d912939148d93b8b5e4c61ab04bd0339.ppt
- Количество слайдов: 17
 Digital Inheritance of Personal and Commercial Content Using DRM H. Li, NXP Research M. Petkovic, Philips Research CCNC’ 07 DRM workshop, Jan 11 2007
Digital Inheritance of Personal and Commercial Content Using DRM H. Li, NXP Research M. Petkovic, Philips Research CCNC’ 07 DRM workshop, Jan 11 2007
 Content • • • Introduction Private content protection model using DRM Inheritance protocols Digital last will Conclusions NXP Research, 11/01/07, H. Li 2
Content • • • Introduction Private content protection model using DRM Inheritance protocols Digital last will Conclusions NXP Research, 11/01/07, H. Li 2
 People own and manage exploding amount of digital content in the whole life • Personal content and commercial content – Personal digital history: photos and video, health info, financial info, behaviours, … – Music, movies… • More will be protected for privacy and for copyright Hackers & Users & Observers NXP Research, 11/01/07, H. Li 3
People own and manage exploding amount of digital content in the whole life • Personal content and commercial content – Personal digital history: photos and video, health info, financial info, behaviours, … – Music, movies… • More will be protected for privacy and for copyright Hackers & Users & Observers NXP Research, 11/01/07, H. Li 3
 How to regulate inheritance of digital property? • Traditional ways insufficient – Free copy or paper last will: usage rights issues – Not easy for managing a huge collection • Traditional ways may fail for confidential content protected by cryptography – His keys, private knowledge and biometric authentication may be lost forever, if a person is dead NXP Research, 11/01/07, H. Li 4
How to regulate inheritance of digital property? • Traditional ways insufficient – Free copy or paper last will: usage rights issues – Not easy for managing a huge collection • Traditional ways may fail for confidential content protected by cryptography – His keys, private knowledge and biometric authentication may be lost forever, if a person is dead NXP Research, 11/01/07, H. Li 4
 Secure digital inheritance solutions are required • Requirements: – Trusted posthumous transaction of the inheritance – Secure process for encrypted personal confidential content – Secure process for transferring usage rights of commercial content – Options for testator to assign conditions and rights to a beneficiary for a particular digital bequest – Non-repudiation – Ease of use NXP Research, 11/01/07, H. Li 5
Secure digital inheritance solutions are required • Requirements: – Trusted posthumous transaction of the inheritance – Secure process for encrypted personal confidential content – Secure process for transferring usage rights of commercial content – Options for testator to assign conditions and rights to a beneficiary for a particular digital bequest – Non-repudiation – Ease of use NXP Research, 11/01/07, H. Li 5
 Content • • • Introduction Private content protection model using DRM Inheritance protocols Digital last will Conclusions NXP Research, 11/01/07, H. Li 6
Content • • • Introduction Private content protection model using DRM Inheritance protocols Digital last will Conclusions NXP Research, 11/01/07, H. Li 6
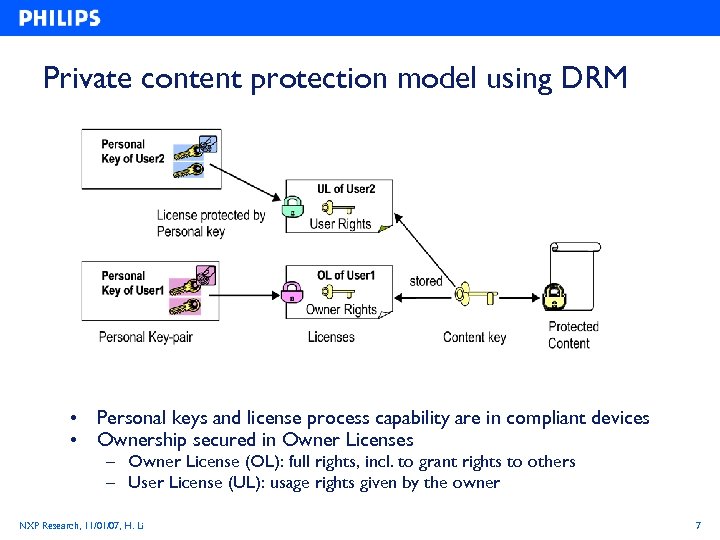 Private content protection model using DRM • Personal keys and license process capability are in compliant devices • Ownership secured in Owner Licenses – Owner License (OL): full rights, incl. to grant rights to others – User License (UL): usage rights given by the owner NXP Research, 11/01/07, H. Li 7
Private content protection model using DRM • Personal keys and license process capability are in compliant devices • Ownership secured in Owner Licenses – Owner License (OL): full rights, incl. to grant rights to others – User License (UL): usage rights given by the owner NXP Research, 11/01/07, H. Li 7
 Ownership and ownership transfer Owner 1 grants ‘take. Ownership’ UL Owner 2 takes ownership Owner 2 asks to clean-up the old ownership Owner 1 cleans the old ownership ULx : Take. Ownership UL ULClean : Clean-up UL Secured by compliant personal devices (keys) NXP Research, 11/01/07, H. Li 8
Ownership and ownership transfer Owner 1 grants ‘take. Ownership’ UL Owner 2 takes ownership Owner 2 asks to clean-up the old ownership Owner 1 cleans the old ownership ULx : Take. Ownership UL ULClean : Clean-up UL Secured by compliant personal devices (keys) NXP Research, 11/01/07, H. Li 8
 Content • • • Introduction Private content protection model using DRM Inheritance protocols Digital last will Conclusions NXP Research, 11/01/07, H. Li 9
Content • • • Introduction Private content protection model using DRM Inheritance protocols Digital last will Conclusions NXP Research, 11/01/07, H. Li 9
 Digital Inheritance Protocols • Principles for inheritance of digital content using DRM – by adding inheritance information (including conditions) to content licenses – by binding activation of inheritance to a death certificate • Two examples of protocols for personal content • One example for commercial content NXP Research, 11/01/07, H. Li 10
Digital Inheritance Protocols • Principles for inheritance of digital content using DRM – by adding inheritance information (including conditions) to content licenses – by binding activation of inheritance to a death certificate • Two examples of protocols for personal content • One example for commercial content NXP Research, 11/01/07, H. Li 10
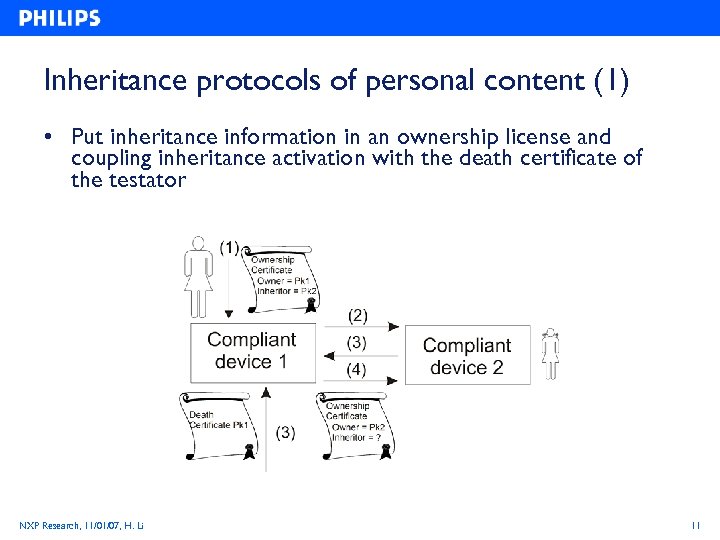 Inheritance protocols of personal content (1) • Put inheritance information in an ownership license and coupling inheritance activation with the death certificate of the testator NXP Research, 11/01/07, H. Li 11
Inheritance protocols of personal content (1) • Put inheritance information in an ownership license and coupling inheritance activation with the death certificate of the testator NXP Research, 11/01/07, H. Li 11
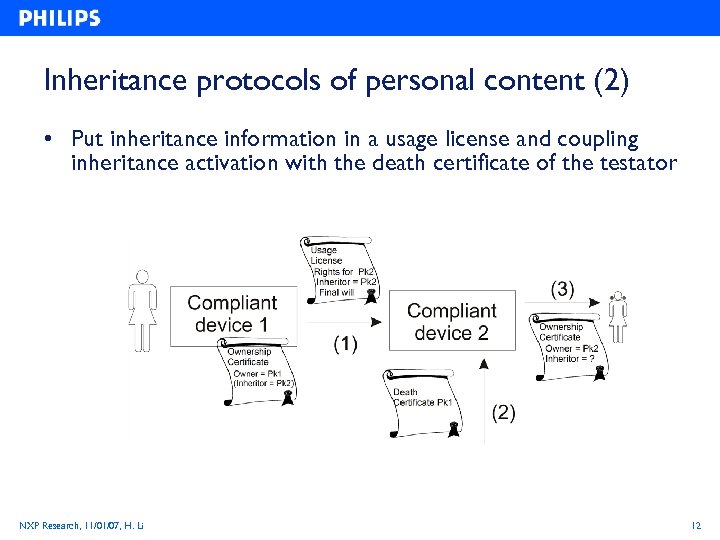 Inheritance protocols of personal content (2) • Put inheritance information in a usage license and coupling inheritance activation with the death certificate of the testator NXP Research, 11/01/07, H. Li 12
Inheritance protocols of personal content (2) • Put inheritance information in a usage license and coupling inheritance activation with the death certificate of the testator NXP Research, 11/01/07, H. Li 12
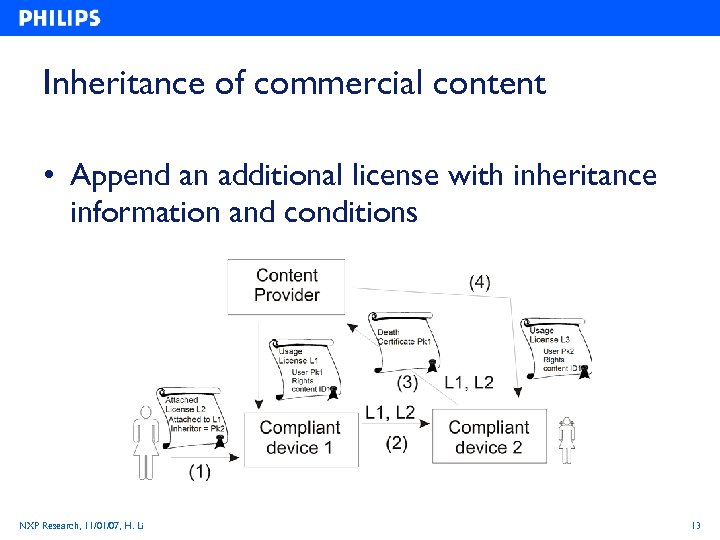 Inheritance of commercial content • Append an additional license with inheritance information and conditions NXP Research, 11/01/07, H. Li 13
Inheritance of commercial content • Append an additional license with inheritance information and conditions NXP Research, 11/01/07, H. Li 13
 Content • • • Introduction Private content protection model using DRM Inheritance protocols Digital last will Conclusions NXP Research, 11/01/07, H. Li 14
Content • • • Introduction Private content protection model using DRM Inheritance protocols Digital last will Conclusions NXP Research, 11/01/07, H. Li 14
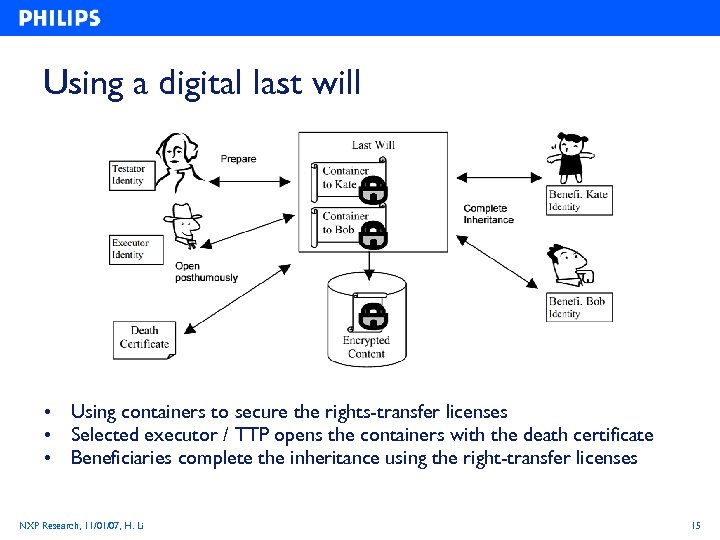 Using a digital last will • Using containers to secure the rights-transfer licenses • Selected executor / TTP opens the containers with the death certificate • Beneficiaries complete the inheritance using the right-transfer licenses NXP Research, 11/01/07, H. Li 15
Using a digital last will • Using containers to secure the rights-transfer licenses • Selected executor / TTP opens the containers with the death certificate • Beneficiaries complete the inheritance using the right-transfer licenses NXP Research, 11/01/07, H. Li 15
 Conclusions • Secure inheritance solutions required for protected digital content • Several protocols presented for transferring the ownership and usage rights posthumously • A digital last will solution presented • More work needed to introduce ownership and inheritance protocols in a real DRM standard / system NXP Research, 11/01/07, H. Li 16
Conclusions • Secure inheritance solutions required for protected digital content • Several protocols presented for transferring the ownership and usage rights posthumously • A digital last will solution presented • More work needed to introduce ownership and inheritance protocols in a real DRM standard / system NXP Research, 11/01/07, H. Li 16



