6f2233e6c3bb91cb4dd4f1c4508d3381.ppt
- Количество слайдов: 59
 Eavesdropping attack over Wi-Fi Course: Security and Privacy on the Internet Instructor: Dr. A. K. Aggarwal Presented By: Fadi Farhat Fall, 2007 1 564 Fall 2007 Security and Privacy on the Internet - Dr. A. K. Aggarwal
Eavesdropping attack over Wi-Fi Course: Security and Privacy on the Internet Instructor: Dr. A. K. Aggarwal Presented By: Fadi Farhat Fall, 2007 1 564 Fall 2007 Security and Privacy on the Internet - Dr. A. K. Aggarwal
 Table of Contents Part I: Paper presentation 1. Define Eavesdropping. 2. Difference between Eavesdropping over wired networks & Eavesdropping over wireless networks. 3. What we need to eavesdrop? 4. Legality of eavesdropping devices. 5. What makes Wi-Fi susceptible to be compromised? 6. How to Secure Wi-Fi Networks? 7. Wi-Fi Special attacks. 8. How to detect eavesdropping over Wi-Fi? 2 564 Fall 2007 Security and Privacy on the Internet - Dr. A. K. Aggarwal
Table of Contents Part I: Paper presentation 1. Define Eavesdropping. 2. Difference between Eavesdropping over wired networks & Eavesdropping over wireless networks. 3. What we need to eavesdrop? 4. Legality of eavesdropping devices. 5. What makes Wi-Fi susceptible to be compromised? 6. How to Secure Wi-Fi Networks? 7. Wi-Fi Special attacks. 8. How to detect eavesdropping over Wi-Fi? 2 564 Fall 2007 Security and Privacy on the Internet - Dr. A. K. Aggarwal
 Table of Contents Part II: Project presentation Introduction 1. Experiment Architecture and Scenarios 2. Hosts Installations and Configuration 3. Tuning Comm. View sniffer for experiment 4. Conducting the Experiment 4. 1. Spying on HTTP (Web Pages) 4. 2. Spying on FTP (Downloading files) 4. 3. Spying on SMTP (Emails) 5. 6. References 7. 3 IDS Promisacn 3. 0 Lab Experiment with ? ? ? 564 Fall 2007 Security and Privacy on the Internet - Dr. A. K. Aggarwal
Table of Contents Part II: Project presentation Introduction 1. Experiment Architecture and Scenarios 2. Hosts Installations and Configuration 3. Tuning Comm. View sniffer for experiment 4. Conducting the Experiment 4. 1. Spying on HTTP (Web Pages) 4. 2. Spying on FTP (Downloading files) 4. 3. Spying on SMTP (Emails) 5. 6. References 7. 3 IDS Promisacn 3. 0 Lab Experiment with ? ? ? 564 Fall 2007 Security and Privacy on the Internet - Dr. A. K. Aggarwal
 Part I Paper presentation 4 564 Fall 2007 Security and Privacy on the Internet - Dr. A. K. Aggarwal
Part I Paper presentation 4 564 Fall 2007 Security and Privacy on the Internet - Dr. A. K. Aggarwal
 Eavesdropping n n To eavesdrop is to secretly overhear a private conversation over a confidential communication in a not legally authorized way. n 5 Eavesdropping is the process of gathering information from a network by snooping on transmitted data. The information remains intact, but its privacy is compromised. 564 Fall 2007 Security and Privacy on the Internet - Dr. A. K. Aggarwal
Eavesdropping n n To eavesdrop is to secretly overhear a private conversation over a confidential communication in a not legally authorized way. n 5 Eavesdropping is the process of gathering information from a network by snooping on transmitted data. The information remains intact, but its privacy is compromised. 564 Fall 2007 Security and Privacy on the Internet - Dr. A. K. Aggarwal
 Eavesdropping over wired & wireless networks Eavesdropping over wired networks Over wired networks eavesdropping is more difficult n It needs the eavesdropper to tap the network, using a network tap which is a hardware device that provides a way to access the data flowing across the network. n Can’t be achieved unless the eavesdropper can be in touch with the wire of the network which is difficult sometimes and impossible the other times. n 6 564 Fall 2007 Security and Privacy on the Internet - Dr. A. K. Aggarwal
Eavesdropping over wired & wireless networks Eavesdropping over wired networks Over wired networks eavesdropping is more difficult n It needs the eavesdropper to tap the network, using a network tap which is a hardware device that provides a way to access the data flowing across the network. n Can’t be achieved unless the eavesdropper can be in touch with the wire of the network which is difficult sometimes and impossible the other times. n 6 564 Fall 2007 Security and Privacy on the Internet - Dr. A. K. Aggarwal
 Eavesdropping over wired & wireless networks Eavesdropping over wireless networks n Easier to be achieved (no compromised dangerous). You need n n To be in the area of the wireless network coverage n 7 A computer with wireless network adapter working on promiscuous mode To have one of the particular software tools that allows the eavesdropping over Wi-Fi. Commercial name for the 802. 11 products. 564 Fall 2007 Security and Privacy on the Internet - Dr. A. K. Aggarwal
Eavesdropping over wired & wireless networks Eavesdropping over wireless networks n Easier to be achieved (no compromised dangerous). You need n n To be in the area of the wireless network coverage n 7 A computer with wireless network adapter working on promiscuous mode To have one of the particular software tools that allows the eavesdropping over Wi-Fi. Commercial name for the 802. 11 products. 564 Fall 2007 Security and Privacy on the Internet - Dr. A. K. Aggarwal
 What we need to eavesdrop? 1. Hardware tools n n 8 Network adapter supporting promiscuous mode (to intercept and read each network packet especially those of other network address). Ex: Prism 2, 2. 5 and 3. High-power antennas can be used to provide intercepting wireless traffic from miles away. 564 Fall 2007 Security and Privacy on the Internet - Dr. A. K. Aggarwal
What we need to eavesdrop? 1. Hardware tools n n 8 Network adapter supporting promiscuous mode (to intercept and read each network packet especially those of other network address). Ex: Prism 2, 2. 5 and 3. High-power antennas can be used to provide intercepting wireless traffic from miles away. 564 Fall 2007 Security and Privacy on the Internet - Dr. A. K. Aggarwal
 What we need to eavesdrop? 2. Software tools n Any Wireless Packet Sniffer can be used n Widely available for sale and even free over the Internet Ex: Network Stumbler, Hitchhiker, Aircrack-ng, Wireshark, Kisemet, Commview, Javvin packet analyzer, Wildpackets, Network monitor, Wireless monitor 9 564 Fall 2007 Security and Privacy on the Internet - Dr. A. K. Aggarwal
What we need to eavesdrop? 2. Software tools n Any Wireless Packet Sniffer can be used n Widely available for sale and even free over the Internet Ex: Network Stumbler, Hitchhiker, Aircrack-ng, Wireshark, Kisemet, Commview, Javvin packet analyzer, Wildpackets, Network monitor, Wireless monitor 9 564 Fall 2007 Security and Privacy on the Internet - Dr. A. K. Aggarwal
 Legality of eavesdropping devices n n It is a crime in most countries to eavesdrop on someone’s privacy n 10 Be aware of the legal issues before you buy eavesdropping devices. But as network administrators need to analyze traffic on their networks (debug networks, find illegitimately installed access points) they may need eavesdropping devices. 564 Fall 2007 Security and Privacy on the Internet - Dr. A. K. Aggarwal
Legality of eavesdropping devices n n It is a crime in most countries to eavesdrop on someone’s privacy n 10 Be aware of the legal issues before you buy eavesdropping devices. But as network administrators need to analyze traffic on their networks (debug networks, find illegitimately installed access points) they may need eavesdropping devices. 564 Fall 2007 Security and Privacy on the Internet - Dr. A. K. Aggarwal
 What makes Wi-Fi susceptible to be compromised n n Many individuals’ and businesses don't understand how to secure a wireless network n 11 Most of the network adapters used around the world are unsecured and open to unauthorized use Many Wi-Fi products come ready-to-use right out of the box. 564 Fall 2007 Security and Privacy on the Internet - Dr. A. K. Aggarwal
What makes Wi-Fi susceptible to be compromised n n Many individuals’ and businesses don't understand how to secure a wireless network n 11 Most of the network adapters used around the world are unsecured and open to unauthorized use Many Wi-Fi products come ready-to-use right out of the box. 564 Fall 2007 Security and Privacy on the Internet - Dr. A. K. Aggarwal
 Securing Wi-Fi Networks? n n 12 The only available way to fight eavesdropping is the encryption. But even using the encryption technique will not prevent capturing the data in its encrypted form. 564 Fall 2007 Security and Privacy on the Internet - Dr. A. K. Aggarwal
Securing Wi-Fi Networks? n n 12 The only available way to fight eavesdropping is the encryption. But even using the encryption technique will not prevent capturing the data in its encrypted form. 564 Fall 2007 Security and Privacy on the Internet - Dr. A. K. Aggarwal
 How to Secure Wi-Fi Networks? Simple Steps to Secure Wi-Fi Network 1. Change the Administrative Password on your Wireless Routers. 2. Installing a Firewall. 3. Change the Default SSID Name and Turn off SSID Broadcasting. 4. Disable DHCP. 5. Replace WEP with WPA. 13 564 Fall 2007 Security and Privacy on the Internet - Dr. A. K. Aggarwal
How to Secure Wi-Fi Networks? Simple Steps to Secure Wi-Fi Network 1. Change the Administrative Password on your Wireless Routers. 2. Installing a Firewall. 3. Change the Default SSID Name and Turn off SSID Broadcasting. 4. Disable DHCP. 5. Replace WEP with WPA. 13 564 Fall 2007 Security and Privacy on the Internet - Dr. A. K. Aggarwal
 How to Secure Wi-Fi Networks? 1. Change the Administrative Password on your Wireless Routers. n n Changing those passwords is one of the first recommended steps to do. n 14 Routers came with default password to provide easy access. Default passwords are posted on the vendor support sites. 564 Fall 2007 Security and Privacy on the Internet - Dr. A. K. Aggarwal
How to Secure Wi-Fi Networks? 1. Change the Administrative Password on your Wireless Routers. n n Changing those passwords is one of the first recommended steps to do. n 14 Routers came with default password to provide easy access. Default passwords are posted on the vendor support sites. 564 Fall 2007 Security and Privacy on the Internet - Dr. A. K. Aggarwal
 How to Secure Wi-Fi Networks? 2. Installing a Firewall. n n 15 A firewall is the fence of your network from any unauthorized accessing Can help in the protection of your PC by blocking or allowing the pass to your network. 564 Fall 2007 Security and Privacy on the Internet - Dr. A. K. Aggarwal
How to Secure Wi-Fi Networks? 2. Installing a Firewall. n n 15 A firewall is the fence of your network from any unauthorized accessing Can help in the protection of your PC by blocking or allowing the pass to your network. 564 Fall 2007 Security and Privacy on the Internet - Dr. A. K. Aggarwal
 How to Secure Wi-Fi Networks? 3. Change the Default SSID Name and Turn off SSID Broadcasting. n n Changing SSID will necessitate the wireless client computers to enter the name of the SSID by hand before they can connect to the network. n 16 In Wi-Fi a service set identifier (SSID) is a code attached to all packets on a wireless network to identify each packet as a part of the network. But even though and because the data packets that are transmitted will include the SSID it may be discovered. 564 Fall 2007 Security and Privacy on the Internet - Dr. A. K. Aggarwal
How to Secure Wi-Fi Networks? 3. Change the Default SSID Name and Turn off SSID Broadcasting. n n Changing SSID will necessitate the wireless client computers to enter the name of the SSID by hand before they can connect to the network. n 16 In Wi-Fi a service set identifier (SSID) is a code attached to all packets on a wireless network to identify each packet as a part of the network. But even though and because the data packets that are transmitted will include the SSID it may be discovered. 564 Fall 2007 Security and Privacy on the Internet - Dr. A. K. Aggarwal
 How to Secure Wi-Fi Networks? 4. Disable DHCP n n 17 Disable the “Dynamic Host Configuration Protocol” Assign IP addresses to the client computers manually to restrict the access to the router to specific MAC addresses. 564 Fall 2007 Security and Privacy on the Internet - Dr. A. K. Aggarwal
How to Secure Wi-Fi Networks? 4. Disable DHCP n n 17 Disable the “Dynamic Host Configuration Protocol” Assign IP addresses to the client computers manually to restrict the access to the router to specific MAC addresses. 564 Fall 2007 Security and Privacy on the Internet - Dr. A. K. Aggarwal
 How to Secure Wi-Fi Networks? 5. Replace WEP with WPA n n 18 WEP “Wired Equivalent Privacy” is a security protocol, encrypting data transmitted over the wireless computer network to provide security and privacy, and to protect the vulnerable wireless link between clients and access points. But as WEP is weak and can be cracked in about 3 minutes as the FBI showed in 2005 using some freely access tools, WPA “Wi-Fi Protected Access” which is more powerful using 128 -bit encryption keys and dynamic session keys, must replace it to provide strong data protection. 564 Fall 2007 Security and Privacy on the Internet - Dr. A. K. Aggarwal
How to Secure Wi-Fi Networks? 5. Replace WEP with WPA n n 18 WEP “Wired Equivalent Privacy” is a security protocol, encrypting data transmitted over the wireless computer network to provide security and privacy, and to protect the vulnerable wireless link between clients and access points. But as WEP is weak and can be cracked in about 3 minutes as the FBI showed in 2005 using some freely access tools, WPA “Wi-Fi Protected Access” which is more powerful using 128 -bit encryption keys and dynamic session keys, must replace it to provide strong data protection. 564 Fall 2007 Security and Privacy on the Internet - Dr. A. K. Aggarwal
 Wi-Fi Special attacks Man-In-The-Middle Attack is one of the attacks that can’t be applied to wired networks, it’s just applicable to Wi-Fi. n Hackers can configure a rogue AP to imitate a legitimate AP. n Once the client is connected to the rogue AP, the hacker can perform any attack that involves modifying the packet stream. n Emails can be read, phishing attacks can be implemented etc. . . 19 564 Fall 2007 Security and Privacy on the Internet - Dr. A. K. Aggarwal
Wi-Fi Special attacks Man-In-The-Middle Attack is one of the attacks that can’t be applied to wired networks, it’s just applicable to Wi-Fi. n Hackers can configure a rogue AP to imitate a legitimate AP. n Once the client is connected to the rogue AP, the hacker can perform any attack that involves modifying the packet stream. n Emails can be read, phishing attacks can be implemented etc. . . 19 564 Fall 2007 Security and Privacy on the Internet - Dr. A. K. Aggarwal
 How to detect eavesdropping over Wi-Fi n Some Wi-Fi equipment makers have added more security measures like n Intrusion detection uses position location technology to detect the presence of a malicious station in order to track down the offending station and remove it. n Sniffing node detection tool to detect the Promiscuous Nodes. Ex: Promi. Scan. 20 564 Fall 2007 Security and Privacy on the Internet - Dr. A. K. Aggarwal
How to detect eavesdropping over Wi-Fi n Some Wi-Fi equipment makers have added more security measures like n Intrusion detection uses position location technology to detect the presence of a malicious station in order to track down the offending station and remove it. n Sniffing node detection tool to detect the Promiscuous Nodes. Ex: Promi. Scan. 20 564 Fall 2007 Security and Privacy on the Internet - Dr. A. K. Aggarwal
 Part II Project presentation 21 564 Fall 2007 Security and Privacy on the Internet - Dr. A. K. Aggarwal
Part II Project presentation 21 564 Fall 2007 Security and Privacy on the Internet - Dr. A. K. Aggarwal
 Introduction n n Unsecured wireless sessions can be target for eavesdropping attackers. n 22 In this project, I simulate an easy, yet important, eavesdropping wireless attack. Serious confidential and personal data can be captured, analyzed and even retransmitted on one’s behalf. 564 Fall 2007 Security and Privacy on the Internet - Dr. A. K. Aggarwal
Introduction n n Unsecured wireless sessions can be target for eavesdropping attackers. n 22 In this project, I simulate an easy, yet important, eavesdropping wireless attack. Serious confidential and personal data can be captured, analyzed and even retransmitted on one’s behalf. 564 Fall 2007 Security and Privacy on the Internet - Dr. A. K. Aggarwal
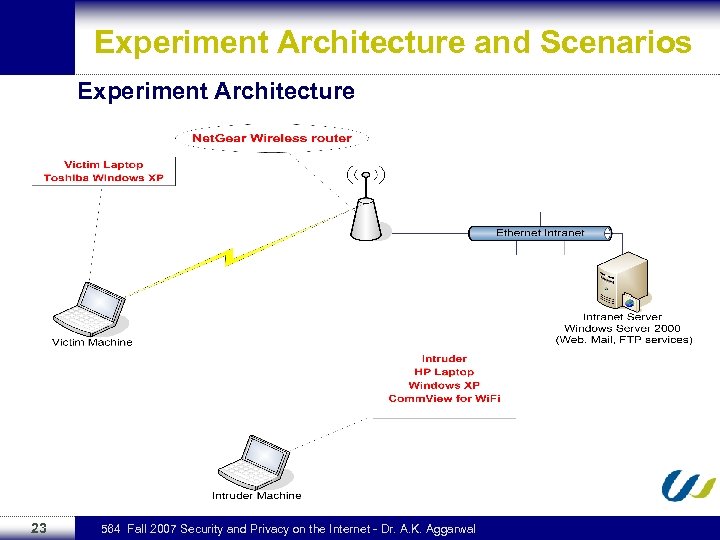 Experiment Architecture and Scenarios Experiment Architecture 23 564 Fall 2007 Security and Privacy on the Internet - Dr. A. K. Aggarwal
Experiment Architecture and Scenarios Experiment Architecture 23 564 Fall 2007 Security and Privacy on the Internet - Dr. A. K. Aggarwal
 Experiment Architecture and Scenarios Experiment Scenarios The intruder (an upset student) will try to listen to the data flow to/from the victim (his professor) and capture important information about him. n n Spying on FTP (Downloading files) n 24 Spying on HTTP (Web Pages) Spying on SMTP (Emails) 564 Fall 2007 Security and Privacy on the Internet - Dr. A. K. Aggarwal
Experiment Architecture and Scenarios Experiment Scenarios The intruder (an upset student) will try to listen to the data flow to/from the victim (his professor) and capture important information about him. n n Spying on FTP (Downloading files) n 24 Spying on HTTP (Web Pages) Spying on SMTP (Emails) 564 Fall 2007 Security and Privacy on the Internet - Dr. A. K. Aggarwal
 Hosts Installations and Configuration of Victim Machine Configuring Outlook Express email client Toshiba Laptop CPU: Centrino 1. 7 Ghz Memory: 1 GB Hard Disk: 80 GB Operating System: Windows XP professional IP Address: 192. 168. 1. 2 25 564 Fall 2007 Security and Privacy on the Internet - Dr. A. K. Aggarwal
Hosts Installations and Configuration of Victim Machine Configuring Outlook Express email client Toshiba Laptop CPU: Centrino 1. 7 Ghz Memory: 1 GB Hard Disk: 80 GB Operating System: Windows XP professional IP Address: 192. 168. 1. 2 25 564 Fall 2007 Security and Privacy on the Internet - Dr. A. K. Aggarwal
 Hosts Installations and Configuration of Victim Machine Configuring Outlook Express email client 26 564 Fall 2007 Security and Privacy on the Internet - Dr. A. K. Aggarwal
Hosts Installations and Configuration of Victim Machine Configuring Outlook Express email client 26 564 Fall 2007 Security and Privacy on the Internet - Dr. A. K. Aggarwal
 Hosts Installations and Configuration of Victim Machine Configuring Outlook Express email client 27 564 Fall 2007 Security and Privacy on the Internet - Dr. A. K. Aggarwal
Hosts Installations and Configuration of Victim Machine Configuring Outlook Express email client 27 564 Fall 2007 Security and Privacy on the Internet - Dr. A. K. Aggarwal
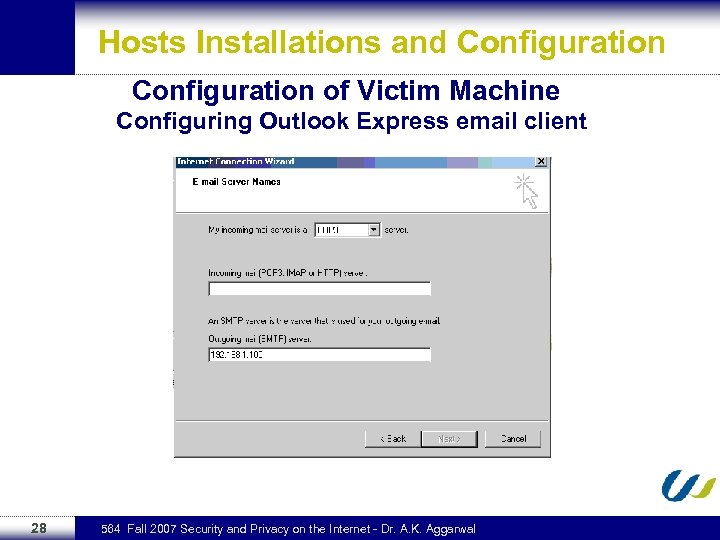 Hosts Installations and Configuration of Victim Machine Configuring Outlook Express email client 28 564 Fall 2007 Security and Privacy on the Internet - Dr. A. K. Aggarwal
Hosts Installations and Configuration of Victim Machine Configuring Outlook Express email client 28 564 Fall 2007 Security and Privacy on the Internet - Dr. A. K. Aggarwal
 Hosts Installations and Configuration of Host Intruder Machine (Laptop) Installing Comm. View for Wi-Fi HP Laptop CPU: Centrino 1. 7 GHz Memory: 512 M Hard Disk: 60 GB Operating System: Windows XP professional IP Address: NO IP ADDRESS Comm. View For Wi-Fi (packet sniffer and generator) 29 564 Fall 2007 Security and Privacy on the Internet - Dr. A. K. Aggarwal
Hosts Installations and Configuration of Host Intruder Machine (Laptop) Installing Comm. View for Wi-Fi HP Laptop CPU: Centrino 1. 7 GHz Memory: 512 M Hard Disk: 60 GB Operating System: Windows XP professional IP Address: NO IP ADDRESS Comm. View For Wi-Fi (packet sniffer and generator) 29 564 Fall 2007 Security and Privacy on the Internet - Dr. A. K. Aggarwal
 Hosts Installations and Configuration of Host Intranet Server Installing IIS, SMTP and FTP Configuring IIS, SMTP, FTP IBM server CPU: Xeon 3. 00 GHz Memory: 256 MB Hard Disk: 80 G Operating System: Windows 2000 Advanced Server (Ser) IP Address: 192. 168. 1. 100 Application: MS-IIS web server, SMTP Relay service, FTP service. Note: For assist limitation: This server is implemented using VMware ver 4. 0. A virtual machine application that runs on top of the installed operating system. I had to use it because the installed OS (windows XP) doesn’t support web services (IIS, SMTP, FTP). 100 Mbps UTP connection to Access point 30 564 Fall 2007 Security and Privacy on the Internet - Dr. A. K. Aggarwal
Hosts Installations and Configuration of Host Intranet Server Installing IIS, SMTP and FTP Configuring IIS, SMTP, FTP IBM server CPU: Xeon 3. 00 GHz Memory: 256 MB Hard Disk: 80 G Operating System: Windows 2000 Advanced Server (Ser) IP Address: 192. 168. 1. 100 Application: MS-IIS web server, SMTP Relay service, FTP service. Note: For assist limitation: This server is implemented using VMware ver 4. 0. A virtual machine application that runs on top of the installed operating system. I had to use it because the installed OS (windows XP) doesn’t support web services (IIS, SMTP, FTP). 100 Mbps UTP connection to Access point 30 564 Fall 2007 Security and Privacy on the Internet - Dr. A. K. Aggarwal
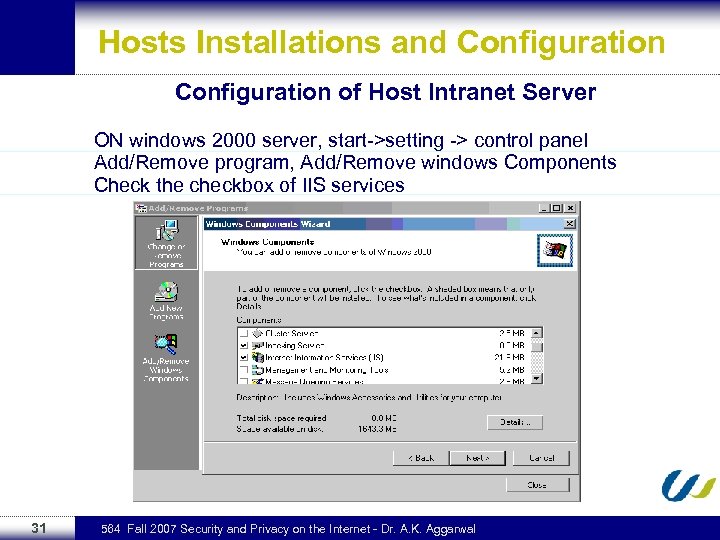 Hosts Installations and Configuration of Host Intranet Server ON windows 2000 server, start->setting -> control panel Add/Remove program, Add/Remove windows Components Check the checkbox of IIS services 31 564 Fall 2007 Security and Privacy on the Internet - Dr. A. K. Aggarwal
Hosts Installations and Configuration of Host Intranet Server ON windows 2000 server, start->setting -> control panel Add/Remove program, Add/Remove windows Components Check the checkbox of IIS services 31 564 Fall 2007 Security and Privacy on the Internet - Dr. A. K. Aggarwal
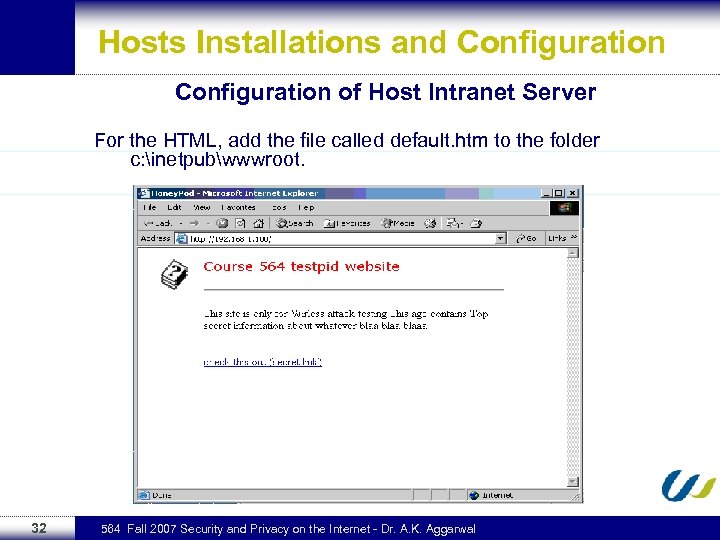 Hosts Installations and Configuration of Host Intranet Server For the HTML, add the file called default. htm to the folder c: inetpubwwwroot. 32 564 Fall 2007 Security and Privacy on the Internet - Dr. A. K. Aggarwal
Hosts Installations and Configuration of Host Intranet Server For the HTML, add the file called default. htm to the folder c: inetpubwwwroot. 32 564 Fall 2007 Security and Privacy on the Internet - Dr. A. K. Aggarwal
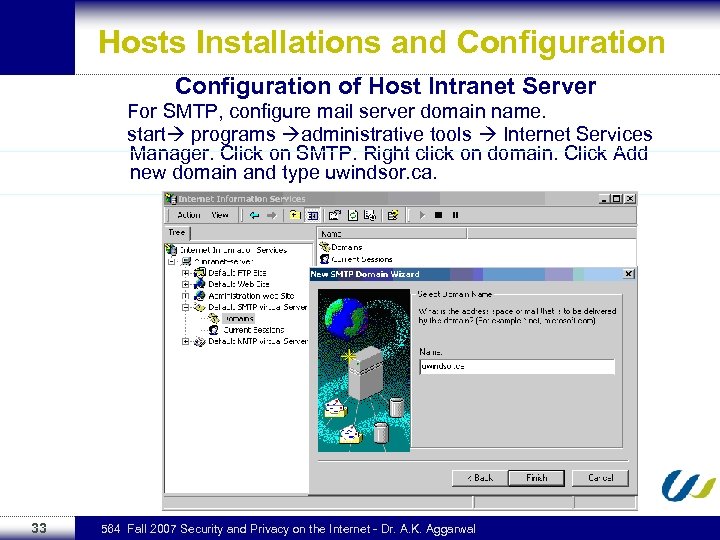 Hosts Installations and Configuration of Host Intranet Server For SMTP, configure mail server domain name. start programs administrative tools Internet Services Manager. Click on SMTP. Right click on domain. Click Add new domain and type uwindsor. ca. 33 564 Fall 2007 Security and Privacy on the Internet - Dr. A. K. Aggarwal
Hosts Installations and Configuration of Host Intranet Server For SMTP, configure mail server domain name. start programs administrative tools Internet Services Manager. Click on SMTP. Right click on domain. Click Add new domain and type uwindsor. ca. 33 564 Fall 2007 Security and Privacy on the Internet - Dr. A. K. Aggarwal
 Hosts Installations and Configuration of Host Intranet Server FTP needs no configuration. Just need to add some file to the ftproot folder. These files will be downloaded by clients. 34 564 Fall 2007 Security and Privacy on the Internet - Dr. A. K. Aggarwal
Hosts Installations and Configuration of Host Intranet Server FTP needs no configuration. Just need to add some file to the ftproot folder. These files will be downloaded by clients. 34 564 Fall 2007 Security and Privacy on the Internet - Dr. A. K. Aggarwal
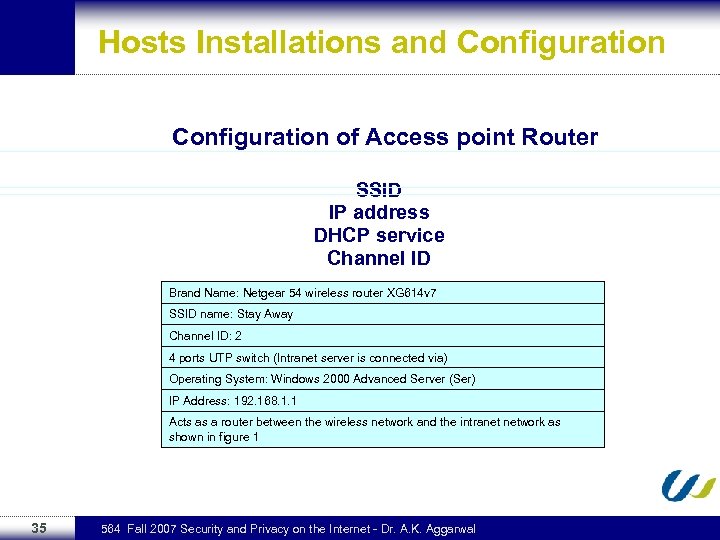 Hosts Installations and Configuration of Access point Router SSID IP address DHCP service Channel ID Brand Name: Netgear 54 wireless router XG 614 v 7 SSID name: Stay Away Channel ID: 2 4 ports UTP switch (Intranet server is connected via) Operating System: Windows 2000 Advanced Server (Ser) IP Address: 192. 168. 1. 1 Acts as a router between the wireless network and the intranet network as shown in figure 1 35 564 Fall 2007 Security and Privacy on the Internet - Dr. A. K. Aggarwal
Hosts Installations and Configuration of Access point Router SSID IP address DHCP service Channel ID Brand Name: Netgear 54 wireless router XG 614 v 7 SSID name: Stay Away Channel ID: 2 4 ports UTP switch (Intranet server is connected via) Operating System: Windows 2000 Advanced Server (Ser) IP Address: 192. 168. 1. 1 Acts as a router between the wireless network and the intranet network as shown in figure 1 35 564 Fall 2007 Security and Privacy on the Internet - Dr. A. K. Aggarwal
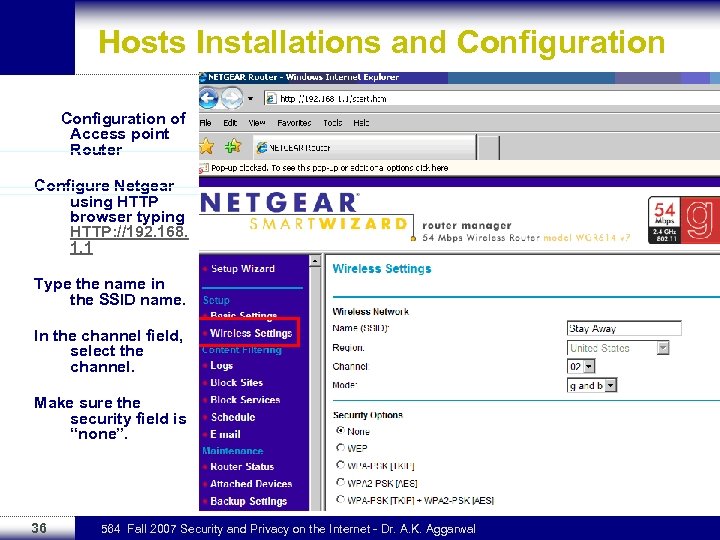 Hosts Installations and Configuration of Access point Router Configure Netgear using HTTP browser typing HTTP: //192. 168. 1. 1 Type the name in the SSID name. In the channel field, select the channel. Make sure the security field is “none”. 36 564 Fall 2007 Security and Privacy on the Internet - Dr. A. K. Aggarwal
Hosts Installations and Configuration of Access point Router Configure Netgear using HTTP browser typing HTTP: //192. 168. 1. 1 Type the name in the SSID name. In the channel field, select the channel. Make sure the security field is “none”. 36 564 Fall 2007 Security and Privacy on the Internet - Dr. A. K. Aggarwal
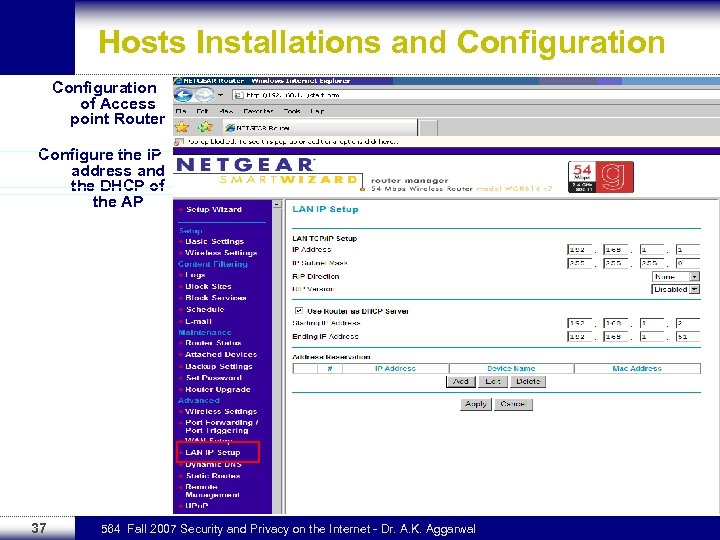 Hosts Installations and Configuration of Access point Router Configure the IP address and the DHCP of the AP 37 564 Fall 2007 Security and Privacy on the Internet - Dr. A. K. Aggarwal
Hosts Installations and Configuration of Access point Router Configure the IP address and the DHCP of the AP 37 564 Fall 2007 Security and Privacy on the Internet - Dr. A. K. Aggarwal
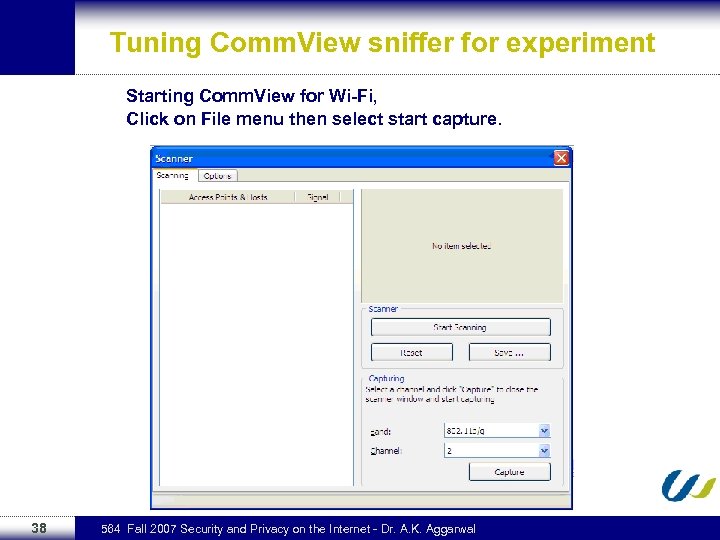 Tuning Comm. View sniffer for experiment Starting Comm. View for Wi-Fi, Click on File menu then select start capture. 38 564 Fall 2007 Security and Privacy on the Internet - Dr. A. K. Aggarwal
Tuning Comm. View sniffer for experiment Starting Comm. View for Wi-Fi, Click on File menu then select start capture. 38 564 Fall 2007 Security and Privacy on the Internet - Dr. A. K. Aggarwal
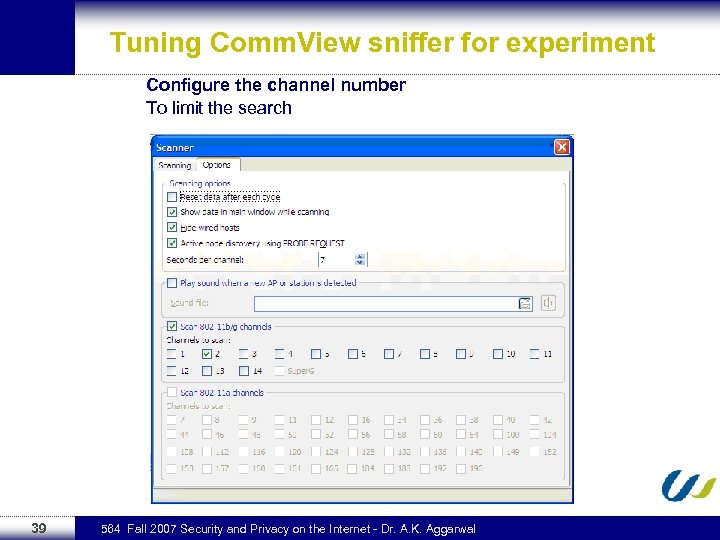 Tuning Comm. View sniffer for experiment Configure the channel number To limit the search 39 564 Fall 2007 Security and Privacy on the Internet - Dr. A. K. Aggarwal
Tuning Comm. View sniffer for experiment Configure the channel number To limit the search 39 564 Fall 2007 Security and Privacy on the Internet - Dr. A. K. Aggarwal
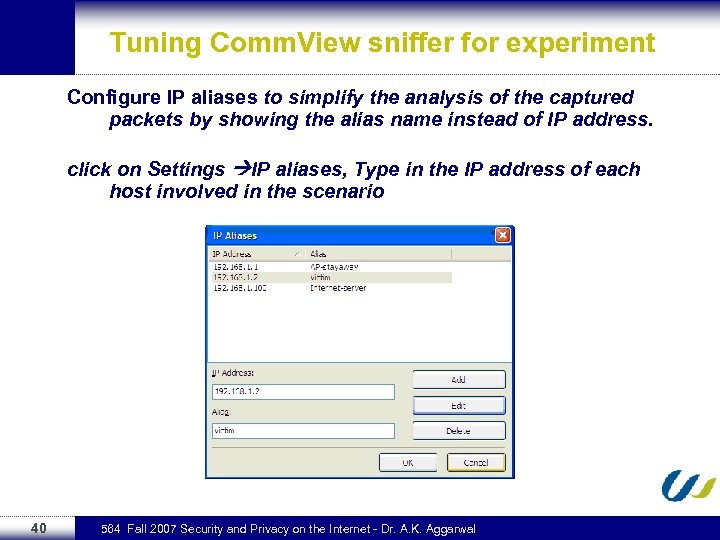 Tuning Comm. View sniffer for experiment Configure IP aliases to simplify the analysis of the captured packets by showing the alias name instead of IP address. click on Settings IP aliases, Type in the IP address of each host involved in the scenario 40 564 Fall 2007 Security and Privacy on the Internet - Dr. A. K. Aggarwal
Tuning Comm. View sniffer for experiment Configure IP aliases to simplify the analysis of the captured packets by showing the alias name instead of IP address. click on Settings IP aliases, Type in the IP address of each host involved in the scenario 40 564 Fall 2007 Security and Privacy on the Internet - Dr. A. K. Aggarwal
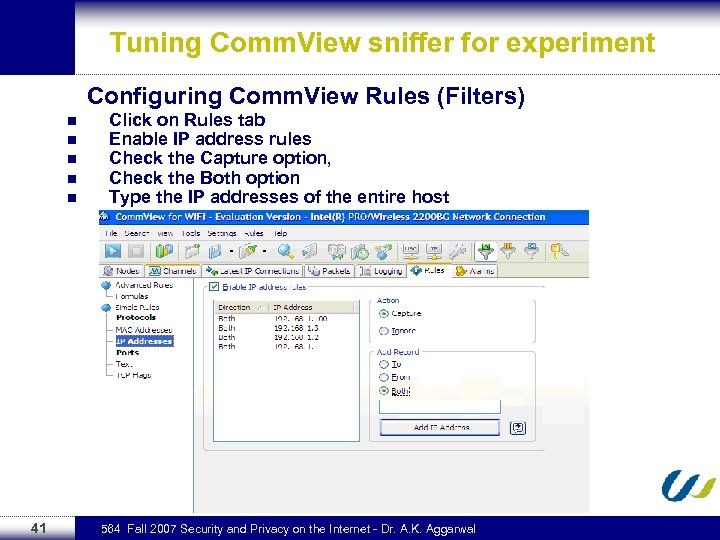 Tuning Comm. View sniffer for experiment Configuring Comm. View Rules (Filters) n n n 41 Click on Rules tab Enable IP address rules Check the Capture option, Check the Both option Type the IP addresses of the entire host 564 Fall 2007 Security and Privacy on the Internet - Dr. A. K. Aggarwal
Tuning Comm. View sniffer for experiment Configuring Comm. View Rules (Filters) n n n 41 Click on Rules tab Enable IP address rules Check the Capture option, Check the Both option Type the IP addresses of the entire host 564 Fall 2007 Security and Privacy on the Internet - Dr. A. K. Aggarwal
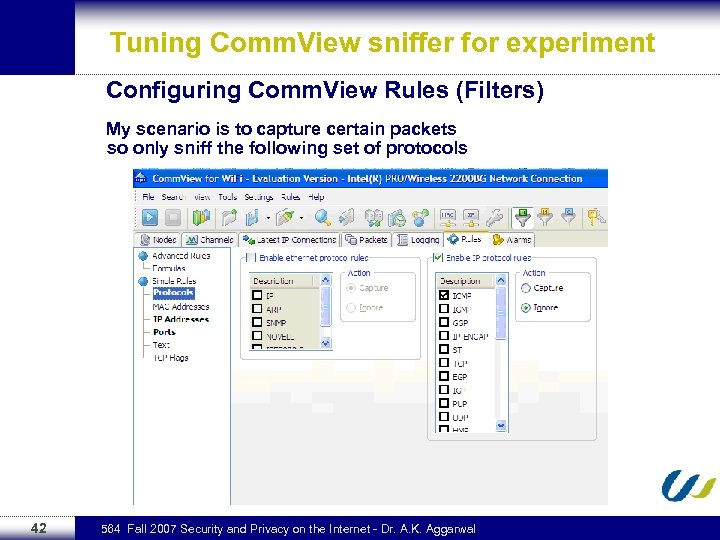 Tuning Comm. View sniffer for experiment Configuring Comm. View Rules (Filters) My scenario is to capture certain packets so only sniff the following set of protocols 42 564 Fall 2007 Security and Privacy on the Internet - Dr. A. K. Aggarwal
Tuning Comm. View sniffer for experiment Configuring Comm. View Rules (Filters) My scenario is to capture certain packets so only sniff the following set of protocols 42 564 Fall 2007 Security and Privacy on the Internet - Dr. A. K. Aggarwal
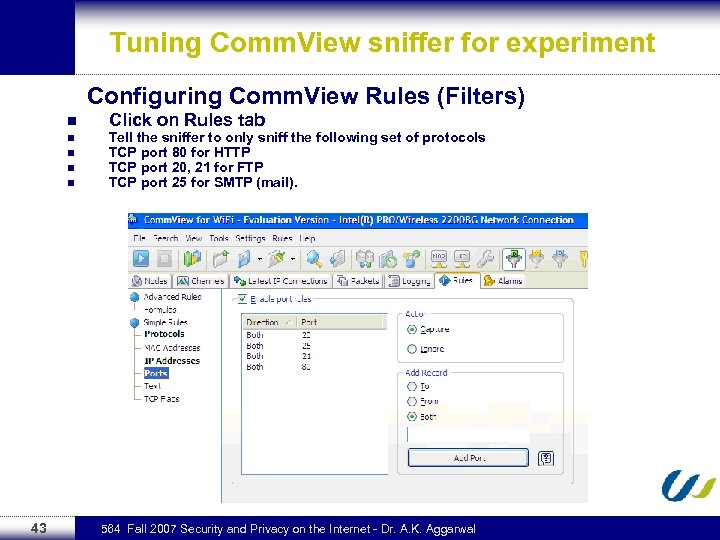 Tuning Comm. View sniffer for experiment Configuring Comm. View Rules (Filters) n n n 43 Click on Rules tab Tell the sniffer to only sniff the following set of protocols TCP port 80 for HTTP TCP port 20, 21 for FTP TCP port 25 for SMTP (mail). 564 Fall 2007 Security and Privacy on the Internet - Dr. A. K. Aggarwal
Tuning Comm. View sniffer for experiment Configuring Comm. View Rules (Filters) n n n 43 Click on Rules tab Tell the sniffer to only sniff the following set of protocols TCP port 80 for HTTP TCP port 20, 21 for FTP TCP port 25 for SMTP (mail). 564 Fall 2007 Security and Privacy on the Internet - Dr. A. K. Aggarwal
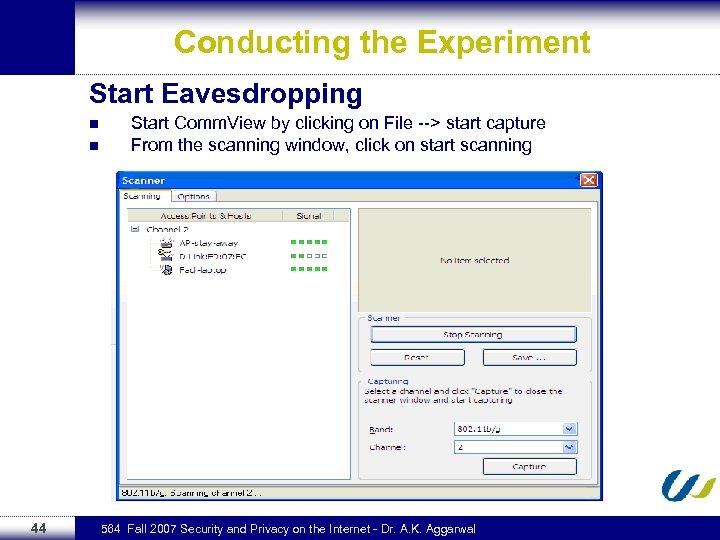 Conducting the Experiment Start Eavesdropping n n 44 Start Comm. View by clicking on File --> start capture From the scanning window, click on start scanning 564 Fall 2007 Security and Privacy on the Internet - Dr. A. K. Aggarwal
Conducting the Experiment Start Eavesdropping n n 44 Start Comm. View by clicking on File --> start capture From the scanning window, click on start scanning 564 Fall 2007 Security and Privacy on the Internet - Dr. A. K. Aggarwal
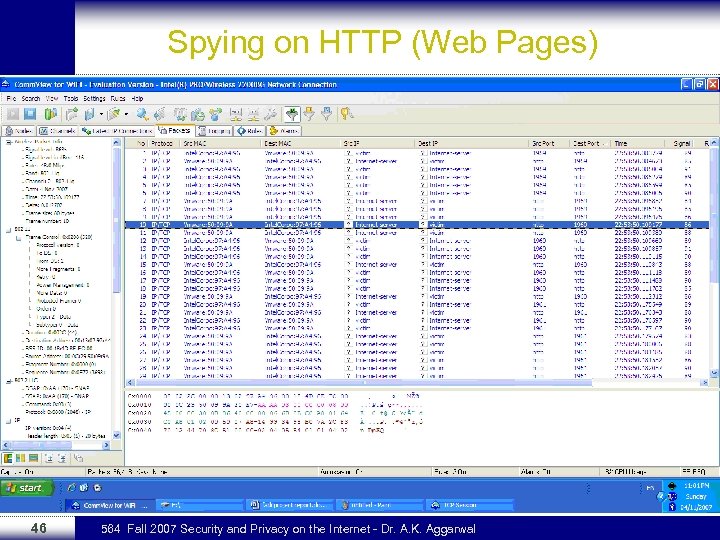
 Conducting the Experiment Spying on HTTP (Web Pages) n n n 45 In this attack the intruder will spy on the victim http traffic. The Victim is accessing a web server and reading a specific important confidential page from his corporate web server. The victim will type in the web browser the website name (here it is an IP address 192. 168. 1. 100) After performing the previous step, Comm. View packet tab shows that there are 45 packets has been captured. 564 Fall 2007 Security and Privacy on the Internet - Dr. A. K. Aggarwal
Conducting the Experiment Spying on HTTP (Web Pages) n n n 45 In this attack the intruder will spy on the victim http traffic. The Victim is accessing a web server and reading a specific important confidential page from his corporate web server. The victim will type in the web browser the website name (here it is an IP address 192. 168. 1. 100) After performing the previous step, Comm. View packet tab shows that there are 45 packets has been captured. 564 Fall 2007 Security and Privacy on the Internet - Dr. A. K. Aggarwal
 Spying on HTTP (Web Pages) 46 564 Fall 2007 Security and Privacy on the Internet - Dr. A. K. Aggarwal
Spying on HTTP (Web Pages) 46 564 Fall 2007 Security and Privacy on the Internet - Dr. A. K. Aggarwal
 Spying on HTTP (Web Pages) To make it easier for the intruder to actually see what the victim was watching the intruder can reconstruct the HTTP session and view it as a web page with some format limitation. To do this the intruder can simply right click on any HTTP packets and select “Reconstruct TCP session. 47 564 Fall 2007 Security and Privacy on the Internet - Dr. A. K. Aggarwal
Spying on HTTP (Web Pages) To make it easier for the intruder to actually see what the victim was watching the intruder can reconstruct the HTTP session and view it as a web page with some format limitation. To do this the intruder can simply right click on any HTTP packets and select “Reconstruct TCP session. 47 564 Fall 2007 Security and Privacy on the Internet - Dr. A. K. Aggarwal
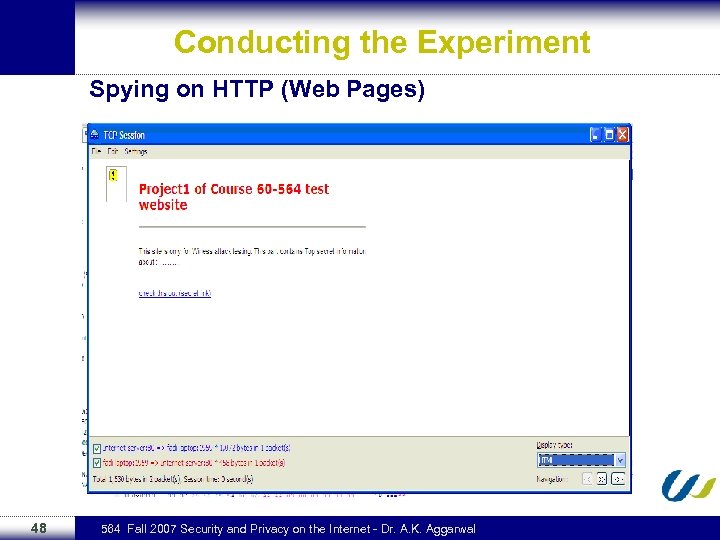 Conducting the Experiment Spying on HTTP (Web Pages) 48 564 Fall 2007 Security and Privacy on the Internet - Dr. A. K. Aggarwal
Conducting the Experiment Spying on HTTP (Web Pages) 48 564 Fall 2007 Security and Privacy on the Internet - Dr. A. K. Aggarwal
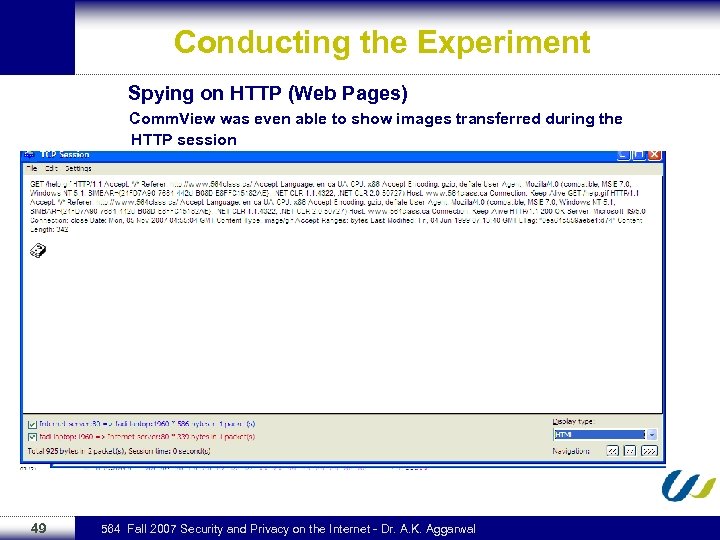 Conducting the Experiment Spying on HTTP (Web Pages) Comm. View was even able to show images transferred during the HTTP session 49 564 Fall 2007 Security and Privacy on the Internet - Dr. A. K. Aggarwal
Conducting the Experiment Spying on HTTP (Web Pages) Comm. View was even able to show images transferred during the HTTP session 49 564 Fall 2007 Security and Privacy on the Internet - Dr. A. K. Aggarwal
 Conducting the Experiment Spying on FTP (Downloading files) n n 50 The victim will connect to an FTP server to download an important confidential file. The victim will do the following steps From command prompt victim will connect to the ftp server entering administrator account and password and then downloading a configuration file called rules. txt 564 Fall 2007 Security and Privacy on the Internet - Dr. A. K. Aggarwal
Conducting the Experiment Spying on FTP (Downloading files) n n 50 The victim will connect to an FTP server to download an important confidential file. The victim will do the following steps From command prompt victim will connect to the ftp server entering administrator account and password and then downloading a configuration file called rules. txt 564 Fall 2007 Security and Privacy on the Internet - Dr. A. K. Aggarwal
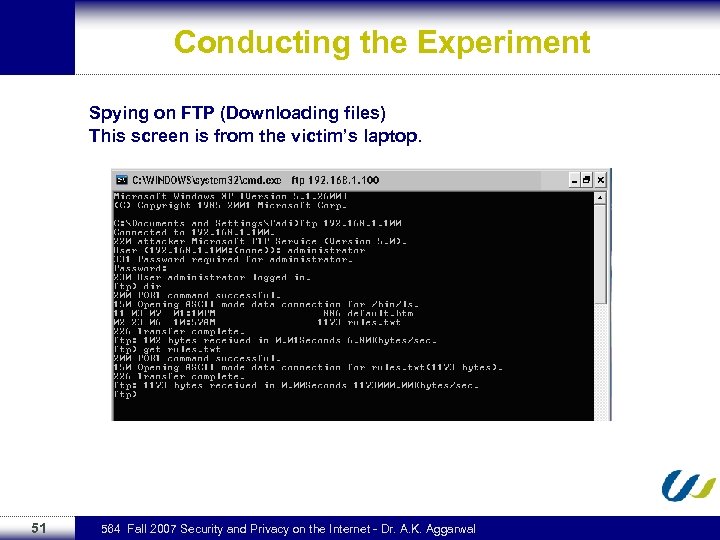 Conducting the Experiment Spying on FTP (Downloading files) This screen is from the victim’s laptop. 51 564 Fall 2007 Security and Privacy on the Internet - Dr. A. K. Aggarwal
Conducting the Experiment Spying on FTP (Downloading files) This screen is from the victim’s laptop. 51 564 Fall 2007 Security and Privacy on the Internet - Dr. A. K. Aggarwal
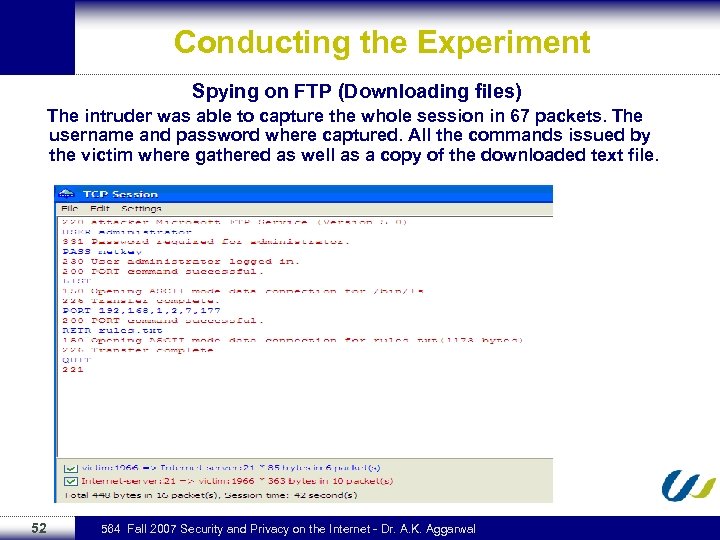 Conducting the Experiment Spying on FTP (Downloading files) The intruder was able to capture the whole session in 67 packets. The username and password where captured. All the commands issued by the victim where gathered as well as a copy of the downloaded text file. 52 564 Fall 2007 Security and Privacy on the Internet - Dr. A. K. Aggarwal
Conducting the Experiment Spying on FTP (Downloading files) The intruder was able to capture the whole session in 67 packets. The username and password where captured. All the commands issued by the victim where gathered as well as a copy of the downloaded text file. 52 564 Fall 2007 Security and Privacy on the Internet - Dr. A. K. Aggarwal
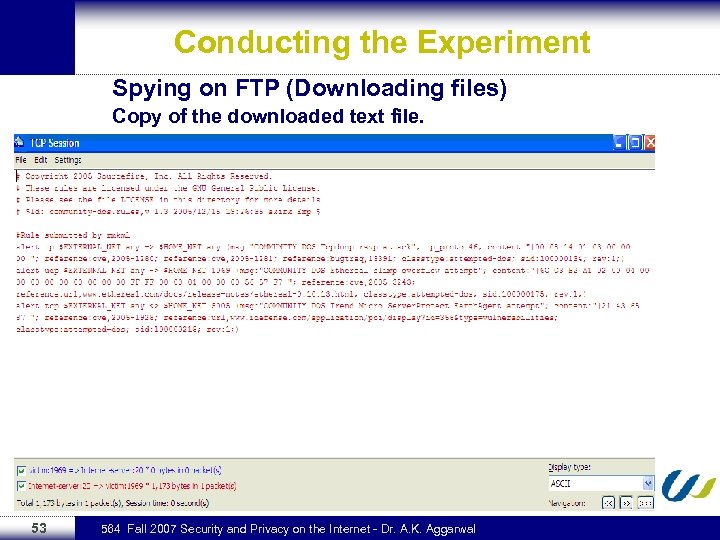 Conducting the Experiment Spying on FTP (Downloading files) Copy of the downloaded text file. 53 564 Fall 2007 Security and Privacy on the Internet - Dr. A. K. Aggarwal
Conducting the Experiment Spying on FTP (Downloading files) Copy of the downloaded text file. 53 564 Fall 2007 Security and Privacy on the Internet - Dr. A. K. Aggarwal
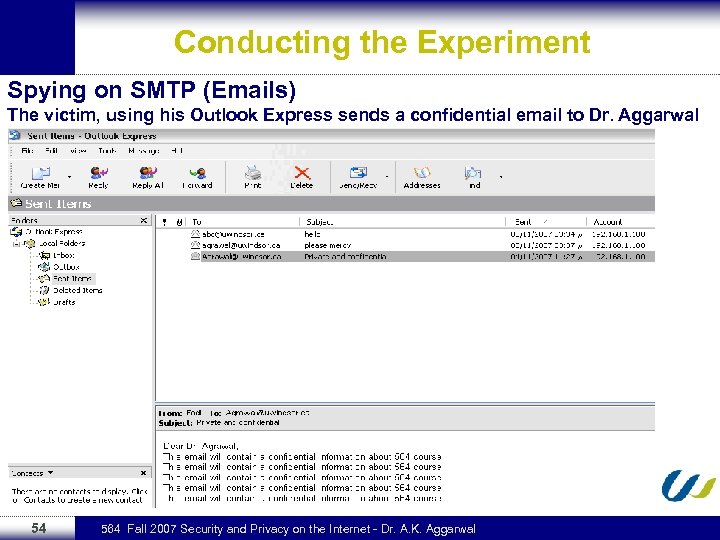 Conducting the Experiment Spying on SMTP (Emails) The victim, using his Outlook Express sends a confidential email to Dr. Aggarwal 54 564 Fall 2007 Security and Privacy on the Internet - Dr. A. K. Aggarwal
Conducting the Experiment Spying on SMTP (Emails) The victim, using his Outlook Express sends a confidential email to Dr. Aggarwal 54 564 Fall 2007 Security and Privacy on the Internet - Dr. A. K. Aggarwal
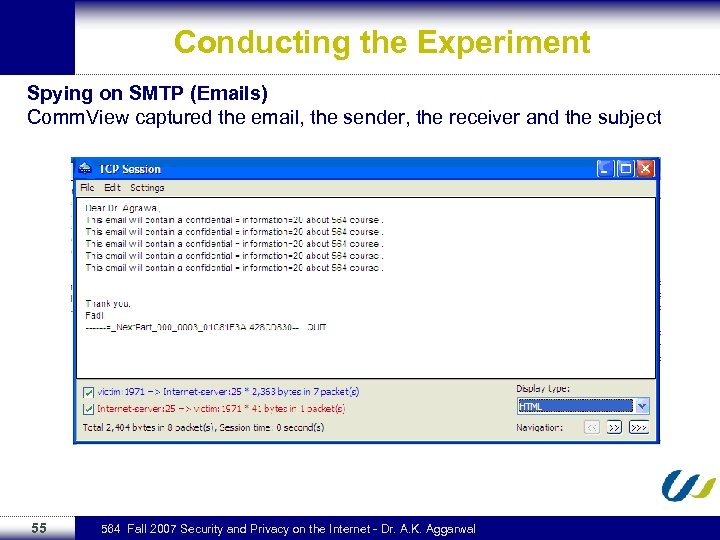 Conducting the Experiment Spying on SMTP (Emails) Comm. View captured the email, the sender, the receiver and the subject 55 564 Fall 2007 Security and Privacy on the Internet - Dr. A. K. Aggarwal
Conducting the Experiment Spying on SMTP (Emails) Comm. View captured the email, the sender, the receiver and the subject 55 564 Fall 2007 Security and Privacy on the Internet - Dr. A. K. Aggarwal
 Conducting the Experiment • This whole experiment was happened over a non secure network. • I conducted the same detailed experiment but over a secure network using WEP security and the results were the same as over a non secure network. • But when I conducted the same experiment over a secure network using WPA security, the laptop using sniffer couldn't even connect to the network. 56 564 Fall 2007 Security and Privacy on the Internet - Dr. A. K. Aggarwal
Conducting the Experiment • This whole experiment was happened over a non secure network. • I conducted the same detailed experiment but over a secure network using WEP security and the results were the same as over a non secure network. • But when I conducted the same experiment over a secure network using WPA security, the laptop using sniffer couldn't even connect to the network. 56 564 Fall 2007 Security and Privacy on the Internet - Dr. A. K. Aggarwal
 IDS Promisacn 3. 0 The intrusion detection system that can detect the Promiscuous sniffing nodes (Eavesdropping) is called Promi. Scan. But due to its high price 500$ I couldn’t used it. The free trial version of that software has many limitations (Special IP address range) and I actually spend more than 10 hours trying it but without any results. 57 564 Fall 2007 Security and Privacy on the Internet - Dr. A. K. Aggarwal
IDS Promisacn 3. 0 The intrusion detection system that can detect the Promiscuous sniffing nodes (Eavesdropping) is called Promi. Scan. But due to its high price 500$ I couldn’t used it. The free trial version of that software has many limitations (Special IP address range) and I actually spend more than 10 hours trying it but without any results. 57 564 Fall 2007 Security and Privacy on the Internet - Dr. A. K. Aggarwal
![References n n n 58 [1] M. Domenico, A. Calandriello, G. Calandriello and A. References n n n 58 [1] M. Domenico, A. Calandriello, G. Calandriello and A.](https://present5.com/presentation/6f2233e6c3bb91cb4dd4f1c4508d3381/image-58.jpg) References n n n 58 [1] M. Domenico, A. Calandriello, G. Calandriello and A. Lioy. Dependability in Wireless Networks: Can We Rely on Wi. Fi? . IEEE Security and Privacy, 5(1): 23 -29, 2007 [2] www. london-wifi. com [3] www. wlantenna. com/wlantenna. htm [4] http: //www. tscmvideo. com/eavesdropping-device. html [5] Lucid. Link, the network security products company, Wi. Fi. Theft. com, wifi. weblogsinc. com, War. Driving. com, Wigle. net, www. intelligentedu. com [6] Wikipedia encyclopedia. Eavesdropping on Wi-Fi, chapter 6 page 122 [7] http: //www. sciam. com/article. cfm [8] A. Nicholson and B. Noble. Automatic Network Management for Mobile Devices. In Proc. Seventh IEEE Workshop on Mobile Computing Systems & Applications, IEEE Computer Society, pages 47– 47, 2006. [9] Eavesdropping on Wi-Fi, chapter 6 page 122 [10] The experiment Scenario figure, Eavesdropping project. [11] www. securityfriday. com/products/promiscan. html 564 Fall 2007 Security and Privacy on the Internet - Dr. A. K. Aggarwal
References n n n 58 [1] M. Domenico, A. Calandriello, G. Calandriello and A. Lioy. Dependability in Wireless Networks: Can We Rely on Wi. Fi? . IEEE Security and Privacy, 5(1): 23 -29, 2007 [2] www. london-wifi. com [3] www. wlantenna. com/wlantenna. htm [4] http: //www. tscmvideo. com/eavesdropping-device. html [5] Lucid. Link, the network security products company, Wi. Fi. Theft. com, wifi. weblogsinc. com, War. Driving. com, Wigle. net, www. intelligentedu. com [6] Wikipedia encyclopedia. Eavesdropping on Wi-Fi, chapter 6 page 122 [7] http: //www. sciam. com/article. cfm [8] A. Nicholson and B. Noble. Automatic Network Management for Mobile Devices. In Proc. Seventh IEEE Workshop on Mobile Computing Systems & Applications, IEEE Computer Society, pages 47– 47, 2006. [9] Eavesdropping on Wi-Fi, chapter 6 page 122 [10] The experiment Scenario figure, Eavesdropping project. [11] www. securityfriday. com/products/promiscan. html 564 Fall 2007 Security and Privacy on the Internet - Dr. A. K. Aggarwal
 Questions in the lab 59 564 Fall 2007 Security and Privacy on the Internet - Dr. A. K. Aggarwal
Questions in the lab 59 564 Fall 2007 Security and Privacy on the Internet - Dr. A. K. Aggarwal


