afa9b61962d76fb7ae46600dbe5cf3f8.ppt
- Количество слайдов: 53
 Digital Certificates (X. 509, Open. PGP), Security Protocols James Joshi, Associate Professor University of Pittsburgh 1
Digital Certificates (X. 509, Open. PGP), Security Protocols James Joshi, Associate Professor University of Pittsburgh 1
 Objectives n Understanding of n n Digital certificate standards X. 509 and Open. PGP Privacy Enhance Mail Secure Socket Layer IPSec 2
Objectives n Understanding of n n Digital certificate standards X. 509 and Open. PGP Privacy Enhance Mail Secure Socket Layer IPSec 2
 Cryptographic Key Infrastructure n Goal: n n Classical Crypto: n n bind identity to key Not possible as all keys are shared Public key Cryptography: n n n Bind identity to public key Erroneous binding means no secrecy between principals Assume principal identified by an acceptable name 3
Cryptographic Key Infrastructure n Goal: n n Classical Crypto: n n bind identity to key Not possible as all keys are shared Public key Cryptography: n n n Bind identity to public key Erroneous binding means no secrecy between principals Assume principal identified by an acceptable name 3
 Certificates n Create token (message) containing n n Identity of principal (here, Alice) Corresponding public key Timestamp (when issued) Other information (identity of signer) signed by trusted authority (here, Cathy) CA = { e. A || Alice || T } d. C CA is A’s certificate 4
Certificates n Create token (message) containing n n Identity of principal (here, Alice) Corresponding public key Timestamp (when issued) Other information (identity of signer) signed by trusted authority (here, Cathy) CA = { e. A || Alice || T } d. C CA is A’s certificate 4
 Use n Bob gets Alice’s certificate n n n If he knows Cathy’s public key, he can decipher the certificate Now Bob has Alice’s public key Problem: n Bob needs Cathy’s public key to validate certificate n Two approaches: n Merkle’s tree, Signature chains 5
Use n Bob gets Alice’s certificate n n n If he knows Cathy’s public key, he can decipher the certificate Now Bob has Alice’s public key Problem: n Bob needs Cathy’s public key to validate certificate n Two approaches: n Merkle’s tree, Signature chains 5
 Certificate Signature Chains n Create certificate n n n Validate n n Generate hash of certificate Encipher hash with issuer’s private key Obtain issuer’s public key Decipher enciphered hash Re-compute hash from certificate and compare Problem: n Validating the certificate of the issuer and getting issuer’s public key 6
Certificate Signature Chains n Create certificate n n n Validate n n Generate hash of certificate Encipher hash with issuer’s private key Obtain issuer’s public key Decipher enciphered hash Re-compute hash from certificate and compare Problem: n Validating the certificate of the issuer and getting issuer’s public key 6
 X. 509 Service n ITU-T recommendation X. 509 n n Defines a framework for the provision of authentication services by X. 509 directory to users X. 509 – an important standard n Used in a variety of context n n The X. 509 Certificate format is used in S/MIME, IP Security and SSL/TLS Initially issued in 1988, another version in 1993 and X. 509 v 3 in 2000 7
X. 509 Service n ITU-T recommendation X. 509 n n Defines a framework for the provision of authentication services by X. 509 directory to users X. 509 – an important standard n Used in a variety of context n n The X. 509 Certificate format is used in S/MIME, IP Security and SSL/TLS Initially issued in 1988, another version in 1993 and X. 509 v 3 in 2000 7
 X. 509 Standard n n Based on public-key cryptograph and digital signatures Standard n n Does not dictate the use of specific algorithm – but recommends RSA Digital signature requires a hash function 8
X. 509 Standard n n Based on public-key cryptograph and digital signatures Standard n n Does not dictate the use of specific algorithm – but recommends RSA Digital signature requires a hash function 8
 X. 509 Chains – key pieces of information n Key certificate fields in X. 509 v 3: n n n n Version Serial number (unique) Signature algorithm identifier Issuer’s name; uniquely identifies issuer Interval of validity Subject’s name; uniquely identifies subject Subject’s public key info … Signature: n Identifies algorithm used to sign the certificate n Signature (enciphered hash) 9
X. 509 Chains – key pieces of information n Key certificate fields in X. 509 v 3: n n n n Version Serial number (unique) Signature algorithm identifier Issuer’s name; uniquely identifies issuer Interval of validity Subject’s name; uniquely identifies subject Subject’s public key info … Signature: n Identifies algorithm used to sign the certificate n Signature (enciphered hash) 9
 X. 509 Certificate n Certification Authority (CA): n n entity that issues certificates A user’s certificate n n Is created for a principal by a CA Placed in a directory server (DS) The CA sign the certificate with its private key n n n Y<
X. 509 Certificate n Certification Authority (CA): n n entity that issues certificates A user’s certificate n n Is created for a principal by a CA Placed in a directory server (DS) The CA sign the certificate with its private key n n n Y<
![X. 509 Detailed Formats [Source: William Stallings, Cryptography and Network Security] 11 X. 509 Detailed Formats [Source: William Stallings, Cryptography and Network Security] 11](https://present5.com/presentation/afa9b61962d76fb7ae46600dbe5cf3f8/image-11.jpg) X. 509 Detailed Formats [Source: William Stallings, Cryptography and Network Security] 11
X. 509 Detailed Formats [Source: William Stallings, Cryptography and Network Security] 11
 X. 509 Certificate Validation n Obtain issuer’s public key n n Decipher signature n n Gives hash of certificate Re-compute hash from certificate and compare n n The one for the particular signature algorithm If they differ, there’s a problem Check interval of validity n This confirms that certificate is current 12
X. 509 Certificate Validation n Obtain issuer’s public key n n Decipher signature n n Gives hash of certificate Re-compute hash from certificate and compare n n The one for the particular signature algorithm If they differ, there’s a problem Check interval of validity n This confirms that certificate is current 12
 Issuers n Certification Authority (CA): entity that issues certificates n n n Multiple issuers pose validation problem Alice’s CA is Cathy; Bob’s CA is Dan; how can Alice validate Bob’s certificate? Have Cathy and Don cross-certify n Each issues certificate for the other 13
Issuers n Certification Authority (CA): entity that issues certificates n n n Multiple issuers pose validation problem Alice’s CA is Cathy; Bob’s CA is Dan; how can Alice validate Bob’s certificate? Have Cathy and Don cross-certify n Each issues certificate for the other 13
 Validation and Cross-Certifying n n Cathy<
Validation and Cross-Certifying n n Cathy<
 Certificate Revocation n Each certificate includes a validity period n n Also needs to revoke a certificate before it expires, n n A new certificate is issued by CA just before it expires If the user’s private key is compromised, The user is no longer certified by the CA The CA’s certificate is compromised Certificate Revocation List (CRL) n n Each CA maintains a CRL of all revoked but no expired certificates Each CRL in the DS is signed by the issuer and includes the issuer’s name, creation date, date of the next CRL to be issued, an entry for each revoked certificate (serial numbers) 15
Certificate Revocation n Each certificate includes a validity period n n Also needs to revoke a certificate before it expires, n n A new certificate is issued by CA just before it expires If the user’s private key is compromised, The user is no longer certified by the CA The CA’s certificate is compromised Certificate Revocation List (CRL) n n Each CA maintains a CRL of all revoked but no expired certificates Each CRL in the DS is signed by the issuer and includes the issuer’s name, creation date, date of the next CRL to be issued, an entry for each revoked certificate (serial numbers) 15
 PGP Chains n Pretty Good Privacy: n n n Open. PGP certificates structured into packets n n n Widely used to provide privacy for electronic mail and signing files digitally Uses Certificate based key management infrastructure for user’s public keys One public key packet Zero or more signature packets For more information: RFC 4880 16
PGP Chains n Pretty Good Privacy: n n n Open. PGP certificates structured into packets n n n Widely used to provide privacy for electronic mail and signing files digitally Uses Certificate based key management infrastructure for user’s public keys One public key packet Zero or more signature packets For more information: RFC 4880 16
 PGP Certificate Signature Chains n Pretty Good Privacy: n n n Widely used to provide privacy for electronic mail and signing files digitally Uses Certificate based key management infrastructure for user’s public keys Open. PGP certificates structured into packets n n One public key packet Zero or more signature packets 17
PGP Certificate Signature Chains n Pretty Good Privacy: n n n Widely used to provide privacy for electronic mail and signing files digitally Uses Certificate based key management infrastructure for user’s public keys Open. PGP certificates structured into packets n n One public key packet Zero or more signature packets 17
 Open. PGP Key Packet n Version n Time of Creation Validity period (Version 3 only) n n n Indicates number of days it is valid; 0 means it does not expire Public key algorithm and parameters n n n (3 or 4; 3 compatible with all versions of PGP, 4 not compatible with older versions of PGP) Version 3 packets contain modulus for RSA Version 4 packets contain parameters for the cryptosystem used Public key n n Version 3: the exponent of the RSA key Version 4: the public key of the crypto system used 18
Open. PGP Key Packet n Version n Time of Creation Validity period (Version 3 only) n n n Indicates number of days it is valid; 0 means it does not expire Public key algorithm and parameters n n n (3 or 4; 3 compatible with all versions of PGP, 4 not compatible with older versions of PGP) Version 3 packets contain modulus for RSA Version 4 packets contain parameters for the cryptosystem used Public key n n Version 3: the exponent of the RSA key Version 4: the public key of the crypto system used 18
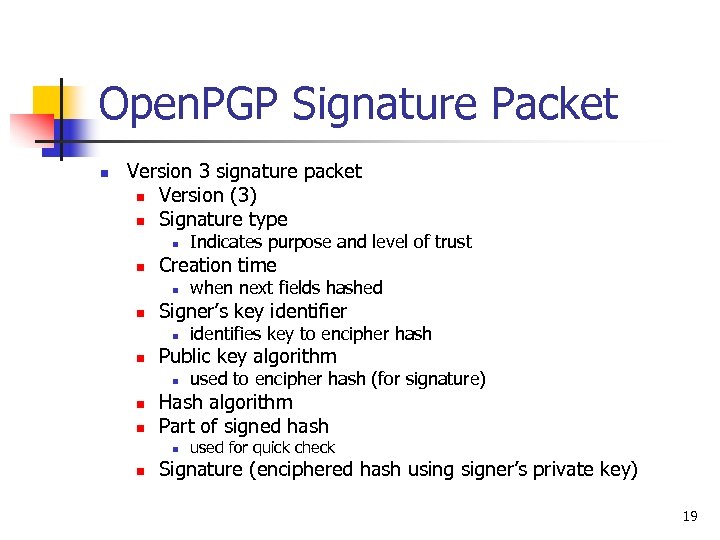 Open. PGP Signature Packet n Version 3 signature packet n Version (3) n Signature type n n Creation time n n n used to encipher hash (for signature) Hash algorithm Part of signed hash n n identifies key to encipher hash Public key algorithm n n when next fields hashed Signer’s key identifier n n Indicates purpose and level of trust used for quick check Signature (enciphered hash using signer’s private key) 19
Open. PGP Signature Packet n Version 3 signature packet n Version (3) n Signature type n n Creation time n n n used to encipher hash (for signature) Hash algorithm Part of signed hash n n identifies key to encipher hash Public key algorithm n n when next fields hashed Signer’s key identifier n n Indicates purpose and level of trust used for quick check Signature (enciphered hash using signer’s private key) 19
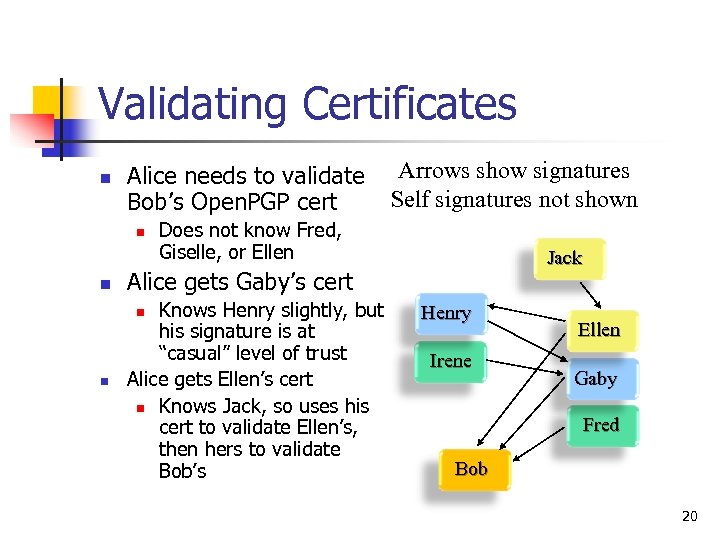 Validating Certificates n Alice needs to validate Bob’s Open. PGP cert n n Does not know Fred, Giselle, or Ellen Jack Alice gets Gaby’s cert Knows Henry slightly, but his signature is at “casual” level of trust Alice gets Ellen’s cert n Knows Jack, so uses his cert to validate Ellen’s, then hers to validate Bob’s n n Arrows show signatures Self signatures not shown Henry Irene Ellen Gaby Fred Bob 20
Validating Certificates n Alice needs to validate Bob’s Open. PGP cert n n Does not know Fred, Giselle, or Ellen Jack Alice gets Gaby’s cert Knows Henry slightly, but his signature is at “casual” level of trust Alice gets Ellen’s cert n Knows Jack, so uses his cert to validate Ellen’s, then hers to validate Bob’s n n Arrows show signatures Self signatures not shown Henry Irene Ellen Gaby Fred Bob 20
 X. 509 vs PGP Certificates n Unlike X. 509, n n n PGP allows multiple signers for the same certificate a notion of trust is included in PGP by using the Signature Type Self-signing is allowed in PGP n All public keys in Version 4 21
X. 509 vs PGP Certificates n Unlike X. 509, n n n PGP allows multiple signers for the same certificate a notion of trust is included in PGP by using the Signature Type Self-signing is allowed in PGP n All public keys in Version 4 21
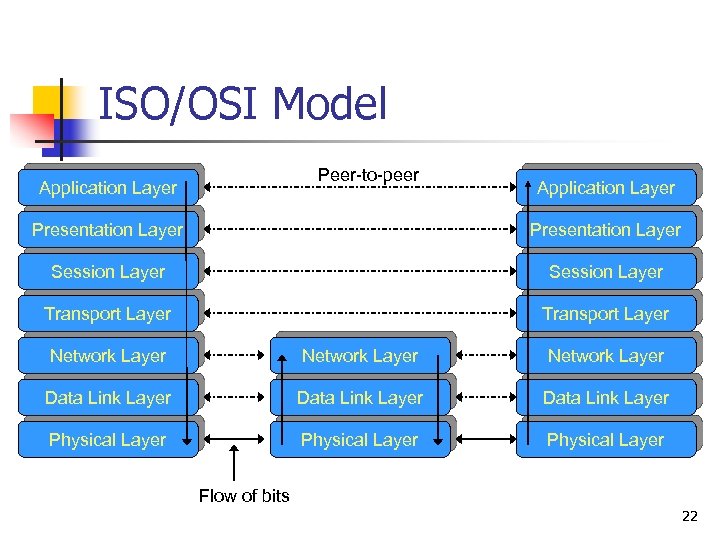 ISO/OSI Model Peer-to-peer Application Layer Presentation Layer Session Layer Transport Layer Network Layer Data Link Layer Physical Layer Flow of bits 22
ISO/OSI Model Peer-to-peer Application Layer Presentation Layer Session Layer Transport Layer Network Layer Data Link Layer Physical Layer Flow of bits 22
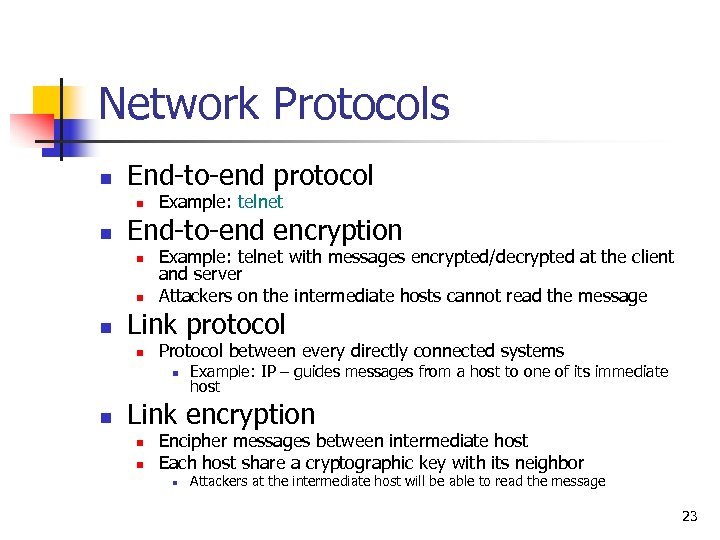 Network Protocols n End-to-end protocol n n End-to-end encryption n Example: telnet with messages encrypted/decrypted at the client and server Attackers on the intermediate hosts cannot read the message Link protocol n Protocol between every directly connected systems n n Example: IP – guides messages from a host to one of its immediate host Link encryption n n Encipher messages between intermediate host Each host share a cryptographic key with its neighbor n Attackers at the intermediate host will be able to read the message 23
Network Protocols n End-to-end protocol n n End-to-end encryption n Example: telnet with messages encrypted/decrypted at the client and server Attackers on the intermediate hosts cannot read the message Link protocol n Protocol between every directly connected systems n n Example: IP – guides messages from a host to one of its immediate host Link encryption n n Encipher messages between intermediate host Each host share a cryptographic key with its neighbor n Attackers at the intermediate host will be able to read the message 23
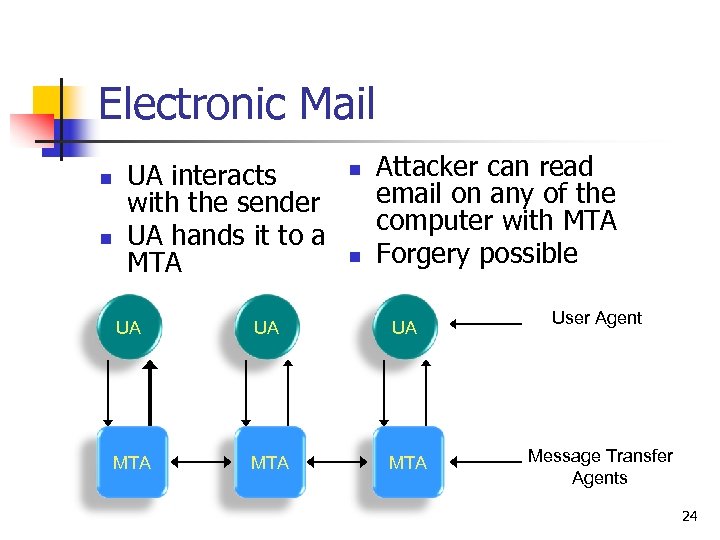 Electronic Mail n n UA interacts with the sender UA hands it to a MTA n n Attacker can read email on any of the computer with MTA Forgery possible UA UA UA MTA MTA User Agent Message Transfer Agents 24
Electronic Mail n n UA interacts with the sender UA hands it to a MTA n n Attacker can read email on any of the computer with MTA Forgery possible UA UA UA MTA MTA User Agent Message Transfer Agents 24
 Security at the Application Layer: Privacy-enhanced Electronic Mail n Study by Internet Research Task Force on Privacy or Privacy Research Group to develop protocols with following services n n Confidentiality, by making the message unreadable except to the sender and recipients Origin authentication, by identifying the sender precisely Data integrity, by ensuring that any changes In the message are easy to detect Non-repudiation of the origin (if possible) 25
Security at the Application Layer: Privacy-enhanced Electronic Mail n Study by Internet Research Task Force on Privacy or Privacy Research Group to develop protocols with following services n n Confidentiality, by making the message unreadable except to the sender and recipients Origin authentication, by identifying the sender precisely Data integrity, by ensuring that any changes In the message are easy to detect Non-repudiation of the origin (if possible) 25
 Design Considerations/goals for PEM n n Not to redesign existing mail system protocols To be compatible with a range of MTAs, UAs and other computers To make privacy enhancements available separately so they are not required To enable parties to use the protocol to communicate without prearrangement 26
Design Considerations/goals for PEM n n Not to redesign existing mail system protocols To be compatible with a range of MTAs, UAs and other computers To make privacy enhancements available separately so they are not required To enable parties to use the protocol to communicate without prearrangement 26
 PEM: Basic Design n Defines two keys n Data Encipherment Key (DEK) to encipher the message sent n n Generated randomly Used only once Sent to the recipient Interchange key: to encipher DEK n Must be obtained some other way than through the message 27
PEM: Basic Design n Defines two keys n Data Encipherment Key (DEK) to encipher the message sent n n Generated randomly Used only once Sent to the recipient Interchange key: to encipher DEK n Must be obtained some other way than through the message 27
 Protocol n Confidential message (DEK: ks) Alice n Bob Authenticated, integrity-checked message Alice n {m}ks || {ks}k. Bob m || {h(m)}k. Alice Bob Enciphered, authenticated, integrity checked message Alice {m}ks || {h(m)}k. Alice || {ks}k. Bob 28
Protocol n Confidential message (DEK: ks) Alice n Bob Authenticated, integrity-checked message Alice n {m}ks || {ks}k. Bob m || {h(m)}k. Alice Bob Enciphered, authenticated, integrity checked message Alice {m}ks || {h(m)}k. Alice || {ks}k. Bob 28
 ISO/OSI Model IPSec: Security at Network Layer Peer-to-peer Application Layer Presentation Layer Session Layer Transport Layer Network Layer Data Link Layer Physical Layer Flow of bits 29
ISO/OSI Model IPSec: Security at Network Layer Peer-to-peer Application Layer Presentation Layer Session Layer Transport Layer Network Layer Data Link Layer Physical Layer Flow of bits 29
 Security at the Transport Layer: Secure Socket Layer (SSL) n Developed by Netscape to provide security in WWW browsers and servers n n Transport Layer Security (TLS) protocol (compatible with SSLv 3) n n Uses X. 509 certificates SSL is the basis for the Internet standard protocol Key idea: Connections and Sessions n n A SSL session is an association between two peers An SSL connection is the set of mechanisms used to transport data in an SSL session
Security at the Transport Layer: Secure Socket Layer (SSL) n Developed by Netscape to provide security in WWW browsers and servers n n Transport Layer Security (TLS) protocol (compatible with SSLv 3) n n Uses X. 509 certificates SSL is the basis for the Internet standard protocol Key idea: Connections and Sessions n n A SSL session is an association between two peers An SSL connection is the set of mechanisms used to transport data in an SSL session
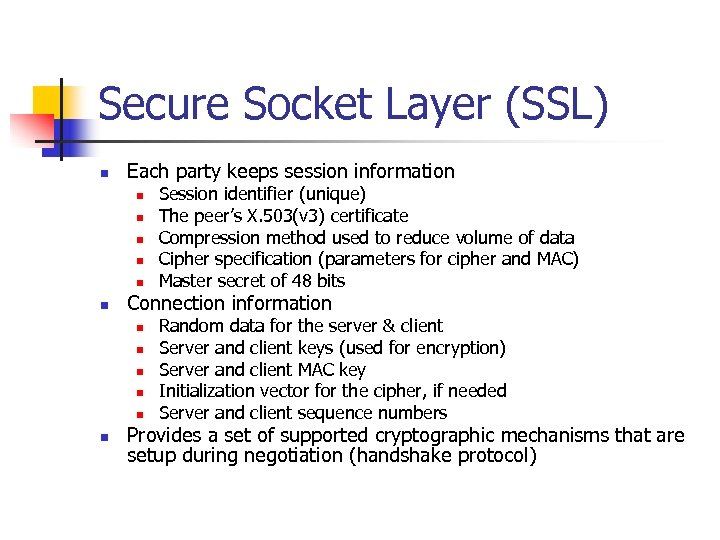 Secure Socket Layer (SSL) n Each party keeps session information n n n Connection information n n n Session identifier (unique) The peer’s X. 503(v 3) certificate Compression method used to reduce volume of data Cipher specification (parameters for cipher and MAC) Master secret of 48 bits Random data for the server & client Server and client keys (used for encryption) Server and client MAC key Initialization vector for the cipher, if needed Server and client sequence numbers Provides a set of supported cryptographic mechanisms that are setup during negotiation (handshake protocol)
Secure Socket Layer (SSL) n Each party keeps session information n n n Connection information n n n Session identifier (unique) The peer’s X. 503(v 3) certificate Compression method used to reduce volume of data Cipher specification (parameters for cipher and MAC) Master secret of 48 bits Random data for the server & client Server and client keys (used for encryption) Server and client MAC key Initialization vector for the cipher, if needed Server and client sequence numbers Provides a set of supported cryptographic mechanisms that are setup during negotiation (handshake protocol)
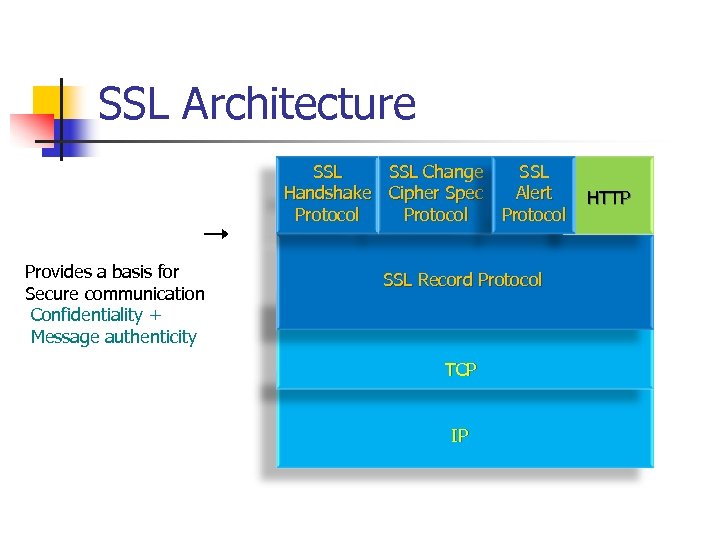 SSL Architecture SSL Change Handshake Cipher Spec Protocol Provides a basis for Secure communication Confidentiality + Message authenticity SSL Alert Protocol SSL Record Protocol TCP IP HTTP
SSL Architecture SSL Change Handshake Cipher Spec Protocol Provides a basis for Secure communication Confidentiality + Message authenticity SSL Alert Protocol SSL Record Protocol TCP IP HTTP
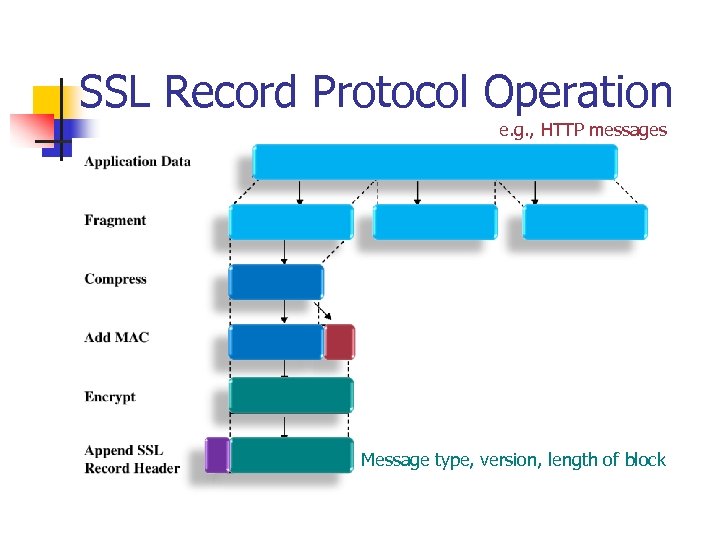 SSL Record Protocol Operation e. g. , HTTP messages Message type, version, length of block
SSL Record Protocol Operation e. g. , HTTP messages Message type, version, length of block
 Handshake Protocol n n The most complex part of SSL Allows the server and client to authenticate each other n n Negotiate encryption, MAC algorithm and cryptographic keys n n Based on interchange cryptosystem (e. g. , RSA) Four rounds Used before any application data are transmitted
Handshake Protocol n n The most complex part of SSL Allows the server and client to authenticate each other n n Negotiate encryption, MAC algorithm and cryptographic keys n n Based on interchange cryptosystem (e. g. , RSA) Four rounds Used before any application data are transmitted
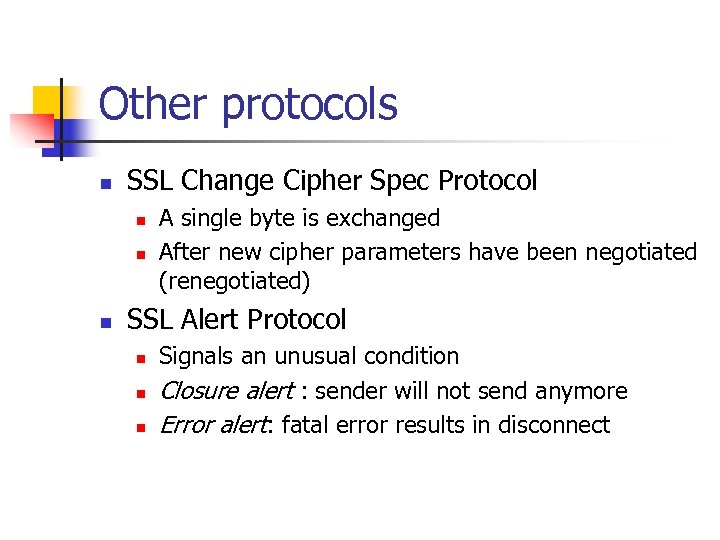 Other protocols n SSL Change Cipher Spec Protocol n n n A single byte is exchanged After new cipher parameters have been negotiated (renegotiated) SSL Alert Protocol n n n Signals an unusual condition Closure alert : sender will not send anymore Error alert: fatal error results in disconnect
Other protocols n SSL Change Cipher Spec Protocol n n n A single byte is exchanged After new cipher parameters have been negotiated (renegotiated) SSL Alert Protocol n n n Signals an unusual condition Closure alert : sender will not send anymore Error alert: fatal error results in disconnect
 ISO/OSI Model IPSec: Security at Network Layer Peer-to-peer Application Layer Presentation Layer Session Layer Transport Layer Network Layer Data Link Layer Physical Layer Flow of bits 36
ISO/OSI Model IPSec: Security at Network Layer Peer-to-peer Application Layer Presentation Layer Session Layer Transport Layer Network Layer Data Link Layer Physical Layer Flow of bits 36
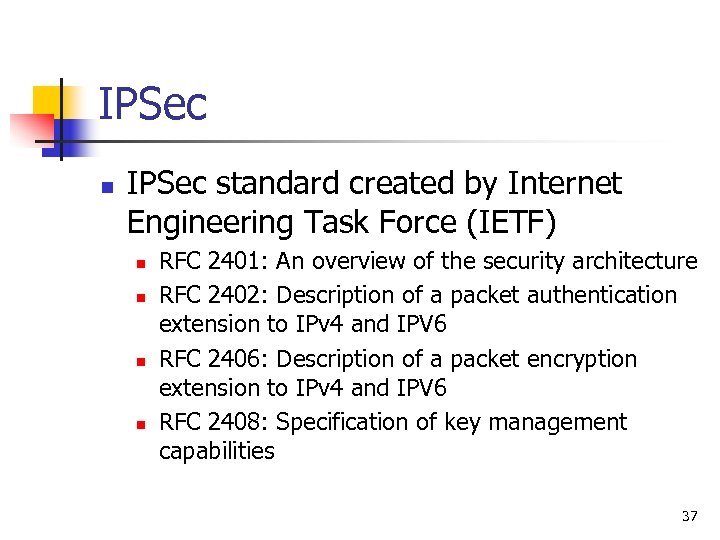 IPSec n IPSec standard created by Internet Engineering Task Force (IETF) n n RFC 2401: An overview of the security architecture RFC 2402: Description of a packet authentication extension to IPv 4 and IPV 6 RFC 2406: Description of a packet encryption extension to IPv 4 and IPV 6 RFC 2408: Specification of key management capabilities 37
IPSec n IPSec standard created by Internet Engineering Task Force (IETF) n n RFC 2401: An overview of the security architecture RFC 2402: Description of a packet authentication extension to IPv 4 and IPV 6 RFC 2406: Description of a packet encryption extension to IPv 4 and IPV 6 RFC 2408: Specification of key management capabilities 37
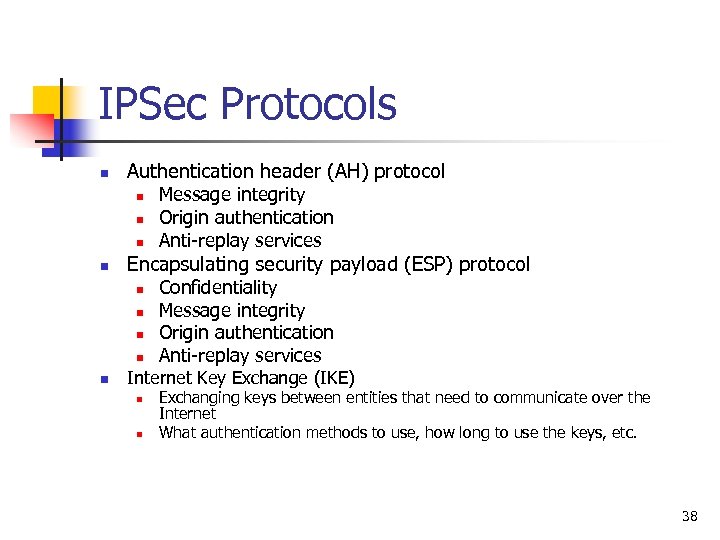 IPSec Protocols n Authentication header (AH) protocol n n Encapsulating security payload (ESP) protocol n n n Message integrity Origin authentication Anti-replay services Confidentiality Message integrity Origin authentication Anti-replay services Internet Key Exchange (IKE) n n Exchanging keys between entities that need to communicate over the Internet What authentication methods to use, how long to use the keys, etc. 38
IPSec Protocols n Authentication header (AH) protocol n n Encapsulating security payload (ESP) protocol n n n Message integrity Origin authentication Anti-replay services Confidentiality Message integrity Origin authentication Anti-replay services Internet Key Exchange (IKE) n n Exchanging keys between entities that need to communicate over the Internet What authentication methods to use, how long to use the keys, etc. 38
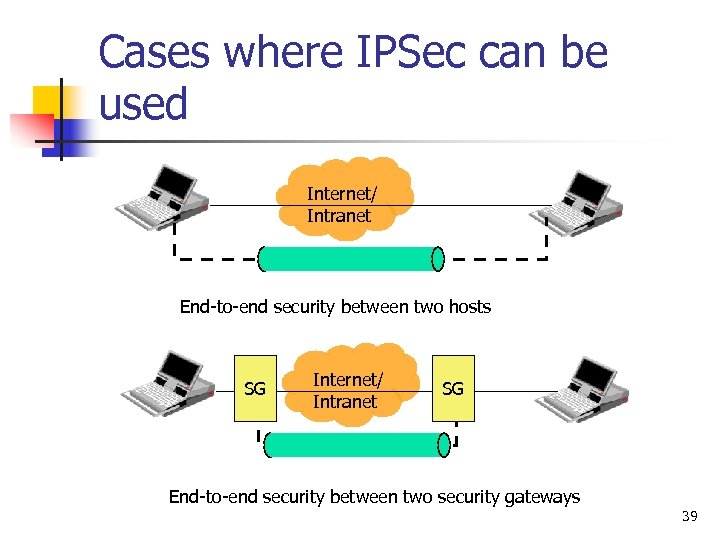 Cases where IPSec can be used Internet/ Intranet End-to-end security between two hosts SG Internet/ Intranet SG End-to-end security between two security gateways 39
Cases where IPSec can be used Internet/ Intranet End-to-end security between two hosts SG Internet/ Intranet SG End-to-end security between two security gateways 39
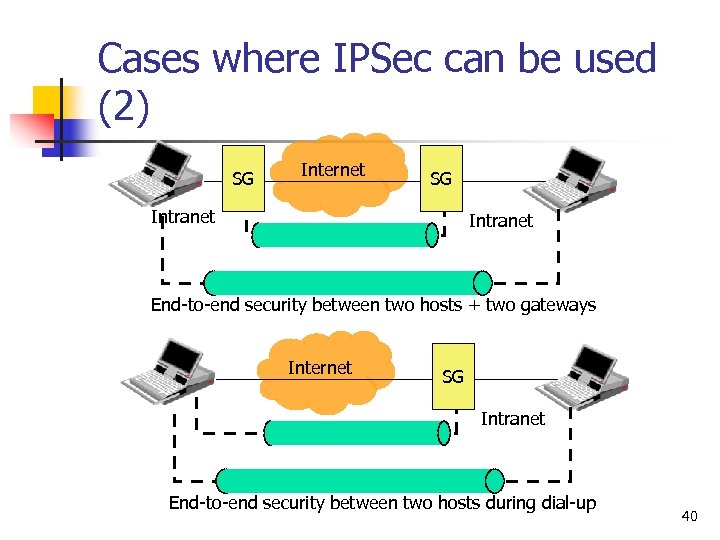 Cases where IPSec can be used (2) SG Internet SG Intranet End-to-end security between two hosts + two gateways Internet SG Intranet End-to-end security between two hosts during dial-up 40
Cases where IPSec can be used (2) SG Internet SG Intranet End-to-end security between two hosts + two gateways Internet SG Intranet End-to-end security between two hosts during dial-up 40
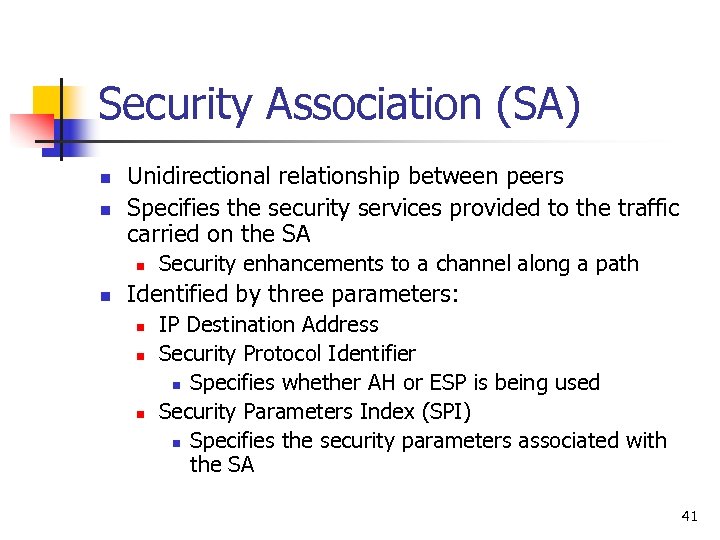 Security Association (SA) n n Unidirectional relationship between peers Specifies the security services provided to the traffic carried on the SA n n Security enhancements to a channel along a path Identified by three parameters: n n n IP Destination Address Security Protocol Identifier n Specifies whether AH or ESP is being used Security Parameters Index (SPI) n Specifies the security parameters associated with the SA 41
Security Association (SA) n n Unidirectional relationship between peers Specifies the security services provided to the traffic carried on the SA n n Security enhancements to a channel along a path Identified by three parameters: n n n IP Destination Address Security Protocol Identifier n Specifies whether AH or ESP is being used Security Parameters Index (SPI) n Specifies the security parameters associated with the SA 41
 Security Association (2) n Each SA uses AH or ESP (not both) n n If both required two SAs are created Multiple security associations may be used to provide required security services n A sequence of security associations is called SA bundle n Example: We can have an AH protocol followed by ESP or vice versa 42
Security Association (2) n Each SA uses AH or ESP (not both) n n If both required two SAs are created Multiple security associations may be used to provide required security services n A sequence of security associations is called SA bundle n Example: We can have an AH protocol followed by ESP or vice versa 42
 Security Association Databases n n IP needs to know the SAs that exist in order to provide security services Security Policy Database (SPD) n IPSec uses SPD to handle messages n n For each IP packet, it decides whether an IPSec service is provided, bypassed, or if the packet is to be discarded Security Association Database (SAD) n n n Keeps track of the sequence number AH information (keys, algorithms, lifetimes) ESP information (keys, algorithms, lifetimes, etc. ) Lifetime of the SA Protocol mode MTU et. c. 43
Security Association Databases n n IP needs to know the SAs that exist in order to provide security services Security Policy Database (SPD) n IPSec uses SPD to handle messages n n For each IP packet, it decides whether an IPSec service is provided, bypassed, or if the packet is to be discarded Security Association Database (SAD) n n n Keeps track of the sequence number AH information (keys, algorithms, lifetimes) ESP information (keys, algorithms, lifetimes, etc. ) Lifetime of the SA Protocol mode MTU et. c. 43
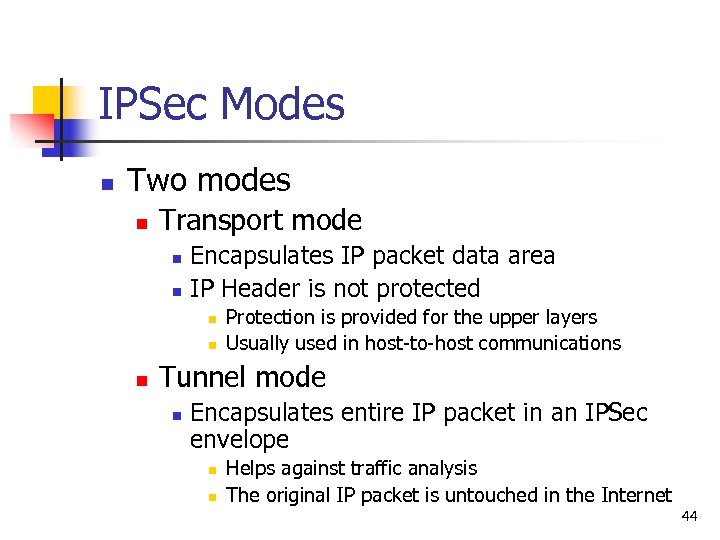 IPSec Modes n Two modes n Transport mode n n Encapsulates IP packet data area IP Header is not protected n n n Protection is provided for the upper layers Usually used in host-to-host communications Tunnel mode n Encapsulates entire IP packet in an IPSec envelope n n Helps against traffic analysis The original IP packet is untouched in the Internet 44
IPSec Modes n Two modes n Transport mode n n Encapsulates IP packet data area IP Header is not protected n n n Protection is provided for the upper layers Usually used in host-to-host communications Tunnel mode n Encapsulates entire IP packet in an IPSec envelope n n Helps against traffic analysis The original IP packet is untouched in the Internet 44
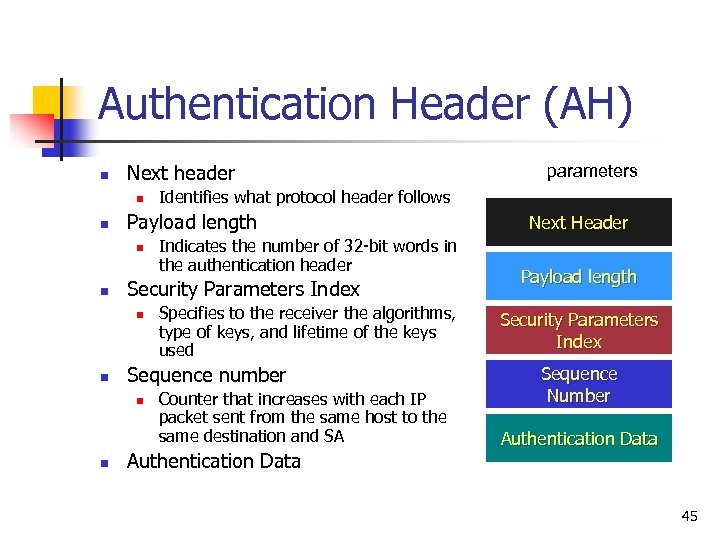 Authentication Header (AH) n Next header n n n Specifies to the receiver the algorithms, type of keys, and lifetime of the keys used Sequence number n n Indicates the number of 32 -bit words in the authentication header Security Parameters Index n n Identifies what protocol header follows Payload length n parameters Counter that increases with each IP packet sent from the same host to the same destination and SA Authentication Data Next Header Payload length Security Parameters Index Sequence Number Authentication Data 45
Authentication Header (AH) n Next header n n n Specifies to the receiver the algorithms, type of keys, and lifetime of the keys used Sequence number n n Indicates the number of 32 -bit words in the authentication header Security Parameters Index n n Identifies what protocol header follows Payload length n parameters Counter that increases with each IP packet sent from the same host to the same destination and SA Authentication Data Next Header Payload length Security Parameters Index Sequence Number Authentication Data 45
 Preventing replay n n Using 32 bit sequence numbers helps detect replay of IP packets The sender initializes a sequence number for every SA Receiver implements a window size of W to keep track of authenticated packets Receiver checks the MAC to see if the packet is authentic 46
Preventing replay n n Using 32 bit sequence numbers helps detect replay of IP packets The sender initializes a sequence number for every SA Receiver implements a window size of W to keep track of authenticated packets Receiver checks the MAC to see if the packet is authentic 46
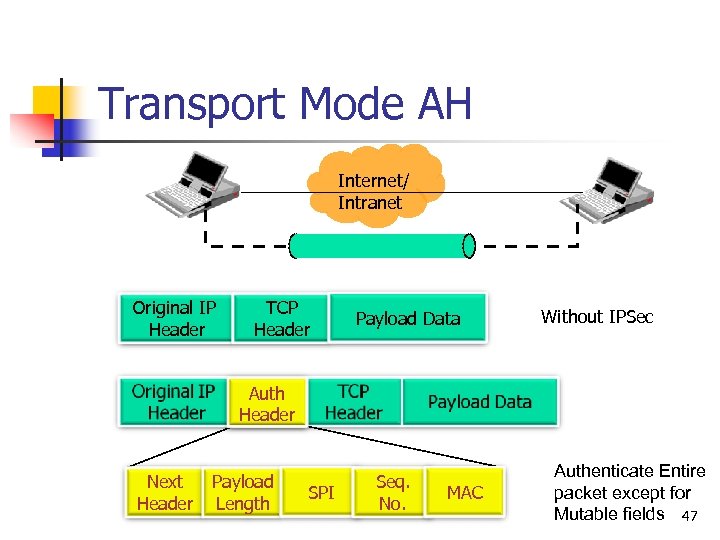 Transport Mode AH Internet/ Intranet Original IP Header TCP Header Payload Data Without IPSec Auth Header Next Header Payload Length SPI Seq. No. MAC Authenticate Entire packet except for Mutable fields 47
Transport Mode AH Internet/ Intranet Original IP Header TCP Header Payload Data Without IPSec Auth Header Next Header Payload Length SPI Seq. No. MAC Authenticate Entire packet except for Mutable fields 47
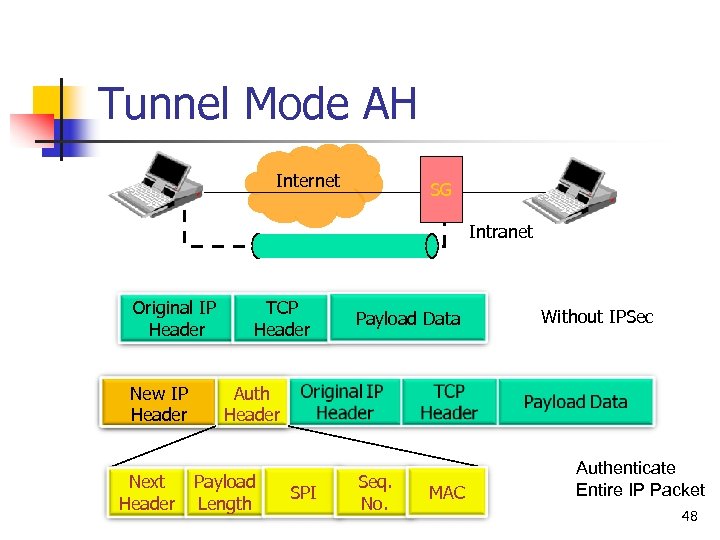 Tunnel Mode AH Internet SG Intranet Original IP Header New IP Header Next Header TCP Header Payload Data Without IPSec Auth Header Payload Length SPI Seq. No. MAC Authenticate Entire IP Packet 48
Tunnel Mode AH Internet SG Intranet Original IP Header New IP Header Next Header TCP Header Payload Data Without IPSec Auth Header Payload Length SPI Seq. No. MAC Authenticate Entire IP Packet 48
 ESP – Encapsulating Security Payload n n n Creates a new header in addition to the IP header Creates a new trailer Encrypts the payload data Authenticates Prevents replay 49
ESP – Encapsulating Security Payload n n n Creates a new header in addition to the IP header Creates a new trailer Encrypts the payload data Authenticates Prevents replay 49
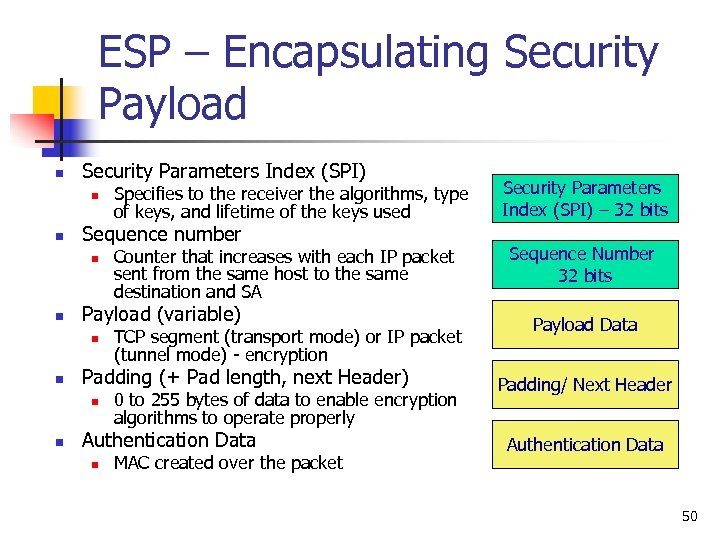 ESP – Encapsulating Security Payload n Security Parameters Index (SPI) n n Sequence number n n TCP segment (transport mode) or IP packet (tunnel mode) - encryption Padding (+ Pad length, next Header) n n Counter that increases with each IP packet sent from the same host to the same destination and SA Payload (variable) n n Specifies to the receiver the algorithms, type of keys, and lifetime of the keys used 0 to 255 bytes of data to enable encryption algorithms to operate properly Authentication Data n MAC created over the packet Security Parameters Index (SPI) – 32 bits Sequence Number 32 bits Payload Data Padding/ Next Header Authentication Data 50
ESP – Encapsulating Security Payload n Security Parameters Index (SPI) n n Sequence number n n TCP segment (transport mode) or IP packet (tunnel mode) - encryption Padding (+ Pad length, next Header) n n Counter that increases with each IP packet sent from the same host to the same destination and SA Payload (variable) n n Specifies to the receiver the algorithms, type of keys, and lifetime of the keys used 0 to 255 bytes of data to enable encryption algorithms to operate properly Authentication Data n MAC created over the packet Security Parameters Index (SPI) – 32 bits Sequence Number 32 bits Payload Data Padding/ Next Header Authentication Data 50
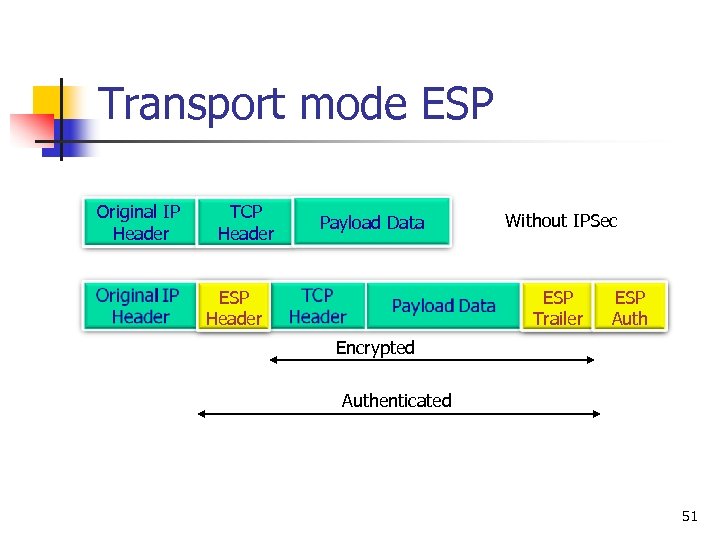 Transport mode ESP Original IP Header TCP Header Payload Data ESP Header Without IPSec ESP Trailer ESP Auth Encrypted Authenticated 51
Transport mode ESP Original IP Header TCP Header Payload Data ESP Header Without IPSec ESP Trailer ESP Auth Encrypted Authenticated 51
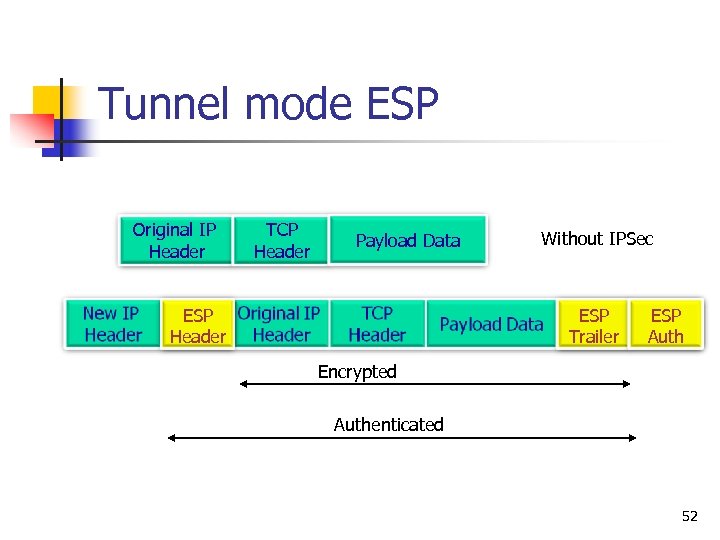 Tunnel mode ESP Original IP Header TCP Header Payload Data ESP Header Without IPSec ESP Trailer ESP Auth Encrypted Authenticated 52
Tunnel mode ESP Original IP Header TCP Header Payload Data ESP Header Without IPSec ESP Trailer ESP Auth Encrypted Authenticated 52
 Summary n n n Overview of X. 509 and Open PGP PEM, SSL and IPSec Security services available at different levels of the OSI seven layer model 53
Summary n n n Overview of X. 509 and Open PGP PEM, SSL and IPSec Security services available at different levels of the OSI seven layer model 53


