1e07c109388b62de17472e911b6a68ad.ppt
- Количество слайдов: 42
 Differences Windows Active Directory and Novell Directory Services Donnie Hamlett Technology Specialist Microsoft – New York
Differences Windows Active Directory and Novell Directory Services Donnie Hamlett Technology Specialist Microsoft – New York
 Agenda v v v v v Introduction X. 500 Directories, History and Terminology X. 500 Implemented with AD and NDS Objects Networking and Services LDAP Directory Design and Partitioning the Directory Programming Summary
Agenda v v v v v Introduction X. 500 Directories, History and Terminology X. 500 Implemented with AD and NDS Objects Networking and Services LDAP Directory Design and Partitioning the Directory Programming Summary
 Introduction v Purpose of this session is to get a thorough understanding of the basic differences between the Windows 2000 AD and Novell NDS.
Introduction v Purpose of this session is to get a thorough understanding of the basic differences between the Windows 2000 AD and Novell NDS.
 X. 500 History v X. 500 is the standard produced by the ISO/ITU defining the protocols and information model for a directory service that is independent of computing application and network platform Ø Ø v v v X. 509 Authentication Framework is a series of standards, describes the use of digital certificates and PKI X. 525 Replication First released in 1988 and updated in 1993 and 1997 X. 500 standard defines a specification for a rich, distributed directory based on hierarchically named information objects (directory entries) that users can browse and search X. 500 – Glorified, very logical, electronic yellow pages for X. 400 messaging systems
X. 500 History v X. 500 is the standard produced by the ISO/ITU defining the protocols and information model for a directory service that is independent of computing application and network platform Ø Ø v v v X. 509 Authentication Framework is a series of standards, describes the use of digital certificates and PKI X. 525 Replication First released in 1988 and updated in 1993 and 1997 X. 500 standard defines a specification for a rich, distributed directory based on hierarchically named information objects (directory entries) that users can browse and search X. 500 – Glorified, very logical, electronic yellow pages for X. 400 messaging systems
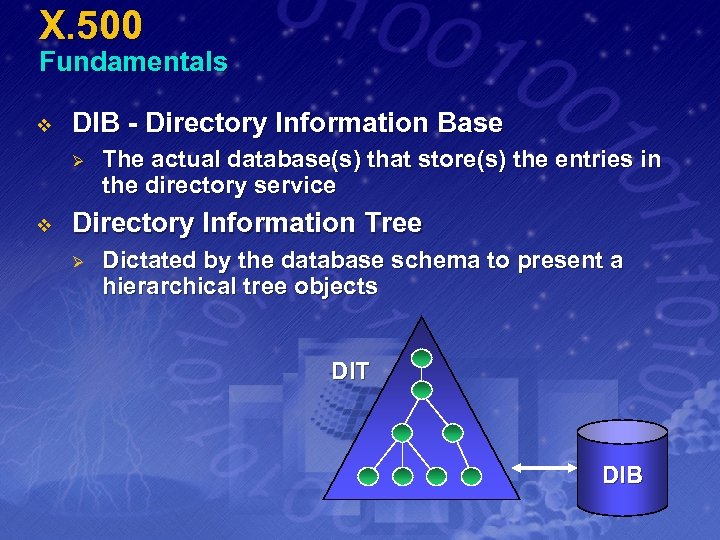 X. 500 Fundamentals v DIB - Directory Information Base Ø v The actual database(s) that store(s) the entries in the directory service Directory Information Tree Ø Dictated by the database schema to present a hierarchical tree objects DIT DIB
X. 500 Fundamentals v DIB - Directory Information Base Ø v The actual database(s) that store(s) the entries in the directory service Directory Information Tree Ø Dictated by the database schema to present a hierarchical tree objects DIT DIB
 X. 500 v Schema Ø v Design of the directory store. Defines objects, attributes, and system information Object Classes Ø Ø Ø Define the kinds of objects that can be instantiated in the directory Define the rules for an object Define the attributes that are intended for the object DIB Object Attribute
X. 500 v Schema Ø v Design of the directory store. Defines objects, attributes, and system information Object Classes Ø Ø Ø Define the kinds of objects that can be instantiated in the directory Define the rules for an object Define the attributes that are intended for the object DIB Object Attribute
 X. 500 v Objects Ø Ø v Specific entries in the directory store Are comprise of attributes Attributes Ø Describe certain aspects of the object USER OBJECT Attributes. . First Name, Last Name, Phone Number, Address
X. 500 v Objects Ø Ø v Specific entries in the directory store Are comprise of attributes Attributes Ø Describe certain aspects of the object USER OBJECT Attributes. . First Name, Last Name, Phone Number, Address
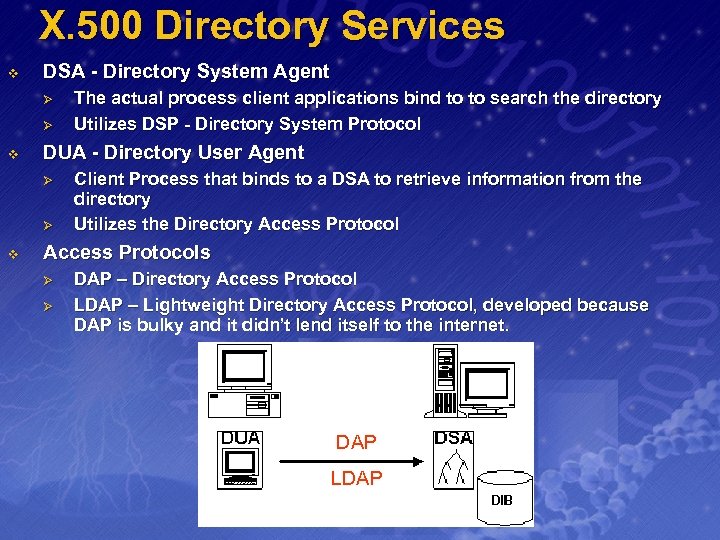 X. 500 Directory Services v DSA - Directory System Agent Ø Ø v DUA - Directory User Agent Ø Ø v The actual process client applications bind to to search the directory Utilizes DSP - Directory System Protocol Client Process that binds to a DSA to retrieve information from the directory Utilizes the Directory Access Protocols Ø Ø DAP – Directory Access Protocol LDAP – Lightweight Directory Access Protocol, developed because DAP is bulky and it didn’t lend itself to the internet. DAP LDAP
X. 500 Directory Services v DSA - Directory System Agent Ø Ø v DUA - Directory User Agent Ø Ø v The actual process client applications bind to to search the directory Utilizes DSP - Directory System Protocol Client Process that binds to a DSA to retrieve information from the directory Utilizes the Directory Access Protocols Ø Ø DAP – Directory Access Protocol LDAP – Lightweight Directory Access Protocol, developed because DAP is bulky and it didn’t lend itself to the internet. DAP LDAP
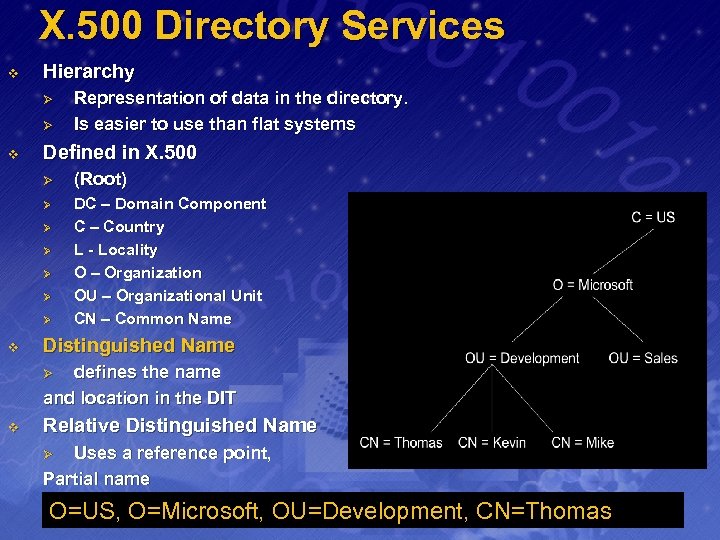 X. 500 Directory Services v Hierarchy Ø Ø v Representation of data in the directory. Is easier to use than flat systems Defined in X. 500 Ø (Root) Ø DC – Domain Component C – Country L - Locality O – Organization OU – Organizational Unit CN – Common Name Ø Ø Ø v Distinguished Name defines the name and location in the DIT Ø v Relative Distinguished Name Uses a reference point, Partial name Ø O=US, O=Microsoft, OU=Development, CN=Thomas
X. 500 Directory Services v Hierarchy Ø Ø v Representation of data in the directory. Is easier to use than flat systems Defined in X. 500 Ø (Root) Ø DC – Domain Component C – Country L - Locality O – Organization OU – Organizational Unit CN – Common Name Ø Ø Ø v Distinguished Name defines the name and location in the DIT Ø v Relative Distinguished Name Uses a reference point, Partial name Ø O=US, O=Microsoft, OU=Development, CN=Thomas
 X. 500 Implemented with AD and NDS v No one used the full set of X. 500 definitions to design their directory service. v Everyone has their own proprietary take on how X. 500 is implemented.
X. 500 Implemented with AD and NDS v No one used the full set of X. 500 definitions to design their directory service. v Everyone has their own proprietary take on how X. 500 is implemented.
 Differences – X. 500 Names v Both Novell and AD use X. 500 name schemes but they do not implement all of them. Active Directory Novell Directory Service DC C OU O CN OU CN
Differences – X. 500 Names v Both Novell and AD use X. 500 name schemes but they do not implement all of them. Active Directory Novell Directory Service DC C OU O CN OU CN
 Differences – Objects v Windows – Static Inheritance Ø Ø v More weight on directory at creation, write intensive All Ace's are contained within the object Larger objects increases the size of the DIB Rights controlled by groups Novell – Dynamic Inheritance Ø Ø When the object is called you must aggregate its rights by walking the tree More weight on the directory when read Rights controlled by OU’s (also groups) Must Tree Walk – this can go across WAN – bad
Differences – Objects v Windows – Static Inheritance Ø Ø v More weight on directory at creation, write intensive All Ace's are contained within the object Larger objects increases the size of the DIB Rights controlled by groups Novell – Dynamic Inheritance Ø Ø When the object is called you must aggregate its rights by walking the tree More weight on the directory when read Rights controlled by OU’s (also groups) Must Tree Walk – this can go across WAN – bad
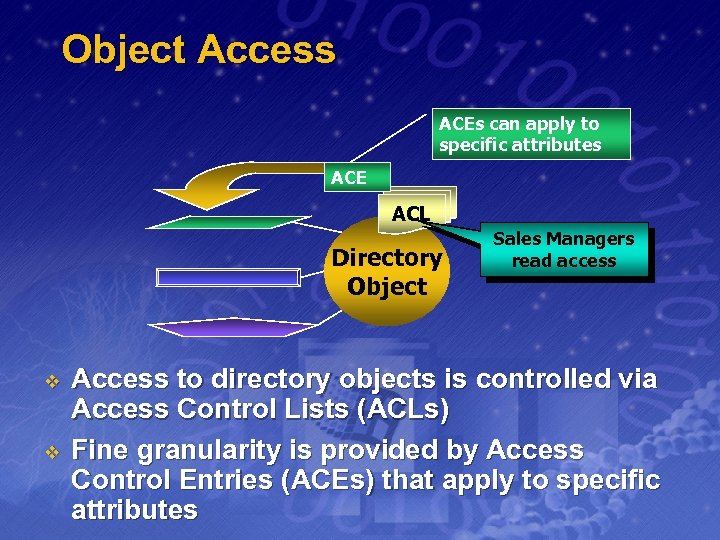 Object Access ACEs can apply to specific attributes ACE ACL Directory Object v v Sales Managers read access Access to directory objects is controlled via Access Control Lists (ACLs) Fine granularity is provided by Access Control Entries (ACEs) that apply to specific attributes
Object Access ACEs can apply to specific attributes ACE ACL Directory Object v v Sales Managers read access Access to directory objects is controlled via Access Control Lists (ACLs) Fine granularity is provided by Access Control Entries (ACEs) that apply to specific attributes
 Global Data Availability - Catalogs Windows 2000 Forest acme. com asia. acme. com v xyx. com europe. acme. com = Global Catalog Replica Active Directory Catalogs: Ø Ø Enable efficient cross-domain data sharing Use the same set-up tools as replicas Use same replication mechanisms and the same interval as domain replicas Enforce object and attribute level security
Global Data Availability - Catalogs Windows 2000 Forest acme. com asia. acme. com v xyx. com europe. acme. com = Global Catalog Replica Active Directory Catalogs: Ø Ø Enable efficient cross-domain data sharing Use the same set-up tools as replicas Use same replication mechanisms and the same interval as domain replicas Enforce object and attribute level security
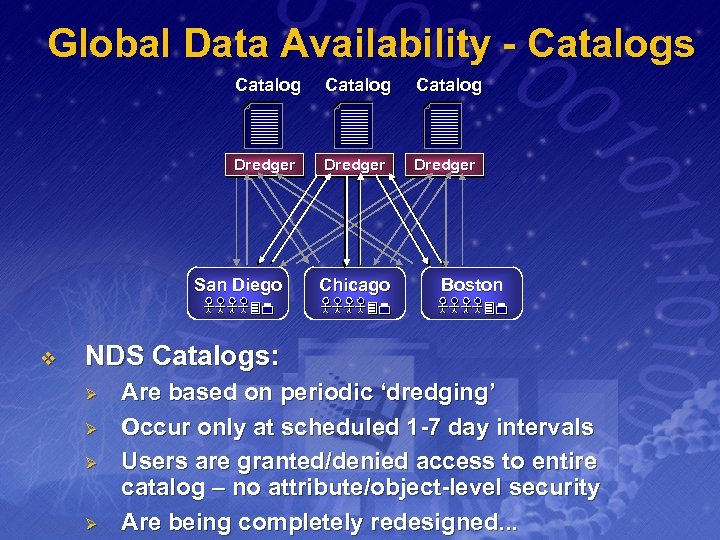 Global Data Availability - Catalogs Catalog Dredger San Diego v Chicago Boston NDS Catalogs: Ø Ø Are based on periodic ‘dredging’ Occur only at scheduled 1 -7 day intervals Users are granted/denied access to entire catalog – no attribute/object-level security Are being completely redesigned. . .
Global Data Availability - Catalogs Catalog Dredger San Diego v Chicago Boston NDS Catalogs: Ø Ø Are based on periodic ‘dredging’ Occur only at scheduled 1 -7 day intervals Users are granted/denied access to entire catalog – no attribute/object-level security Are being completely redesigned. . .
 Differences – Networking and Services v Active Directory Ø Ø Ø v Based on TCPIP DNS Server Resource Records ( MX-Record) LDAP for internal searches, each object has a unique GUID example on following page All Domain Controllers are native LDAP Servers Integrates with DNS NDS Ø Originally based on IPX/SPX v Ø Implemented in TCPIP with v v Ø Ø Service Advertising Protocol (SAP) to advertise Services Service Location Protocol (SLIP) also advertisement based SLIP does not integrate with DNS proprietary When implemented together reduces network performance because routers must support RIP that allows for both SLIP and SAP protocols Not a native LDAP Server – it has a LDAP interface that translates LDAP request to native NDAP protocols
Differences – Networking and Services v Active Directory Ø Ø Ø v Based on TCPIP DNS Server Resource Records ( MX-Record) LDAP for internal searches, each object has a unique GUID example on following page All Domain Controllers are native LDAP Servers Integrates with DNS NDS Ø Originally based on IPX/SPX v Ø Implemented in TCPIP with v v Ø Ø Service Advertising Protocol (SAP) to advertise Services Service Location Protocol (SLIP) also advertisement based SLIP does not integrate with DNS proprietary When implemented together reduces network performance because routers must support RIP that allows for both SLIP and SAP protocols Not a native LDAP Server – it has a LDAP interface that translates LDAP request to native NDAP protocols
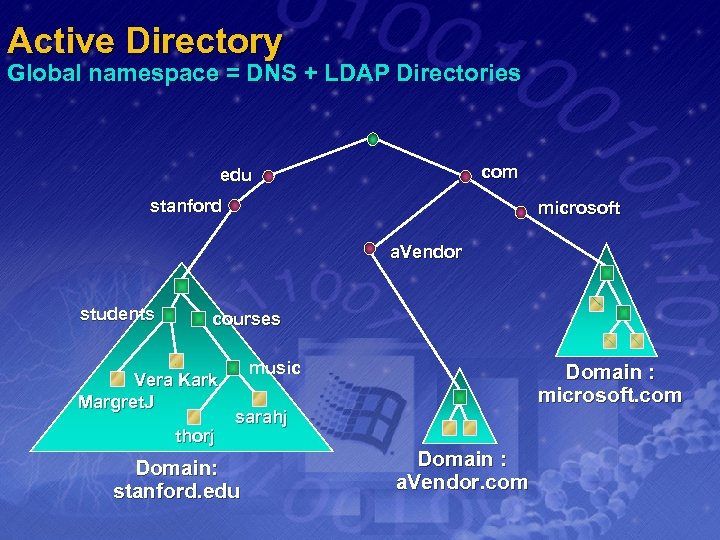 Active Directory Global namespace = DNS + LDAP Directories com edu stanford microsoft a. Vendor students courses Vera Kark Margret. J thorj music Domain : microsoft. com sarahj Domain: stanford. edu Domain : a. Vendor. com
Active Directory Global namespace = DNS + LDAP Directories com edu stanford microsoft a. Vendor students courses Vera Kark Margret. J thorj music Domain : microsoft. com sarahj Domain: stanford. edu Domain : a. Vendor. com
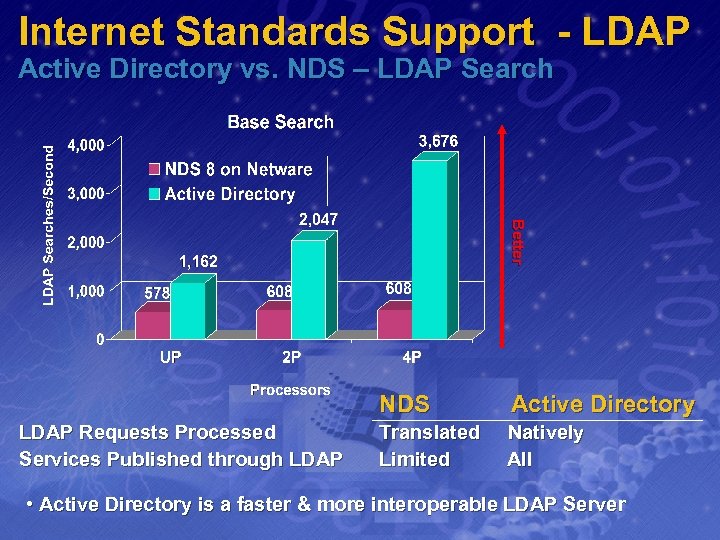 Internet Standards Support - LDAP Active Directory vs. NDS – LDAP Search Better LDAP Requests Processed Services Published through LDAP NDS Active Directory Translated Natively Limited All • Active Directory is a faster & more interoperable LDAP Server
Internet Standards Support - LDAP Active Directory vs. NDS – LDAP Search Better LDAP Requests Processed Services Published through LDAP NDS Active Directory Translated Natively Limited All • Active Directory is a faster & more interoperable LDAP Server
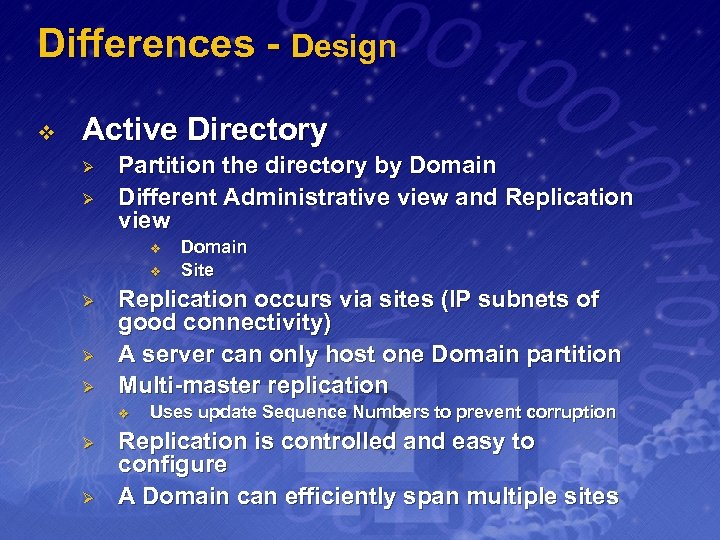 Differences - Design v Active Directory Ø Ø Partition the directory by Domain Different Administrative view and Replication view v v Ø Ø Ø Replication occurs via sites (IP subnets of good connectivity) A server can only host one Domain partition Multi-master replication v Ø Ø Domain Site Uses update Sequence Numbers to prevent corruption Replication is controlled and easy to configure A Domain can efficiently span multiple sites
Differences - Design v Active Directory Ø Ø Partition the directory by Domain Different Administrative view and Replication view v v Ø Ø Ø Replication occurs via sites (IP subnets of good connectivity) A server can only host one Domain partition Multi-master replication v Ø Ø Domain Site Uses update Sequence Numbers to prevent corruption Replication is controlled and easy to configure A Domain can efficiently span multiple sites
 Replication v What is Replicated ? – only changes are replicated Directory Information v Configuration v Schema v v There are two forms of replication Intrasite Replication v Intersite Replication v v Knowledge Consistency Checker v v Automatically configures and checks topology for the most efficient replication Tools Sites and Services MMC snap-in v Replmon v
Replication v What is Replicated ? – only changes are replicated Directory Information v Configuration v Schema v v There are two forms of replication Intrasite Replication v Intersite Replication v v Knowledge Consistency Checker v v Automatically configures and checks topology for the most efficient replication Tools Sites and Services MMC snap-in v Replmon v
 Sites v A Site separates networks physical topology from the Active Directories logical view of the Network v Site is a area of “good connectivity” v A Site is a collection of subnets v All directory replication is controlled via Sites v A Site can be composed of multiple Domains v Clients discover their site based on the subnet mask received from DHCP (or hand-configured) v Basis for locality-based resource discovery
Sites v A Site separates networks physical topology from the Active Directories logical view of the Network v Site is a area of “good connectivity” v A Site is a collection of subnets v All directory replication is controlled via Sites v A Site can be composed of multiple Domains v Clients discover their site based on the subnet mask received from DHCP (or hand-configured) v Basis for locality-based resource discovery
 Intrasite Replication v v Automatically Configured for you Replication occurs whenever there is a directory change or a interval of ~ 7 minutes Not Compressed Not easily controllable
Intrasite Replication v v Automatically Configured for you Replication occurs whenever there is a directory change or a interval of ~ 7 minutes Not Compressed Not easily controllable
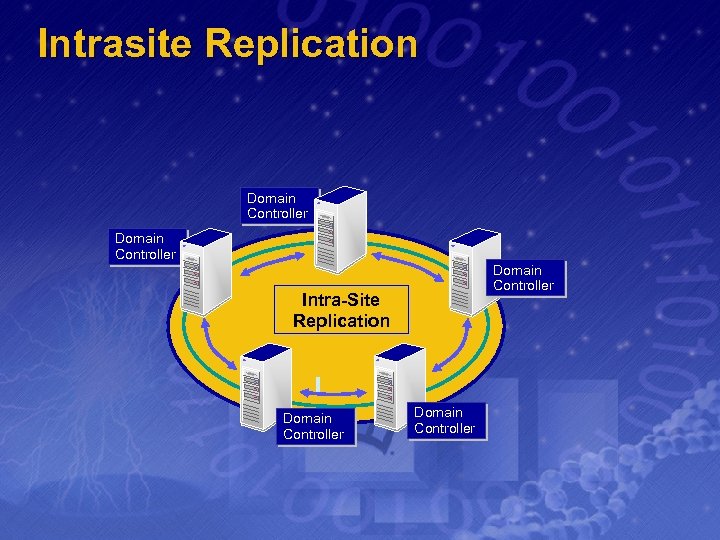 Intrasite Replication Domain Controller Intra-Site Replication Domain Controller
Intrasite Replication Domain Controller Intra-Site Replication Domain Controller
 Intersite Replication Compressed 10 -1 v Configurable v v Scheduled (15 minutes – 3 hours) v RPC or SMTP v Site Links v Site Bridges
Intersite Replication Compressed 10 -1 v Configurable v v Scheduled (15 minutes – 3 hours) v RPC or SMTP v Site Links v Site Bridges
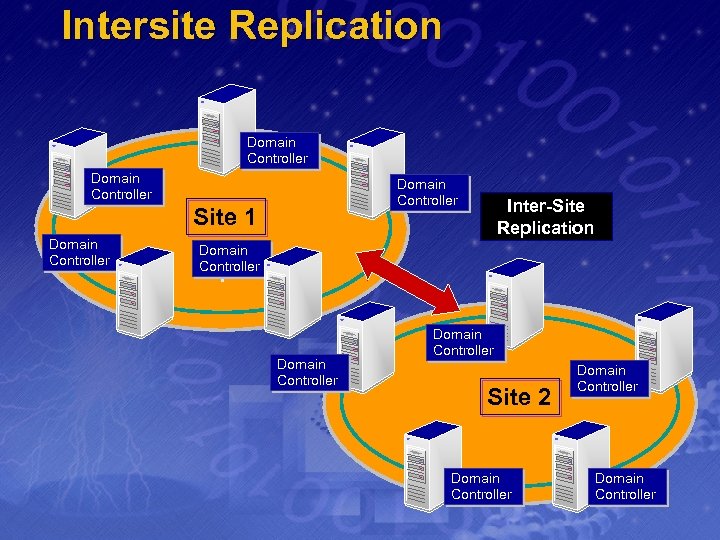 Intersite Replication Domain Controller Site 1 Domain Controller Inter-Site Replication Domain Controller Site 2 Domain Controller
Intersite Replication Domain Controller Site 1 Domain Controller Inter-Site Replication Domain Controller Site 2 Domain Controller
 Site Links · · · Represents the Priority of Replication Traffic Between the Sites Identified in the Site Link Higher Cost Numbers Represent Lower Priority Replication Paths Control Topology by Setting the Costs on Site Links Control the Replication Frequency by Setting the Number of Minutes Between Replication Attempts Control Link Availability Using the Schedule on Site Links Can Link multiple site to create a controlled path of replication called a Site Bridge
Site Links · · · Represents the Priority of Replication Traffic Between the Sites Identified in the Site Link Higher Cost Numbers Represent Lower Priority Replication Paths Control Topology by Setting the Costs on Site Links Control the Replication Frequency by Setting the Number of Minutes Between Replication Attempts Control Link Availability Using the Schedule on Site Links Can Link multiple site to create a controlled path of replication called a Site Bridge
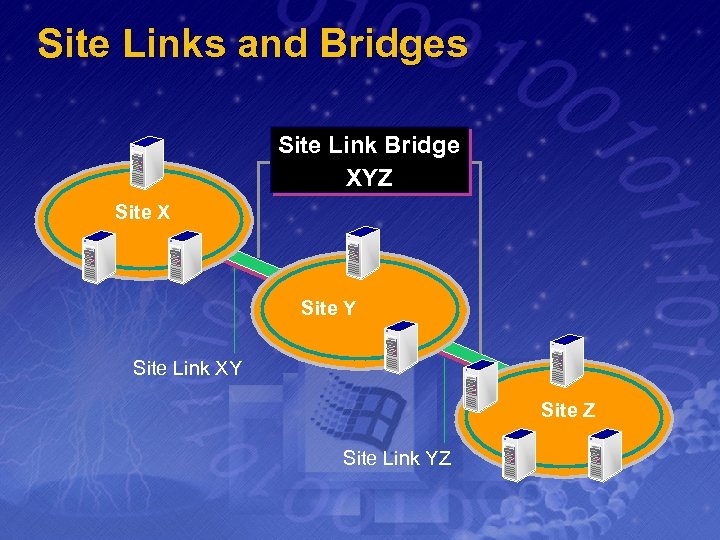 Site Links and Bridges Site Link Bridge XYZ Site X Site Y Site Link XY Site Z Site Link YZ
Site Links and Bridges Site Link Bridge XYZ Site X Site Y Site Link XY Site Z Site Link YZ
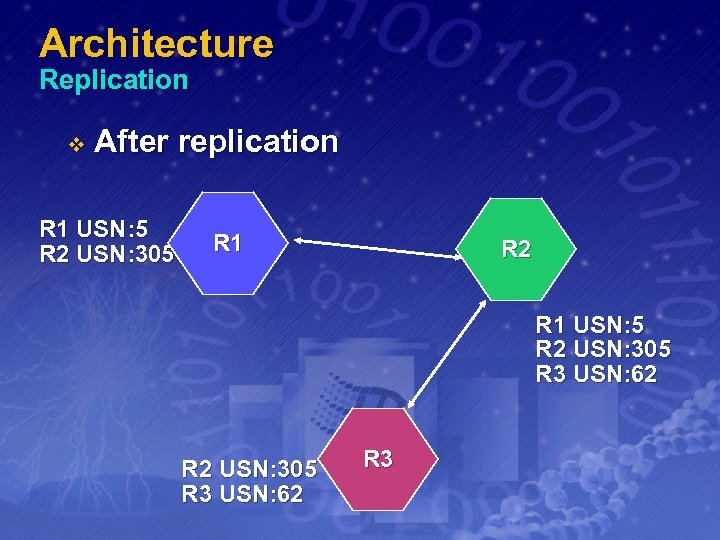 Architecture Replication v After replication R 1 USN: 5 R 2 USN: 305 R 1 R 2 R 1 USN: 5 R 2 USN: 305 R 3 USN: 62 R 3
Architecture Replication v After replication R 1 USN: 5 R 2 USN: 305 R 1 R 2 R 1 USN: 5 R 2 USN: 305 R 3 USN: 62 R 3
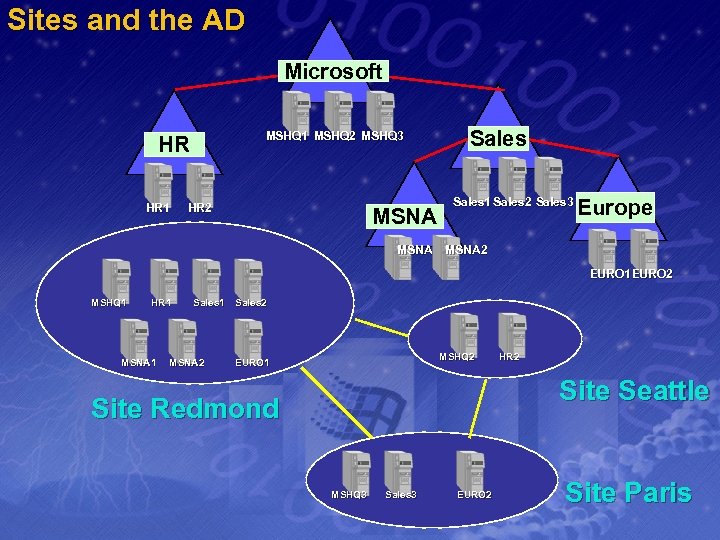 Sites and the AD Microsoft MSHQ 1 MSHQ 2 MSHQ 3 HR HR 1 HR 2 MSNA Sales 1 Sales 2 Sales 3 Europe MSNA 1 MSNA 2 EURO 1 EURO 2 MSHQ 1 HR 1 MSNA 1 Sales 2 MSNA 2 MSHQ 2 EURO 1 HR 2 Site Seattle Site Redmond MSHQ 3 Sales 3 EURO 2 Site Paris
Sites and the AD Microsoft MSHQ 1 MSHQ 2 MSHQ 3 HR HR 1 HR 2 MSNA Sales 1 Sales 2 Sales 3 Europe MSNA 1 MSNA 2 EURO 1 EURO 2 MSHQ 1 HR 1 MSNA 1 Sales 2 MSNA 2 MSHQ 2 EURO 1 HR 2 Site Seattle Site Redmond MSHQ 3 Sales 3 EURO 2 Site Paris
 Operation Masters v These Roles are v v v Recoverable – Recovery Console Transferable – Command Line These are the following Roles v v v RID Master – one per domain, controls relative id’s PDC Emulator – one per domain, allows password updates and backwards compatibility with NT 4. 0 BDC’s Infrastructure Master – one per domain, updates group and user information when changes are made Schema Master – one per forest, controls schema updates Domain Naming Master – one per forest, controls all additions and removals of domains
Operation Masters v These Roles are v v v Recoverable – Recovery Console Transferable – Command Line These are the following Roles v v v RID Master – one per domain, controls relative id’s PDC Emulator – one per domain, allows password updates and backwards compatibility with NT 4. 0 BDC’s Infrastructure Master – one per domain, updates group and user information when changes are made Schema Master – one per forest, controls schema updates Domain Naming Master – one per forest, controls all additions and removals of domains
 Differences - Design v NDS Ø Ø Ø Ø Partition the directory by OU OU’s are tied to physical locations Multimaster replication A server can host multiple partitions Replication occurs via time stamps Replication is very difficult to configure and is not controllable It is not recommended to have OU’s span physical boundaries
Differences - Design v NDS Ø Ø Ø Ø Partition the directory by OU OU’s are tied to physical locations Multimaster replication A server can host multiple partitions Replication occurs via time stamps Replication is very difficult to configure and is not controllable It is not recommended to have OU’s span physical boundaries
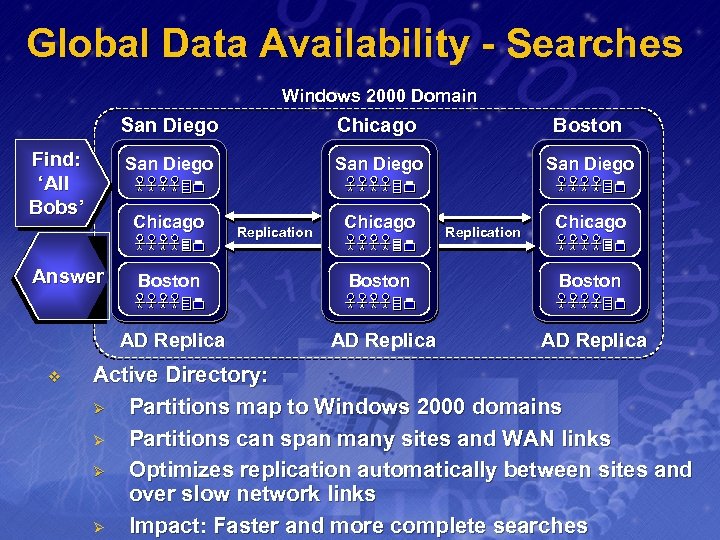 Global Data Availability - Searches Windows 2000 Domain San Diego Find: ‘All Bobs’ Chicago San Diego Chicago Answer Boston San Diego Replication Chicago Boston AD Replica v Boston AD Replica Active Directory: Ø Partitions map to Windows 2000 domains Ø Partitions can span many sites and WAN links Ø Optimizes replication automatically between sites and over slow network links Ø Impact: Faster and more complete searches
Global Data Availability - Searches Windows 2000 Domain San Diego Find: ‘All Bobs’ Chicago San Diego Chicago Answer Boston San Diego Replication Chicago Boston AD Replica v Boston AD Replica Active Directory: Ø Partitions map to Windows 2000 domains Ø Partitions can span many sites and WAN links Ø Optimizes replication automatically between sites and over slow network links Ø Impact: Faster and more complete searches
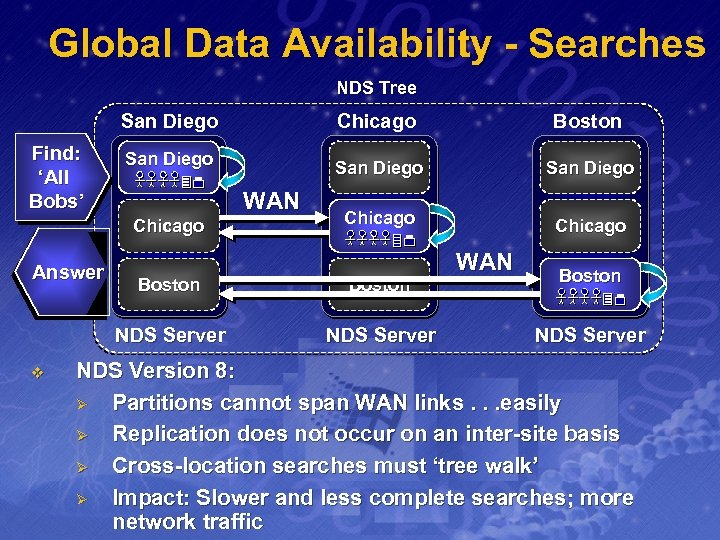 Global Data Availability - Searches NDS Tree San Diego Find: ‘All Bobs’ San Diego Chicago Boston NDS Server v Boston San Diego WAN Chicago Answer Chicago NDS Server WAN Boston NDS Server NDS Version 8: Ø Partitions cannot span WAN links. . . easily Ø Replication does not occur on an inter-site basis Ø Cross-location searches must ‘tree walk’ Ø Impact: Slower and less complete searches; more network traffic
Global Data Availability - Searches NDS Tree San Diego Find: ‘All Bobs’ San Diego Chicago Boston NDS Server v Boston San Diego WAN Chicago Answer Chicago NDS Server WAN Boston NDS Server NDS Version 8: Ø Partitions cannot span WAN links. . . easily Ø Replication does not occur on an inter-site basis Ø Cross-location searches must ‘tree walk’ Ø Impact: Slower and less complete searches; more network traffic
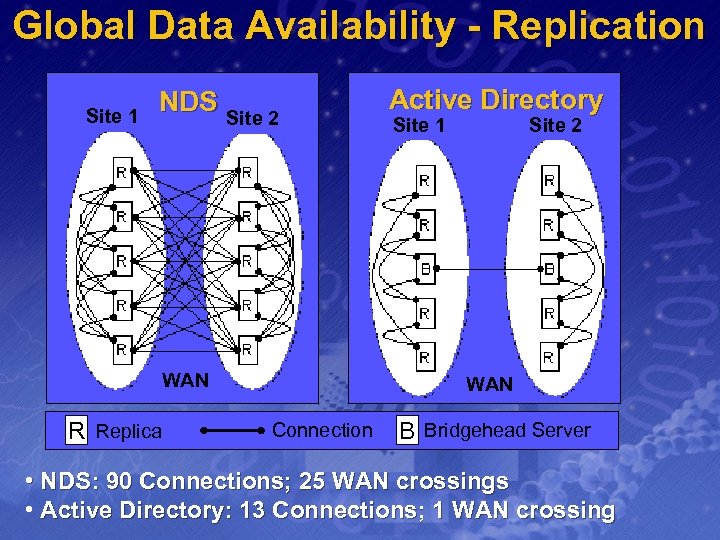 Global Data Availability - Replication Site 1 NDS Site 2 WAN R Replica Active Directory Site 1 Site 2 WAN Connection B Bridgehead Server • NDS: 90 Connections; 25 WAN crossings • Active Directory: 13 Connections; 1 WAN crossing
Global Data Availability - Replication Site 1 NDS Site 2 WAN R Replica Active Directory Site 1 Site 2 WAN Connection B Bridgehead Server • NDS: 90 Connections; 25 WAN crossings • Active Directory: 13 Connections; 1 WAN crossing
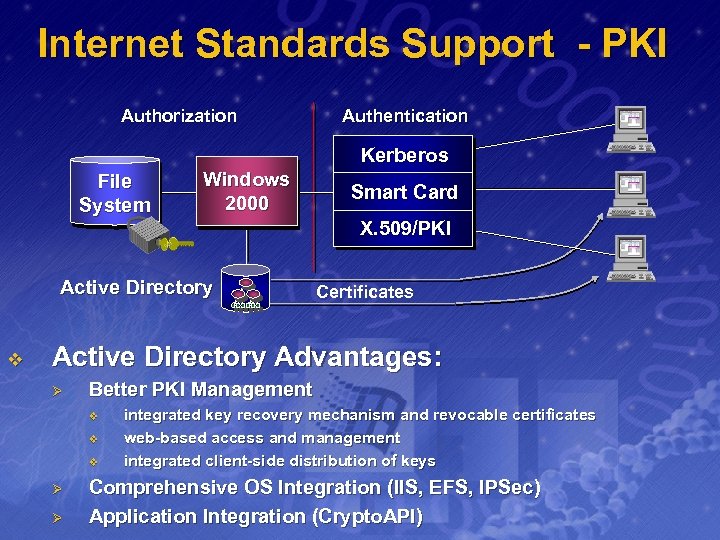 Internet Standards Support - PKI Authorization Authentication Kerberos File System Windows 2000 Smart Card X. 509/PKI Active Directory v Certificates Active Directory Advantages: Ø Better PKI Management v v v Ø Ø integrated key recovery mechanism and revocable certificates web-based access and management integrated client-side distribution of keys Comprehensive OS Integration (IIS, EFS, IPSec) Application Integration (Crypto. API)
Internet Standards Support - PKI Authorization Authentication Kerberos File System Windows 2000 Smart Card X. 509/PKI Active Directory v Certificates Active Directory Advantages: Ø Better PKI Management v v v Ø Ø integrated key recovery mechanism and revocable certificates web-based access and management integrated client-side distribution of keys Comprehensive OS Integration (IIS, EFS, IPSec) Application Integration (Crypto. API)
 Internet Standards Support - Summary v Active Directory Ø Ø Ø v Native LDAP server Full namespace integration with DNS Integrated support for PKI technologies NDS Ø Ø Ø LDAP requests are translated No Namespace Integration with DNS Limited Integration with PKI
Internet Standards Support - Summary v Active Directory Ø Ø Ø v Native LDAP server Full namespace integration with DNS Integrated support for PKI technologies NDS Ø Ø Ø LDAP requests are translated No Namespace Integration with DNS Limited Integration with PKI
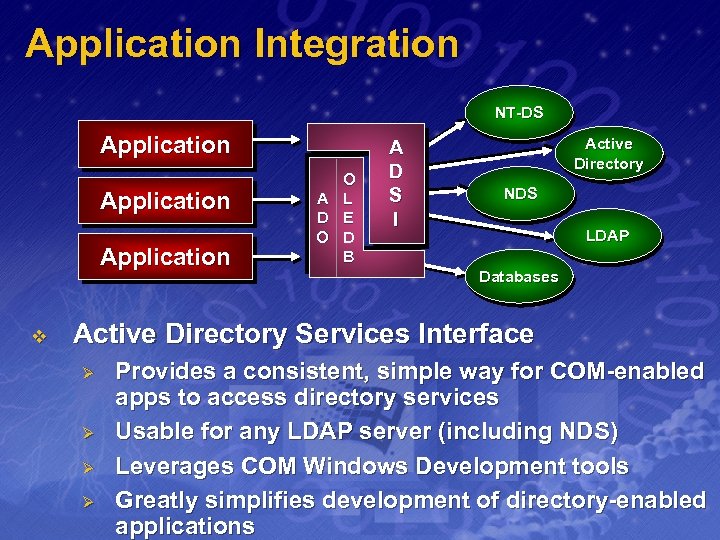 Application Integration NT-DS Application v A D O O L E D B A D S I Active Directory NDS LDAP Databases Active Directory Services Interface Ø Ø Provides a consistent, simple way for COM-enabled apps to access directory services Usable for any LDAP server (including NDS) Leverages COM Windows Development tools Greatly simplifies development of directory-enabled applications
Application Integration NT-DS Application v A D O O L E D B A D S I Active Directory NDS LDAP Databases Active Directory Services Interface Ø Ø Provides a consistent, simple way for COM-enabled apps to access directory services Usable for any LDAP server (including NDS) Leverages COM Windows Development tools Greatly simplifies development of directory-enabled applications
 Application Integration v Active Directory enables powerful directory-enabled applications Ø Ø Ø v Group Policy Integration Service Publication Directory Object Extension ADSI Extension Model Active Directory Class Sore AD-enabled Applications Ø Baan, J. D. Edwards, SAP, Cisco & others Ø Back. Office 2000, MSMQ, MTS and most others
Application Integration v Active Directory enables powerful directory-enabled applications Ø Ø Ø v Group Policy Integration Service Publication Directory Object Extension ADSI Extension Model Active Directory Class Sore AD-enabled Applications Ø Baan, J. D. Edwards, SAP, Cisco & others Ø Back. Office 2000, MSMQ, MTS and most others
 Application Integration - Summary v Windows 2000 & Active Directory Ø Ø Ø v COM, ADSI, Logo programs LDAP-based access to all features Rich Development Environment (VB, C++, Java) Supports Distributed Applications over WANs Large ISV Support: 8, 000+ Windows Applications Net. Ware & NDS Ø Ø Ø ADSI support not available on Net. Ware Incomplete LDAP-based access to NDS features Java-only development environment Partitions limit application functionality Poor ISV Support - Group. Wise not even NDS-enabled
Application Integration - Summary v Windows 2000 & Active Directory Ø Ø Ø v COM, ADSI, Logo programs LDAP-based access to all features Rich Development Environment (VB, C++, Java) Supports Distributed Applications over WANs Large ISV Support: 8, 000+ Windows Applications Net. Ware & NDS Ø Ø Ø ADSI support not available on Net. Ware Incomplete LDAP-based access to NDS features Java-only development environment Partitions limit application functionality Poor ISV Support - Group. Wise not even NDS-enabled
 Active Directory vs. NDS Comparison Active Directory NDS Version 8 Storage technology Max objects/partition Partition Boundary Partition-spanning groups? Same store for catalogs? Catalog update interval Attribute security in catalog? Native LDAP support? Global change LDAP interface? DNS naming integration Integrated PKI support? ADSI provider support? Java Support VB, C, C++ Support Interoperability Tools Indexed Millions Geo/Political Yes Continuous Yes Yes (JADSI) Yes Indexed Millions WAN Not Advised No Scheduled No No No Yes* Yes (JNDI) No No * Not available to Net. Ware applications
Active Directory vs. NDS Comparison Active Directory NDS Version 8 Storage technology Max objects/partition Partition Boundary Partition-spanning groups? Same store for catalogs? Catalog update interval Attribute security in catalog? Native LDAP support? Global change LDAP interface? DNS naming integration Integrated PKI support? ADSI provider support? Java Support VB, C, C++ Support Interoperability Tools Indexed Millions Geo/Political Yes Continuous Yes Yes (JADSI) Yes Indexed Millions WAN Not Advised No Scheduled No No No Yes* Yes (JNDI) No No * Not available to Net. Ware applications
 This document is for informational purposes only. MICROSOFT MAKES NO WARRANTIES, EXPRESS OR IMPLIED, IN THIS DOCUMENT. © 2000 Microsoft Corporation. All rights reserved. Microsoft, Active Directory, Where do you want to go today? , Windows, the Windows logo and Windows NT are either registered trademarks or trademarks of Microsoft Corporation in the United States and/or other countries. The names of actual companies and products mentioned herein may be the trademarks of their respective owners.
This document is for informational purposes only. MICROSOFT MAKES NO WARRANTIES, EXPRESS OR IMPLIED, IN THIS DOCUMENT. © 2000 Microsoft Corporation. All rights reserved. Microsoft, Active Directory, Where do you want to go today? , Windows, the Windows logo and Windows NT are either registered trademarks or trademarks of Microsoft Corporation in the United States and/or other countries. The names of actual companies and products mentioned herein may be the trademarks of their respective owners.



