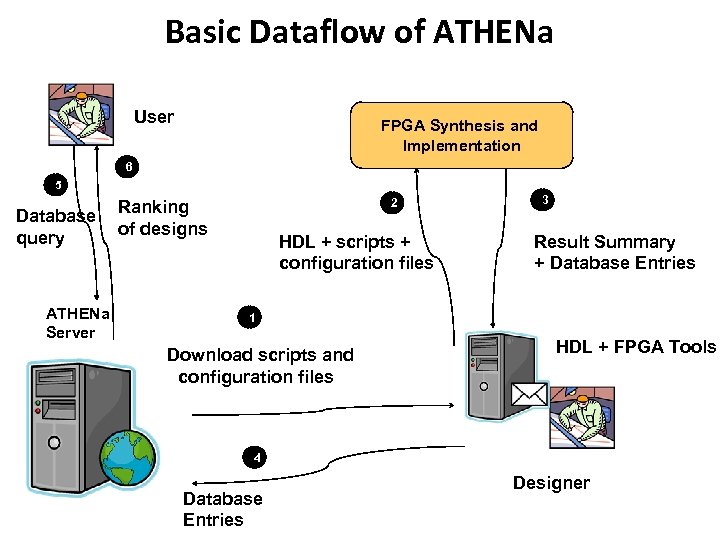 Basic Dataflow of ATHENa User FPGA Synthesis and Implementation 6 5 Database query ATHENa Server 2 Ranking of designs HDL + scripts + configuration files 3 Result Summary + Database Entries 1 Download scripts and configuration files 8 HDL + FPGA Tools 4 Database Entries Designer
Basic Dataflow of ATHENa User FPGA Synthesis and Implementation 6 5 Database query ATHENa Server 2 Ranking of designs HDL + scripts + configuration files 3 Result Summary + Database Entries 1 Download scripts and configuration files 8 HDL + FPGA Tools 4 Database Entries Designer
 Draft Specification due in two weeks Specification should include the choice of: • software vs. hardware • software cryptographic libraries or hardware cryptographic cores • languages • platforms • tools • list of cryptographic algorithms included in comparison (common for selected libraries)
Draft Specification due in two weeks Specification should include the choice of: • software vs. hardware • software cryptographic libraries or hardware cryptographic cores • languages • platforms • tools • list of cryptographic algorithms included in comparison (common for selected libraries)
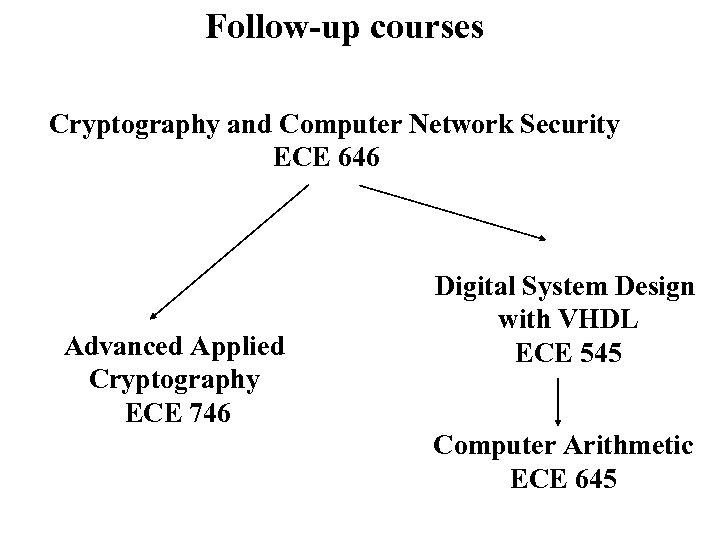 Follow-up courses Cryptography and Computer Network Security ECE 646 Advanced Applied Cryptography ECE 746 Digital System Design with VHDL ECE 545 Computer Arithmetic ECE 645
Follow-up courses Cryptography and Computer Network Security ECE 646 Advanced Applied Cryptography ECE 746 Digital System Design with VHDL ECE 545 Computer Arithmetic ECE 645
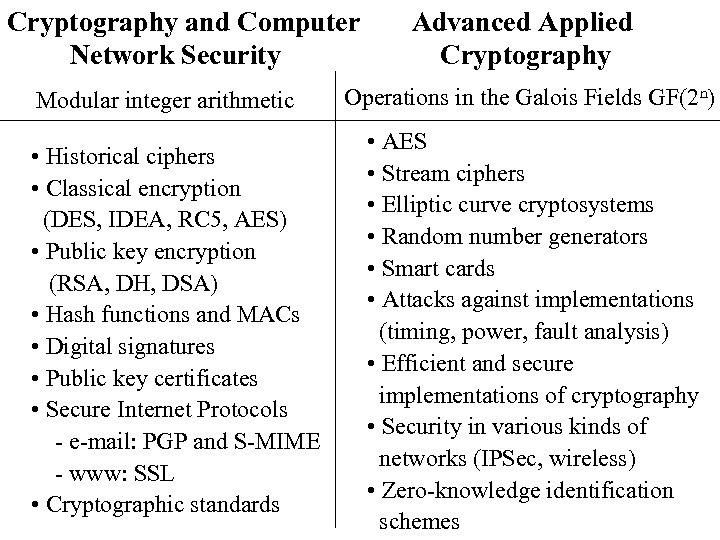 Cryptography and Computer Network Security Modular integer arithmetic • Historical ciphers • Classical encryption (DES, IDEA, RC 5, AES) • Public key encryption (RSA, DH, DSA) • Hash functions and MACs • Digital signatures • Public key certificates • Secure Internet Protocols - e-mail: PGP and S-MIME - www: SSL • Cryptographic standards Advanced Applied Cryptography Operations in the Galois Fields GF(2 n) • AES • Stream ciphers • Elliptic curve cryptosystems • Random number generators • Smart cards • Attacks against implementations (timing, power, fault analysis) • Efficient and secure implementations of cryptography • Security in various kinds of networks (IPSec, wireless) • Zero-knowledge identification schemes
Cryptography and Computer Network Security Modular integer arithmetic • Historical ciphers • Classical encryption (DES, IDEA, RC 5, AES) • Public key encryption (RSA, DH, DSA) • Hash functions and MACs • Digital signatures • Public key certificates • Secure Internet Protocols - e-mail: PGP and S-MIME - www: SSL • Cryptographic standards Advanced Applied Cryptography Operations in the Galois Fields GF(2 n) • AES • Stream ciphers • Elliptic curve cryptosystems • Random number generators • Smart cards • Attacks against implementations (timing, power, fault analysis) • Efficient and secure implementations of cryptography • Security in various kinds of networks (IPSec, wireless) • Zero-knowledge identification schemes
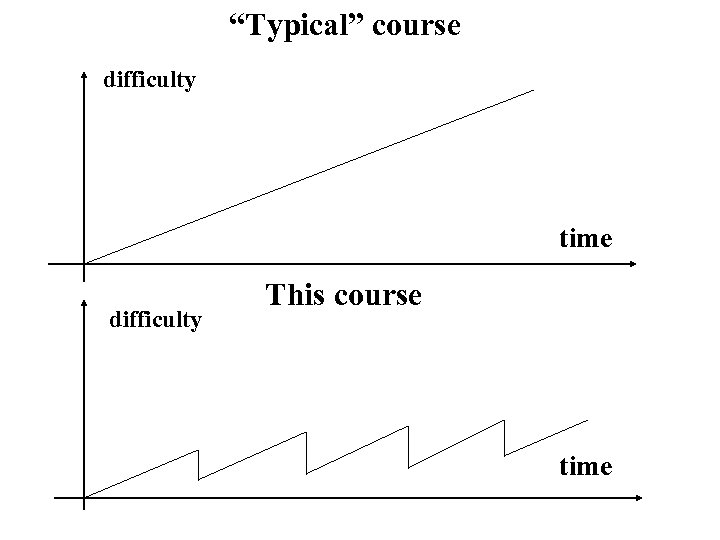 “Typical” course difficulty time difficulty This course time
“Typical” course difficulty time difficulty This course time


