b79abd8a5ceb5d620b71ac8c4f79d0f7.ppt
- Количество слайдов: 25
 Directory Service Continuity • Monitor Active Directory • Manage the Active Directory Database • Back Up and Restore AD DS and Domain Controllers 1
Directory Service Continuity • Monitor Active Directory • Manage the Active Directory Database • Back Up and Restore AD DS and Domain Controllers 1
 Understand Performance and Bottlenecks • Key system resources § CPU § Disk § Memory § Network • Bottleneck: Resource that is currently at peak utilization • Tools § Task Manager § Event Viewer § Resource Monitor § Reliability Monitor § Performance Monitor § System Center Operations Manager 2
Understand Performance and Bottlenecks • Key system resources § CPU § Disk § Memory § Network • Bottleneck: Resource that is currently at peak utilization • Tools § Task Manager § Event Viewer § Resource Monitor § Reliability Monitor § Performance Monitor § System Center Operations Manager 2
 Task Manager • Starting taskmgr. exe § CTRL+SHIFT+ESC § CTRL+ALT+DEL § Right-click taskbar § Start taskmgr. exe • Real-time performance § Applications § Processes § Services § Performance • • § High-level CPU, network, memory No disk counters Logged-on users • Entry point to Resource Monitor 3
Task Manager • Starting taskmgr. exe § CTRL+SHIFT+ESC § CTRL+ALT+DEL § Right-click taskbar § Start taskmgr. exe • Real-time performance § Applications § Processes § Services § Performance • • § High-level CPU, network, memory No disk counters Logged-on users • Entry point to Resource Monitor 3
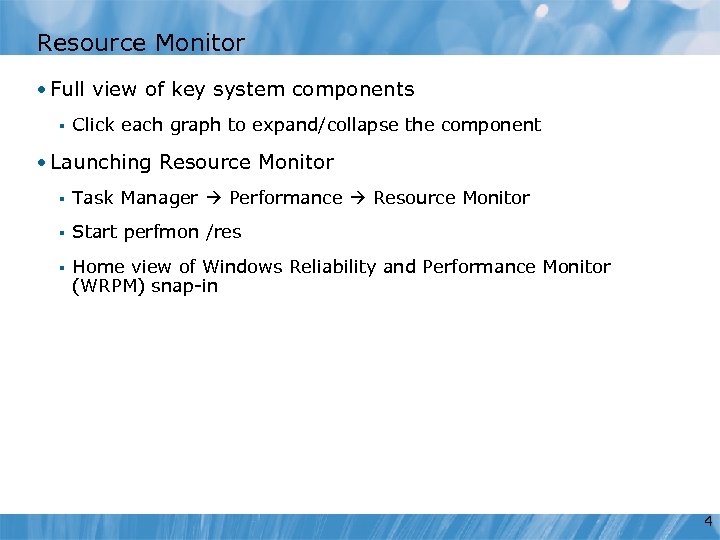 Resource Monitor • Full view of key system components § Click each graph to expand/collapse the component • Launching Resource Monitor § Task Manager Performance Resource Monitor § Start perfmon /res § Home view of Windows Reliability and Performance Monitor (WRPM) snap-in 4
Resource Monitor • Full view of key system components § Click each graph to expand/collapse the component • Launching Resource Monitor § Task Manager Performance Resource Monitor § Start perfmon /res § Home view of Windows Reliability and Performance Monitor (WRPM) snap-in 4
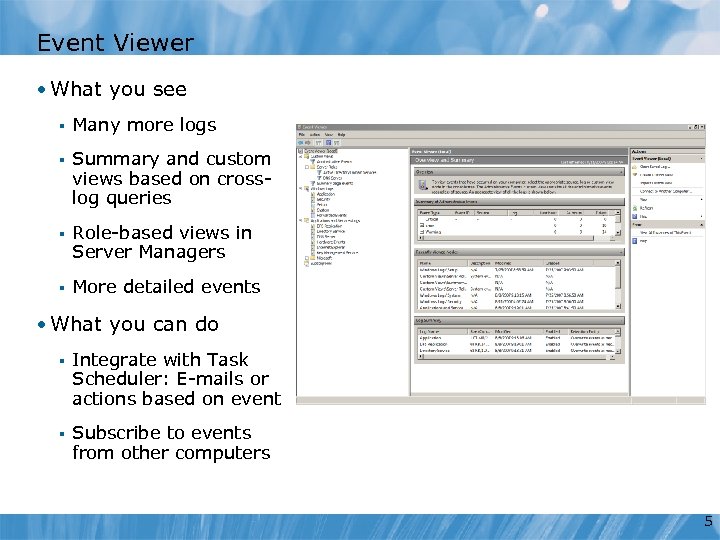 Event Viewer • What you see § Many more logs § Summary and custom views based on crosslog queries § Role-based views in Server Managers § More detailed events • What you can do § Integrate with Task Scheduler: E-mails or actions based on event § Subscribe to events from other computers 5
Event Viewer • What you see § Many more logs § Summary and custom views based on crosslog queries § Role-based views in Server Managers § More detailed events • What you can do § Integrate with Task Scheduler: E-mails or actions based on event § Subscribe to events from other computers 5
 Demonstration: Event Viewer In this demonstration, we will • Explore Event Viewer • Identify the Active Directory logs § Directory Service § Domain Name System (DNS) § Distributed File System Replication (DFSR) § Group Policy Operational log • Discover the new features in the Windows Server 2008 Event Viewer 6
Demonstration: Event Viewer In this demonstration, we will • Explore Event Viewer • Identify the Active Directory logs § Directory Service § Domain Name System (DNS) § Distributed File System Replication (DFSR) § Group Policy Operational log • Discover the new features in the Windows Server 2008 Event Viewer 6
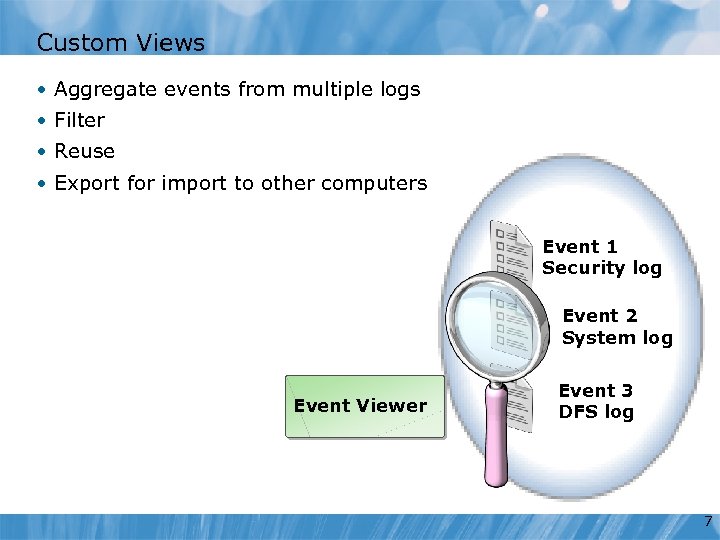 Custom Views • Aggregate events from multiple logs • Filter • Reuse • Export for import to other computers Event 1 Security log Event 2 System log Event Viewer Event 3 DFS log 7
Custom Views • Aggregate events from multiple logs • Filter • Reuse • Export for import to other computers Event 1 Security log Event 2 System log Event Viewer Event 3 DFS log 7
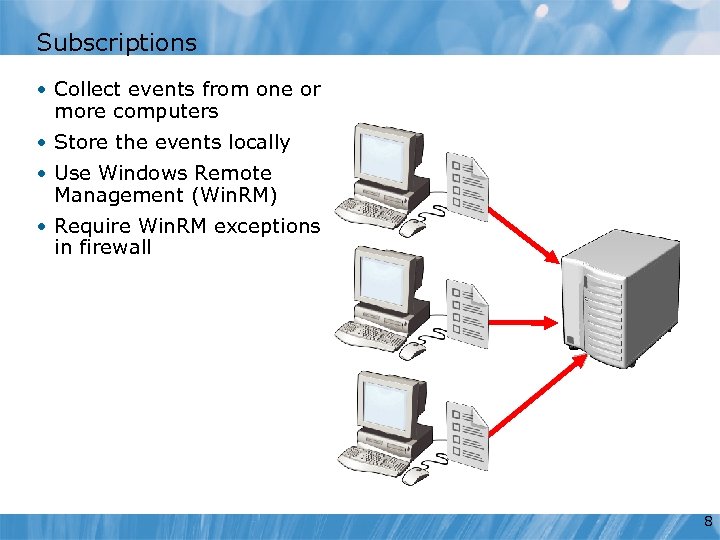 Subscriptions • Collect events from one or more computers • Store the events locally • Use Windows Remote Management (Win. RM) • Require Win. RM exceptions in firewall 8
Subscriptions • Collect events from one or more computers • Store the events locally • Use Windows Remote Management (Win. RM) • Require Win. RM exceptions in firewall 8
 Windows Reliability and Performance Monitor (WRPM) • Track system changes (Reliability Monitor) • Display real-time or logged performance data (Performance Monitor) § Generate reports or graphical views of performance § Generate alerts § Take action when thresholds are reached • Collect data (Data Collector Sets and Reports) § Generate reports § Generate graphical views of logged performance 9
Windows Reliability and Performance Monitor (WRPM) • Track system changes (Reliability Monitor) • Display real-time or logged performance data (Performance Monitor) § Generate reports or graphical views of performance § Generate alerts § Take action when thresholds are reached • Collect data (Data Collector Sets and Reports) § Generate reports § Generate graphical views of logged performance 9
 Reliability Monitor • Tracks system changes § Software install/uninstall § Application failures § Windows failures § Hardware failures 10
Reliability Monitor • Tracks system changes § Software install/uninstall § Application failures § Windows failures § Hardware failures 10
 Performance Monitor • Useful counters in any server baseline § Memory Pages/sec § Physical. Disk Avg. Disk Queue Length § Processor %Processor Time • Useful counters for monitoring Active Directory § NTDS DRA Inbound Bytes Total/sec § NTDS DRA Inbound Object § NTDS DRA Outbound Bytes Total/sec § NTDS DRA Pending Replication Synchronizations § NTDS Kerberos Authentications/sec § NTDS NTLM Authentications 11
Performance Monitor • Useful counters in any server baseline § Memory Pages/sec § Physical. Disk Avg. Disk Queue Length § Processor %Processor Time • Useful counters for monitoring Active Directory § NTDS DRA Inbound Bytes Total/sec § NTDS DRA Inbound Object § NTDS DRA Outbound Bytes Total/sec § NTDS DRA Pending Replication Synchronizations § NTDS Kerberos Authentications/sec § NTDS NTLM Authentications 11
 Data Collector Sets • Collections of data points § Performance counters § Event trace data § System configuration information (registry keys) • Use to § View real-time performance with Performance Monitor § Create a log (manually invoked or scheduled) and then view Reports § Generate alerts based on thresholds § Use by other applications • Create § Start from a template; role templates added by Windows § Save an existing set of counters in a Performance Monitor view § Manually specify and configure data collectors in a set § Export/import data collector set as XML 12
Data Collector Sets • Collections of data points § Performance counters § Event trace data § System configuration information (registry keys) • Use to § View real-time performance with Performance Monitor § Create a log (manually invoked or scheduled) and then view Reports § Generate alerts based on thresholds § Use by other applications • Create § Start from a template; role templates added by Windows § Save an existing set of counters in a Performance Monitor view § Manually specify and configure data collectors in a set § Export/import data collector set as XML 12
 Monitoring Best Practices 1. Monitor early to establish baselines! § Document performance when things are working well § Include server and role-related counters during idle and busy times 2. Monitor often to identify potential problems § Compare to baseline and watch for troublesome deviation 3. Know how to monitor and interpret performance before a meltdown § Establish Data Collector Sets § Build the skills to interpret performance counters 4. Capture appropriately § Don’t overcapture • Degrades performance • Creates “noise, ” making it difficult to identify real problems 13
Monitoring Best Practices 1. Monitor early to establish baselines! § Document performance when things are working well § Include server and role-related counters during idle and busy times 2. Monitor often to identify potential problems § Compare to baseline and watch for troublesome deviation 3. Know how to monitor and interpret performance before a meltdown § Establish Data Collector Sets § Build the skills to interpret performance counters 4. Capture appropriately § Don’t overcapture • Degrades performance • Creates “noise, ” making it difficult to identify real problems 13
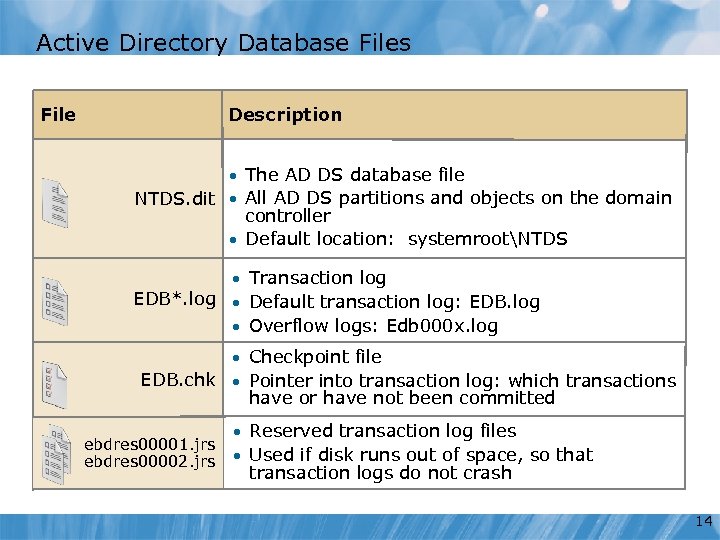 Active Directory Database Files Description File • The AD DS database file NTDS. dit • All AD DS partitions and objects on the domain controller • Default location: systemrootNTDS • Transaction log EDB*. log • Default transaction log: EDB. log • Overflow logs: Edb 000 x. log • Checkpoint file EDB. chk • Pointer into transaction log: which transactions have or have not been committed ebdres 00001. jrs ebdres 00002. jrs • Reserved transaction log files • Used if disk runs out of space, so that transaction logs do not crash 14
Active Directory Database Files Description File • The AD DS database file NTDS. dit • All AD DS partitions and objects on the domain controller • Default location: systemrootNTDS • Transaction log EDB*. log • Default transaction log: EDB. log • Overflow logs: Edb 000 x. log • Checkpoint file EDB. chk • Pointer into transaction log: which transactions have or have not been committed ebdres 00001. jrs ebdres 00002. jrs • Reserved transaction log files • Used if disk runs out of space, so that transaction logs do not crash 14
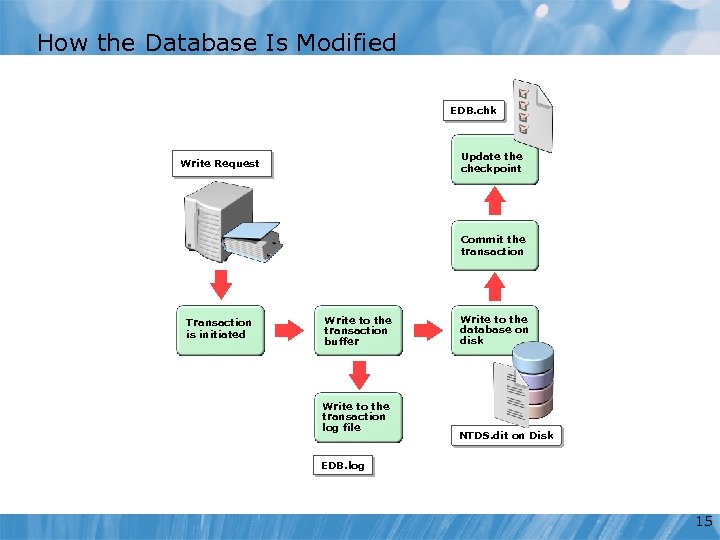 How the Database Is Modified EDB. chk Update the checkpoint Write Request Commit the transaction Transaction is initiated Write to the transaction buffer Write to the transaction log file Write to the database on disk NTDS. dit on Disk EDB. log 15
How the Database Is Modified EDB. chk Update the checkpoint Write Request Commit the transaction Transaction is initiated Write to the transaction buffer Write to the transaction log file Write to the database on disk NTDS. dit on Disk EDB. log 15
 NTDSUtil • Manage and control single master operations (Module 11) • Perform AD DS database maintenance (Module 13) § Perform offline defragmentation § Create and mount snapshots § Move database files • Clean domain controller metadata § Domain controller removal or demotion while not connected to domain • Reset Directory Services Restore Mode password § set dsrm 16
NTDSUtil • Manage and control single master operations (Module 11) • Perform AD DS database maintenance (Module 13) § Perform offline defragmentation § Create and mount snapshots § Move database files • Clean domain controller metadata § Domain controller removal or demotion while not connected to domain • Reset Directory Services Restore Mode password § set dsrm 16
 Perform Database Maintenance • Garbage collection § Scavenging: Removing deleted items that have reached their tombstone lifetime • Defragmentation § Online defrag (part of garbage collection): reclaims unused space § Offline defrag (manual): releases unused space, reduces file size • Use NTDSUtil • Restartable AD DS § You can stop AD DS in Services just like any other service § For applying updates that affect AD DS files § Before performing offline defragmentation 17
Perform Database Maintenance • Garbage collection § Scavenging: Removing deleted items that have reached their tombstone lifetime • Defragmentation § Online defrag (part of garbage collection): reclaims unused space § Offline defrag (manual): releases unused space, reduces file size • Use NTDSUtil • Restartable AD DS § You can stop AD DS in Services just like any other service § For applying updates that affect AD DS files § Before performing offline defragmentation 17
 Active Directory Snapshots • Create a snapshot of Active Directory § NTDSUtil • Mount the snapshot to a unique port § NTDSUtil • Expose the snapshot § Right-click the root node of Active Directory Users and Computers and choose Connect to Domain Controller § Enter server. FQDN: port • View (read-only) snapshot § Cannot directly restore data from the snapshot • Recover data § Manually re-enter data or § Restore a backup from the same date as the snapshot 18
Active Directory Snapshots • Create a snapshot of Active Directory § NTDSUtil • Mount the snapshot to a unique port § NTDSUtil • Expose the snapshot § Right-click the root node of Active Directory Users and Computers and choose Connect to Domain Controller § Enter server. FQDN: port • View (read-only) snapshot § Cannot directly restore data from the snapshot • Recover data § Manually re-enter data or § Restore a backup from the same date as the snapshot 18
 Restore Deleted Objects • When an object is deleted § Stripped of almost every attribute except • § SID, object. GUID, last. Known. Parent, s. AMAccount. Name Moved to Deleted Objects container, marked as is. Deleted • You can restore (“reanimate”) deleted (“tombstoned”) objects when § Domain functional level is Windows Server 2003 or greater § Deleted object has not yet been scavenged • Steps § LDP. exe • • § Modify is. Deleted Provide distinguished name (DN) Repopulate all other attributes 19
Restore Deleted Objects • When an object is deleted § Stripped of almost every attribute except • § SID, object. GUID, last. Known. Parent, s. AMAccount. Name Moved to Deleted Objects container, marked as is. Deleted • You can restore (“reanimate”) deleted (“tombstoned”) objects when § Domain functional level is Windows Server 2003 or greater § Deleted object has not yet been scavenged • Steps § LDP. exe • • § Modify is. Deleted Provide distinguished name (DN) Repopulate all other attributes 19
 Backup and Recovery Tools • Windows Server Backup snap-in (use locally or remotely) § Back up a full server (all volumes) § Back up selected volume(s) § Back up system state (includes all critical volumes) § Recover volumes, folders, files, or system state • wbadmin. exe • Perform manual or automated backup • Back up to CD/DVD/HDD § No tape! § Use a dedicated HDD for backup: recommended or required 20
Backup and Recovery Tools • Windows Server Backup snap-in (use locally or remotely) § Back up a full server (all volumes) § Back up selected volume(s) § Back up system state (includes all critical volumes) § Recover volumes, folders, files, or system state • wbadmin. exe • Perform manual or automated backup • Back up to CD/DVD/HDD § No tape! § Use a dedicated HDD for backup: recommended or required 20
 Overview of AD DS and Domain Controller Backup • You must back up all critical volumes § System volume: The volume that contains boot files § Boot volume: The volume that contains the Windows operating system and the registry § Volume(s) hosting SYSVOL, AD DS database (NTDS. dit), logs § Do not store other data on these volumes as it will increase backup and restore times • Windows Server Backup (wbadmin. exe) 21
Overview of AD DS and Domain Controller Backup • You must back up all critical volumes § System volume: The volume that contains boot files § Boot volume: The volume that contains the Windows operating system and the registry § Volume(s) hosting SYSVOL, AD DS database (NTDS. dit), logs § Do not store other data on these volumes as it will increase backup and restore times • Windows Server Backup (wbadmin. exe) 21
 Other Backup and Recovery Tools • Active Directory Snapshots • Power. Shell cmdlets • Windows Recovery Environment § Boot to Windows Server 2008 DVD and choose System Recovery Options § Install locally as a boot option § Useful for full system recovery • Microsoft System Center Data Protection Manager 2007 22
Other Backup and Recovery Tools • Active Directory Snapshots • Power. Shell cmdlets • Windows Recovery Environment § Boot to Windows Server 2008 DVD and choose System Recovery Options § Install locally as a boot option § Useful for full system recovery • Microsoft System Center Data Protection Manager 2007 22
 Active Directory Restore Options • Nonauthoritative (normal) restore § Restore domain controller to previously known good state of Active Directory § Domain controller will be updated using standard replication from up-to-date partners • Authoritative restore § Restore domain controller to previously known good state of Active Directory § “Mark” objects that you want to be authoritative • Windows sets the version numbers very high § Domain controller is updated from its up-to-date-partners § Domain controller sends authoritative updates to its partners • Full Server Restore § Typically performed in Windows Recovery Environment • Alternate Location Restore 23
Active Directory Restore Options • Nonauthoritative (normal) restore § Restore domain controller to previously known good state of Active Directory § Domain controller will be updated using standard replication from up-to-date partners • Authoritative restore § Restore domain controller to previously known good state of Active Directory § “Mark” objects that you want to be authoritative • Windows sets the version numbers very high § Domain controller is updated from its up-to-date-partners § Domain controller sends authoritative updates to its partners • Full Server Restore § Typically performed in Windows Recovery Environment • Alternate Location Restore 23
 Nonauthoritative Restore • Restart the domain controller in DSRM § Locally: Press F 8 on restart § Remotely using remote desktop: • Configure restart in DSRM: bcdedit /set safeboot dsarepair • Restart: shutdown -t 0 -r • Log on with the Administrator account and the DSRM password • Perform the nonauthoritative restore § Use Windows Server Backup (wbadmin. exe) to restore AD DS • Restart § Set normal restart: bcdedit /deletevalue safeboot dsarepair § Restart: shutdown -t 0 -r • Domain controller replicates all changes since date of backup from its partners 24
Nonauthoritative Restore • Restart the domain controller in DSRM § Locally: Press F 8 on restart § Remotely using remote desktop: • Configure restart in DSRM: bcdedit /set safeboot dsarepair • Restart: shutdown -t 0 -r • Log on with the Administrator account and the DSRM password • Perform the nonauthoritative restore § Use Windows Server Backup (wbadmin. exe) to restore AD DS • Restart § Set normal restart: bcdedit /deletevalue safeboot dsarepair § Restart: shutdown -t 0 -r • Domain controller replicates all changes since date of backup from its partners 24
 Authoritative Restore • Restart the domain controller in DSRM • Log on with the Administrator account and the DSRM password • Perform the nonauthoritative restore § Use Windows Server Backup (wbadmin. exe) to restore AD DS • Mark selected objects as authoritative § restore [object|subtree] “object. DN" § Authoritative changes have a higher version number than on partners • Restart • Restored domain controller replicates changes since date of backup • Partners see authoritative changes with high version numbers § Partners pull the authoritative changes from the restored domain controller 25
Authoritative Restore • Restart the domain controller in DSRM • Log on with the Administrator account and the DSRM password • Perform the nonauthoritative restore § Use Windows Server Backup (wbadmin. exe) to restore AD DS • Mark selected objects as authoritative § restore [object|subtree] “object. DN" § Authoritative changes have a higher version number than on partners • Restart • Restored domain controller replicates changes since date of backup • Partners see authoritative changes with high version numbers § Partners pull the authoritative changes from the restored domain controller 25


