eff6212dd432bbe79eeda3e4cf76efe8.ppt
- Количество слайдов: 27
 Direct Texting Direct Messaging A Concept/Proposal from Direct. Trust to In-Bundle HISPs and CAs www. directtrust. org 1101 Connecticut Ave NW, Washington, DC 20036 Direct Texting
Direct Texting Direct Messaging A Concept/Proposal from Direct. Trust to In-Bundle HISPs and CAs www. directtrust. org 1101 Connecticut Ave NW, Washington, DC 20036 Direct Texting
 The basic idea • To leverage Direct. Trust’s security and trust infrastructure, and our national network, to provide open, standards-based, secure, and identity validated Direct texting. • HISPs could offer Direct texting services to existing and new customers alongside their Direct messaging services. • Anyone on the network could connect with anyone else on the network via Direct texting apps. • Direct. Trust would hold license to open technical specification for Direct texting, analogous to the Applicability Statement for Direct messaging. • Other licensing arrangements to be considered. Direct Messaging Direct Texting www. directtrust. org 1101 Connecticut Ave NW, Washington, DC 20036
The basic idea • To leverage Direct. Trust’s security and trust infrastructure, and our national network, to provide open, standards-based, secure, and identity validated Direct texting. • HISPs could offer Direct texting services to existing and new customers alongside their Direct messaging services. • Anyone on the network could connect with anyone else on the network via Direct texting apps. • Direct. Trust would hold license to open technical specification for Direct texting, analogous to the Applicability Statement for Direct messaging. • Other licensing arrangements to be considered. Direct Messaging Direct Texting www. directtrust. org 1101 Connecticut Ave NW, Washington, DC 20036
 Outline • • • Defining the smartphone texting markets Barriers to healthcare texting What the healthcare market needs The opportunity for the Direct. Trust network How to accelerate process Next steps Direct Messaging Direct Texting www. directtrust. org 1101 Connecticut Ave NW, Washington, DC 20036
Outline • • • Defining the smartphone texting markets Barriers to healthcare texting What the healthcare market needs The opportunity for the Direct. Trust network How to accelerate process Next steps Direct Messaging Direct Texting www. directtrust. org 1101 Connecticut Ave NW, Washington, DC 20036
 The three use cases 1. Provider to Provider: Texting between providers including Protected Health Information (PHI). Happens regularly; hospitals are trying to prohibit for compliance reasons. 2. Hospital to Provider: Aka paging, this has been used for a long time. Hospitals and providers would prefer to avoid dedicated pagers, and have the ability to include PHI information in such texts (currently not allowed). 3. Provider to Patient: Texting between providers and patients. Widespread for appointment reminders. Increasing, especially with younger patients, for other purposes. www. directtrust. org 1101 Connecticut Ave NW, Washington, DC 20036
The three use cases 1. Provider to Provider: Texting between providers including Protected Health Information (PHI). Happens regularly; hospitals are trying to prohibit for compliance reasons. 2. Hospital to Provider: Aka paging, this has been used for a long time. Hospitals and providers would prefer to avoid dedicated pagers, and have the ability to include PHI information in such texts (currently not allowed). 3. Provider to Patient: Texting between providers and patients. Widespread for appointment reminders. Increasing, especially with younger patients, for other purposes. www. directtrust. org 1101 Connecticut Ave NW, Washington, DC 20036
 The current barriers 1. No guarantee of privacy: Texts within i. OS, Android and BBM are encrypted, but cross platform texts use SMS network and there is no guarantee that they will be encrypted at carriers. 2. Complete lack of auditability: End to end encryption within the i. OS, Android and BBM networks prevent audits. The SMS networks do not have any easy auditability. 3. Standards Vacuum: Closest spec (XMPP/Jabber/XCP) has ‘perfect forward security’ model (no auditability) or no end user PKI credentials. 4. Lack of reliability: Cross platform texts, or hospital paging, lack guaranteed delivery. 2 -5% of all texts are lost. 5. Proprietary Silos: Private app-based solutions solving some of the above exist. They are siloed, centralized services. They do not inter-operate and either lack end to end encryption or auditability. Also lack strong identity proofing and authentication. Providers unlikely to use different apps for texting different providers or patients. www. directtrust. org 1101 Connecticut Ave NW, Washington, DC 20036
The current barriers 1. No guarantee of privacy: Texts within i. OS, Android and BBM are encrypted, but cross platform texts use SMS network and there is no guarantee that they will be encrypted at carriers. 2. Complete lack of auditability: End to end encryption within the i. OS, Android and BBM networks prevent audits. The SMS networks do not have any easy auditability. 3. Standards Vacuum: Closest spec (XMPP/Jabber/XCP) has ‘perfect forward security’ model (no auditability) or no end user PKI credentials. 4. Lack of reliability: Cross platform texts, or hospital paging, lack guaranteed delivery. 2 -5% of all texts are lost. 5. Proprietary Silos: Private app-based solutions solving some of the above exist. They are siloed, centralized services. They do not inter-operate and either lack end to end encryption or auditability. Also lack strong identity proofing and authentication. Providers unlikely to use different apps for texting different providers or patients. www. directtrust. org 1101 Connecticut Ave NW, Washington, DC 20036
 The solution needed 1. An open standard for healthcare texting stewarded by a trusted and competent neutral organization. 2. Interoperable end to end privacy. Implication of a PKI solution is unavoidable. 3. The solution must have end to end privacy WITH auditability AND WITH strong identity proofing and authentication. 4. The solution must have guaranteed delivery with return receipts. 5. The solution must work on any platform – TODAY, without persuading Apple, Google, Black. Berry, Microsoft, etc. to endorse standard. www. directtrust. org 1101 Connecticut Ave NW, Washington, DC 20036
The solution needed 1. An open standard for healthcare texting stewarded by a trusted and competent neutral organization. 2. Interoperable end to end privacy. Implication of a PKI solution is unavoidable. 3. The solution must have end to end privacy WITH auditability AND WITH strong identity proofing and authentication. 4. The solution must have guaranteed delivery with return receipts. 5. The solution must work on any platform – TODAY, without persuading Apple, Google, Black. Berry, Microsoft, etc. to endorse standard. www. directtrust. org 1101 Connecticut Ave NW, Washington, DC 20036
 The Direct. Trust opportunity • • Direct. Trust is a trusted organization capable of stewarding the healthcare texting standard in partnership with ? ? There are two aspects to any such standard: 1. The operational standards, e. g. Certificate Policy, ID proofing, accreditation via EHNAC-Direct. Trust. 2. The technical specs. Direct. Trust has already done all the work on the operational standards. Direct. Trust accreditation and credentials can be reused by a PKI based healthcare texting standard. Leveraging the work already done by Direct. Trust and its members is key to this opportunity’s success. • Direct. Trust in-bundle HISPs are ideally positioned to expand their service offerings to include Direct secure texting and paging, starting with existing customer base of hospitals, health systems, medical practices, etc. www. directtrust. org 1101 Connecticut Ave NW, Washington, DC 20036
The Direct. Trust opportunity • • Direct. Trust is a trusted organization capable of stewarding the healthcare texting standard in partnership with ? ? There are two aspects to any such standard: 1. The operational standards, e. g. Certificate Policy, ID proofing, accreditation via EHNAC-Direct. Trust. 2. The technical specs. Direct. Trust has already done all the work on the operational standards. Direct. Trust accreditation and credentials can be reused by a PKI based healthcare texting standard. Leveraging the work already done by Direct. Trust and its members is key to this opportunity’s success. • Direct. Trust in-bundle HISPs are ideally positioned to expand their service offerings to include Direct secure texting and paging, starting with existing customer base of hospitals, health systems, medical practices, etc. www. directtrust. org 1101 Connecticut Ave NW, Washington, DC 20036
 3 p. TALK Background • Part of incubator set up with (unusual) business model: • Identify market vacuum, invent, build proof of concept, license/sell intellectual property and s/w • Not a traditional software or SAAS vendor • • • No direct sales to enterprises or consumers Invest little… Sell for little more… Status of technology relevant to this conversation: • Owns or licenses relevant intellectual property • Well developed alpha code (ready to show customers) • Exploring various licensing/sale options • E. g. make SPEC open; license app and server software www. directtrust. org 1101 Connecticut Ave NW, Washington, DC 20036
3 p. TALK Background • Part of incubator set up with (unusual) business model: • Identify market vacuum, invent, build proof of concept, license/sell intellectual property and s/w • Not a traditional software or SAAS vendor • • • No direct sales to enterprises or consumers Invest little… Sell for little more… Status of technology relevant to this conversation: • Owns or licenses relevant intellectual property • Well developed alpha code (ready to show customers) • Exploring various licensing/sale options • E. g. make SPEC open; license app and server software www. directtrust. org 1101 Connecticut Ave NW, Washington, DC 20036
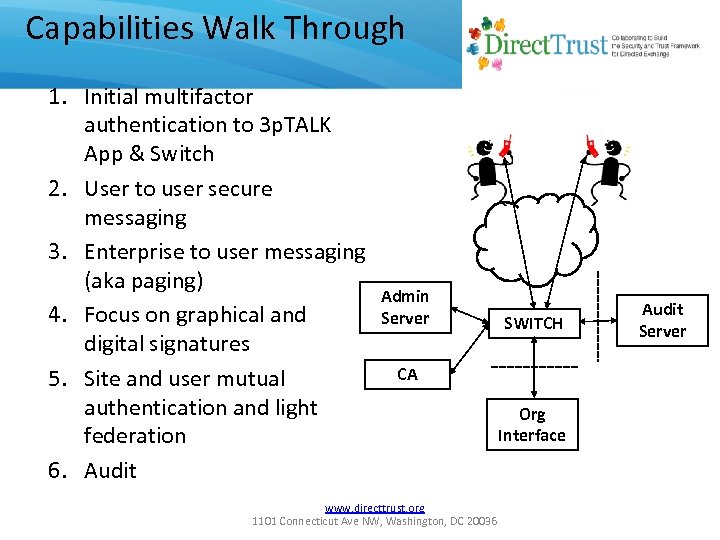 Capabilities Walk Through 1. Initial multifactor authentication to 3 p. TALK App & Switch 2. User to user secure messaging 3. Enterprise to user messaging (aka paging) 4. Focus on graphical and digital signatures 5. Site and user mutual authentication and light federation 6. Audit Admin Server SWITCH CA www. directtrust. org 1101 Connecticut Ave NW, Washington, DC 20036 Org Interface Audit Server
Capabilities Walk Through 1. Initial multifactor authentication to 3 p. TALK App & Switch 2. User to user secure messaging 3. Enterprise to user messaging (aka paging) 4. Focus on graphical and digital signatures 5. Site and user mutual authentication and light federation 6. Audit Admin Server SWITCH CA www. directtrust. org 1101 Connecticut Ave NW, Washington, DC 20036 Org Interface Audit Server
 Back Up – More Info • If you want to try app, we will set up an account on our guest network. Please contact: – – • Or, the screen shots that follow give you a taste of the product. – – • Ravi Ganesan, ravi@findravi. com, +1. 415. 680. 5746 Note we currently support i. OS and Android. Black. Berry is supported via Android side loading (no PUSH notifications). Messaging types – CONFIRM, QUERY, OPTION and INFORM. OTP and Federation Lite flow Sample Org Interface screen shot Sample Audit System screen shot You can also see videos at http: //3 ptalk. com/appinaction/ www. directtrust. org 1101 Connecticut Ave NW, Washington, DC 20036
Back Up – More Info • If you want to try app, we will set up an account on our guest network. Please contact: – – • Or, the screen shots that follow give you a taste of the product. – – • Ravi Ganesan, ravi@findravi. com, +1. 415. 680. 5746 Note we currently support i. OS and Android. Black. Berry is supported via Android side loading (no PUSH notifications). Messaging types – CONFIRM, QUERY, OPTION and INFORM. OTP and Federation Lite flow Sample Org Interface screen shot Sample Audit System screen shot You can also see videos at http: //3 ptalk. com/appinaction/ www. directtrust. org 1101 Connecticut Ave NW, Washington, DC 20036
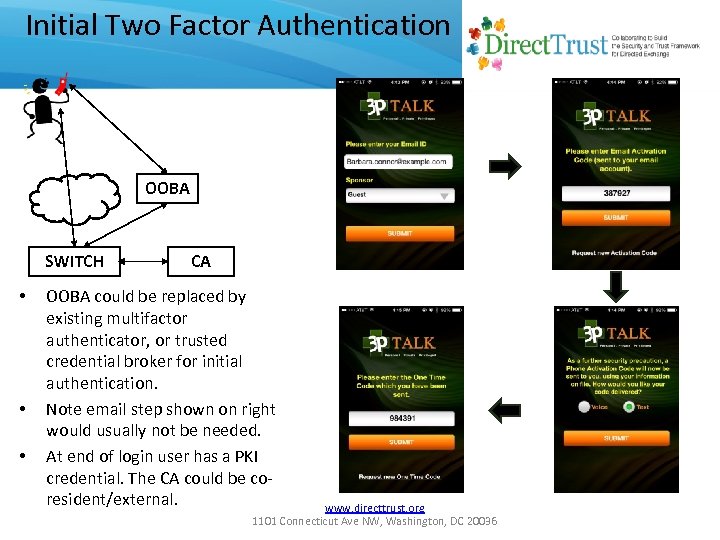 Initial Two Factor Authentication OOBA SWITCH • • • CA OOBA could be replaced by existing multifactor authenticator, or trusted credential broker for initial authentication. Note email step shown on right would usually not be needed. At end of login user has a PKI credential. The CA could be coresident/external. www. directtrust. org 1101 Connecticut Ave NW, Washington, DC 20036
Initial Two Factor Authentication OOBA SWITCH • • • CA OOBA could be replaced by existing multifactor authenticator, or trusted credential broker for initial authentication. Note email step shown on right would usually not be needed. At end of login user has a PKI credential. The CA could be coresident/external. www. directtrust. org 1101 Connecticut Ave NW, Washington, DC 20036
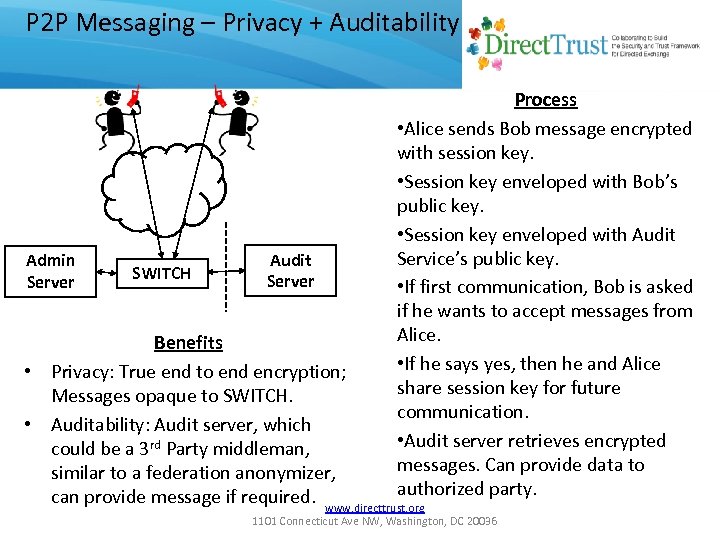 P 2 P Messaging – Privacy + Auditability Admin Server SWITCH Audit Server Process • Alice sends Bob message encrypted with session key. • Session key enveloped with Bob’s public key. • Session key enveloped with Audit Service’s public key. • If first communication, Bob is asked if he wants to accept messages from Alice. • If he says yes, then he and Alice share session key for future communication. • Audit server retrieves encrypted messages. Can provide data to authorized party. Benefits • Privacy: True end to end encryption; Messages opaque to SWITCH. • Auditability: Audit server, which could be a 3 rd Party middleman, similar to a federation anonymizer, can provide message if required. www. directtrust. org 1101 Connecticut Ave NW, Washington, DC 20036
P 2 P Messaging – Privacy + Auditability Admin Server SWITCH Audit Server Process • Alice sends Bob message encrypted with session key. • Session key enveloped with Bob’s public key. • Session key enveloped with Audit Service’s public key. • If first communication, Bob is asked if he wants to accept messages from Alice. • If he says yes, then he and Alice share session key for future communication. • Audit server retrieves encrypted messages. Can provide data to authorized party. Benefits • Privacy: True end to end encryption; Messages opaque to SWITCH. • Auditability: Audit server, which could be a 3 rd Party middleman, similar to a federation anonymizer, can provide message if required. www. directtrust. org 1101 Connecticut Ave NW, Washington, DC 20036
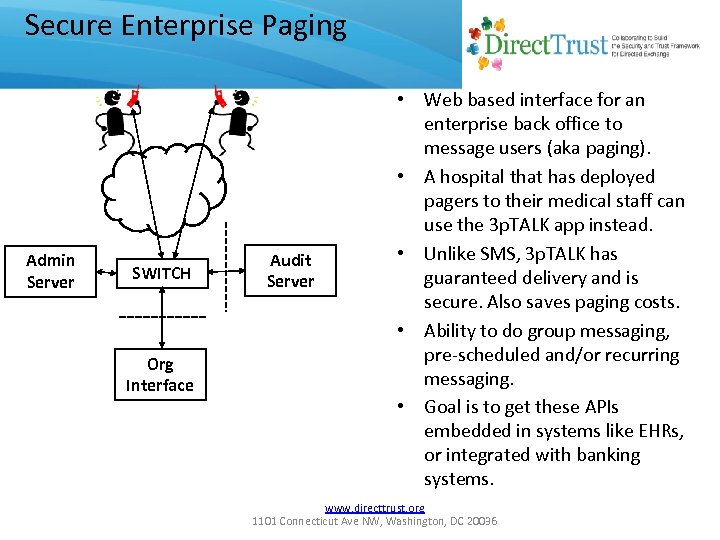 Secure Enterprise Paging Admin Server SWITCH Org Interface Audit Server • Web based interface for an enterprise back office to message users (aka paging). • A hospital that has deployed pagers to their medical staff can use the 3 p. TALK app instead. • Unlike SMS, 3 p. TALK has guaranteed delivery and is secure. Also saves paging costs. • Ability to do group messaging, pre-scheduled and/or recurring messaging. • Goal is to get these APIs embedded in systems like EHRs, or integrated with banking systems. www. directtrust. org 1101 Connecticut Ave NW, Washington, DC 20036
Secure Enterprise Paging Admin Server SWITCH Org Interface Audit Server • Web based interface for an enterprise back office to message users (aka paging). • A hospital that has deployed pagers to their medical staff can use the 3 p. TALK app instead. • Unlike SMS, 3 p. TALK has guaranteed delivery and is secure. Also saves paging costs. • Ability to do group messaging, pre-scheduled and/or recurring messaging. • Goal is to get these APIs embedded in systems like EHRs, or integrated with banking systems. www. directtrust. org 1101 Connecticut Ave NW, Washington, DC 20036
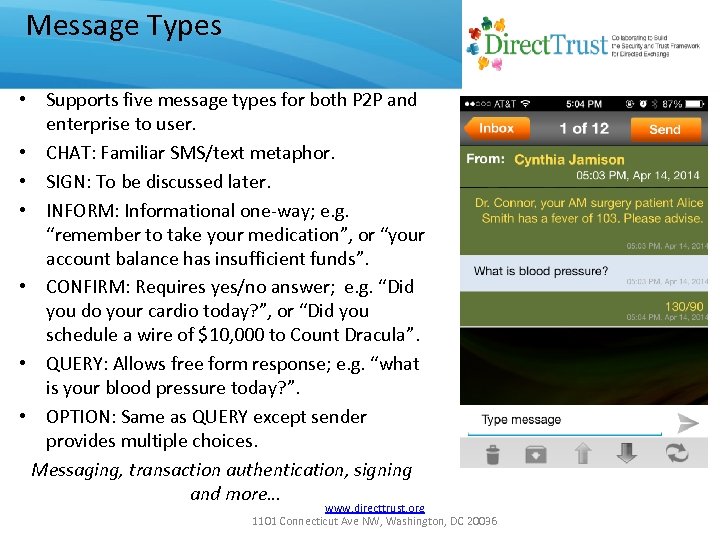 Message Types • Supports five message types for both P 2 P and enterprise to user. • CHAT: Familiar SMS/text metaphor. • SIGN: To be discussed later. • INFORM: Informational one-way; e. g. “remember to take your medication”, or “your account balance has insufficient funds”. • CONFIRM: Requires yes/no answer; e. g. “Did you do your cardio today? ”, or “Did you schedule a wire of $10, 000 to Count Dracula”. • QUERY: Allows free form response; e. g. “what is your blood pressure today? ”. • OPTION: Same as QUERY except sender provides multiple choices. Messaging, transaction authentication, signing and more… www. directtrust. org 1101 Connecticut Ave NW, Washington, DC 20036
Message Types • Supports five message types for both P 2 P and enterprise to user. • CHAT: Familiar SMS/text metaphor. • SIGN: To be discussed later. • INFORM: Informational one-way; e. g. “remember to take your medication”, or “your account balance has insufficient funds”. • CONFIRM: Requires yes/no answer; e. g. “Did you do your cardio today? ”, or “Did you schedule a wire of $10, 000 to Count Dracula”. • QUERY: Allows free form response; e. g. “what is your blood pressure today? ”. • OPTION: Same as QUERY except sender provides multiple choices. Messaging, transaction authentication, signing and more… www. directtrust. org 1101 Connecticut Ave NW, Washington, DC 20036
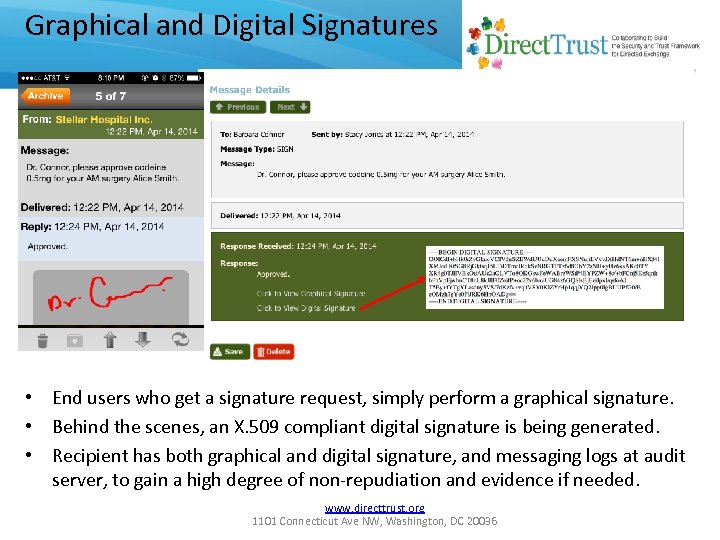 Graphical and Digital Signatures • End users who get a signature request, simply perform a graphical signature. • Behind the scenes, an X. 509 compliant digital signature is being generated. • Recipient has both graphical and digital signature, and messaging logs at audit server, to gain a high degree of non-repudiation and evidence if needed. www. directtrust. org 1101 Connecticut Ave NW, Washington, DC 20036
Graphical and Digital Signatures • End users who get a signature request, simply perform a graphical signature. • Behind the scenes, an X. 509 compliant digital signature is being generated. • Recipient has both graphical and digital signature, and messaging logs at audit server, to gain a high degree of non-repudiation and evidence if needed. www. directtrust. org 1101 Connecticut Ave NW, Washington, DC 20036
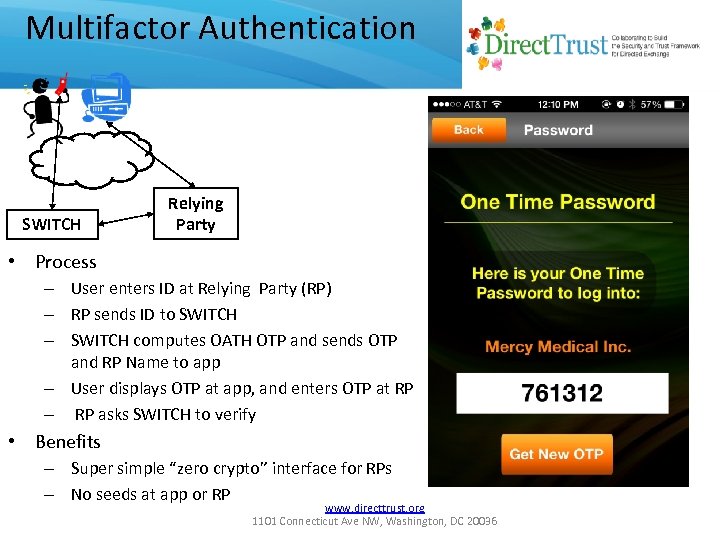 Multifactor Authentication SWITCH Relying Party • Process – User enters ID at Relying Party (RP) – RP sends ID to SWITCH – SWITCH computes OATH OTP and sends OTP and RP Name to app – User displays OTP at app, and enters OTP at RP – RP asks SWITCH to verify • Benefits – Super simple “zero crypto” interface for RPs – No seeds at app or RP www. directtrust. org 1101 Connecticut Ave NW, Washington, DC 20036
Multifactor Authentication SWITCH Relying Party • Process – User enters ID at Relying Party (RP) – RP sends ID to SWITCH – SWITCH computes OATH OTP and sends OTP and RP Name to app – User displays OTP at app, and enters OTP at RP – RP asks SWITCH to verify • Benefits – Super simple “zero crypto” interface for RPs – No seeds at app or RP www. directtrust. org 1101 Connecticut Ave NW, Washington, DC 20036
 Back Up – More Info • If you want to try app, we will set up an account on our guest network. Please contact: – – • Or, the screen shots that follow give you a taste of the product. – – • Ravi Ganesan, ravi@findravi. com, +1. 415. 680. 5746 Note we currently support i. OS and Android. Black. Berry is supported via Android side loading (no PUSH notifications). Messaging types – CONFIRM, QUERY, OPTION and INFORM. OTP and Federation Lite flow Sample Org Interface screen shot Sample Audit System screen shot You can also see videos at http: //3 ptalk. com/appinaction/ www. directtrust. org 1101 Connecticut Ave NW, Washington, DC 20036
Back Up – More Info • If you want to try app, we will set up an account on our guest network. Please contact: – – • Or, the screen shots that follow give you a taste of the product. – – • Ravi Ganesan, ravi@findravi. com, +1. 415. 680. 5746 Note we currently support i. OS and Android. Black. Berry is supported via Android side loading (no PUSH notifications). Messaging types – CONFIRM, QUERY, OPTION and INFORM. OTP and Federation Lite flow Sample Org Interface screen shot Sample Audit System screen shot You can also see videos at http: //3 ptalk. com/appinaction/ www. directtrust. org 1101 Connecticut Ave NW, Washington, DC 20036
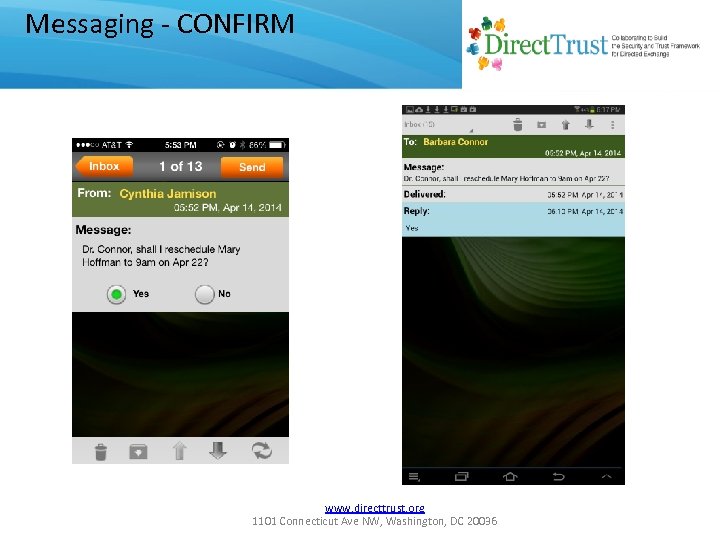 Messaging - CONFIRM www. directtrust. org 1101 Connecticut Ave NW, Washington, DC 20036
Messaging - CONFIRM www. directtrust. org 1101 Connecticut Ave NW, Washington, DC 20036
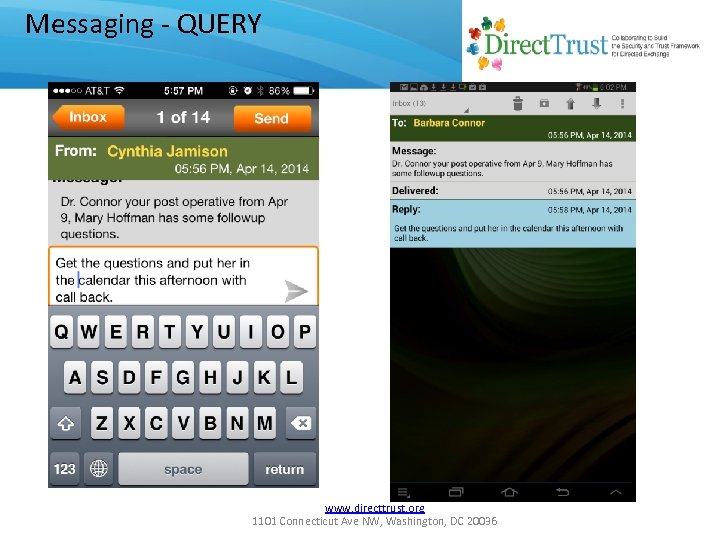 Messaging - QUERY www. directtrust. org 1101 Connecticut Ave NW, Washington, DC 20036
Messaging - QUERY www. directtrust. org 1101 Connecticut Ave NW, Washington, DC 20036
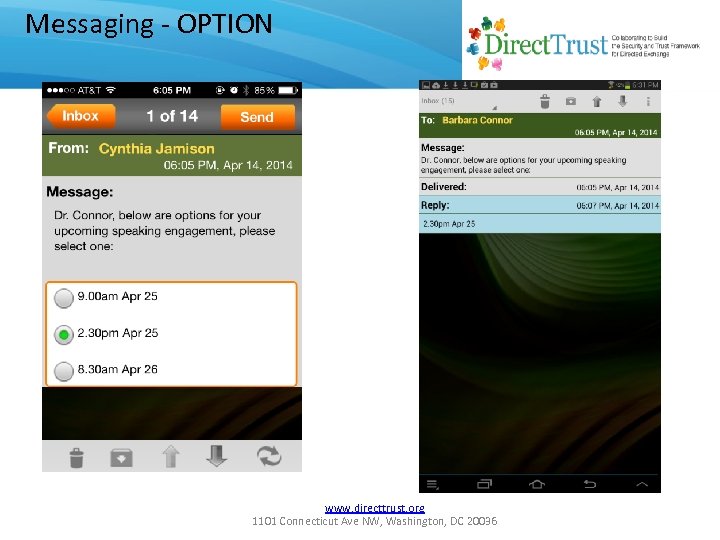 Messaging - OPTION www. directtrust. org 1101 Connecticut Ave NW, Washington, DC 20036
Messaging - OPTION www. directtrust. org 1101 Connecticut Ave NW, Washington, DC 20036
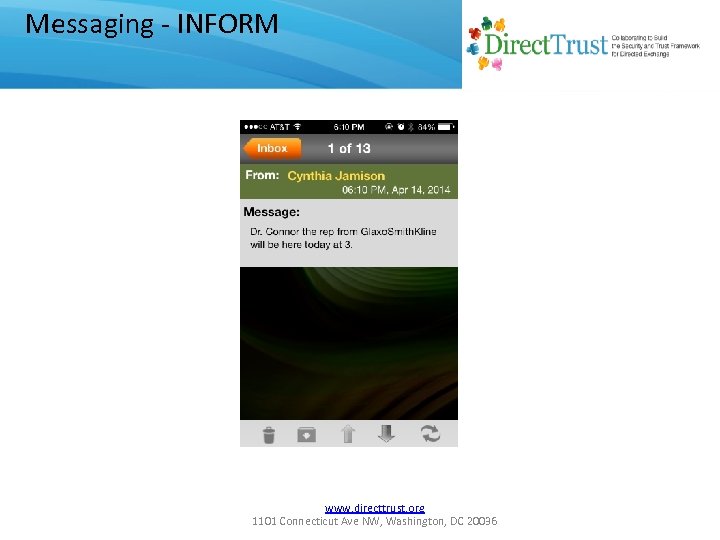 Messaging - INFORM www. directtrust. org 1101 Connecticut Ave NW, Washington, DC 20036
Messaging - INFORM www. directtrust. org 1101 Connecticut Ave NW, Washington, DC 20036
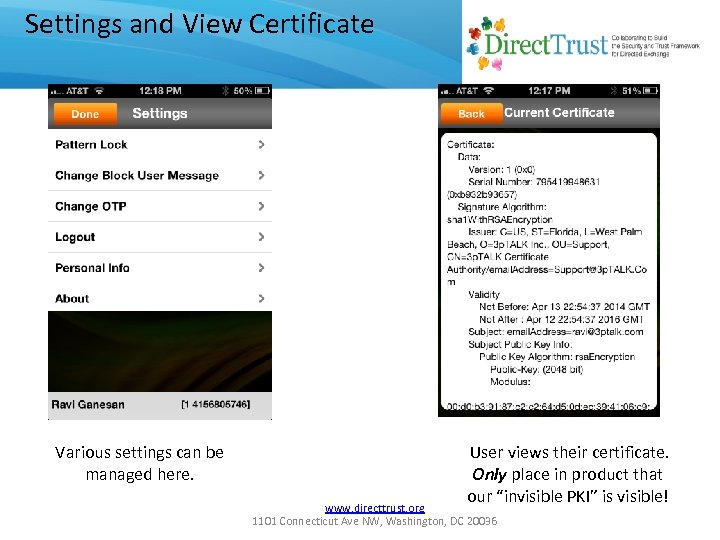 Settings and View Certificate Various settings can be managed here. User views their certificate. Only place in product that our “invisible PKI” is visible! www. directtrust. org 1101 Connecticut Ave NW, Washington, DC 20036
Settings and View Certificate Various settings can be managed here. User views their certificate. Only place in product that our “invisible PKI” is visible! www. directtrust. org 1101 Connecticut Ave NW, Washington, DC 20036
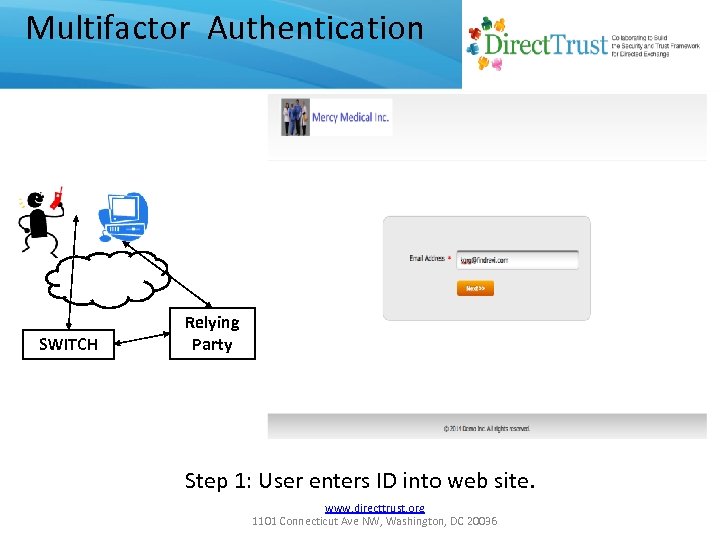 Multifactor Authentication SWITCH Relying Party Step 1: User enters ID into web site. www. directtrust. org 1101 Connecticut Ave NW, Washington, DC 20036
Multifactor Authentication SWITCH Relying Party Step 1: User enters ID into web site. www. directtrust. org 1101 Connecticut Ave NW, Washington, DC 20036
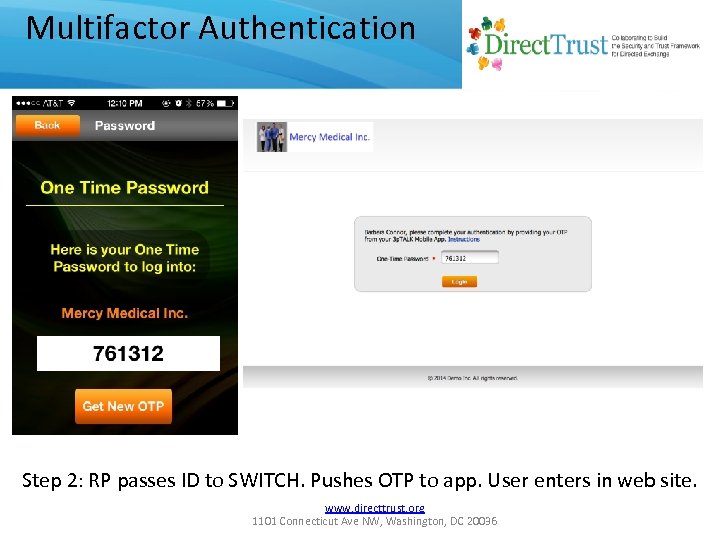 Multifactor Authentication Step 2: RP passes ID to SWITCH. Pushes OTP to app. User enters in web site. www. directtrust. org 1101 Connecticut Ave NW, Washington, DC 20036
Multifactor Authentication Step 2: RP passes ID to SWITCH. Pushes OTP to app. User enters in web site. www. directtrust. org 1101 Connecticut Ave NW, Washington, DC 20036
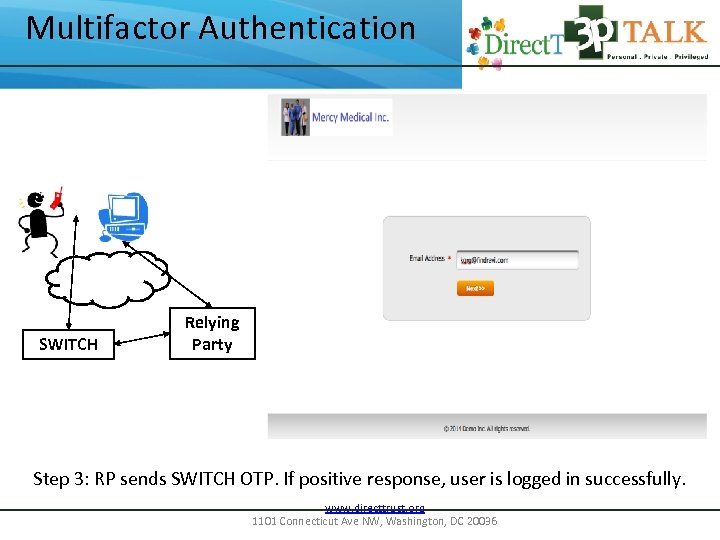 Multifactor Authentication SWITCH Relying Party Step 3: RP sends SWITCH OTP. If positive response, user is logged in successfully. www. directtrust. org 1101 Connecticut Ave NW, Washington, DC 20036
Multifactor Authentication SWITCH Relying Party Step 3: RP sends SWITCH OTP. If positive response, user is logged in successfully. www. directtrust. org 1101 Connecticut Ave NW, Washington, DC 20036
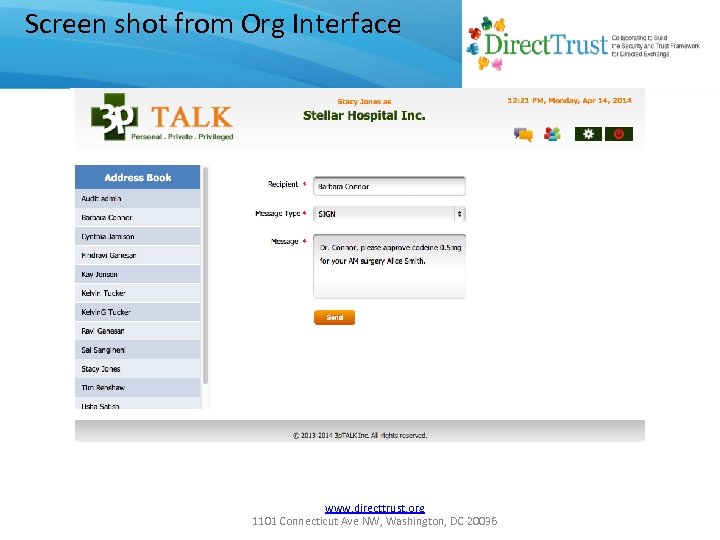 Screen shot from Org Interface www. directtrust. org 1101 Connecticut Ave NW, Washington, DC 20036
Screen shot from Org Interface www. directtrust. org 1101 Connecticut Ave NW, Washington, DC 20036
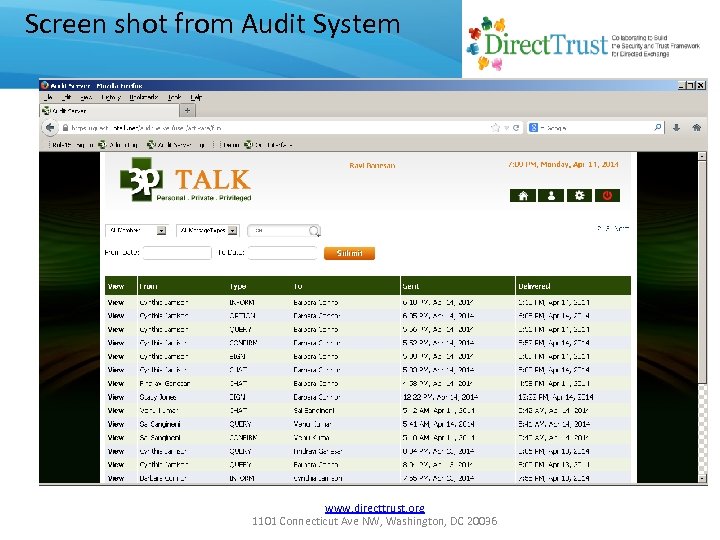 Screen shot from Audit System www. directtrust. org 1101 Connecticut Ave NW, Washington, DC 20036
Screen shot from Audit System www. directtrust. org 1101 Connecticut Ave NW, Washington, DC 20036


