9b10c3594e04325f94edfe962326e30c.ppt
- Количество слайдов: 39

Dialog Attack Sniffing – Spoofing Session Hijacking Isbat Uzzin Nadhori Informatical Engineering PENS-ITS Politeknik Elektronika Negeri Surabaya ITS - Surabaya 1
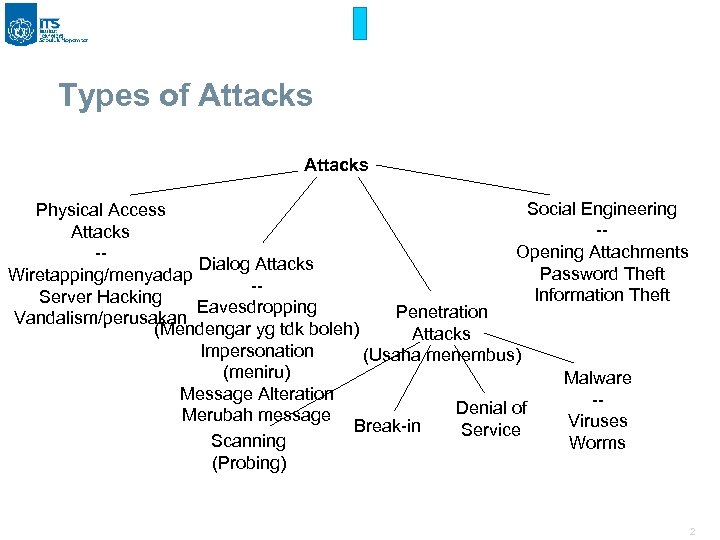
Types of Attacks Social Engineering Physical Access -Attacks Opening Attachments -Dialog Attacks Password Theft Wiretapping/menyadap -Information Theft Server Hacking Eavesdropping Penetration Vandalism/perusakan (Mendengar yg tdk boleh) Attacks Impersonation (Usaha menembus) (meniru) Malware Message Alteration -Denial of Merubah message Viruses Break-in Service Scanning Worms (Probing) 2
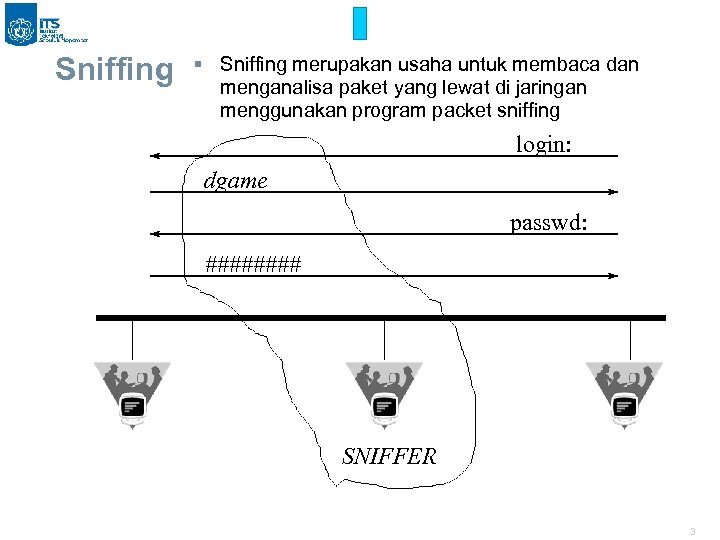
Sniffing § Sniffing merupakan usaha untuk membaca dan menganalisa paket yang lewat di jaringan menggunakan program packet sniffing login: dgame passwd: #### SNIFFER 3

Major Problems with Sniffing § Any mischievious machine can examine any packet on a BROADCAST medium § Ethernet is BROADCAST at least on the segments over which it travels § Getting passwords is the first step in exploiting a machine § email is plaintext and vulnerable 4

What does one sniff? § passwords § email § financial account information § confidential information § low-level protocol info to attack hardware addresses IP addresses routing, etc 5
Spoofing § In spoofing (fooling, deceiving), an attacker impersonates someone else. 6
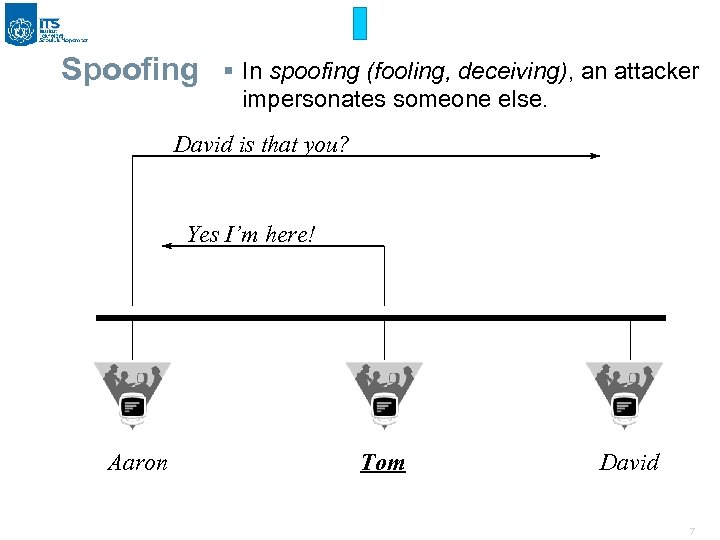
Spoofing § In spoofing (fooling, deceiving), an attacker impersonates someone else. David is that you? Yes I’m here! Aaron Tom David 7
Type of Spoofing § ARP Spoofing / MAC Spoofing Attacker change MAC address client with MAC Address Attacker § IP spoofing Attacker uses IP address of another computer to acquire information or gain access § Email spoofing Attacker sends email but makes it appear to come from someone else § Web spoofing Attacker tricks web browser into communicating with a different web server than the user intended. § Non-network (social engineering) 8

MAC level Spoofing § Focus on ethernet (widespread use) § Cards have unique addresses at manufacturer § Many cards CAN be reconfigured by user bridge has no MAC address but sends with source address of the originator § faking address has opportunity for mischief 9
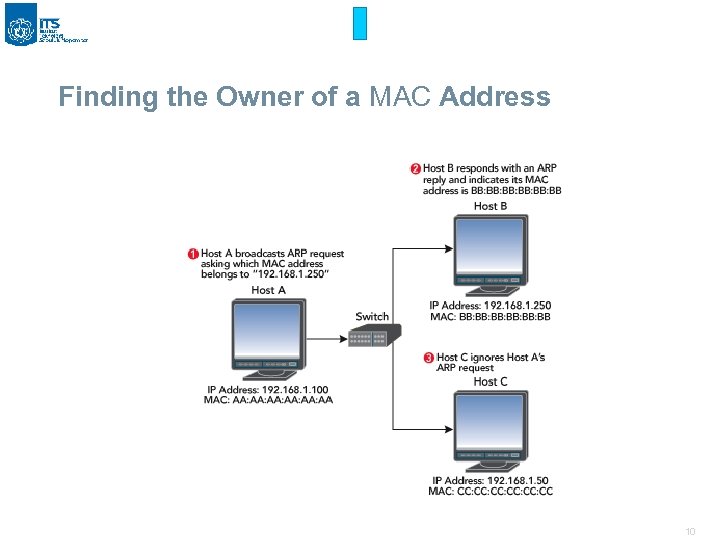
Finding the Owner of a MAC Address 10
ARP Table Modifications § However Host A doesn’t know that Host B really did send the ARP reply. § In the previous example, attackers could spoof an ARP reply to Host A before Host B responded, indicating that the hardware address E 0: E 0: E 0 corresponds to Host B's IP address. Host A would then send any traffic intended for Host B to the attacker, and the attacker could choose to forward that data (probably after some tampering) to Host B. 11
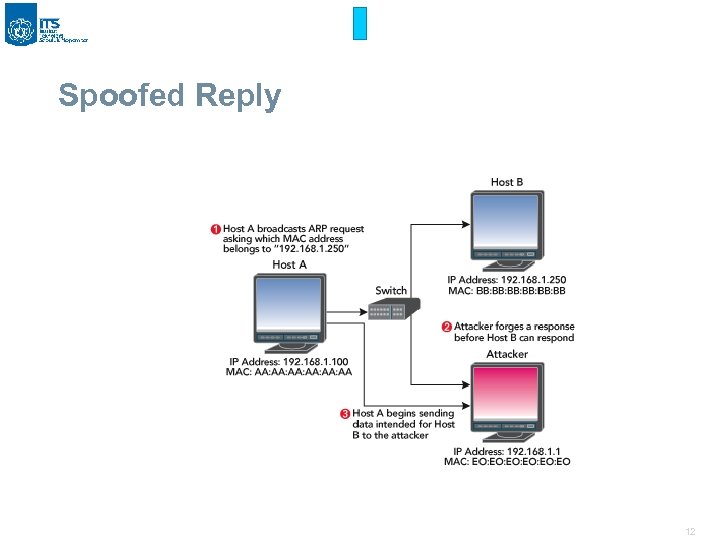
Spoofed Reply 12

ARP spoofing § What is ARP? IP->MAC mapping § Make some machine think that the IP address it is searching for is you. § How it works: Broadcast and ask if anyone knows Response is typically from that IP 13

ARP spoofing (more) § If 2 machines (real and fake) respond, effect depends on OS some OS overwrite earlier response other OS ignore unless it’s current entry expires § Original can be disconnected by Power Wiring (connectivity) 14

IP Spoofing § IP spoofing is the creation of TCP/IP packets with somebody else's IP address in the header. § Routers use the destination IP address to forward packets, but ignore the source IP address. § The source IP address is used only by the destination machine, when it responds back to the source. § When an attacker spoofs someone’s IP address, the victim’s reply goes back to that address. § Since the attacker does not receive packets back, this is called a one-way attack or blind spoofing. 15
Email Spoofing § 3 Basic way to perform : – Aliasing – Modify mail client – Telnet to port 25 16
Email Spoofing § One simple form of email spoofing is to create a valid email account (on yahoo or hotmail) and put someone else’s name in the alias field. § In mail relaying, an attacker uses a mail server to send mail to someone in a different domain § When email is sent by a user, the From: address is not validated. 17
Web Spoofing § One way to lure people to a malicious site is to give it a URL that is similar to that of a legitimate site, e. g. , www. paypai. com www. First. National. Bank. com § Another way is for the attacker to provide HTML with a mislabeled link to another page, e. g. , in an email. Example: <a HREF="http: //www. badhack. org"> American Red Cross</a> 18

Fake url § that is, sites claiming to be a particular Web site but, when clicked on, actually link to a hacker's Web site. The URL is the Web address for any Web site § There are some clues in it that may indicate it will lead you to a fake or a phishing site. Defence : – One of the first rules of online security is to exercise caution at all times. Try to avoid clicking on links in pop-up ads or links in emails that seem to be phony or suspicious. A good general rule is to type the Web site address in your address bar directly, rather than use a link in an email message, especially if you are going to a financial site. – You can check the URL in any email or on another Web site by simply holding your mouse above the link. The URL will appear in your browser or status bar (the bar that is usually at the bottom of your screen) and you can see what the name of the site is before you actually click on it. – A fairly sure sign that a URL is fake is if the URL contains the "@" sign in the middle of the address. If a URL contains the "@" sign, the browser ignores everything to the left of the link. For example, if you go to a Web site that is www. paypal@150. 44. 134. 189, you are not going to the Paypal site at all. Legitimate sites and companies use a domain name as part of their name rather than the "@" sign. – A dead giveaway for a fake URL or a fake Web site is basic spelling mistakes in the Web address itself. Some URLs look very much like the name of a well-known company, but there may be letters transposed or left out. An example might be "mircosoft. com" instead of "microsoft. com. " These slight differences can be easy to miss, and that's what phishers are counting on. – The popular Paypal site is a common target for phishers and scammers. Even if a URL contains the word "paypal, " it may not be the authentic Paypal site. Some common URLs that will NOT lead you to the real Paypal site are: www. paypalsecure. com and www. paypal@accounts. com. 19
TCP Session Hijacking § TCP session hijacking is when a hacker takes over a TCP session between two machines. § Since most authentication only occurs at the start of a TCP session, this allows the hacker to gain access to a machine. 20

Categories of TCP Session Hijacking § Based on the anticipation of sequence numbers there are two types of TCP hijacking: Man-in-the-middle (MITM) Blind Hijack 21

Passive Sniffers § Passive sniffers monitors and sniffs packet from a network having same collision domain (i. e. network with a hub, as all packets are broadcasted on each port of hub. ) 22

Active Sniffers § One way of doing so is to change the default gateway of the client’s machine so that it will route its packets via the hijacker’s machine. § This can be done by ARP spoofing (i. e. by sending malicious ARP packets mapping its MAC address to the default gateways IP address so as to update the ARP cache on the client, to redirect the traffic to hijacker). 23
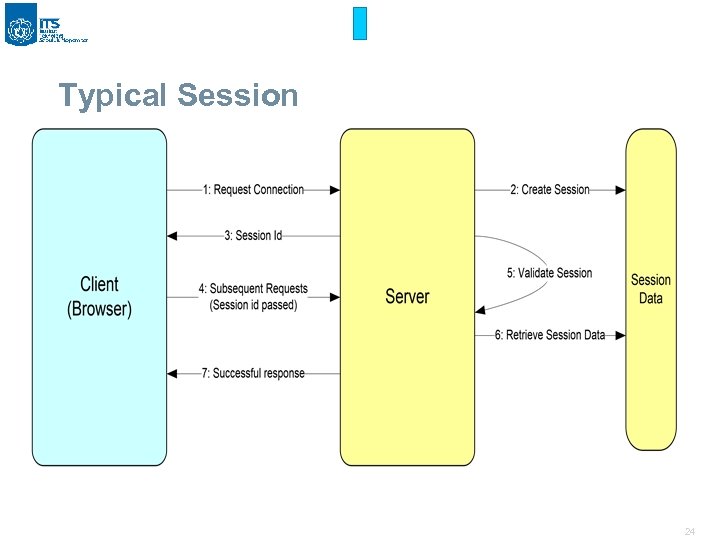
Typical Session 24

Attack Methods § Guessing Session Id shorter length, predictable § Session Fixing predictable, session created before authenticated § Security Vulnerabilities in Hops trusting private networks, vulnerabilites in web servers, etc § Session Sniffing (typical on non SSL sessions) same subnet as client or server § Man in the Middle Attack (SSL) ARP Poisoning, DNS Spoofing § Cross Site Scripting (XSS) User trusting source, application vulnerability 25
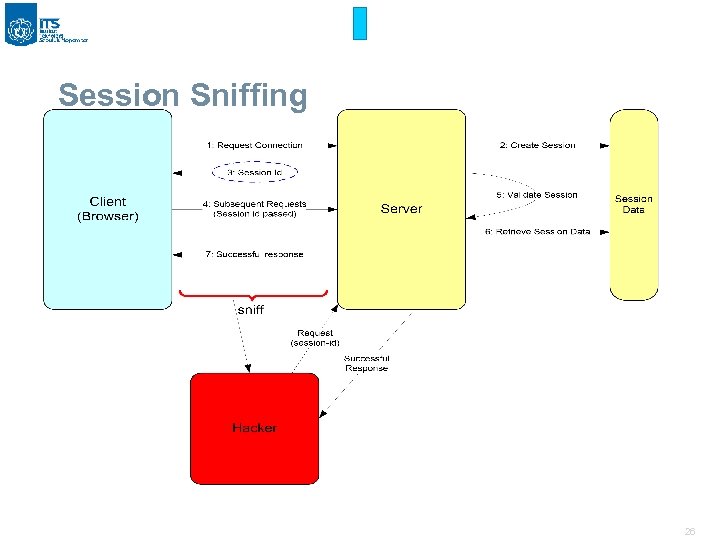
Session Sniffing 26

Man-in-the-middle (MITM) § A hacker can also be "inline" between B and C using a sniffing program to watch the sequence numbers and acknowledge numbers in the IP packets transmitted between B and C. And then hijack the connection. § This is known as a "man-in-the-middle attack". 27

Man in the Middle Attack Using Packet Sniffers § This technique involves using a packet sniffer to intercept the communication between client and the server. § Packet sniffer comes in two categories: Active sniffers Passive sniffers. 28
![Blind Hijacking [Shray Kapoor] § If you are NOT able to sniff the packets Blind Hijacking [Shray Kapoor] § If you are NOT able to sniff the packets](https://present5.com/presentation/9b10c3594e04325f94edfe962326e30c/image-29.jpg)
Blind Hijacking [Shray Kapoor] § If you are NOT able to sniff the packets and guess the correct sequence number expected by server, you have to implement “Blind Session Hijacking. ’’ § You have to brute force 4 billion combinations of sequence number which will be an unreliable task. 29

Ways to Suppress a Hijacked Host to Send Packets § A common way is to execute a Denial-of-Service (Do. S) attack against one end-point to stop it from responding. This attack can be either against the machine to force it to crash or against the network connection to force heavy packet loss. § Send packets with commands that request the recipient not to send back response. 30
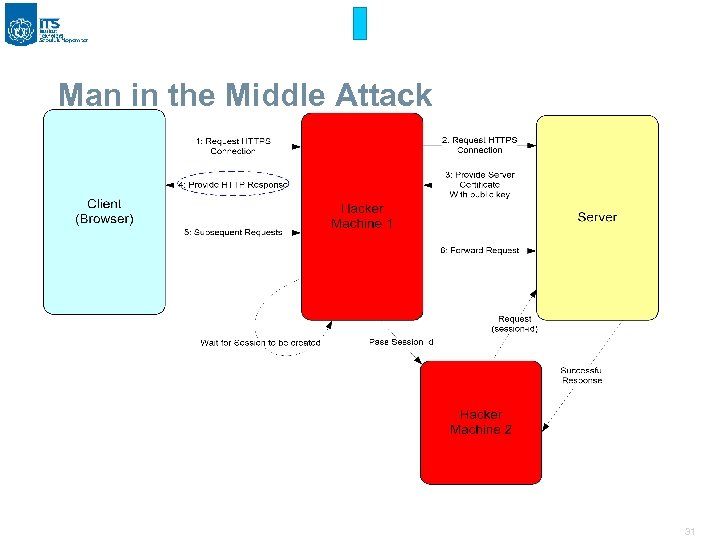
Man in the Middle Attack 31

Mit. M Attacks § ‘Man-in-the-Middle’ refers to a machine that is set up so that traffic between two other machines must pass through the Mit. M machine. § Difficult to setup, especially over the Internet. Not so difficult in a LAN environment. § Provides no additional advantages over a ‘sniffer’ – is actually just a way to implement a sniffer. § Defense: Encryption – however, Mit. M can refer to an intermediate encrypter Strong perimeter security for Internet Mit. M attacks. Only secure as the weakest link – the Mit. M can attack from either end. So, even if you have strong security, but your partner does not, the Mit. M is possible from the other end. 32

Prevention of Sniffing § Segmentation into trustworthy segments bridges better yet. . switched hubs § Not enough “not to allow sniffing” easy to add a machine on the net may try using X-terminals vs workstations 33

Prevention of Sniffing(more) § Avoid password transmission one solution is r. . family rlogin, rcp, rsh, etc put trusted hosts in. rhosts many SAs don’t want users to use them § Using encrypted passwords Kerberos PGP public keys 34

Prevention MAC spoofing § VERY difficult § Intelligent hubs can be made to expect certain MACs on ports but machines can still be swapped § physical measures 35

Prevention of ARP spoofing § Basic Premise: ARP TRUSTS RESPONSE § If the machine is one you need to trust: make a PERMANENT entry in arp cache arp -p. . . § Use an arp server Don’t let the machine respond for itself make administration a little more cumbersone but is probably worth it! but. . server can be spoofed 36

Countermeasure § IP Spoofing Protect against with good firewall rules – keep your machines from launching a spoofed IP – router filters Limit configuration access on machines Programs like arpwatch that keep track of IP/MAC pairings The best way to protect against source routing spoofing is to simply disable source routing at your routers. § Email Spoofing Most email servers today do not allow email relaying. They only allow emails to be sent to/from their range of IP addresses. They insure that the recipient’s domain is the same domain as the mail server. The attacker can run his own email server, but then he is easier to trace. Defense - Do not allow Email relaying on your STMP servers § Web Spoofing Use a ‘server-side certificate’. Still, users should Examine the browser location/status line Examine links in HTML source code. Disable “active” content (Java, Java. Script, Active X) in the browser. Ensure that your browser starts on a “secure page” (a local HTML page) 37

Countermeasures - Encryption § The most effective is encryption such as IPSec. Internet Protocol Security has the ability to encrypt your IP packets based on a Pre-Shared Key or with more complex systems like a Public Key Infrastructure PKI. This will also defend against many other attack vectors such as sniffing. The attacker may be able to passively monitor your connection, but they will not be able to read any data as it is all encrypted. There might be actions an attacker could take against an IPSec enabled network, depending on if they use IKE-PSK or PKI to manage the encryption keys, but this would require an experienced hacker. Don’t think that IPSec is the panacea to all your ills, there are IPSec cracking tools available on the internet that will attempt to guess the PSK and decrypt packets. 38
Countermeasures – Encrypted Application § Other countermeasures include encrypted applications like ssh (Secure SHell, an encrypted telnet) or ssl (Secure Sockets Layer, HTTPS traffic). Again this reflects back to using encryption, but a subtle difference being that you are using the encryption within an application. Be aware though that there are known attacks against ssh and ssl. OWA, Outlook Web Access uses ssl to encrypt data between an internet client browser and the Exchange mail server, but tools like Cain & Abel can spoof the ssl certificate and mount a Man-In-The-Middle (MITM) attack and decrypt everything! 39
9b10c3594e04325f94edfe962326e30c.ppt