b790c60849a283bff80840425e2bd406.ppt
- Количество слайдов: 84

Digital Rights Management the Good, the Bad and the Ugly Mark Stamp Department of Computer Science San Jose State University stamp@cs. sjsu. edu DRM resources at http: //www. cs. sjsu. edu/faculty/stamp/DRM/ DRM 1

Who Am I? q 1992: Ph. D, Texas Tech q 1992 -1993: WPI q 1993 -2000: NSA q 2000 -2002: Media. Snap, Inc. q 2002 -Present: SJSU DRM 2
What was Media. Snap? q Silicon Valley startup company o Founded June 2000 o I joined in December 2000 Maximum of 15 employees q Not a dot-com q Funded by In-Q-Tel (CIA VC fund) q Digital rights management (DRM) product q DRM 3

Why Media. Snap? q NSA provided o o o q q Job security “Tenure” after 1 year Interesting work, good people, etc. Why leave NSA for startup company? Three reasons… 1. Money 2. Money (salary) 3. Money (benefits) (worthless stock options) DRM 4

Outline of Talk What is DRM? q Overview of Media. Snap DRM system q Overview of streaming media DRM model q Media. Snap’s competitors q TCG/NGSCB q Non-technical issues q Enterprise DRM q Conclusions q DRM 5

DRM Overview DRM 6

What is DRM? q “Remote control” problem q Digital book example q Digital music, video, etc. q Enterprise document protection q Privacy-enhancing technology? DRM 7

Persistent Protection q Restrictions q For o o o DRM example on use after delivery No copying Limited number of reads/plays Time limits: do not open until Christmas No forwarding Etc. 8

What to Do? q The honor system? q Give up? q q If you can’t beat ‘em, join ‘em. . . Lame software-based DRM? q Better software-based DRM? q Tamper-resistant hardware? o Stephen King’s, The Plant o Internet sales? HIPAA? SOA? etc. o The standard DRM system today DRM o Media. Snap’s goal o Closed systems: Game Cube, etc. o Open systems: TCG/NGSCB for PCs 9
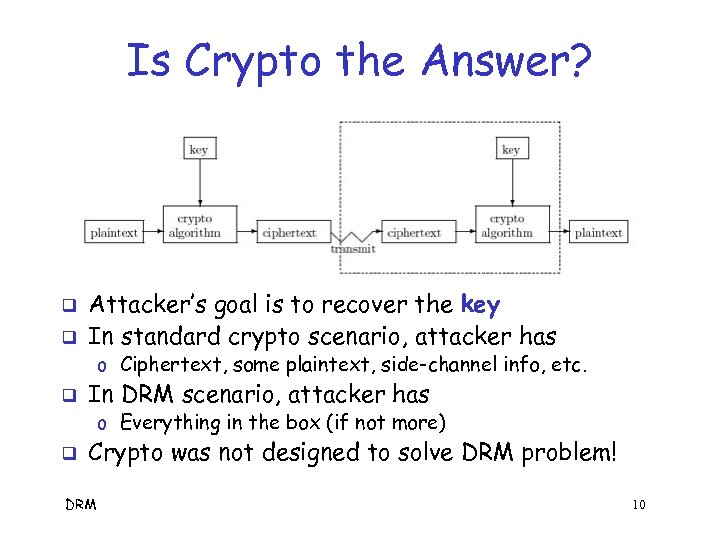
Is Crypto the Answer? q q Attacker’s goal is to recover the key In standard crypto scenario, attacker has o Ciphertext, some plaintext, side-channel info, etc. q In DRM scenario, attacker has o Everything in the box (if not more) q Crypto was not designed to solve DRM problem! DRM 10
Current State of DRM q At best, security by obscurity o A derogatory term in the security world q Secret designs o In violation of Kerckhoffs Principle q Crypto is king o “Whoever thinks his problem can be solved using cryptography, doesn’t understand his problem and doesn’t understand cryptography. ” --- Attributed by Roger Needham and Butler Lampson to each other DRM 11

Rules to the DRM Game q The analog hole o When content is rendered, it can be captured in analog form o DRM cannot prevent attack via the analog hole q Human nature matters o Absolute DRM security is impossible o Want something that “works” in practice o What works depends on context q DRM lives in no man’s land o Somewhere between CS and MIS DRM 12

Software-based DRM Strong software-based DRM is impossible q We can’t really hide a secret in software q To do so, we would have to prevent software reverse engineering (SRE) q User of system with full admin privilege can break anti-SRE protection q Bottom line: The killer attack on softwarebased DRM is software reverse engineering q DRM 13

Media. Snap DRM 14
Media. Snap DRM Overview q Server side o Secure Document Server (SDS) q Client side o PDF plugin (reader) DRM 15
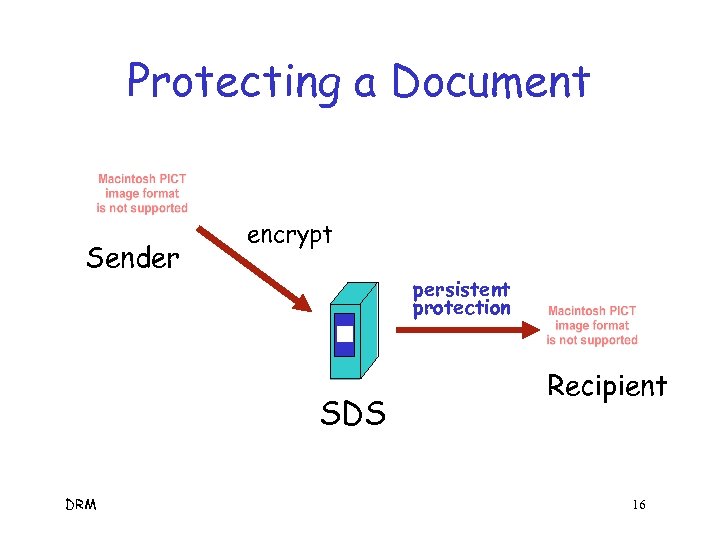
Protecting a Document Sender encrypt persistent protection SDS DRM Recipient 16
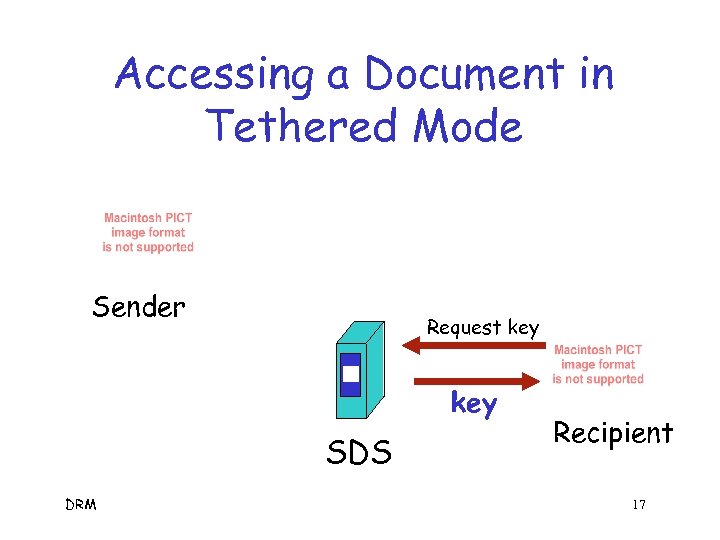
Accessing a Document in Tethered Mode Sender Request key SDS DRM Recipient 17
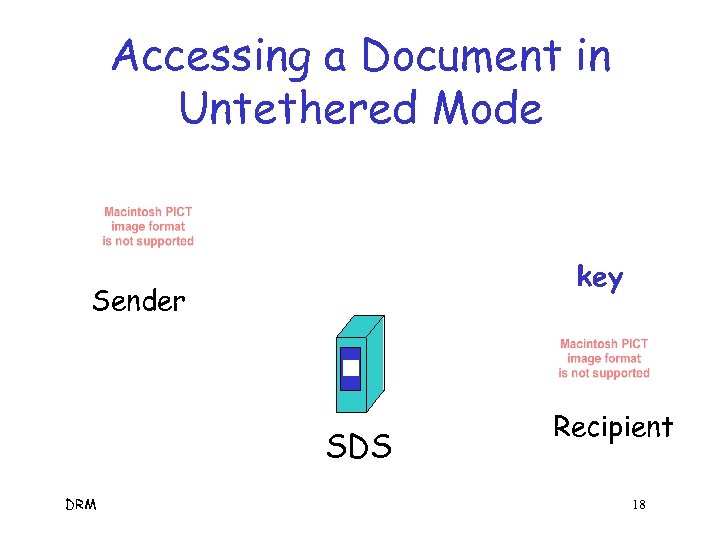
Accessing a Document in Untethered Mode key Sender SDS DRM Recipient 18
Tethered vs Untethered q Tethered advantages o Server controls access o Document can be “shredded” (Authentica) o Key is less exposed q Untethered advantages o Can access data without network connection o Key is “more exposed” q Media. Snap implemented both modes DRM 19
Security Issues q Server side (SDS) o Protect keys, authentication data, etc. o Apply persistent protection q Client side (Reader/PDF plugin) o Protect keys, authenticate user, etc. o Enforce persistent protection q DRM Remaining discussion concerns client 20
Security Overview Tamper-resistance Obscurity DRM 21
Tamper-Resistance Anti-debugger Encrypted code DRM 22

Obscurity q Applied to o o o q Key management Authentication Caching (keys, authentication, etc. ) Encryption and “scrambling” Key parts (data and/or code) Multiple keys/key parts Obscurity can only slow down attacker --the persistent attacker wins! DRM 23
Other Media. Snap Features q Code tamper checking (hashing) o Must know what code is executing q Anti-screen capture o Prevent most obvious attack on documents q Watermarking o In theory, can trace stolen content o In practice, watermarking is disappointing q “Unique-ification” (or metamorphism) o Break once, break everywhere (BOBE) resistant DRM 24

Other Measures/Concerns q General code obfuscation o Collberg and Thomborson o Questions concerning actual strength q Code “fragilization” (guards) o Code hash checks itself o Any change should cause code to break q Can we trust OS? o How can we protect ourselves? DRM 25

DRM for Streaming Media DRM 26

Attacks on Streaming Media q Spoof stream between endpoints q Man in the middle q Capture stream o Malicious software stealing stream at client end q Replay/redistribute DRM data 27

Design q Scrambling algorithms o Encryption-like algorithms o Many such algorithms avaliable q Negotiation of random algorithm o Server and client must share algorithm q Decryption at receiver end o Remove strong encryption q De-scrambling in device driver o Remove scrambling just prior to rendering DRM 28
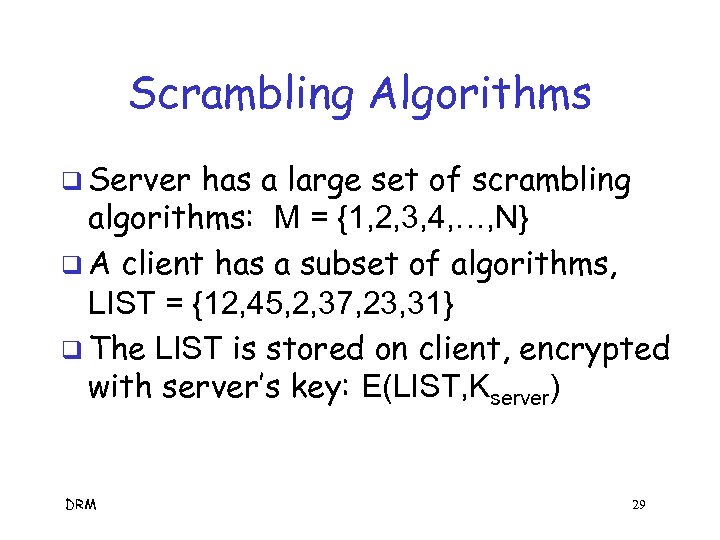
Scrambling Algorithms q Server has a large set of scrambling algorithms: M = {1, 2, 3, 4, …, N} q A client has a subset of algorithms, LIST = {12, 45, 2, 37, 23, 31} q The LIST is stored on client, encrypted with server’s key: E(LIST, Kserver) DRM 29
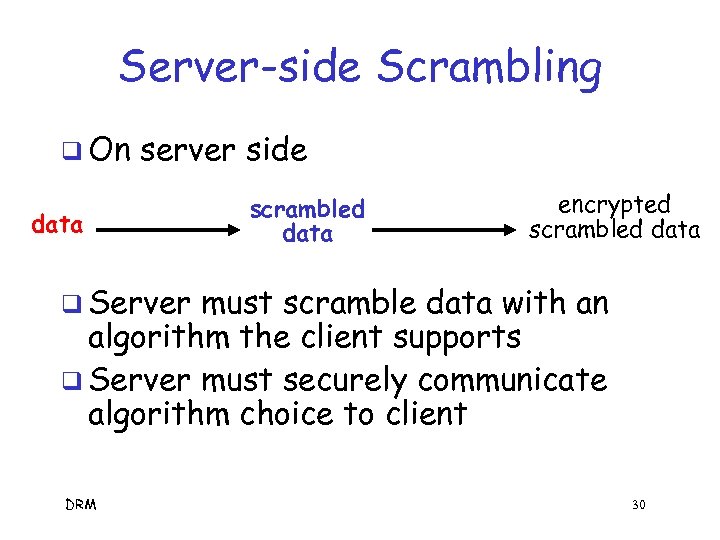
Server-side Scrambling q On server side data scrambled data encrypted scrambled data q Server must scramble data with an algorithm the client supports q Server must securely communicate algorithm choice to client DRM 30
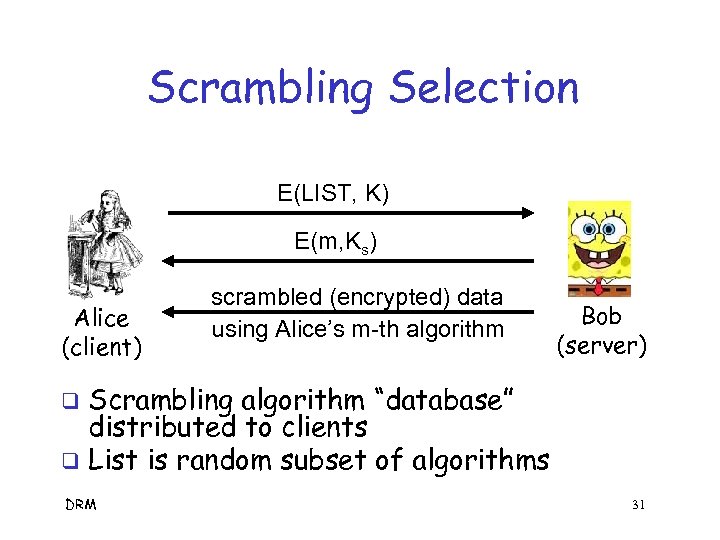
Scrambling Selection E(LIST, K) E(m, Ks) Alice (client) scrambled (encrypted) data using Alice’s m-th algorithm Bob (server) Scrambling algorithm “database” distributed to clients q List is random subset of algorithms q DRM 31
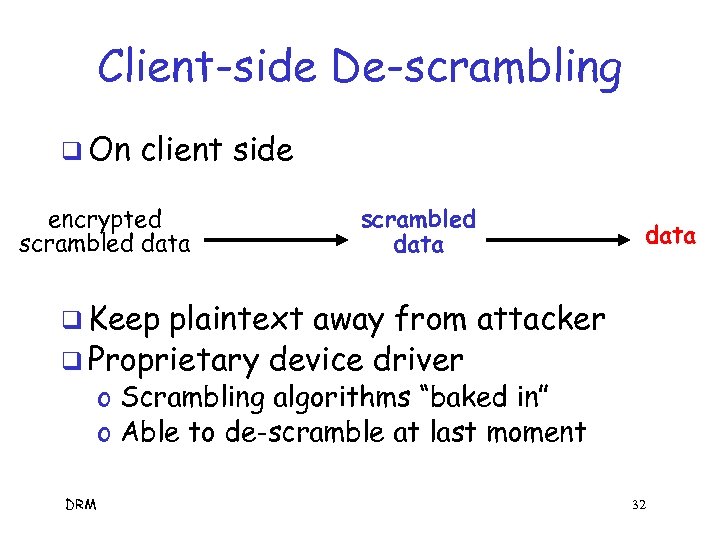
Client-side De-scrambling q On client side encrypted scrambled data q Keep plaintext away from attacker q Proprietary device driver o Scrambling algorithms “baked in” o Able to de-scramble at last moment DRM 32
Why Scrambling? Uniqueness or metamorphism q If a scrambling algorithm is known to be broken, server does not choose it q If client has too many broken algorithms, server can force upgrade q Proprietary algorithm harder to reverse engineer q We cannot trust crypto strength of proprietary algorithms, so we also encrypt q DRM 33

Why Uniqueness? The threat is reverse engineering (SRE) q Reverse engineering a standard crypto algorithm is easy (unnecessary) q Reverse engineering a scrambling algorithm is potentially much more difficult q We also encrypt so not violating Kerchoffs Principle (at least not too much…) q This is clearly security by obscurity and I’m not ashamed to admit it! q DRM 34

Exploit Systems and DRM 35

Exploit Systems q Exploit Systems (ES) management consists entirely of musicians o Not all of them are on drugs o They offered me a job with huge salary… o Payable as soon as the get funding q Exploit Systems international office? o A coffee shop in Palo Alto q Only in Silicon Valley… DRM 36

Exploit Systems is a “peer offering service” q Their web site is (purposely? ) vague on the definition of “peer offering service” q But I happen to know what they are doing. . . q ES tries to gently coerce people into paying for content obtained from a peer-to-peer (P 2 P) network q DRM 37
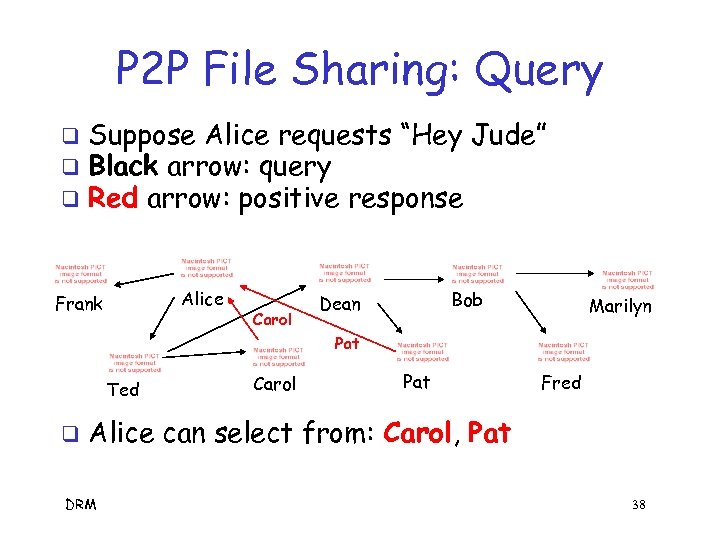
P 2 P File Sharing: Query q q q Suppose Alice requests “Hey Jude” Black arrow: query Red arrow: positive response Alice Frank Carol Bob Dean Marilyn Pat Ted q Carol Pat Fred Alice can select from: Carol, Pat DRM 38
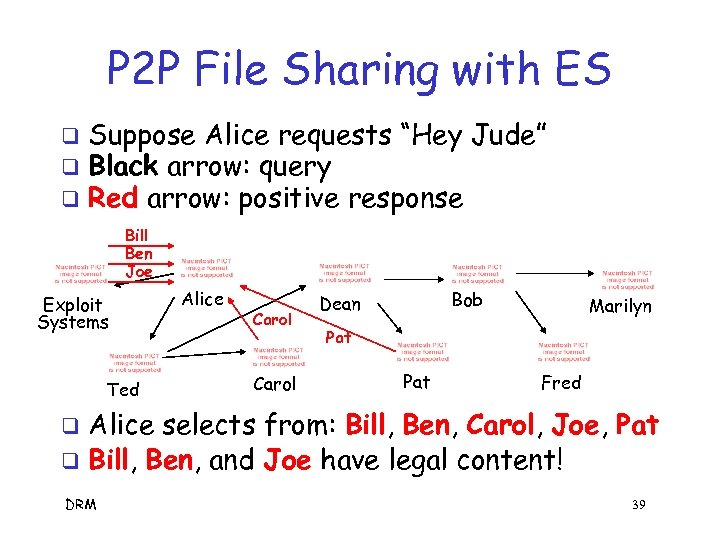
P 2 P File Sharing with ES q q q Suppose Alice requests “Hey Jude” Black arrow: query Red arrow: positive response Bill Ben Joe Exploit Systems Ted Alice Carol Bob Dean Marilyn Pat Fred Alice selects from: Bill, Ben, Carol, Joe, Pat q Bill, Ben, and Joe have legal content! q DRM 39

Exploit Systems Bill, Ben and Joe look legitimate q Goal is to have at least half of top 10 be Exploit Systems (ES) responses q If “victim” clicks on ES response q o DRM protected (legal) content downloaded o Then small payment required to play q Victim can choose not to pay o But then must download again o Is it worth the hassle to avoid paying $0. 25? o ES content also offers extras DRM 40

Exploit Systems A very clever idea q Piggybacking on P 2 P network q Weak DRM works well here q o Pirated content already exists o DRM only needs to be more hassle to break than hassle of clicking and waiting (a few times) q Current state of Exploit Systems? o Very little interest from the music industry o Lots of interest from the “adult” industry DRM 41

Enterprise DRM 42

Why Enterprise DRM? q Health Insurance Portability and Accountability Act (HIPAA) o Medical records must be protected o Fines of up to $10, 000 “per incident” q Sarbanes-Oxley Act (SOA) o Protect documents of interest to SEC o Also Draconian penalties q DRM required for regulatory compliance DRM 43
What’s Different in Enterprise DRM? Technically, it is similar to e-commerce q But motivation for DRM is different q o Regulatory compliance o Not to make money, but to not lose money! q Human dimension is also much different o Legal threats are far more plausible q Legally, corporation is probably off the hook provided active attack is necessary DRM 44
Enterprise DRM Moderate DRM security is sufficient q Policy management issues q o Easy to set policies for groups, roles, etc. o Yet policies must be flexible q Authentication issues o Must interface with existing system o Must prevent network authentication spoofing (authenticate the authentication server) q Enterprise DRM is a solvable problem DRM 45

Case Study I Sarbanes-Oxley Act (SOA) q Requires retention/tagging of all documents related to SEC disclosure q DRM software q o Tag new documents created by SOA authors o Allow any SOA author to modify tagged doc’s o Read-only access for non-SOA authors q Transparent to users --- comply by default! DRM 46

Case Study II Access control without authentication q Example: A large automotive company wants to limit access to documents to q o Company employees authoring documents o Partner company employees to whom documents are electronically distributed o Other partner company employees to whom the documents are purposely re-distributed DRM 47

Case Study II Accomplished via simple shared password q Modest security requirement q o Met with minimal complexity o Works with any partner’s system q Risk of unauthorized password sharing o Acceptable due to legal obligations Deployment will reach 10’s of thousands q Modest DRM software suffices q DRM 48

DRM Nonsense DRM 49

Silly DRM q We’ll only consider a few examples o o o DRM Patently obvious Crypto claims Extremely silly stuff Adobe’s “Respect” model Microsoft’s MS-DRM 50

Inter. Trust “…a company whose business model appears to rely entirely on legal filings against Microsoft. ” DRM 51

Absurd Crypto Claims Q: How does Atabok security compare to the competition? A: The majority of service providers offer the ability to encrypt at 128 bits. Atabok encrypts your content with 256 -bit encryption, which is exponentially more secure. DRM 52

Extremely Silly q Secret. Seal’s five radical innovations o o o Hieroglyphic passwords Variable-length encrypted keys “Morphogenetic” encryption algorithm No encryption formula in software The use of public keys q Do DRM these guys still exist? 53

Adobe’s “Respect” Model Adobe e. Books and PDF protection q Adobe documentation: “It is up to the implementors of PDF viewer applications to respect the intent of the document creator by restricting access to an encrypted PDF file according to passwords and permissions contained in the file. ” q Fail to “respect the intent” and goto jail! q o First prosecution under DMCA DRM 54

MS-DRM (version 2) MS-DRM: an early Microsoft DRM attempt q MS-DRM employed q o o q Weak proprietary block cipher (Multi. Swap) Multiswap used for hashing No controlled execution No obfuscation, no individualization, etc. Hard to believe this was serious DRM effort! DRM 55

Microsoft’s NGSCB DRM 56

Next Generation Secure Computing Base q q q NGSCB pronounced “n scub” (the G pronounces like a U after migrating to the right) Will be part of Microsoft’s Longhorn OS TCG (Trusted Computing Group) o Led by Intel, TCG makes special hardware q q NGSCB is the part of Windows that will interface with TCG hardware TCG/NGSCB formerly TCPA/Palladium o Why the name changes? DRM 57

NGSCB The original motivation for TCG/NGSCB was digital rights management (DRM) q Today, it is promoted as general securityenhancing technology q o DRM just one of many potential applications q Depending on who you ask, TCG/NGSCB is o Trusted computing o Treacherous computing DRM 58

Motivation for TCG q Closed systems: Game consoles, smartcards, etc. o Good at protecting secrets (tamper resistant) o Good at forcing people to pay o Limited flexibility q Open systems: PCs o Incredible flexibility o Poor at protecting secrets o Poor at protecting their own software q q TCG goal is to provide closed system security benefits on an open system “A virtual set-top box inside your PC” --- Rivest DRM 59

TCG/NGSCB q TCG provides tamper-resistant hardware o Secure place to store cryptographic key o Keys (or other secrets) secure even from a legitimate user with full admin privileges TCG hardware is in addition to ordinary hardware, not in place of it q PC has two OSs --- usual OS and special “trusted” OS to deal with TCG hardware q NGSCB is Microsoft’s version of secure OS q DRM 60

NGSCB Design Goals According to Microsoft q Provide high assurance o High confidence that system behaves correctly o Correct behavior even if system is under attack Provide authenticated operation q Protection against hardware tampering is not a design goal of NGSCB q o Hardware tampering is the domain of TCG DRM 61

Disclaimer q NGSCB details are sketchy q Based on talk presented at RSA Conference 2004, Microsoft has not worked out all of the details q What follows are my best guesses q This should all become much clearer in the not-too-distant future DRM 62
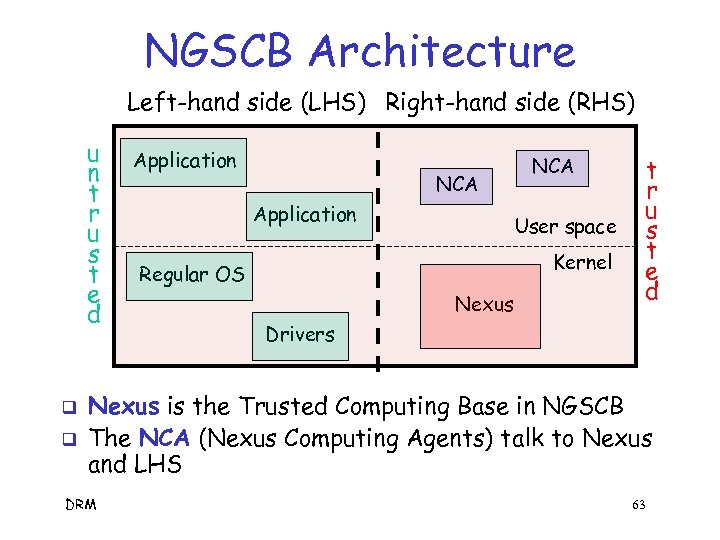
NGSCB Architecture Left-hand side (LHS) Right-hand side (RHS) u n t r u s t e d q q Application NCA Application User space Kernel Regular OS Nexus t r u s t e d Drivers Nexus is the Trusted Computing Base in NGSCB The NCA (Nexus Computing Agents) talk to Nexus and LHS DRM 63

NGSCB q NGSCB “feature groups” 1. Strong process isolation o Processes do not interfere with each other 2. Sealed storage o Data protected (tamper resistant hardware) 3. Secure path o Paths to and from I/O protected 4. Attestation o “Things” securely authenticated o Allows TCB to be extended via NCAs r DRM 1. , 2. and 3. aimed at malicious code 64
Process Isolation Curtained memory q Process isolation and the OS q o Trusted OS protected from insecure OS o Isolate trusted OS from BIOS, device drivers q Process isolation and NCAs o o DRM NCAs isolated from software they do not trust Trust determined by users --- to an extent… User can disallow a trusted NCA User cannot allow an untrusted NCA 65

Sealed Storage q Sealed storage contains secret data o If code X wants access to secret, a hash of X must be verified (must be sure X is trusted) o Implemented via symmetric key cryptography Confidentiality of secret is protected since only accessed by trusted software q Integrity of secret is assured since it’s in sealed storage q DRM 66
Secure Path q Secure path for input o From keyboard to Nexus o From mouse to Nexus q Secure path for output o From Nexus to the screen q Details DRM are vague 67

Attestation (1) q Secure authentication of things o Authenticate devices, services, code, etc. o Separate from user authentication q Public key cryptography used o Certified key pair required o Private key not user-accessible o Sign and send result to remote system q Nexus “extended” via attestation of NCAs o This is a major feature DRM 68

Attestation (2) q Public key required to verify attestation o Verification (i. e. , public key) reveals the user o Anonymity is lost q Trusted third party (TTP) can be used o TTP verifies signature o Then TTP vouches for signature to recipient o Anonymity preserved (except to TTP) q Claimed support for zero knowledge proofs o Verify knowledge of a secret without revealing it o Anonymity “preserved unconditionally” DRM 69

NGSCB Compelling Apps (1) Type a Word document in Windows q Move document to RHS q o Trusted area Read document carefully q Digitally sign the document q What you see is what you sign q o Virtually impossible to assure this on your PC! DRM 70

NGSCB Compelling Apps (2) Digital Rights Management (DRM) q DRM problems solved by NGSCB q Protect secret --- sealed storage q o Impossible without something like NGSCB q Scraping data --- secure path o Can’t prevent without something like NGSCB q Positively ID users --- attestation o Higher assurance with NBSCB DRM 71

NGSCB Design Principles According to Microsoft q q Everything in Windows must work in NGSCB User is in charge of o Which Nexuses (Nexii? ) will run on system o Which NCAs allowed to identify the system, etc. q q q No external process can enable Nexus or NCA Nexus does not block, delete or censor any data (NCA does, but NCAs must be authorized by user) Nexus source code publicly available DRM 72

NGSCB Critics There are many critics --- we consider two q Ross Anderson q o Perhaps the most influential critic o One of the harshest (extreme? ) critics q Clark Thomborson o Lesser-known critic o More rational (IMHO) DRM 73

Anderson’s NGSCB Criticism (1) Digital object controlled by its creator, not user of machine where it currently resides q Why? q o Creator can specify the NCA o If user does not accept NCA, access is denied o Aside: Such control is good in MLS applications q MS Word could encrypt documents with key only available to Microsoft products, then… o Very difficult to stop using Microsoft products! DRM 74

Anderson’s NGSCB Criticism (2) Files from a compromised machine could be blacklisted (e. g. , to prevent music piracy) q Suppose “everyone in China uses same copy of Microsoft Word” q o If you stop this copy from working on all NGSCB machines, Chinese users will not use NGSCB o Instead, make all NGSCB machines refuse to open documents created with this instance of Word! q I’m not convinced… DRM 75

Anderson’s NGSCB Criticism (3) Going off the deep end? q “The Soviet Union tried to register and control all typewriters. NGSCB attempts to register and control all computers. ” q “In 2010 President Clinton may have two red buttons on her desk --- one that sends missiles to China and another that turns off all of the PCs in China…” q DRM 76

Thomborson’s NGSCB Criticism NGSCB acts like a security guard q By passive observation, NGSCB “security guard” can see lots of sensitive information q How to know NGSCB is not spying on you? q According to Microsoft q o Nexus software will be public o NCAs can be debugged (for app development) o NGSCB is strictly “opt in” q But… release version of NCA not debuggable and versions have different hash values! DRM 77

NGSCB Bottom Line (1) TCG/NGSCB provides a trusted OS buried within an open platform q Without something similar, PC may lose out q o Particularly in entertainment-related areas With NGSCB it is claimed that users will lose some control over their PCs q But users must choose to “opt in” q o If user does not opt in, what has been lost? DRM 78

NGSCB Bottom Line (2) NGSCB is a trusted system q Only a trusted system can break security q o By definition, an untrusted system is not trusted with security critical tasks o If untrusted system does not perform as expected, security is not at risk o Also by definition, a trusted system is trusted with security critical tasks o If trusted system does not perform as expected, security is at risk DRM 79

DRM Conclusions DRM 80

My DRM Theories My theories, which are mine… q DRM for e-commerce q Strong DRM in software is impossible Moderate DRM is possible in some cases Weak DRM is OK if business model supports it Charging $1/song is not supportable given P 2 P, high speed Internet connections, etc. o NGSCB may tilt the balance somewhat o o q DRM in enterprise DRM o Legal mandates driving adoption o Realistic legal threat enhances DRM greatly 81
Conclusions q Current DRM systems are weak o Ironically, weak systems have worked better than (moderately) strong systems, at least so far o Stronger systems more complex/cumbersome q Ideal software-based DRM… o o DRM Individual content is non-trivial to attack Overall system survives repeated attacks In other words, BOBE-resistant Is this possible? 82
DRM References q M. Stamp, Digital rights management: The technology behind the hype, Journal of Electronic Commerce Research, http: //www. csulb. edu/web/journals/jecr/issues/20033/paper 3. pdf q M. Stamp, Risks of digital rights management, Communications of the ACM, http: //www. csl. sri. com/users/neumann/insiderisks. html#147 q M. Stamp, Digital rights management: For better or for worse? , Extreme. Tech, http: //www. extremetech. com/article 2/0, 3973, 1051610, 00. asp q E. J. Sebes and M. Stamp, Enterprise digital rights management: ready for prime time? http: //www. bcr. com/bcrmag/2004/03/p 52. asp q P. Biddle, et. al. , The darknet and the future of content distribution, http: //crypto. stanford. edu/DRM 2002/darknet 5. doc DRM 83

NGSCB References q NGSCB: Trusted Computing Base and Software Authentication, http: //www. microsoft. com/resources/ngscb/documents/ngscb_tcb. doc q P. England, et al, A Trusted Open Platform, http: //www. cs. cornell. edu/People/egs/syslunch-spring 04/palladium. pdf q E. Cram, Migrating Applications to NGSCB, http: //www. intel. com/idf/us/fall 2003/presentations/F 03 USSCMS 22_OS. pdf q R. Merritt, Cryptographers Sound Warnings on Microsoft Security Plan, http: //www. eetimes. com/sys/news/OEG 20030415 S 0013 DRM 84
b790c60849a283bff80840425e2bd406.ppt