382c4e5152c4f0f492b4a87eb9812a5a.ppt
- Количество слайдов: 15
 DOSA: An Architecture for IP Telephony Services Chuck Kalmanek AT&T Labs - Research With grateful acknowledgement of the contributions of the Packet. Cable DQo. S and DCS focus teams, Bill Marshall, Partho Mishra, Doug Nortz, and K. K. Ramakrishnan Presentation at Opensig’ 99 Pittsburgh October 15, 1999 1
DOSA: An Architecture for IP Telephony Services Chuck Kalmanek AT&T Labs - Research With grateful acknowledgement of the contributions of the Packet. Cable DQo. S and DCS focus teams, Bill Marshall, Partho Mishra, Doug Nortz, and K. K. Ramakrishnan Presentation at Opensig’ 99 Pittsburgh October 15, 1999 1
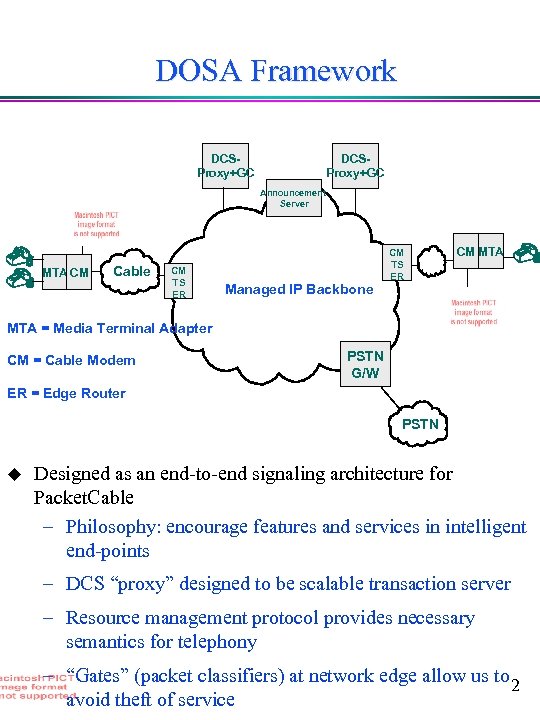 DOSA Framework DCSProxy+GC Announcement Server MTA CM Cable CM TS ER Managed IP Backbone CM TS ER CM MTA = Media Terminal Adapter CM = Cable Modem PSTN G/W ER = Edge Router PSTN u Designed as an end-to-end signaling architecture for Packet. Cable – Philosophy: encourage features and services in intelligent end-points – DCS “proxy” designed to be scalable transaction server – Resource management protocol provides necessary semantics for telephony – “Gates” (packet classifiers) at network edge allow us to 2 avoid theft of service
DOSA Framework DCSProxy+GC Announcement Server MTA CM Cable CM TS ER Managed IP Backbone CM TS ER CM MTA = Media Terminal Adapter CM = Cable Modem PSTN G/W ER = Edge Router PSTN u Designed as an end-to-end signaling architecture for Packet. Cable – Philosophy: encourage features and services in intelligent end-points – DCS “proxy” designed to be scalable transaction server – Resource management protocol provides necessary semantics for telephony – “Gates” (packet classifiers) at network edge allow us to 2 avoid theft of service
 Distributed Call Signaling u Distributed Call Signaling (DCS): SIP w/ carrier class features – takes advantage of SIP feature support in endpoints and proxies – adds resource management, privacy, authorization & billing, LNP u Motivation: service provider must meet user expectations – quality, privacy, existing services are critical needs u Coordination between call signaling and Qo. S control – authorize a call and allocate resources precisely when needed » prevent Call Defects: don’t ring the phone if resources are unavailable » ensure service quality requirements are met (e. g. , don’t clip “Hello”) – provide the ability to bill for usage, without trusting endpoints » prevent Theft Of Service: associate usage recording and 3 resource allocation
Distributed Call Signaling u Distributed Call Signaling (DCS): SIP w/ carrier class features – takes advantage of SIP feature support in endpoints and proxies – adds resource management, privacy, authorization & billing, LNP u Motivation: service provider must meet user expectations – quality, privacy, existing services are critical needs u Coordination between call signaling and Qo. S control – authorize a call and allocate resources precisely when needed » prevent Call Defects: don’t ring the phone if resources are unavailable » ensure service quality requirements are met (e. g. , don’t clip “Hello”) – provide the ability to bill for usage, without trusting endpoints » prevent Theft Of Service: associate usage recording and 3 resource allocation
 Perspective on Service Provider’s Needs u Need for differentiated quality-of-service is fundamental – must support resource reservation and admission control, where needed u u u Allow for authentication and authorization on a call -by-call basis Can’t trust CPE to transmit accurate information or keep it private Need to guarantee privacy and accuracy of feature information – e. g. , Caller ID-block, Calling Name, Forwarding Number » privacy may also imply keeping IP addresses private u Protect the network from fraud and theft of service – critical, given the incentive to bypass network controls u Must operate in large scale, cost-effectively – SIP philosophy: don’t keep state for stable calls in proxies; end-points keep state associated with their calls 4
Perspective on Service Provider’s Needs u Need for differentiated quality-of-service is fundamental – must support resource reservation and admission control, where needed u u u Allow for authentication and authorization on a call -by-call basis Can’t trust CPE to transmit accurate information or keep it private Need to guarantee privacy and accuracy of feature information – e. g. , Caller ID-block, Calling Name, Forwarding Number » privacy may also imply keeping IP addresses private u Protect the network from fraud and theft of service – critical, given the incentive to bypass network controls u Must operate in large scale, cost-effectively – SIP philosophy: don’t keep state for stable calls in proxies; end-points keep state associated with their calls 4
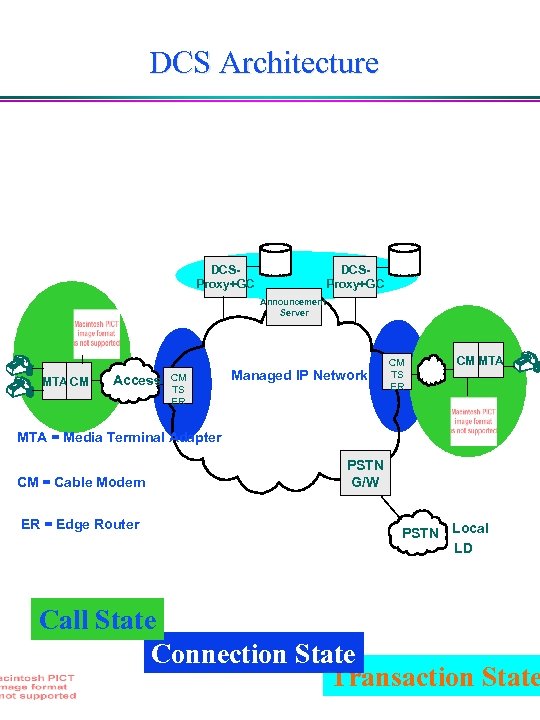 DCS Architecture DCSProxy+GC Announcement Server MTA CM Access CM TS ER Managed IP Network CM TS ER CM MTA = Media Terminal Adapter CM = Cable Modem ER = Edge Router PSTN G/W PSTN Local LD Call State Connection State Transaction State 5
DCS Architecture DCSProxy+GC Announcement Server MTA CM Access CM TS ER Managed IP Network CM TS ER CM MTA = Media Terminal Adapter CM = Cable Modem ER = Edge Router PSTN G/W PSTN Local LD Call State Connection State Transaction State 5
 “Gates” and Edge Routers u “Gates” in edge routers opened for individual calls – call admission control and policing implemented in edge routers » gate is a packet filter in edge router: “allow from this source to this destination” ê for a particular range of traffic parameters, and a particular duration, etc. – however, policy is controlled by the gate controller u Gate controller manipulates a gate after call setup is authorized – setting up gate in advance of reservation request allows a proxy to be stateless u MTA makes a resource reservation request by signaling to edge router – edge router admits the reservation if consistent with gate parameters – edge router generates usage recording events based on reservation state u Accounting info stored at the edge router to generate usage events 6 » opaque info sent to record keeping servers for tracking
“Gates” and Edge Routers u “Gates” in edge routers opened for individual calls – call admission control and policing implemented in edge routers » gate is a packet filter in edge router: “allow from this source to this destination” ê for a particular range of traffic parameters, and a particular duration, etc. – however, policy is controlled by the gate controller u Gate controller manipulates a gate after call setup is authorized – setting up gate in advance of reservation request allows a proxy to be stateless u MTA makes a resource reservation request by signaling to edge router – edge router admits the reservation if consistent with gate parameters – edge router generates usage recording events based on reservation state u Accounting info stored at the edge router to generate usage events 6 » opaque info sent to record keeping servers for tracking
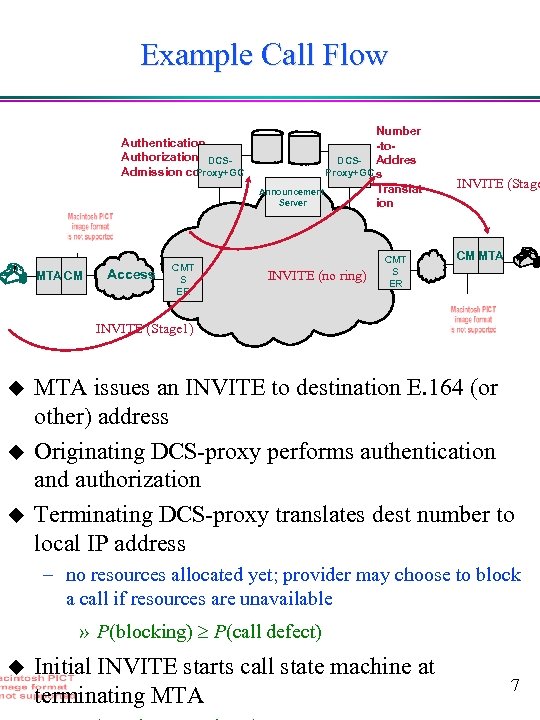 Example Call Flow Authentication, Authorization, DCSAdmission control Proxy+GC MTA CM Access CMT S ER Number -to. DCS- Addres Proxy+GC s Translat Announcement Server ion INVITE (no ring) CMT S ER INVITE (Stage CM MTA INVITE (Stage 1) u u u MTA issues an INVITE to destination E. 164 (or other) address Originating DCS-proxy performs authentication and authorization Terminating DCS-proxy translates dest number to local IP address – no resources allocated yet; provider may choose to block a call if resources are unavailable » P(blocking) P(call defect) u Initial INVITE starts call state machine at terminating MTA 7
Example Call Flow Authentication, Authorization, DCSAdmission control Proxy+GC MTA CM Access CMT S ER Number -to. DCS- Addres Proxy+GC s Translat Announcement Server ion INVITE (no ring) CMT S ER INVITE (Stage CM MTA INVITE (Stage 1) u u u MTA issues an INVITE to destination E. 164 (or other) address Originating DCS-proxy performs authentication and authorization Terminating DCS-proxy translates dest number to local IP address – no resources allocated yet; provider may choose to block a call if resources are unavailable » P(blocking) P(call defect) u Initial INVITE starts call state machine at terminating MTA 7
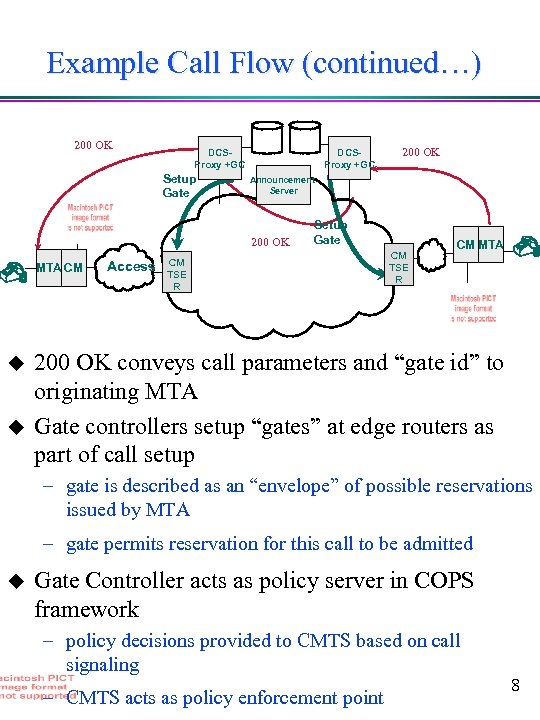 Example Call Flow (continued…) 200 OK DCSProxy +GC Setup Gate DCSProxy +GC Announcement Server 200 OK MTA CM u u Access 200 OK Setup Gate CM TSE R CM MTA 200 OK conveys call parameters and “gate id” to originating MTA Gate controllers setup “gates” at edge routers as part of call setup – gate is described as an “envelope” of possible reservations issued by MTA – gate permits reservation for this call to be admitted u Gate Controller acts as policy server in COPS framework – policy decisions provided to CMTS based on call signaling – CMTS acts as policy enforcement point 8
Example Call Flow (continued…) 200 OK DCSProxy +GC Setup Gate DCSProxy +GC Announcement Server 200 OK MTA CM u u Access 200 OK Setup Gate CM TSE R CM MTA 200 OK conveys call parameters and “gate id” to originating MTA Gate controllers setup “gates” at edge routers as part of call setup – gate is described as an “envelope” of possible reservations issued by MTA – gate permits reservation for this call to be admitted u Gate Controller acts as policy server in COPS framework – policy decisions provided to CMTS based on call signaling – CMTS acts as policy enforcement point 8
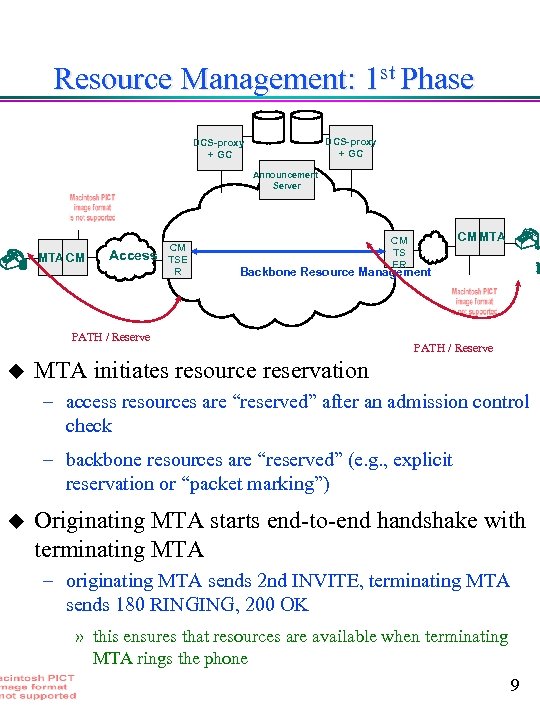 Resource Management: 1 st Phase DCS-proxy + GC Announcement Server MTA CM Access CM TSE R Backbone Resource Management PATH / Reserve u CM MTA CM TS ER PATH / Reserve MTA initiates resource reservation – access resources are “reserved” after an admission control check – backbone resources are “reserved” (e. g. , explicit reservation or “packet marking”) u Originating MTA starts end-to-end handshake with terminating MTA – originating MTA sends 2 nd INVITE, terminating MTA sends 180 RINGING, 200 OK » this ensures that resources are available when terminating MTA rings the phone 9
Resource Management: 1 st Phase DCS-proxy + GC Announcement Server MTA CM Access CM TSE R Backbone Resource Management PATH / Reserve u CM MTA CM TS ER PATH / Reserve MTA initiates resource reservation – access resources are “reserved” after an admission control check – backbone resources are “reserved” (e. g. , explicit reservation or “packet marking”) u Originating MTA starts end-to-end handshake with terminating MTA – originating MTA sends 2 nd INVITE, terminating MTA sends 180 RINGING, 200 OK » this ensures that resources are available when terminating MTA rings the phone 9
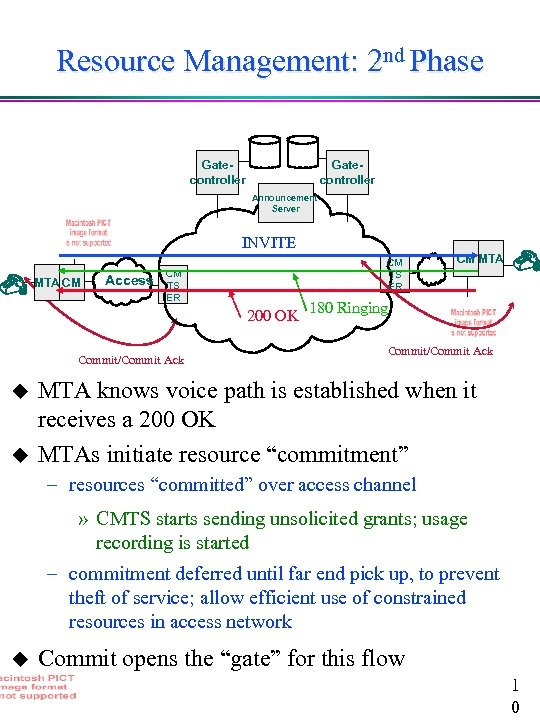 Resource Management: 2 nd Phase Gatecontroller Announcement Server INVITE MTA CM Access CM TS ER 200 OK Commit/Commit Ack u u CM MTA 180 Ringing Commit/Commit Ack MTA knows voice path is established when it receives a 200 OK MTAs initiate resource “commitment” – resources “committed” over access channel » CMTS starts sending unsolicited grants; usage recording is started – commitment deferred until far end pick up, to prevent theft of service; allow efficient use of constrained resources in access network u Commit opens the “gate” for this flow 1 0
Resource Management: 2 nd Phase Gatecontroller Announcement Server INVITE MTA CM Access CM TS ER 200 OK Commit/Commit Ack u u CM MTA 180 Ringing Commit/Commit Ack MTA knows voice path is established when it receives a 200 OK MTAs initiate resource “commitment” – resources “committed” over access channel » CMTS starts sending unsolicited grants; usage recording is started – commitment deferred until far end pick up, to prevent theft of service; allow efficient use of constrained resources in access network u Commit opens the “gate” for this flow 1 0
 Privacy u Want to meet user expectations r. e. accuracy and privacy of info – Calling Identity Delivery allows called party to get info about caller – Calling Identity Delivery Blocking allows calling party to restrict presentation of info (e. g. , calling number, calling name) u SIP supports some privacy mechanisms : From header can be anything chosen by MTA, e. g. , “anonymous” – but, can’t be modified by proxies u DCS-Proxy acts a trusted intermediary – ensures calling identity provided by user agent is valid » user agents are CPE and can’t be trusted – proxy adds calling identity info when not provided by user agent to enable call trace u New header conveys caller identity Dcs-Caller: John Smith; 555 -1212 1 1
Privacy u Want to meet user expectations r. e. accuracy and privacy of info – Calling Identity Delivery allows called party to get info about caller – Calling Identity Delivery Blocking allows calling party to restrict presentation of info (e. g. , calling number, calling name) u SIP supports some privacy mechanisms : From header can be anything chosen by MTA, e. g. , “anonymous” – but, can’t be modified by proxies u DCS-Proxy acts a trusted intermediary – ensures calling identity provided by user agent is valid » user agents are CPE and can’t be trusted – proxy adds calling identity info when not provided by user agent to enable call trace u New header conveys caller identity Dcs-Caller: John Smith; 555 -1212 1 1
 Proxy to Proxy SIP extensions: Billing u Motivation: need to monitor and derive revenue from resource usage – proxies have access to customer info (user identity, services subscribed, payment method) – billing models can be complex, requiring billing info from multiple parties (split charging for call forwarding, etc. ) u Header requirements – need a unique id to associate event records from multiple sources with the call – need a header to carry information about the billable account, record keeping system, etc. – need a header identifying the location where resource usage info is captured 1 2
Proxy to Proxy SIP extensions: Billing u Motivation: need to monitor and derive revenue from resource usage – proxies have access to customer info (user identity, services subscribed, payment method) – billing models can be complex, requiring billing info from multiple parties (split charging for call forwarding, etc. ) u Header requirements – need a unique id to associate event records from multiple sources with the call – need a header to carry information about the billable account, record keeping system, etc. – need a header identifying the location where resource usage info is captured 1 2
 State Header u Motivation – proxies sometimes need state information about an active call » “return call” for a call where the caller wanted privacy » ability to bill correctly for call forwarding (e. g. , international call) » “call trace” where the user wishes to have law enforcement trace a call – but, we want proxies to remain stateless u State Header – proxies stores call state at the endpoints during the initial INVITE exchange » state object is signed and encrypted by proxy; cannot be altered by endpoints – endpoint passes state information to proxies when needed 1 3
State Header u Motivation – proxies sometimes need state information about an active call » “return call” for a call where the caller wanted privacy » ability to bill correctly for call forwarding (e. g. , international call) » “call trace” where the user wishes to have law enforcement trace a call – but, we want proxies to remain stateless u State Header – proxies stores call state at the endpoints during the initial INVITE exchange » state object is signed and encrypted by proxy; cannot be altered by endpoints – endpoint passes state information to proxies when needed 1 3
 OSPS Header (Operator Services Positioning System) u Motivation – PSTN based services like Busy Line Verify and Emergency Interrupt require special treatment – PSTN operator is unaware that the call is to a destination on the IP network – PSTN gateway initiates SIP INVITE to endpoint » this includes the OSPS header – an active endpoint receiving an INVITE containing OSPS : EI header does not return “Busy” u Header Format OSPS = “OSPS” “: ” OSPS-Tag = “BLV” | “EI” 1 4
OSPS Header (Operator Services Positioning System) u Motivation – PSTN based services like Busy Line Verify and Emergency Interrupt require special treatment – PSTN operator is unaware that the call is to a destination on the IP network – PSTN gateway initiates SIP INVITE to endpoint » this includes the OSPS header – an active endpoint receiving an INVITE containing OSPS : EI header does not return “Busy” u Header Format OSPS = “OSPS” “: ” OSPS-Tag = “BLV” | “EI” 1 4
 Unique Contributions and Status u u DOSA introduced the concept of integrating Qo. S with call signaling protocol DCS call signaling allows use of end-point intelligence to support new services and integration with other applications Dynamic Qo. S provides common underlying framework of Qo. S for call signaling protocols Two phase Reserve/Commit for managing resources – provides semantics that resources are available when phone rings, without billing for ringing u Gates for each call: allows provider to manage access to resources – ensures that users who want toll quality go through network proxies – avoid theft of service with careful coordination between signaling and Qo. S u DCS proxies not required to be involved throughout call 1 – simple transaction processor; less stringent reliability 5
Unique Contributions and Status u u DOSA introduced the concept of integrating Qo. S with call signaling protocol DCS call signaling allows use of end-point intelligence to support new services and integration with other applications Dynamic Qo. S provides common underlying framework of Qo. S for call signaling protocols Two phase Reserve/Commit for managing resources – provides semantics that resources are available when phone rings, without billing for ringing u Gates for each call: allows provider to manage access to resources – ensures that users who want toll quality go through network proxies – avoid theft of service with careful coordination between signaling and Qo. S u DCS proxies not required to be involved throughout call 1 – simple transaction processor; less stringent reliability 5


