83c637d58c19a2a24707af173a740895.ppt
- Количество слайдов: 17

“Discouraging Software Piracy Using Software Aging” Markus Jakobsson & Michael Reiter “According to a recent study, the computer industry loses $11 billion annually to piracy…”

Outline What constitutes piracy? n Piracy and Ethics n The prevention by “Software Aging” proposition n Issues n

Assumptions n There is only one distributor ¨ Is n Illegitimate users do not collude ¨ In n this really a practical model? reality, they do Only pirates who operate for profit are considered
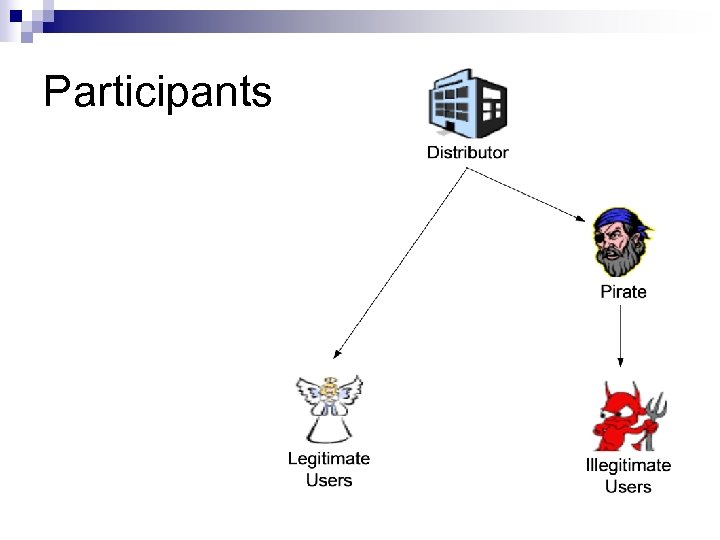
Participants
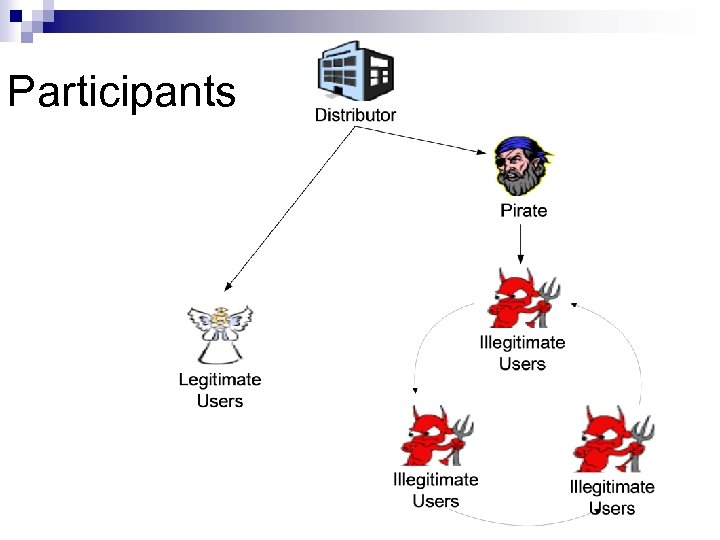
Participants

Piracy and Pfleeger’s Taxonomy n n n Where does it fit in? Interruption? – No Interception? – Sort of: unauthorised parties gain possession of software Modification? – Yes: some sort of “crack” is usually necessary to circumvent standard anticopying measures Fabrication? – Possibly: a fabricated licence management module is sometimes added to software to force it to run

Piracy and “Universal” Ethics n n Right to knowledge – some would argue that software is knowledge and should be owned by all… therefore piracy is not wrong Right to privacy – is applicable to this particular prevention system… more later Right to fair compensation – if it is fair that anyone who uses a piece of software should have given the author financial compensation… Is there an alternative form of compensation?

Approach n Try to tie the process of software updates (bug-fixes, enhancements etc) to a piracy prevention system n Minimize negative impact on legitimate users n Maximize cost for pirates n Force continuous software updates – attempt to force pirate to be responsible for providing these
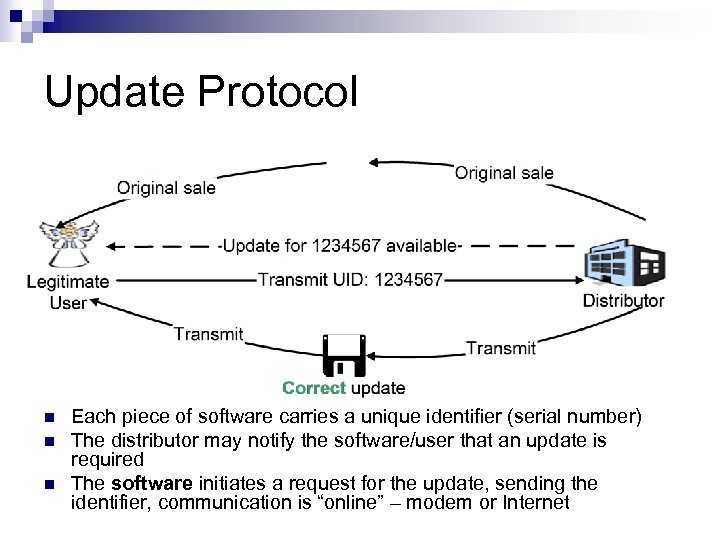
Update Protocol n n n Each piece of software carries a unique identifier (serial number) The distributor may notify the software/user that an update is required The software initiates a request for the update, sending the identifier, communication is “online” – modem or Internet
Forcing Updates The program version of files output by the software is included in the file n The output files are encrypted via a symmetric key, e. g. DES n The key only works for one file/software version n
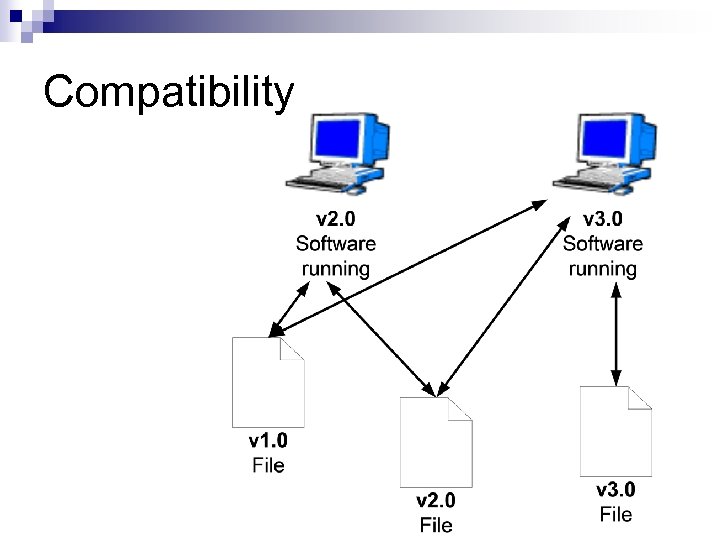
Compatibility
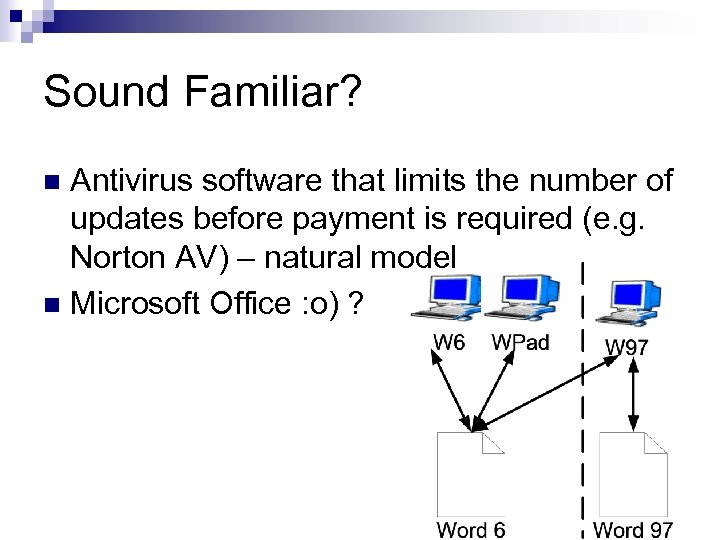
Sound Familiar? Antivirus software that limits the number of updates before payment is required (e. g. Norton AV) – natural model n Microsoft Office : o) ? n

Do We Really Want This? n n What are some problems with an encrypted file format? Makes integration difficult – if we wish to import the file into another program to manipulate it The file is not “human readable”, the computing community as a whole is moving towards open standards, e. g. XML Error recovery – if your XML file gets corrupted and confuses its application, you can always fix it with notepad

Accessibility and Privacy Not everyone has an Internet connection n Not everyone has a modem n We are allowing a connection to our machine from a remote site n Are we just transmitting what we think we are? n

Conclusion n The paper proposes forcing users to update regularly by making all files output by a piece of software encrypted, and changing the encryption key with every upgrade Backwards compatibility is maintained If continuous updates to a given piece of software required, this system could work, but there are issues…

Conclusion Updates must be essential n Users must have “online” access n Integration is difficult (impossible? ) with encrypted files n A new cost model is introduced n Finally and most importantly… n

Conclusion n Would you buy software that utilises this system?
83c637d58c19a2a24707af173a740895.ppt