ce0105723c0ca9060ddca906a34a7745.ppt
- Количество слайдов: 146

e-Services 64157 電子商務模式設計與應用 國立中山大學企管所 2002 Spring, Week 8 -2 太世科網路行銷公司 TASKCO Corporation Info@taskco. com 886 -2 -8772 -2583 黃光彩 博士 太世科公司 2002/05/18 1 CONFIDENTIAL
Example of e-Services in IT Many different network services provided to many different clients • Routing and Transport (OSPF, RIP, TCP, SCCP) • Qo. S (Intserv, Diffser) • Naming (DNS, Enum, X. 500) • Security (Diameter, Kerberos) • Informational (Yahoo, CNN) • E-mail (RFC 822 & MIME, X. 400) • Internet Phone (Megaco, SIP) • Single Sign on 2 CONFIDENTIAL
Services Evolve If market uncertainty exists services must evolve in random ways with the market being the selection mechanism • many ideas for different services • many ways to provide a particular service As the service providers learn and user expectations evolve market uncertainty may decreases, thus lowering the value of many experiments • When market uncertainty is low centralized managed services may become more attractive. 3 CONFIDENTIAL

Service Location Definitions Where the management of the service is Some services are more internal to the network • Internal - inside the core network – Routing, Qo. S - Diff-serv Vs Int-serv • Middle-ware/Core - helping to provide a service – DNS, caching, security certificates, Hotmail e-2 -e service no application specific knowledge e-2 -e services tend to promote innovation • Anybody can do it • Napster (free music download) • SIP phones (easy to experiment with) 4 CONFIDENTIAL
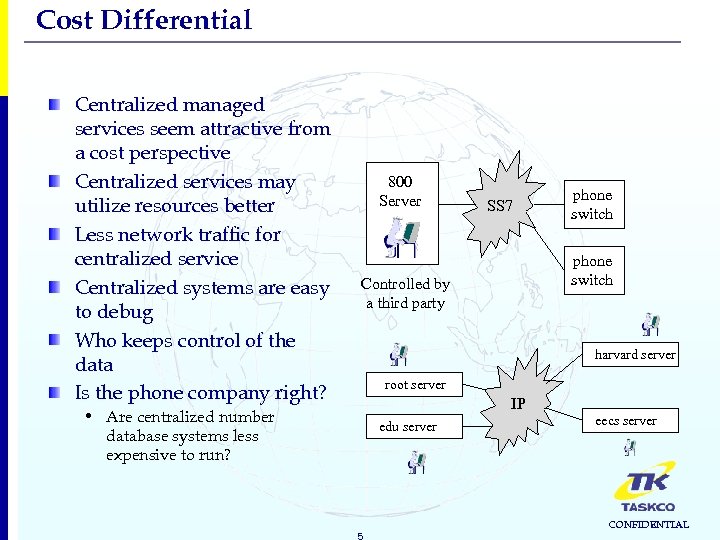
Cost Differential Centralized managed services seem attractive from a cost perspective Centralized services may utilize resources better Less network traffic for centralized service Centralized systems are easy to debug Who keeps control of the data Is the phone company right? 800 Server SS 7 phone switch Controlled by a third party harvard server root server IP • Are centralized number database systems less expensive to run? edu server 5 eecs server CONFIDENTIAL
What Pulls a Service to the Edges? Sometimes its “better” to do it at the ends (e-2 -e error checking Vs hop-by-hop) Parallel experimentation • easy to do many experiments at the ends • easy to do many “small” tests • experiments are less disruptive Market Uncertainty • Customer and vendors don’t know what is best Greater market uncertainty => greater value of more experiments 6 CONFIDENTIAL

Market Uncertainty With new Services customers don’t know what they want With new technologies customers’ expectations evolve with the technology • At first, new services are viewed in the context of older services Providing new services is like rolling the dice • Sometimes you win, sometimes not 7 CONFIDENTIAL
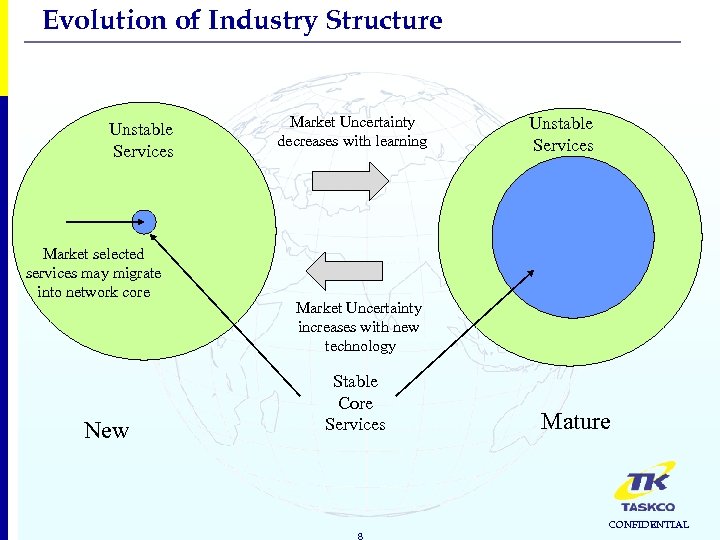
Evolution of Industry Structure Unstable Services Market selected services may migrate into network core New Market Uncertainty decreases with learning Unstable Services Market Uncertainty increases with new technology Stable Core Services 8 Mature CONFIDENTIAL

Phone Vs Internet Phone network started out with a smart network and dumb phones • PBX’s and more intelligent phones have changed this, now more intelligence at the edges Internet started out with smart ends and a dumb network • More intelligence inside the network – Qo. S, middle-ware Both networks are converging on a environment allowing easy non-disruptive experimentation 9 CONFIDENTIAL
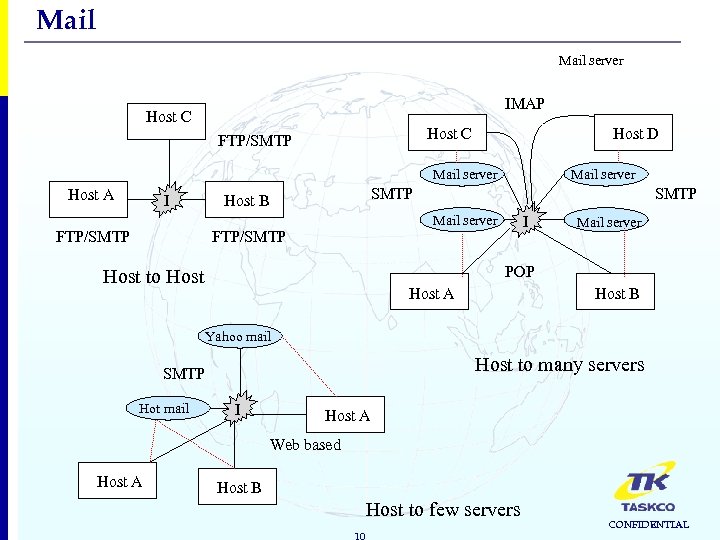
Mail server IMAP Host C FTP/SMTP Host D Mail server Host A I Mail server SMTP Host B SMTP Mail server FTP/SMTP I FTP/SMTP Mail server POP Host to Host A Host B Yahoo mail Host to many servers SMTP Hot mail I Host A Web based Host A Host B Host to few servers 10 CONFIDENTIAL
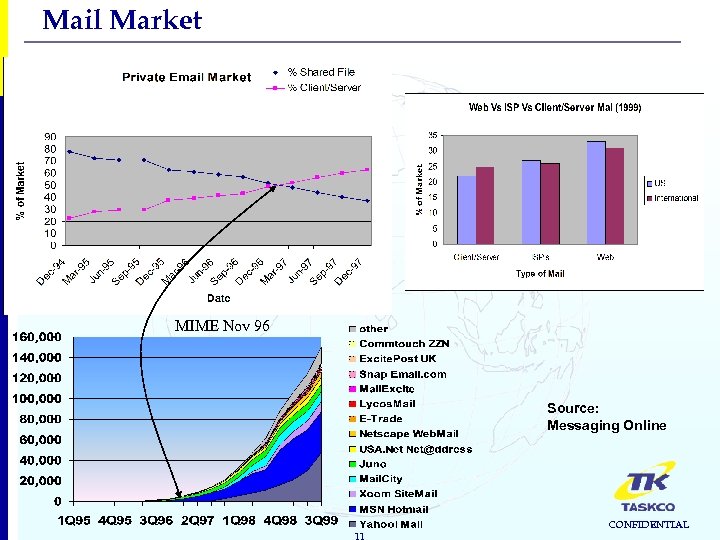
Mail Market MIME Nov 96 Source: Messaging Online 11 CONFIDENTIAL

Security Authentication Authorisation Accounting ARCHitecture 12 CONFIDENTIAL
Next Generation of AAA 3 of 14 Authorization subgroup of AAA-WG • This RG will work to define a next generation AAA architecture that incorporates a set of interconnected "generic" AAA servers and an application interface that allows Application Specific Modules access to AAA functions. 13 CONFIDENTIAL

Focus 4 of 14 The architecture's focus is to support AAA services that: • can inter-operate across organizational boundaries • are extensible yet common across a wide variety of Internet services • enables a concept of an AAA transaction spanning many stakeholders • provides application independent session management mechanisms • contains strong security mechanisms that be tuned to local policies • is a scalable to the size of the global Internet 14 CONFIDENTIAL

Basic AAA 5 of 14 Service perspective: • Who is it who wants to use my resource – Establish security context • Do I allow him to access my resource – Create a capability / ticket /authorization • Can I track the usage of the resource – Based on type of request (policy) track the usage User perspective • Where do I find this or that service • What am I allowed to do • What do I need to do to get authorization • What does it cost Intermediaries perspective • Service creation • Brokerage / portals Organizational perspective • What do I allow my people to do • Contractual relationships (SLA’s) 15 CONFIDENTIAL

Applications • • • 6 of 14 Web access Network Access Bandwidth Broker, VLL service Authorization of usage of combination of resources living in many administrative domains Computing grids, data grids, HEP community Budget system Library system Tele-learning E-Commerce Micro-payments 16 CONFIDENTIAL
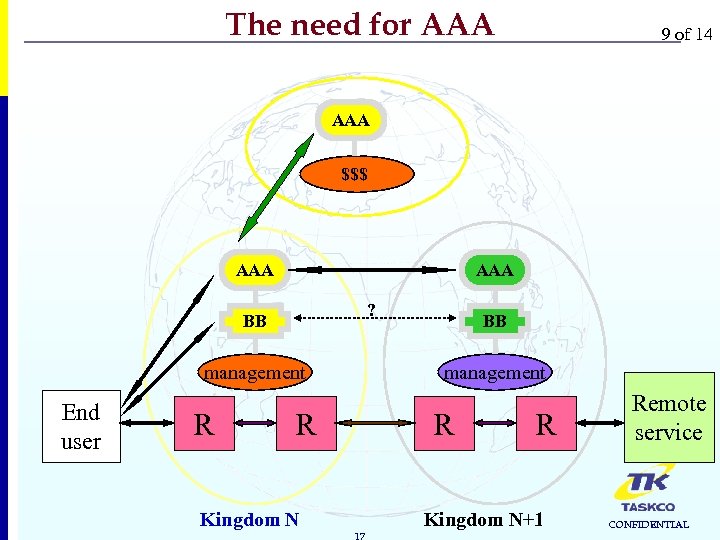
The need for AAA 9 of 14 AAA $$$ AAA ? BB management End user R management R Kingdom N BB R 17 R Kingdom N+1 Remote service CONFIDENTIAL
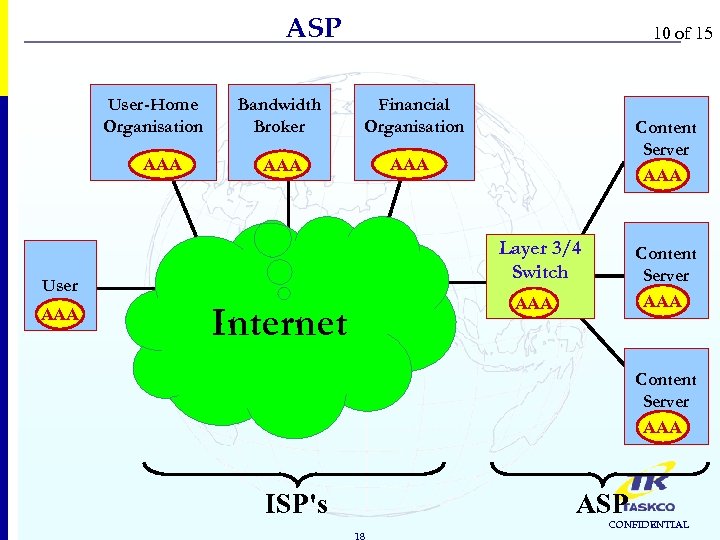
ASP User-Home Organisation AAA 10 of 15 Bandwidth Broker Financial Organisation AAA Layer 3/4 Switch User AAA Content Server AAA Internet Content Server AAA ISP's ASP 18 CONFIDENTIAL
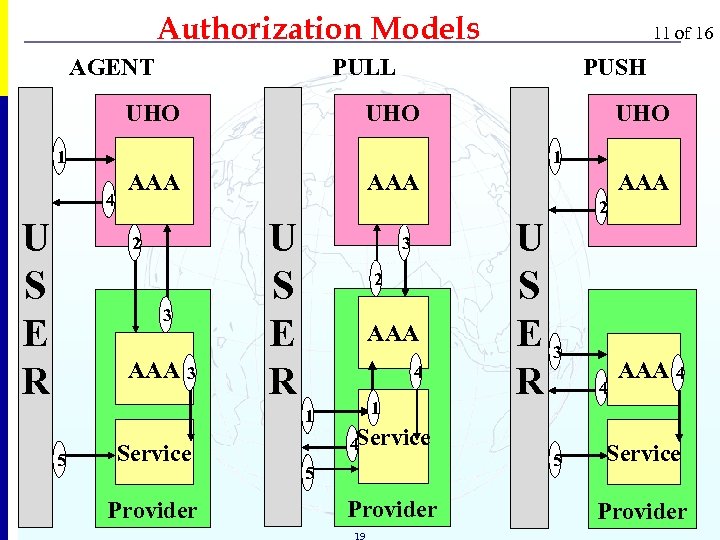
Authorization Models AGENT PULL PUSH UHO 1 AAA 2 3 AAA 3 U S E R 3 2 AAA 4 1 5 UHO 1 4 U S E R 11 of 16 Service Provider 1 4 Service 5 Provider 19 AAA U S E 3 R 5 2 4 AAA 4 Service Provider CONFIDENTIAL
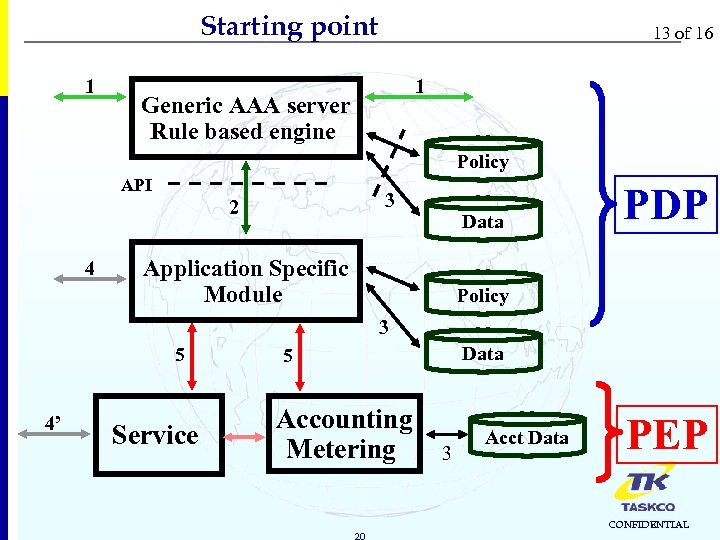
Starting point 1 13 of 16 1 Generic AAA server Rule based engine Policy API 3 2 4 Data Application Specific Module PDP Policy 3 5 4’ Service Data 5 Accounting Metering 20 3 Acct Data PEP CONFIDENTIAL
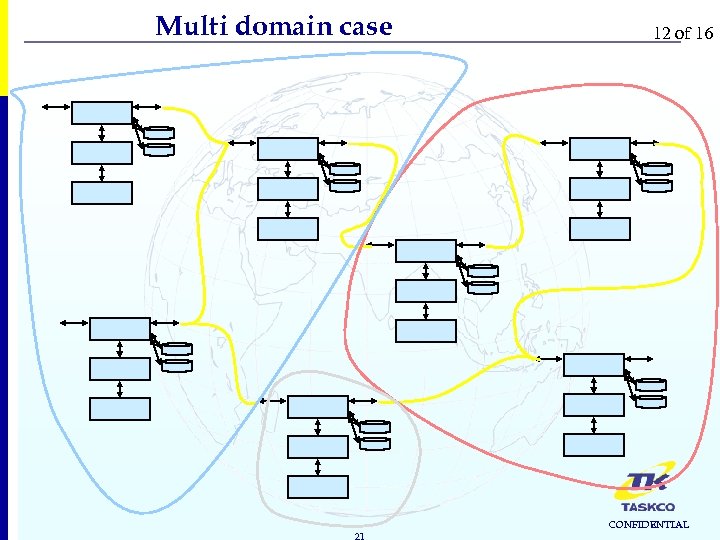
Multi domain case 21 12 of 16 CONFIDENTIAL
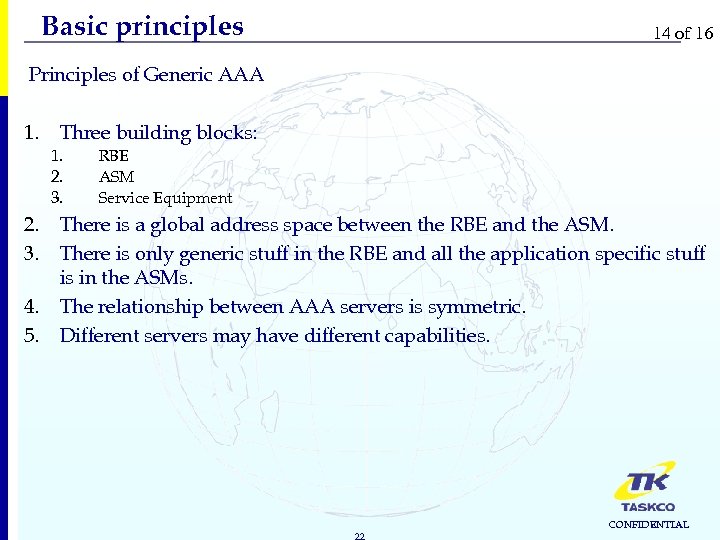
Basic principles 14 of 16 Principles of Generic AAA 1. Three building blocks: 1. 2. 3. 4. 5. RBE ASM Service Equipment There is a global address space between the RBE and the ASM. There is only generic stuff in the RBE and all the application specific stuff is in the ASMs. The relationship between AAA servers is symmetric. Different servers may have different capabilities. 22 CONFIDENTIAL

Message types 15 a of 16 Service request/reply Authorization request/reply Solicit Service Offer request/reply Authentication Challenge request/reply Policy Evaluation request/reply Data request/reply Event Log indication/confirmation Accounting indication/confirmation Service (session) Configuration indication/confirmation Service (session) Management indication/confirmation Capability request/reply (supports resource discovery) 23 CONFIDENTIAL

Top Level Objects 15 b of 16 Identity Authentication Data Authentication Challenge Service Data Service Offer Answer Error Policy • [service specification policy, authorization policy, provisioning policy, configuration policy, accounting policy, metering policy] Policy Reference Policy Data Configuration Data Service Management Accounting Event 24 CONFIDENTIAL
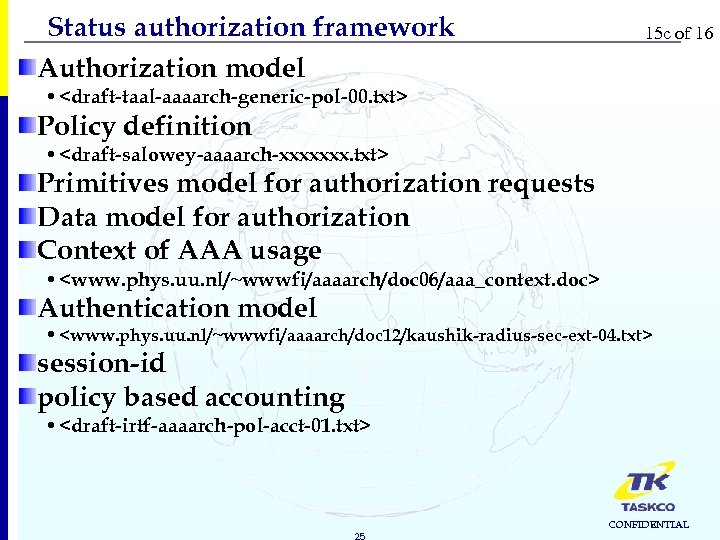
Status authorization framework Authorization model 15 c of 16 • <draft-taal-aaaarch-generic-pol-00. txt> Policy definition • <draft-salowey-aaaarch-xxxxxxx. txt> Primitives model for authorization requests Data model for authorization Context of AAA usage • <www. phys. uu. nl/~wwwfi/aaaarch/doc 06/aaa_context. doc> Authentication model • <www. phys. uu. nl/~wwwfi/aaaarch/doc 12/kaushik-radius-sec-ext-04. txt> session-id policy based accounting • <draft-irtf-aaaarch-pol-acct-01. txt> 25 CONFIDENTIAL
Status-2 15 d of 16 relation to other groups: • AAA --> DATA model • Policy Framework • SLS BOF • GAAAPI (Generic Authorization and Access control API) • GSSAPI (Generic Security Services API) • RAP (BB) • SIP <session initiation protocol> • Computing/data grids < www. gridforum. org/> • Middleware 26 CONFIDENTIAL
Future work 15 e of 16 develop audibility framework specification that allows the AAA system functions to be checked in a multi-organization environment develop a model that supports management of a "mesh" of interconnected AAA Servers implement a simulation model that allows experimentation with the proposed architectural models (UU) describe inter-domain issues using generic model Future issues: • AAA-WG-actions • unresolved topics • (protocol) work for WG's • future AAAARCH work complete the work in Q 1 - 2001 (ambitious) 27 CONFIDENTIAL

E-Service Paradigm E-Services as a new IT service paradigm E-Service quality Relationship Marketing Relationship marketing and e-service support E-Service software support 28 CONFIDENTIAL

The shift to an online economy directly exposes our IT infrastructure to customers. To maintain our competitive advantage, we must ensure the best possible experience for customers and business partners by keeping our Internet banking services available and performing well 24 x 7. " Susan Blew, senior vice president of Enterprise Infrastructure Services at Wells Fargo Bank 29 CONFIDENTIAL

User to Audiences Development to Production Implementation to Publication 30 CONFIDENTIAL
Service Issues Availability Performance Security Loyalty 31 CONFIDENTIAL

User Behavior by Gartner Group From the time an end user lands on a website • They’ll wait an average of just 20 seconds to see something on the page • you have a maximum of 40 seconds to complete the home page display • within 6 seconds the customer has decided to stay or leave the site • the customer will use a maximum of 6 mouse clicks to find the desired information • the maximum amount of time spent on a site is, on average, 12 minutes 32 CONFIDENTIAL

Jupiter Communications Approximately 50% of Web sites surveyed took five or more days to respond, never responded or failed to post an e-mail address on their Web site for customer requests. 33 CONFIDENTIAL

Service Quality Issues Tangibles • Is the E-service website high quality and easy to use? • Does it reward the user sufficiently to promote repeat visits? • Is it visually appealing and complete? Reliability • How do we differentiate between signal and noise? • How do we evaluate the website? • How do we ensure its security? Responsiveness • How do we assure a rapid response time and reply to user communications in an order that reflects their priority. • How do we deal with the large information / communication volume? Assurance • How do we control customer expectations concerning, for example, speed and veracity? Empathy • How do we identify the stage of each customer relationship and respond appropriately? • How do we assure trust and commitment? 34 CONFIDENTIAL
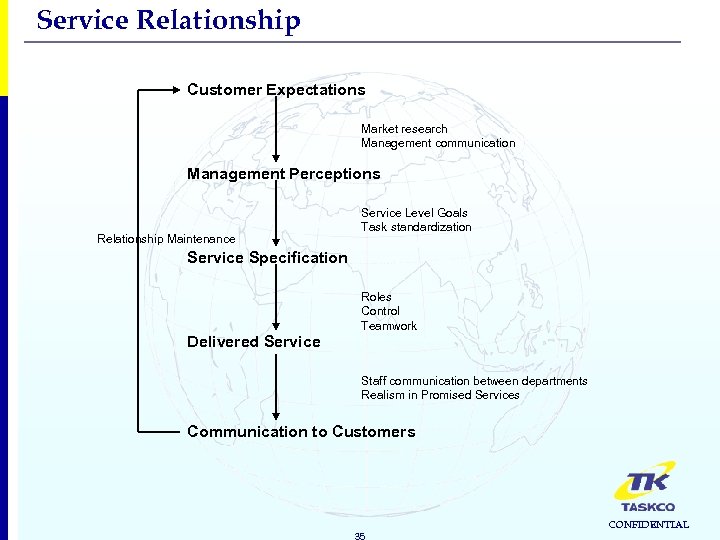
Service Relationship Customer Expectations Market research Management communication Management Perceptions Relationship Maintenance Service Level Goals Task standardization Service Specification Roles Control Teamwork Delivered Service Staff communication between departments Realism in Promised Services Communication to Customers 35 CONFIDENTIAL

Service Quality Attributes • Responsiveness Operationalized Indicators • Response time to e-mail enquiry Standards • Response with 15 minutes Performance Targets • 80% of all e-mails responded to in 30 minutes 36 CONFIDENTIAL
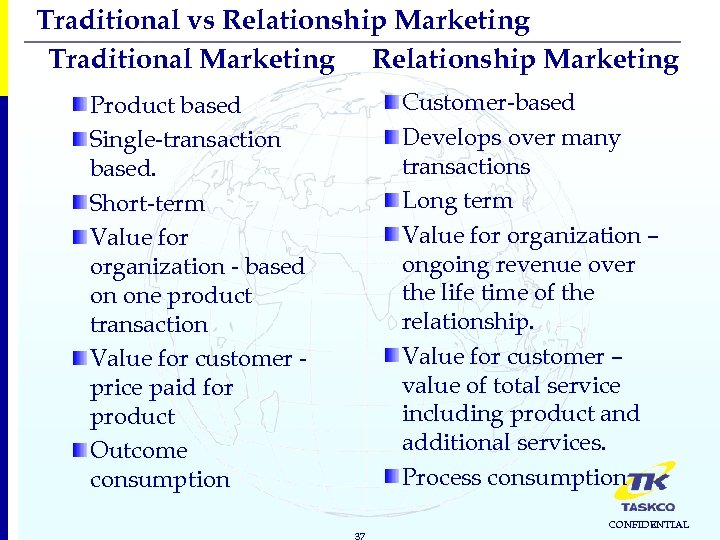
Traditional vs Relationship Marketing Traditional Marketing Relationship Marketing Customer-based Develops over many transactions Long term Value for organization – ongoing revenue over the life time of the relationship. Value for customer – value of total service including product and additional services. Process consumption Product based Single-transaction based. Short-term Value for organization - based on one product transaction Value for customer price paid for product Outcome consumption 37 CONFIDENTIAL
Interaction • Continuous Two-way dialogue • Learning process. Communication • Planned and unplanned • Proactive as well as reactive. Value • Understanding the customer's internal processes. • Understanding the process by which they meet their needs. • Relationship cost for the customer 38 CONFIDENTIAL
Acts, Episodes and Sequences Act • Smallest unit of analysis. e. g. click on site's home page. Episode • A series of acts forming one interaction e. g. Finding and submitting an order, dealing with a technical problem. Sequence • A series of episodes. E. g. orders with in a year. Relationship 39 CONFIDENTIAL
Communication Before episode • Providing training to customer. • Diagnosis of type of problems. • Communicating information about service process. During episode • Capturing information about the episode. After Episode • Evaluation • Analysis and review of outcome. Communication should be planned to support expected and unexpected episodes. 40 CONFIDENTIAL
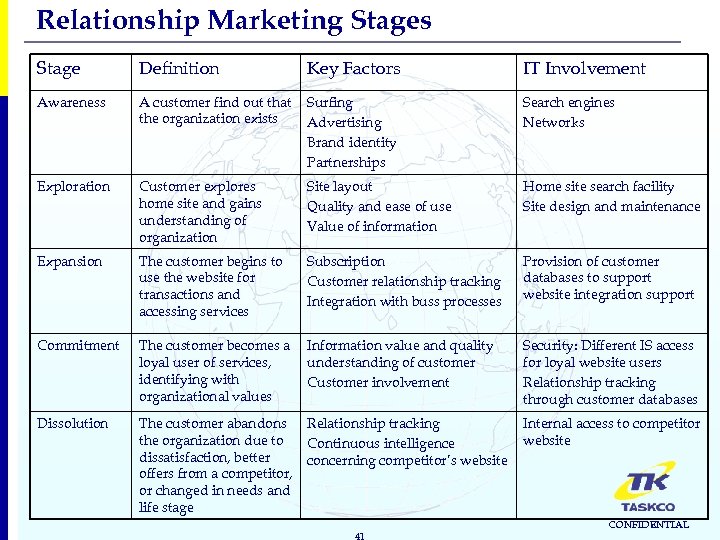
Relationship Marketing Stages Stage Definition Key Factors IT Involvement Awareness A customer find out that the organization exists Surfing Advertising Brand identity Partnerships Search engines Networks Exploration Customer explores home site and gains understanding of organization Site layout Quality and ease of use Value of information Home site search facility Site design and maintenance Expansion The customer begins to use the website for transactions and accessing services Subscription Customer relationship tracking Integration with buss processes Provision of customer databases to support website integration support Commitment The customer becomes a loyal user of services, identifying with organizational values Information value and quality understanding of customer Customer involvement Security: Different IS access for loyal website users Relationship tracking through customer databases Dissolution The customer abandons the organization due to dissatisfaction, better offers from a competitor, or changed in needs and life stage Relationship tracking Continuous intelligence concerning competitor’s website Internal access to competitor website 41 CONFIDENTIAL

Best Practices Loyalty becomes an IT service issue Managing an E-service is about managing a relationship Planned communication is essential Evaluation of acts, episodes and sequences may lead to an improved relationship 42 CONFIDENTIAL
What is E-government ? E-government is a continuous optimization of service delivery and governance by transforming internal and external relationships through technology, internet and new media external relationships • government to citizen • government to business – user of public services – provider of services internal relationships • government to government • government to employees 43 CONFIDENTIAL

E-government: a structural reform process technology is only a means E-government requires • change of mindsets: from government centric to customer centric • re-engineering of processes • re-organization of public services • changes of legal environment • cooperation between several government levels: one virtual electronic government 44 CONFIDENTIAL
Customer centric delivery of services based on the logic of the customer • life events (birth, marriage, etc. ) • life styles (sport, culture, etc. ) • life status (unemployed, retired, etc. ) p-channels and e-channels must co-exist multi device access (PC, TV, WAP GSM, PDA, …) integrated services • information • interaction • transaction 45 CONFIDENTIAL
Customer centric critical reflection on principles of data collection and creation of new added value • readable and understandable text • analysis of the necessity to collect data • harmonization of basic concepts • first data verification, then data collection • default values based on previously entered data • on-line help • simulation environments 46 CONFIDENTIAL
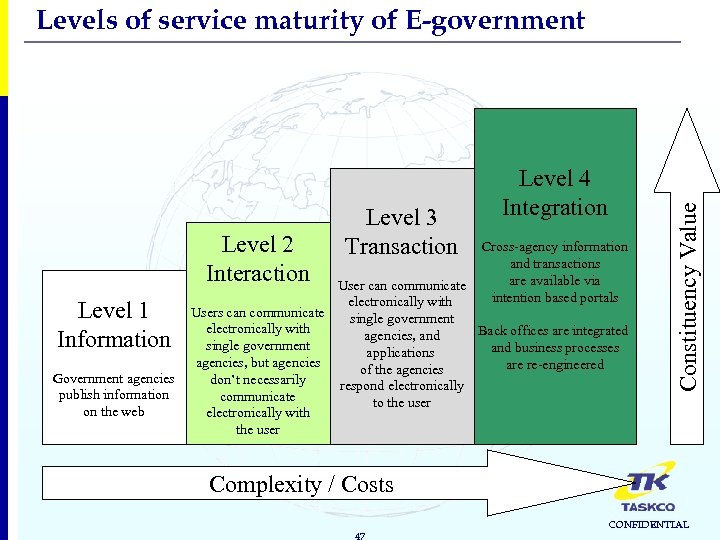
Level 2 Interaction Level 1 Information Government agencies publish information on the web Level 3 Transaction Level 4 Integration Cross-agency information and transactions are available via intention based portals User can communicate electronically with Users can communicate single government electronically with Back offices are integrated agencies, and single government and business processes applications agencies, but agencies are re-engineered of the agencies don’t necessarily respond electronically communicate to the user electronically with the user Constituency Value Levels of service maturity of E-government Complexity / Costs 47 CONFIDENTIAL

Back office integration is the key in most countries, many public services are concerned with delivering services to citizens and businesses a lot of information is needed by several public services, e. g. • identification data • data concerning the professional and social status • periodical data related to working periods • periodical data related to income • data concerning certain events, e. g. the start of a company, the occurence of a social risk, . . . 48 CONFIDENTIAL
Back office integration is the key lack of back office integration leads to • overloading of the users – multiple collection of the same information by several public authorities – no reuse of available information • waste of efficiency and time within the public services • suboptimal support of the policy • higher possibilities of fraud 49 CONFIDENTIAL
Back office integration: basic principles decentralised but unique data collection decentralised and distributed data management • functional task-sharing between public services • principle of the authentic source electronic information exchange and work flow • every public service can be a supplier or applicant of data • information exchange can be initiated – by the public service needing the information – by the public service disposing of new information – by the instution managing the network for electronic information exchange • application to application (no manual intervention) unique identification key for each entity 50 CONFIDENTIAL
Back office integration: basic principles global coordination • common architecture • common open standards • common horizontal services – messaging and transaction services – security services – portal services – content management services • normalisation of information • stimulation • project management 51 CONFIDENTIAL
Back office integration: basic principles control mechanisms by an independent third party (cf information is often of a sensible nature) • preventive access control • preventive control on the legitimacy of the exchange • loggings legal framework • organization of the back office integration • harmonization of basic concepts 52 CONFIDENTIAL

Useful tools electronic identity and authentication card for every entity, containing the unique identification key reference directory • structure: – directory of people: who and in which capacity has personal files in which social security institutions for which periods – data availability table: which data are available in which social security institutions for which types of files – access authorization table: which data may be transmitted to which institutions for which types of files • 3 functions: – access control – routing of information – automatic transmission of information 53 CONFIDENTIAL
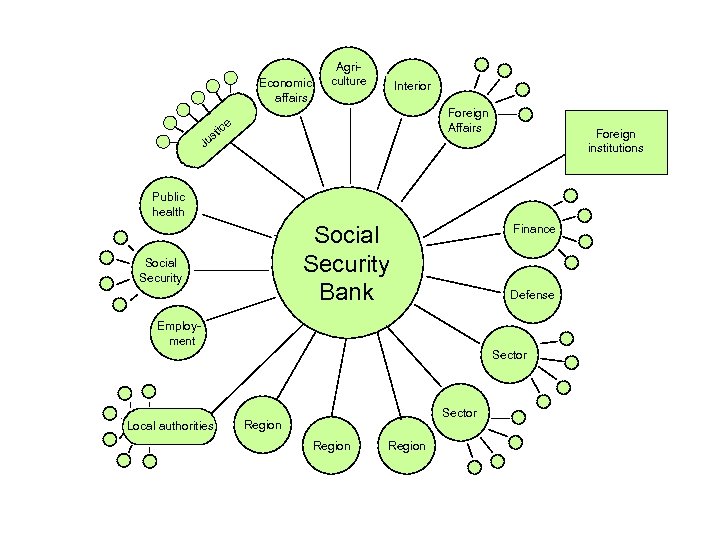
Economic affairs Ju Agriculture Interior Foreign Affairs e tic s Foreign institutions Public health Social Security Bank Social Security Finance Defense Employment Sector Local authorities Sector Region
e. Justice - Datahighway to Austrian Courts Electronic Legal Communicaton (ELC) Transmission of Legal Documents The Austrian Courts Automation of Court Proceedings - Business Goals Electronic Legal Communication Development of the Information Highway to the Courts Key Figures Success Factors Benefits 55 Flow Chart Document Transmission Benefits Success Factors Future Developments Statements CONFIDENTIAL
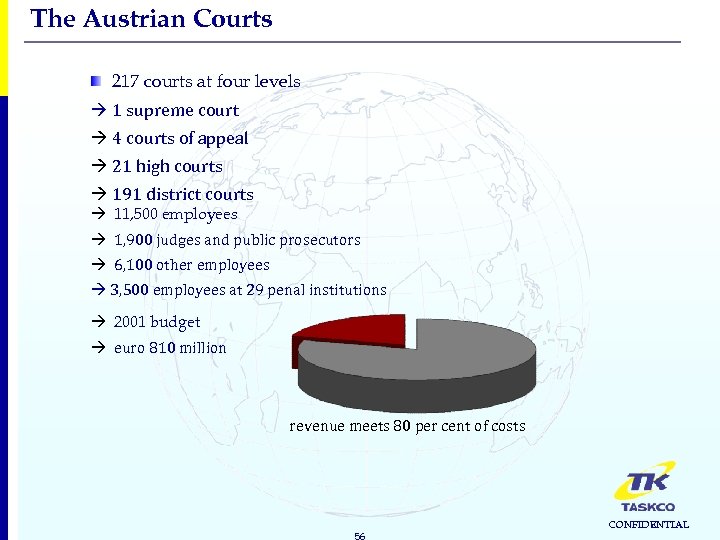
The Austrian Courts 217 courts at four levels 1 supreme court 4 courts of appeal 21 high courts 191 district courts 11, 500 employees 1, 900 judges and public prosecutors 6, 100 other employees 3, 500 employees at 29 penal institutions 2001 budget euro 810 million revenue meets 80 per cent of costs 56 CONFIDENTIAL
Automation of Court Proceedings - Business Goals One uniform application for all 40 different types of proceedings (prosecution and criminal proceedings at court, civil, enforcement of civil titles, family, remedy, insolvency cases, etc. ) For all the different types of courts all over Austria Rationalising and increasing the speed of court and prosecution proceedings, improving the service for the general public. Fast, reliable and secure electronic interface essential: Electronic Legal Communication (ELC) 57 CONFIDENTIAL

Electronic Legal Communication - Definition Communication Paperless Structured Electronic From the parties to the courts and vice versa Substitutes communication on paper and is a legal equivalent Not to be confused with faxing or sending a simple e-mail 58 CONFIDENTIAL
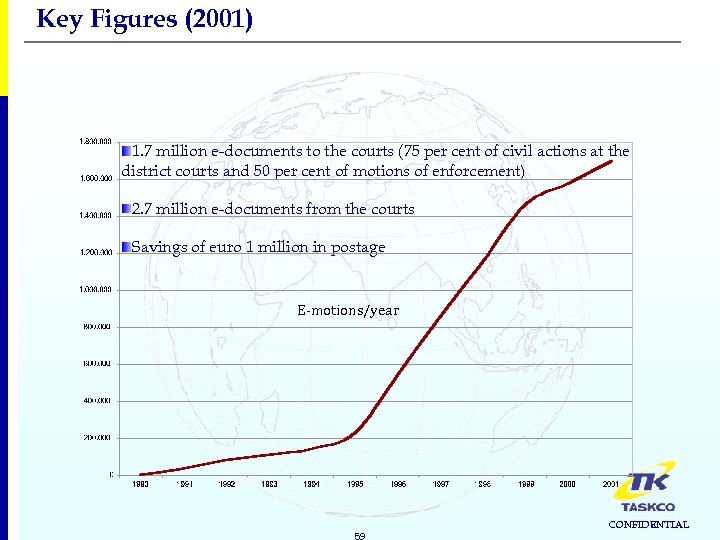
Key Figures (2001) 1. 7 million e-documents to the courts (75 per cent of civil actions at the district courts and 50 per cent of motions of enforcement) 2. 7 million e-documents from the courts Savings of euro 1 million in postage E-motions/year 59 CONFIDENTIAL
Success Factors Optimisation of the business process Synergy of IT and business models Legal changes: eg filing to court and service Cooperation with partners (lawyers, clearing house, software companies) Orientation to actual needs (general public and business) Financial incentives (reduced court fees) Clearly defined and published interface Structured data for further processing 60 CONFIDENTIAL

Benefits Speeding up court proceedings Improved service, quality and case information for parties Reductions in costs and personnel High level of security Available 7 days a week, 24 hours a day Integration of e-banking for court fees 61 CONFIDENTIAL
Flow Chart Subscriber Court 62 CONFIDENTIAL
Document Transmission Documents sent to courts Default summonses for district courts and industrial tribunals Requests for warrants of execution and attachment of earnings orders Other misc. documents to any Austrian court Documents received from courts Information on case files and court records Court orders to pay Approved warrants of execution Settlements, writs 63 CONFIDENTIAL
Benefits Data only has to be entered once in EDP-Systems Both courts and users can use input data Quick and secure service Quick and secure transmission Every document can be traced Quality higher than with conventional transmission Higher fees for lawyers: euro 3. 20 per document Court charges paid after transmission Direct debit Toll free hotline Access to log files via the internet Break-even point for users: 15 documents per month 64 CONFIDENTIAL

Success Factors Cooperation with key partners Austrian Bar Association Major customers and customer groups Software companies Benefits for users on introduction Price policy Cheaper than non-electronic solution Future development in stages Information policy Same high level of information for everyone Mailing list and website Meetings and presentations 65 CONFIDENTIAL

Future Developments Ø Focusing on standard products rather than customised software Ø Promoting the use of public systems (eg Internet) Ø Harmonising systems and equipment Ø Integrating additional secure features (eg Digital Signature) Ø Paving the way for internationalisation Ø Making the system accessible to citizens 66 CONFIDENTIAL

Singapore e-Government Status 67 CONFIDENTIAL

Cover Background Infocomm 21 Programme e-Government Strategic Framework and Initiatives Legal and Policy Environment Governance 68 CONFIDENTIAL
i. DA Formed Dec 1999 - NCB & TAS Oversees IT and Telecoms related industries and policies 69 CONFIDENTIAL
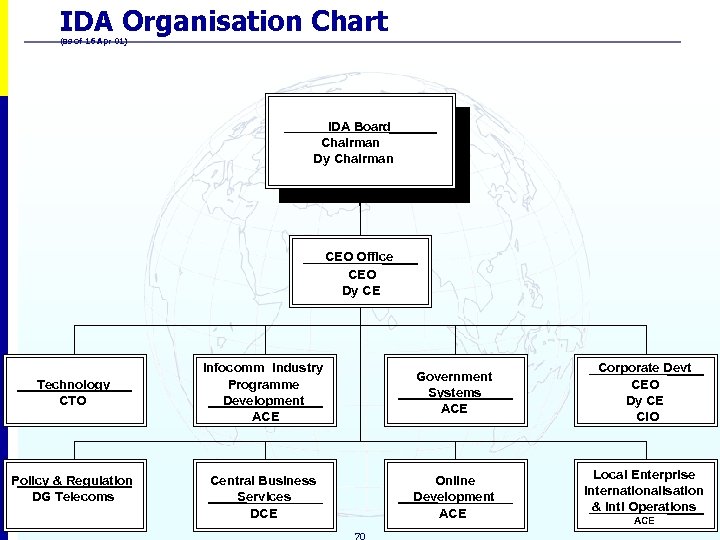
IDA Organisation Chart (as of 16 Apr 01) IDA Board Chairman Dy Chairman CEO Office CEO Dy CE Technology CTO Policy & Regulation DG Telecoms Infocomm Industry Programme Development ACE Government Systems ACE Corporate Devt CEO Dy CE CIO Central Business Services DCE Online Development ACE Local Enterprise Internationalisation & Intl Operations 70 ACE CONFIDENTIAL

i. DA VISION “Singapore - Where the Digital Future is “ 71 CONFIDENTIAL

National Computerisation Plan Civil Service Computerisation Prog Development and Growth of local IT Industry Develop pool of IT Manpower 72 CONFIDENTIAL

National IT Plan CSCP to encompass IT Electronic Data Interchange linking up Public, Businesses and Government 73 CONFIDENTIAL

IT 2000 Intelligent Island Concept IT readily accessible to the nation Singapore One Broadband Infrastructure 74 CONFIDENTIAL

Infocomm 21 Enable Public Sector to harness ICT June 2000 - e. Government Action Plan 75 CONFIDENTIAL

e. Govt VISION To be a leading e-Government to better serve the nation in the Digital Economy 76 CONFIDENTIAL
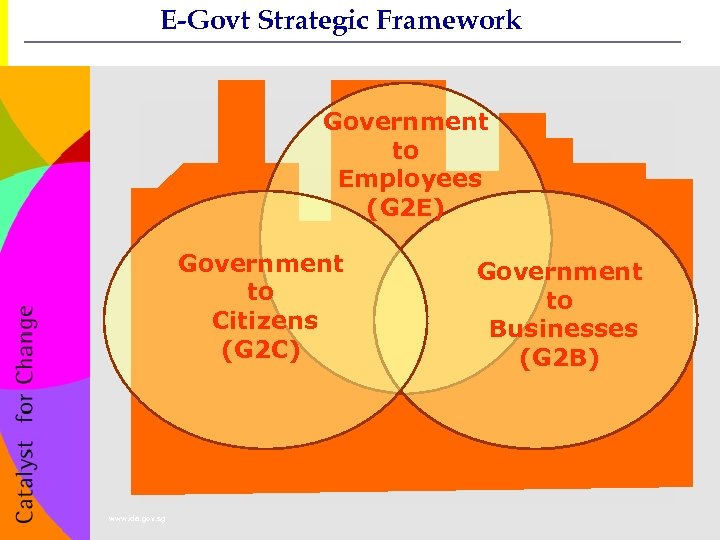
E-Govt Strategic Framework Government to Employees (G 2 E) Government to Citizens (G 2 C) Government to Businesses (G 2 B) www. ida. gov. sg 77 CONFIDENTIAL
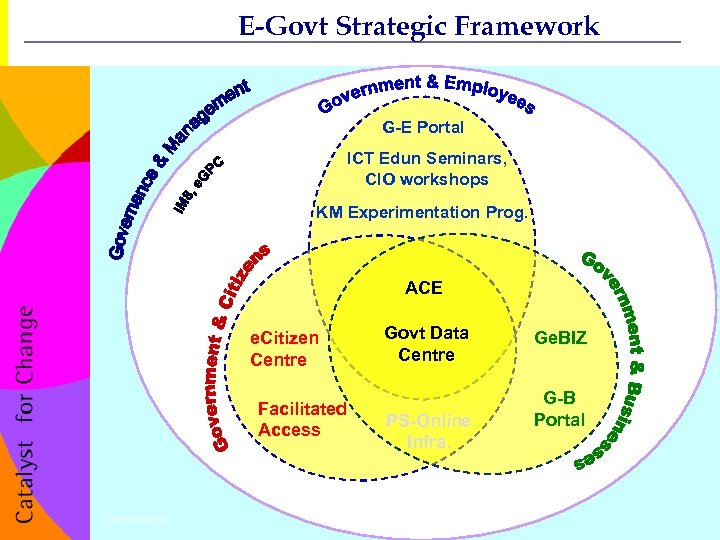
E-Govt Strategic Framework G-E Portal ICT Edun Seminars, CIO workshops KM Experimentation Prog. ACE Govt Data Centre e. Citizen Centre Facilitated Access PS-Online Infra. www. ida. gov. sg 78 Ge. BIZ G-B Portal CONFIDENTIAL
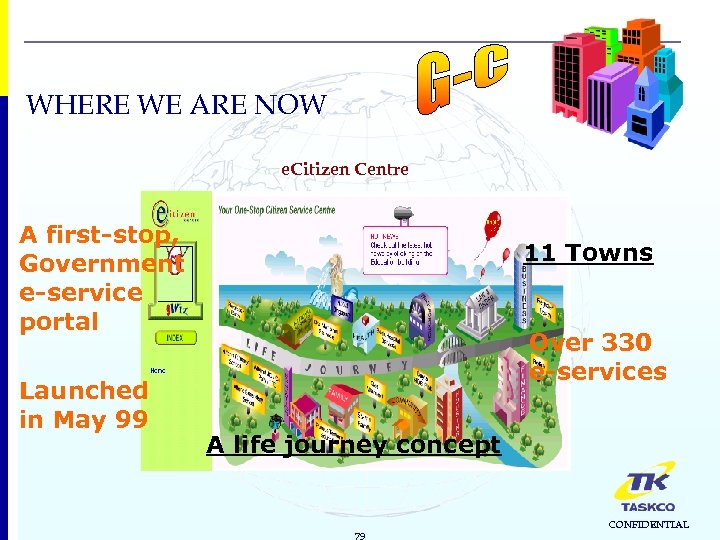
WHERE WE ARE NOW e. Citizen Centre A first-stop, Government e-service portal Launched in May 99 11 Towns Over 330 e-services A life journey concept 79 CONFIDENTIAL

Examples of e. Services: Renewal of Driver’s Licence Online booking of Sports Facilities Booking of Marriage Registration Date Open COE bidding Immediate Future • Renewal of Road Tax by Individuals • Application for Employment Pass Service Packages: Start a Business One-Stop Public Entertainment Licensing Centre Search for Jobs Get Married Buying a property 80 CONFIDENTIAL

e. CITIZEN CENTRE REVAMP 81 CONFIDENTIAL
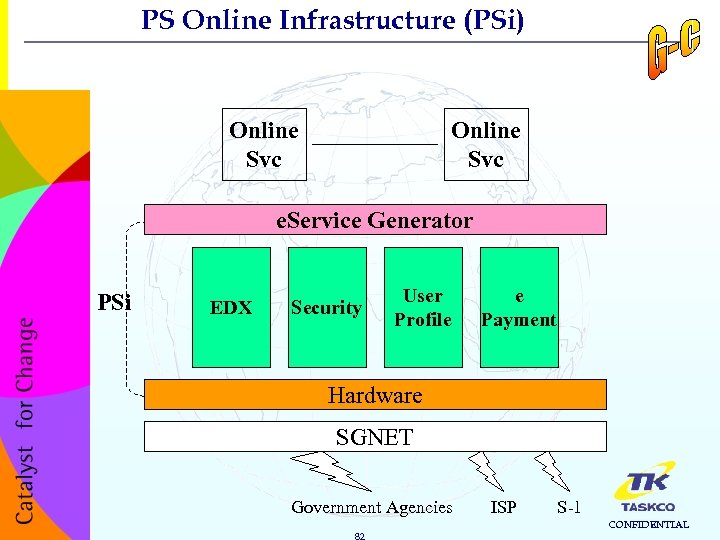
PS Online Infrastructure (PSi) Online Svc e. Service Generator PSi EDX Security User Profile e Payment Hardware SGNET Government Agencies 82 ISP S-1 CONFIDENTIAL

WHERE WE ARE NOW Ge. Biz (Government Electronic Business Centre) - implemented Dec 2000 An integrated, end-to-end, web-based system for online procurement & revenue tender activities 83 CONFIDENTIAL

Ge. Biz (Government Electronic Business Centre) 138 participating government agencies Over 100 suppliers Over 7, 600 Purchase Orders Total value of $93 million 84 CONFIDENTIAL
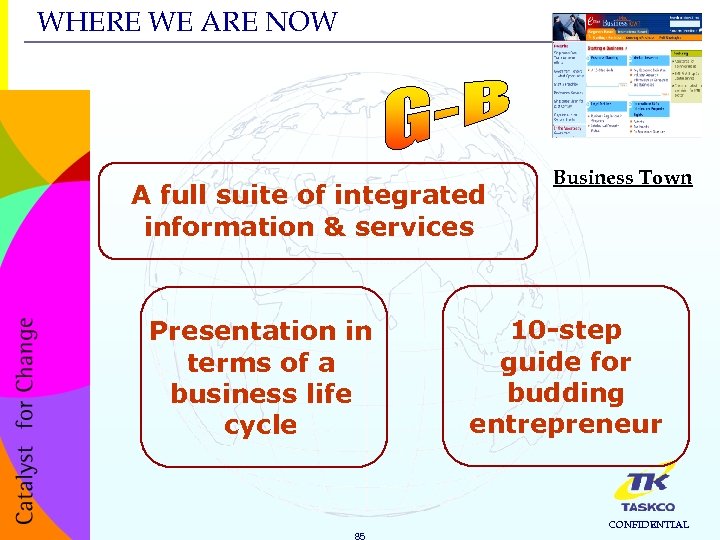
WHERE WE ARE NOW A full suite of integrated information & services Presentation in terms of a business life cycle 85 Business Town 10 -step guide for budding entrepreneur CONFIDENTIAL
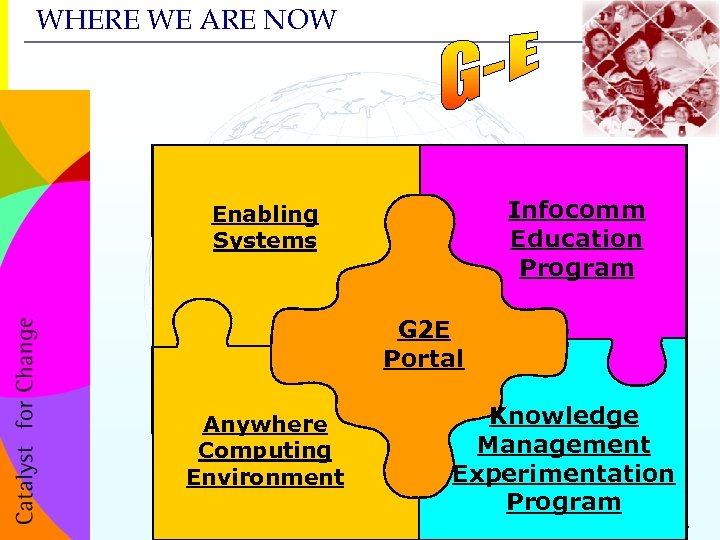
WHERE WE ARE NOW Infocomm Education Program Enabling Systems G 2 E Portal Knowledge Management Experimentation Program Anywhere Computing Environment 86 CONFIDENTIAL
87 CONFIDENTIAL
88 CONFIDENTIAL
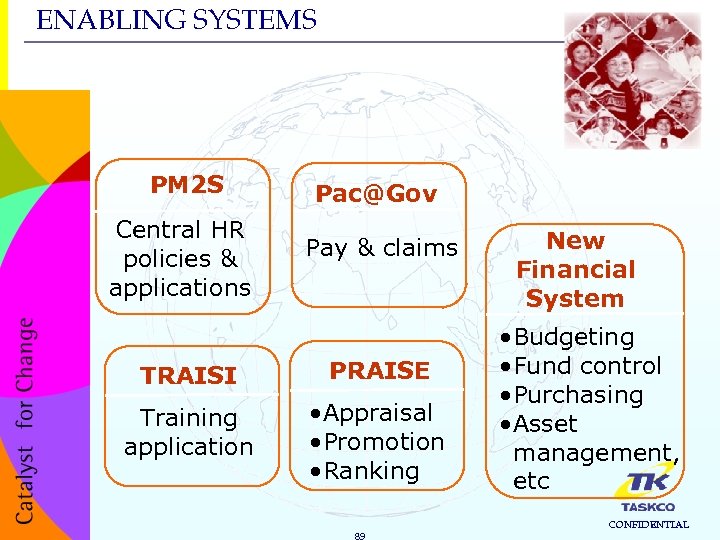
ENABLING SYSTEMS PM 2 S Pac@Gov Central HR policies & applications Pay & claims TRAISI PRAISE Training application • Appraisal • Promotion • Ranking 89 New Financial System • Budgeting • Fund control • Purchasing • Asset management, etc CONFIDENTIAL

Knowledge Management Interest Group (May 2000) • Share KM concepts, trends, best practices and explore development strategies KM Experimentation Programme (May 2001) • Co-funding to jump start KM projects • Gain experience on the various facets of KM implementation eg organisational enablers and impediments, processes, tools and solutions • Share project experience and results with all • 8 agencies identified 90 CONFIDENTIAL
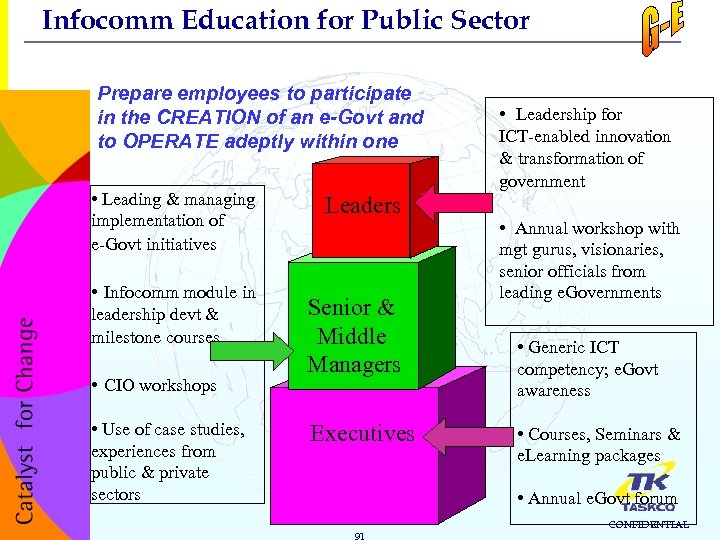
Infocomm Education for Public Sector Prepare employees to participate in the CREATION of an e-Govt and to OPERATE adeptly within one • Leading & managing implementation of e-Govt initiatives • Infocomm module in leadership devt & milestone courses • CIO workshops • Use of case studies, experiences from public & private sectors Leaders Senior & Middle Managers Executives • Leadership for ICT-enabled innovation & transformation of government • Annual workshop with mgt gurus, visionaries, senior officials from leading e. Governments • Generic ICT competency; e. Govt awareness • Courses, Seminars & e. Learning packages • Annual e. Govt forum 91 CONFIDENTIAL
Adaptive & Robust Infocomm Infrastructure Broadband Infra. for Government (BIG) Broadband connections from 1 Mbps to 70 Mbps with Telco class of reliability, availability and scalability Headway towards ACE Government Data Centre (DC@GOV) Operational since May 2001 Pricing model based on cost recovery Key benefits • Economies of scale • Govt systems connected to national broadband infra. (S 1) • Robust, secure and high availability (24 x 7) www. ida. gov. sg 92 CONFIDENTIAL

Legal and Policy Environment • facilitate the growth of electronic commerce • transparent, market-favourable regulation and legislation • support industry development and growth in the digital economy • do not unnecessarily impede the development of new and innovative applications • New regulations should also be flexible enough to cater for technology changes and new global policy • encourages industry self-regulation • industry practices are aligned with international practices 93 CONFIDENTIAL
• Electronic Transactions Act • provide a legal foundation for electronic signatures, and gives predictability and certainty to contracts formed electronically • Intellectual Property Rights • the protection of rights for copyright owners and increased public access to intellectual property • Amendments to Evidence Act • allow the use of electronic records as evidence in the courts • Contents Regulation • safeguard values and promote healthy growth & encourage industry self-regulation • Tax Issues & Import / Export Procedures 94 CONFIDENTIAL

Governance & Management Framework e. Government Policy Committee Public Sector Infocomm Steering Committee Public Sector Infocomm Review Committee IDA - CTO & CIO of Govt GCIO - IT Plng & Execution at the Ministries and Statutory Boards 95 CONFIDENTIAL
Challenges for e. Government Maturity of e. Services Integrated service delivery • Cross-agency collaboration • Multi-channel access Public-private sectors collaboration Ubiquitous access by all, facilitated where necessary Seamless information exchange across agencies Technology-enabled innovations to drive enterprise transformation Risk management of deploying leading-edge technologies 96 CONFIDENTIAL

URL’s www. egov. sg www. ecitizen. gov. sg 97 CONFIDENTIAL

E-Gov in South Africa 98 CONFIDENTIAL

Key IT Focus areas of SA Government Improved Service Delivery is paramount to e-Government vision E-Gov must increase the productivity levels and accessibility of the public service for the benefit of the citizen. E-Gov must result in government efficiencies and a reduction in costs Has to improve the functioning of the Government d y se vit ea cti cr u In rod P Re du ce d Co st Service delivery (User welfare) • Interoperability and Compatibility • Information Systems security • Economies of Scale • Avoidance of Duplication 99 CONFIDENTIAL
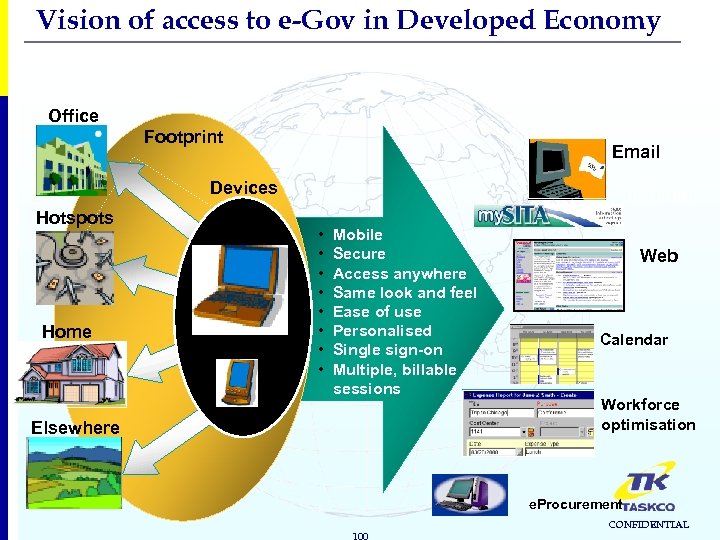
Vision of access to e-Gov in Developed Economy Office Footprint Email Devices Hotspots Home Intranet • • Mobile Secure Access anywhere Same look and feel Ease of use Personalised Single sign-on Multiple, billable sessions Elsewhere Web Calendar Workforce optimisation e. Procurement 100 CONFIDENTIAL
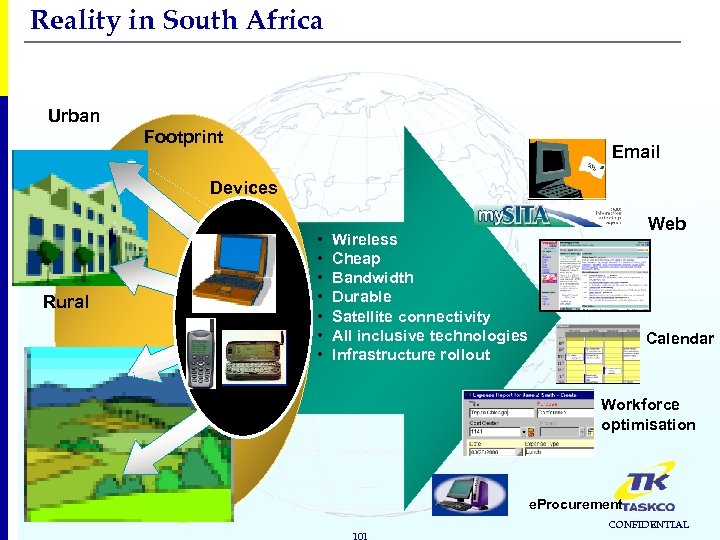
Reality in South Africa Urban Footprint Email Devices Rural Intranet • • Web Wireless Cheap Bandwidth Durable Satellite connectivity All inclusive technologies Infrastructure rollout Calendar Workforce optimisation e. Procurement 101 CONFIDENTIAL

Digital Divide reality in one country Cannot be oblivious to majority of people in country hence need to ensure true inclusion – South Africa represents “two nations” (north, south; rural, urban; black, white; literate, illiterate …but to mention a few of the extremes) and lack of infrastructure in some areas e. g. 30% telephony penetration but only 1% penetration in rural areas. – Eleven Languages Technologies need to be suited for African conditions – GSM growth has exceeded all expectations. In seven years GSM overtaken fixed line penetration Training programmes an integral part of success factors Multinational involvement in research and development critical to develop Africa specific solutions Investment in access and infrastructure needs to be aggressive Rollout needs to be aggressive, inexpensive, sustainable and suited for Africa 102 CONFIDENTIAL
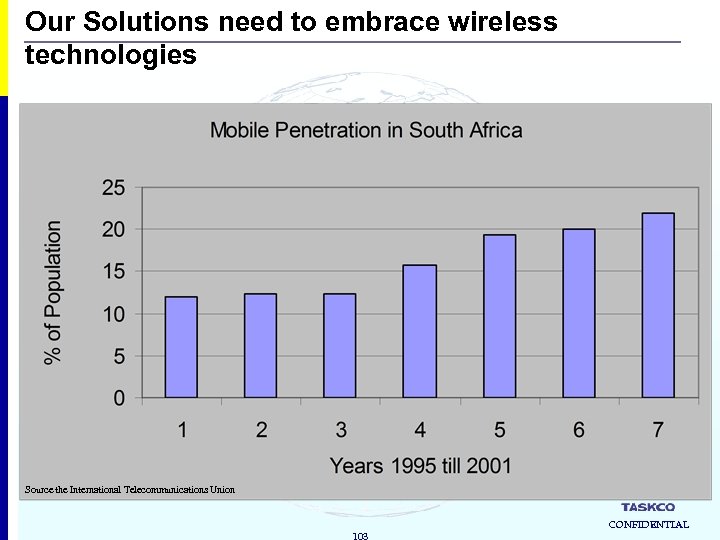
Our Solutions need to embrace wireless technologies Source the International Telecommunications Union 103 CONFIDENTIAL
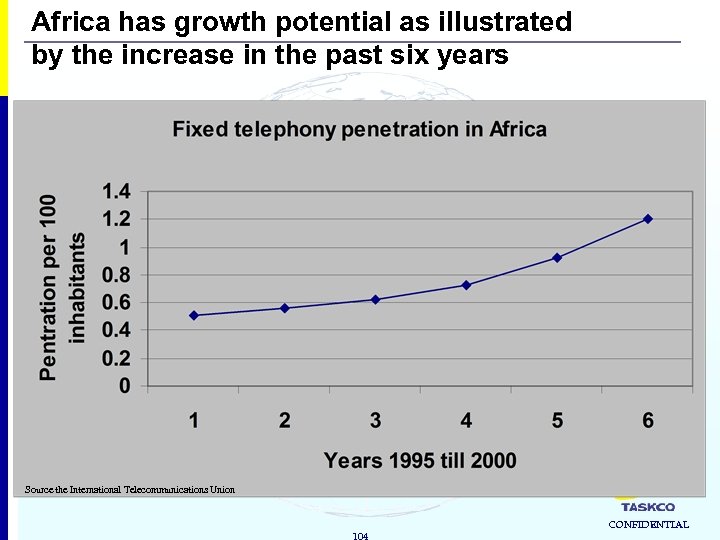
Africa has growth potential as illustrated by the increase in the past six years Source the International Telecommunications Union 104 CONFIDENTIAL

What South Africa have achieved ? Formation of the Government Information Technology Officer Council and the State Information Technology Agency An assertive drive to improve skill levels across the country and public servants in particular Aggressive technology and universal service rollout R&D emphasis for Africa specific solution Political drive of e-Government policies at the highest political level by the President – Establishment of an international advisory commission inclusive of the heads of the major ICT industry vendors focused on bridging the Digital divide and improving the economies of the African Continent Projects include: Smart-card based ID document, online tax completion, Gateway/Portal project, Consolidation of the back-office 105 CONFIDENTIAL

E-services offered by the Spanish Tax Agency 106 CONFIDENTIAL
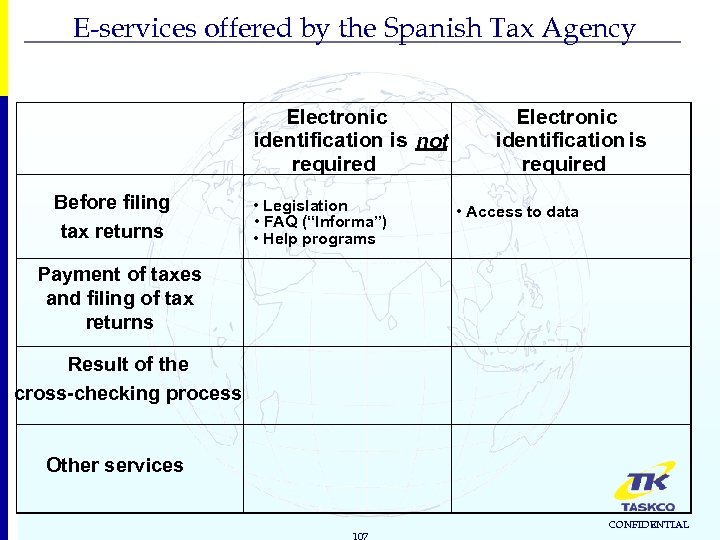
E-services offered by the Spanish Tax Agency Electronic identification is not required Before filing tax returns • Legislation • FAQ (“Informa”) • Help programs Electronic identification is required • Access to data Payment of taxes and filing of tax returns Result of the cross-checking process Other services 107 CONFIDENTIAL
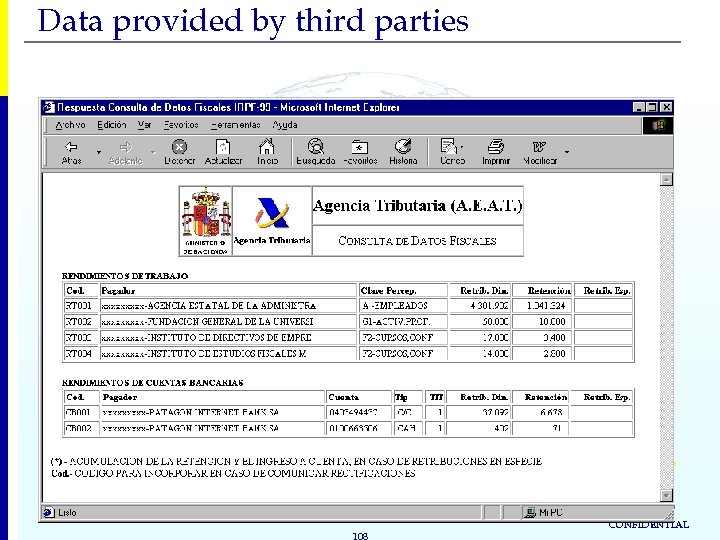
Data provided by third parties 108 CONFIDENTIAL
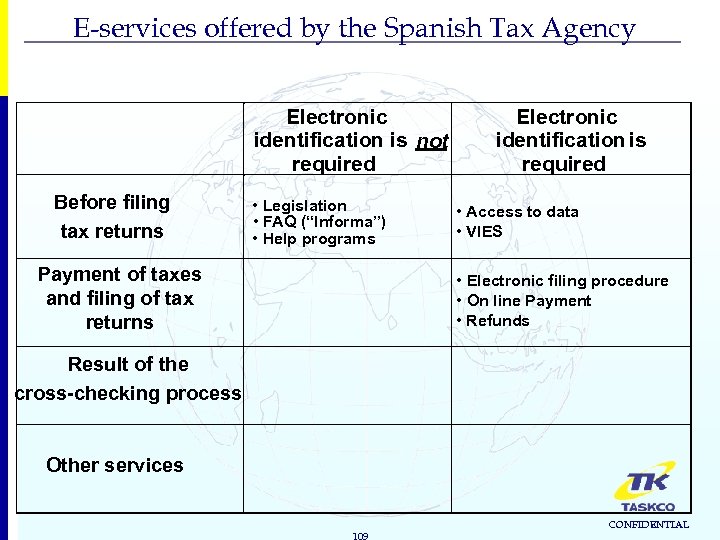
E-services offered by the Spanish Tax Agency Electronic identification is not required Before filing tax returns • Legislation • FAQ (“Informa”) • Help programs Payment of taxes and filing of tax returns Electronic identification is required • Access to data • VIES • Electronic filing procedure • On line Payment • Refunds Result of the cross-checking process Other services 109 CONFIDENTIAL
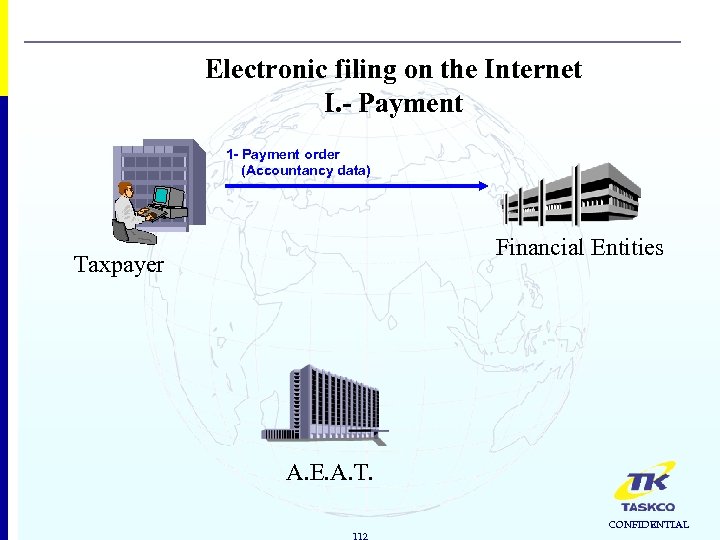
Electronic filing on the Internet I. - Payment 1 - Payment order (Accountancy data) Financial Entities Taxpayer A. E. A. T. 112 CONFIDENTIAL
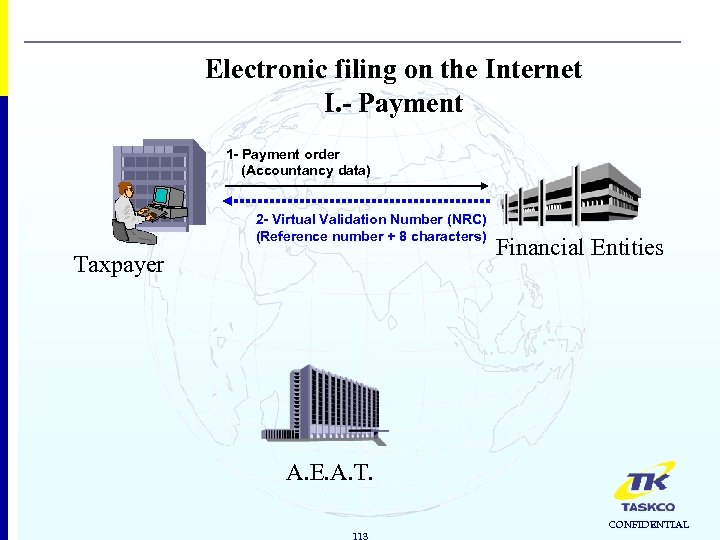
Electronic filing on the Internet I. - Payment 1 - Payment order (Accountancy data) 2 - Virtual Validation Number (NRC) (Reference number + 8 characters) Taxpayer Financial Entities A. E. A. T. 113 CONFIDENTIAL
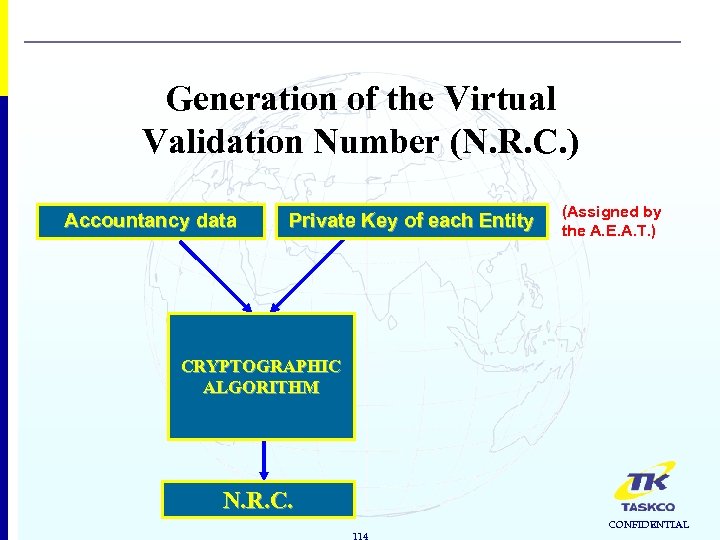
Generation of the Virtual Validation Number (N. R. C. ) Accountancy data Private Key of each Entity (Assigned by the A. E. A. T. ) CRYPTOGRAPHIC ALGORITHM N. R. C. 114 CONFIDENTIAL
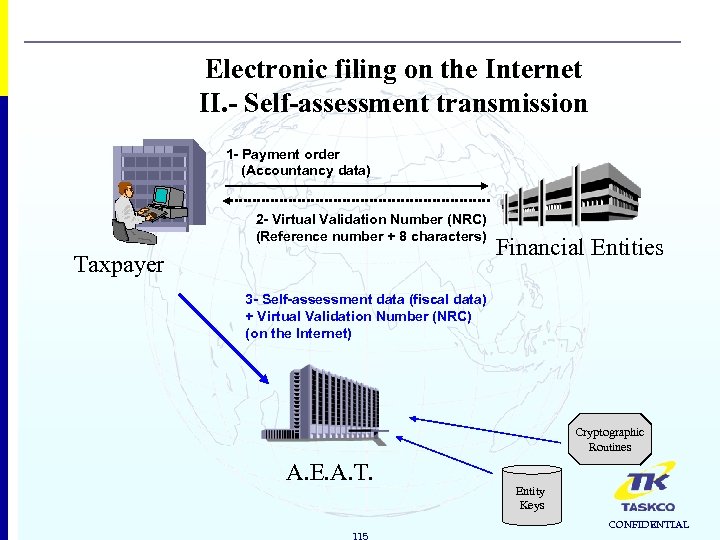
Electronic filing on the Internet II. - Self-assessment transmission 1 - Payment order (Accountancy data) 2 - Virtual Validation Number (NRC) (Reference number + 8 characters) Taxpayer Financial Entities 3 - Self-assessment data (fiscal data) + Virtual Validation Number (NRC) (on the Internet) Cryptographic Routines A. E. A. T. 115 Entity Keys CONFIDENTIAL
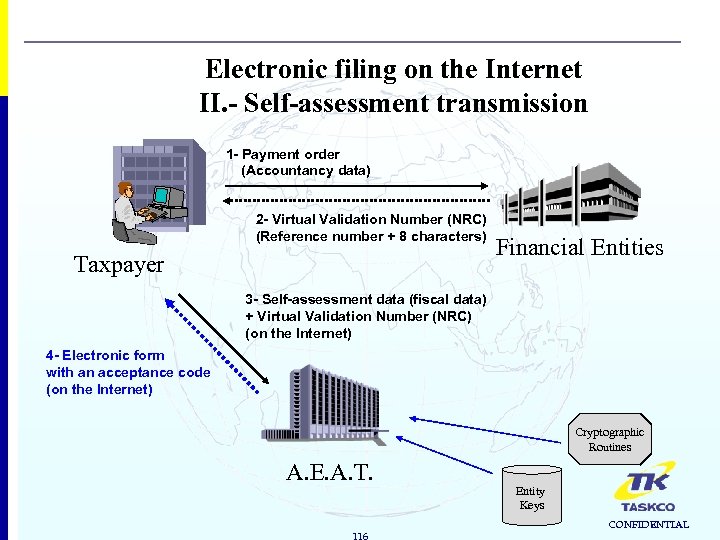
Electronic filing on the Internet II. - Self-assessment transmission 1 - Payment order (Accountancy data) 2 - Virtual Validation Number (NRC) (Reference number + 8 characters) Taxpayer Financial Entities 3 - Self-assessment data (fiscal data) + Virtual Validation Number (NRC) (on the Internet) 4 - Electronic form with an acceptance code (on the Internet) Cryptographic Routines A. E. A. T. 116 Entity Keys CONFIDENTIAL
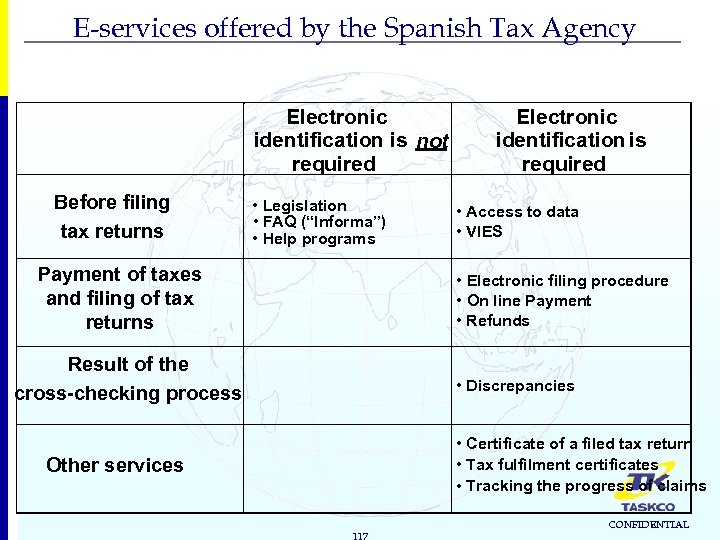
E-services offered by the Spanish Tax Agency Electronic identification is not required Before filing tax returns • Legislation • FAQ (“Informa”) • Help programs Payment of taxes and filing of tax returns Electronic identification is required • Access to data • VIES • Electronic filing procedure • On line Payment • Refunds Result of the cross-checking process • Discrepancies • Certificate of a filed tax return • Tax fulfilment certificates • Tracking the progress of claims Other services 117 CONFIDENTIAL

E-Services: Europe Public Services Geoff Unwin – CEO CGE&Y Brussels, November 30 th 2001 118 CONFIDENTIAL
Web-based Survey on electronic Public Services 1. Context 2. Scope 4. Conclusions 3. Results 119 CONFIDENTIAL
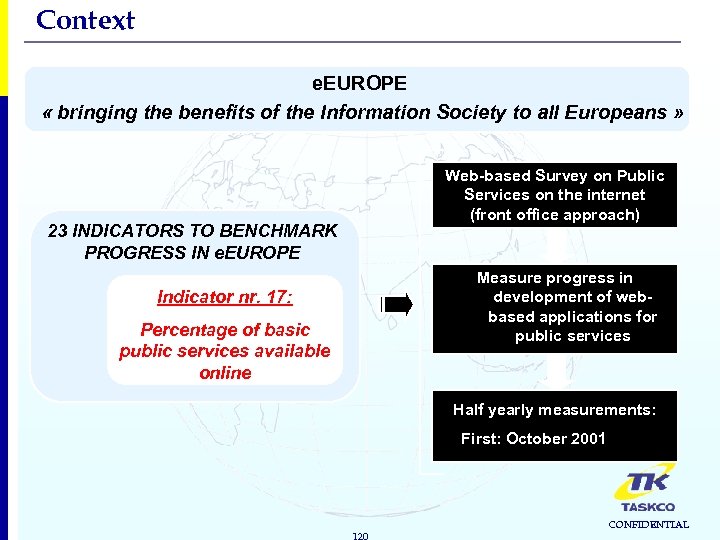
Context e. EUROPE « bringing the benefits of the Information Society to all Europeans » Web-based Survey on Public Services on the internet (front office approach) 23 INDICATORS TO BENCHMARK PROGRESS IN e. EUROPE Measure progress in development of webbased applications for public services Indicator nr. 17: Percentage of basic public services available online Half yearly measurements: First: October 2001 120 CONFIDENTIAL
Agenda Web-based Survey on electronic Public Services 1. Context 2. Scope 4. Conclusions 3. Results 121 CONFIDENTIAL
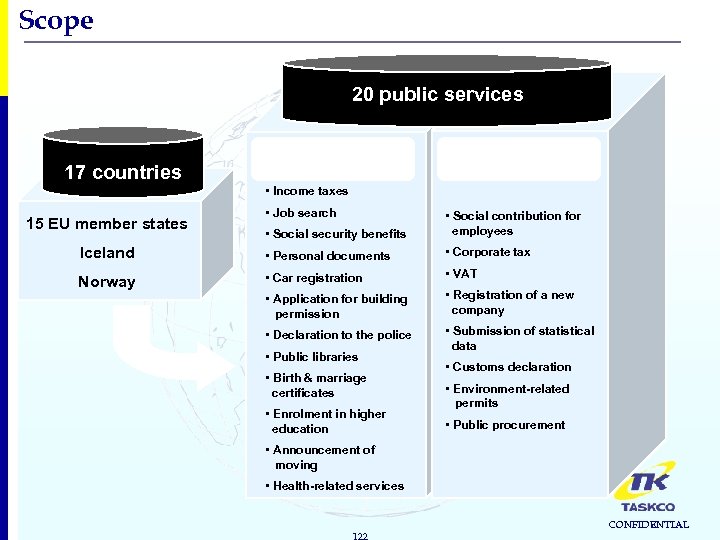
Scope 20 public services 17 countries Citizens Businesses • Income taxes • Job search • Social security benefits • Social contribution for employees Iceland • Personal documents • Corporate tax Norway • Car registration • VAT • Application for building permission • Registration of a new company • Declaration to the police • Submission of statistical data 15 EU member states • Public libraries • Birth & marriage certificates • Enrolment in higher education • Customs declaration • Environment-related permits • Public procurement • Announcement of moving • Health-related services 122 CONFIDENTIAL
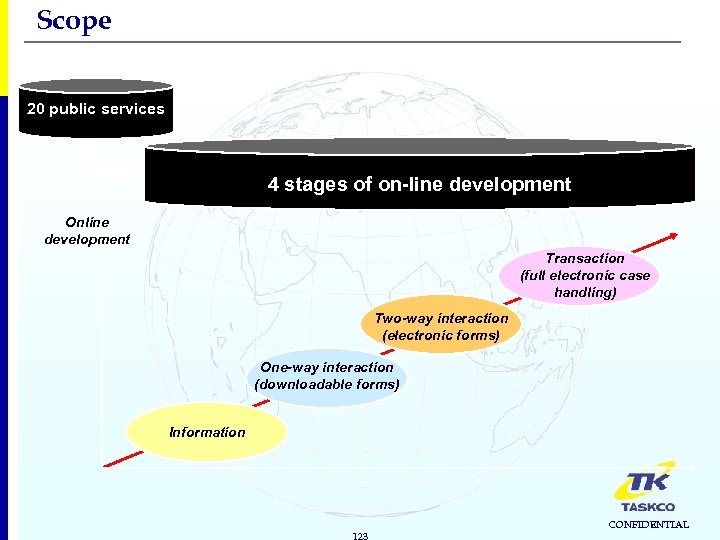
Scope 20 public services 4 stages of on-line development Online development Transaction (full electronic case handling) Two-way interaction (electronic forms) One-way interaction (downloadable forms) Information 123 CONFIDENTIAL
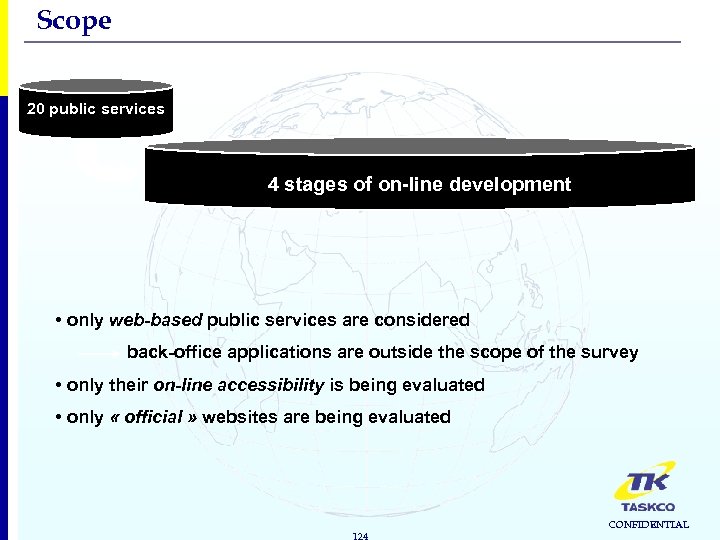
Scope 20 public services 4 stages of on-line development • only web-based public services are considered back-office applications are outside the scope of the survey • only their on-line accessibility is being evaluated • only « official » websites are being evaluated 124 CONFIDENTIAL
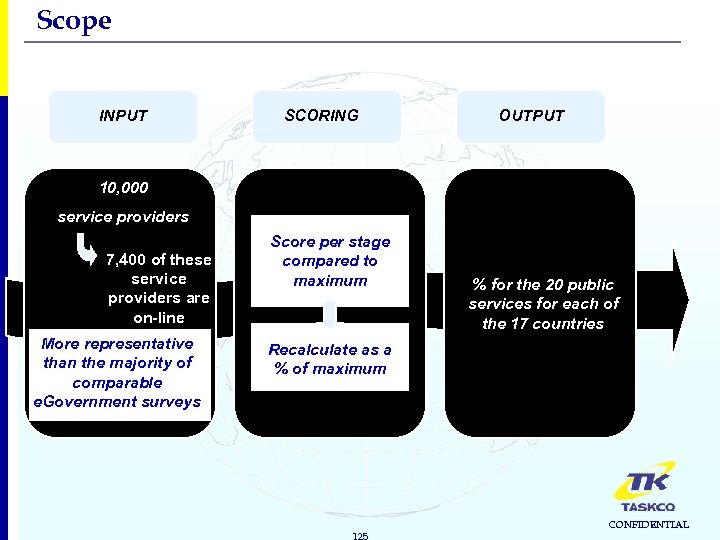
Scope INPUT SCORING OUTPUT 10, 000 service providers 7, 400 of these service providers are on-line More representative than the majority of comparable e. Government surveys Score per stage compared to maximum % for the 20 public services for each of the 17 countries Recalculate as a % of maximum 125 CONFIDENTIAL
Agenda Web-based Survey on electronic Public Services 1. Context 2. Scope 3. Results 4. Conclusions 1. Target group 2. Service content 126 CONFIDENTIAL
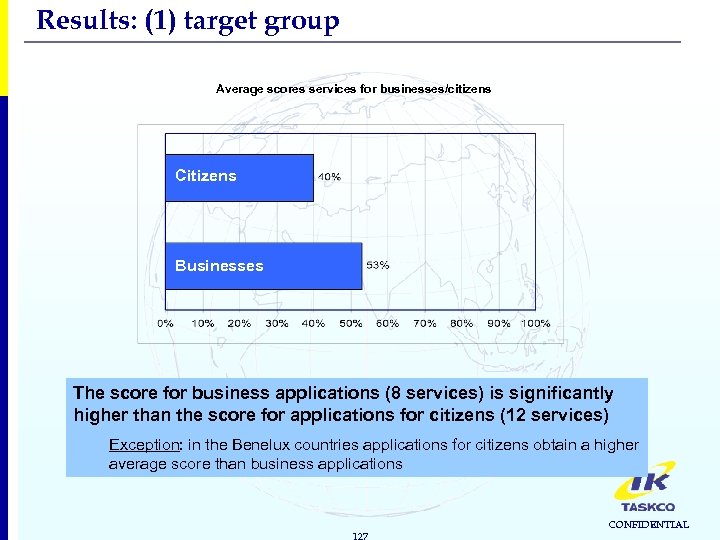
Results: (1) target group Average scores services for businesses/citizens Citizens Businesses The score for business applications (8 services) is significantly higher than the score for applications for citizens (12 services) Exception: in the Benelux countries applications for citizens obtain a higher average score than business applications 127 CONFIDENTIAL
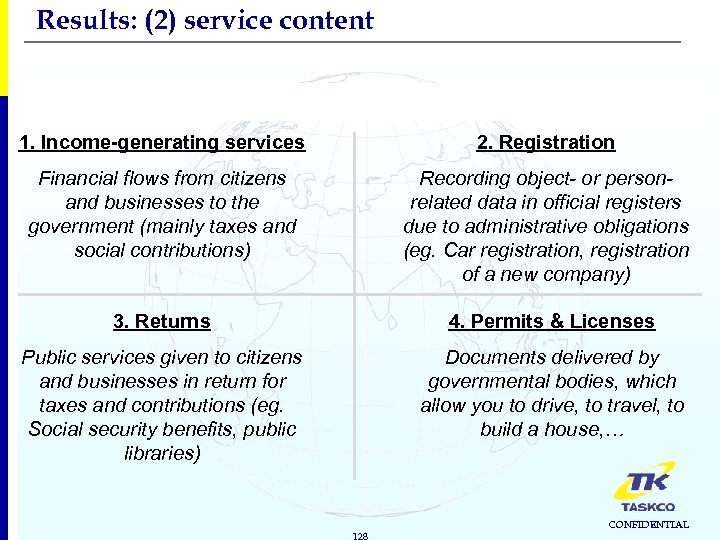
Results: (2) service content FOUR PUBLIC SERVICE CLUSTERS 1. Income-generating services 2. Registration Financial flows from citizens and businesses to the government (mainly taxes and social contributions) Recording object- or personrelated data in official registers due to administrative obligations (eg. Car registration, registration of a new company) 3. Returns 4. Permits & Licenses Public services given to citizens and businesses in return for taxes and contributions (eg. Social security benefits, public libraries) Documents delivered by governmental bodies, which allow you to drive, to travel, to build a house, … 128 CONFIDENTIAL
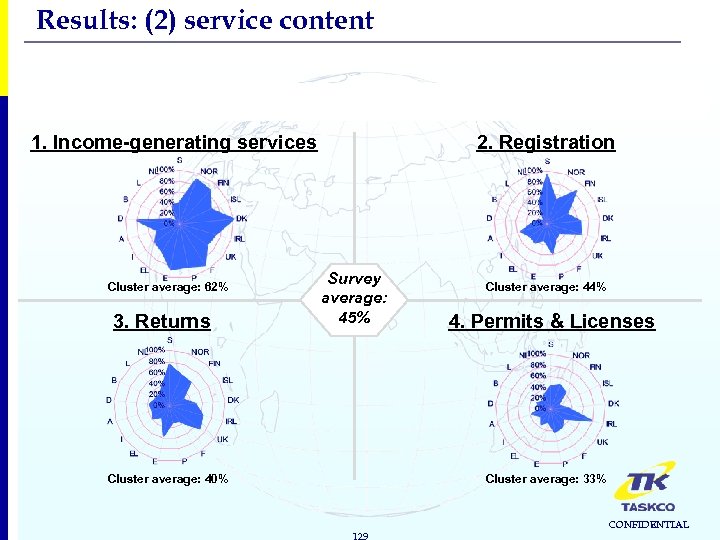
Results: (2) service content FOUR PUBLIC SERVICE CLUSTERS 1. Income-generating services Cluster average: 62% 3. Returns 2. Registration Survey average: 45% Cluster average: 40% Cluster average: 44% 4. Permits & Licenses Cluster average: 33% 129 CONFIDENTIAL
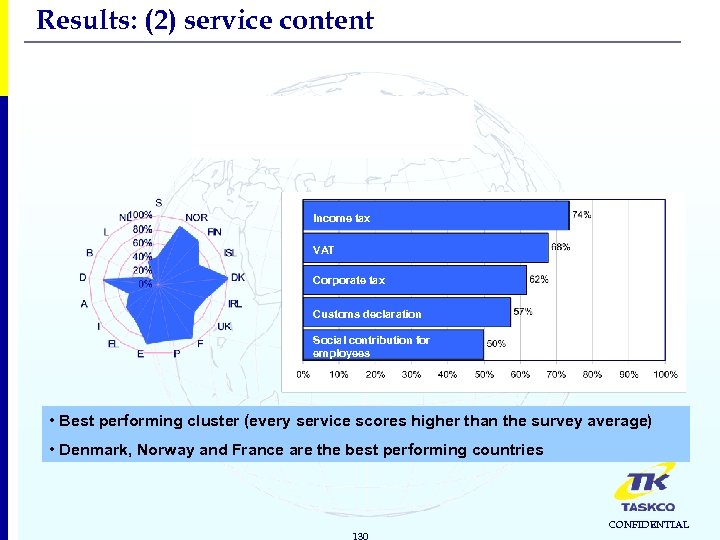
Results: (2) service content 1. Income-generating services Cluster average: 62% Income tax VAT Corporate tax Customs declaration Social contribution for employees • Best performing cluster (every service scores higher than the survey average) • Denmark, Norway and France are the best performing countries 130 CONFIDENTIAL
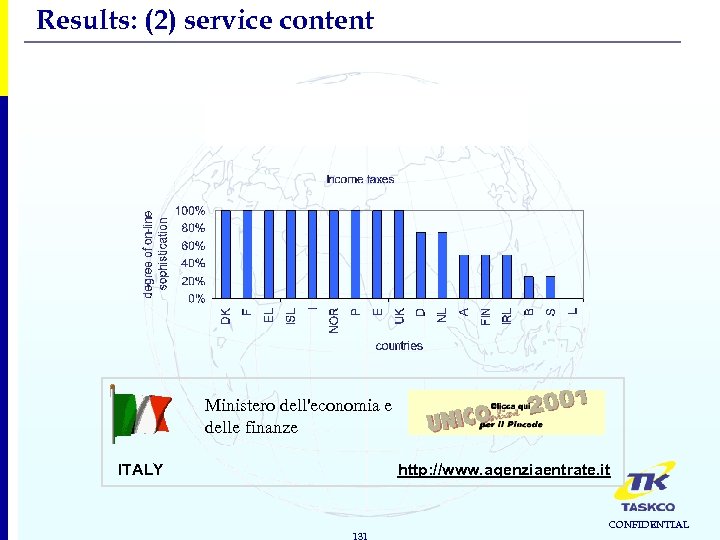
Results: (2) service content 1. Income-generating services Best scoring service: Income taxes Ministero dell'economia e delle finanze ITALY http: //www. agenziaentrate. it 131 CONFIDENTIAL
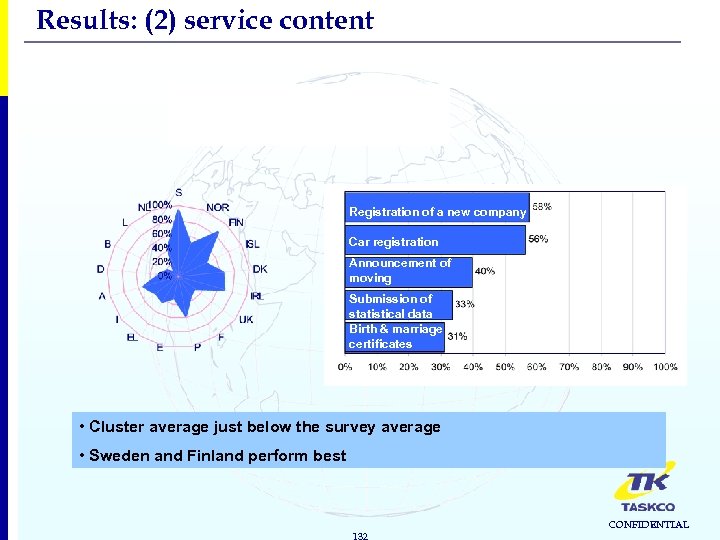
Results: (2) service content 2. Registration Cluster average: 44% Registration of a new company Car registration Announcement of moving Submission of statistical data Birth & marriage certificates • Cluster average just below the survey average • Sweden and Finland perform best 132 CONFIDENTIAL
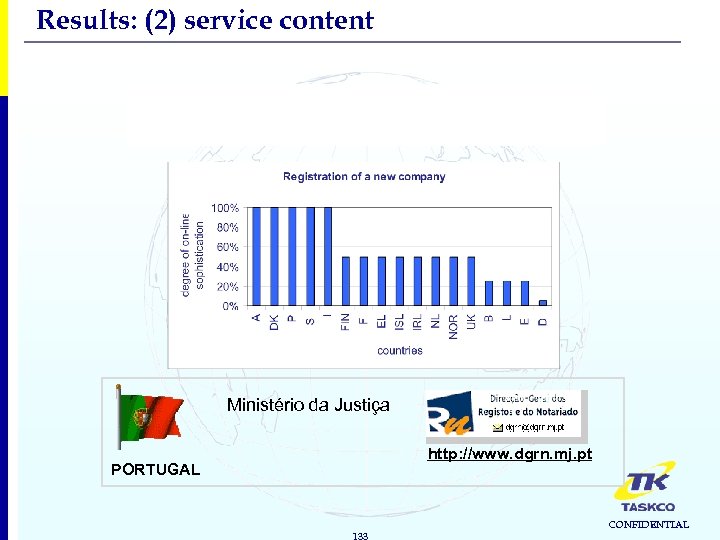
Results: (2) service content 2. Registration Best scoring service: Registration of a new company Ministério da Justiça http: //www. dgrn. mj. pt PORTUGAL 133 CONFIDENTIAL
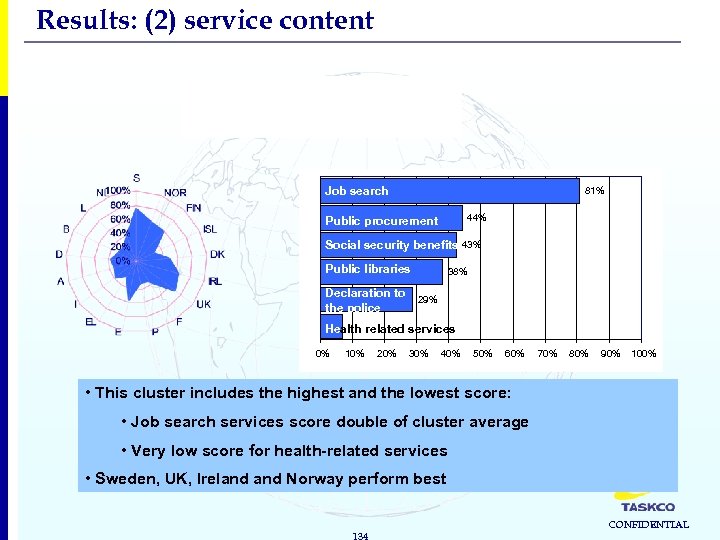
Results: (2) service content 3. Returns Cluster average: 40% Job search 81% 44% Public procurement Social security benefits 43% Public libraries Declaration to the police 38% 29% Health related services 7% 0% 10% 20% 30% 40% 50% 60% 70% 80% 90% 100% • This cluster includes the highest and the lowest score: • Job search services score double of cluster average • Very low score for health-related services • Sweden, UK, Ireland Norway perform best 134 CONFIDENTIAL
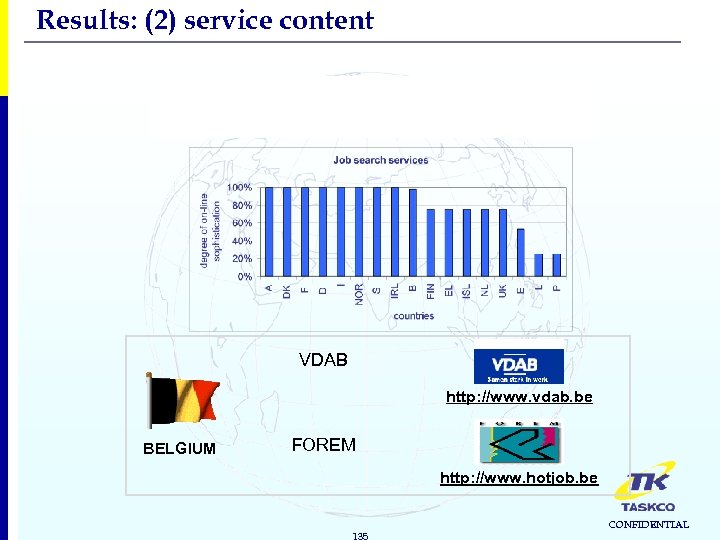
Results: (2) service content 3. Returns Best scoring service: Job search services Public procurement VDAB http: //www. vdab. be BELGIUM FOREM http: //www. hotjob. be 135 CONFIDENTIAL
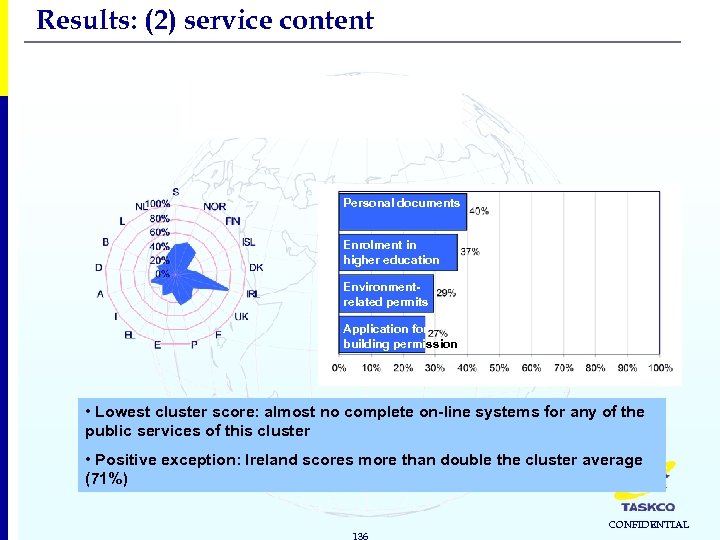
Results: (2) service content 4. Permits & Licenses Cluster average: 33% Personal documents Enrolment in higher education Environmentrelated permits Application for building permission • Lowest cluster score: almost no complete on-line systems for any of the public services of this cluster • Positive exception: Ireland scores more than double the cluster average (71%) 136 CONFIDENTIAL
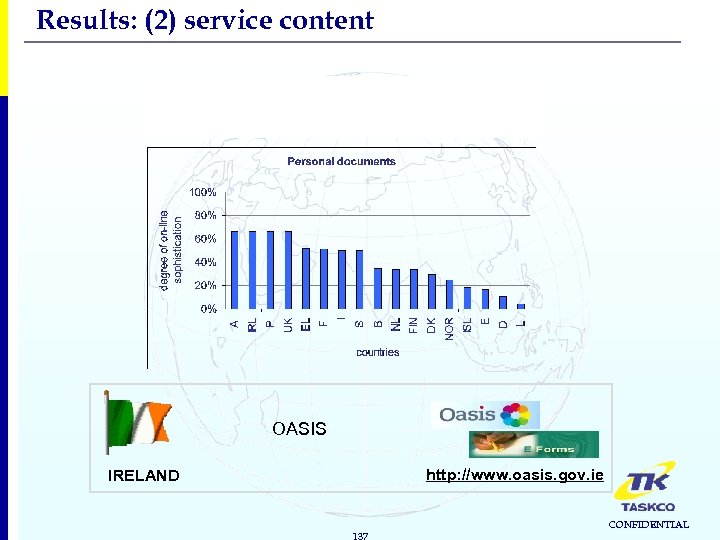
Results: (2) service content 4. Permits & Licenses Best scoring service: Personal documents OASIS http: //www. oasis. gov. ie IRELAND 137 CONFIDENTIAL
Agenda Web-based Survey on electronic Public Services 1. Context 2. Scope 4. Conclusions 3. Results 138 CONFIDENTIAL
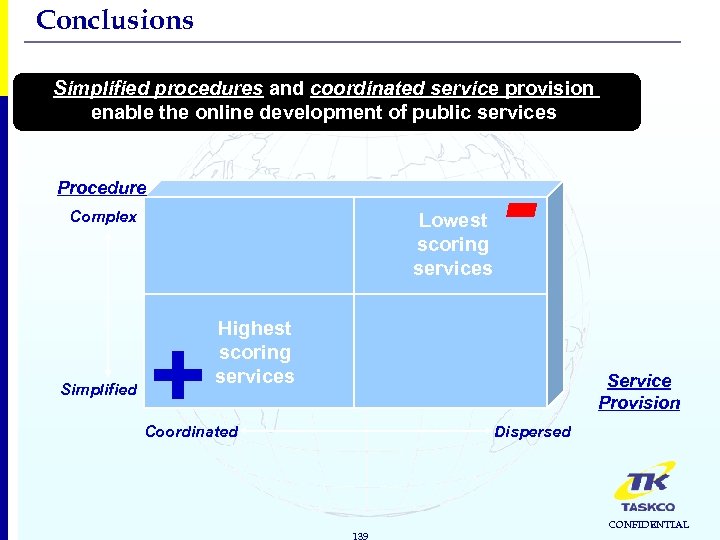
Conclusions Simplified procedures and coordinated service provision enable the online development of public services Procedure Complex Simplified Lowest scoring services + - Highest scoring services Service Provision Coordinated Dispersed 139 CONFIDENTIAL
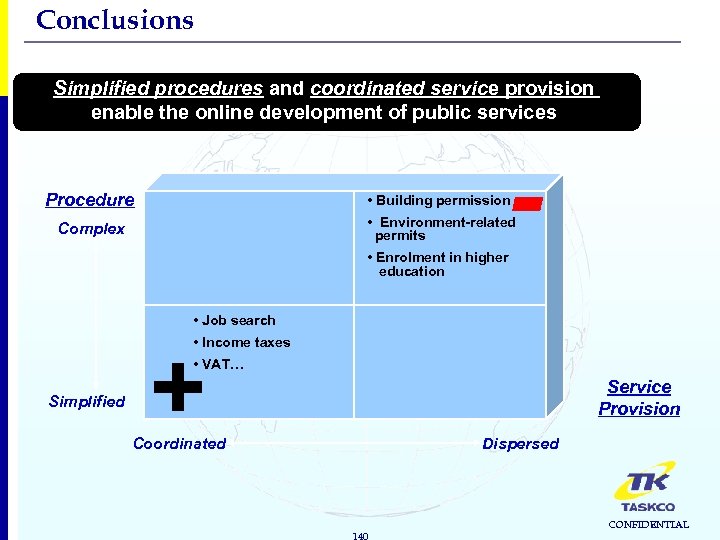
Conclusions Simplified procedures and coordinated service provision enable the online development of public services - Procedure • Building permission Complex • Environment-related permits • Enrolment in higher education • Job search • Income taxes + • VAT… Simplified Service Provision Coordinated Dispersed 140 CONFIDENTIAL
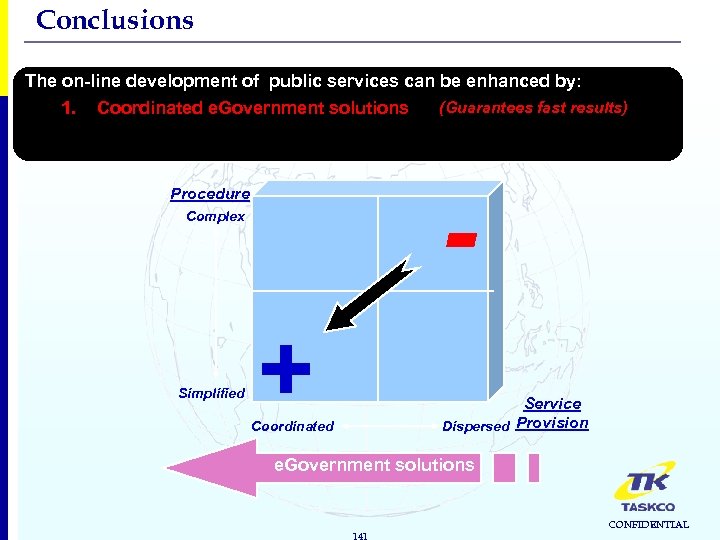
Conclusions The on-line development of public services can be enhanced by: 1. Coordinated e. Government solutions - Procedure Complex Simplified (Guarantees fast results) + Service Coordinated Dispersed Provision e. Government solutions 141 CONFIDENTIAL
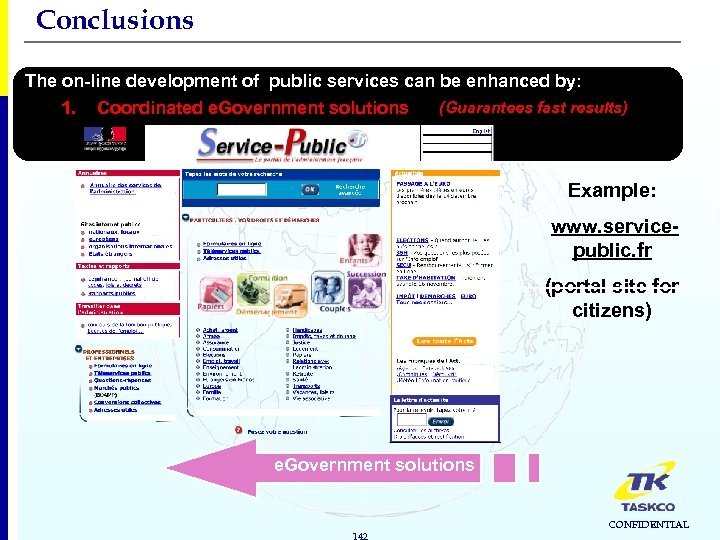
Conclusions The on-line development of public services can be enhanced by: 1. Coordinated e. Government solutions (Guarantees fast results) Example: www. servicepublic. fr (portal site for citizens) e. Government solutions 142 CONFIDENTIAL
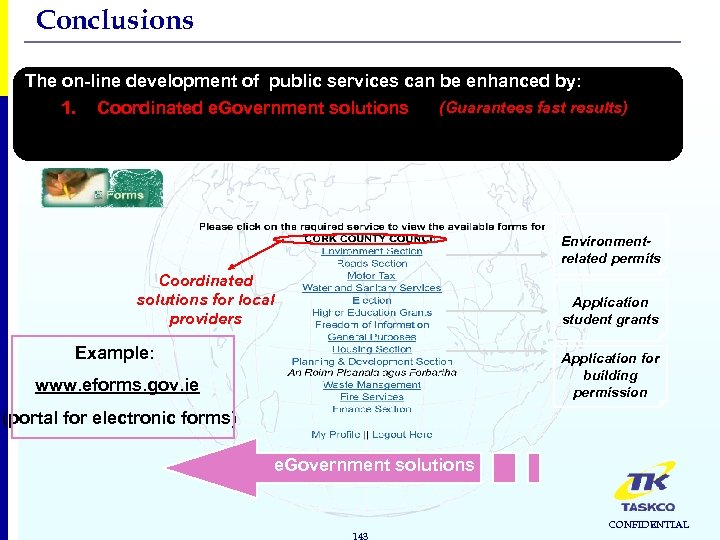
Conclusions The on-line development of public services can be enhanced by: 1. Coordinated e. Government solutions (Guarantees fast results) Environmentrelated permits Coordinated solutions for local providers Application student grants Example: Application for building permission www. eforms. gov. ie (portal for electronic forms) e. Government solutions 143 CONFIDENTIAL
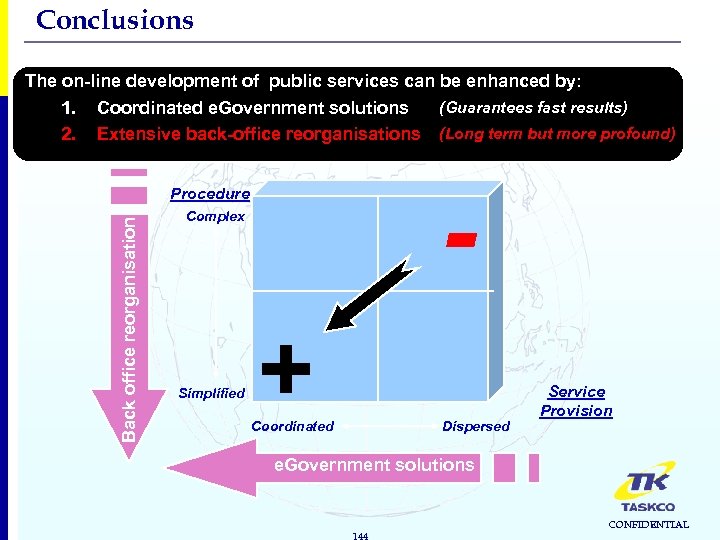
Conclusions The on-line development of public services can be enhanced by: Coordinated e. Government solutions Extensive back-office reorganisations Complex Simplified (Guarantees fast results) (Long term but more profound) - Procedure Back office reorganisation 1. 2. + Coordinated Dispersed Service Provision e. Government solutions 144 CONFIDENTIAL
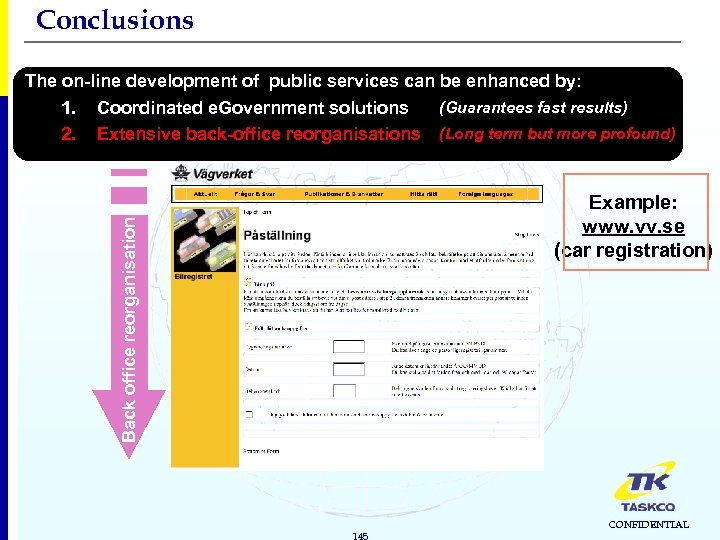
Conclusions The on-line development of public services can be enhanced by: Coordinated e. Government solutions Extensive back-office reorganisations Back office reorganisation 1. 2. (Guarantees fast results) (Long term but more profound) Example: www. vv. se (car registration) 145 CONFIDENTIAL
Conclusions The on-line development of public services can be enhanced by: (Guarantees fast results) Coordinated e. Government solutions Advanced back office reorganisations (Long term but more profound) Back office reorganisation 1. 2. • The Crossroads Bank for Social Security: one declaration valid for all administrative authorities Belgium • Finland almost all the Income tax proposal automatically generated through a system of back office electronic data transfer => over 70% of the tax- payers do not need to fill in a tax declaration • Car registration by third parties (car importers, dealers, insurance companies) through direct terminal access to Vehicle Register • Edifact systems for customs declaration countries 146 CONFIDENTIAL
Agenda Web-based Survey on electronic Public Services 1. Context 2. Scope 3. Results Where does Europe stand? 147 CONFIDENTIAL

Back office reorganisation Where does Europe stand? • Take advantage of the quick wins, bring the less complex services online • Master quite well the philosophy and the technological tools of the Internet (client oriented e-portals) • Still a lot of work to do on the more complex services (what happens in the back-offices of the administration? ) • If the back-office is well prepared; bringing services online can be done very quickly • To meet the true aim of the survey, “measure progress”, the survey will be repeated every 6 months e. Government solutions 148 CONFIDENTIAL
ce0105723c0ca9060ddca906a34a7745.ppt