bd3349de8dfbef7674cace15b1a14ac4.ppt
- Количество слайдов: 23
 Diameter EAP Application (draft-ietf-aaa-eap-02. txt) Jari. Arkko@ericsson. com on behalf of. . . Pasi. Eronen@nokia. com July 16, 2003 1
Diameter EAP Application (draft-ietf-aaa-eap-02. txt) Jari. Arkko@ericsson. com on behalf of. . . Pasi. Eronen@nokia. com July 16, 2003 1
 Outline of the Presentation • • • Part 1: Introduction Part 2: Redirects Part 3: Protocol details Part 4: Security considerations Part 5: Next Steps July 16, 2003 2
Outline of the Presentation • • • Part 1: Introduction Part 2: Redirects Part 3: Protocol details Part 4: Security considerations Part 5: Next Steps July 16, 2003 2
 Part 1: Introduction July 16, 2003 3
Part 1: Introduction July 16, 2003 3
 Introduction • ” 2869 bis plus key AVPs for Diameter” • Scope – One EAP conversation, no role reversal – One NAS, no handoffs or key distribution to multiple NASes – No new NAS-to-home-server security mechanisms, but works end-to-end between the NAS and the home server July 16, 2003 4
Introduction • ” 2869 bis plus key AVPs for Diameter” • Scope – One EAP conversation, no role reversal – One NAS, no handoffs or key distribution to multiple NASes – No new NAS-to-home-server security mechanisms, but works end-to-end between the NAS and the home server July 16, 2003 4
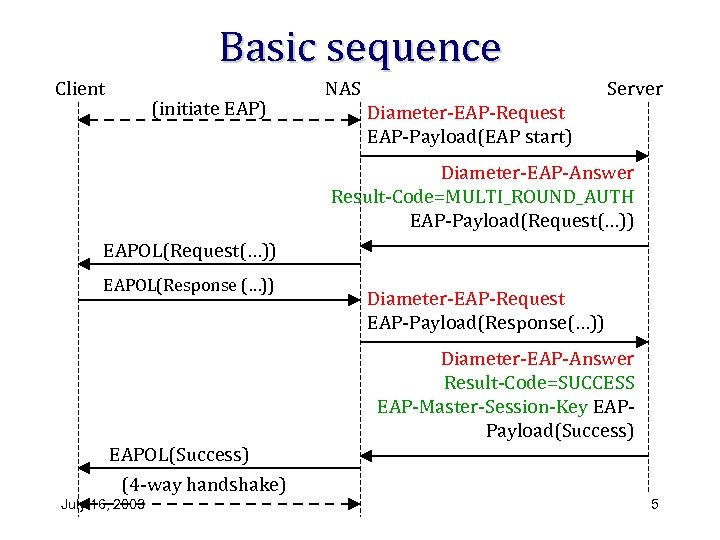 Basic sequence Client (initiate EAP) NAS Server Diameter-EAP-Request EAP-Payload(EAP start) Diameter-EAP-Answer Result-Code=MULTI_ROUND_AUTH EAP-Payload(Request(…)) EAPOL(Response (…)) Diameter-EAP-Request EAP-Payload(Response(…)) Diameter-EAP-Answer Result-Code=SUCCESS EAP-Master-Session-Key EAPPayload(Success) EAPOL(Success) (4 -way handshake) July 16, 2003 5
Basic sequence Client (initiate EAP) NAS Server Diameter-EAP-Request EAP-Payload(EAP start) Diameter-EAP-Answer Result-Code=MULTI_ROUND_AUTH EAP-Payload(Request(…)) EAPOL(Response (…)) Diameter-EAP-Request EAP-Payload(Response(…)) Diameter-EAP-Answer Result-Code=SUCCESS EAP-Master-Session-Key EAPPayload(Success) EAPOL(Success) (4 -way handshake) July 16, 2003 5
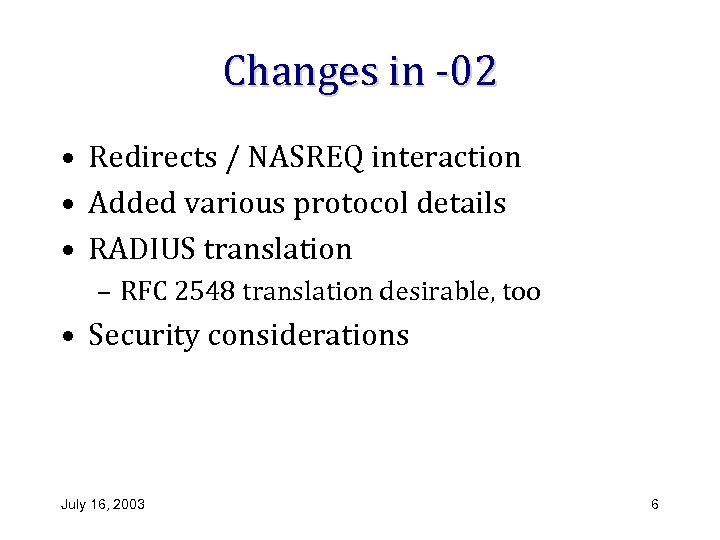 Changes in -02 • Redirects / NASREQ interaction • Added various protocol details • RADIUS translation – RFC 2548 translation desirable, too • Security considerations July 16, 2003 6
Changes in -02 • Redirects / NASREQ interaction • Added various protocol details • RADIUS translation – RFC 2548 translation desirable, too • Security considerations July 16, 2003 6
 Part 2: Redirects July 16, 2003 7
Part 2: Redirects July 16, 2003 7
 Redirects and NASREQ interaction • Without CMS, proxy agents can see the EAP MSK • Solution in – 02 for avoiding proxies: – NAS contacts the home server directly; redirects used if there would otherwise be a proxy – An optional separate request to retrieve authorization AVPs through the proxy chain July 16, 2003 8
Redirects and NASREQ interaction • Without CMS, proxy agents can see the EAP MSK • Solution in – 02 for avoiding proxies: – NAS contacts the home server directly; redirects used if there would otherwise be a proxy – An optional separate request to retrieve authorization AVPs through the proxy chain July 16, 2003 8
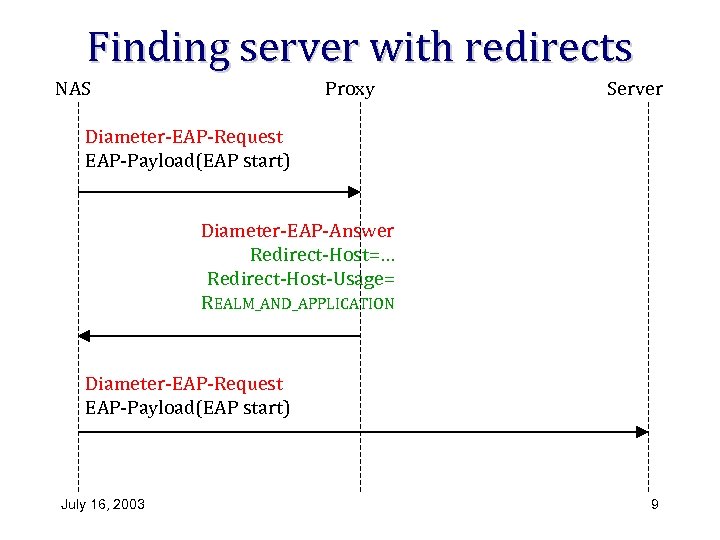 Finding server with redirects NAS Proxy Server Diameter-EAP-Request EAP-Payload(EAP start) Diameter-EAP-Answer Redirect-Host=… Redirect-Host-Usage= REALM_AND_APPLICATION Diameter-EAP-Request EAP-Payload(EAP start) July 16, 2003 9
Finding server with redirects NAS Proxy Server Diameter-EAP-Request EAP-Payload(EAP start) Diameter-EAP-Answer Redirect-Host=… Redirect-Host-Usage= REALM_AND_APPLICATION Diameter-EAP-Request EAP-Payload(EAP start) July 16, 2003 9
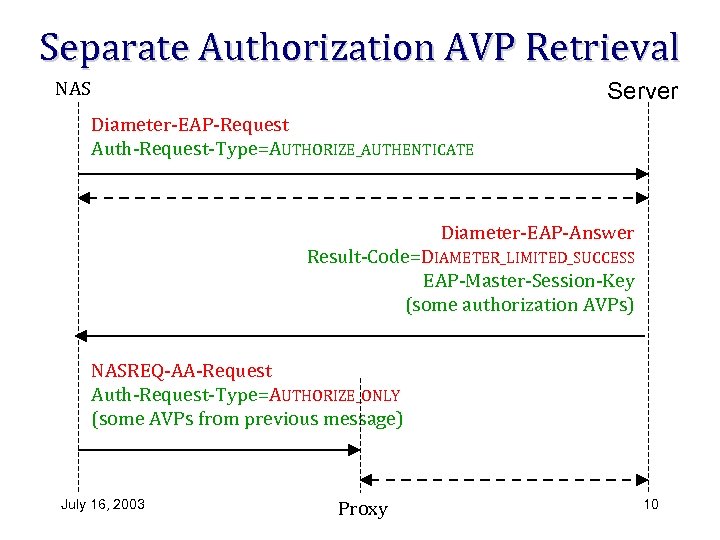 Separate Authorization AVP Retrieval Server NAS Diameter-EAP-Request Auth-Request-Type=AUTHORIZE_AUTHENTICATE Diameter-EAP-Answer Result-Code=DIAMETER_LIMITED_SUCCESS EAP-Master-Session-Key (some authorization AVPs) NASREQ-AA-Request Auth-Request-Type=AUTHORIZE_ONLY (some AVPs from previous message) July 16, 2003 Proxy 10
Separate Authorization AVP Retrieval Server NAS Diameter-EAP-Request Auth-Request-Type=AUTHORIZE_AUTHENTICATE Diameter-EAP-Answer Result-Code=DIAMETER_LIMITED_SUCCESS EAP-Master-Session-Key (some authorization AVPs) NASREQ-AA-Request Auth-Request-Type=AUTHORIZE_ONLY (some AVPs from previous message) July 16, 2003 Proxy 10
 Issues in Redirects • The authorization AVP retrieval uses NASREQ, since Diameter realm routing table isn’t command-specific • Who decides whether the separate proxy pass is needed? • What exactly does a redirect + elimination of proxies buy us? July 16, 2003 12
Issues in Redirects • The authorization AVP retrieval uses NASREQ, since Diameter realm routing table isn’t command-specific • Who decides whether the separate proxy pass is needed? • What exactly does a redirect + elimination of proxies buy us? July 16, 2003 12
 Proxy Elimination + Key is not shown to other parties + Lengthy EAP runs become faster + We authenticate the node on the other side - But untrusted proxies can still misbehave! – Proxy might not send a Redirect – Proxy might send the wrong server’s address => We need additional authorization – Configuration – Attributes in server certs? – NAI realm vs. FQDN in server check July 16, 2003 13
Proxy Elimination + Key is not shown to other parties + Lengthy EAP runs become faster + We authenticate the node on the other side - But untrusted proxies can still misbehave! – Proxy might not send a Redirect – Proxy might send the wrong server’s address => We need additional authorization – Configuration – Attributes in server certs? – NAI realm vs. FQDN in server check July 16, 2003 13
 Diameter authorization • TLS authenticates Diameter nodes, but… • When the NAS talks to foo. example. com, is this actually the server for realm example. com? – – – Local configuration Trust redirect agent Trust DNS Separate CA for servers Certificate name matching (+possibly separate CA) Certificate extensions • When the server gets a connection from bar. example. com, is this a valid access point? – Separate CA for access points – Certificate extensions July 16, 2003 14
Diameter authorization • TLS authenticates Diameter nodes, but… • When the NAS talks to foo. example. com, is this actually the server for realm example. com? – – – Local configuration Trust redirect agent Trust DNS Separate CA for servers Certificate name matching (+possibly separate CA) Certificate extensions • When the server gets a connection from bar. example. com, is this a valid access point? – Separate CA for access points – Certificate extensions July 16, 2003 14
 Part 3: Protocol Details July 16, 2003 15
Part 3: Protocol Details July 16, 2003 15
 Protocol details • • • Invalid packets Fragmentation EAP retransmission Accounting-EAP-Auth-Method EAP-Master-Session-Key July 16, 2003 16
Protocol details • • • Invalid packets Fragmentation EAP retransmission Accounting-EAP-Auth-Method EAP-Master-Session-Key July 16, 2003 16
 Protocol details: Invalid packets • In RADIUS, this message contains a copy of the previous EAP Request, but we don’t want to keep inter-request state • Some alternatives – EAP-Reissued-Payload AVP (instead of EAP-Payload), and normal DIAMETER_MULTI_ROUND_AUTH Result-Code – New DIAMETER_EAP_INVALID_PACKET Result-Code, and normal EAP -Payload AVP – But BASE and NASREQ contain multiple statements like ”if Result-Code is DIAMETER_MULTI_ROUND_AUTH, then…” July 16, 2003 17
Protocol details: Invalid packets • In RADIUS, this message contains a copy of the previous EAP Request, but we don’t want to keep inter-request state • Some alternatives – EAP-Reissued-Payload AVP (instead of EAP-Payload), and normal DIAMETER_MULTI_ROUND_AUTH Result-Code – New DIAMETER_EAP_INVALID_PACKET Result-Code, and normal EAP -Payload AVP – But BASE and NASREQ contain multiple statements like ”if Result-Code is DIAMETER_MULTI_ROUND_AUTH, then…” July 16, 2003 17
 Protocol details: Fragmentation • New AVP: EAP-MTU – Link MTU != max. size of EAP packet – E. g. , IKEv 2 can carry large EAP packets, but the MTU of the IPsec tunnel set up by IKEv 2 is something different • RADIUS translation waiting for clarification of 2869 bis and/or draft-congdon-radius-8021 x July 16, 2003 18
Protocol details: Fragmentation • New AVP: EAP-MTU – Link MTU != max. size of EAP packet – E. g. , IKEv 2 can carry large EAP packets, but the MTU of the IPsec tunnel set up by IKEv 2 is something different • RADIUS translation waiting for clarification of 2869 bis and/or draft-congdon-radius-8021 x July 16, 2003 18
 Protocol details: Accounting-EAP-Auth-Method • How NAS determines the method? – Not specified for MS-Acct-EAP-Type – Proposed solution: server returns it in successful Diameter-EAP-Answer • RFC 2548 has also MS-Acct-Auth-Type – PAP/CHAP/EAP/MS-CHAP-2/etc. – Should we add Accounting-Auth-Method to NASREQ or here? July 16, 2003 19
Protocol details: Accounting-EAP-Auth-Method • How NAS determines the method? – Not specified for MS-Acct-EAP-Type – Proposed solution: server returns it in successful Diameter-EAP-Answer • RFC 2548 has also MS-Acct-Auth-Type – PAP/CHAP/EAP/MS-CHAP-2/etc. – Should we add Accounting-Auth-Method to NASREQ or here? July 16, 2003 19
 Protocol details: EAP-Master-Session-Key • Simple AVP (Octet. String) • Can be translated to MS-MPPE-* • But EAP WG is discussing key naming! We may need more AVPs July 16, 2003 20
Protocol details: EAP-Master-Session-Key • Simple AVP (Octet. String) • Can be translated to MS-MPPE-* • But EAP WG is discussing key naming! We may need more AVPs July 16, 2003 20
 Part 4: Security Considerations July 16, 2003 21
Part 4: Security Considerations July 16, 2003 21
 Security considerations: System perspective EAP 802. 11 Diameter • No document contains security considerations for the whole system? – Gets even more complex if we have handoffs or key distribution to multiple NASes – (May require changes not just to all three components, but to interfaces between them) July 16, 2003 22
Security considerations: System perspective EAP 802. 11 Diameter • No document contains security considerations for the whole system? – Gets even more complex if we have handoffs or key distribution to multiple NASes – (May require changes not just to all three components, but to interfaces between them) July 16, 2003 22
 Part 5: Next Steps July 16, 2003 23
Part 5: Next Steps July 16, 2003 23
 Next steps • Very much dependent on EAP keying framework security discussion & Russ’ requirements from IETF-56 – Finish that discussion first • Identify other issues that still need work – Comments really welcome! • Finish document – Keep current scope July 16, 2003 24
Next steps • Very much dependent on EAP keying framework security discussion & Russ’ requirements from IETF-56 – Finish that discussion first • Identify other issues that still need work – Comments really welcome! • Finish document – Keep current scope July 16, 2003 24


