265d9e4ed44ba4935d5796ef6ef1fee2.ppt
- Количество слайдов: 17
 DNS Security Extension 1
DNS Security Extension 1
 Implication of Kaminsky Attack • Dramatically reduces the complexity and increases the effectiveness of DNS cache poisoning – No longer needs to wait for TTL to expire – The attacker can control when and what queries are issued – A complete domain may be hijacked • Even TLD’s are vulnerable – Only needs 10 secs to succeed 2
Implication of Kaminsky Attack • Dramatically reduces the complexity and increases the effectiveness of DNS cache poisoning – No longer needs to wait for TTL to expire – The attacker can control when and what queries are issued – A complete domain may be hijacked • Even TLD’s are vulnerable – Only needs 10 secs to succeed 2
 Short-term mitigation • Increase the brute-force search space – 16 bits TXID is too small and can be easily brute-forced – Randomize source port number – Use other entropy in DNS messages • e. g. Letter cases in URL 3
Short-term mitigation • Increase the brute-force search space – 16 bits TXID is too small and can be easily brute-forced – Randomize source port number – Use other entropy in DNS messages • e. g. Letter cases in URL 3
 Long-term Solution: DNSSEC • Use public-key signature to authenticate DNS messages – Domain names already form a hierarchy – Parent signs children’s public keys – Resolver only needs to know the root public key to authenticate DNS messages 4
Long-term Solution: DNSSEC • Use public-key signature to authenticate DNS messages – Domain names already form a hierarchy – Parent signs children’s public keys – Resolver only needs to know the root public key to authenticate DNS messages 4
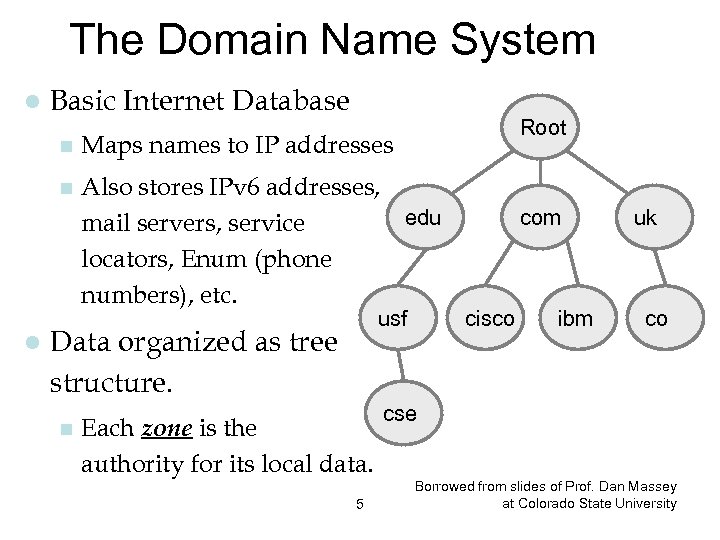 The Domain Name System l Basic Internet Database Root n n l Maps names to IP addresses Also stores IPv 6 addresses, edu mail servers, service locators, Enum (phone numbers), etc. usf Data organized as tree structure. n Each zone is the authority for its local data. 5 com cisco ibm uk co cse Borrowed from slides of Prof. Dan Massey at Colorado State University
The Domain Name System l Basic Internet Database Root n n l Maps names to IP addresses Also stores IPv 6 addresses, edu mail servers, service locators, Enum (phone numbers), etc. usf Data organized as tree structure. n Each zone is the authority for its local data. 5 com cisco ibm uk co cse Borrowed from slides of Prof. Dan Massey at Colorado State University
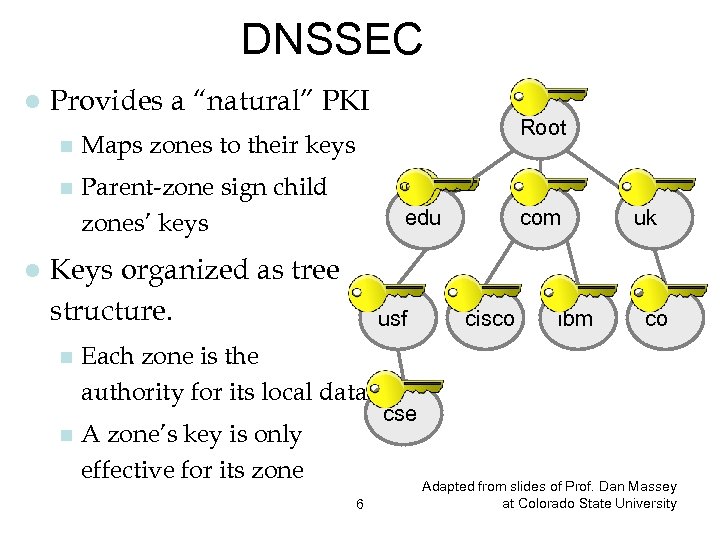 DNSSEC l Provides a “natural” PKI n l Maps zones to their keys n Parent-zone sign child zones’ keys Root edu Keys organized as tree structure. n n usf Each zone is the authority for its local data. A zone’s key is only effective for its zone 6 com cisco ibm uk co cse Adapted from slides of Prof. Dan Massey at Colorado State University
DNSSEC l Provides a “natural” PKI n l Maps zones to their keys n Parent-zone sign child zones’ keys Root edu Keys organized as tree structure. n n usf Each zone is the authority for its local data. A zone’s key is only effective for its zone 6 com cisco ibm uk co cse Adapted from slides of Prof. Dan Massey at Colorado State University
 DNS RR Review • DNS Resource Record (RR) – Can be viewed as tuples of the form
DNS RR Review • DNS Resource Record (RR) – Can be viewed as tuples of the form
 DNSSEC Records • Introduce a new data type: RRSIG name TTL class type value {www. usf. edu. 82310 IN A 131. 247. 182. 171} name TTL class type covered_type {www. usf. edu. 82310 IN RRSIG A … not after 20151216023910 not before 20141216023910 … usf. edu. key name Base 64 encoding of signature} 8
DNSSEC Records • Introduce a new data type: RRSIG name TTL class type value {www. usf. edu. 82310 IN A 131. 247. 182. 171} name TTL class type covered_type {www. usf. edu. 82310 IN RRSIG A … not after 20151216023910 not before 20141216023910 … usf. edu. key name Base 64 encoding of signature} 8
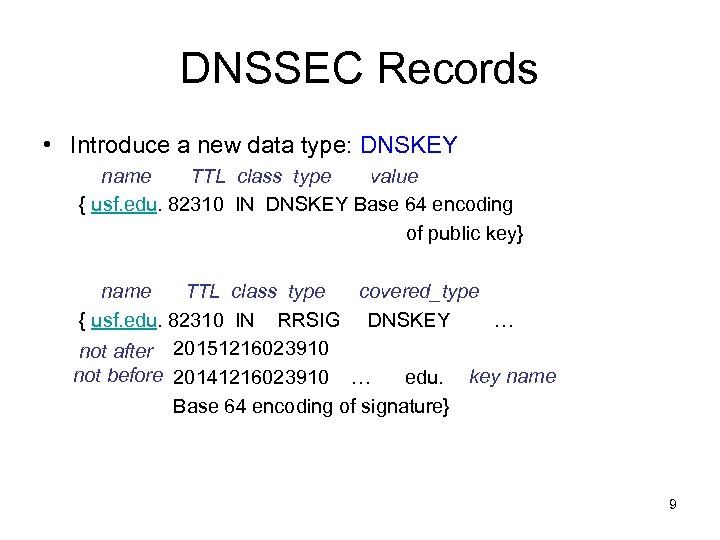 DNSSEC Records • Introduce a new data type: DNSKEY name TTL class type value { usf. edu. 82310 IN DNSKEY Base 64 encoding of public key} name TTL class type covered_type { usf. edu. 82310 IN RRSIG DNSKEY … not after 20151216023910 not before 20141216023910 … edu. key name Base 64 encoding of signature} 9
DNSSEC Records • Introduce a new data type: DNSKEY name TTL class type value { usf. edu. 82310 IN DNSKEY Base 64 encoding of public key} name TTL class type covered_type { usf. edu. 82310 IN RRSIG DNSKEY … not after 20151216023910 not before 20141216023910 … edu. key name Base 64 encoding of signature} 9
 Authenticated Non-existence • What if the usf. edu server is asked the IP address of a non-existent url (e. g. foo. usf. edu)? – Can’t sign non-existence on the fly because the server does not have the private key (why? ) • NSEC record – “The url after eng. usf. edu is global. usf. edu” – Order all the url’s in a zone and sign all the NSEC records ahead of time – Problem: enables zone enumeration – NSEC 3 addresses this concern by using hashes of zone names instead of zone names themselves 10
Authenticated Non-existence • What if the usf. edu server is asked the IP address of a non-existent url (e. g. foo. usf. edu)? – Can’t sign non-existence on the fly because the server does not have the private key (why? ) • NSEC record – “The url after eng. usf. edu is global. usf. edu” – Order all the url’s in a zone and sign all the NSEC records ahead of time – Problem: enables zone enumeration – NSEC 3 addresses this concern by using hashes of zone names instead of zone names themselves 10
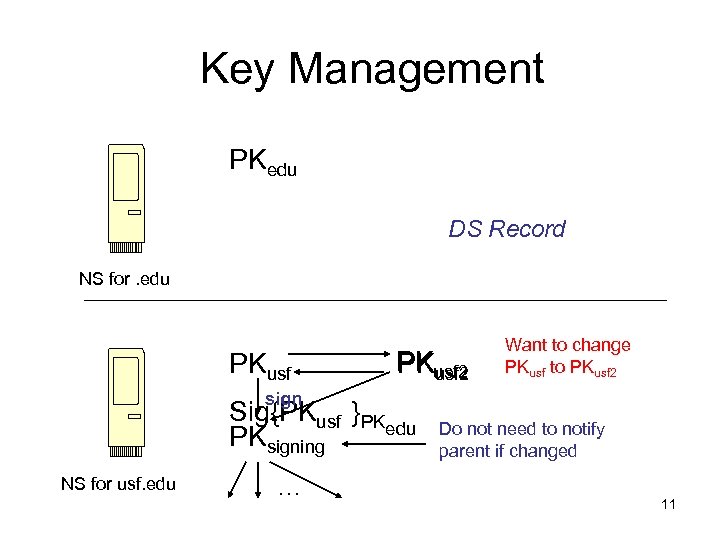 Key Management PKedu DS Record NS for. edu PKusf 2 Want to change PKusf to PKusf 2 sign Sig{PKusf }PK edu PKsigning NS for usf. edu … Do not need to notify parent if changed 11
Key Management PKedu DS Record NS for. edu PKusf 2 Want to change PKusf to PKusf 2 sign Sig{PKusf }PK edu PKsigning NS for usf. edu … Do not need to notify parent if changed 11
 Potential Usage of DNSSEC • If successfully deployed, DNSSEC can serve as a universal Public Key Infrastructure (PKI) – Sign public keys for web sites – Sign public keys for email addresses • Can this really be achieved? – Existing systems like X. 509 have so far failed to provide a universal PKI – DNSSEC has a major difference from X. 509 • Key compromise at a node only affects a subdomain 12
Potential Usage of DNSSEC • If successfully deployed, DNSSEC can serve as a universal Public Key Infrastructure (PKI) – Sign public keys for web sites – Sign public keys for email addresses • Can this really be achieved? – Existing systems like X. 509 have so far failed to provide a universal PKI – DNSSEC has a major difference from X. 509 • Key compromise at a node only affects a subdomain 12
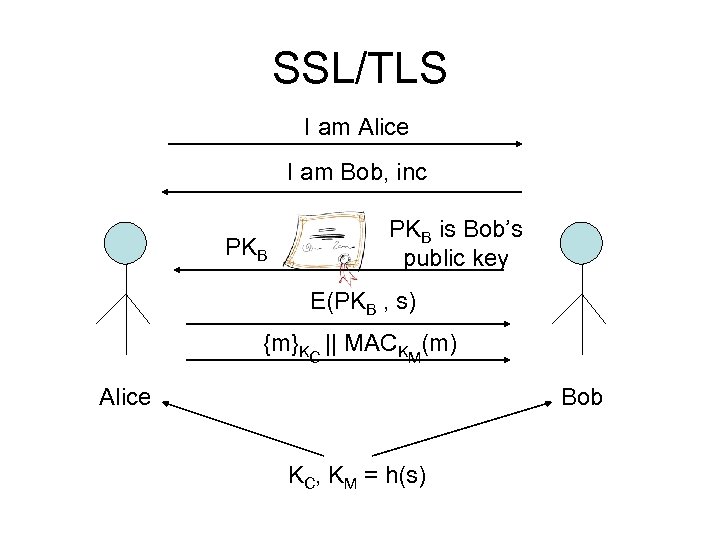 SSL/TLS I am Alice I am Bob, inc PKB is Bob’s public key E(PKB , s) {m}KC || MACKM(m) Alice Bob KC, KM = h(s)
SSL/TLS I am Alice I am Bob, inc PKB is Bob’s public key E(PKB , s) {m}KC || MACKM(m) Alice Bob KC, KM = h(s)
 DNS-based Authentication of Named Entities (DANE) • Use DNSSEC to sign certain statements (DANE records) – The currently proposed DANE records address trust of TLS certificates • TLSA DANE records – Yet another type of DNS resource record (RR) – Three types of statements • CA Constraints • Service Certificate Constraints • Trust Anchor Assertion 14
DNS-based Authentication of Named Entities (DANE) • Use DNSSEC to sign certain statements (DANE records) – The currently proposed DANE records address trust of TLS certificates • TLSA DANE records – Yet another type of DNS resource record (RR) – Three types of statements • CA Constraints • Service Certificate Constraints • Trust Anchor Assertion 14
 Advantages of DANE compared with X. 509 • Real delegation of power – Better accountability – More flexibility – Better damage control • Clearer semantics – X. 509 certificate encompasses everything – DANE records only means that “this domain’s owner says…” 15
Advantages of DANE compared with X. 509 • Real delegation of power – Better accountability – More flexibility – Better damage control • Clearer semantics – X. 509 certificate encompasses everything – DANE records only means that “this domain’s owner says…” 15
 Problems of DNSSEC • Key revocation – If a zone’s private key is compromised, the damage continues even after the key is replaced, until the parent’s cert on the key expires – Certificate revocation? • All the revocation problems with public keys will apply – Issue short-term certificates instead? • Then the upper-level zones will have to be more involved in maintaining the DNSSEC structure • Against the initial design principles of DNS: autonomy of individual zones 16
Problems of DNSSEC • Key revocation – If a zone’s private key is compromised, the damage continues even after the key is replaced, until the parent’s cert on the key expires – Certificate revocation? • All the revocation problems with public keys will apply – Issue short-term certificates instead? • Then the upper-level zones will have to be more involved in maintaining the DNSSEC structure • Against the initial design principles of DNS: autonomy of individual zones 16
 Deployment Status • Has been on-going for a number of years – Check status: http: //www. dnssec-deployment. org/ http: //www. internetsociety. org/deploy 360/dnssec/m aps/ • Root domain signed July, 2010 – DNSSEC now deployed at key zones including net, com, gov, and edu • “Almost” ready to use at the resolver level 17
Deployment Status • Has been on-going for a number of years – Check status: http: //www. dnssec-deployment. org/ http: //www. internetsociety. org/deploy 360/dnssec/m aps/ • Root domain signed July, 2010 – DNSSEC now deployed at key zones including net, com, gov, and edu • “Almost” ready to use at the resolver level 17


