fad25f1c41225f62af540a9d078a6634.ppt
- Количество слайдов: 16
 doc. : IEEE 802. 11 -12/0041 r 1 Jan 2012 Performance Analysis of 802. 11 authentication and authorization • Date: 2011 -11 -15 Authors: Name Affiliations Robert Sun; Yunbo Li; Edward Au; Phillip Barber Suite 400, 303 Terry Fox Huawei Technologies Drive, Kanata, Ontario Co. , Ltd. K 2 K 3 J 1 Submission Address Slide 1 Phone email +1 613 2871948 Rob. sun@huawei. com Rob Sun etc, Huawei.
doc. : IEEE 802. 11 -12/0041 r 1 Jan 2012 Performance Analysis of 802. 11 authentication and authorization • Date: 2011 -11 -15 Authors: Name Affiliations Robert Sun; Yunbo Li; Edward Au; Phillip Barber Suite 400, 303 Terry Fox Huawei Technologies Drive, Kanata, Ontario Co. , Ltd. K 2 K 3 J 1 Submission Address Slide 1 Phone email +1 613 2871948 Rob. sun@huawei. com Rob Sun etc, Huawei.
 doc. : IEEE 802. 11 -12/0041 r 1 Jan 2012 Abstract • This proposal provides analysis of primary delay contributors within RSNA security protocol in accordance with IEEE 802. 11 i. Submission Slide 2 Rob Sun etc, Huawei.
doc. : IEEE 802. 11 -12/0041 r 1 Jan 2012 Abstract • This proposal provides analysis of primary delay contributors within RSNA security protocol in accordance with IEEE 802. 11 i. Submission Slide 2 Rob Sun etc, Huawei.
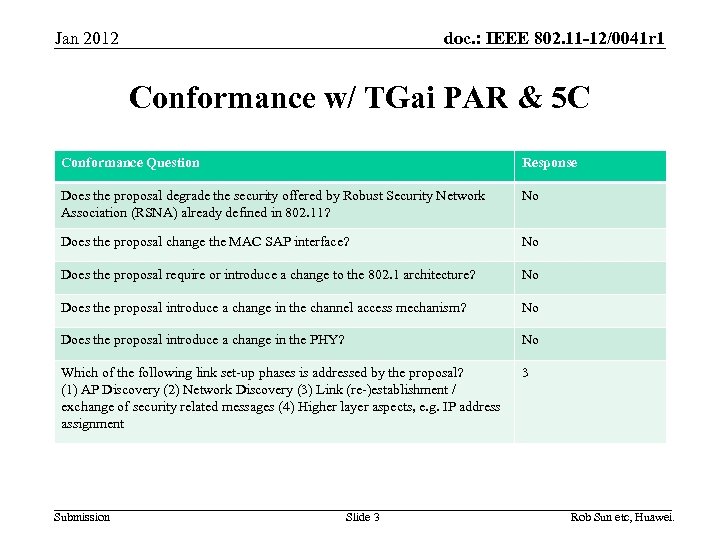 doc. : IEEE 802. 11 -12/0041 r 1 Jan 2012 Conformance w/ TGai PAR & 5 C Conformance Question Response Does the proposal degrade the security offered by Robust Security Network Association (RSNA) already defined in 802. 11? No Does the proposal change the MAC SAP interface? No Does the proposal require or introduce a change to the 802. 1 architecture? No Does the proposal introduce a change in the channel access mechanism? No Does the proposal introduce a change in the PHY? No Which of the following link set-up phases is addressed by the proposal? (1) AP Discovery (2) Network Discovery (3) Link (re-)establishment / exchange of security related messages (4) Higher layer aspects, e. g. IP address assignment 3 Submission Slide 3 Rob Sun etc, Huawei.
doc. : IEEE 802. 11 -12/0041 r 1 Jan 2012 Conformance w/ TGai PAR & 5 C Conformance Question Response Does the proposal degrade the security offered by Robust Security Network Association (RSNA) already defined in 802. 11? No Does the proposal change the MAC SAP interface? No Does the proposal require or introduce a change to the 802. 1 architecture? No Does the proposal introduce a change in the channel access mechanism? No Does the proposal introduce a change in the PHY? No Which of the following link set-up phases is addressed by the proposal? (1) AP Discovery (2) Network Discovery (3) Link (re-)establishment / exchange of security related messages (4) Higher layer aspects, e. g. IP address assignment 3 Submission Slide 3 Rob Sun etc, Huawei.
 doc. : IEEE 802. 11 -12/0041 r 1 Jan 2012 IEEE 802. 11 EAP Authentication and Authorization Delay Contributors • EAP Authentication Phases – EAPOL handshake – EAP specific methods Authentication and Key establishment • • • Key Agreement Key Generation Key Transport – 4 -Way handshake Submission Slide 4 Rob Sun etc, Huawei.
doc. : IEEE 802. 11 -12/0041 r 1 Jan 2012 IEEE 802. 11 EAP Authentication and Authorization Delay Contributors • EAP Authentication Phases – EAPOL handshake – EAP specific methods Authentication and Key establishment • • • Key Agreement Key Generation Key Transport – 4 -Way handshake Submission Slide 4 Rob Sun etc, Huawei.
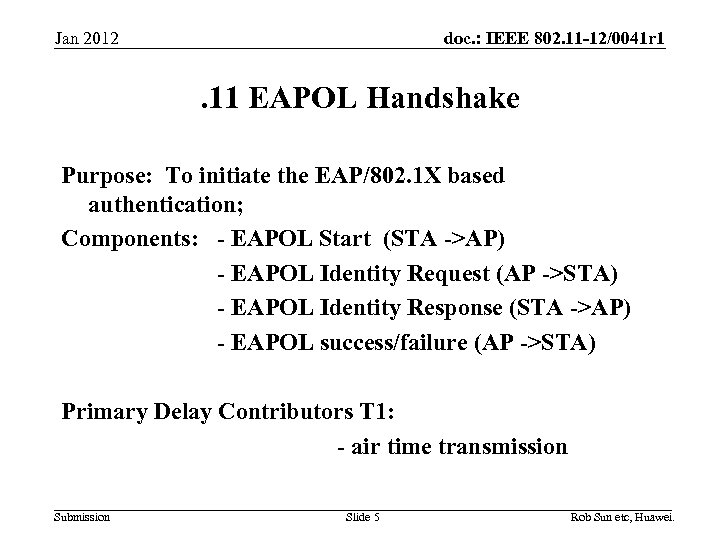 doc. : IEEE 802. 11 -12/0041 r 1 Jan 2012 . 11 EAPOL Handshake Purpose: To initiate the EAP/802. 1 X based authentication; Components: - EAPOL Start (STA ->AP) - EAPOL Identity Request (AP ->STA) - EAPOL Identity Response (STA ->AP) - EAPOL success/failure (AP ->STA) Primary Delay Contributors T 1: - air time transmission Submission Slide 5 Rob Sun etc, Huawei.
doc. : IEEE 802. 11 -12/0041 r 1 Jan 2012 . 11 EAPOL Handshake Purpose: To initiate the EAP/802. 1 X based authentication; Components: - EAPOL Start (STA ->AP) - EAPOL Identity Request (AP ->STA) - EAPOL Identity Response (STA ->AP) - EAPOL success/failure (AP ->STA) Primary Delay Contributors T 1: - air time transmission Submission Slide 5 Rob Sun etc, Huawei.
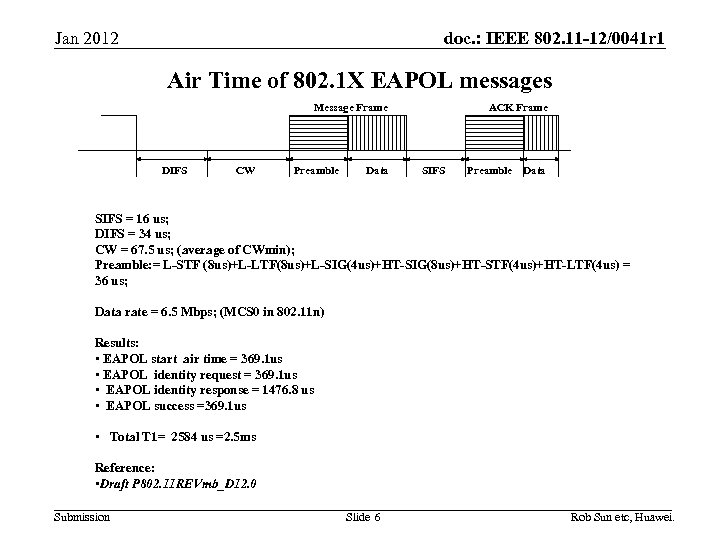 doc. : IEEE 802. 11 -12/0041 r 1 Jan 2012 Air Time of 802. 1 X EAPOL messages Message Frame DIFS CW Preamble Data ACK Frame SIFS Preamble Data SIFS = 16 us; DIFS = 34 us; CW = 67. 5 us; (average of CWmin); Preamble: = L-STF (8 us)+L-LTF(8 us)+L-SIG(4 us)+HT-SIG(8 us)+HT-STF(4 us)+HT-LTF(4 us) = 36 us; Data rate = 6. 5 Mbps; (MCS 0 in 802. 11 n) Results: • EAPOL start air time = 369. 1 us • EAPOL identity request = 369. 1 us • EAPOL identity response = 1476. 8 us • EAPOL success =369. 1 us • Total T 1= 2584 us =2. 5 ms Reference: • Draft P 802. 11 REVmb_D 12. 0 Submission Slide 6 Rob Sun etc, Huawei.
doc. : IEEE 802. 11 -12/0041 r 1 Jan 2012 Air Time of 802. 1 X EAPOL messages Message Frame DIFS CW Preamble Data ACK Frame SIFS Preamble Data SIFS = 16 us; DIFS = 34 us; CW = 67. 5 us; (average of CWmin); Preamble: = L-STF (8 us)+L-LTF(8 us)+L-SIG(4 us)+HT-SIG(8 us)+HT-STF(4 us)+HT-LTF(4 us) = 36 us; Data rate = 6. 5 Mbps; (MCS 0 in 802. 11 n) Results: • EAPOL start air time = 369. 1 us • EAPOL identity request = 369. 1 us • EAPOL identity response = 1476. 8 us • EAPOL success =369. 1 us • Total T 1= 2584 us =2. 5 ms Reference: • Draft P 802. 11 REVmb_D 12. 0 Submission Slide 6 Rob Sun etc, Huawei.
 doc. : IEEE 802. 11 -12/0041 r 1 Jan 2012 EAP Authentication and Key establishment • Purpose : To provide the mutual authentication and RSNA key establishment • Components : EAP Specific Authentication - Different EAP methods are examined for delay comparison Hypothesis : PSK based EAP methods consumes less key establishment time than X. 509 certificate based pair-wise key establishment ( reference: RFC 5216, and FIPS SP 800 56 A). Primary Delay Contributor T 2: - X. 509 certificate verification delay - Key generation delay - Handshake Delay (Air time + Wired Delay) Note 1: All EAP methods are assumed using minimum 4 message handshake as per RFC 5216 Note 2: Wired Delay is non negligible but wasn’t calculated Submission Slide 7 Rob Sun etc, Huawei.
doc. : IEEE 802. 11 -12/0041 r 1 Jan 2012 EAP Authentication and Key establishment • Purpose : To provide the mutual authentication and RSNA key establishment • Components : EAP Specific Authentication - Different EAP methods are examined for delay comparison Hypothesis : PSK based EAP methods consumes less key establishment time than X. 509 certificate based pair-wise key establishment ( reference: RFC 5216, and FIPS SP 800 56 A). Primary Delay Contributor T 2: - X. 509 certificate verification delay - Key generation delay - Handshake Delay (Air time + Wired Delay) Note 1: All EAP methods are assumed using minimum 4 message handshake as per RFC 5216 Note 2: Wired Delay is non negligible but wasn’t calculated Submission Slide 7 Rob Sun etc, Huawei.
 doc. : IEEE 802. 11 -12/0041 r 1 Jan 2012 Performance of various EAP methods and EAP-PSK methods • Testing Environment: Server and Client Side: – – – Submission CPU: PIII 550 Mhz RAM: 256 M OS: Windows XP HD: 40 G Simulation Software: Open. SSL (Open source toolkit for TLS) # of Iterations: 100, 000 Slide 8 Rob Sun etc, Huawei.
doc. : IEEE 802. 11 -12/0041 r 1 Jan 2012 Performance of various EAP methods and EAP-PSK methods • Testing Environment: Server and Client Side: – – – Submission CPU: PIII 550 Mhz RAM: 256 M OS: Windows XP HD: 40 G Simulation Software: Open. SSL (Open source toolkit for TLS) # of Iterations: 100, 000 Slide 8 Rob Sun etc, Huawei.
 doc. : IEEE 802. 11 -12/0041 r 1 Jan 2012 Client and Server processing time • • Both Client and Server processing time including the following operations – Initialization – Key Processing – Signature Processing Tested Candidates: 1) EAP-PSK (RFC 4764) 2) EAP-TLS w/ cipher suites of DHE-DSS-1024 3) EAP-TLS w/ cipher suites of RSA 1024 (PKCS #1) – For DHE-DSS-1024 with mutual authentication – Submission For RSA 1024 with server authentication Slide 9 Rob Sun etc, Huawei.
doc. : IEEE 802. 11 -12/0041 r 1 Jan 2012 Client and Server processing time • • Both Client and Server processing time including the following operations – Initialization – Key Processing – Signature Processing Tested Candidates: 1) EAP-PSK (RFC 4764) 2) EAP-TLS w/ cipher suites of DHE-DSS-1024 3) EAP-TLS w/ cipher suites of RSA 1024 (PKCS #1) – For DHE-DSS-1024 with mutual authentication – Submission For RSA 1024 with server authentication Slide 9 Rob Sun etc, Huawei.
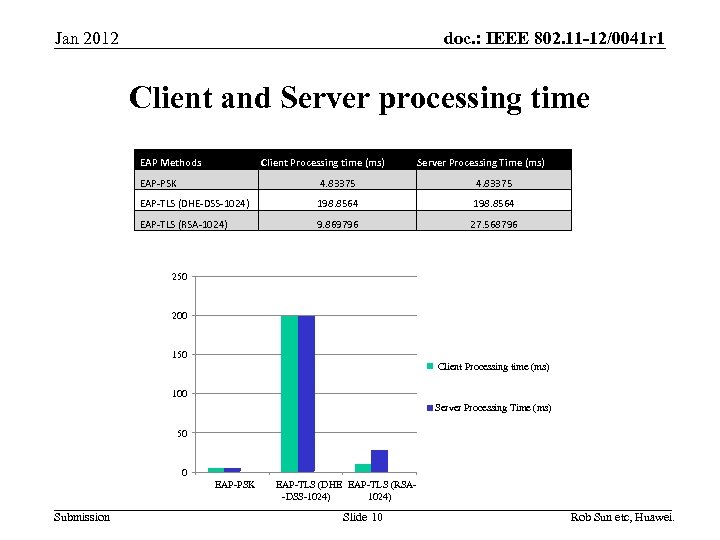 doc. : IEEE 802. 11 -12/0041 r 1 Jan 2012 Client and Server processing time EAP Methods Client Processing time (ms) Server Processing Time (ms) EAP-PSK 4. 83375 EAP-TLS (DHE-DSS-1024) 198. 8564 EAP-TLS (RSA-1024) 9. 869796 27. 568796 250 200 150 Client Processing time (ms) 100 Server Processing Time (ms) 50 0 EAP-PSK Submission EAP-TLS (DHE EAP-TLS (RSA-DSS-1024) Slide 10 Rob Sun etc, Huawei.
doc. : IEEE 802. 11 -12/0041 r 1 Jan 2012 Client and Server processing time EAP Methods Client Processing time (ms) Server Processing Time (ms) EAP-PSK 4. 83375 EAP-TLS (DHE-DSS-1024) 198. 8564 EAP-TLS (RSA-1024) 9. 869796 27. 568796 250 200 150 Client Processing time (ms) 100 Server Processing Time (ms) 50 0 EAP-PSK Submission EAP-TLS (DHE EAP-TLS (RSA-DSS-1024) Slide 10 Rob Sun etc, Huawei.
 doc. : IEEE 802. 11 -12/0041 r 1 Jan 2012 4 -Way Handshake Processing Time • Purpose: To establish the trust and derive the over-theair session keys between STA and AP • Component: – – Initialization (Nonce generation) MIC calculation KDF function 4 EAPOL key messages • Primary delay contributors T 3: - KDF function - Handshake air time 4 WAY handshake Processing Time (ms) Initialization KDF functions and MIC Air time Total Submission 0. 635518 5. 03574 1. 22 6. 891258 Note: same testing environment Slide 11 Rob Sun etc, Huawei.
doc. : IEEE 802. 11 -12/0041 r 1 Jan 2012 4 -Way Handshake Processing Time • Purpose: To establish the trust and derive the over-theair session keys between STA and AP • Component: – – Initialization (Nonce generation) MIC calculation KDF function 4 EAPOL key messages • Primary delay contributors T 3: - KDF function - Handshake air time 4 WAY handshake Processing Time (ms) Initialization KDF functions and MIC Air time Total Submission 0. 635518 5. 03574 1. 22 6. 891258 Note: same testing environment Slide 11 Rob Sun etc, Huawei.
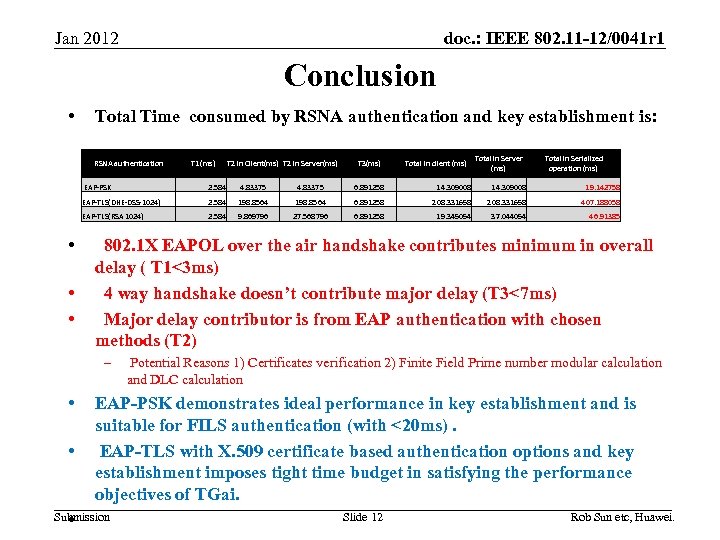 doc. : IEEE 802. 11 -12/0041 r 1 Jan 2012 Conclusion • Total Time consumed by RSNA authentication and key establishment is: RSNA authentication T 1 (ms) T 2 in Client(ms) T 2 in Server(ms) EAP-PSK 2. 584 EAP-TLS(RSA 1024) • • 4. 83375 EAP-TLS(DHE-DSS-1024) • 2. 584 • Total in client (ms) Total in Server (ms) Total in Serialized operation (ms) 4. 83375 6. 891258 14. 309008 19. 142758 198. 8564 6. 891258 208. 331658 407. 188058 9. 869796 27. 568796 6. 891258 19. 345054 37. 044054 46. 91385 802. 1 X EAPOL over the air handshake contributes minimum in overall delay ( T 1<3 ms) 4 way handshake doesn’t contribute major delay (T 3<7 ms) Major delay contributor is from EAP authentication with chosen methods (T 2) – • T 3(ms) Potential Reasons 1) Certificates verification 2) Finite Field Prime number modular calculation and DLC calculation EAP-PSK demonstrates ideal performance in key establishment and is suitable for FILS authentication (with <20 ms). EAP-TLS with X. 509 certificate based authentication options and key establishment imposes tight time budget in satisfying the performance objectives of TGai. Submission • Slide 12 Rob Sun etc, Huawei.
doc. : IEEE 802. 11 -12/0041 r 1 Jan 2012 Conclusion • Total Time consumed by RSNA authentication and key establishment is: RSNA authentication T 1 (ms) T 2 in Client(ms) T 2 in Server(ms) EAP-PSK 2. 584 EAP-TLS(RSA 1024) • • 4. 83375 EAP-TLS(DHE-DSS-1024) • 2. 584 • Total in client (ms) Total in Server (ms) Total in Serialized operation (ms) 4. 83375 6. 891258 14. 309008 19. 142758 198. 8564 6. 891258 208. 331658 407. 188058 9. 869796 27. 568796 6. 891258 19. 345054 37. 044054 46. 91385 802. 1 X EAPOL over the air handshake contributes minimum in overall delay ( T 1<3 ms) 4 way handshake doesn’t contribute major delay (T 3<7 ms) Major delay contributor is from EAP authentication with chosen methods (T 2) – • T 3(ms) Potential Reasons 1) Certificates verification 2) Finite Field Prime number modular calculation and DLC calculation EAP-PSK demonstrates ideal performance in key establishment and is suitable for FILS authentication (with <20 ms). EAP-TLS with X. 509 certificate based authentication options and key establishment imposes tight time budget in satisfying the performance objectives of TGai. Submission • Slide 12 Rob Sun etc, Huawei.
 doc. : IEEE 802. 11 -12/0041 r 1 Jan 2012 Further discussion • Even though the choice of EAP methods are out of scope of IEEE 802 working group, would it be necessary to promote EAP-PSK as the candidate for the FILS authentication specific method? • DHCP and DNS are both the major contributors of the delay, pre-establishment should be ideal for TGai. Submission Slide 13 Rob Sun etc, Huawei.
doc. : IEEE 802. 11 -12/0041 r 1 Jan 2012 Further discussion • Even though the choice of EAP methods are out of scope of IEEE 802 working group, would it be necessary to promote EAP-PSK as the candidate for the FILS authentication specific method? • DHCP and DNS are both the major contributors of the delay, pre-establishment should be ideal for TGai. Submission Slide 13 Rob Sun etc, Huawei.
 doc. : IEEE 802. 11 -12/0041 r 1 Jan 2012 References • • RFC 5216 RFC 4764 RFC 2246 and RFC 2246 -bis-13 Draft P 802. 11 REVmb_D 12. 0 FIPS SP 800 56 A FIP 140 -2 annex C RSA PKCS #1 Submission Slide 14 Rob Sun etc, Huawei.
doc. : IEEE 802. 11 -12/0041 r 1 Jan 2012 References • • RFC 5216 RFC 4764 RFC 2246 and RFC 2246 -bis-13 Draft P 802. 11 REVmb_D 12. 0 FIPS SP 800 56 A FIP 140 -2 annex C RSA PKCS #1 Submission Slide 14 Rob Sun etc, Huawei.
 doc. : IEEE 802. 11 -12/0041 r 1 Jan 2012 Performance of Public-Key Cryptograph • Reference: I. Branovic, R. Giorgi, E. Martinelli, "Memory Performance of Public-Key cryptography Methods in Mobile Environments", ACM SIGARCH Workshop on MEmory performance: DEaling with Applications, systems and architecture (MEDEA-03), New Orleans, LA, USA, Sept. 2003, pp. 24 -31. Submission Slide 15 Rob Sun etc, Huawei.
doc. : IEEE 802. 11 -12/0041 r 1 Jan 2012 Performance of Public-Key Cryptograph • Reference: I. Branovic, R. Giorgi, E. Martinelli, "Memory Performance of Public-Key cryptography Methods in Mobile Environments", ACM SIGARCH Workshop on MEmory performance: DEaling with Applications, systems and architecture (MEDEA-03), New Orleans, LA, USA, Sept. 2003, pp. 24 -31. Submission Slide 15 Rob Sun etc, Huawei.
 doc. : IEEE 802. 11 -12/0041 r 1 Jan 2012 Questions & Comments Submission Slide 16 Rob Sun etc, Huawei.
doc. : IEEE 802. 11 -12/0041 r 1 Jan 2012 Questions & Comments Submission Slide 16 Rob Sun etc, Huawei.


