1fb7e969982acc79ec6b951e76a91a26.ppt
- Количество слайдов: 18
 DNSSec. TLD is signed! What next? V. Dolmatov November 2011
DNSSec. TLD is signed! What next? V. Dolmatov November 2011
 Topics • DNSSec now (Nov. 2011) • Cryptography in DNSSec • DNSSec caveats and pitfalls
Topics • DNSSec now (Nov. 2011) • Cryptography in DNSSec • DNSSec caveats and pitfalls
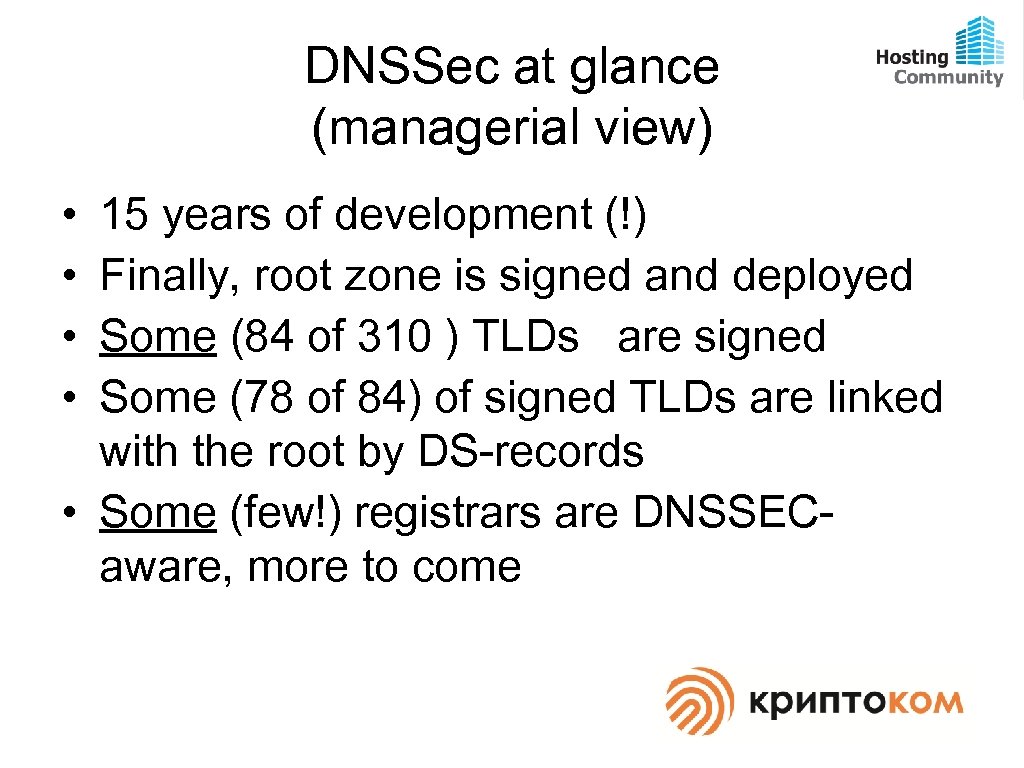 DNSSec at glance (managerial view) • • 15 years of development (!) Finally, root zone is signed and deployed Some (84 of 310 ) TLDs are signed Some (78 of 84) of signed TLDs are linked with the root by DS-records • Some (few!) registrars are DNSSECaware, more to come
DNSSec at glance (managerial view) • • 15 years of development (!) Finally, root zone is signed and deployed Some (84 of 310 ) TLDs are signed Some (78 of 84) of signed TLDs are linked with the root by DS-records • Some (few!) registrars are DNSSECaware, more to come
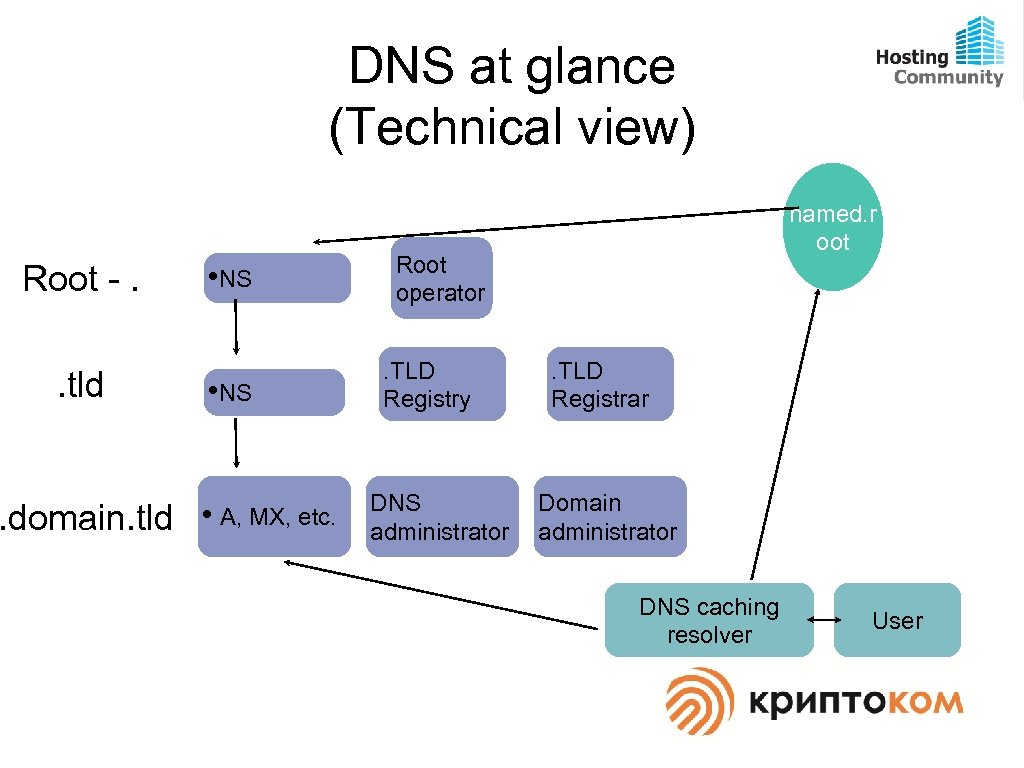 DNS at glance (Technical view) Root -. . tld • NS . domain. tld • A, MX, etc. named. r oot Root operator. TLD Registry DNS administrator . TLD Registrar Domain administrator DNS caching resolver User
DNS at glance (Technical view) Root -. . tld • NS . domain. tld • A, MX, etc. named. r oot Root operator. TLD Registry DNS administrator . TLD Registrar Domain administrator DNS caching resolver User
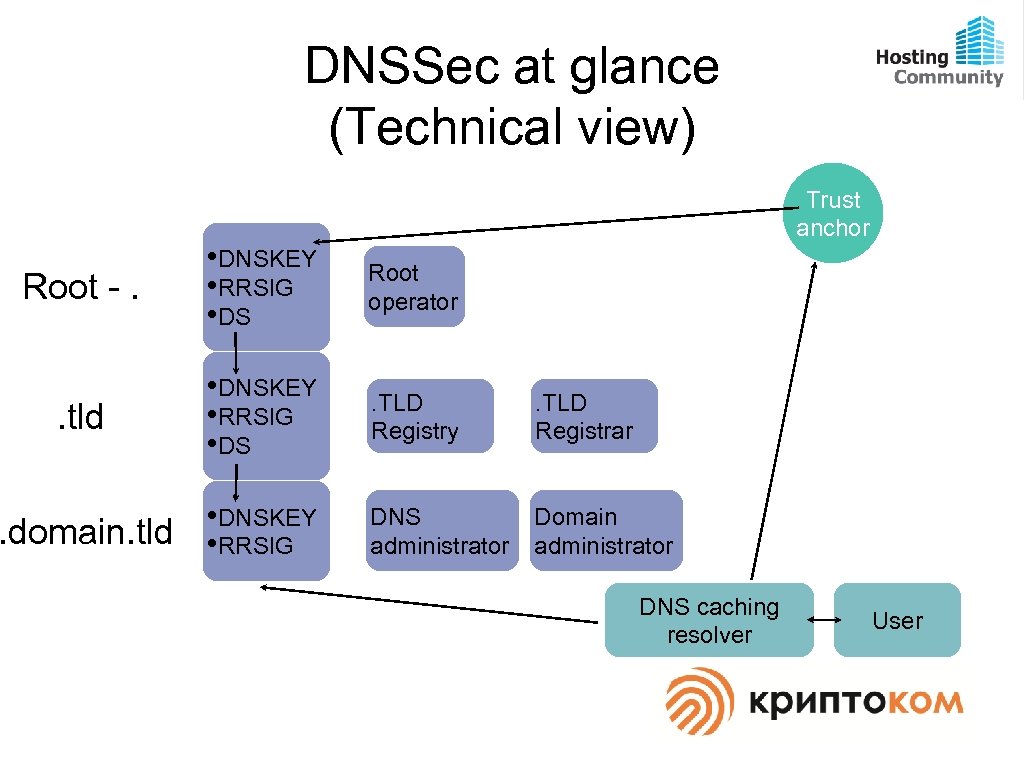 DNSSec at glance (Technical view) Trust anchor Root -. • DNSKEY • RRSIG • DS Root operator . tld • DNSKEY • RRSIG • DS . TLD Registry . TLD Registrar . domain. tld • DNSKEY • RRSIG DNS administrator Domain administrator DNS caching resolver User
DNSSec at glance (Technical view) Trust anchor Root -. • DNSKEY • RRSIG • DS Root operator . tld • DNSKEY • RRSIG • DS . TLD Registry . TLD Registrar . domain. tld • DNSKEY • RRSIG DNS administrator Domain administrator DNS caching resolver User
 Cryptic cryptos • Cryptography is a sensitive field • Cryptography has a lot of specifics • Cryptography is monitored and controlled by governments • There are different specific laws and rules in different countries which should be followed simultaneously
Cryptic cryptos • Cryptography is a sensitive field • Cryptography has a lot of specifics • Cryptography is monitored and controlled by governments • There are different specific laws and rules in different countries which should be followed simultaneously
 GOST cryptography • ГОСТ 28147 -89, ГОСТ Р 34. 10 -2001, ГОСТ Р 34. 11 -94 (open and proved to be reliable and stable) • RFCs 5830, 5831, 5832 • Open and not limited usage in the world • Certified implementations should be used for public services and/or personal data handling in Russia
GOST cryptography • ГОСТ 28147 -89, ГОСТ Р 34. 10 -2001, ГОСТ Р 34. 11 -94 (open and proved to be reliable and stable) • RFCs 5830, 5831, 5832 • Open and not limited usage in the world • Certified implementations should be used for public services and/or personal data handling in Russia
 GOST in DNSSEC • • RFC 5933 – Standard Track RRSIG algorithm code – 12 DS algorithm code – 3 Fully featured DNSSEC set of GOST algorithms
GOST in DNSSEC • • RFC 5933 – Standard Track RRSIG algorithm code – 12 DS algorithm code – 3 Fully featured DNSSEC set of GOST algorithms
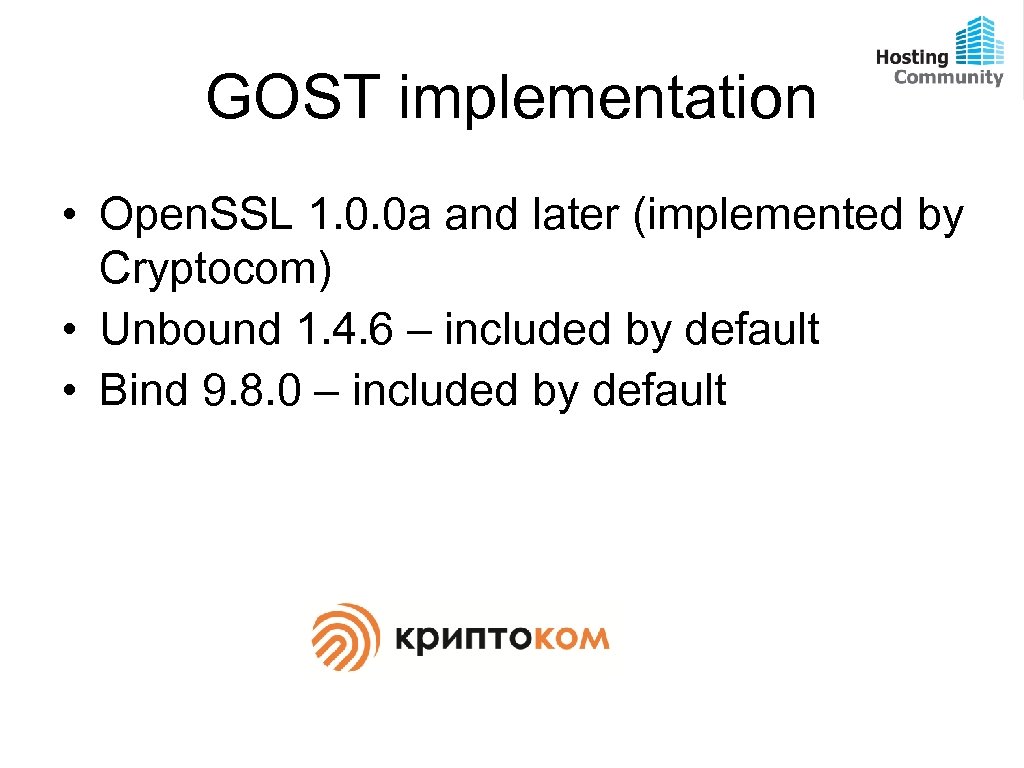 GOST implementation • Open. SSL 1. 0. 0 a and later (implemented by Cryptocom) • Unbound 1. 4. 6 – included by default • Bind 9. 8. 0 – included by default
GOST implementation • Open. SSL 1. 0. 0 a and later (implemented by Cryptocom) • Unbound 1. 4. 6 – included by default • Bind 9. 8. 0 – included by default
 DNSSEC with GOST in the wild • . (root is RSA signed) • TLD. org (is RSA signed) • dnssec-with-gost. org (is GOST signed) • gost. dnssec-with-gost. org (is GOST signed) • rsa. dnssec-with-gost. org (is RSA signed)
DNSSEC with GOST in the wild • . (root is RSA signed) • TLD. org (is RSA signed) • dnssec-with-gost. org (is GOST signed) • gost. dnssec-with-gost. org (is GOST signed) • rsa. dnssec-with-gost. org (is RSA signed)
 RSA-GOST chain – OK!
RSA-GOST chain – OK!
 RSA-GOST-RSA chain – OK!
RSA-GOST-RSA chain – OK!
 How to switch it on? • Unbound 1. 4. 6 + ldns – ready now! • bind 9. 8. 0 - ready now! • Cryptography • Open version – Open. SSL 1. 0. 0 a • Certified version – “Mag. Pro DNS” by Cryptocom • Open. DNSSEC (support moved to 2. x version)
How to switch it on? • Unbound 1. 4. 6 + ldns – ready now! • bind 9. 8. 0 - ready now! • Cryptography • Open version – Open. SSL 1. 0. 0 a • Certified version – “Mag. Pro DNS” by Cryptocom • Open. DNSSEC (support moved to 2. x version)
 DNSSEC in Russia • All main DNSSEC services are GOSTcapable • Certified GOST DNSSEC is also available • Waiting for DNSSEC GOST-capable support in. RU, . SU and. РФ TLDs • Usage in other TLDs is not restricted
DNSSEC in Russia • All main DNSSEC services are GOSTcapable • Certified GOST DNSSEC is also available • Waiting for DNSSEC GOST-capable support in. RU, . SU and. РФ TLDs • Usage in other TLDs is not restricted
 DNSSec Caveats and pitfalls • Wrong feeling of «security» ( «using cryptography makes everything secure» ) • Generating keys and switching DNSSec «on» in given zone does NOT mean automatic increase in the security of this zone • Signing TLD zone and linking it to the root does NOT mean «DNSSec implementation» in this zone • DNSSec demands a LOT of changes in DNS operations and procedures in TLD
DNSSec Caveats and pitfalls • Wrong feeling of «security» ( «using cryptography makes everything secure» ) • Generating keys and switching DNSSec «on» in given zone does NOT mean automatic increase in the security of this zone • Signing TLD zone and linking it to the root does NOT mean «DNSSec implementation» in this zone • DNSSec demands a LOT of changes in DNS operations and procedures in TLD
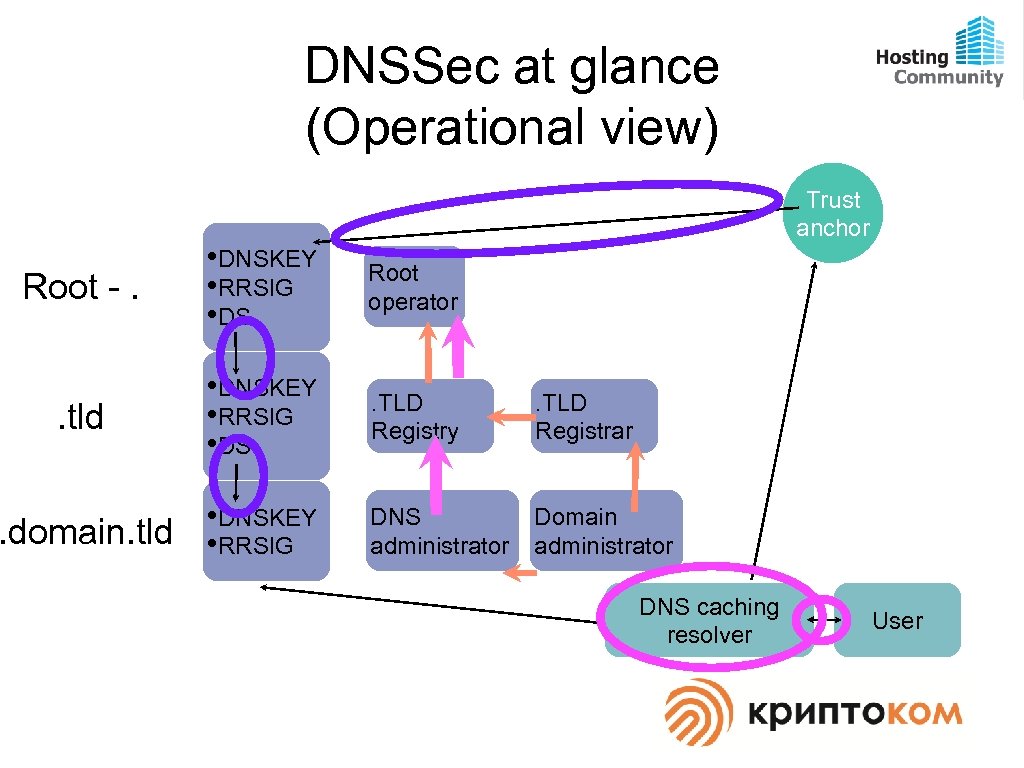 DNSSec at glance (Operational view) Trust anchor Root -. • DNSKEY • RRSIG • DS Root operator . tld • DNSKEY • RRSIG • DS . TLD Registry . TLD Registrar . domain. tld • DNSKEY • RRSIG DNS administrator Domain administrator DNS caching resolver User
DNSSec at glance (Operational view) Trust anchor Root -. • DNSKEY • RRSIG • DS Root operator . tld • DNSKEY • RRSIG • DS . TLD Registry . TLD Registrar . domain. tld • DNSKEY • RRSIG DNS administrator Domain administrator DNS caching resolver User
 DNSSec Caveats and pitfalls (Cont. ) • Wrong feeling of «authenticity» ( «using DNSSec makes everything authentic» ) • DNSSec was designed to solve particular DNS operation problems • Signed DNS-record does NOT add any trust to the resource it points to (Hello, JANE, EFF and other «initiatives» ) • Huge problems with random data sources
DNSSec Caveats and pitfalls (Cont. ) • Wrong feeling of «authenticity» ( «using DNSSec makes everything authentic» ) • DNSSec was designed to solve particular DNS operation problems • Signed DNS-record does NOT add any trust to the resource it points to (Hello, JANE, EFF and other «initiatives» ) • Huge problems with random data sources
 Questions? v. dolmatov@hostcomm. ru
Questions? v. dolmatov@hostcomm. ru


