 Digital crime CRE AT E A ND FORMALIZED BY PESTOV NIKITA
Digital crime CRE AT E A ND FORMALIZED BY PESTOV NIKITA
 History (briefly) The first recorded cyber crime took place in 1820. That is not surprising considering the fact that the abacus, which is thought to be the earliest from of a computer, has been around since 3500 B. c. In India, Japan and China, the era of modern computer, however, began with the analytical engine of Charles Babbage. The first spam email took place in 1976 when it was sent out over the ARPANT.
History (briefly) The first recorded cyber crime took place in 1820. That is not surprising considering the fact that the abacus, which is thought to be the earliest from of a computer, has been around since 3500 B. c. In India, Japan and China, the era of modern computer, however, began with the analytical engine of Charles Babbage. The first spam email took place in 1976 when it was sent out over the ARPANT.
 Types of the digital crime 1. Hack: computer based intrusion 2. Mule: entity(ies) or individuals used as middleman in fraudulent transactions 3. Phishing: masquerading as a trustworthy entity in an electronic communication to obtain data 4. Skimming: using electronic device to swipe CC numbers 5. Compromised: unauthorized point of entry 6. VIRUS DISSMINITION : Malicious software that attaches itself to other software. VIRUS , WORMS, TROJAN HORSE , WEB JACKING, E-MAIL BOMBING etc. 7. COMPUTER VANDALISM : Damaging or destroying data rather than stealing or misusing them is called cyber vandalism. These are program that attach themselves to a file and then circulate. 8. CYBER TERRORISM : Terrorist attacks on the Internet is by distributed denial of service attacks, hate websites and hate E-mails , attacks on service network etc. 9. SOFTWARE PIRACY : Theft of software through the illegal copying of genuine programs or the counterfeiting and distribution of products intended to pass for the original.
Types of the digital crime 1. Hack: computer based intrusion 2. Mule: entity(ies) or individuals used as middleman in fraudulent transactions 3. Phishing: masquerading as a trustworthy entity in an electronic communication to obtain data 4. Skimming: using electronic device to swipe CC numbers 5. Compromised: unauthorized point of entry 6. VIRUS DISSMINITION : Malicious software that attaches itself to other software. VIRUS , WORMS, TROJAN HORSE , WEB JACKING, E-MAIL BOMBING etc. 7. COMPUTER VANDALISM : Damaging or destroying data rather than stealing or misusing them is called cyber vandalism. These are program that attach themselves to a file and then circulate. 8. CYBER TERRORISM : Terrorist attacks on the Internet is by distributed denial of service attacks, hate websites and hate E-mails , attacks on service network etc. 9. SOFTWARE PIRACY : Theft of software through the illegal copying of genuine programs or the counterfeiting and distribution of products intended to pass for the original.
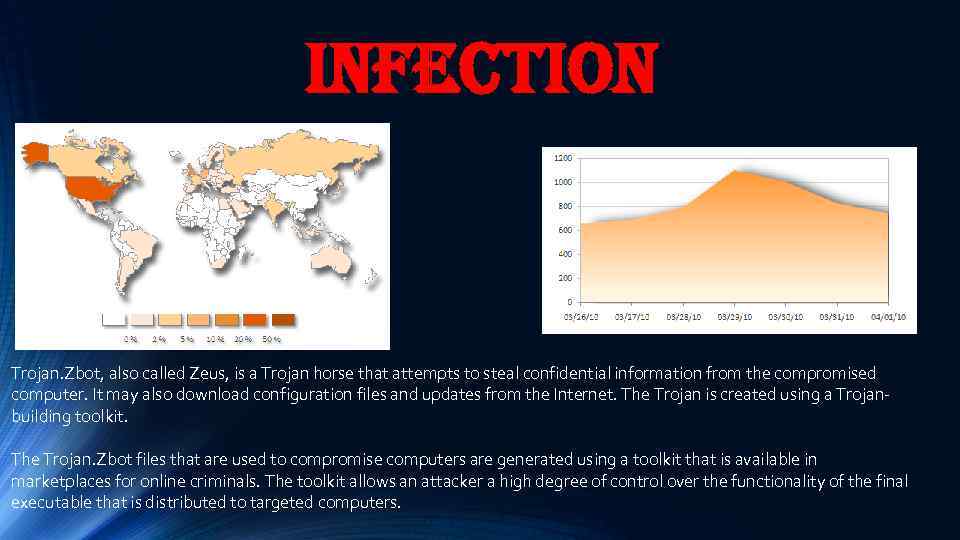 infection Trojan. Zbot, also called Zeus, is a Trojan horse that attempts to steal confidential information from the compromised computer. It may also download configuration files and updates from the Internet. The Trojan is created using a Trojanbuilding toolkit. The Trojan. Zbot files that are used to compromise computers are generated using a toolkit that is available in marketplaces for online criminals. The toolkit allows an attacker a high degree of control over the functionality of the final executable that is distributed to targeted computers.
infection Trojan. Zbot, also called Zeus, is a Trojan horse that attempts to steal confidential information from the compromised computer. It may also download configuration files and updates from the Internet. The Trojan is created using a Trojanbuilding toolkit. The Trojan. Zbot files that are used to compromise computers are generated using a toolkit that is available in marketplaces for online criminals. The toolkit allows an attacker a high degree of control over the functionality of the final executable that is distributed to targeted computers.
 Sources: 1. https: //www. fbi. gov/investigate/cyber 2. https: //www. channel 4. com/news/cybe r-crime-game-over-zeus-crew-nccupolice-russia 3. http: //www. frbsf. org/banking/files/Call -the-Fed-Cybercrime-3 -14 -13. pdf 4. https: //en. wikipedia. org/wiki/Cybercri me 5. https: //www. symantec. com/security_r esponse/writeup. jsp? docid=2010011016 -3514 -99
Sources: 1. https: //www. fbi. gov/investigate/cyber 2. https: //www. channel 4. com/news/cybe r-crime-game-over-zeus-crew-nccupolice-russia 3. http: //www. frbsf. org/banking/files/Call -the-Fed-Cybercrime-3 -14 -13. pdf 4. https: //en. wikipedia. org/wiki/Cybercri me 5. https: //www. symantec. com/security_r esponse/writeup. jsp? docid=2010011016 -3514 -99