bfb12b8796107a443f0de1e494d6f9a8.ppt
- Количество слайдов: 33
 Deploying VPN Eric Vyncke Cisco Systems Field Distinguished Engineer evyncke@cisco. com © 2003, Cisco Systems, Inc. All rights reserved. 1
Deploying VPN Eric Vyncke Cisco Systems Field Distinguished Engineer evyncke@cisco. com © 2003, Cisco Systems, Inc. All rights reserved. 1
 Forewords Focus mainly on VPN for one organization Evyncke ucl vpn workshop © 2003, Cisco Systems, Inc. All rights reserved. 2
Forewords Focus mainly on VPN for one organization Evyncke ucl vpn workshop © 2003, Cisco Systems, Inc. All rights reserved. 2
 Agenda • Cisco Definition of VPN • Using Layer 3 Tunnels & Routing • Security of the Above • Existing Techniques for Dynamic VPN • Deployment Examples Evyncke ucl vpn workshop © 2003, Cisco Systems, Inc. All rights reserved. 3
Agenda • Cisco Definition of VPN • Using Layer 3 Tunnels & Routing • Security of the Above • Existing Techniques for Dynamic VPN • Deployment Examples Evyncke ucl vpn workshop © 2003, Cisco Systems, Inc. All rights reserved. 3
 Virtual Private Network (VPN) Defined “ A Virtual Private Network Carries Private Traffic Over a Public Network Cisco 'official' definition Evyncke ucl vpn workshop © 2003, Cisco Systems, Inc. All rights reserved. ” 4
Virtual Private Network (VPN) Defined “ A Virtual Private Network Carries Private Traffic Over a Public Network Cisco 'official' definition Evyncke ucl vpn workshop © 2003, Cisco Systems, Inc. All rights reserved. ” 4
 What Is a “Public” Network? • In this context, any network shared among different administrative domains • A shared network such as the Internet • A privately owned network which services many external/internal customers Evyncke ucl vpn workshop © 2003, Cisco Systems, Inc. All rights reserved. 5
What Is a “Public” Network? • In this context, any network shared among different administrative domains • A shared network such as the Internet • A privately owned network which services many external/internal customers Evyncke ucl vpn workshop © 2003, Cisco Systems, Inc. All rights reserved. 5
 What is 'Private' Traffic? • Can be anything desired by an organization Confidentiality => IPSec IP Routing independance (address and IGP) => MPLS & RFC 2547 Qo. S end to end Efficient multicast Evyncke ucl vpn workshop © 2003, Cisco Systems, Inc. All rights reserved. 6
What is 'Private' Traffic? • Can be anything desired by an organization Confidentiality => IPSec IP Routing independance (address and IGP) => MPLS & RFC 2547 Qo. S end to end Efficient multicast Evyncke ucl vpn workshop © 2003, Cisco Systems, Inc. All rights reserved. 6
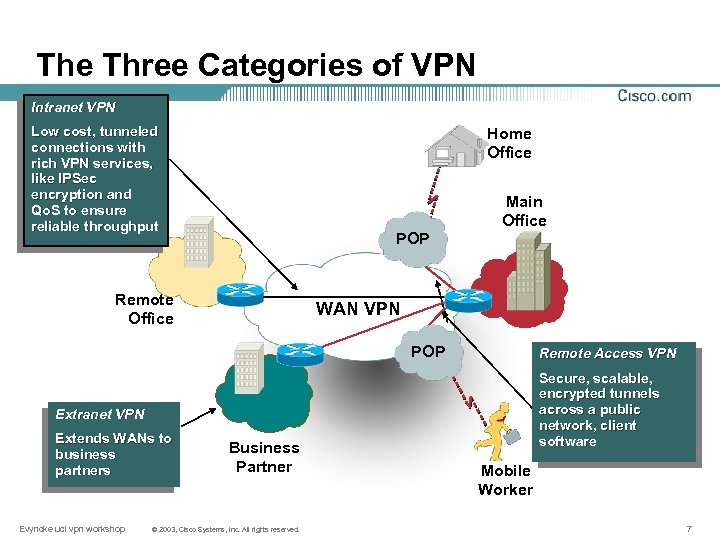 The Three Categories of VPN Intranet VPN Low cost, tunneled connections with rich VPN services, like IPSec encryption and Qo. S to ensure reliable throughput Home Office Main Office POP Remote Office WAN VPN POP Remote Access VPN Secure, scalable, encrypted tunnels across a public network, client software Extranet VPN Extends WANs to business partners Evyncke ucl vpn workshop Business Partner © 2003, Cisco Systems, Inc. All rights reserved. Mobile Worker 7
The Three Categories of VPN Intranet VPN Low cost, tunneled connections with rich VPN services, like IPSec encryption and Qo. S to ensure reliable throughput Home Office Main Office POP Remote Office WAN VPN POP Remote Access VPN Secure, scalable, encrypted tunnels across a public network, client software Extranet VPN Extends WANs to business partners Evyncke ucl vpn workshop Business Partner © 2003, Cisco Systems, Inc. All rights reserved. Mobile Worker 7
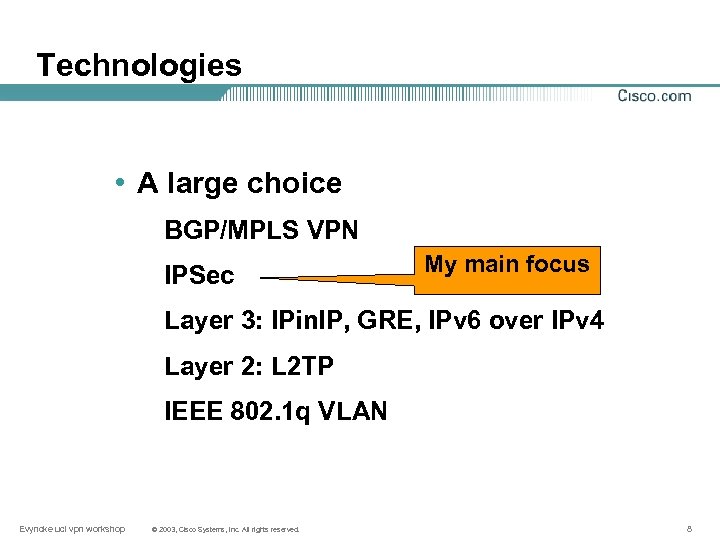 Technologies • A large choice BGP/MPLS VPN IPSec My main focus Layer 3: IPin. IP, GRE, IPv 6 over IPv 4 Layer 2: L 2 TP IEEE 802. 1 q VLAN Evyncke ucl vpn workshop © 2003, Cisco Systems, Inc. All rights reserved. 8
Technologies • A large choice BGP/MPLS VPN IPSec My main focus Layer 3: IPin. IP, GRE, IPv 6 over IPv 4 Layer 2: L 2 TP IEEE 802. 1 q VLAN Evyncke ucl vpn workshop © 2003, Cisco Systems, Inc. All rights reserved. 8
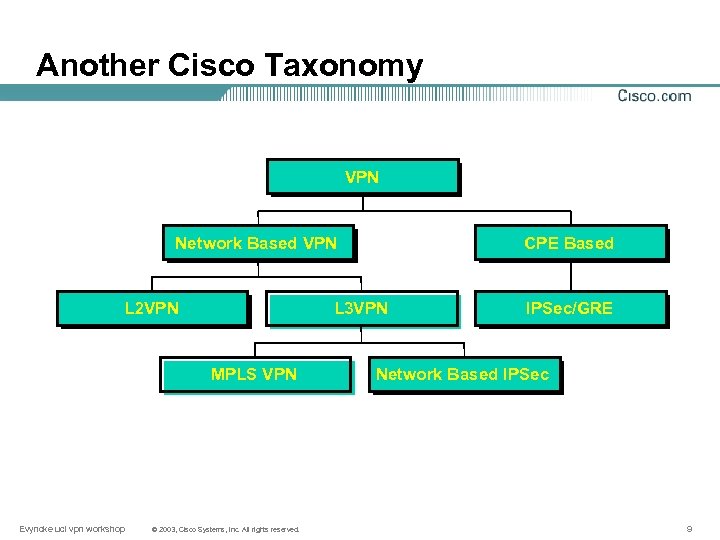 Another Cisco Taxonomy VPN Network Based VPN L 2 VPN L 3 VPN MPLS VPN Evyncke ucl vpn workshop CPE Based © 2003, Cisco Systems, Inc. All rights reserved. IPSec/GRE Network Based IPSec 9
Another Cisco Taxonomy VPN Network Based VPN L 2 VPN L 3 VPN MPLS VPN Evyncke ucl vpn workshop CPE Based © 2003, Cisco Systems, Inc. All rights reserved. IPSec/GRE Network Based IPSec 9
 Agenda • Cisco Definition of VPN • Using Layer 3 Tunnels & Routing • Security of the Above • Existing Techniques for Dynamic VPN • Deployment Examples Evyncke ucl vpn workshop © 2003, Cisco Systems, Inc. All rights reserved. 10
Agenda • Cisco Definition of VPN • Using Layer 3 Tunnels & Routing • Security of the Above • Existing Techniques for Dynamic VPN • Deployment Examples Evyncke ucl vpn workshop © 2003, Cisco Systems, Inc. All rights reserved. 10
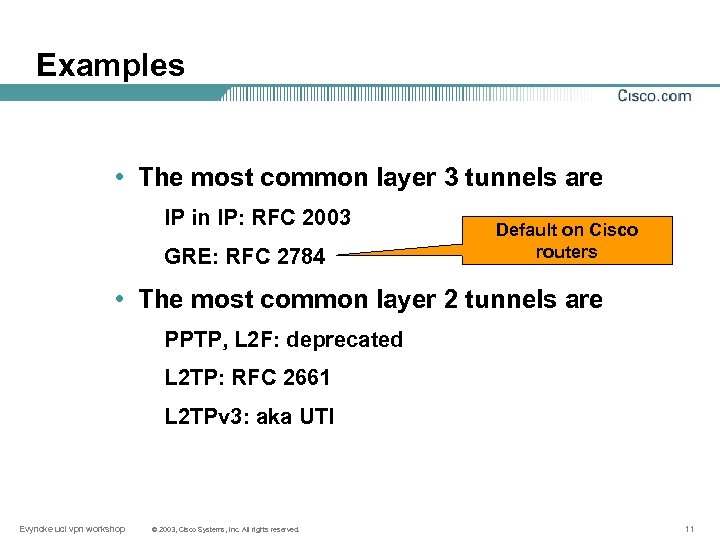 Examples • The most common layer 3 tunnels are IP in IP: RFC 2003 GRE: RFC 2784 Default on Cisco routers • The most common layer 2 tunnels are PPTP, L 2 F: deprecated L 2 TP: RFC 2661 L 2 TPv 3: aka UTI Evyncke ucl vpn workshop © 2003, Cisco Systems, Inc. All rights reserved. 11
Examples • The most common layer 3 tunnels are IP in IP: RFC 2003 GRE: RFC 2784 Default on Cisco routers • The most common layer 2 tunnels are PPTP, L 2 F: deprecated L 2 TP: RFC 2661 L 2 TPv 3: aka UTI Evyncke ucl vpn workshop © 2003, Cisco Systems, Inc. All rights reserved. 11
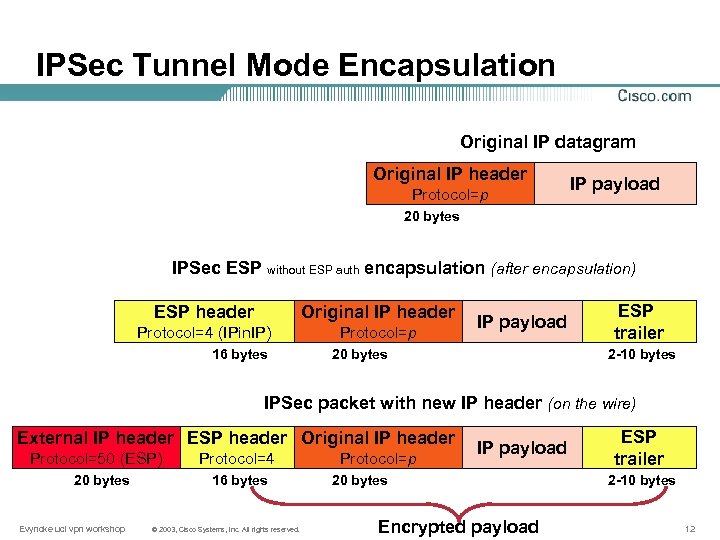 IPSec Tunnel Mode Encapsulation Original IP datagram Original IP header Protocol=p IP payload 20 bytes IPSec ESP without ESP auth encapsulation (after encapsulation) ESP header Original IP header Protocol=4 (IPin. IP) Protocol=p 16 bytes IP payload 20 bytes ESP trailer 2 -10 bytes IPSec packet with new IP header (on the wire) External IP header ESP header Original IP header Protocol=50 (ESP) 20 bytes Evyncke ucl vpn workshop Protocol=4 16 bytes © 2003, Cisco Systems, Inc. All rights reserved. Protocol=p IP payload 20 bytes Encrypted payload ESP trailer 2 -10 bytes 12
IPSec Tunnel Mode Encapsulation Original IP datagram Original IP header Protocol=p IP payload 20 bytes IPSec ESP without ESP auth encapsulation (after encapsulation) ESP header Original IP header Protocol=4 (IPin. IP) Protocol=p 16 bytes IP payload 20 bytes ESP trailer 2 -10 bytes IPSec packet with new IP header (on the wire) External IP header ESP header Original IP header Protocol=50 (ESP) 20 bytes Evyncke ucl vpn workshop Protocol=4 16 bytes © 2003, Cisco Systems, Inc. All rights reserved. Protocol=p IP payload 20 bytes Encrypted payload ESP trailer 2 -10 bytes 12
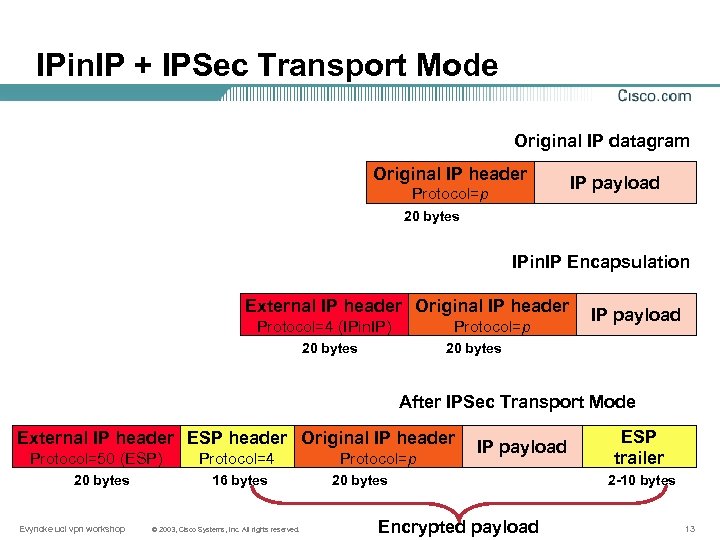 IPin. IP + IPSec Transport Mode Original IP datagram Original IP header Protocol=p IP payload 20 bytes IPin. IP Encapsulation External IP header Original IP header Protocol=4 (IPin. IP) Protocol=p IP payload 20 bytes After IPSec Transport Mode External IP header ESP header Original IP header Protocol=50 (ESP) 20 bytes Evyncke ucl vpn workshop Protocol=4 16 bytes © 2003, Cisco Systems, Inc. All rights reserved. Protocol=p IP payload 20 bytes Encrypted payload ESP trailer 2 -10 bytes 13
IPin. IP + IPSec Transport Mode Original IP datagram Original IP header Protocol=p IP payload 20 bytes IPin. IP Encapsulation External IP header Original IP header Protocol=4 (IPin. IP) Protocol=p IP payload 20 bytes After IPSec Transport Mode External IP header ESP header Original IP header Protocol=50 (ESP) 20 bytes Evyncke ucl vpn workshop Protocol=4 16 bytes © 2003, Cisco Systems, Inc. All rights reserved. Protocol=p IP payload 20 bytes Encrypted payload ESP trailer 2 -10 bytes 13
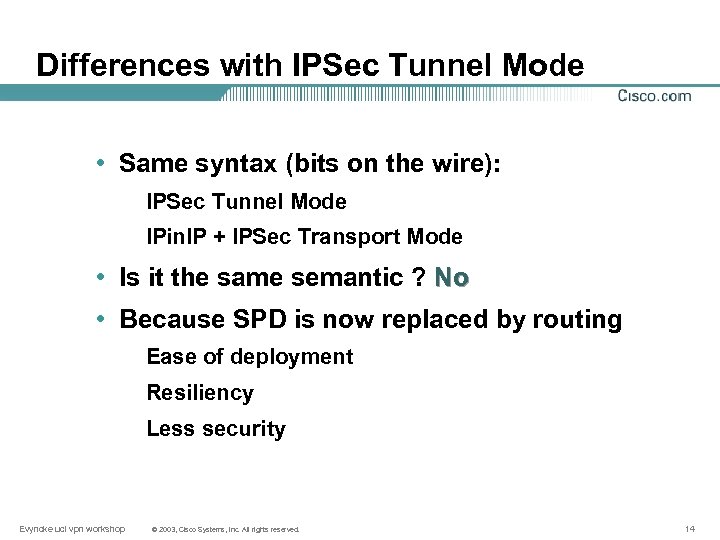 Differences with IPSec Tunnel Mode • Same syntax (bits on the wire): IPSec Tunnel Mode IPin. IP + IPSec Transport Mode • Is it the same semantic ? No • Because SPD is now replaced by routing Ease of deployment Resiliency Less security Evyncke ucl vpn workshop © 2003, Cisco Systems, Inc. All rights reserved. 14
Differences with IPSec Tunnel Mode • Same syntax (bits on the wire): IPSec Tunnel Mode IPin. IP + IPSec Transport Mode • Is it the same semantic ? No • Because SPD is now replaced by routing Ease of deployment Resiliency Less security Evyncke ucl vpn workshop © 2003, Cisco Systems, Inc. All rights reserved. 14
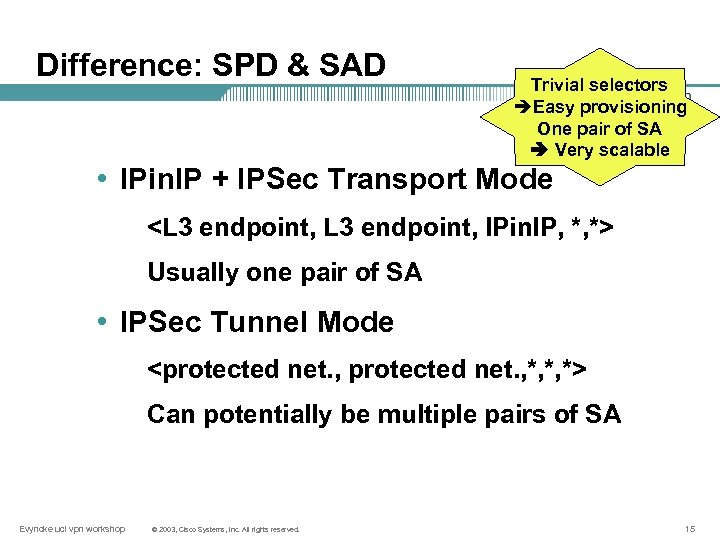 Difference: SPD & SAD Trivial selectors èEasy provisioning One pair of SA Very scalable • IPin. IP + IPSec Transport Mode
Difference: SPD & SAD Trivial selectors èEasy provisioning One pair of SA Very scalable • IPin. IP + IPSec Transport Mode
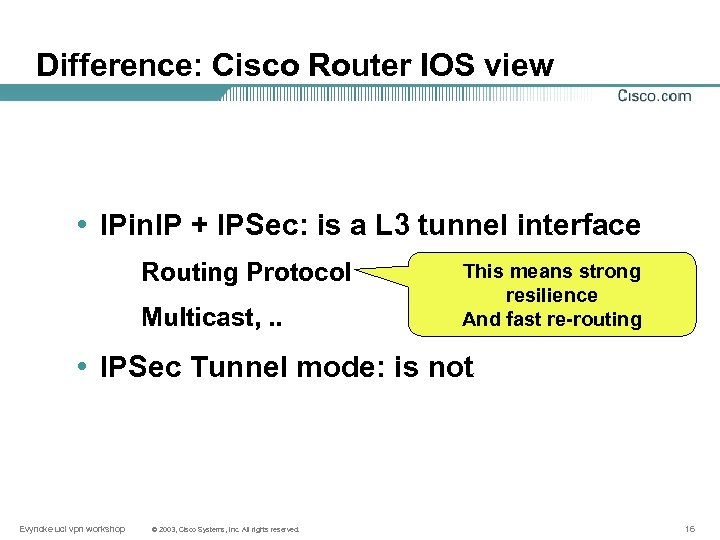 Difference: Cisco Router IOS view • IPin. IP + IPSec: is a L 3 tunnel interface Routing Protocol Multicast, . . This means strong resilience And fast re-routing • IPSec Tunnel mode: is not Evyncke ucl vpn workshop © 2003, Cisco Systems, Inc. All rights reserved. 16
Difference: Cisco Router IOS view • IPin. IP + IPSec: is a L 3 tunnel interface Routing Protocol Multicast, . . This means strong resilience And fast re-routing • IPSec Tunnel mode: is not Evyncke ucl vpn workshop © 2003, Cisco Systems, Inc. All rights reserved. 16
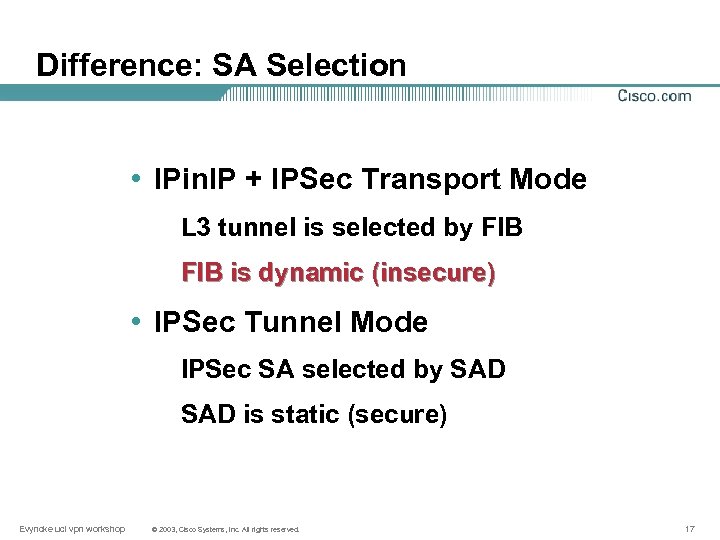 Difference: SA Selection • IPin. IP + IPSec Transport Mode L 3 tunnel is selected by FIB is dynamic (insecure) • IPSec Tunnel Mode IPSec SA selected by SAD is static (secure) Evyncke ucl vpn workshop © 2003, Cisco Systems, Inc. All rights reserved. 17
Difference: SA Selection • IPin. IP + IPSec Transport Mode L 3 tunnel is selected by FIB is dynamic (insecure) • IPSec Tunnel Mode IPSec SA selected by SAD is static (secure) Evyncke ucl vpn workshop © 2003, Cisco Systems, Inc. All rights reserved. 17
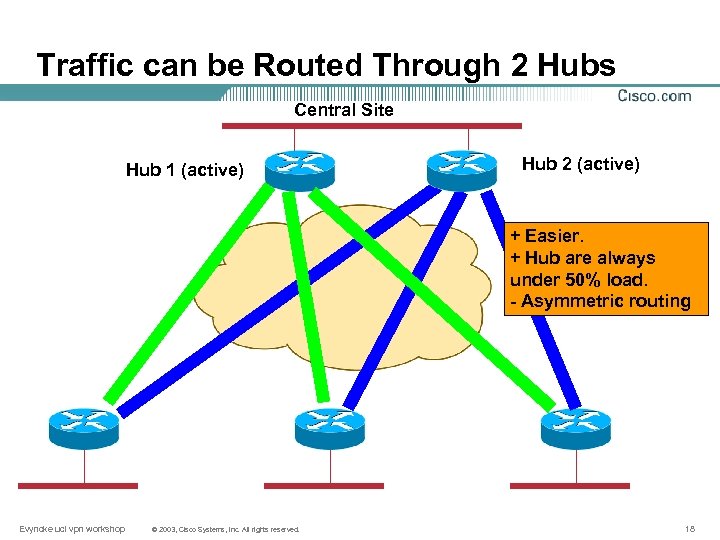 Traffic can be Routed Through 2 Hubs Central Site Hub 1 (active) Hub 2 (active) + Easier. + Hub are always under 50% load. - Asymmetric routing Evyncke ucl vpn workshop © 2003, Cisco Systems, Inc. All rights reserved. 18
Traffic can be Routed Through 2 Hubs Central Site Hub 1 (active) Hub 2 (active) + Easier. + Hub are always under 50% load. - Asymmetric routing Evyncke ucl vpn workshop © 2003, Cisco Systems, Inc. All rights reserved. 18
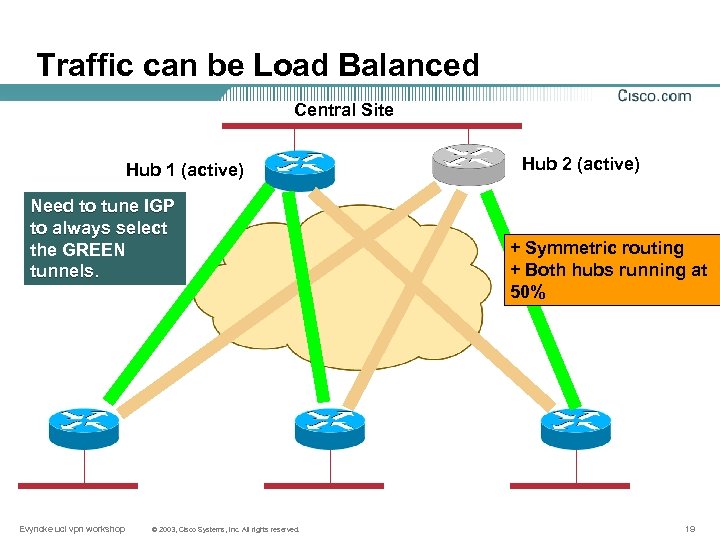 Traffic can be Load Balanced Central Site Hub 1 (active) Need to tune IGP to always select the GREEN tunnels. Evyncke ucl vpn workshop © 2003, Cisco Systems, Inc. All rights reserved. Hub 2 (active) + Symmetric routing + Both hubs running at 50% 19
Traffic can be Load Balanced Central Site Hub 1 (active) Need to tune IGP to always select the GREEN tunnels. Evyncke ucl vpn workshop © 2003, Cisco Systems, Inc. All rights reserved. Hub 2 (active) + Symmetric routing + Both hubs running at 50% 19
 Agenda • Using Layer 3 Tunnels & Routing • Security of the Above • Existing Techniques for Dynamic VPN • Deployment Examples Evyncke ucl vpn workshop © 2003, Cisco Systems, Inc. All rights reserved. 20
Agenda • Using Layer 3 Tunnels & Routing • Security of the Above • Existing Techniques for Dynamic VPN • Deployment Examples Evyncke ucl vpn workshop © 2003, Cisco Systems, Inc. All rights reserved. 20
 Agenda • Using Layer 3 Tunnels & Routing • Security of the Above • Existing Techniques for Dynamic VPN • Deployment Examples Evyncke ucl vpn workshop © 2003, Cisco Systems, Inc. All rights reserved. 28
Agenda • Using Layer 3 Tunnels & Routing • Security of the Above • Existing Techniques for Dynamic VPN • Deployment Examples Evyncke ucl vpn workshop © 2003, Cisco Systems, Inc. All rights reserved. 28
 Next Hop Resolution Protocol, RFC 2332 • IETF protocol • Used on NBMA Non Broadcast Multi-Access networks (Frame Relay, X. 25, …) to discover peers • Can also be used on multi-point GRE, m. GRE Specific kind of GRE tunnel Fan-out like: one hub and multiple spokes Hub can speak direct to all spokes Spokes can only talk to hub • Cannot be used over IPin. IP since NHRP does not run over IP Evyncke ucl vpn workshop © 2003, Cisco Systems, Inc. All rights reserved. 29
Next Hop Resolution Protocol, RFC 2332 • IETF protocol • Used on NBMA Non Broadcast Multi-Access networks (Frame Relay, X. 25, …) to discover peers • Can also be used on multi-point GRE, m. GRE Specific kind of GRE tunnel Fan-out like: one hub and multiple spokes Hub can speak direct to all spokes Spokes can only talk to hub • Cannot be used over IPin. IP since NHRP does not run over IP Evyncke ucl vpn workshop © 2003, Cisco Systems, Inc. All rights reserved. 29
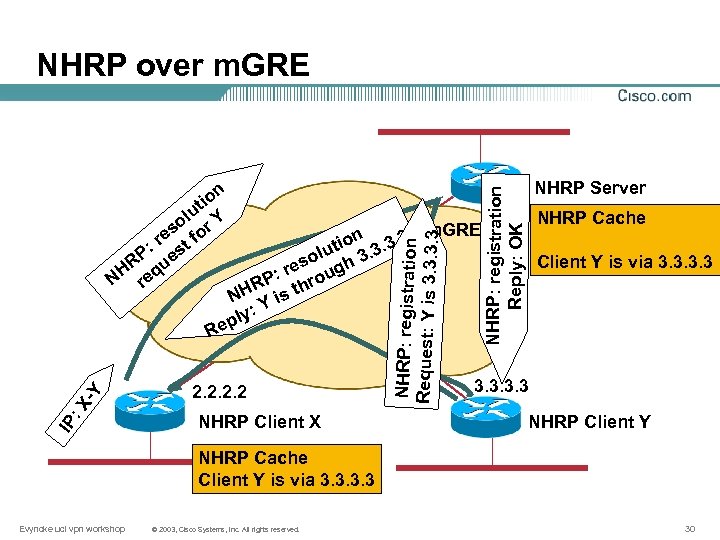 NHRP over m. GRE IP : X -Y R 2. 2 NHRP Client X NHRP: registration Request: Y is 3. 3 m. GRE n tio. 3. 3. 3 lu so gh 3 re P: hrou R NH Y is t : ply e NHRP Server NHRP: registration Reply: OK n tio u ol r Y s re t fo P: es HR equ N r NHRP Cache Client Y is via 3. 3 NHRP Client Y NHRP Cache Client Y is via 3. 3 Evyncke ucl vpn workshop © 2003, Cisco Systems, Inc. All rights reserved. 30
NHRP over m. GRE IP : X -Y R 2. 2 NHRP Client X NHRP: registration Request: Y is 3. 3 m. GRE n tio. 3. 3. 3 lu so gh 3 re P: hrou R NH Y is t : ply e NHRP Server NHRP: registration Reply: OK n tio u ol r Y s re t fo P: es HR equ N r NHRP Cache Client Y is via 3. 3 NHRP Client Y NHRP Cache Client Y is via 3. 3 Evyncke ucl vpn workshop © 2003, Cisco Systems, Inc. All rights reserved. 30
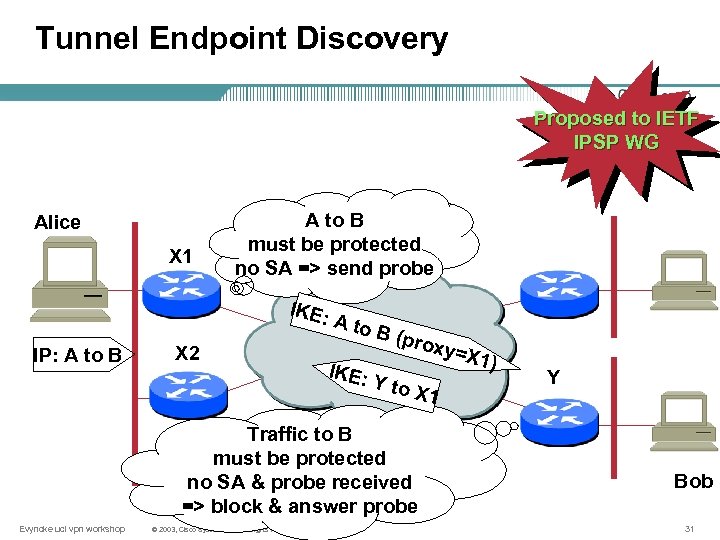 Tunnel Endpoint Discovery Proposed to IETF IPSP WG Alice X 1 A to B must be protected no SA => send probe IKE: IP: A to B X 2 A to IKE: B (p Y to roxy = X 1 Traffic to B must be protected no SA & probe received => block & answer probe Evyncke ucl vpn workshop © 2003, Cisco Systems, Inc. All rights reserved. X 1) Y Bob 31
Tunnel Endpoint Discovery Proposed to IETF IPSP WG Alice X 1 A to B must be protected no SA => send probe IKE: IP: A to B X 2 A to IKE: B (p Y to roxy = X 1 Traffic to B must be protected no SA & probe received => block & answer probe Evyncke ucl vpn workshop © 2003, Cisco Systems, Inc. All rights reserved. X 1) Y Bob 31
 NRHP, TED and Routing • NHRP+m. GRE requires routing inside the GRE tunnel to learn about connected networks • TED requires routing in the core to learn about connected networks Evyncke ucl vpn workshop © 2003, Cisco Systems, Inc. All rights reserved. 32
NRHP, TED and Routing • NHRP+m. GRE requires routing inside the GRE tunnel to learn about connected networks • TED requires routing in the core to learn about connected networks Evyncke ucl vpn workshop © 2003, Cisco Systems, Inc. All rights reserved. 32
 Agenda • Using Layer 3 Tunnels & Routing • Security of the Above • Existing Techniques for Dynamic VPN • Deployment Examples Evyncke ucl vpn workshop © 2003, Cisco Systems, Inc. All rights reserved. 33
Agenda • Using Layer 3 Tunnels & Routing • Security of the Above • Existing Techniques for Dynamic VPN • Deployment Examples Evyncke ucl vpn workshop © 2003, Cisco Systems, Inc. All rights reserved. 33
 Case #1: 1500 Nodes Hierarchical Network With IPX • Customer: large retail bank • Requirements: Mix of IP and IPX traffic Large scale 1500 nodes Hierarchical structure: branch, regional office Bandwidth: 128 kbps, 512 kbps & 10 Mbps Outsourced IP services Evyncke ucl vpn workshop © 2003, Cisco Systems, Inc. All rights reserved. 34
Case #1: 1500 Nodes Hierarchical Network With IPX • Customer: large retail bank • Requirements: Mix of IP and IPX traffic Large scale 1500 nodes Hierarchical structure: branch, regional office Bandwidth: 128 kbps, 512 kbps & 10 Mbps Outsourced IP services Evyncke ucl vpn workshop © 2003, Cisco Systems, Inc. All rights reserved. 34
 Case #1: Issues • Large scale Need to use a layered structure • Mix of IPX & IP Use of GRE encapsulation • High Availability (Resilience) Use routing protocol (EIGRP for IP & IPX) • Outsourced IP services 1 router managed by IP Service Provider 1 router managed by customer (IPSec) Evyncke ucl vpn workshop © 2003, Cisco Systems, Inc. All rights reserved. 35
Case #1: Issues • Large scale Need to use a layered structure • Mix of IPX & IP Use of GRE encapsulation • High Availability (Resilience) Use routing protocol (EIGRP for IP & IPX) • Outsourced IP services 1 router managed by IP Service Provider 1 router managed by customer (IPSec) Evyncke ucl vpn workshop © 2003, Cisco Systems, Inc. All rights reserved. 35
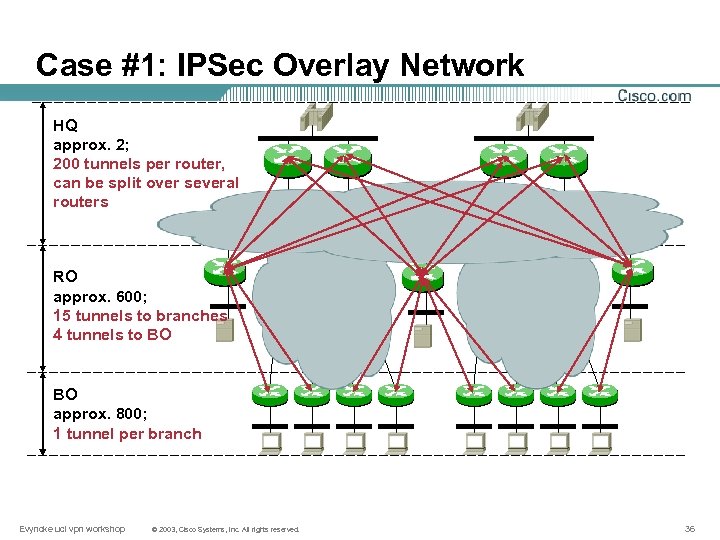 Case #1: IPSec Overlay Network HQ approx. 2; 200 tunnels per router, can be split over several routers RO approx. 600; 15 tunnels to branches 4 tunnels to BO BO approx. 800; 1 tunnel per branch Evyncke ucl vpn workshop © 2003, Cisco Systems, Inc. All rights reserved. 36
Case #1: IPSec Overlay Network HQ approx. 2; 200 tunnels per router, can be split over several routers RO approx. 600; 15 tunnels to branches 4 tunnels to BO BO approx. 800; 1 tunnel per branch Evyncke ucl vpn workshop © 2003, Cisco Systems, Inc. All rights reserved. 36
 Case #2: MPLS BGP VPN & IPSec • Customer: SP for a bank • Requirements Outsourced network: connectivity & security Double management ? Interworking with MPLS (RFC 2547) 300 Nodes Evyncke ucl vpn workshop © 2003, Cisco Systems, Inc. All rights reserved. 37
Case #2: MPLS BGP VPN & IPSec • Customer: SP for a bank • Requirements Outsourced network: connectivity & security Double management ? Interworking with MPLS (RFC 2547) 300 Nodes Evyncke ucl vpn workshop © 2003, Cisco Systems, Inc. All rights reserved. 37
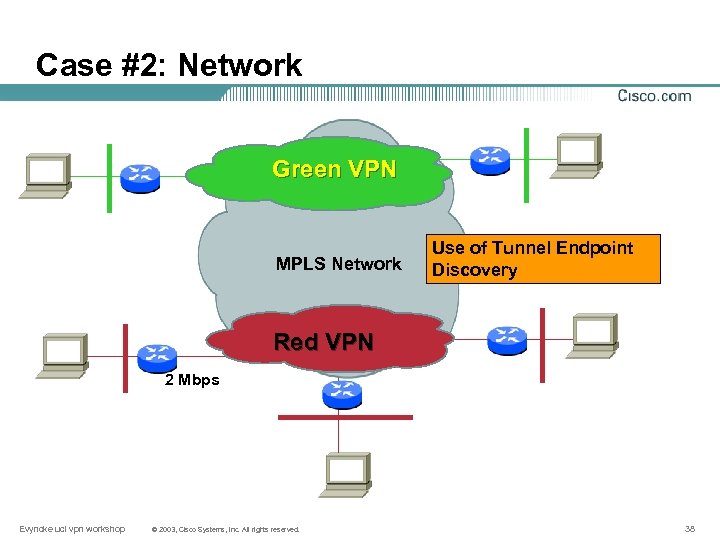 Case #2: Network Green VPN MPLS Network Use of Tunnel Endpoint Discovery Red VPN 2 Mbps Evyncke ucl vpn workshop © 2003, Cisco Systems, Inc. All rights reserved. 38
Case #2: Network Green VPN MPLS Network Use of Tunnel Endpoint Discovery Red VPN 2 Mbps Evyncke ucl vpn workshop © 2003, Cisco Systems, Inc. All rights reserved. 38
 Case #3: Mapping IPSec Remote Access to another VPN • SP customer • Wants to connect remote user over a remote access IPSec VPN to Specific L 3 VPN: GRE, BGP/MPLS Specific L 2 VPN: Frame Relay, 802. 1 Q VLAN • Solution: IPSec termination in different VRF based on IKE identity Evyncke ucl vpn workshop © 2003, Cisco Systems, Inc. All rights reserved. 39
Case #3: Mapping IPSec Remote Access to another VPN • SP customer • Wants to connect remote user over a remote access IPSec VPN to Specific L 3 VPN: GRE, BGP/MPLS Specific L 2 VPN: Frame Relay, 802. 1 Q VLAN • Solution: IPSec termination in different VRF based on IKE identity Evyncke ucl vpn workshop © 2003, Cisco Systems, Inc. All rights reserved. 39
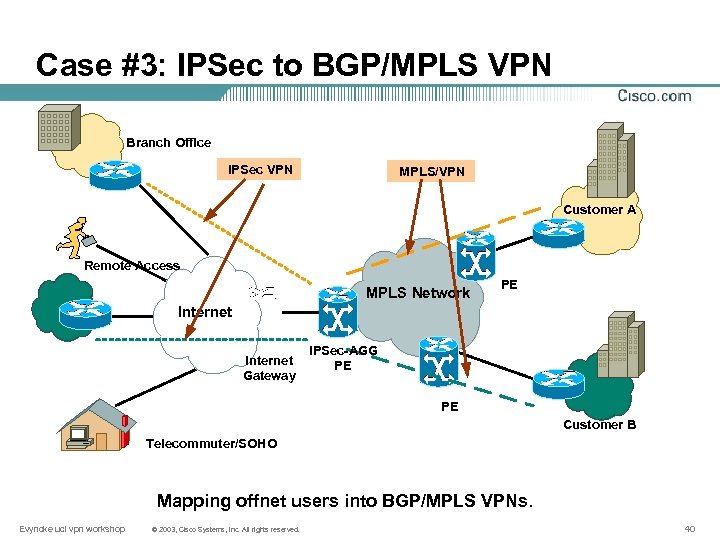 Case #3: IPSec to BGP/MPLS VPN Branch Office IPSec VPN MPLS/VPN Customer A Remote Access MPLS Network PE Internet Gateway IPSec-AGG PE PE Customer B Telecommuter/SOHO Mapping offnet users into BGP/MPLS VPNs. Evyncke ucl vpn workshop © 2003, Cisco Systems, Inc. All rights reserved. 40
Case #3: IPSec to BGP/MPLS VPN Branch Office IPSec VPN MPLS/VPN Customer A Remote Access MPLS Network PE Internet Gateway IPSec-AGG PE PE Customer B Telecommuter/SOHO Mapping offnet users into BGP/MPLS VPNs. Evyncke ucl vpn workshop © 2003, Cisco Systems, Inc. All rights reserved. 40


