fabde3a4a27f7add73d7399210ed1160.ppt
- Количество слайдов: 24
 Digital signature in automatic analyses for confidentiality against active adversaries Ilja Tšahhirov, Peeter Laud
Digital signature in automatic analyses for confidentiality against active adversaries Ilja Tšahhirov, Peeter Laud
 Goal of the analysis • Problem statement – Given the protocol (set of programs making calculations and exchanging messages) – It works with some secret data – No active adversary should be able to learn anything about the secret data • Automatically determine whether the protocol is secure or not.
Goal of the analysis • Problem statement – Given the protocol (set of programs making calculations and exchanging messages) – It works with some secret data – No active adversary should be able to learn anything about the secret data • Automatically determine whether the protocol is secure or not.
 Original technique • Published in: Peeter Laud. Symmetric encryption in automatic analyses for confidentiality against active adversaries. 2004 IEEE Symposium on Security and Privacy, pages 71 -85, May 2004. – – – Automatic analyzer present Programming language Single cryptographic primitive – symmetric encryption Definition of the adversary Definition of the security Protocol transformations
Original technique • Published in: Peeter Laud. Symmetric encryption in automatic analyses for confidentiality against active adversaries. 2004 IEEE Symposium on Security and Privacy, pages 71 -85, May 2004. – – – Automatic analyzer present Programming language Single cryptographic primitive – symmetric encryption Definition of the adversary Definition of the security Protocol transformations
 Programming language • Instruction set P : : = | | | k: =gen_key | y: =(x 1, …, xm) | x: = πim(y) x: =encrk(y) | y: =decrk(x) | x: =random | check(x=y) send(x) | x: =receivel x: =constant(b) | x: =y kp: =gen_key_pair | pk: =public_key(kp) sm: =signkp(m) | testpk(sm) m: =get_signed_message(sm) • The only cryptographic primitive in original analysis – symmetric encryption • Our contribution is adding the digital signature primitive support (commands in bold) to the language.
Programming language • Instruction set P : : = | | | k: =gen_key | y: =(x 1, …, xm) | x: = πim(y) x: =encrk(y) | y: =decrk(x) | x: =random | check(x=y) send(x) | x: =receivel x: =constant(b) | x: =y kp: =gen_key_pair | pk: =public_key(kp) sm: =signkp(m) | testpk(sm) m: =get_signed_message(sm) • The only cryptographic primitive in original analysis – symmetric encryption • Our contribution is adding the digital signature primitive support (commands in bold) to the language.
 Adversary • Adversary is active - it schedules the participants and relays messages between them • Can modify, create new, or not deliver sent messages
Adversary • Adversary is active - it schedules the participants and relays messages between them • Can modify, create new, or not deliver sent messages
 Security definition The protocol is considered secure if the secret message is computationally independent from the adversary’s view.
Security definition The protocol is considered secure if the secret message is computationally independent from the adversary’s view.
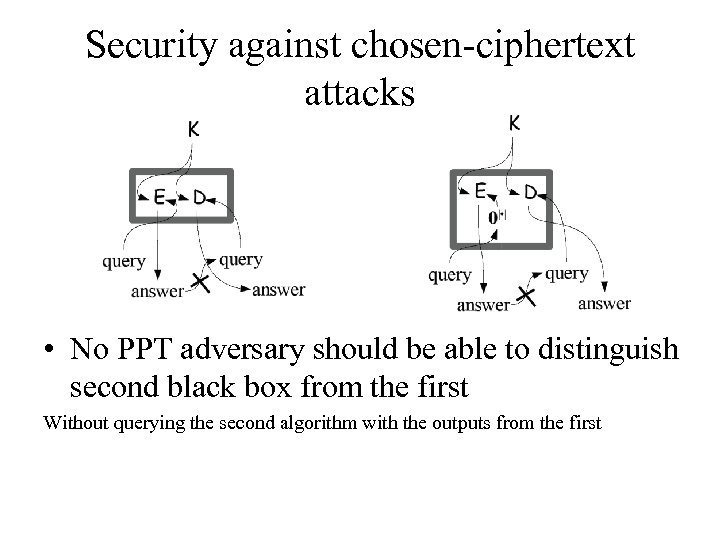 Security against chosen-ciphertext attacks • No PPT adversary should be able to distinguish second black box from the first Without querying the second algorithm with the outputs from the first
Security against chosen-ciphertext attacks • No PPT adversary should be able to distinguish second black box from the first Without querying the second algorithm with the outputs from the first
 Protocol transformations - encryption • During the analysis protocols are transformed • Protocols working with the first black box can be replaced to use the second (under certain conditions)
Protocol transformations - encryption • During the analysis protocols are transformed • Protocols working with the first black box can be replaced to use the second (under certain conditions)
 Information flow analysis • If some participant of the protocol contains a statement of the form x: =E(x 1, …, xn) there is an information flow from the variable xi to the variable x. • The protocol is deemed secure if M * y holds for no y affecting the adversary’s view. • The protocol transformation described above breaks some of those links.
Information flow analysis • If some participant of the protocol contains a statement of the form x: =E(x 1, …, xn) there is an information flow from the variable xi to the variable x. • The protocol is deemed secure if M * y holds for no y affecting the adversary’s view. • The protocol transformation described above breaks some of those links.
 Unforgeability under adaptive chosen message attack • The property we require signature scheme to satisfy • Adversary making queries to the signature oracle should not be able to create a valid signature for the message that has not previously been signed by it
Unforgeability under adaptive chosen message attack • The property we require signature scheme to satisfy • Adversary making queries to the signature oracle should not be able to create a valid signature for the message that has not previously been signed by it
 Protocol transformations – digital signature • Signature operations are replaced with checking whether the signed message being tested belongs to the set of the actually signed messages.
Protocol transformations – digital signature • Signature operations are replaced with checking whether the signed message being tested belongs to the set of the actually signed messages.
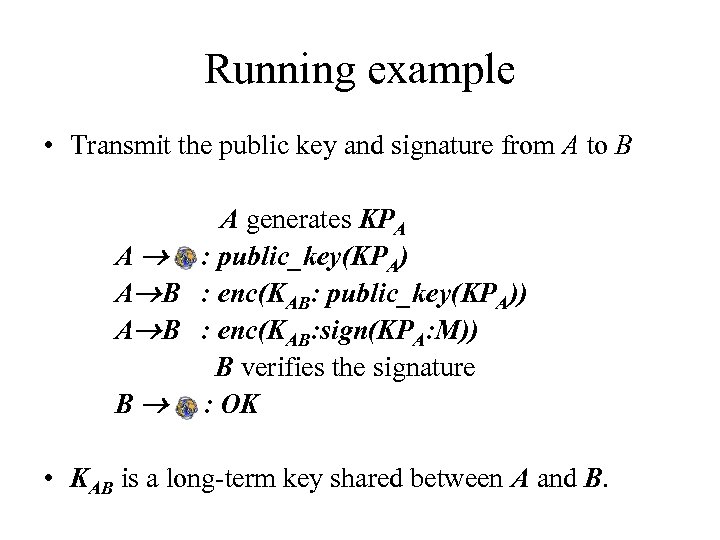 Running example • Transmit the public key and signature from A to B A generates KPA A : public_key(KPA) A B : enc(KAB: public_key(KPA)) A B : enc(KAB: sign(KPA: M)) B verifies the signature B : OK • KAB is a long-term key shared between A and B.
Running example • Transmit the public key and signature from A to B A generates KPA A : public_key(KPA) A B : enc(KAB: public_key(KPA)) A B : enc(KAB: sign(KPA: M)) B verifies the signature B : OK • KAB is a long-term key shared between A and B.
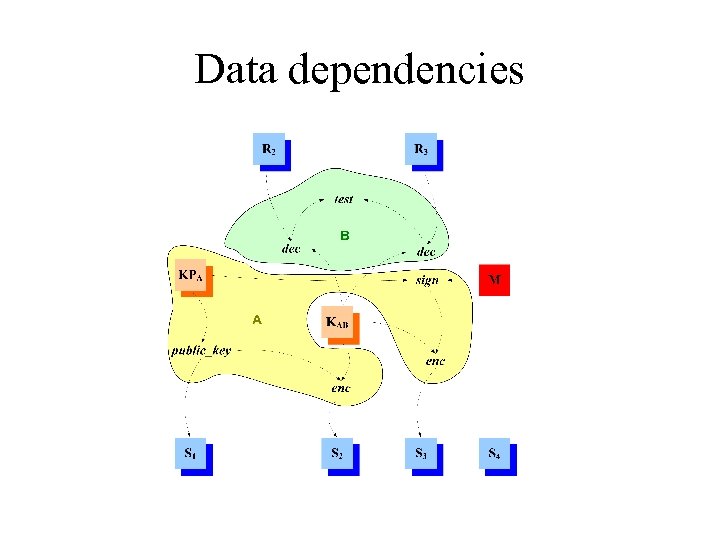 Data dependencies
Data dependencies
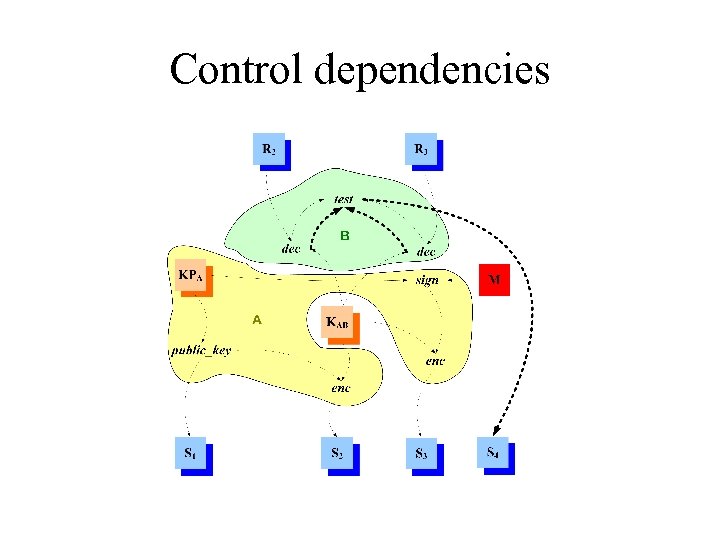 Control dependencies
Control dependencies
 Criterion for security No path from M to any Si The system is secure
Criterion for security No path from M to any Si The system is secure
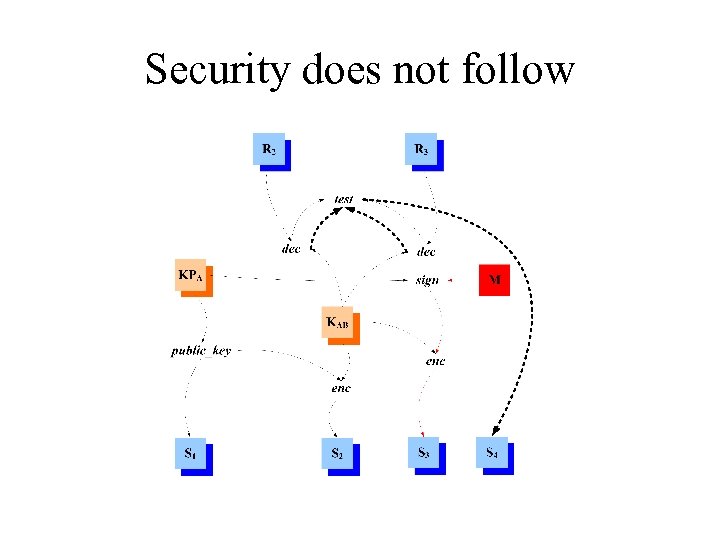 Security does not follow
Security does not follow
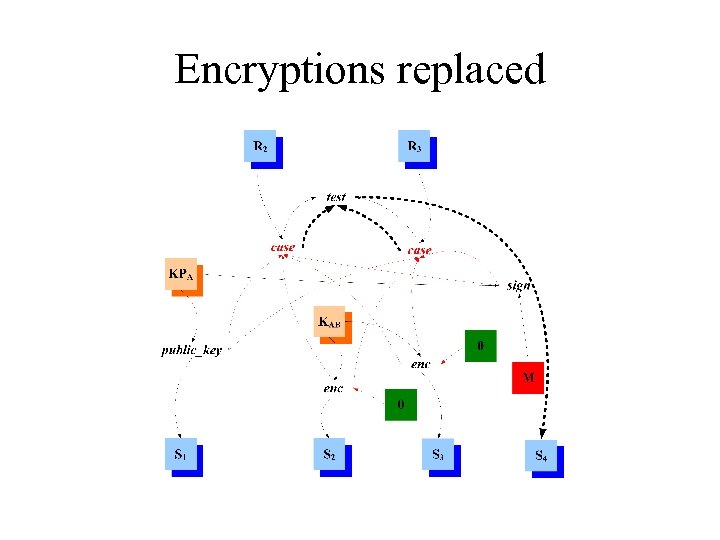 Encryptions replaced
Encryptions replaced
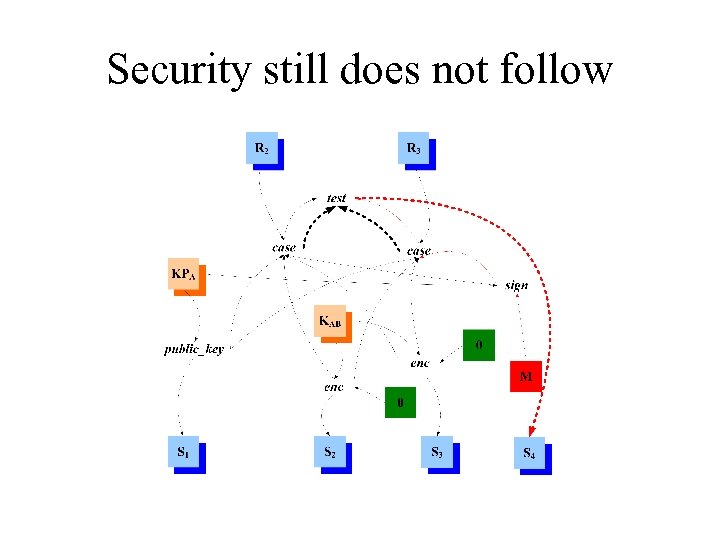 Security still does not follow
Security still does not follow
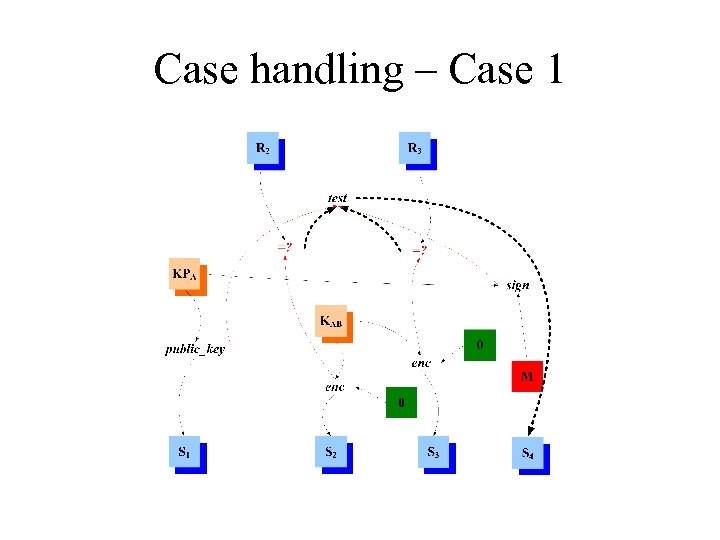 Case handling – Case 1
Case handling – Case 1
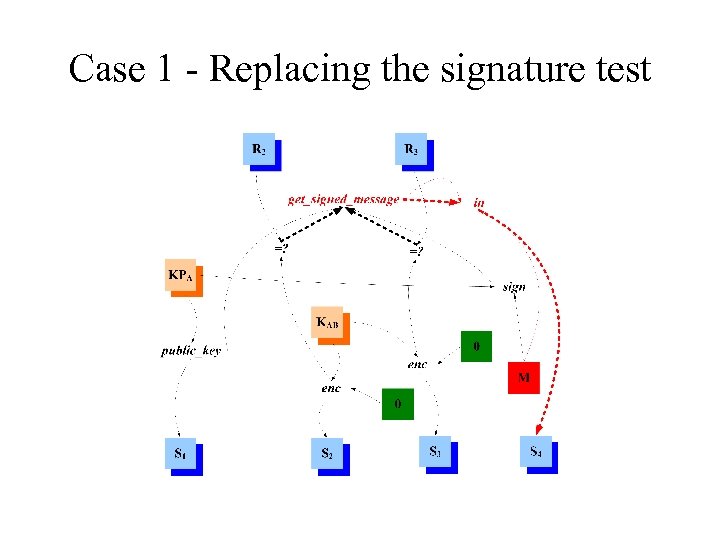 Case 1 - Replacing the signature test
Case 1 - Replacing the signature test
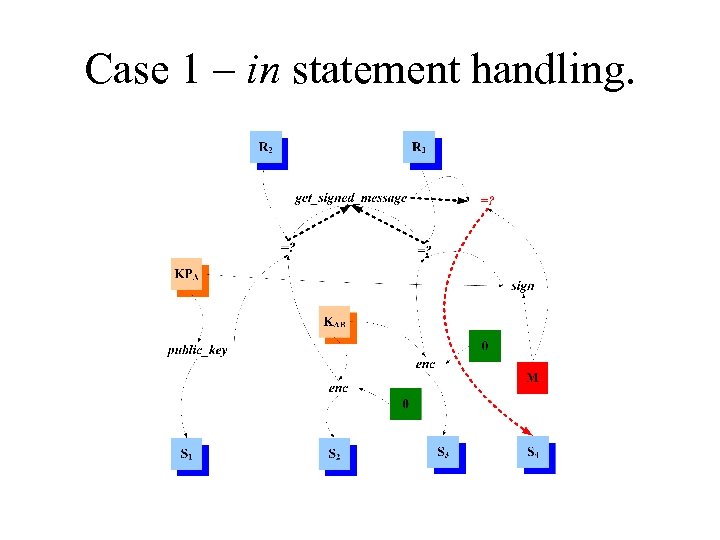 Case 1 – in statement handling.
Case 1 – in statement handling.
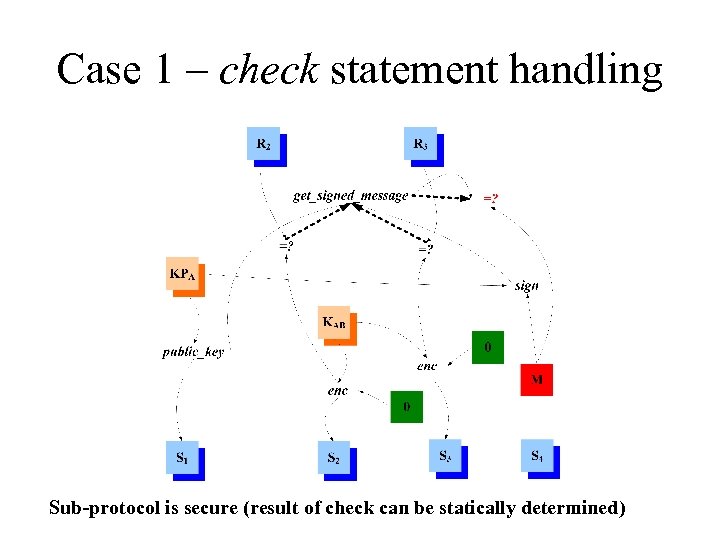 Case 1 – check statement handling Sub-protocol is secure (result of check can be statically determined)
Case 1 – check statement handling Sub-protocol is secure (result of check can be statically determined)
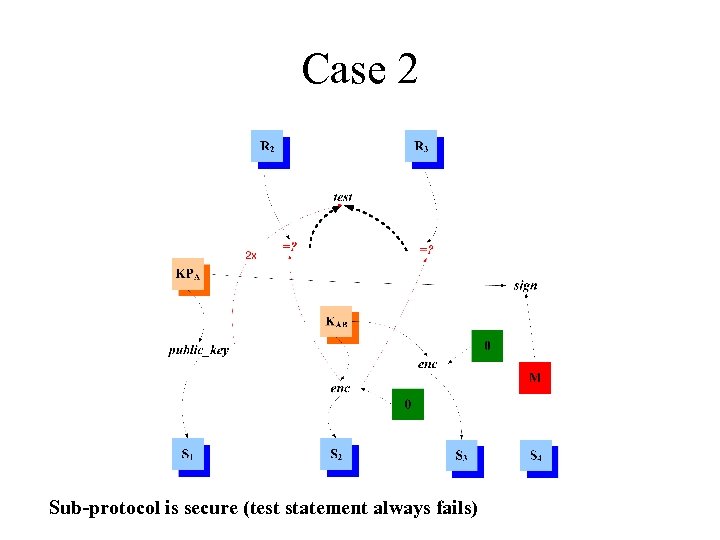 Case 2 Sub-protocol is secure (test statement always fails)
Case 2 Sub-protocol is secure (test statement always fails)
 Conclusions and future work • Conclusions – The presented technique can be used in automated analysis of the cryptographic protocols – Technique is published in Nordsec 2005 proceedings, p 29 -41. • Future work – Implementation of the automated analyser – Introducing the support for other cryptographic primitives
Conclusions and future work • Conclusions – The presented technique can be used in automated analysis of the cryptographic protocols – Technique is published in Nordsec 2005 proceedings, p 29 -41. • Future work – Implementation of the automated analyser – Introducing the support for other cryptographic primitives


