6b6b47ec06a36b23b7c984b26ebfd105.ppt
- Количество слайдов: 35
 E-MAIL SECURITY – Chapter 15 …. for authentication and confidentiality PGP 1. Uses best algorithms as building blocks 2. General purpose 3. Package/source code free 4. Low-cost commercial version 5. No government
E-MAIL SECURITY – Chapter 15 …. for authentication and confidentiality PGP 1. Uses best algorithms as building blocks 2. General purpose 3. Package/source code free 4. Low-cost commercial version 5. No government
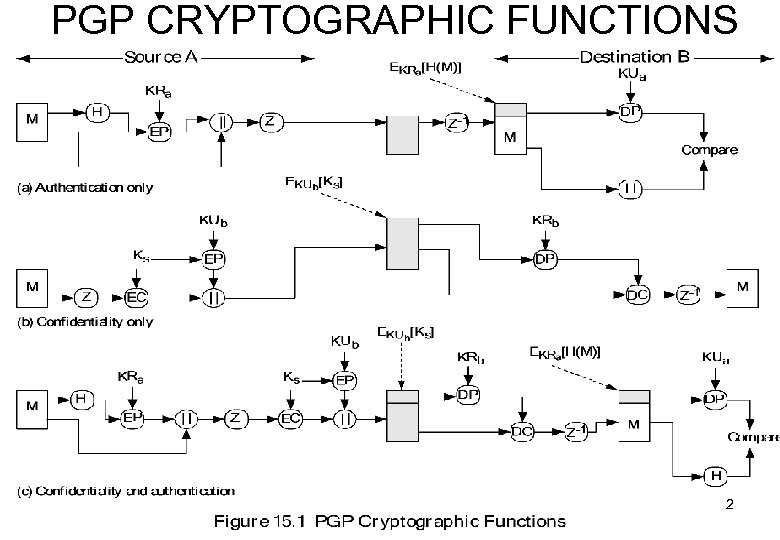 PGP CRYPTOGRAPHIC FUNCTIONS 2
PGP CRYPTOGRAPHIC FUNCTIONS 2
 PGP for……. Authentication Confidentiality Compression e-mail Segmentation
PGP for……. Authentication Confidentiality Compression e-mail Segmentation
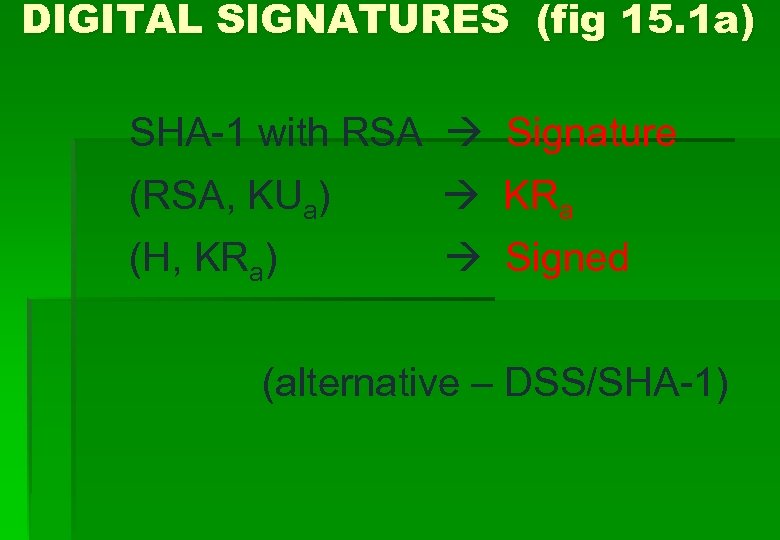 DIGITAL SIGNATURES (fig 15. 1 a) SHA-1 with RSA Signature (RSA, KUa) KRa (H, KRa) Signed (alternative – DSS/SHA-1)
DIGITAL SIGNATURES (fig 15. 1 a) SHA-1 with RSA Signature (RSA, KUa) KRa (H, KRa) Signed (alternative – DSS/SHA-1)
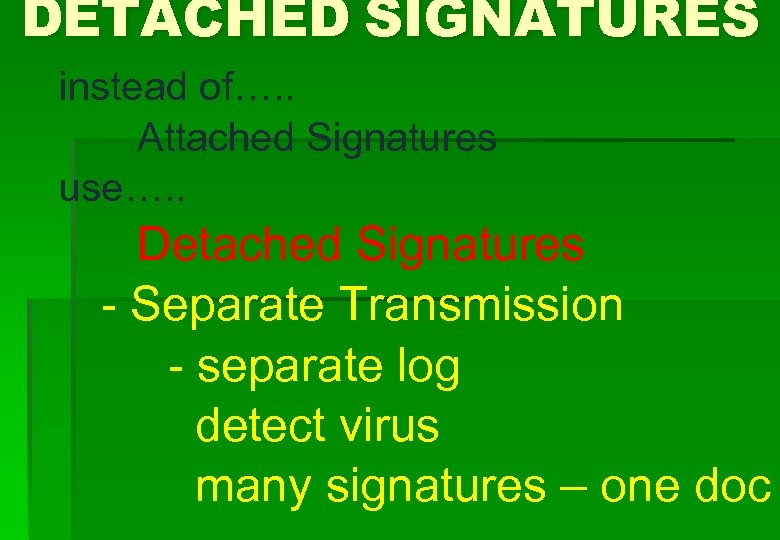 DETACHED SIGNATURES instead of…. . Attached Signatures use…. . Detached Signatures - Separate Transmission - separate log detect virus many signatures – one doc
DETACHED SIGNATURES instead of…. . Attached Signatures use…. . Detached Signatures - Separate Transmission - separate log detect virus many signatures – one doc
 CONFIDENTIALITY (fig 15. 1 b) CAST or IDEA or 3 DES : CFB – 64 Key Distribution: RSA/Diffie-Hellman/El Gamal Symmetric Key used once/message Random 128 -bit key, Ks : key sent with message
CONFIDENTIALITY (fig 15. 1 b) CAST or IDEA or 3 DES : CFB – 64 Key Distribution: RSA/Diffie-Hellman/El Gamal Symmetric Key used once/message Random 128 -bit key, Ks : key sent with message
 SYMMETRIC/PUBLIC COMBINATION • • • Faster than just PUBLIC solves key distribution No protocol – one-time message No handshaking One-time keys strengthen security (weakest link is public)
SYMMETRIC/PUBLIC COMBINATION • • • Faster than just PUBLIC solves key distribution No protocol – one-time message No handshaking One-time keys strengthen security (weakest link is public)
 CONFIDENTIALITY and AUTHENTICATION (fig 15. c) Authentication - plaintext mess. stored third-party can verify signature without needing to know secret key Compression Confidentiality
CONFIDENTIALITY and AUTHENTICATION (fig 15. c) Authentication - plaintext mess. stored third-party can verify signature without needing to know secret key Compression Confidentiality
 COMPRESSION - why? Benefit - efficiency Why, Signature then Compression then Confidentiality ? • Sign Uncompressed Message - off-line storage • No need for single compression algorithm • Encryption after compression is stronger
COMPRESSION - why? Benefit - efficiency Why, Signature then Compression then Confidentiality ? • Sign Uncompressed Message - off-line storage • No need for single compression algorithm • Encryption after compression is stronger
 E-Mail COMPATIBILITY e-mail uses ASCII PGP(8 -bit) ASCII Base-64: 3 x 8 4 x ASCII + CRC 33% Expansion !! (fig 15. 2)
E-Mail COMPATIBILITY e-mail uses ASCII PGP(8 -bit) ASCII Base-64: 3 x 8 4 x ASCII + CRC 33% Expansion !! (fig 15. 2)
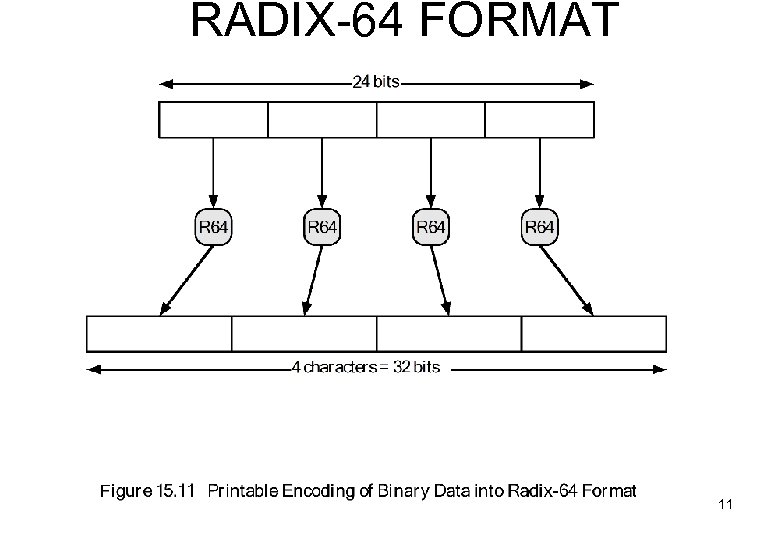 RADIX-64 FORMAT 11
RADIX-64 FORMAT 11
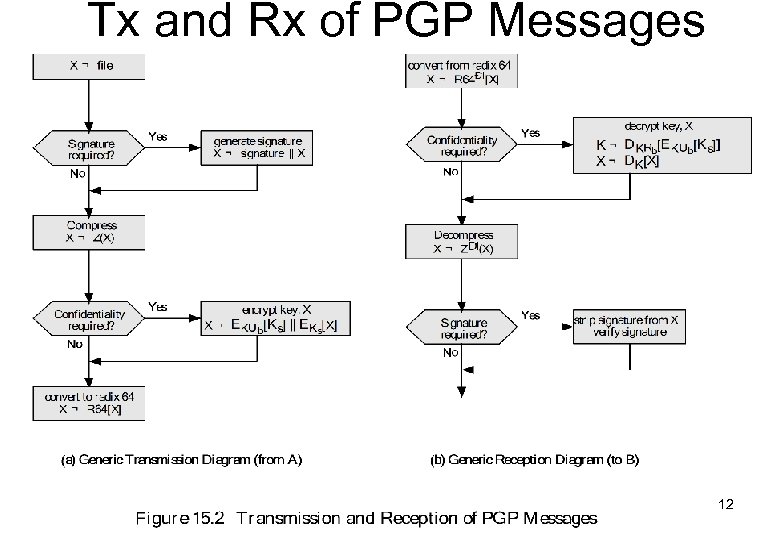 Tx and Rx of PGP Messages 12
Tx and Rx of PGP Messages 12
 SEGMENTATION / REASSEMBLY Max length restriction e. g. internet = 50, 000 x 8 -bits PGP Segments automatically but, One session key, signature/message
SEGMENTATION / REASSEMBLY Max length restriction e. g. internet = 50, 000 x 8 -bits PGP Segments automatically but, One session key, signature/message
 PGP KEYS 1. one-time session : 2. use random number gen. key id 3. 2. public file of key pairs multiple pairs for all users 4. 3. private 5. 4. passphrase-based }
PGP KEYS 1. one-time session : 2. use random number gen. key id 3. 2. public file of key pairs multiple pairs for all users 4. 3. private 5. 4. passphrase-based }
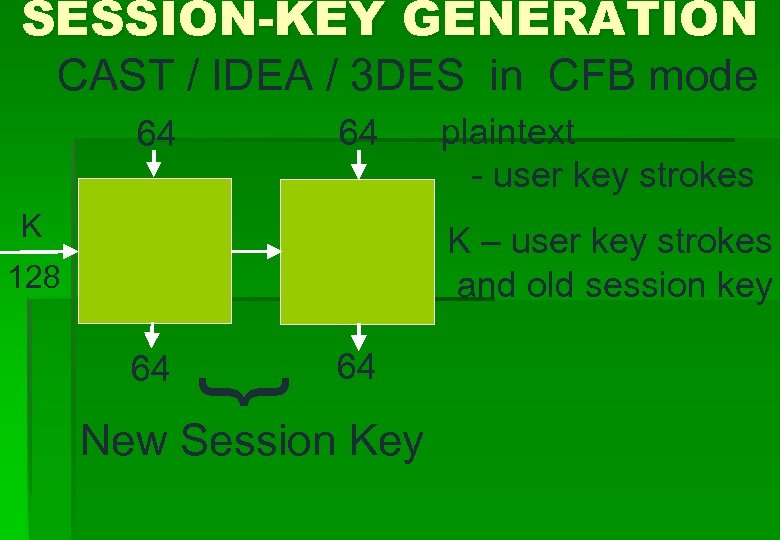 SESSION-KEY GENERATION CAST / IDEA / 3 DES in CFB mode 64 64 K plaintext - user key strokes K – user key strokes and old session key 128 } 64 64 New Session Key
SESSION-KEY GENERATION CAST / IDEA / 3 DES in CFB mode 64 64 K plaintext - user key strokes K – user key strokes and old session key 128 } 64 64 New Session Key
 KEY IDENTIFIERS Which public key? each public key has key ID (least 64 bits) With high prob. , no key ID collision
KEY IDENTIFIERS Which public key? each public key has key ID (least 64 bits) With high prob. , no key ID collision
![MESSAGE FORMAT (fig 15. 3) Message, m [data, filename, timestamp] signature (optional) includes digest MESSAGE FORMAT (fig 15. 3) Message, m [data, filename, timestamp] signature (optional) includes digest](https://present5.com/presentation/6b6b47ec06a36b23b7c984b26ebfd105/image-17.jpg) MESSAGE FORMAT (fig 15. 3) Message, m [data, filename, timestamp] signature (optional) includes digest = hash(m(data)||T) therefore signature is: [T, EKRa(digest), 2 x 8(digest), Key. ID] session key (optional) [key, IDKUb]
MESSAGE FORMAT (fig 15. 3) Message, m [data, filename, timestamp] signature (optional) includes digest = hash(m(data)||T) therefore signature is: [T, EKRa(digest), 2 x 8(digest), Key. ID] session key (optional) [key, IDKUb]
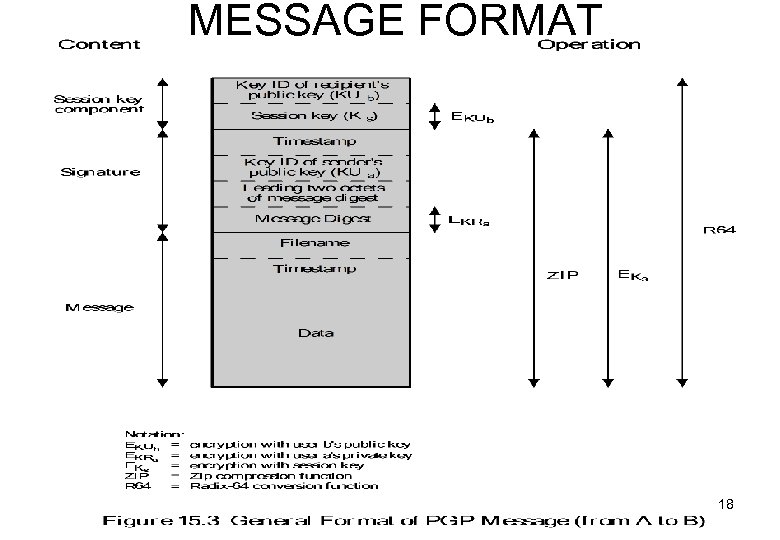 MESSAGE FORMAT 18
MESSAGE FORMAT 18
 KEY RINGS (fig 15. 4) Private Key Ring store public/private pairs of node A Public Key Ring store public keys of all other nodes
KEY RINGS (fig 15. 4) Private Key Ring store public/private pairs of node A Public Key Ring store public keys of all other nodes
 KEY RINGS 20
KEY RINGS 20
 ENCRYPTED PRIVATE KEYS on PRIVATE KEY-RING 1. User passphrase 2. System asks user for passphrase 3. Passphrase 160 -bit hash 4. Ehash(private key) 5. subsequent access requires passphras
ENCRYPTED PRIVATE KEYS on PRIVATE KEY-RING 1. User passphrase 2. System asks user for passphrase 3. Passphrase 160 -bit hash 4. Ehash(private key) 5. subsequent access requires passphras
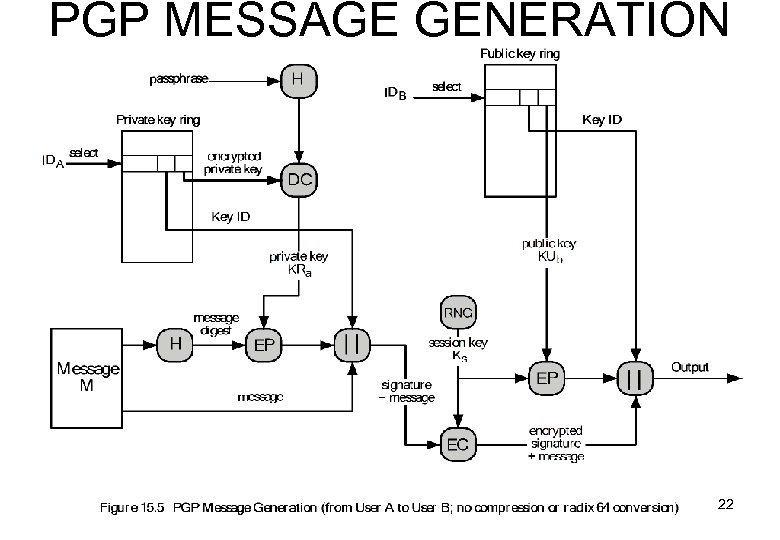 PGP MESSAGE GENERATION 22
PGP MESSAGE GENERATION 22
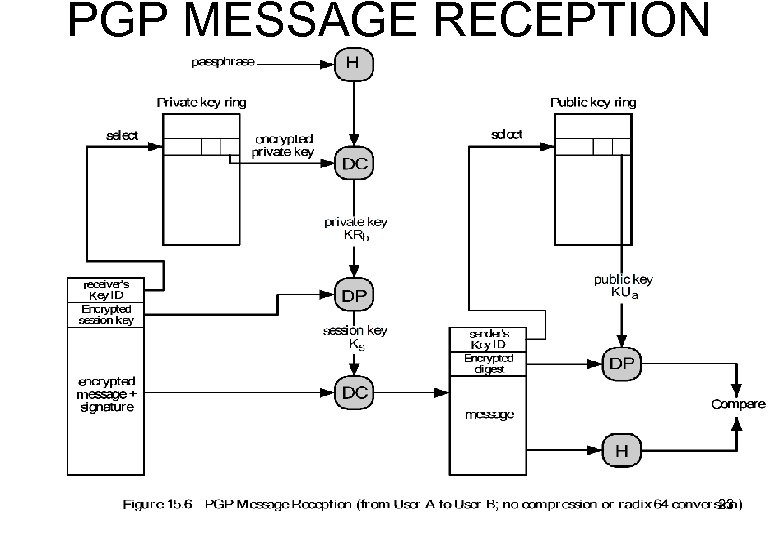 PGP MESSAGE RECEPTION 23
PGP MESSAGE RECEPTION 23
 PUBLIC KEY MANAGEMENT Problem: need tamper-resistant public-keys (e. g. in case A thinks KUc is KUb) Two threats: C A (forge B’s signature) A B (decrypt by C) solution: Key-Revoking
PUBLIC KEY MANAGEMENT Problem: need tamper-resistant public-keys (e. g. in case A thinks KUc is KUb) Two threats: C A (forge B’s signature) A B (decrypt by C) solution: Key-Revoking
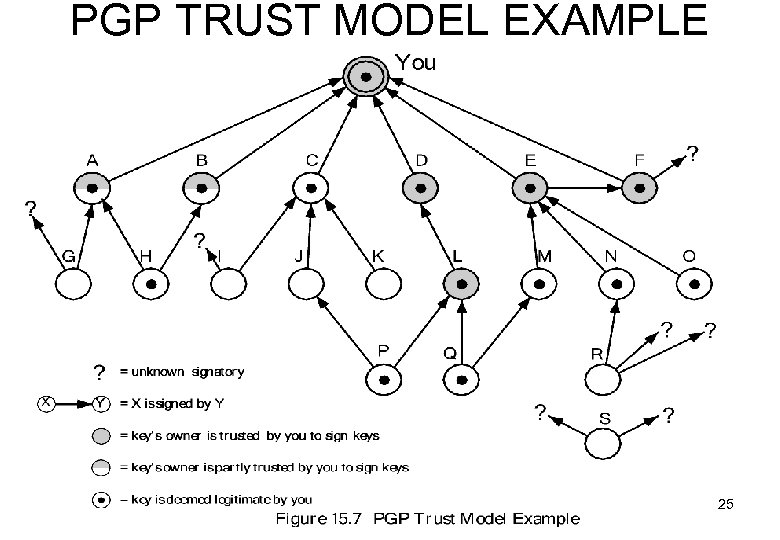 PGP TRUST MODEL EXAMPLE 25
PGP TRUST MODEL EXAMPLE 25
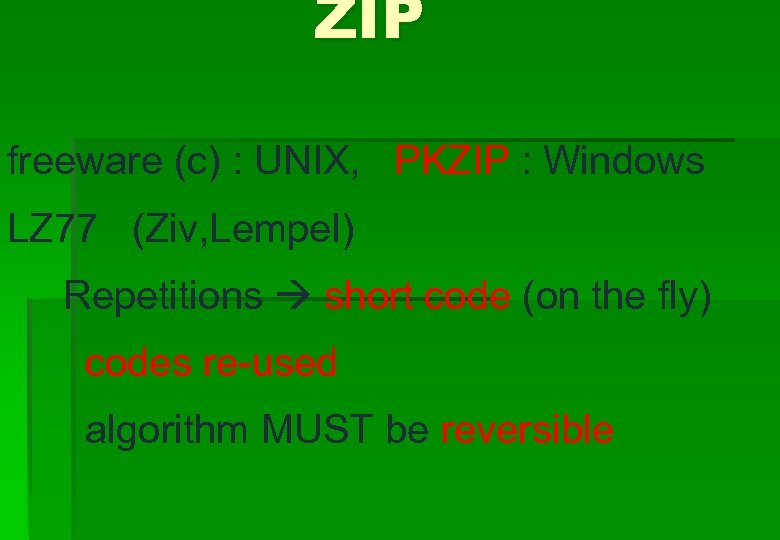 ZIP freeware (c) : UNIX, PKZIP : Windows LZ 77 (Ziv, Lempel) Repetitions short code (on the fly) codes re-used algorithm MUST be reversible
ZIP freeware (c) : UNIX, PKZIP : Windows LZ 77 (Ziv, Lempel) Repetitions short code (on the fly) codes re-used algorithm MUST be reversible
 ZIP (example) (Fig 15. 9) char 9 bits = 1 bit + 8 -bit ascii look for repeated sequences continue until repetition ends e. g. the brown fox 8 -bit pointer, 4 -bit length, 00 12 -bit pointer, 6 -bit length, 01 then ’ jump’ ptr + length, ind compressed to 35 x 9 -bit + two codes = 343 bits Compression Ratio = 424/343 = 1. 24
ZIP (example) (Fig 15. 9) char 9 bits = 1 bit + 8 -bit ascii look for repeated sequences continue until repetition ends e. g. the brown fox 8 -bit pointer, 4 -bit length, 00 12 -bit pointer, 6 -bit length, 01 then ’ jump’ ptr + length, ind compressed to 35 x 9 -bit + two codes = 343 bits Compression Ratio = 424/343 = 1. 24
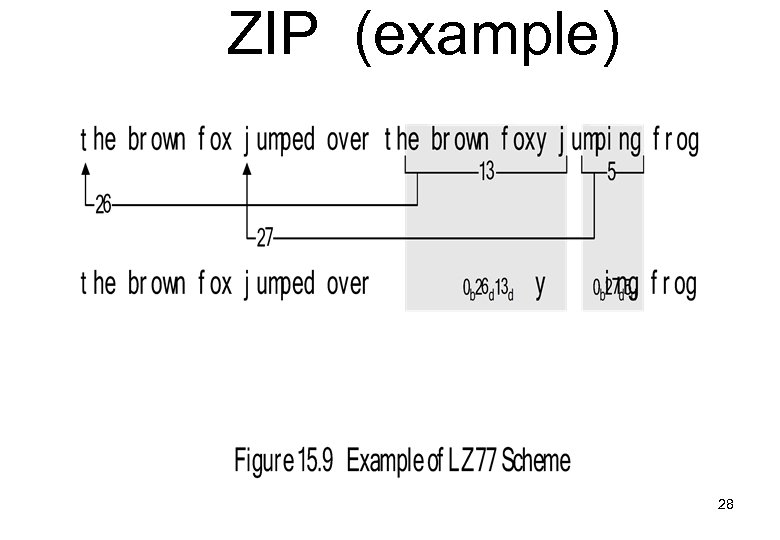 ZIP (example) 28
ZIP (example) 28
 COMPRESSION ALGORITHM 1. Sliding History Buffer – last N chars 2. Look-Ahead Buffer – next N chars 3. Algorithm tries to match chars from 2. to 1 4. if no match, 5. 9 bits LAB 9 bits SHB 6. else if match found output: 7. indicator for length K string, ptr, length 8. 9. K bits LAB K bits SHB
COMPRESSION ALGORITHM 1. Sliding History Buffer – last N chars 2. Look-Ahead Buffer – next N chars 3. Algorithm tries to match chars from 2. to 1 4. if no match, 5. 9 bits LAB 9 bits SHB 6. else if match found output: 7. indicator for length K string, ptr, length 8. 9. K bits LAB K bits SHB
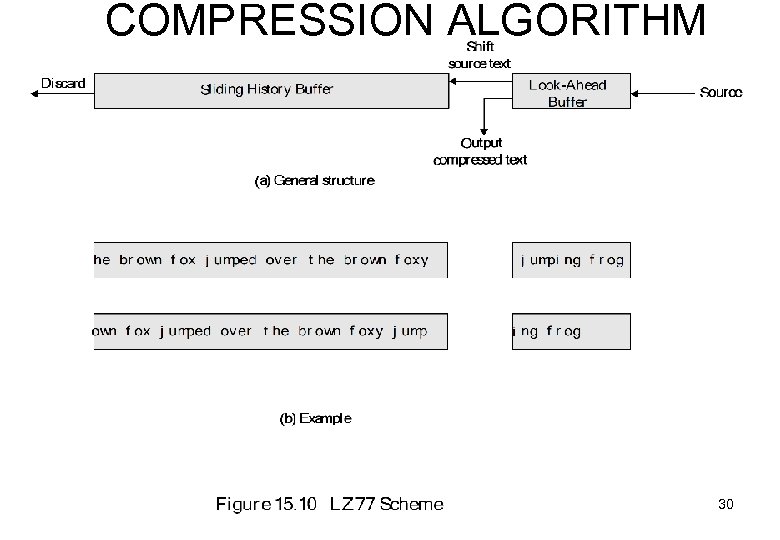 COMPRESSION ALGORITHM 30
COMPRESSION ALGORITHM 30
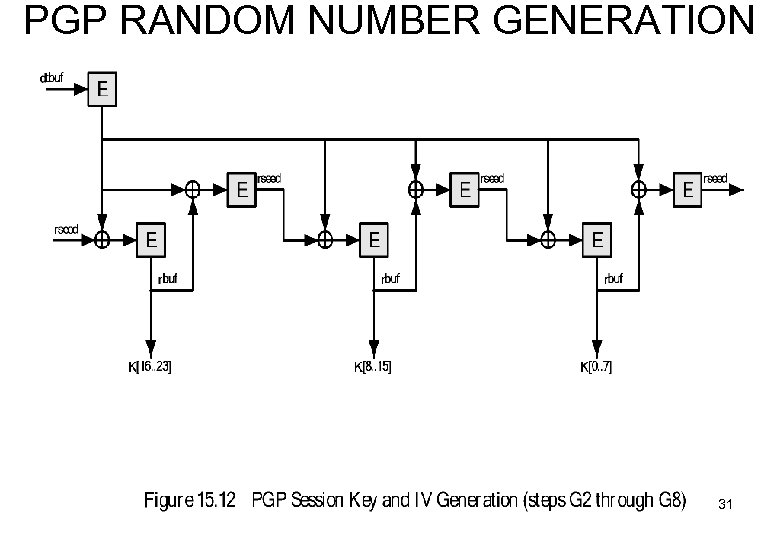 PGP RANDOM NUMBER GENERATION 31
PGP RANDOM NUMBER GENERATION 31
 S/MIME (Secure/Multipurpose Mail Extension) S/MIME - commercial PGP - private S/MIME - based on MIME (designed for RFC 822) RFC 822 - traditional text-mail internet standard Envelope + Contents
S/MIME (Secure/Multipurpose Mail Extension) S/MIME - commercial PGP - private S/MIME - based on MIME (designed for RFC 822) RFC 822 - traditional text-mail internet standard Envelope + Contents
 CRYPTO ALGORITHMS USED in S/MIME (Table 15. 6) Sender/Recipients must agree on common encryption algorithm S/MIME secures MIME entity with signature and/or encryption MIME entity entire message subpart of message
CRYPTO ALGORITHMS USED in S/MIME (Table 15. 6) Sender/Recipients must agree on common encryption algorithm S/MIME secures MIME entity with signature and/or encryption MIME entity entire message subpart of message
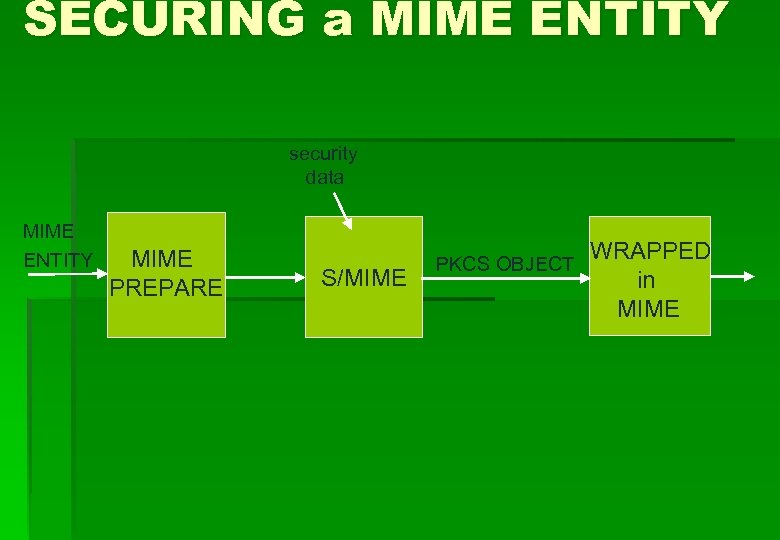 SECURING a MIME ENTITY security data MIME ENTITY MIME PREPARE S/MIME PKCS OBJECT WRAPPED in MIME
SECURING a MIME ENTITY security data MIME ENTITY MIME PREPARE S/MIME PKCS OBJECT WRAPPED in MIME
 S/MIME CERTIFICATE PROCESSING Hybrid of X. 509 certification authority and PGP’s ”web of trust” Configure each client Trusted Keys Certification Revocation List
S/MIME CERTIFICATE PROCESSING Hybrid of X. 509 certification authority and PGP’s ”web of trust” Configure each client Trusted Keys Certification Revocation List


