460083bb64319abbc644624cdc1cb1e1.ppt
- Количество слайдов: 39
 Digital Days Information Hiding Content Verification Anastasios Tefas Department of Informatics, Aristotle University of Thessaloniki
Digital Days Information Hiding Content Verification Anastasios Tefas Department of Informatics, Aristotle University of Thessaloniki
 Presentation Outline • Information hiding – Introduction – Terminology – Applications • Content verification – Introduction – Image authentication and tamper proofing using watermarking techniques Department of Informatics, Aristotle University of Thessaloniki
Presentation Outline • Information hiding – Introduction – Terminology – Applications • Content verification – Introduction – Image authentication and tamper proofing using watermarking techniques Department of Informatics, Aristotle University of Thessaloniki
 Information Hiding Introduction • Information hiding or steganography: embedding information within a medium in an imperceptible way. Thus, the secret’s very existence is concealed. • This technique dates back to ancient Egypt and Greece. • Steganography means ”covered writing”. • Information can be hidden in all types of digital media. Department of Informatics, Aristotle University of Thessaloniki
Information Hiding Introduction • Information hiding or steganography: embedding information within a medium in an imperceptible way. Thus, the secret’s very existence is concealed. • This technique dates back to ancient Egypt and Greece. • Steganography means ”covered writing”. • Information can be hidden in all types of digital media. Department of Informatics, Aristotle University of Thessaloniki
 Information Hiding Introduction Motivation: – An opponent cannot control your message, if he cannot find it. – If you hide communications, you can protect your thoughts from censorship or discovery. • Historically, data hiding has been preferred to encryption because it arouses less suspicion. Department of Informatics, Aristotle University of Thessaloniki
Information Hiding Introduction Motivation: – An opponent cannot control your message, if he cannot find it. – If you hide communications, you can protect your thoughts from censorship or discovery. • Historically, data hiding has been preferred to encryption because it arouses less suspicion. Department of Informatics, Aristotle University of Thessaloniki
 Information Hiding Introduction • The human visual and auditory systems are not perfect. • Inability to distinguish slight color/audio tone alterations. • Information embedding by altering data values imperceptibly: – Image color at certain positions. – Audio intensity at certain time instants. Department of Informatics, Aristotle University of Thessaloniki
Information Hiding Introduction • The human visual and auditory systems are not perfect. • Inability to distinguish slight color/audio tone alterations. • Information embedding by altering data values imperceptibly: – Image color at certain positions. – Audio intensity at certain time instants. Department of Informatics, Aristotle University of Thessaloniki
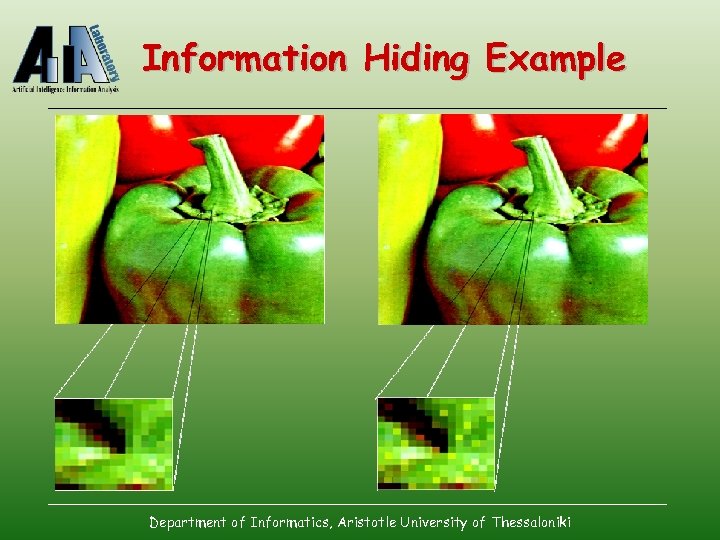 Information Hiding Example Department of Informatics, Aristotle University of Thessaloniki
Information Hiding Example Department of Informatics, Aristotle University of Thessaloniki
 The Prisoner’s Problem • Alice and Bob are in jail and want to hatch an escape plan. • Alice and Bob can communicate, but all their communications pass through Wendy, the Warden. Department of Informatics, Aristotle University of Thessaloniki
The Prisoner’s Problem • Alice and Bob are in jail and want to hatch an escape plan. • Alice and Bob can communicate, but all their communications pass through Wendy, the Warden. Department of Informatics, Aristotle University of Thessaloniki
 The Prisoner’s problem • Options for private communication: – encryption: • Wendy will suspect something is up and frustrate their plan by placing them in solitary confinement. – data hiding: • Wendy can’t find or prove that there is secret communication, Alice and Bob have a secure channel in which to communicate. Department of Informatics, Aristotle University of Thessaloniki
The Prisoner’s problem • Options for private communication: – encryption: • Wendy will suspect something is up and frustrate their plan by placing them in solitary confinement. – data hiding: • Wendy can’t find or prove that there is secret communication, Alice and Bob have a secure channel in which to communicate. Department of Informatics, Aristotle University of Thessaloniki
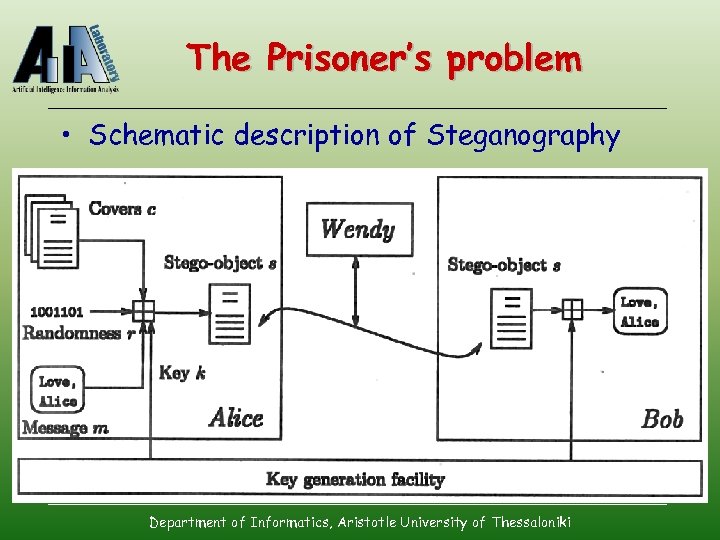 The Prisoner’s problem • Schematic description of Steganography Department of Informatics, Aristotle University of Thessaloniki
The Prisoner’s problem • Schematic description of Steganography Department of Informatics, Aristotle University of Thessaloniki
 Implicit and Explicit Data Hiding There are two strategies to hide information: • implicit: the cover-object is constructed for the purpose of masking the message. • explicit: a given object is modified in some way to fundamentally tie the message to the object. Department of Informatics, Aristotle University of Thessaloniki
Implicit and Explicit Data Hiding There are two strategies to hide information: • implicit: the cover-object is constructed for the purpose of masking the message. • explicit: a given object is modified in some way to fundamentally tie the message to the object. Department of Informatics, Aristotle University of Thessaloniki
 Goals of explicit information hiding • An opponent who understands the system, but does not know the key, can not obtain evidence (or even grounds for suspicion), that a covert communication has taken place • No information for the embedded message can be obtained from knowledge of the stego-objects • Like encryption, security comes from lack of knowledge of the key Department of Informatics, Aristotle University of Thessaloniki
Goals of explicit information hiding • An opponent who understands the system, but does not know the key, can not obtain evidence (or even grounds for suspicion), that a covert communication has taken place • No information for the embedded message can be obtained from knowledge of the stego-objects • Like encryption, security comes from lack of knowledge of the key Department of Informatics, Aristotle University of Thessaloniki
 Information Hiding • Pure: no key is needed for the detection of the secret message. • Secret key: the embedding and the detection of the message is done using a secret key. • Public key: message embedding using a secret key and detection using a public key. Department of Informatics, Aristotle University of Thessaloniki
Information Hiding • Pure: no key is needed for the detection of the secret message. • Secret key: the embedding and the detection of the message is done using a secret key. • Public key: message embedding using a secret key and detection using a public key. Department of Informatics, Aristotle University of Thessaloniki
 Applications of Information Hiding • Military and intelligence agencies • Health care industry: hiding patients data to the medical images so that only authorized persons can decode this data. • Watermarking is information hiding. • All watermarking applications: – Automatic monitoring – Tamper proofing – Piracy tracking Department of Informatics, Aristotle University of Thessaloniki
Applications of Information Hiding • Military and intelligence agencies • Health care industry: hiding patients data to the medical images so that only authorized persons can decode this data. • Watermarking is information hiding. • All watermarking applications: – Automatic monitoring – Tamper proofing – Piracy tracking Department of Informatics, Aristotle University of Thessaloniki
 Differences Between Information Hiding and Watermarking • Watermarks should be robust. Robustness limits depend on the application. • Watermarks do not have to be secret. Company logos or those used by TV channels. • Watermarks always carry information associated to the digital object to be protected. • Watermarks: One to many. • Information Hiding: One to one. Department of Informatics, Aristotle University of Thessaloniki
Differences Between Information Hiding and Watermarking • Watermarks should be robust. Robustness limits depend on the application. • Watermarks do not have to be secret. Company logos or those used by TV channels. • Watermarks always carry information associated to the digital object to be protected. • Watermarks: One to many. • Information Hiding: One to one. Department of Informatics, Aristotle University of Thessaloniki
 Content Verification Introduction • Digital media advantages: ü Efficient storage. ü Ease/speed of manipulation and transmission. ü Superior quality. • Digital media disadvantages: – Illegal copies identical to the originals. – Vulnerability to: • tampering • unauthorized copying and distribution (copyright violation) Department of Informatics, Aristotle University of Thessaloniki
Content Verification Introduction • Digital media advantages: ü Efficient storage. ü Ease/speed of manipulation and transmission. ü Superior quality. • Digital media disadvantages: – Illegal copies identical to the originals. – Vulnerability to: • tampering • unauthorized copying and distribution (copyright violation) Department of Informatics, Aristotle University of Thessaloniki
 Content Verification Introduction • Text documents • Digital audio • Digital images • Graphics • Digital video • Multimedia Department of Informatics, Aristotle University of Thessaloniki
Content Verification Introduction • Text documents • Digital audio • Digital images • Graphics • Digital video • Multimedia Department of Informatics, Aristotle University of Thessaloniki
 Content Verification Application Scenario • The owner embeds a watermark in his digital product in order to have the ability, he or another user, to check in an other time instance if the product has been tampered. • Watermark conveyed info: authenticity/integrity information. • Attacker’s objective: to change the content of the product without altering the watermark. Department of Informatics, Aristotle University of Thessaloniki
Content Verification Application Scenario • The owner embeds a watermark in his digital product in order to have the ability, he or another user, to check in an other time instance if the product has been tampered. • Watermark conveyed info: authenticity/integrity information. • Attacker’s objective: to change the content of the product without altering the watermark. Department of Informatics, Aristotle University of Thessaloniki
 Content Verification Introduction • Authentication (data integrity verification). – Violation signaling only when significant visual content modifications occur. • Fragile watermarks are the watermarks that have the property of being distorted when the host media is tampered somehow. • Robust watermarks can be also used. Department of Informatics, Aristotle University of Thessaloniki
Content Verification Introduction • Authentication (data integrity verification). – Violation signaling only when significant visual content modifications occur. • Fragile watermarks are the watermarks that have the property of being distorted when the host media is tampered somehow. • Robust watermarks can be also used. Department of Informatics, Aristotle University of Thessaloniki
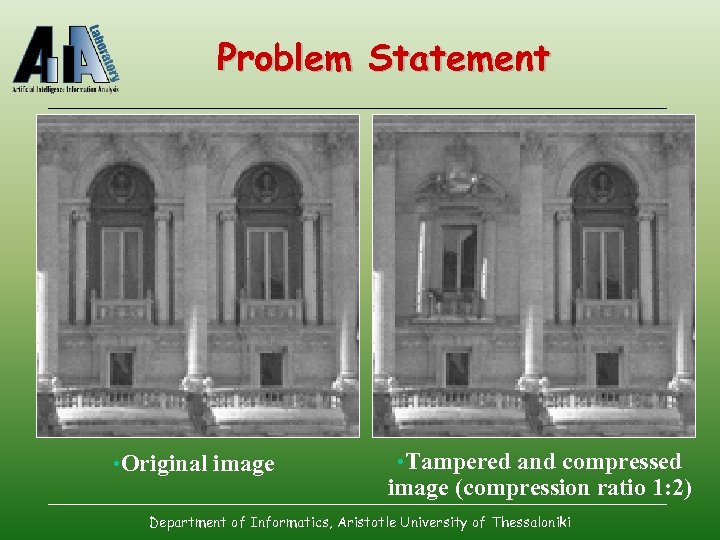 Problem Statement • Original image • Tampered and compressed image (compression ratio 1: 2) Department of Informatics, Aristotle University of Thessaloniki
Problem Statement • Original image • Tampered and compressed image (compression ratio 1: 2) Department of Informatics, Aristotle University of Thessaloniki
 Watermarking for Tamper Proofing • The watermark ensures that the medium has not been altered. • The watermark should be distorted when the host media is tampered. • Detection of tampered regions. • Example: Montage of a digital video or image in order to change the visual content (removal of a person from a scene). Department of Informatics, Aristotle University of Thessaloniki
Watermarking for Tamper Proofing • The watermark ensures that the medium has not been altered. • The watermark should be distorted when the host media is tampered. • Detection of tampered regions. • Example: Montage of a digital video or image in order to change the visual content (removal of a person from a scene). Department of Informatics, Aristotle University of Thessaloniki
 Tampering Example YES Has this image been tampered? Original image Department of Informatics, Aristotle University of Thessaloniki
Tampering Example YES Has this image been tampered? Original image Department of Informatics, Aristotle University of Thessaloniki
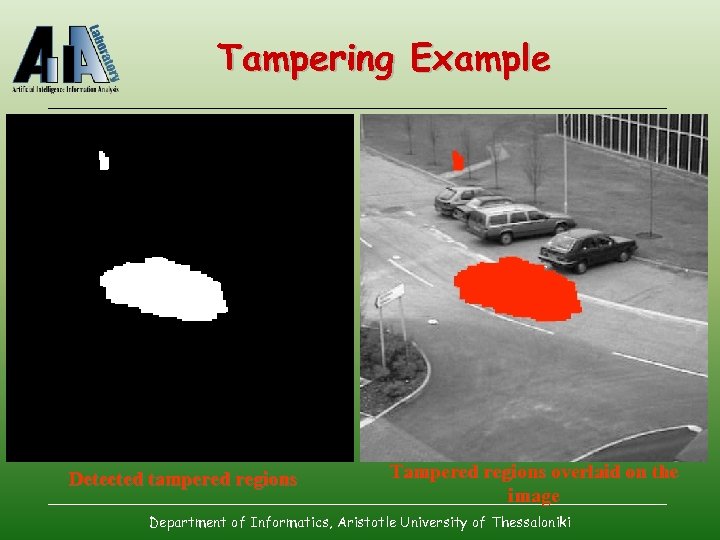 Tampering Example Detected tampered regions Tampered regions overlaid on the image Department of Informatics, Aristotle University of Thessaloniki
Tampering Example Detected tampered regions Tampered regions overlaid on the image Department of Informatics, Aristotle University of Thessaloniki
 Introduction • Objectives of an image authentication algorithm: – Imperceptible watermark embedding. – Watermark detection without using the original image or a separate header (digital signature). – Detection of host image tampered regions and alterations in fine image details. – Watermark robustness against high quality lossy image compression. Department of Informatics, Aristotle University of Thessaloniki
Introduction • Objectives of an image authentication algorithm: – Imperceptible watermark embedding. – Watermark detection without using the original image or a separate header (digital signature). – Detection of host image tampered regions and alterations in fine image details. – Watermark robustness against high quality lossy image compression. Department of Informatics, Aristotle University of Thessaloniki
 Digital Signature Methods • The original signal is passed through a hash function to produce a piece of data separate from the signal. • This data is either encrypted or not and it is stored in a separate header (digital signature) that is transmitted with the image. • The data is used in the second phase to verify that the received image has not been modified. Department of Informatics, Aristotle University of Thessaloniki
Digital Signature Methods • The original signal is passed through a hash function to produce a piece of data separate from the signal. • This data is either encrypted or not and it is stored in a separate header (digital signature) that is transmitted with the image. • The data is used in the second phase to verify that the received image has not been modified. Department of Informatics, Aristotle University of Thessaloniki
 Substitution Methods • Least significant bit (LSB) substitution. • LSB of each pixel is replaced by the corresponding binary watermark value. • In the detection phase if the image is tampered the watermark will not be detected in these regions. • Drawbacks: – The image can be easily altered without changing the LSB. – Ii is not robust against lossy compression. Department of Informatics, Aristotle University of Thessaloniki
Substitution Methods • Least significant bit (LSB) substitution. • LSB of each pixel is replaced by the corresponding binary watermark value. • In the detection phase if the image is tampered the watermark will not be detected in these regions. • Drawbacks: – The image can be easily altered without changing the LSB. – Ii is not robust against lossy compression. Department of Informatics, Aristotle University of Thessaloniki
 Transform Based Methods • The watermark is embedded in a transform domain (e. g. DWT) for achieving robustness against compression. • Other problems: – Binary decision output instead of a measure or a map highlighting the altered regions. – Detection of the tampered regions. Department of Informatics, Aristotle University of Thessaloniki
Transform Based Methods • The watermark is embedded in a transform domain (e. g. DWT) for achieving robustness against compression. • Other problems: – Binary decision output instead of a measure or a map highlighting the altered regions. – Detection of the tampered regions. Department of Informatics, Aristotle University of Thessaloniki
 Robust Methods • Robust watermarks are used. The encrypted message describes the image characteristics. • The watermark is embedded in the image and in the detection phase the image under test is compared against its description extracted from the watermark. • Disadvantages. – Only a crude description of the image can be encrypted in the message. – The tampered regions can not be detected. Department of Informatics, Aristotle University of Thessaloniki
Robust Methods • Robust watermarks are used. The encrypted message describes the image characteristics. • The watermark is embedded in the image and in the detection phase the image under test is compared against its description extracted from the watermark. • Disadvantages. – Only a crude description of the image can be encrypted in the message. – The tampered regions can not be detected. Department of Informatics, Aristotle University of Thessaloniki
 Watermark Generation • Given an image f(x) and a watermark key k, a ternary watermark w(x) can be produced by the watermark generation procedure. • For generating the watermark one of the following procedures can be used: – Pseudorandom number generators. – Chaotic maps. – Chaotic mixing systems. Department of Informatics, Aristotle University of Thessaloniki
Watermark Generation • Given an image f(x) and a watermark key k, a ternary watermark w(x) can be produced by the watermark generation procedure. • For generating the watermark one of the following procedures can be used: – Pseudorandom number generators. – Chaotic maps. – Chaotic mixing systems. Department of Informatics, Aristotle University of Thessaloniki
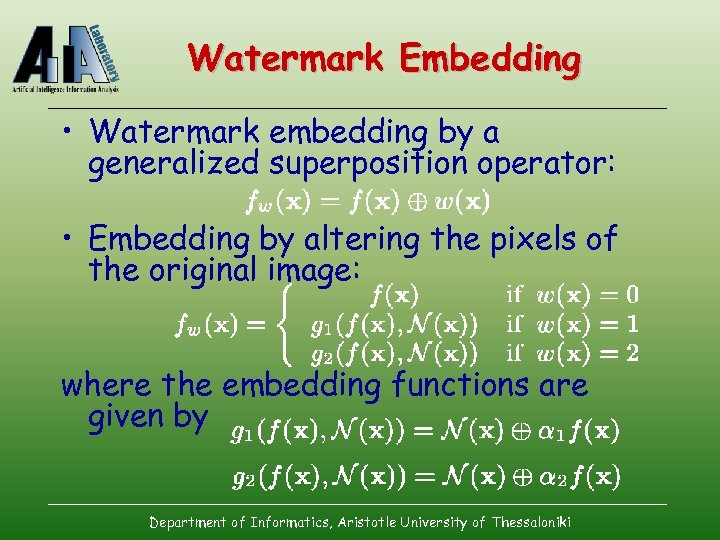 Watermark Embedding • Watermark embedding by a generalized superposition operator: • Embedding by altering the pixels of the original image: where the embedding functions are given by Department of Informatics, Aristotle University of Thessaloniki
Watermark Embedding • Watermark embedding by a generalized superposition operator: • Embedding by altering the pixels of the original image: where the embedding functions are given by Department of Informatics, Aristotle University of Thessaloniki
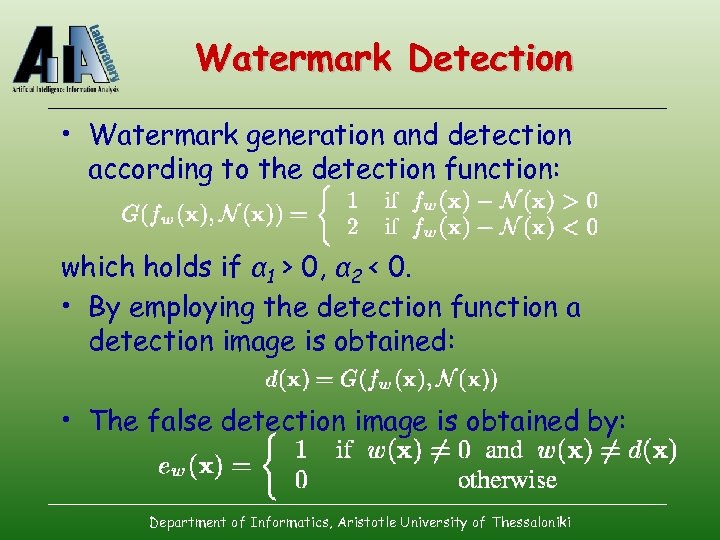 Watermark Detection • Watermark generation and detection according to the detection function: which holds if α 1 > 0, α 2 < 0. • By employing the detection function a detection image is obtained: • The false detection image is obtained by: Department of Informatics, Aristotle University of Thessaloniki
Watermark Detection • Watermark generation and detection according to the detection function: which holds if α 1 > 0, α 2 < 0. • By employing the detection function a detection image is obtained: • The false detection image is obtained by: Department of Informatics, Aristotle University of Thessaloniki
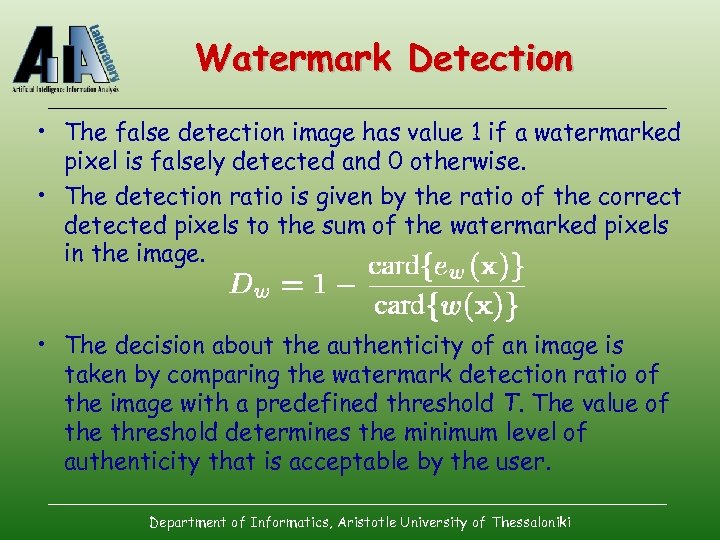 Watermark Detection • The false detection image has value 1 if a watermarked pixel is falsely detected and 0 otherwise. • The detection ratio is given by the ratio of the correct detected pixels to the sum of the watermarked pixels in the image. • The decision about the authenticity of an image is taken by comparing the watermark detection ratio of the image with a predefined threshold T. The value of the threshold determines the minimum level of authenticity that is acceptable by the user. Department of Informatics, Aristotle University of Thessaloniki
Watermark Detection • The false detection image has value 1 if a watermarked pixel is falsely detected and 0 otherwise. • The detection ratio is given by the ratio of the correct detected pixels to the sum of the watermarked pixels in the image. • The decision about the authenticity of an image is taken by comparing the watermark detection ratio of the image with a predefined threshold T. The value of the threshold determines the minimum level of authenticity that is acceptable by the user. Department of Informatics, Aristotle University of Thessaloniki
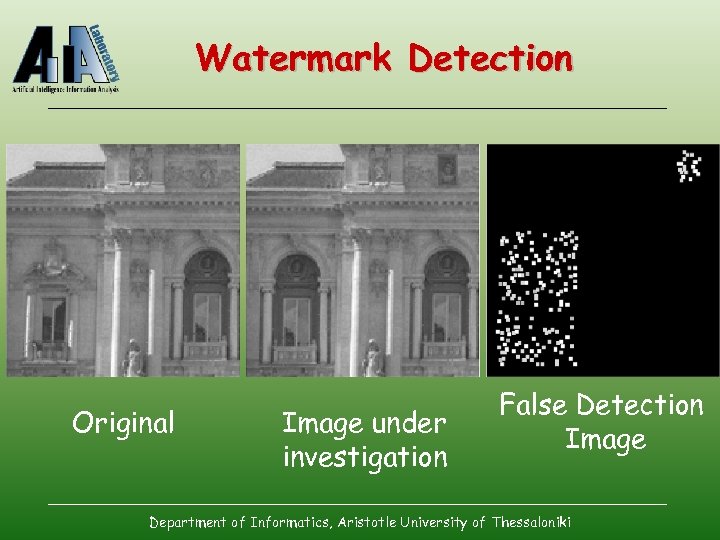 Watermark Detection Original Image under investigation False Detection Image Department of Informatics, Aristotle University of Thessaloniki
Watermark Detection Original Image under investigation False Detection Image Department of Informatics, Aristotle University of Thessaloniki
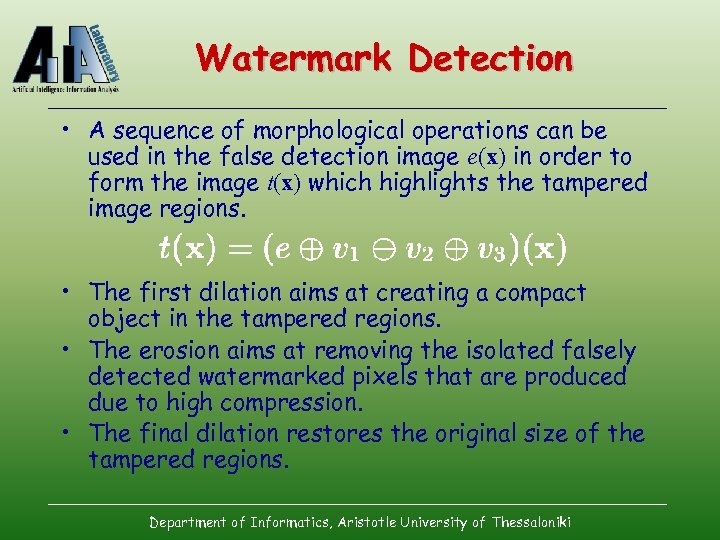 Watermark Detection • A sequence of morphological operations can be used in the false detection image e(x) in order to form the image t(x) which highlights the tampered image regions. • The first dilation aims at creating a compact object in the tampered regions. • The erosion aims at removing the isolated falsely detected watermarked pixels that are produced due to high compression. • The final dilation restores the original size of the tampered regions. Department of Informatics, Aristotle University of Thessaloniki
Watermark Detection • A sequence of morphological operations can be used in the false detection image e(x) in order to form the image t(x) which highlights the tampered image regions. • The first dilation aims at creating a compact object in the tampered regions. • The erosion aims at removing the isolated falsely detected watermarked pixels that are produced due to high compression. • The final dilation restores the original size of the tampered regions. Department of Informatics, Aristotle University of Thessaloniki
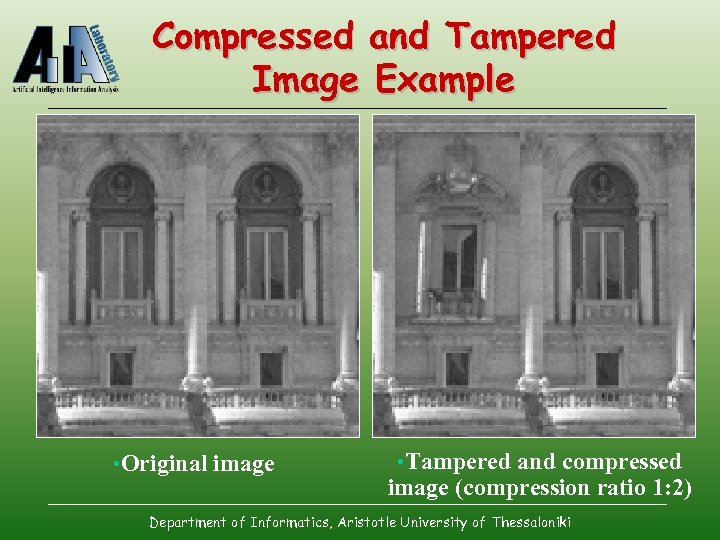 Compressed and Tampered Image Example • Original image • Tampered and compressed image (compression ratio 1: 2) Department of Informatics, Aristotle University of Thessaloniki
Compressed and Tampered Image Example • Original image • Tampered and compressed image (compression ratio 1: 2) Department of Informatics, Aristotle University of Thessaloniki
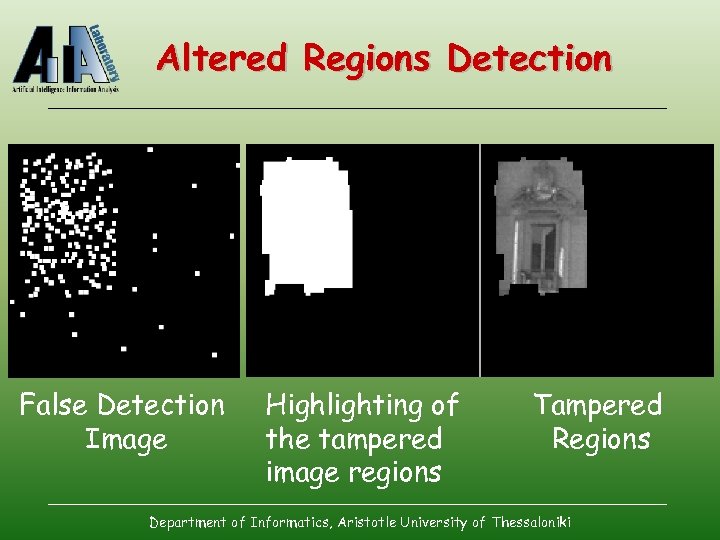 Altered Regions Detection False Detection Image Highlighting of the tampered image regions Tampered Regions Department of Informatics, Aristotle University of Thessaloniki
Altered Regions Detection False Detection Image Highlighting of the tampered image regions Tampered Regions Department of Informatics, Aristotle University of Thessaloniki
 Conclusions • Need for combined copyright protection and tamper proofing using watermarks. • Need for more reliable algorithms. • Need to clarify the legal status of watermarking for tamper proofing. • Need to establish confidence among possible users for the potentials of watermarking. Department of Informatics, Aristotle University of Thessaloniki
Conclusions • Need for combined copyright protection and tamper proofing using watermarks. • Need for more reliable algorithms. • Need to clarify the legal status of watermarking for tamper proofing. • Need to establish confidence among possible users for the potentials of watermarking. Department of Informatics, Aristotle University of Thessaloniki
 References • F. A. P. Petitcolas, R. J Anderson, and M. G. Kuhn, Information hiding - a survey, Proceedings of the IEEE, vol. 87, no. 7, pp. 1062 -1078, July 1999. • G. L. Friedman, The trustworthy digital camera: Restoring credibility to the photographic image, IEEE Transactions on Consumer Electronics, vol. 39, no. 4, pp. 905 -910, November 1993. • M. Schneider and S. F. Chang, A robust content-based digital signature for image authentication, Proc. of ICIP'96, Lausanne, Switzerland, September 1996, vol. III, pp. 227230. • S. Bhattacharjee and M. Kutter, Compression tolerant image authentication, in Proc. of ICIP'98, Chicago, USA, 4 -7 October 1998, vol. I, pp. 425 -429. • M. Wu and B. Liu, Watermarking for image authentication, in Proc. of ICIP'98, Chicago, USA, 4 -7 October 1998, vol. I, pp. 425 -429. Department of Informatics, Aristotle University of Thessaloniki
References • F. A. P. Petitcolas, R. J Anderson, and M. G. Kuhn, Information hiding - a survey, Proceedings of the IEEE, vol. 87, no. 7, pp. 1062 -1078, July 1999. • G. L. Friedman, The trustworthy digital camera: Restoring credibility to the photographic image, IEEE Transactions on Consumer Electronics, vol. 39, no. 4, pp. 905 -910, November 1993. • M. Schneider and S. F. Chang, A robust content-based digital signature for image authentication, Proc. of ICIP'96, Lausanne, Switzerland, September 1996, vol. III, pp. 227230. • S. Bhattacharjee and M. Kutter, Compression tolerant image authentication, in Proc. of ICIP'98, Chicago, USA, 4 -7 October 1998, vol. I, pp. 425 -429. • M. Wu and B. Liu, Watermarking for image authentication, in Proc. of ICIP'98, Chicago, USA, 4 -7 October 1998, vol. I, pp. 425 -429. Department of Informatics, Aristotle University of Thessaloniki
 References • B. Zhu, M. D. Swanson, and A. H. Tewfik, Transparent robust authentication and distortion measurement technique for images, in Proc. of DSP'96, Loen, Norway, September 1996, pp. 45 -48. • P. W. Wong, A public key watermark for image verification and authentication, in Proc. of ICIP'98, Chicago, USA, 4 -7 October 1998, vol. I, pp. 425 -429. • L. Xie and G. R. Arce, Joint wavelet compression and authentication watermarking, in Proc. of ICIP'98 , Chicago, Illinois, USA, 4 -7 October 1998, vol. II, pp. 427 -431. • D. Kundur and D. Hatzinakos, Digital watermarking for telltale tamper proofing and authentication, Proceedings of the IEEE , vol. 87, no. 7, pp. 1167 -1180, July 1999. • S. Katzenbeisser and F. A. P. Petitcolas, Information hiding – techniques for steganography and digital watermarking, Artech House, 2000. Department of Informatics, Aristotle University of Thessaloniki
References • B. Zhu, M. D. Swanson, and A. H. Tewfik, Transparent robust authentication and distortion measurement technique for images, in Proc. of DSP'96, Loen, Norway, September 1996, pp. 45 -48. • P. W. Wong, A public key watermark for image verification and authentication, in Proc. of ICIP'98, Chicago, USA, 4 -7 October 1998, vol. I, pp. 425 -429. • L. Xie and G. R. Arce, Joint wavelet compression and authentication watermarking, in Proc. of ICIP'98 , Chicago, Illinois, USA, 4 -7 October 1998, vol. II, pp. 427 -431. • D. Kundur and D. Hatzinakos, Digital watermarking for telltale tamper proofing and authentication, Proceedings of the IEEE , vol. 87, no. 7, pp. 1167 -1180, July 1999. • S. Katzenbeisser and F. A. P. Petitcolas, Information hiding – techniques for steganography and digital watermarking, Artech House, 2000. Department of Informatics, Aristotle University of Thessaloniki
 References • M. Barni, A. Tefas, F. Bartollini and I. Pitas, Image Authentication Techniques for Surveillance Applications, Proceedings of the IEEE, July 2001. • A. Tefas and I. Pitas, Image Authentication and Tamper Proofing based on Chaotic Mixing and Mathematical Morphology, IEEE Transactions on Image Processing, second review, February 2001. • A. Tefas and I. Pitas, Image Authentication based on Chaotic Mixing, IEEE International Symposium on Circuits and Systems (ISCAS'2000), Geneva, Switzerland, 28 -31 May 2000. • A. Tefas and I. Pitas, Image Authentication and Tamper Proofing using Mathematical Morphology, European Signal Processing Conference (EUSIPCO'2000), Tampere, Finland, 5 -8 September 2000. Department of Informatics, Aristotle University of Thessaloniki
References • M. Barni, A. Tefas, F. Bartollini and I. Pitas, Image Authentication Techniques for Surveillance Applications, Proceedings of the IEEE, July 2001. • A. Tefas and I. Pitas, Image Authentication and Tamper Proofing based on Chaotic Mixing and Mathematical Morphology, IEEE Transactions on Image Processing, second review, February 2001. • A. Tefas and I. Pitas, Image Authentication based on Chaotic Mixing, IEEE International Symposium on Circuits and Systems (ISCAS'2000), Geneva, Switzerland, 28 -31 May 2000. • A. Tefas and I. Pitas, Image Authentication and Tamper Proofing using Mathematical Morphology, European Signal Processing Conference (EUSIPCO'2000), Tampere, Finland, 5 -8 September 2000. Department of Informatics, Aristotle University of Thessaloniki


