ba1aebf6c3a034be70f4ec38c1718520.ppt
- Количество слайдов: 58

E-commerce 2014 business. technology. society. tenth edition Kenneth C. Laudon Carol Guercio Traver Copyright © 2014 Pearson Education, Inc. Publishing as Prentice Hall

Chapter 5 E-commerce Security and Payment Systems Copyright © 2014 Pearson Education, Inc. Publishing as Prentice Hall
Class Discussion Cyberwar: MAD 2. 0 n What is the difference between hacking and cyberwar? n Why has cyberwar become more potentially devastating in the past decade? n Why has Google been the target of so many cyberattacks? n Is it possible to find a political solution to MAD 2. 0? Copyright © 2014 Pearson Education, Inc. Publishing as Prentice Hall Slide 5 -3
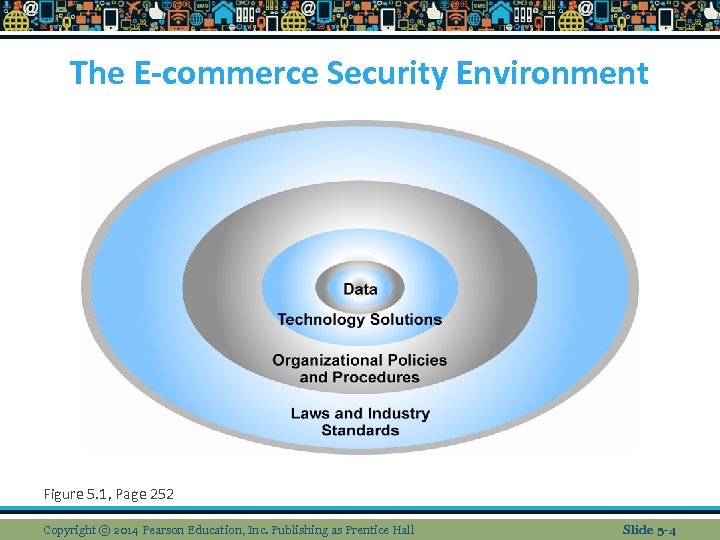
The E-commerce Security Environment Figure 5. 1, Page 252 Copyright © 2014 Pearson Education, Inc. Publishing as Prentice Hall Slide 5 -4

Dimensions of E-commerce Security n n n Integrity ensures that info sent and received has not been altered by unauthorized party Nonrepudiation ability to ensure that participants do not deny (repudiate) their online actions Authenticity ability to identify the person’s identity with whom you are dealing with over the internet Confidentiality authorized to be seen by those who should view it Privacy ability to control who sees your info Availability e-commerce site functions as intended Copyright © 2014 Pearson Education, Inc. Publishing as Prentice Hall Slide 5 -5
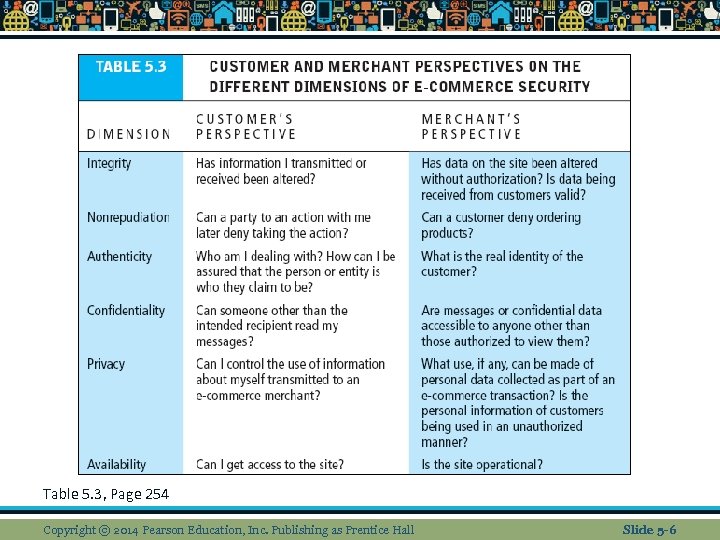
Table 5. 3, Page 254 Copyright © 2014 Pearson Education, Inc. Publishing as Prentice Hall Slide 5 -6

The Tension Between Security and Other Values n Ease of use v The more security measures added, the more difficult a site is to use, and the slower it becomes v Security costs money and too much of it can reduce profitability n Public safety and criminal uses of the Internet v Use of technology by criminals to plan crimes or threaten nation-state Copyright © 2014 Pearson Education, Inc. Publishing as Prentice Hall Slide 5 -7

Security Threats in E-commerce Environment n Three key points of vulnerability in e -commerce environment: 1. Client 2. Server 3. Communications pipeline (Internet communications channels) Copyright © 2014 Pearson Education, Inc. Publishing as Prentice Hall Slide 5 -8
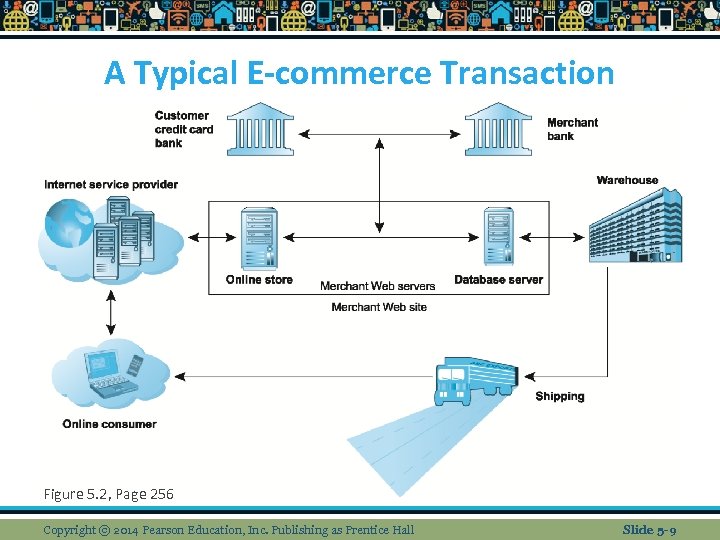
A Typical E-commerce Transaction Figure 5. 2, Page 256 Copyright © 2014 Pearson Education, Inc. Publishing as Prentice Hall Slide 5 -9
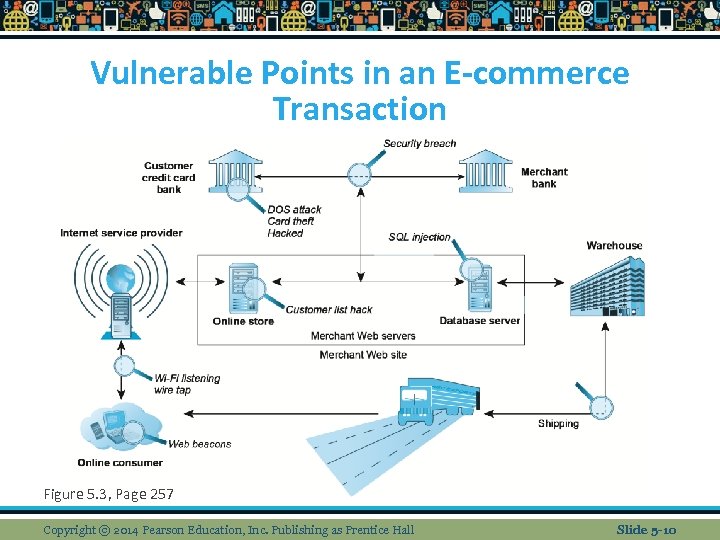
Vulnerable Points in an E-commerce Transaction Figure 5. 3, Page 257 Copyright © 2014 Pearson Education, Inc. Publishing as Prentice Hall Slide 5 -10

Most Common Security Threats in the E-commerce Environment n Malicious code (malware, exploits) v Drive-by downloads malware that comes with a downloaded file the user intentionally or unintentionally request v Viruses v Worms spread from computer to comp without human intervention v Ransomware (scareware) used to solicit money from users by locking up your browser or files and displaying fake notices from FBI or IRS etc v Trojan horses appear benign but is a way to introduce viruses into a computer system v Threats at both client and server levels Slide 5 -11

Most Common Security Threats in the E-commerce Environment n Malicious code (malware, exploits) v Backdoors introduce viruses, worms, etc. that allow an attacker to remotely access a computer v Botnets are a collection of captured bot computers or zombies used to send spam, DDo. S attacks, steal information from computers, and store network traffic for later analysis. v Bots, as in robots, are malicious code that can be covertly installed on a computer when connected to the internet. Once installed, they respond to external commands from the attacker Copyright © 2014 Pearson Education, Inc. Publishing as Prentice Hall Slide 5 -12

n Most Common Security Threats (cont. ) Potentially unwanted programs (PUPs) Example Vista antispyware 2013 infects computers running Vista v Browser parasites changes your computer settings v Adware displays calls for pop-up ads when you visit sites v Spyware may be used to obtain information such as keystrokes, email, IM etc. v n Phishing Social engineering relies on human curiosity, greed, and gullibility to trick users into taking action that results into downloading malware v E-mail scams v Spear-phishing spear phishing messages appear to come from a trusted source v Identity fraud/theft v Copyright © 2014 Pearson Education, Inc. Publishing as Prentice Hall Slide 5 -13

Most Common Security Threats (cont. ) n Hacking v Hackers gain unauthorized access n White hat role is to help identify and fix vulnerabilities n Black hat intent on causing hard n Grey hat breaks in to expose flaws and report them without disrupting the company. They may even try to profit from the event v Crackers have criminal intent v Hacktivist are politically motivated (Green Peace) Copyright © 2014 Pearson Education, Inc. Publishing as Prentice Hall Slide 5 -14

Most Common Security Threats (cont. ) Cybervandalism: v Disrupting, defacing, destroying Web site n Data breach v Losing control over corporate information to outsiders n Copyright © 2014 Pearson Education, Inc. Publishing as Prentice Hall Slide 5 -15

Insight on Business: Class Discussion We Are Legion n What organization and technical failures led to the data breach on the Play. Station Network? n Are there any positive social benefits of hacktivism? n Have you or anyone you know experienced data breaches or cybervandalism? Copyright © 2014 Pearson Education, Inc. Publishing as Prentice Hall Slide 5 -16

Most Common Security Threats (cont. ) n n n Credit card fraud/theft Spoofing involves attempting to hide a true identity by using someone else’s email or IP address Pharming automatically directing a web link to a fake address Spam (junk) Web sites (link farms) promise to offer products but are just full of ads Identity fraud/theft involves unauthorized/illegal use of another person’s data Denial of service (Do. S) attack Hackers flood site with useless traffic to overwhelm network Copyright © 2014 Pearson Education, Inc. Publishing as Prentice Hall Slide 5 -17

Most Common Security Threats (cont. ) Denial of service (Do. S) attack Hackers flood site with useless traffic to overwhelm network n Distributed denial of service (DDo. S) attack uses numerous computers to launch attacks on sites or computers systems. The attack comes from several locations n Copyright © 2014 Pearson Education, Inc. Publishing as Prentice Hall Slide 5 -18

Most Common Security Threats (cont. ) n n n Sniffing, a sniffer is a type of eavesdropping program that monitors information traveling over a network Insider attacks caused by employees Poorly designed server and client software leads to SQL injection attacks by taking advantage of poorly coded applications that fails to validate data entered by web users Zero-Day vulnerability software vulnerability that is reported or unreported but no current fix exists Social network security issues like forgetting to log out, connecting with strangers, exposing too much information Copyright © 2014 Pearson Education, Inc. Publishing as Prentice Hall Slide 5 -19

Most Common Security Threats (cont. ) Mobile platform security issues v Vishing works like phishing but does not always occur over the Internet and is carried out using voice technology. A vishing attack can be conducted by voice email, Vo. IP (voice over IP), or landline or cellular telephone. v Smishing exploits SMS/text messages that may contain links and other personal info that may be exploited v Madware is innocent looking apps containing adware that launches pop-up ads and text messages on you mobile device (mobile + adware = madware) n Cloud security issues example, DDo. S attacks threaten the availability and viability of cloud services n Copyright © 2014 Pearson Education, Inc. Publishing as Prentice Hall Slide 5 -20

Insight on Technology: Class Discussion Think Your Smartphone Is Secure? n What types of threats do smartphones face? n Are there any particular vulnerabilities to this type of device? n Are apps more or less likely to be subject to threats than traditional PC software programs? Copyright © 2014 Pearson Education, Inc. Publishing as Prentice Hall Slide 5 -21

Technology Solutions n Protecting Internet communications v Encryption altering plain text so that it cannot be read by anyone other than the sender & receiver v It provides security for 4 of 6 security dimensions n Integrity by ensuring the messages has not been tampered with n Nonrepudiation by preventing users from denying they sent the message n Authentication by verifying the person’s identity or computer sending the message n Confidentiality by ensuring the message was not read by others Copyright © 2014 Pearson Education, Inc. Publishing as Prentice Hall Slide 5 -22
Types of Encryption Cipher is disguised way of writing; a code where letters of the message are replaced systematically by another letter n Transportation cipher ordering the letters in some systematic way e. g. , reverse order, or 2 letters ahead n Symmetric key both sender and receiver use the same key to encrypt and decrypt the message. The key is sent over a secure line or exchanged in person n Data Encryption Stds developed by IBM and NSA; now we have 128, 192, and 256 bit encryption n v Google coming out with 2048 bit keys Copyright © 2014 Pearson Education, Inc. Publishing as Prentice Hall Slide 5 -23
Symmetric Key Encryption Sender and receiver use same digital key to encrypt and decrypt message v Requires sophisticated mechanisms to securely distribute the secret-key to both parties n Requires different set of keys for each transaction n Strength of encryption n v Length of binary key used to encrypt data Data Encryption Standard (DES) n Advanced Encryption Standard (AES) n Most widely used symmetric key encryption v Uses 128, 192, and 256 -bit encryption keys v n Other standards use keys with up to 2, 048 bits Copyright © 2014 Pearson Education, Inc. Publishing as Prentice Hall Slide 5 -24
Common ways of Sending of Keys n The establishment of symmetric keys can be performed in several ways: n Authenticated Key Agreement (KA) is the ability to construct a key, agree on it, and then validate it. Sending of an (authenticated) encrypted key, also known as key wrapping Derivation from a base key using a Key Derivation Function (KDF), using other data as input, for instance a unique number. If derivation is used for multiple devices it is often called key diversification. Ways to send or exchange keys, v by a previous telephone call v sending a letter v meeting in a pub (handing over a USB stick or other data carrier) Creating a key from key parts held by different persons n n Copyright © 2014 Pearson Education, Inc. Publishing as Prentice Hall Slide 5 -25
Public Key Encryption using Digital Signatures and Hash Digests Hash function is any function that can be used to map data of arbitrary size to data of fixed size. The values returned by a hash function are called hash values, hash codes, digests, or simply hashes. The output is often shorter than the input. n Hash digest of message is sent to recipient along with a message to verify integrity n Hash digest and message encrypted with recipient’s public key n Example of hash algorithm: http: //www. metamorphosite. com/one-wayn hash-encryption-sha 1 -data-software Copyright © 2014 Pearson Education, Inc. Publishing as Prentice Hall Slide 5 -26

Public Key Encryption using Digital Signatures and Hash Digests n Entire cipher text is then encrypted with recipient’s private key — creating digital signature — for authenticity, nonrepudiation n digital signature is a type of electronic signature that encrypts documents with digital codes that are particularly difficult to duplicate n Example of WEP generator: http: //www. andrewscompanies. com/tools/wep. asp Copyright © 2014 Pearson Education, Inc. Publishing as Prentice Hall Slide 5 -27
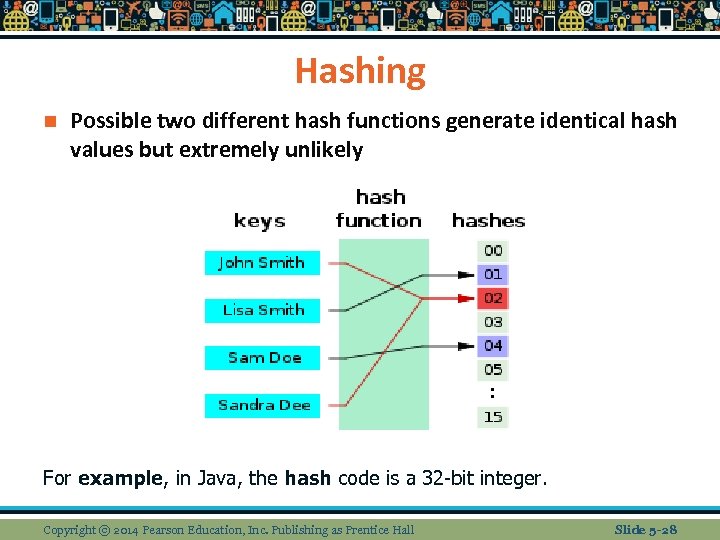
Hashing n Possible two different hash functions generate identical hash values but extremely unlikely For example, in Java, the hash code is a 32 -bit integer. Copyright © 2014 Pearson Education, Inc. Publishing as Prentice Hall Slide 5 -28
Types of Encryption Public Key there are two mathematically related keys, a public key and private key. Private key kept secretly by owner and public key disseminated to the public. Both keys are used to encrypt and decrypt the message. Once the keys are used, they can no longer be used to unencrypt the message. They are one-way irreversible functions. n Hash function creates a fixed length number that replaces the original message, then the hash is used to recreate the message on the recipient side (fig 5. 7) n Digital signature is a signed cipher text sent over the internet n Copyright © 2014 Pearson Education, Inc. Publishing as Prentice Hall Slide 5 -29
Types of Encryption Digital envelope uses symmetric encryption for large docs n Digital certificate (DC) issues by trusted 3 rd party known as certification authority that contains (the subject name, public key, digital cert serial #, exp date, issuance date and digital signature) n There are various types of certs (personal, institutional, web server, software publ, and Certificate Authority (CA)) v Verisign, post office, Fed Reserve issue certs v n Key infrastructure (PKI) when you sign into a secure site you see the “s” or the lock which means the site has a digital certificate issued by a CA Copyright © 2014 Pearson Education, Inc. Publishing as Prentice Hall Slide 5 -30

Technology Solutions n Securing channels of communication v Secure Socket Layer; a secure negotiated session is a client server session in which the URL of the requested doc, its contents, and cookies are encrypted through a series of communication handshakes between computers. A unique symmetric encryption session key is chosen for each session v VPNs allow computers to securely communicate via tunneling by adding invisible encrypted wrappers around messages to hide their contents Slide 5 -31

Technology Solutions n Securing channels of communication n Protecting networks v Firewalls are hard/software that filters comm packets and prevent unauthorized access v They filter traffic based on packets, IP address, type of service http, www, domain name etc v 2 Ways to validate traffic n Packet filters examine whether they are destined for a prohibited port or originate from one n App gateway filters traffic based on the app being requested Copyright © 2014 Pearson Education, Inc. Publishing as Prentice Hall Slide 5 -32

Technology Solutions n Proxy servers are software servers that handle comm by acting as a spokesperson and body guard for the organization. To local computers, proxy servers are known as a gateway, but to external servers known as mail server. Proxy servers sit betw users and back end systems. They may be used to restrict access by employees. n Securing channels of communication v. Protecting networks Slide 5 -33

Technology Solutions n Securing channels of communication v. Protecting networks n Intrusion detection systems IDS monitor traffic looking for patterns or preconfigured rules that may indicate an attack n IPS (prevention) prevents attacks by taking action to block the attack Copyright © 2014 Pearson Education, Inc. Publishing as Prentice Hall Slide 5 -34
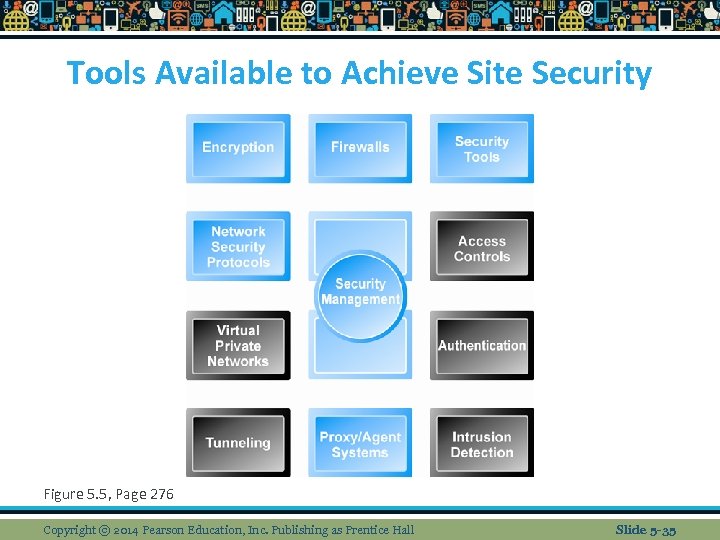
Tools Available to Achieve Site Security Figure 5. 5, Page 276 Copyright © 2014 Pearson Education, Inc. Publishing as Prentice Hall Slide 5 -35
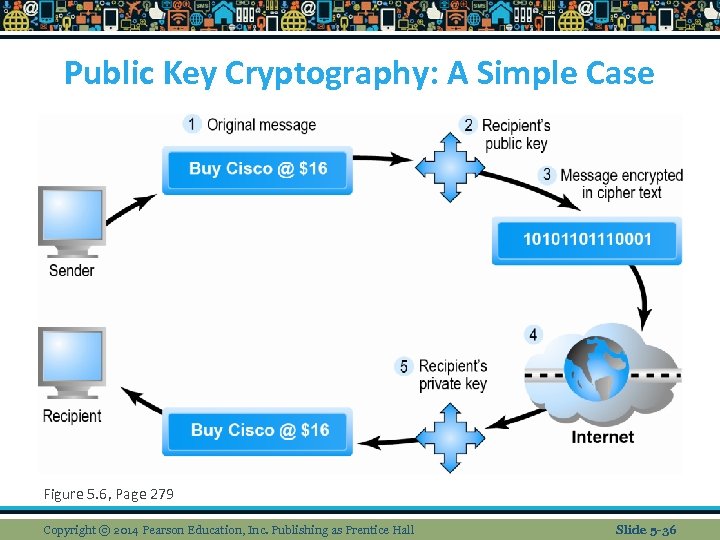
Public Key Cryptography: A Simple Case Figure 5. 6, Page 279 Copyright © 2014 Pearson Education, Inc. Publishing as Prentice Hall Slide 5 -36
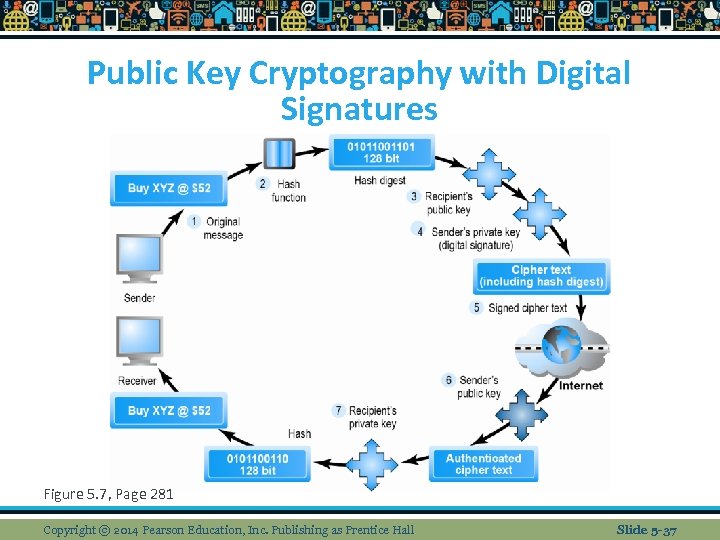
Public Key Cryptography with Digital Signatures Figure 5. 7, Page 281 Copyright © 2014 Pearson Education, Inc. Publishing as Prentice Hall Slide 5 -37
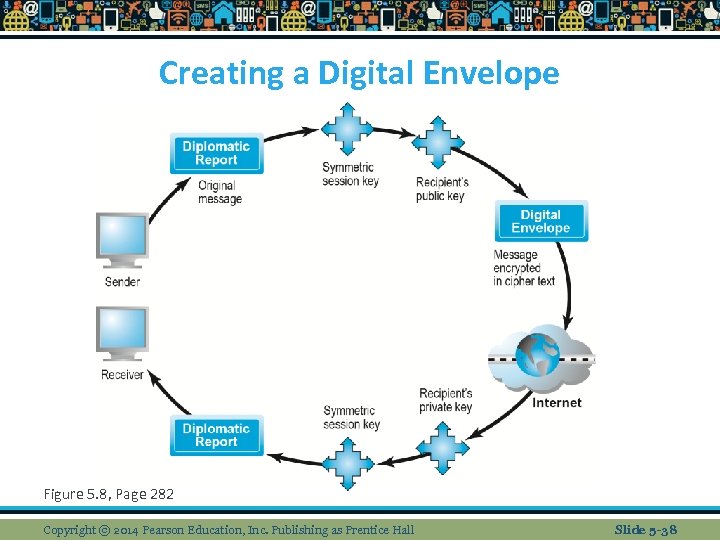
Creating a Digital Envelope Figure 5. 8, Page 282 Copyright © 2014 Pearson Education, Inc. Publishing as Prentice Hall Slide 5 -38
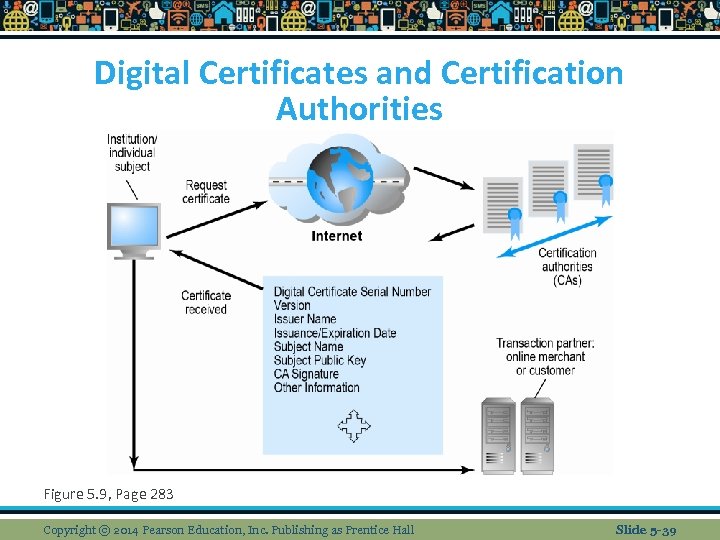
Digital Certificates and Certification Authorities Figure 5. 9, Page 283 Copyright © 2014 Pearson Education, Inc. Publishing as Prentice Hall Slide 5 -39

Limits to Encryption Solutions n Doesn’t protect storage of private key v PKI not effective against insiders, employees v Protection of private keys by individuals may be haphazard n No guarantee that verifying computer of merchant is secure n CAs are unregulated, self-selecting organizations Copyright © 2014 Pearson Education, Inc. Publishing as Prentice Hall Slide 5 -40
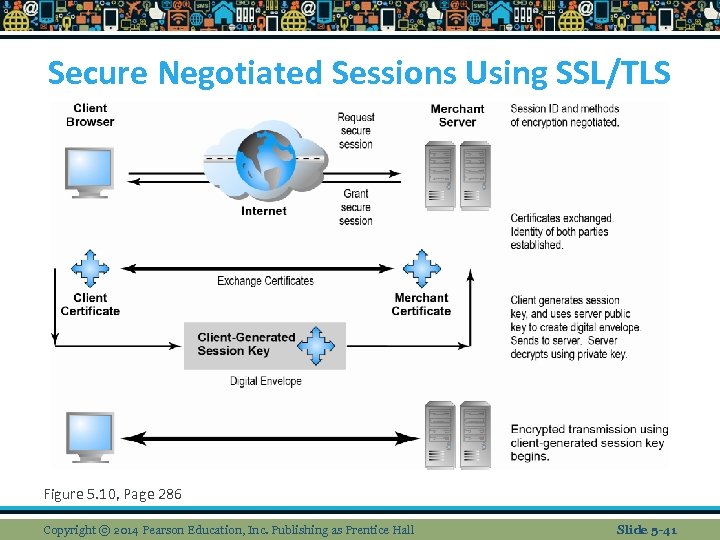
Secure Negotiated Sessions Using SSL/TLS Figure 5. 10, Page 286 Copyright © 2014 Pearson Education, Inc. Publishing as Prentice Hall Slide 5 -41
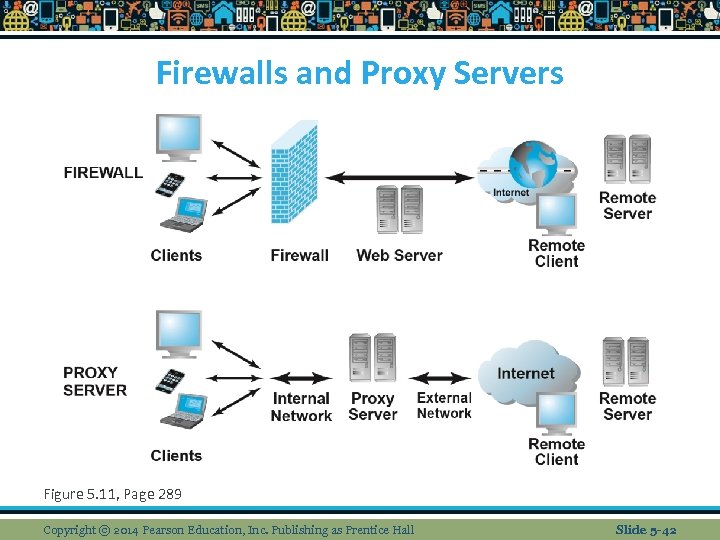
Firewalls and Proxy Servers Figure 5. 11, Page 289 Copyright © 2014 Pearson Education, Inc. Publishing as Prentice Hall Slide 5 -42

Protecting Servers and Clients n Operating system security enhancements v Upgrades, patches n Anti-virus software v Easiest and least expensive way to prevent threats to system integrity v Requires daily updates Copyright © 2014 Pearson Education, Inc. Publishing as Prentice Hall Slide 5 -43

Management Policies, Business Procedures, and Public Laws n Worldwide, companies spend more than $65 billion on security hardware, software, services n Managing risk includes: v Technology v Effective management policies v Public laws and active enforcement Copyright © 2014 Pearson Education, Inc. Publishing as Prentice Hall Slide 5 -44

A Security Plan: Management Policies n Risk assessment n Security policy n Implementation plan v Security organization v Access controls v Authentication procedures, including biometrics v Authorization policies, authorization management systems n Security audit provides ability to audit access logs for security breaches and unauthorized use Copyright © 2014 Pearson Education, Inc. Publishing as Prentice Hall Slide 5 -45
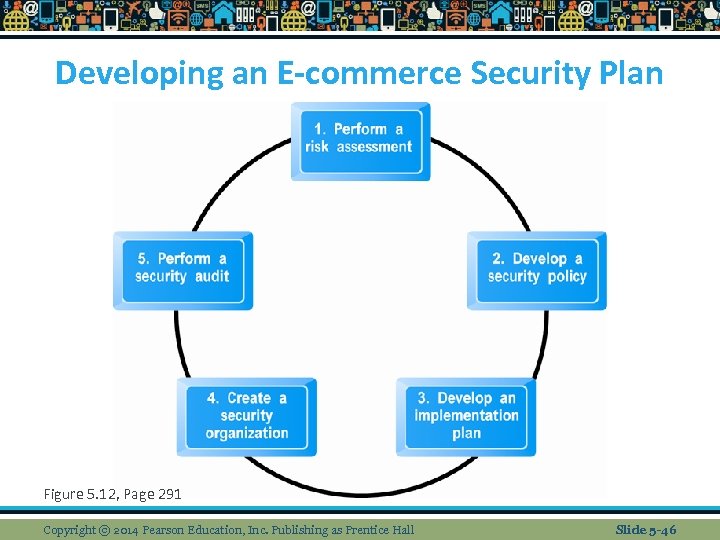
Developing an E-commerce Security Plan Figure 5. 12, Page 291 Copyright © 2014 Pearson Education, Inc. Publishing as Prentice Hall Slide 5 -46

The Role of Laws and Public Policy n Laws that give authorities tools for identifying, tracing, prosecuting cybercriminals: National Information Infrastructure Protection Act of 1996 v USA Patriot Act v Homeland Security Act v n Private and private-public cooperation Community Emergency Response Team (CERT) Coordination Center v US-Computer Emergency Response Team (US-CERT) v n Government policies and controls on encryption software v OECD, G 7/G 8, Council of Europe, Wassener Arrangement Copyright © 2014 Pearson Education, Inc. Publishing as Prentice Hall Slide 5 -47
Types of Payment Systems n Cash v Most common form of payment v Instantly convertible into other forms of value v No float n Checking transfer v Second most common payment form in United States n Credit card v Credit card associations (VISA, Mastercard) v Issuing banks v Processing centers are clearing houses. Copyright © 2014 Pearson Education, Inc. Publishing as Prentice Hall Slide 5 -48
Types of Payment Systems (cont. ) n Stored value v Funds deposited into account, from which funds are paid out or withdrawn as needed (Pay. Pal) v Debit cards, gift certificates v Peer-to-peer payment systems (Pay. Pal) n Accumulating balance v Accounts that accumulate expenditures and to which consumers make period payments v Utility, phone, American Express accounts Copyright © 2014 Pearson Education, Inc. Publishing as Prentice Hall Slide 5 -49

Payment System Stakeholders n Consumers v Low-risk, low-cost, refutable, convenience, reliability n Merchants v Low-risk, low-cost, irrefutable, secure, reliable n Financial intermediaries v Secure, low-risk, maximizing profit n Government regulators v Security, trust, protecting participants and enforcing reporting Copyright © 2014 Pearson Education, Inc. Publishing as Prentice Hall Slide 5 -50

E-commerce Payment Systems n Credit cards v 42% of online payments in 2013 (United States) n Debit cards v 29% online payments in 2013 (United States) n Limitations of online credit card payment v Security, merchant risk v Cost v Social equity Copyright © 2014 Pearson Education, Inc. Publishing as Prentice Hall Slide 5 -51
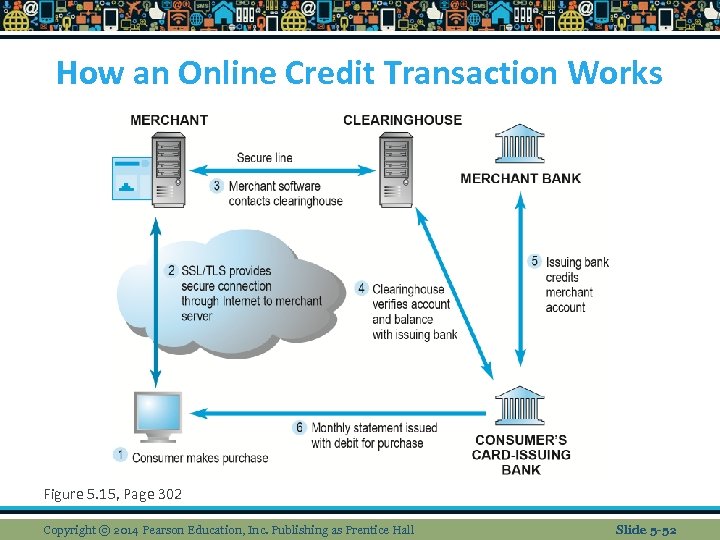
How an Online Credit Transaction Works Figure 5. 15, Page 302 Copyright © 2014 Pearson Education, Inc. Publishing as Prentice Hall Slide 5 -52

Alternative Online Payment Systems n Online stored value systems: v Based on value stored in a consumer’s bank, checking, or credit card account v Example: Pay. Pal n Other alternatives: v Amazon Payments v Google Checkout v Bill Me Later v WUPay, Dwolla, Stripe Copyright © 2014 Pearson Education, Inc. Publishing as Prentice Hall Slide 5 -53
Mobile Payment Systems n Use of mobile phones as payment devices established in Europe, Japan, South Korea n Near field communication (NFC) v Short-range (2”) wireless for sharing data between devices n Expanding in United States v Google Wallet n Mobile app designed to work with NFC chips v Pay. Pal v Square Copyright © 2014 Pearson Education, Inc. Publishing as Prentice Hall Slide 5 -54
Digital Cash and Virtual Currencies n Digital cash v Based on algorithm that generates unique tokens that can be used in “real” world v Example: Bitcoin n Virtual currencies v Circulate within internal virtual world v Example: Linden Dollars in the virtual world called Second Life, Facebook Credits Copyright © 2014 Pearson Education, Inc. Publishing as Prentice Hall Slide 5 -55

Insight on Society: Class Discussion Bitcoin n What are some of the benefits of using a digital currency? n What are the risks involved to the user? n What are the political and economic repercussions of a digital currency? n Have you or anyone you know ever used Bitcoin? Copyright © 2014 Pearson Education, Inc. Publishing as Prentice Hall Slide 5 -56
Electronic Billing Presentment and Payment (EBPP) n Online payment systems for monthly bills n 50% of all bill payments n Two competing EBPP business models: v Biller-direct (dominant model) v Consolidator or 3 rd party like your bank n Both models are supported by EBPP infrastructure providers Copyright © 2014 Pearson Education, Inc. Publishing as Prentice Hall Slide 5 -57

Copyright © 2014 Pearson Education, Inc. Publishing as Prentice Hall Slide 5 -58
ba1aebf6c3a034be70f4ec38c1718520.ppt