e1383e3580186699f7db88514f8505a7.ppt
- Количество слайдов: 49
 Device. Lock 7. 0 Endpoint DLP Full Introduction for Partners
Device. Lock 7. 0 Endpoint DLP Full Introduction for Partners
 www. devicelock. com CONFIDENTIAL Agenda } } } Company Brief The Data Leakage Problem Device. Lock Solution Content Filtering Network Communications Control Device. Lock 7. 0 – The Basic Component w Pre-7. 0 Fundamentals w New Capabilities } Licensing } Product Positioning & Value for Partners } Messaging for Customers www. devicelock. com 2 2
www. devicelock. com CONFIDENTIAL Agenda } } } Company Brief The Data Leakage Problem Device. Lock Solution Content Filtering Network Communications Control Device. Lock 7. 0 – The Basic Component w Pre-7. 0 Fundamentals w New Capabilities } Licensing } Product Positioning & Value for Partners } Messaging for Customers www. devicelock. com 2 2
 www. devicelock. com CONFIDENTIAL Company Brief DEVICELOCK, INC. www. devicelock. com 3 3
www. devicelock. com CONFIDENTIAL Company Brief DEVICELOCK, INC. www. devicelock. com 3 3
 www. devicelock. com CONFIDENTIAL Company Facts } Device. Lock, Inc. established as Smart. Line in 1996 } Develops and markets Device. Lock® software w Endpoint device control and data leak prevention solution } Leader of Device/Port Control niche w 60, 000 corporate customers worldwide w 4 M+ computers protected by Device. Lock } Offices in Russia (HQs, R&D), USA, UK, Germany, Italy w About 60 full-time employees including 30+ in R&D } Privately owned, self-funded, dynamically growing www. devicelock. com 4 4
www. devicelock. com CONFIDENTIAL Company Facts } Device. Lock, Inc. established as Smart. Line in 1996 } Develops and markets Device. Lock® software w Endpoint device control and data leak prevention solution } Leader of Device/Port Control niche w 60, 000 corporate customers worldwide w 4 M+ computers protected by Device. Lock } Offices in Russia (HQs, R&D), USA, UK, Germany, Italy w About 60 full-time employees including 30+ in R&D } Privately owned, self-funded, dynamically growing www. devicelock. com 4 4
 www. devicelock. com CONFIDENTIAL Device. Lock Customers } Historically, due to higher data security concerns, most customers came from Financial, Government, Defense Contractor, Health Care, Bio-Tech, High-Tech Manufacturing, Education, and Gambling Resorts & Casinos verticals } Recently, various organizations regardless of vertical industry, size, network topology, geography… } One of the world’s largest mutual fund groups (in US), City of London Police, SAIC, Societe Generale, BAE Systems, Central Bank of Russia, Lukoil, Savings Bank of Russia, VTB 24 Bank, … w See case studies at Device. Lock web-site } Major production installation 70, 000+ seats (in US) www. devicelock. com 5 5
www. devicelock. com CONFIDENTIAL Device. Lock Customers } Historically, due to higher data security concerns, most customers came from Financial, Government, Defense Contractor, Health Care, Bio-Tech, High-Tech Manufacturing, Education, and Gambling Resorts & Casinos verticals } Recently, various organizations regardless of vertical industry, size, network topology, geography… } One of the world’s largest mutual fund groups (in US), City of London Police, SAIC, Societe Generale, BAE Systems, Central Bank of Russia, Lukoil, Savings Bank of Russia, VTB 24 Bank, … w See case studies at Device. Lock web-site } Major production installation 70, 000+ seats (in US) www. devicelock. com 5 5
 www. devicelock. com CONFIDENTIAL The Data Leakage Problem DEVICELOCK 7. 0 ENDPOINT DLP SUITE www. devicelock. com 6 6
www. devicelock. com CONFIDENTIAL The Data Leakage Problem DEVICELOCK 7. 0 ENDPOINT DLP SUITE www. devicelock. com 6 6
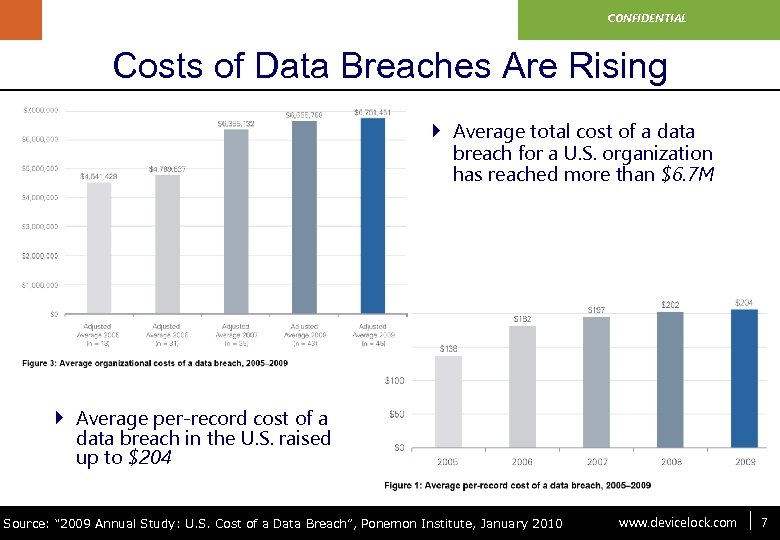 www. devicelock. com CONFIDENTIAL Costs of Data Breaches Are Rising } Average total cost of a data breach for a U. S. organization has reached more than $6. 7 M } Average per-record cost of a data breach in the U. S. raised up to $204 Source: “ 2009 Annual Study: U. S. Cost of a Data Breach”, Ponemon Institute, January 2010 www. devicelock. com 7 7
www. devicelock. com CONFIDENTIAL Costs of Data Breaches Are Rising } Average total cost of a data breach for a U. S. organization has reached more than $6. 7 M } Average per-record cost of a data breach in the U. S. raised up to $204 Source: “ 2009 Annual Study: U. S. Cost of a Data Breach”, Ponemon Institute, January 2010 www. devicelock. com 7 7
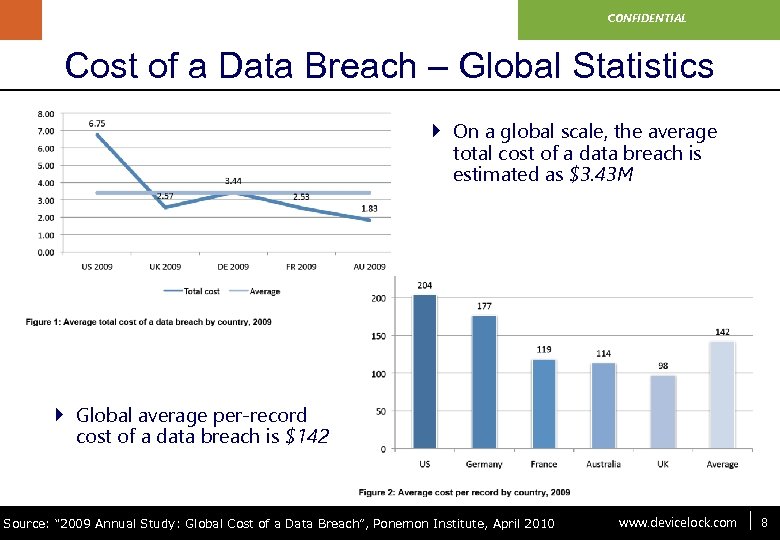 www. devicelock. com CONFIDENTIAL Cost of a Data Breach – Global Statistics } On a global scale, the average total cost of a data breach is estimated as $3. 43 M } Global average per-record cost of a data breach is $142 Source: “ 2009 Annual Study: Global Cost of a Data Breach”, Ponemon Institute, April 2010 www. devicelock. com 8 8
www. devicelock. com CONFIDENTIAL Cost of a Data Breach – Global Statistics } On a global scale, the average total cost of a data breach is estimated as $3. 43 M } Global average per-record cost of a data breach is $142 Source: “ 2009 Annual Study: Global Cost of a Data Breach”, Ponemon Institute, April 2010 www. devicelock. com 8 8
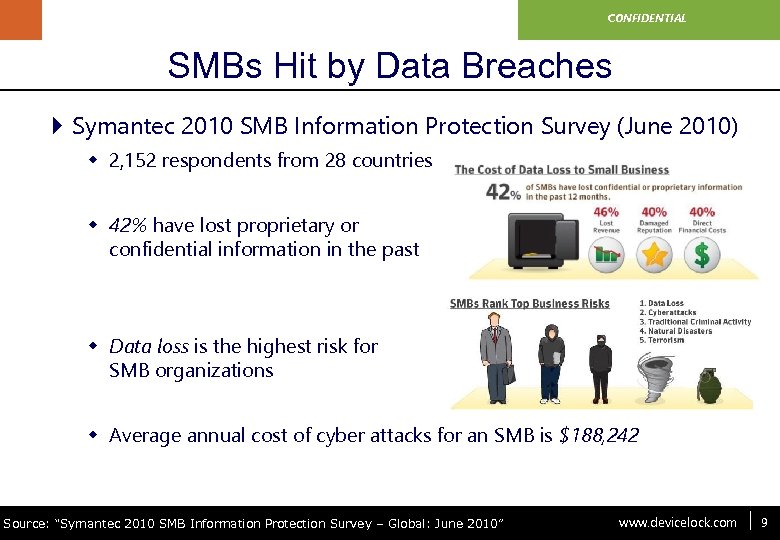 www. devicelock. com CONFIDENTIAL SMBs Hit by Data Breaches } Symantec 2010 SMB Information Protection Survey (June 2010) w 2, 152 respondents from 28 countries w 42% have lost proprietary or confidential information in the past w Data loss is the highest risk for SMB organizations w Average annual cost of cyber attacks for an SMB is $188, 242 Source: “Symantec 2010 SMB Information Protection Survey – Global: June 2010” www. devicelock. com 9 9
www. devicelock. com CONFIDENTIAL SMBs Hit by Data Breaches } Symantec 2010 SMB Information Protection Survey (June 2010) w 2, 152 respondents from 28 countries w 42% have lost proprietary or confidential information in the past w Data loss is the highest risk for SMB organizations w Average annual cost of cyber attacks for an SMB is $188, 242 Source: “Symantec 2010 SMB Information Protection Survey – Global: June 2010” www. devicelock. com 9 9
 www. devicelock. com CONFIDENTIAL More Stringent Data Protection Laws } Forty six states in the US have already enacted data breach notification laws } In the UK, since of April 2010 the Information Commissioner’s Office can fine organizations up to £ 500, 000 as a penalty for breaches of the Data Protection Act } In EU, data breach notifications will become obligatory for a wide range of businesses w In January 2010, European Commission announced the start of data protection law improvement process www. devicelock. com 10 10
www. devicelock. com CONFIDENTIAL More Stringent Data Protection Laws } Forty six states in the US have already enacted data breach notification laws } In the UK, since of April 2010 the Information Commissioner’s Office can fine organizations up to £ 500, 000 as a penalty for breaches of the Data Protection Act } In EU, data breach notifications will become obligatory for a wide range of businesses w In January 2010, European Commission announced the start of data protection law improvement process www. devicelock. com 10 10
 www. devicelock. com CONFIDENTIAL Local Leaks Prevail } Most methods leaving employees used for taking away corporate data relate to local ports and peripheral devices of endpoint computers } Number of local leak cases far outweighs other ways of stealing data Source: “Data Loss Risks During Downsizing”, Ponemon Institute, February 2009 www. devicelock. com 11 11
www. devicelock. com CONFIDENTIAL Local Leaks Prevail } Most methods leaving employees used for taking away corporate data relate to local ports and peripheral devices of endpoint computers } Number of local leak cases far outweighs other ways of stealing data Source: “Data Loss Risks During Downsizing”, Ponemon Institute, February 2009 www. devicelock. com 11 11
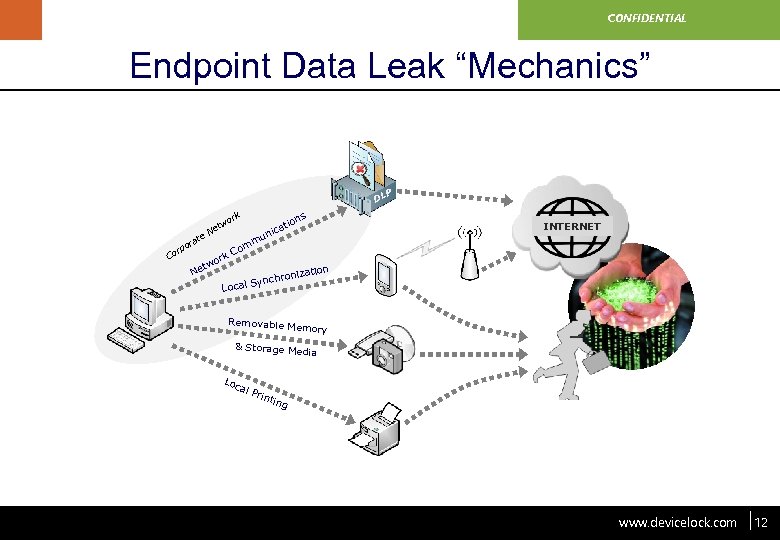 www. devicelock. com CONFIDENTIAL Endpoint Data Leak “Mechanics” P DL k or w et N te a or rp Co t Ne rk wo C tio ica un m om ns INTERNET tion roniza Synch Local Removable Memory & Storage M edia Loc a l Pr inti ng www. devicelock. com 12 12
www. devicelock. com CONFIDENTIAL Endpoint Data Leak “Mechanics” P DL k or w et N te a or rp Co t Ne rk wo C tio ica un m om ns INTERNET tion roniza Synch Local Removable Memory & Storage M edia Loc a l Pr inti ng www. devicelock. com 12 12
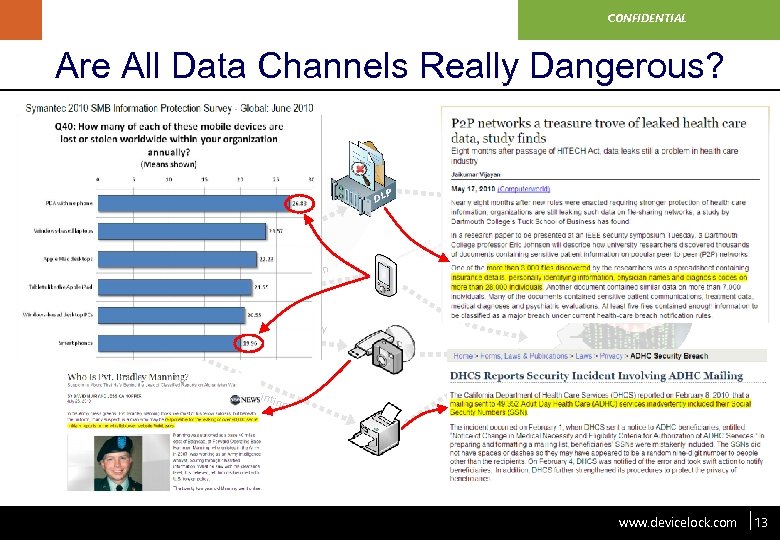 www. devicelock. com CONFIDENTIAL Are All Data Channels Really Dangerous? P DL k or w et N te a or rp Co t Ne rk wo C tio ica un m om ns INTERNET tion roniza Synch Local Removable Mem ory & Storage Med ia Loc a l Pr inti ng www. devicelock. com 13 13
www. devicelock. com CONFIDENTIAL Are All Data Channels Really Dangerous? P DL k or w et N te a or rp Co t Ne rk wo C tio ica un m om ns INTERNET tion roniza Synch Local Removable Mem ory & Storage Med ia Loc a l Pr inti ng www. devicelock. com 13 13
 www. devicelock. com CONFIDENTIAL Device. Lock Solution DEVICELOCK 7. 0 ENDPOINT DLP SUITE www. devicelock. com 14 14
www. devicelock. com CONFIDENTIAL Device. Lock Solution DEVICELOCK 7. 0 ENDPOINT DLP SUITE www. devicelock. com 14 14
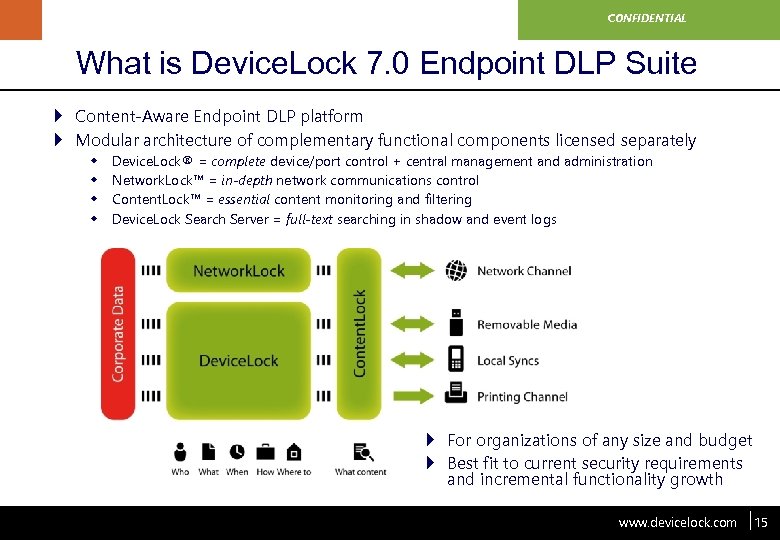 www. devicelock. com CONFIDENTIAL What is Device. Lock 7. 0 Endpoint DLP Suite } Content-Aware Endpoint DLP platform } Modular architecture of complementary functional components licensed separately w w Device. Lock® = complete device/port control + central management and administration Network. Lock™ = in-depth network communications control Content. Lock™ = essential content monitoring and filtering Device. Lock Search Server = full-text searching in shadow and event logs } For organizations of any size and budget } Best fit to current security requirements and incremental functionality growth www. devicelock. com 15 15
www. devicelock. com CONFIDENTIAL What is Device. Lock 7. 0 Endpoint DLP Suite } Content-Aware Endpoint DLP platform } Modular architecture of complementary functional components licensed separately w w Device. Lock® = complete device/port control + central management and administration Network. Lock™ = in-depth network communications control Content. Lock™ = essential content monitoring and filtering Device. Lock Search Server = full-text searching in shadow and event logs } For organizations of any size and budget } Best fit to current security requirements and incremental functionality growth www. devicelock. com 15 15
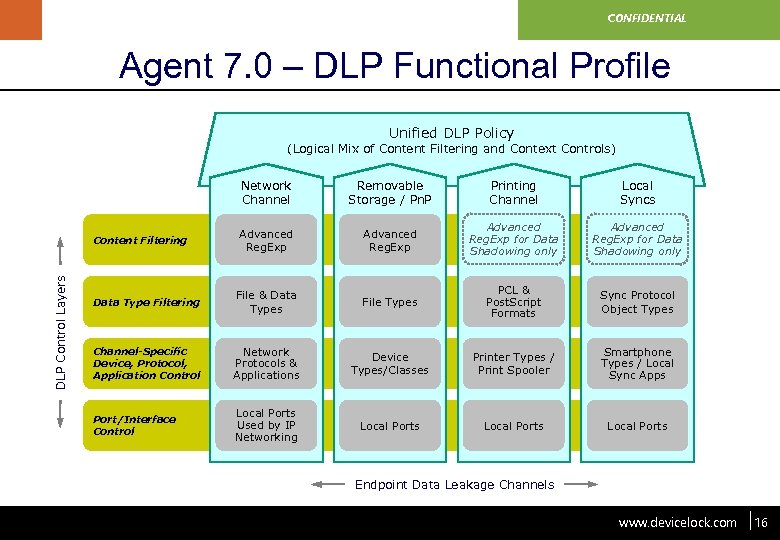 www. devicelock. com CONFIDENTIAL Agent 7. 0 – DLP Functional Profile Unified DLP Policy (Logical Mix of Content Filtering and Context Controls) Network Channel Removable Storage / Pn. P Printing Channel Local Syncs Advanced Reg. Exp for Data Shadowing only Data Type Filtering File & Data Types File Types PCL & Post. Script Formats Sync Protocol Object Types Channel-Specific Device, Protocol, Application Control Network Protocols & Applications Device Types/Classes Printer Types / Print Spooler Smartphone Types / Local Sync Apps Port/Interface Control Local Ports Used by IP Networking Local Ports DLP Control Layers Content Filtering Endpoint Data Leakage Channels Confidential www. devicelock. com 16 16
www. devicelock. com CONFIDENTIAL Agent 7. 0 – DLP Functional Profile Unified DLP Policy (Logical Mix of Content Filtering and Context Controls) Network Channel Removable Storage / Pn. P Printing Channel Local Syncs Advanced Reg. Exp for Data Shadowing only Data Type Filtering File & Data Types File Types PCL & Post. Script Formats Sync Protocol Object Types Channel-Specific Device, Protocol, Application Control Network Protocols & Applications Device Types/Classes Printer Types / Print Spooler Smartphone Types / Local Sync Apps Port/Interface Control Local Ports Used by IP Networking Local Ports DLP Control Layers Content Filtering Endpoint Data Leakage Channels Confidential www. devicelock. com 16 16
 www. devicelock. com CONFIDENTIAL Content Filtering DEVICELOCK 7. 0 ENDPOINT DLP SUITE www. devicelock. com 17 17
www. devicelock. com CONFIDENTIAL Content Filtering DEVICELOCK 7. 0 ENDPOINT DLP SUITE www. devicelock. com 17 17
 www. devicelock. com CONFIDENTIAL Content Filtering: Where and What } Controlled data channels w Removable media (Content. Lock) w Other Pn. P storage devices (Content. Lock) w Network channel (Content. Lock + Network. Lock) } Data and file format agnostic textual content extraction w 80+ file formats w Emails (messages and attachments) w Webmails and web-forms w Instant messages w Social network exchanges w Telnet data www. devicelock. com 18 18
www. devicelock. com CONFIDENTIAL Content Filtering: Where and What } Controlled data channels w Removable media (Content. Lock) w Other Pn. P storage devices (Content. Lock) w Network channel (Content. Lock + Network. Lock) } Data and file format agnostic textual content extraction w 80+ file formats w Emails (messages and attachments) w Webmails and web-forms w Instant messages w Social network exchanges w Telnet data www. devicelock. com 18 18
 www. devicelock. com CONFIDENTIAL Content Filtering: How } Advanced Regular Expression patterns with numerical conditions w Boolean combination of matching criteria § ({regexp("b(?
www. devicelock. com CONFIDENTIAL Content Filtering: How } Advanced Regular Expression patterns with numerical conditions w Boolean combination of matching criteria § ({regexp("b(?
 www. devicelock. com CONFIDENTIAL Content-Aware Data Shadowing } For all endpoint data channels w w w Removable and Pn. P storage devices Network communications Local synchronizations with smartphones Document printing Clipboard copy/paste operations } Content-filtered w All 80+ supported file formats and data objects w PCL and Postscript printouts } Tremendously reduces w Storage space requirements and w Network bandwidth consumption www. devicelock. com 20 20
www. devicelock. com CONFIDENTIAL Content-Aware Data Shadowing } For all endpoint data channels w w w Removable and Pn. P storage devices Network communications Local synchronizations with smartphones Document printing Clipboard copy/paste operations } Content-filtered w All 80+ supported file formats and data objects w PCL and Postscript printouts } Tremendously reduces w Storage space requirements and w Network bandwidth consumption www. devicelock. com 20 20
 www. devicelock. com CONFIDENTIAL Network Communications Control DEVICELOCK 7. 0 ENDPOINT DLP SUITE www. devicelock. com 21 21
www. devicelock. com CONFIDENTIAL Network Communications Control DEVICELOCK 7. 0 ENDPOINT DLP SUITE www. devicelock. com 21 21
 www. devicelock. com CONFIDENTIAL Network Communications Control } Functions w w Port-independent application/protocol detection and filtering Message/session reconstruction with file/data/parameter extraction Content filtering (Network. Lock + Content. Lock) Event/audit logging & data shadowing } Network-related parameters controlled w IP address, range, subnet, masking w Network ports, ranges, “more/less than” criteria w Protocols and network application types } Identity-based parameters controlled w User IDs and groups, email and IP addresses, Instant Messaging ID, URI/URL, etc. www. devicelock. com 22 22
www. devicelock. com CONFIDENTIAL Network Communications Control } Functions w w Port-independent application/protocol detection and filtering Message/session reconstruction with file/data/parameter extraction Content filtering (Network. Lock + Content. Lock) Event/audit logging & data shadowing } Network-related parameters controlled w IP address, range, subnet, masking w Network ports, ranges, “more/less than” criteria w Protocols and network application types } Identity-based parameters controlled w User IDs and groups, email and IP addresses, Instant Messaging ID, URI/URL, etc. www. devicelock. com 22 22
 www. devicelock. com CONFIDENTIAL Network Traffic Content Filtering } Network. Lock + Content. Lock } Plain and SSL-tunneled SMTP emails w Messages and attachments – separately } HTTP/HTTPS-based web access, popular webmail & social networking applications w Gmail, Yahoo! Mail, Windows Live Mail w Facebook, Twitter, Live. Journal, Linked. In, My. Space, Odnoklassniki, Vkontakte } Instant Messaging w ICQ/AOL, MSN Messenger, Jabber, IRC, Yahoo Messenger, Mail. ru Agent } File transfer via FTP and FTP-SSL } Telnet sessions www. devicelock. com 23 23
www. devicelock. com CONFIDENTIAL Network Traffic Content Filtering } Network. Lock + Content. Lock } Plain and SSL-tunneled SMTP emails w Messages and attachments – separately } HTTP/HTTPS-based web access, popular webmail & social networking applications w Gmail, Yahoo! Mail, Windows Live Mail w Facebook, Twitter, Live. Journal, Linked. In, My. Space, Odnoklassniki, Vkontakte } Instant Messaging w ICQ/AOL, MSN Messenger, Jabber, IRC, Yahoo Messenger, Mail. ru Agent } File transfer via FTP and FTP-SSL } Telnet sessions www. devicelock. com 23 23
 www. devicelock. com CONFIDENTIAL Device. Lock 7. 0 The Basic Component DEVICELOCK 7. 0 ENDPOINT DLP SUITE www. devicelock. com 24 24
www. devicelock. com CONFIDENTIAL Device. Lock 7. 0 The Basic Component DEVICELOCK 7. 0 ENDPOINT DLP SUITE www. devicelock. com 24 24
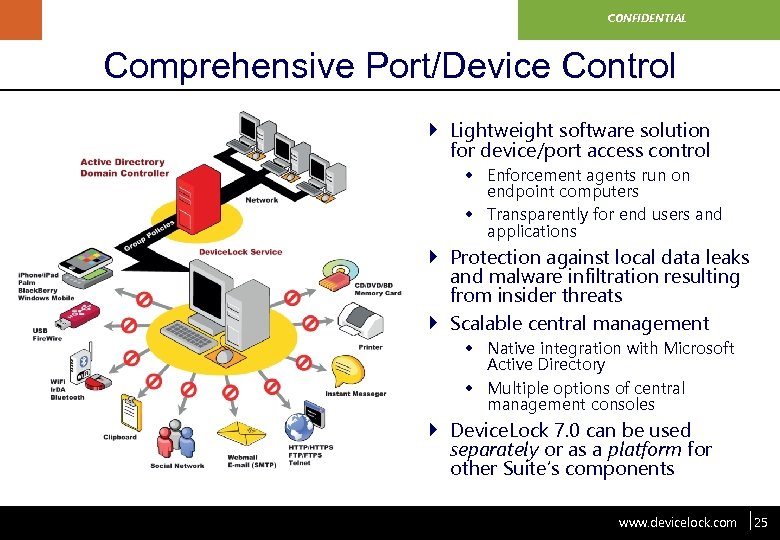 www. devicelock. com CONFIDENTIAL Comprehensive Port/Device Control } Lightweight software solution for device/port access control w Enforcement agents run on endpoint computers w Transparently for end users and applications } Protection against local data leaks and malware infiltration resulting from insider threats } Scalable central management w Native integration with Microsoft Active Directory w Multiple options of central management consoles } Device. Lock 7. 0 can be used separately or as a platform for other Suite’s components www. devicelock. com 25 25
www. devicelock. com CONFIDENTIAL Comprehensive Port/Device Control } Lightweight software solution for device/port access control w Enforcement agents run on endpoint computers w Transparently for end users and applications } Protection against local data leaks and malware infiltration resulting from insider threats } Scalable central management w Native integration with Microsoft Active Directory w Multiple options of central management consoles } Device. Lock 7. 0 can be used separately or as a platform for other Suite’s components www. devicelock. com 25 25
 www. devicelock. com CONFIDENTIAL New Capabilities DEVICELOCK 7. 0 www. devicelock. com 26 26
www. devicelock. com CONFIDENTIAL New Capabilities DEVICELOCK 7. 0 www. devicelock. com 26 26
 www. devicelock. com CONFIDENTIAL Integration with Bit. Locker To Go™ } Device. Lock controls user access to BL 2 G-protected drives on Windows 7 powered endpoints } Integrated solution is a functional analog of a built-in Removable Media Encryption for Device. Lock w Windows’ native encryption w Device. Lock and BL 2 G are centrally & natively managed from the same Active Directory platform w Device. Lock “heals” BL 2 G limitations § User/Group/Time-based “Encrypted” permissions make BL 2 G’s per-computer enforcement far more granular and flexible § Read, Read/Format, Read/Write/Format “Encrypted” operations instead of BL 2 G’s “full access only” option w Device. Lock reinforces BL 2 G security § Being logically chained with BL 2 G’s enforcement, Device. Lock prevents unauthorized data copying to unencrypted removable drives when local sysadmins turn BL 2 G off www. devicelock. com 27 27
www. devicelock. com CONFIDENTIAL Integration with Bit. Locker To Go™ } Device. Lock controls user access to BL 2 G-protected drives on Windows 7 powered endpoints } Integrated solution is a functional analog of a built-in Removable Media Encryption for Device. Lock w Windows’ native encryption w Device. Lock and BL 2 G are centrally & natively managed from the same Active Directory platform w Device. Lock “heals” BL 2 G limitations § User/Group/Time-based “Encrypted” permissions make BL 2 G’s per-computer enforcement far more granular and flexible § Read, Read/Format, Read/Write/Format “Encrypted” operations instead of BL 2 G’s “full access only” option w Device. Lock reinforces BL 2 G security § Being logically chained with BL 2 G’s enforcement, Device. Lock prevents unauthorized data copying to unencrypted removable drives when local sysadmins turn BL 2 G off www. devicelock. com 27 27
 www. devicelock. com CONFIDENTIAL Clipboard Operations Control } Clipboard copy/paste operations w Prevents unauthorized data transfers between applications } Controlled data types w Text w Images w Audio (e. g. audio recordings captured by Windows Sound Recorder) w File types (4 K+) w Screenshots (Print. Screen + 3 rd party screenshot applications) w Unidentified www. devicelock. com 28 28
www. devicelock. com CONFIDENTIAL Clipboard Operations Control } Clipboard copy/paste operations w Prevents unauthorized data transfers between applications } Controlled data types w Text w Images w Audio (e. g. audio recordings captured by Windows Sound Recorder) w File types (4 K+) w Screenshots (Print. Screen + 3 rd party screenshot applications) w Unidentified www. devicelock. com 28 28
 www. devicelock. com CONFIDENTIAL Improved Context Controls } Incoming data shadowing w Shadowing of data copied/transmitted to the computer } New parameters controlled for file operations w File size, date of modification, process initiated the operation } “Text-in-picture” detection & control w In intercepted graphical files and pictures embedded in documents (e. g. MS Office) w Block, shadow-copy, and log the file transfer/storage/access operation www. devicelock. com 29 29
www. devicelock. com CONFIDENTIAL Improved Context Controls } Incoming data shadowing w Shadowing of data copied/transmitted to the computer } New parameters controlled for file operations w File size, date of modification, process initiated the operation } “Text-in-picture” detection & control w In intercepted graphical files and pictures embedded in documents (e. g. MS Office) w Block, shadow-copy, and log the file transfer/storage/access operation www. devicelock. com 29 29
 www. devicelock. com CONFIDENTIAL Pre-7. 0 Fundamentals DEVICELOCK 7. 0 www. devicelock. com 30 30
www. devicelock. com CONFIDENTIAL Pre-7. 0 Fundamentals DEVICELOCK 7. 0 www. devicelock. com 30 30
 www. devicelock. com CONFIDENTIAL Security Functions } Highly-granular control over end user access to local ports, peripheral devices, and data input/output channels on endpoint computers } Detailed event logging and data shadowing w Event Log: automatic collection, centralized storage and auditing support w Data Shadowing: hidden copying, centralized collection, storage, searching and reviewing of data uploaded through local ports & interfaces w Central database: Microsoft SQL or any ODBC-compliant w Built-in full-text search server, Audit Log and Shadow Log Viewers } Integration with 3 rd party removable device encryption solutions w Software: PGP WDE, Drive. Crypt from Secur. Star, True. Crypt, Safe. Disk, w USB drives with hardware encryption: Block. Master (Safe. Stick 4. 0), Lexar, Iron. Key } Blocking USB and PS/2 hardware keyloggers } Tamper-proof operations w No chance to disable or remove Device. Lock agent for end users and local system administrators www. devicelock. com 31 31
www. devicelock. com CONFIDENTIAL Security Functions } Highly-granular control over end user access to local ports, peripheral devices, and data input/output channels on endpoint computers } Detailed event logging and data shadowing w Event Log: automatic collection, centralized storage and auditing support w Data Shadowing: hidden copying, centralized collection, storage, searching and reviewing of data uploaded through local ports & interfaces w Central database: Microsoft SQL or any ODBC-compliant w Built-in full-text search server, Audit Log and Shadow Log Viewers } Integration with 3 rd party removable device encryption solutions w Software: PGP WDE, Drive. Crypt from Secur. Star, True. Crypt, Safe. Disk, w USB drives with hardware encryption: Block. Master (Safe. Stick 4. 0), Lexar, Iron. Key } Blocking USB and PS/2 hardware keyloggers } Tamper-proof operations w No chance to disable or remove Device. Lock agent for end users and local system administrators www. devicelock. com 31 31
 www. devicelock. com CONFIDENTIAL Access & Log Policy Granularity (1) } Who: w User, user group, Windows system user types/groups, Group Objects from Microsoft Active Directory } Where From & Where To: w Any type of standard Windows local ports/interfaces and peripherals w USB devices by type/vendor/model, unique device w Windows Mobile®, i. Phone®/i. Pad®/i. Pod®, Black. Berry®, Palm® devices w Printers (local, network, virtual) w Encrypted removable storage w Computers, computer groups, computers in organizational unit w Computers inside or outside of corporate network www. devicelock. com 32 32
www. devicelock. com CONFIDENTIAL Access & Log Policy Granularity (1) } Who: w User, user group, Windows system user types/groups, Group Objects from Microsoft Active Directory } Where From & Where To: w Any type of standard Windows local ports/interfaces and peripherals w USB devices by type/vendor/model, unique device w Windows Mobile®, i. Phone®/i. Pad®/i. Pod®, Black. Berry®, Palm® devices w Printers (local, network, virtual) w Encrypted removable storage w Computers, computer groups, computers in organizational unit w Computers inside or outside of corporate network www. devicelock. com 32 32
 www. devicelock. com CONFIDENTIAL Access & Log Policy Granularity (2) } When w Time & date intervals, weekly schedule w Per user request (Temporary White List) } What w Input/output and device control operations w Operations with generic and encrypted storage w Data channels (removable storage, printing spooler, local synchronizations with smartphones and PDAs) w Data flow directions w Data types (file types, data objects of local sync protocols) w Specific media content (CDs/DVDs) } All the above in a flexible mix www. devicelock. com 33 33
www. devicelock. com CONFIDENTIAL Access & Log Policy Granularity (2) } When w Time & date intervals, weekly schedule w Per user request (Temporary White List) } What w Input/output and device control operations w Operations with generic and encrypted storage w Data channels (removable storage, printing spooler, local synchronizations with smartphones and PDAs) w Data flow directions w Data types (file types, data objects of local sync protocols) w Specific media content (CDs/DVDs) } All the above in a flexible mix www. devicelock. com 33 33
 www. devicelock. com CONFIDENTIAL True File Type Control } File transfer operation control based on its true type } For any File System operations with peripheral devices w NOT limited to Windows Explorer operations } Binary signature-based file type detection algorithm w Based on data type analysis of the entire file content w NOT vulnerable to encapsulation concealment techniques w 4, 000+ formats supported out-of-the-box w Extensible architecture for adding new file types } File type-based data shadowing policy w Increased control flexibility w Reduced memory consumption www. devicelock. com 34 34
www. devicelock. com CONFIDENTIAL True File Type Control } File transfer operation control based on its true type } For any File System operations with peripheral devices w NOT limited to Windows Explorer operations } Binary signature-based file type detection algorithm w Based on data type analysis of the entire file content w NOT vulnerable to encapsulation concealment techniques w 4, 000+ formats supported out-of-the-box w Extensible architecture for adding new file types } File type-based data shadowing policy w Increased control flexibility w Reduced memory consumption www. devicelock. com 34 34
 www. devicelock. com CONFIDENTIAL Local Sync Control } Patent-pending access and data type control for locally connected mobile devices w Windows Mobile, Palm OS, i. Phone/i. Pod/i. Pad, Black. Berry* } Local Sync protocol filtering w Microsoft Active. Sync, Windows Mobile Device Center, Hot. Sync, i. Tunes } Control granularity – protocol object types w Files, emails, contacts, tasks, notes, calendars, Web bookmarks, email accounts, media types (music, photos, podcasts, movies, …) } Data flow direction control (read, write) } Time-based permissions } Device presence detection and white-listing w Regardless of connection interface w Device vendor/model/unique ID (for USB connections) } Detailed centralized event logging and data shadowing www. devicelock. com 35 35
www. devicelock. com CONFIDENTIAL Local Sync Control } Patent-pending access and data type control for locally connected mobile devices w Windows Mobile, Palm OS, i. Phone/i. Pod/i. Pad, Black. Berry* } Local Sync protocol filtering w Microsoft Active. Sync, Windows Mobile Device Center, Hot. Sync, i. Tunes } Control granularity – protocol object types w Files, emails, contacts, tasks, notes, calendars, Web bookmarks, email accounts, media types (music, photos, podcasts, movies, …) } Data flow direction control (read, write) } Time-based permissions } Device presence detection and white-listing w Regardless of connection interface w Device vendor/model/unique ID (for USB connections) } Detailed centralized event logging and data shadowing www. devicelock. com 35 35
 www. devicelock. com CONFIDENTIAL Device. Lock Printing Security } Printing channel control technology w Print Spooler operations intercepted & filtered } User access control to local, network, and virtual printers } Printer connections detected regardless of the connection interface w USB control granularity: vendor ID, model ID, unique printer } Time-based permissions } Centralized event logging and data shadowing w Built-in printout viewer w Full-text search in PCL and Post. Script printouts www. devicelock. com 36 36
www. devicelock. com CONFIDENTIAL Device. Lock Printing Security } Printing channel control technology w Print Spooler operations intercepted & filtered } User access control to local, network, and virtual printers } Printer connections detected regardless of the connection interface w USB control granularity: vendor ID, model ID, unique printer } Time-based permissions } Centralized event logging and data shadowing w Built-in printout viewer w Full-text search in PCL and Post. Script printouts www. devicelock. com 36 36
 www. devicelock. com CONFIDENTIAL Event Logging & Data Shadowing } } Centralized automatic log and shadow data collection Scalable multi-server architecture for load sharing Agent-based server connection quality detection algorithm Traffic shaping & data compression for event/shadow log delivery to central server } Central data storage in MS SQL database } Full-text search server in Data Shadowing / Audit Log Database w Facilitates compliance auditing, incident investigations, forensic analysis w 80+ file formats and PCL/Post. Script printouts } Built-in tools for Audit and Shadow Log viewing, filtering, and graphical report generation www. devicelock. com 37 37
www. devicelock. com CONFIDENTIAL Event Logging & Data Shadowing } } Centralized automatic log and shadow data collection Scalable multi-server architecture for load sharing Agent-based server connection quality detection algorithm Traffic shaping & data compression for event/shadow log delivery to central server } Central data storage in MS SQL database } Full-text search server in Data Shadowing / Audit Log Database w Facilitates compliance auditing, incident investigations, forensic analysis w 80+ file formats and PCL/Post. Script printouts } Built-in tools for Audit and Shadow Log viewing, filtering, and graphical report generation www. devicelock. com 37 37
 www. devicelock. com CONFIDENTIAL Management & Administration } Management consoles with same look-n-feel GUI to fit any size customer } Device. Lock Group Policy Manager w Native & full integration with GPO Editor in Microsoft Active Directory w MMC snap-in for Group Policy Editor w Full life-cycle management for Device. Lock agents from Microsoft AD domain } Device. Lock Enterprise Manager w Separate management server w Full support of non-AD customers } Device. Lock Management Console (MMC snap-in) w Per-computer remote management for small organizations } Real-time agent status and policy consistency monitoring/repair } Agent installation, upgrade and removal in unattended centralized, interactive or local mode without system reboot } Network-awareness with automatic policy mode switching www. devicelock. com 38 38
www. devicelock. com CONFIDENTIAL Management & Administration } Management consoles with same look-n-feel GUI to fit any size customer } Device. Lock Group Policy Manager w Native & full integration with GPO Editor in Microsoft Active Directory w MMC snap-in for Group Policy Editor w Full life-cycle management for Device. Lock agents from Microsoft AD domain } Device. Lock Enterprise Manager w Separate management server w Full support of non-AD customers } Device. Lock Management Console (MMC snap-in) w Per-computer remote management for small organizations } Real-time agent status and policy consistency monitoring/repair } Agent installation, upgrade and removal in unattended centralized, interactive or local mode without system reboot } Network-awareness with automatic policy mode switching www. devicelock. com 38 38
 www. devicelock. com CONFIDENTIAL Operating Platforms } Device. Lock Agents, Management Consoles, Enterprise Server, Enterprise Manager w Windows NT/2000 w Windows XP/2003/Vista/2008 (32/64 -bit) w Windows 7 (32/64 -bit) } Directory integration w Microsoft AD (native), Novel e. Directory, any LDAP } Databases (optional) w Microsoft SQL, MSDE, any ODBC-compliant SQL www. devicelock. com 39 39
www. devicelock. com CONFIDENTIAL Operating Platforms } Device. Lock Agents, Management Consoles, Enterprise Server, Enterprise Manager w Windows NT/2000 w Windows XP/2003/Vista/2008 (32/64 -bit) w Windows 7 (32/64 -bit) } Directory integration w Microsoft AD (native), Novel e. Directory, any LDAP } Databases (optional) w Microsoft SQL, MSDE, any ODBC-compliant SQL www. devicelock. com 39 39
 www. devicelock. com CONFIDENTIAL Licensing DEVICELOCK 7. 0 ENDPOINT DLP SUITE www. devicelock. com 40 40
www. devicelock. com CONFIDENTIAL Licensing DEVICELOCK 7. 0 ENDPOINT DLP SUITE www. devicelock. com 40 40
 www. devicelock. com CONFIDENTIAL Licensing } Perpetual with 1 st year upgrades and support included w Annually paid upgrades and support for the 2 nd year and further on } Device. Lock – complete contextual controls over local devices/ports/channels w Basic and mandatory Suite’s component w Can be purchased independently } Content. Lock (CL) – content filtering functionality w Optional add-on with Device. Lock (2 -license pack: DL+CL) w Upgrade from Device. Lock (CL license) } Network. Lock (NL) – network communications control functionality w Optional add-on with Device. Lock (2 -license pack: DL+NL) w Upgrade from Device. Lock (NL license) } Device. Lock Endpoint DLP w Device. Lock + Content. Lock + Network. Lock (3 -license pack) w Upgrade from DL+NL or DL+CL } Device. Lock Search Server (DLSS) w Optional add-on for any other Suite configurations www. devicelock. com 41 41
www. devicelock. com CONFIDENTIAL Licensing } Perpetual with 1 st year upgrades and support included w Annually paid upgrades and support for the 2 nd year and further on } Device. Lock – complete contextual controls over local devices/ports/channels w Basic and mandatory Suite’s component w Can be purchased independently } Content. Lock (CL) – content filtering functionality w Optional add-on with Device. Lock (2 -license pack: DL+CL) w Upgrade from Device. Lock (CL license) } Network. Lock (NL) – network communications control functionality w Optional add-on with Device. Lock (2 -license pack: DL+NL) w Upgrade from Device. Lock (NL license) } Device. Lock Endpoint DLP w Device. Lock + Content. Lock + Network. Lock (3 -license pack) w Upgrade from DL+NL or DL+CL } Device. Lock Search Server (DLSS) w Optional add-on for any other Suite configurations www. devicelock. com 41 41
 www. devicelock. com CONFIDENTIAL Product Positioning & Value for Partners DEVICELOCK 7. 0 ENDPOINT DLP SUITE www. devicelock. com 42 42
www. devicelock. com CONFIDENTIAL Product Positioning & Value for Partners DEVICELOCK 7. 0 ENDPOINT DLP SUITE www. devicelock. com 42 42
 www. devicelock. com CONFIDENTIAL Product Positioning & Target Customers } Best price/performance endpoint DLP solution w with essential content filtering capabilities that makes DLP technologies w practical for the mainstream corporate market, and w affordable for organizations of any size and budget including SMBs } Customers – pragmatic organizations from the mainstream corporate market including SMBs w Need a cost-effective, reliable, and scalable endpoint DLP solution with the potential to grow consistently with customer requirements w Would like to deploy an endpoint DLP solution cost-effectively and safely, by gradually growing its capabilities from necessary to enhanced www. devicelock. com 43 43
www. devicelock. com CONFIDENTIAL Product Positioning & Target Customers } Best price/performance endpoint DLP solution w with essential content filtering capabilities that makes DLP technologies w practical for the mainstream corporate market, and w affordable for organizations of any size and budget including SMBs } Customers – pragmatic organizations from the mainstream corporate market including SMBs w Need a cost-effective, reliable, and scalable endpoint DLP solution with the potential to grow consistently with customer requirements w Would like to deploy an endpoint DLP solution cost-effectively and safely, by gradually growing its capabilities from necessary to enhanced www. devicelock. com 43 43
 www. devicelock. com CONFIDENTIAL Product Value for Partners (1) } Partners can sell Device. Lock 7. 0 Endpoint DLP as a mainstream revenue-generating product w Product price/seat increased manifold vs earlier versions § Aggregate margin/seat (in $) justifies dedicated sales efforts w Product can generate significant Professional Services revenue while being deployed and in post-sales support phases § Device. Lock DLP policy becomes much more complex and needs to be fine-tuned to comply with organization’s data protection policy, state regulations, industry standards } Device. Lock Endpoint DLP targets all market segments w SMB – where DLP penetration is still minimal w Enterprise segment – competing as the best “price/performance” endpoint DLP with well-balanced overall functionality www. devicelock. com 44 44
www. devicelock. com CONFIDENTIAL Product Value for Partners (1) } Partners can sell Device. Lock 7. 0 Endpoint DLP as a mainstream revenue-generating product w Product price/seat increased manifold vs earlier versions § Aggregate margin/seat (in $) justifies dedicated sales efforts w Product can generate significant Professional Services revenue while being deployed and in post-sales support phases § Device. Lock DLP policy becomes much more complex and needs to be fine-tuned to comply with organization’s data protection policy, state regulations, industry standards } Device. Lock Endpoint DLP targets all market segments w SMB – where DLP penetration is still minimal w Enterprise segment – competing as the best “price/performance” endpoint DLP with well-balanced overall functionality www. devicelock. com 44 44
 www. devicelock. com CONFIDENTIAL Product Value for Partners (2) } Large customer/installed base – let’s go upsell } Device. Lock product w Trusted and widely used in (= sellable to) § Financial, health-care, defense, military, government verticals across the globe w Complementary to (= sellable with) § Popular Anti-Virus solutions (ESET, Kaspersky, Panda) § Network-based DLP solutions (Fidelis, Palisade) w Easy to learn, deploy and support www. devicelock. com 45 45
www. devicelock. com CONFIDENTIAL Product Value for Partners (2) } Large customer/installed base – let’s go upsell } Device. Lock product w Trusted and widely used in (= sellable to) § Financial, health-care, defense, military, government verticals across the globe w Complementary to (= sellable with) § Popular Anti-Virus solutions (ESET, Kaspersky, Panda) § Network-based DLP solutions (Fidelis, Palisade) w Easy to learn, deploy and support www. devicelock. com 45 45
 www. devicelock. com CONFIDENTIAL Messaging for Customers DEVICELOCK 7. 0 ENDPOINT DLP SUITE www. devicelock. com 46 46
www. devicelock. com CONFIDENTIAL Messaging for Customers DEVICELOCK 7. 0 ENDPOINT DLP SUITE www. devicelock. com 46 46
 www. devicelock. com CONFIDENTIAL Device. Lock Value for Customers (1) } Best price/performance endpoint DLP solution w with essential content filtering capabilities that makes DLP technologies w practical and affordable for the mainstream corporate market } Well-balanced set of endpoint DLP features w Best-in-class context DLP controls with granular and flexible policy w Essential content filtering functionality – effective, highly configurable, reliable w Control over all endpoint input/output channels with protection for all data leakage scenarios w Comprehensive audit logging and data shadowing with built-in full-text searching w Centrally managed removable media encryption at no additional cost through integration with Bit. Locker To Go™ www. devicelock. com 47 47
www. devicelock. com CONFIDENTIAL Device. Lock Value for Customers (1) } Best price/performance endpoint DLP solution w with essential content filtering capabilities that makes DLP technologies w practical and affordable for the mainstream corporate market } Well-balanced set of endpoint DLP features w Best-in-class context DLP controls with granular and flexible policy w Essential content filtering functionality – effective, highly configurable, reliable w Control over all endpoint input/output channels with protection for all data leakage scenarios w Comprehensive audit logging and data shadowing with built-in full-text searching w Centrally managed removable media encryption at no additional cost through integration with Bit. Locker To Go™ www. devicelock. com 47 47
 www. devicelock. com CONFIDENTIAL Device. Lock Value for Customers (2) } Scalable from small to largest organizations w With central management natively integrated in Microsoft Active Directory } Affordable for any organizations including SMBs w Competitive price and flexible function-based licensing w Cost-effective deployment of required DLP functions w Incrementally “turn on” new capabilities as requirements grow } Easy to learn, deploy, use and maintain w Familiar Windows native MMC interface AD’s stylistics w Transparent for end users } Time-proven, trusted and widely deployed in data security sensitive organizations worldwide www. devicelock. com 48 48
www. devicelock. com CONFIDENTIAL Device. Lock Value for Customers (2) } Scalable from small to largest organizations w With central management natively integrated in Microsoft Active Directory } Affordable for any organizations including SMBs w Competitive price and flexible function-based licensing w Cost-effective deployment of required DLP functions w Incrementally “turn on” new capabilities as requirements grow } Easy to learn, deploy, use and maintain w Familiar Windows native MMC interface AD’s stylistics w Transparent for end users } Time-proven, trusted and widely deployed in data security sensitive organizations worldwide www. devicelock. com 48 48
 THANK YOU!
THANK YOU!


