7152a9ae4804fda81e772962e5fdd23c.ppt
- Количество слайдов: 22
 Digital Signature and Authentication Protocols Ch 13 of Cryptography and Network Security -Third Edition by William Stallings Modified from lecture slides by Lawrie Brown CIM 3681 - PKI 05 1
Digital Signature and Authentication Protocols Ch 13 of Cryptography and Network Security -Third Edition by William Stallings Modified from lecture slides by Lawrie Brown CIM 3681 - PKI 05 1
 Digital Signatures & Authentication Protocols To guard against the baneful有害的, 使人苦惱的 influence exerted by strangers is therefore an elementary dictate of savage無禮的, 殘酷的, prudence原始的審慎, 慎重, 精明, . Hence before strangers are allowed to enter a district, or at least before they are permitted to mingle freely with the inhabitants, certain ceremonies are often performed by the natives of the country for the purpose of disarming the strangers of their magical powers, or of disinfecting, so to speak, the tainted atmosphere by which they are supposed to be surrounded. —The Golden Bough, Sir James George Frazer CIM 3681 - PKI 05 2
Digital Signatures & Authentication Protocols To guard against the baneful有害的, 使人苦惱的 influence exerted by strangers is therefore an elementary dictate of savage無禮的, 殘酷的, prudence原始的審慎, 慎重, 精明, . Hence before strangers are allowed to enter a district, or at least before they are permitted to mingle freely with the inhabitants, certain ceremonies are often performed by the natives of the country for the purpose of disarming the strangers of their magical powers, or of disinfecting, so to speak, the tainted atmosphere by which they are supposed to be surrounded. —The Golden Bough, Sir James George Frazer CIM 3681 - PKI 05 2
 Digital Signatures & Authentication Protocols n n n Digital Signatures 數位的簽署 Authentication Protocols 鑑別協定 Digital Signature Standard 標準 CIM 3681 - PKI 05 3
Digital Signatures & Authentication Protocols n n n Digital Signatures 數位的簽署 Authentication Protocols 鑑別協定 Digital Signature Standard 標準 CIM 3681 - PKI 05 3
 Digital Signatures n have looked at message authentication 訊息鑑別 q n digital signatures provide the ability to: q q q n but does not address issues of lack of trust 缺乏信任 Verify 証實 author, date & time of signature authenticate 鑑別message contents be verified by third parties to resolve disputes 爭執 hence include authentication function with additional capabilities CIM 3681 - PKI 05 4
Digital Signatures n have looked at message authentication 訊息鑑別 q n digital signatures provide the ability to: q q q n but does not address issues of lack of trust 缺乏信任 Verify 証實 author, date & time of signature authenticate 鑑別message contents be verified by third parties to resolve disputes 爭執 hence include authentication function with additional capabilities CIM 3681 - PKI 05 4
 Digital Signature Properties n must depend on the message signed n must use information unique 獨一無二的 to sender q to prevent both forgery and denial n must be relatively easy to produce must be relatively easy to recognize & verify n be computationally infeasible 不可實行的 to forge n 偽造 q q n with new message for existing digital signature with fraudulent欺詐的, 不正的, 不誠實的 digital signature for given message be practical save digital signature in storage CIM 3681 - PKI 05 5
Digital Signature Properties n must depend on the message signed n must use information unique 獨一無二的 to sender q to prevent both forgery and denial n must be relatively easy to produce must be relatively easy to recognize & verify n be computationally infeasible 不可實行的 to forge n 偽造 q q n with new message for existing digital signature with fraudulent欺詐的, 不正的, 不誠實的 digital signature for given message be practical save digital signature in storage CIM 3681 - PKI 05 5
 Direct Digital Signatures n n n involve only sender & receiver assumed receiver has sender’s public-key digital signature made by sender signing entire 整個, 全部 message or hash with private-key can encrypt using receivers public-key important that sign first then encrypt message & signature security depends on sender’s private-key CIM 3681 - PKI 05 6
Direct Digital Signatures n n n involve only sender & receiver assumed receiver has sender’s public-key digital signature made by sender signing entire 整個, 全部 message or hash with private-key can encrypt using receivers public-key important that sign first then encrypt message & signature security depends on sender’s private-key CIM 3681 - PKI 05 6
 Arbitrated 仲裁, 公斷 Digital Signatures n involves use of arbiter A q q n n n validates any signed message then dated and sent to recipient requires suitable level of trust in arbiter can be implemented with either private or public-key algorithms arbiter may or may not see message CIM 3681 - PKI 05 7
Arbitrated 仲裁, 公斷 Digital Signatures n involves use of arbiter A q q n n n validates any signed message then dated and sent to recipient requires suitable level of trust in arbiter can be implemented with either private or public-key algorithms arbiter may or may not see message CIM 3681 - PKI 05 7
 Authentication Protocols n n n used to convince 使確信 parties of each others identity and to exchange session keys may be one-way or mutual 彼此的; 共同的 key issues are q q confidentiality – to protect session keys timeliness合時; 適時; 剛巧 – to prevent replay重演 attacks CIM 3681 - PKI 05 8
Authentication Protocols n n n used to convince 使確信 parties of each others identity and to exchange session keys may be one-way or mutual 彼此的; 共同的 key issues are q q confidentiality – to protect session keys timeliness合時; 適時; 剛巧 – to prevent replay重演 attacks CIM 3681 - PKI 05 8
 Replay Attacks n where a valid signed message is copied and later resent q q n simple replay repetition that can be logged repetition that cannot be detected backward replay without modification countermeasures include q use of sequence 序 numbers (generally impractical) q timestamps 時間標志 (needs synchronized clocks) q challenge/response (using unique nonce當前 )要求/回應 CIM 3681 - PKI 05 9
Replay Attacks n where a valid signed message is copied and later resent q q n simple replay repetition that can be logged repetition that cannot be detected backward replay without modification countermeasures include q use of sequence 序 numbers (generally impractical) q timestamps 時間標志 (needs synchronized clocks) q challenge/response (using unique nonce當前 )要求/回應 CIM 3681 - PKI 05 9
 Using Symmetric Encryption n n as discussed previously can use a two-level hierarchy 階層 of keys usually with a trusted Key Distribution Center (KDC) q q q each party shares own master key with KDC generates session keys used for connections between parties master keys used to distribute these to them CIM 3681 - PKI 05 10
Using Symmetric Encryption n n as discussed previously can use a two-level hierarchy 階層 of keys usually with a trusted Key Distribution Center (KDC) q q q each party shares own master key with KDC generates session keys used for connections between parties master keys used to distribute these to them CIM 3681 - PKI 05 10
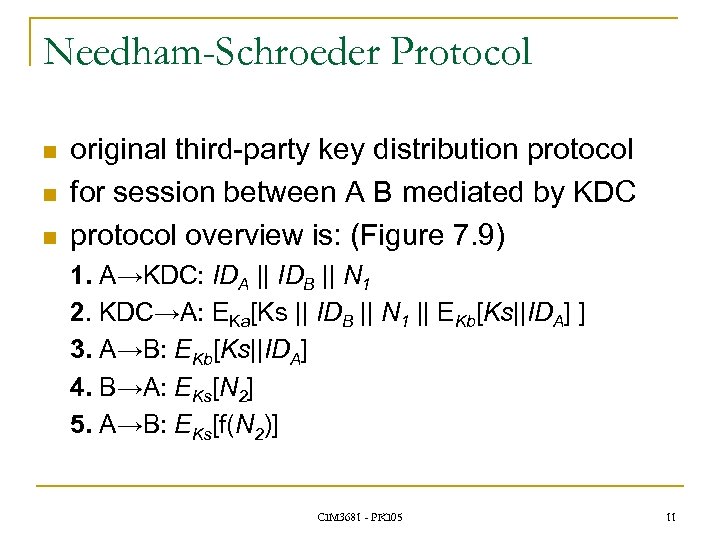 Needham-Schroeder Protocol n n n original third-party key distribution protocol for session between A B mediated by KDC protocol overview is: (Figure 7. 9) 1. A→KDC: IDA || IDB || N 1 2. KDC→A: EKa[Ks || IDB || N 1 || EKb[Ks||IDA] ] 3. A→B: EKb[Ks||IDA] 4. B→A: EKs[N 2] 5. A→B: EKs[f(N 2)] CIM 3681 - PKI 05 11
Needham-Schroeder Protocol n n n original third-party key distribution protocol for session between A B mediated by KDC protocol overview is: (Figure 7. 9) 1. A→KDC: IDA || IDB || N 1 2. KDC→A: EKa[Ks || IDB || N 1 || EKb[Ks||IDA] ] 3. A→B: EKb[Ks||IDA] 4. B→A: EKs[N 2] 5. A→B: EKs[f(N 2)] CIM 3681 - PKI 05 11
 Needham-Schroeder Protocol n n used to securely distribute a new session key for communications between A & B but is vulnerable to a replay attack if an old session key has been compromised 危害 q n then message 3 can be resent convincing B that is communicating with A modifications to address this require: q q timestamps (Denning 81) using an extra nonce (Neuman 93) CIM 3681 - PKI 05 12
Needham-Schroeder Protocol n n used to securely distribute a new session key for communications between A & B but is vulnerable to a replay attack if an old session key has been compromised 危害 q n then message 3 can be resent convincing B that is communicating with A modifications to address this require: q q timestamps (Denning 81) using an extra nonce (Neuman 93) CIM 3681 - PKI 05 12
 Using Public-Key Encryption n n have a range of approaches based on the use of public-key encryption need to ensure have correct public keys for other parties using a central Authentication Server (AS) various protocols exist using timestamps or nonces CIM 3681 - PKI 05 13
Using Public-Key Encryption n n have a range of approaches based on the use of public-key encryption need to ensure have correct public keys for other parties using a central Authentication Server (AS) various protocols exist using timestamps or nonces CIM 3681 - PKI 05 13
 Denning AS Protocol n Denning 81 presented the following: 1. A→AS: IDA || IDB 2. AS→A: EKRas[IDA||KUa||T] || EKRas[IDB||KUb||T] 3. A→B: EKRas[IDA||KUa||T] || EKRas[IDB||KUb||T] || EKUb[EKRas[Ks||T]] n n note session key is chosen by A, hence AS need not be trusted to protect it timestamps prevent replay but require synchronized clocks CIM 3681 - PKI 05 14
Denning AS Protocol n Denning 81 presented the following: 1. A→AS: IDA || IDB 2. AS→A: EKRas[IDA||KUa||T] || EKRas[IDB||KUb||T] 3. A→B: EKRas[IDA||KUa||T] || EKRas[IDB||KUb||T] || EKUb[EKRas[Ks||T]] n n note session key is chosen by A, hence AS need not be trusted to protect it timestamps prevent replay but require synchronized clocks CIM 3681 - PKI 05 14
 One-Way單向 Authentication n required when sender & receiver are not in communications at same time (eg. email) have header in clear so can be delivered by email system may want contents of body protected & sender authenticated CIM 3681 - PKI 05 15
One-Way單向 Authentication n required when sender & receiver are not in communications at same time (eg. email) have header in clear so can be delivered by email system may want contents of body protected & sender authenticated CIM 3681 - PKI 05 15
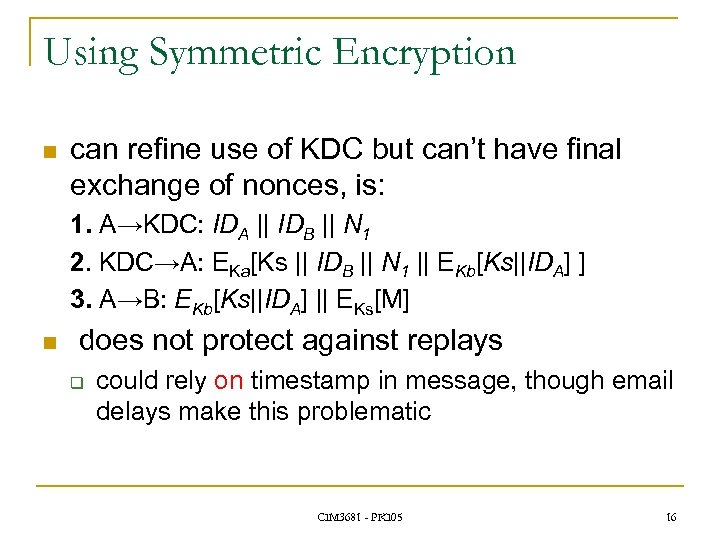 Using Symmetric Encryption n can refine use of KDC but can’t have final exchange of nonces, is: 1. A→KDC: IDA || IDB || N 1 2. KDC→A: EKa[Ks || IDB || N 1 || EKb[Ks||IDA] ] 3. A→B: EKb[Ks||IDA] || EKs[M] n does not protect against replays q could rely on timestamp in message, though email delays make this problematic CIM 3681 - PKI 05 16
Using Symmetric Encryption n can refine use of KDC but can’t have final exchange of nonces, is: 1. A→KDC: IDA || IDB || N 1 2. KDC→A: EKa[Ks || IDB || N 1 || EKb[Ks||IDA] ] 3. A→B: EKb[Ks||IDA] || EKs[M] n does not protect against replays q could rely on timestamp in message, though email delays make this problematic CIM 3681 - PKI 05 16
 Public-Key Approaches n n have seen some public-key approaches if confidentiality is major concern, can use: A→B: EKUb[Ks] || EKs[M] q has encrypted session key, encrypted message n if authentication needed use a digital signature with a digital certificate: A→B: M || EKRa[H(M)] || EKRas[T||IDA||KUa] q with message, signature, certificate CIM 3681 - PKI 05 17
Public-Key Approaches n n have seen some public-key approaches if confidentiality is major concern, can use: A→B: EKUb[Ks] || EKs[M] q has encrypted session key, encrypted message n if authentication needed use a digital signature with a digital certificate: A→B: M || EKRa[H(M)] || EKRas[T||IDA||KUa] q with message, signature, certificate CIM 3681 - PKI 05 17
 Digital Signature Standard (DSS) n n n n US Govt approved signature scheme FIPS 186 uses the SHA hash algorithm designed by NIST & NSA in early 90's DSS is the standard, DSA is the algorithm a variant on El. Gamal and Schnorr schemes creates a 320 bit signature, but with 512 -1024 bit security depends on difficulty of computing discrete logarithms CIM 3681 - PKI 05 18
Digital Signature Standard (DSS) n n n n US Govt approved signature scheme FIPS 186 uses the SHA hash algorithm designed by NIST & NSA in early 90's DSS is the standard, DSA is the algorithm a variant on El. Gamal and Schnorr schemes creates a 320 bit signature, but with 512 -1024 bit security depends on difficulty of computing discrete logarithms CIM 3681 - PKI 05 18
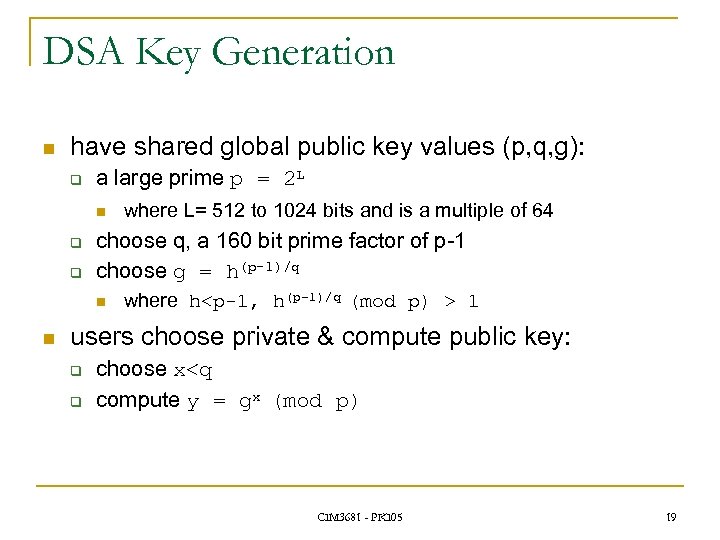 DSA Key Generation n have shared global public key values (p, q, g): q a large prime p = 2 L n q q choose q, a 160 bit prime factor of p-1 choose g = h(p-1)/q n n where L= 512 to 1024 bits and is a multiple of 64 where h
DSA Key Generation n have shared global public key values (p, q, g): q a large prime p = 2 L n q q choose q, a 160 bit prime factor of p-1 choose g = h(p-1)/q n n where L= 512 to 1024 bits and is a multiple of 64 where h
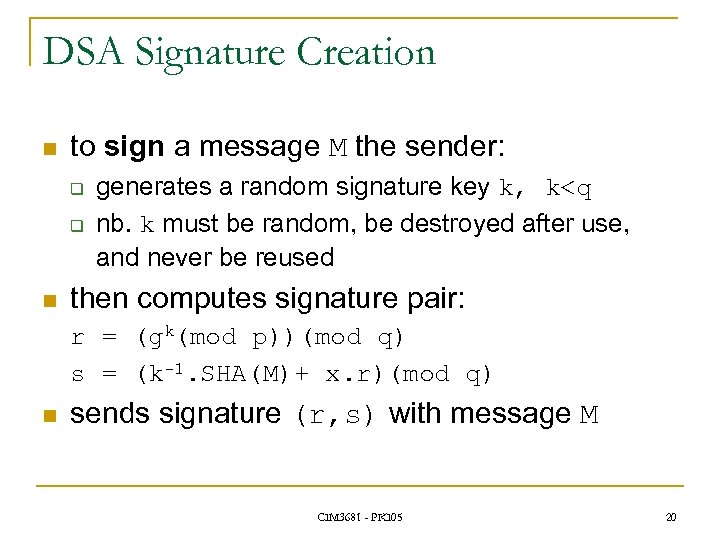 DSA Signature Creation n to sign a message M the sender: q q n generates a random signature key k, k
DSA Signature Creation n to sign a message M the sender: q q n generates a random signature key k, k
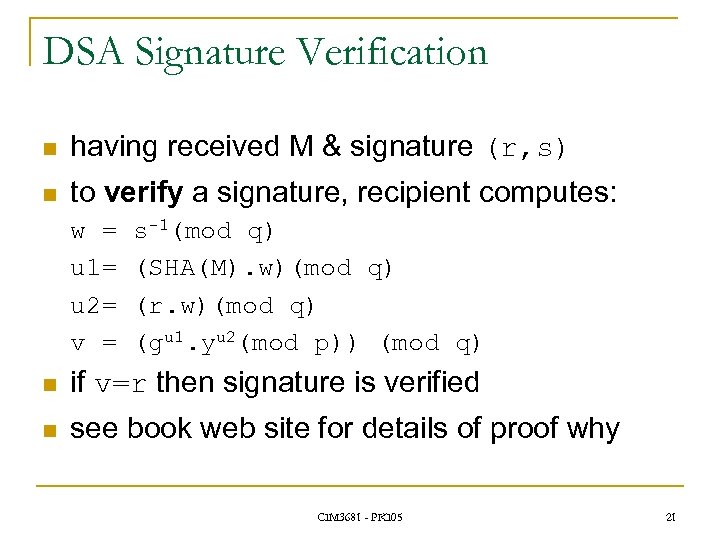 DSA Signature Verification n having received M & signature (r, s) n to verify a signature, recipient computes: w = u 1= u 2= v = s-1(mod q) (SHA(M). w)(mod q) (r. w)(mod q) (gu 1. yu 2(mod p)) (mod q) n if v=r then signature is verified n see book web site for details of proof why CIM 3681 - PKI 05 21
DSA Signature Verification n having received M & signature (r, s) n to verify a signature, recipient computes: w = u 1= u 2= v = s-1(mod q) (SHA(M). w)(mod q) (r. w)(mod q) (gu 1. yu 2(mod p)) (mod q) n if v=r then signature is verified n see book web site for details of proof why CIM 3681 - PKI 05 21
 Summary n have considered: q q q digital signatures authentication protocols (mutual & one-way) digital signature standard CIM 3681 - PKI 05 22
Summary n have considered: q q q digital signatures authentication protocols (mutual & one-way) digital signature standard CIM 3681 - PKI 05 22


