4116b43c8dd9924818b8cadeb6bce2ad.ppt
- Количество слайдов: 26
 Department of Defense (DOD) Class 3 Medium Assurance Public Key Infrastructure (PKI) Status 21 September 2000 Gilda Mc. Kinnon DISA D 25 (703) 681 -9024 mckinnog@ncr. disa. mi • Colleen Carboni • DISA D 25 • (703) 681 -6139
Department of Defense (DOD) Class 3 Medium Assurance Public Key Infrastructure (PKI) Status 21 September 2000 Gilda Mc. Kinnon DISA D 25 (703) 681 -9024 mckinnog@ncr. disa. mi • Colleen Carboni • DISA D 25 • (703) 681 -6139
 Agenda • Do. D Class 3 PKI • Medium Assurance Pilot, Release 1. 0 • Class 3 PKI Release 2. 0 • Class 3 PKI Release 3. 0 – Common Access Card (CAC) Beta • • Registration Training Application Support External Certification Authorities and Interim External Certification Authorities • Using the Do. D PKI - An Example • Way Ahead 2
Agenda • Do. D Class 3 PKI • Medium Assurance Pilot, Release 1. 0 • Class 3 PKI Release 2. 0 • Class 3 PKI Release 3. 0 – Common Access Card (CAC) Beta • • Registration Training Application Support External Certification Authorities and Interim External Certification Authorities • Using the Do. D PKI - An Example • Way Ahead 2
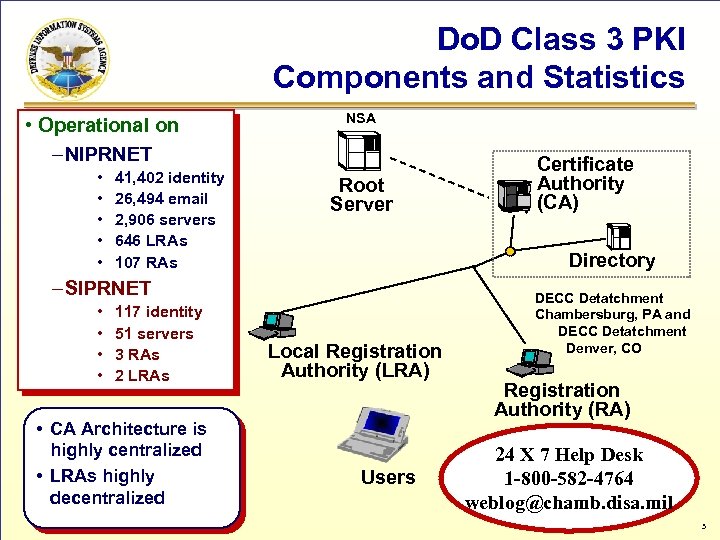 Do. D Class 3 PKI Components and Statistics • Operational on – NIPRNET NSA • • • Root Server 41, 402 identity 26, 494 email 2, 906 servers 646 LRAs 107 RAs Directory – SIPRNET • • 117 identity 51 servers 3 RAs 2 LRAs • CA Architecture is highly centralized • LRAs highly decentralized Certificate Authority (CA) Local Registration Authority (LRA) Users DECC Detatchment Chambersburg, PA and DECC Detatchment Denver, CO Registration Authority (RA) 24 X 7 Help Desk 1 -800 -582 -4764 weblog@chamb. disa. mil 3
Do. D Class 3 PKI Components and Statistics • Operational on – NIPRNET NSA • • • Root Server 41, 402 identity 26, 494 email 2, 906 servers 646 LRAs 107 RAs Directory – SIPRNET • • 117 identity 51 servers 3 RAs 2 LRAs • CA Architecture is highly centralized • LRAs highly decentralized Certificate Authority (CA) Local Registration Authority (LRA) Users DECC Detatchment Chambersburg, PA and DECC Detatchment Denver, CO Registration Authority (RA) 24 X 7 Help Desk 1 -800 -582 -4764 weblog@chamb. disa. mil 3
 Medium Assurance PKI Pilot, Release 1. 0 • Operational on – NIPRNET since April 1998 – SIPRNET since September 1999 • Certificates are valid until their expiration date • Interoperable with Class 3 PKI Release 2. 0 • NIPRNET user registration should transition to Class 3 PKI - 31 Dec 00 – Exceptions will be made on a case by case basis by the PKI PMO 4
Medium Assurance PKI Pilot, Release 1. 0 • Operational on – NIPRNET since April 1998 – SIPRNET since September 1999 • Certificates are valid until their expiration date • Interoperable with Class 3 PKI Release 2. 0 • NIPRNET user registration should transition to Class 3 PKI - 31 Dec 00 – Exceptions will be made on a case by case basis by the PKI PMO 4
 • Operational July 31, 2000 • Asserts Class 3 level of assurance • Enhancements RAISING THE BAR Class 3 PKI Release 2. 0 Enhancements – Key Escrow/Key Recovery – FIPS 140 -1 level 2 hardware signing of certificates – Added Policy Object Identifiers to differentiate between HW/SW certificates – FIPS 140 -1 level 2 smart cards for registration personnel – Larger capacity infrastructure – Improved firewall protection of the enclaves • Training – RA/LRA training started in May 00 will continue through FY 01 5
• Operational July 31, 2000 • Asserts Class 3 level of assurance • Enhancements RAISING THE BAR Class 3 PKI Release 2. 0 Enhancements – Key Escrow/Key Recovery – FIPS 140 -1 level 2 hardware signing of certificates – Added Policy Object Identifiers to differentiate between HW/SW certificates – FIPS 140 -1 level 2 smart cards for registration personnel – Larger capacity infrastructure – Improved firewall protection of the enclaves • Training – RA/LRA training started in May 00 will continue through FY 01 5
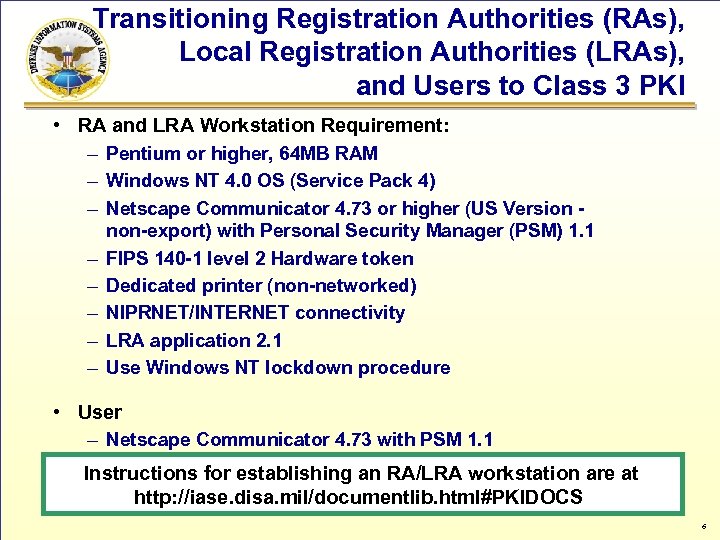 Transitioning Registration Authorities (RAs), Local Registration Authorities (LRAs), and Users to Class 3 PKI • RA and LRA Workstation Requirement: – Pentium or higher, 64 MB RAM – Windows NT 4. 0 OS (Service Pack 4) – Netscape Communicator 4. 73 or higher (US Version – – – non-export) with Personal Security Manager (PSM) 1. 1 FIPS 140 -1 level 2 Hardware token Dedicated printer (non-networked) NIPRNET/INTERNET connectivity LRA application 2. 1 Use Windows NT lockdown procedure • User – Netscape Communicator 4. 73 with PSM 1. 1 Instructions for establishing an RA/LRA workstation are at http: //iase. disa. mil/documentlib. html#PKIDOCS 6
Transitioning Registration Authorities (RAs), Local Registration Authorities (LRAs), and Users to Class 3 PKI • RA and LRA Workstation Requirement: – Pentium or higher, 64 MB RAM – Windows NT 4. 0 OS (Service Pack 4) – Netscape Communicator 4. 73 or higher (US Version – – – non-export) with Personal Security Manager (PSM) 1. 1 FIPS 140 -1 level 2 Hardware token Dedicated printer (non-networked) NIPRNET/INTERNET connectivity LRA application 2. 1 Use Windows NT lockdown procedure • User – Netscape Communicator 4. 73 with PSM 1. 1 Instructions for establishing an RA/LRA workstation are at http: //iase. disa. mil/documentlib. html#PKIDOCS 6
 Class 3 PKI Release 3. 0 Enhancements • Establishes connection to Defense Enrollment Eligibility Reporting System (DEERS), DEERS provides the PKI Unique Identification Number • Enables Real-time Automated Personnel Identification System (RAPIDS) Verification Officers (VOs) to issue PKI certificates on Common Access Card (CAC) • Schedule: – CAC BETA 1 st QTR FY 01 – System Security Assessment 1 st QTR FY 01 – Release 3. 0 2 nd QTR FY 01 7
Class 3 PKI Release 3. 0 Enhancements • Establishes connection to Defense Enrollment Eligibility Reporting System (DEERS), DEERS provides the PKI Unique Identification Number • Enables Real-time Automated Personnel Identification System (RAPIDS) Verification Officers (VOs) to issue PKI certificates on Common Access Card (CAC) • Schedule: – CAC BETA 1 st QTR FY 01 – System Security Assessment 1 st QTR FY 01 – Release 3. 0 2 nd QTR FY 01 7
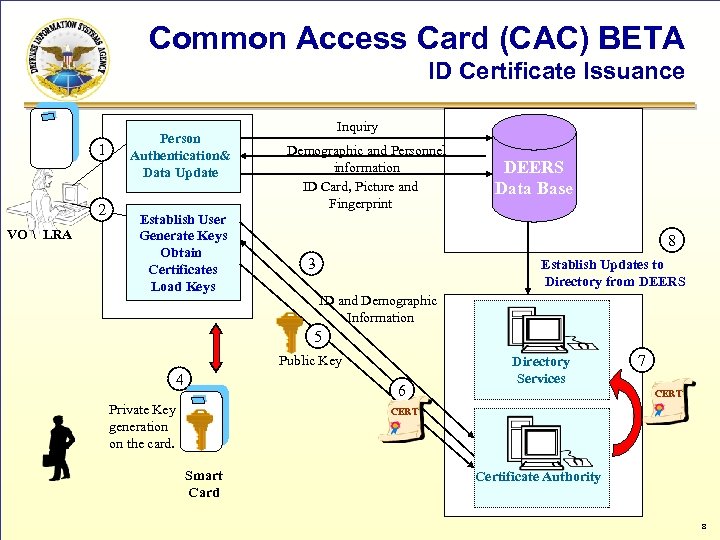 Common Access Card (CAC) BETA ID Certificate Issuance 1 2 VO LRA Person Authentication& Data Update Establish User Generate Keys Obtain Certificates Load Keys Inquiry Demographic and Personnel information ID Card, Picture and Fingerprint DEERS Data Base 8 3 Establish Updates to Directory from DEERS ID and Demographic Information 5 Public Key 4 6 Private Key generation on the card. Directory Services 7 CERT Smart Card Certificate Authority 8
Common Access Card (CAC) BETA ID Certificate Issuance 1 2 VO LRA Person Authentication& Data Update Establish User Generate Keys Obtain Certificates Load Keys Inquiry Demographic and Personnel information ID Card, Picture and Fingerprint DEERS Data Base 8 3 Establish Updates to Directory from DEERS ID and Demographic Information 5 Public Key 4 6 Private Key generation on the card. Directory Services 7 CERT Smart Card Certificate Authority 8
 Common Access Card (CAC) BETA Email Certificate Issuance • If you know your e-mail address at initial issuance of CAC – VO/LRA will issue both identity and email certificates on your CAC • If not, once you do know your email address – You can return to the VO/LRA at a later date to obtain your email certificates; or – You can go to your CINC/Service/Agency LRA for your certificates on a software token. 9
Common Access Card (CAC) BETA Email Certificate Issuance • If you know your e-mail address at initial issuance of CAC – VO/LRA will issue both identity and email certificates on your CAC • If not, once you do know your email address – You can return to the VO/LRA at a later date to obtain your email certificates; or – You can go to your CINC/Service/Agency LRA for your certificates on a software token. 9
 PKI Integration with CAC • Teaming with DMDC • PKI registration built into RAPIDS terminal – Process is transparent – When card issued, private key and certificate placed on card – Floppy containing same keys may also be provided • Applications still mostly required this form of certificate • Identification information for certificate and directory from DEERS – For both RAPIDS registration and native PKI LRA registration • Unique user id from DEERS – Needed to sync directories across Do. D 10
PKI Integration with CAC • Teaming with DMDC • PKI registration built into RAPIDS terminal – Process is transparent – When card issued, private key and certificate placed on card – Floppy containing same keys may also be provided • Applications still mostly required this form of certificate • Identification information for certificate and directory from DEERS – For both RAPIDS registration and native PKI LRA registration • Unique user id from DEERS – Needed to sync directories across Do. D 10
 Registration Authorities and Local Registration Authorities • Registration Authorities (RAs) – List of RAs can be found at http: //iase. disa. mil/PKI/RA/ra. html • Local Registration Authorities (LRAs) – List of LRAs can be found at http: //iase. disa. mil/PKI/RA/lra. html 11
Registration Authorities and Local Registration Authorities • Registration Authorities (RAs) – List of RAs can be found at http: //iase. disa. mil/PKI/RA/ra. html • Local Registration Authorities (LRAs) – List of LRAs can be found at http: //iase. disa. mil/PKI/RA/lra. html 11
 Training Information • Training will be provided monthly throughout FY 01 – 4 days Local Registration Authority (LRA) Training – 1 day Registration Authority (RA) Training • An additional 16 hours of LRA training at Defense Security Service Academy (DSSA) each quarter • Three (3) 1 week on-site training sessions are planned for C/S/As • Attendees must coordinate registration for RA/LRA class with their respective C/S/A PKI representative http: //iase. disa. mil/PKITrain. html 12
Training Information • Training will be provided monthly throughout FY 01 – 4 days Local Registration Authority (LRA) Training – 1 day Registration Authority (RA) Training • An additional 16 hours of LRA training at Defense Security Service Academy (DSSA) each quarter • Three (3) 1 week on-site training sessions are planned for C/S/As • Attendees must coordinate registration for RA/LRA class with their respective C/S/A PKI representative http: //iase. disa. mil/PKITrain. html 12
 Application Support • Requirement Documentation: – Department of Defense Class 3 Public Key Infrastructure Interface Specification, Version 1. 2, dated August 10, 2000, draft – Department of Defense CLASS 3 PKI Public Infrastructure Public Key. Enabled of Application Requirements, dated July 31, 2000 – Documents are available at http: //iase. disa. mil/documentlib. html#PKIDOCS • Class 3 PKI Testbed – Mirrors Do. D PKI Class 3 operational environment – Resides at the DISA Joint Interoperability Test Command (JITC) – Additional information at http: //jitc/fhu. disa. mil • Working with Defense Information Assurance Program on process for PK-enabling applications 13
Application Support • Requirement Documentation: – Department of Defense Class 3 Public Key Infrastructure Interface Specification, Version 1. 2, dated August 10, 2000, draft – Department of Defense CLASS 3 PKI Public Infrastructure Public Key. Enabled of Application Requirements, dated July 31, 2000 – Documents are available at http: //iase. disa. mil/documentlib. html#PKIDOCS • Class 3 PKI Testbed – Mirrors Do. D PKI Class 3 operational environment – Resides at the DISA Joint Interoperability Test Command (JITC) – Additional information at http: //jitc/fhu. disa. mil • Working with Defense Information Assurance Program on process for PK-enabling applications 13
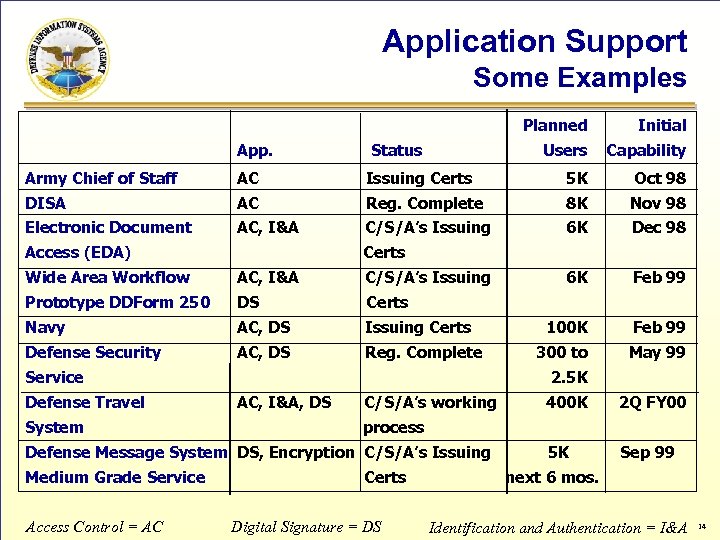 Application Support Some Examples Planned App. Users Status Initial Capability Army Chief of Staff AC Issuing Certs 5 K Oct 98 DISA AC Reg. Complete 8 K Nov 98 Electronic Document AC, I&A C/S/A’s Issuing 6 K Dec 98 6 K Feb 99 100 K Feb 99 300 to May 99 Access (EDA) Certs Wide Area Workflow AC, I&A C/S/A’s Issuing Prototype DDForm 250 DS Certs Navy AC, DS Issuing Certs Defense Security AC, DS Reg. Complete Service Defense Travel System 2. 5 K AC, I&A, DS C/S/A’s working Access Control = AC 2 Q FY 00 5 K Sep 99 process Defense Message System DS, Encryption C/S/A’s Issuing Medium Grade Service 400 K Certs Digital Signature = DS next 6 mos. Identification and Authentication = I&A 14
Application Support Some Examples Planned App. Users Status Initial Capability Army Chief of Staff AC Issuing Certs 5 K Oct 98 DISA AC Reg. Complete 8 K Nov 98 Electronic Document AC, I&A C/S/A’s Issuing 6 K Dec 98 6 K Feb 99 100 K Feb 99 300 to May 99 Access (EDA) Certs Wide Area Workflow AC, I&A C/S/A’s Issuing Prototype DDForm 250 DS Certs Navy AC, DS Issuing Certs Defense Security AC, DS Reg. Complete Service Defense Travel System 2. 5 K AC, I&A, DS C/S/A’s working Access Control = AC 2 Q FY 00 5 K Sep 99 process Defense Message System DS, Encryption C/S/A’s Issuing Medium Grade Service 400 K Certs Digital Signature = DS next 6 mos. Identification and Authentication = I&A 14
 External Certificate Authority (ECA) & Interim External Certificate Authority (IECA) • An ECA is an entity authorized to issue certificates interoperable with the Do. D PKI to non-Do. D personnel • What is an IECA? – Entity authorized to issue certificates interoperable with the Do. D PKI to non-Do. D personnel, for a period of one year • Why an Interim ECA? – Need to work out best practices, understand technical and process issues, understand resolve legal concerns before finalizing ECA approach and processes. • IECA Help Desk and Website – E-mail: pkieca@ncr. disa. mil – Phone: (703) 681 -6139 – http: //www. disa. mil/infosec/pkieca 15
External Certificate Authority (ECA) & Interim External Certificate Authority (IECA) • An ECA is an entity authorized to issue certificates interoperable with the Do. D PKI to non-Do. D personnel • What is an IECA? – Entity authorized to issue certificates interoperable with the Do. D PKI to non-Do. D personnel, for a period of one year • Why an Interim ECA? – Need to work out best practices, understand technical and process issues, understand resolve legal concerns before finalizing ECA approach and processes. • IECA Help Desk and Website – E-mail: pkieca@ncr. disa. mil – Phone: (703) 681 -6139 – http: //www. disa. mil/infosec/pkieca 15
 IECA Web Site http: //www. disa. mil/infosec/pkieca
IECA Web Site http: //www. disa. mil/infosec/pkieca
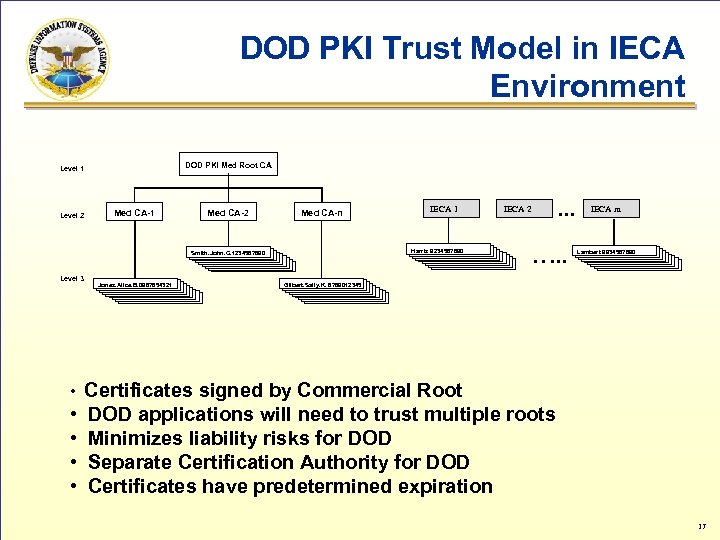 DOD PKI Trust Model in IECA Environment DOD PKI Med Root CA Level 1 Level 2 Med CA-1 Med CA-2 Med CA-n Harris 9234567890 Smith. John. C. 1234567890 Level 3 • • • Jones. Alice. B. 0987654321 IECA 1 . . . IECA 2 …. . IECA m Lambert 9934567890 Gilbert. Sally. K. 6789012345 Certificates signed by Commercial Root DOD applications will need to trust multiple roots Minimizes liability risks for DOD Separate Certification Authority for DOD Certificates have predetermined expiration 17
DOD PKI Trust Model in IECA Environment DOD PKI Med Root CA Level 1 Level 2 Med CA-1 Med CA-2 Med CA-n Harris 9234567890 Smith. John. C. 1234567890 Level 3 • • • Jones. Alice. B. 0987654321 IECA 1 . . . IECA 2 …. . IECA m Lambert 9934567890 Gilbert. Sally. K. 6789012345 Certificates signed by Commercial Root DOD applications will need to trust multiple roots Minimizes liability risks for DOD Separate Certification Authority for DOD Certificates have predetermined expiration 17
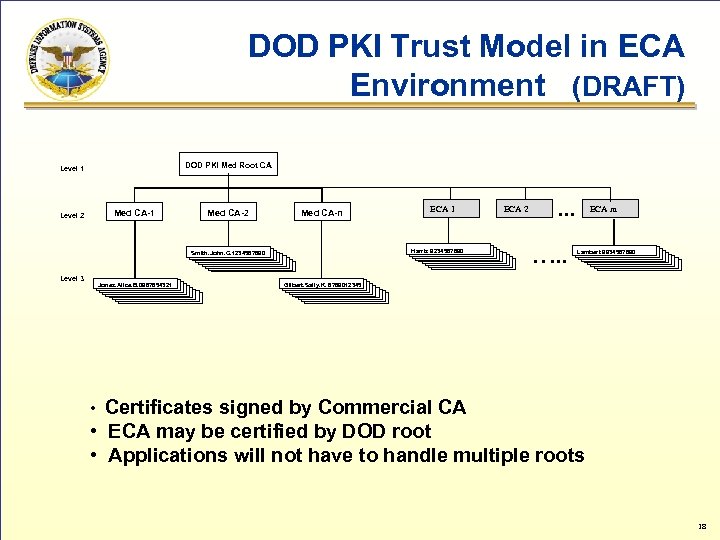 DOD PKI Trust Model in ECA Environment (DRAFT) DOD PKI Med Root CA Level 1 Med CA-1 Level 2 Med CA-n Harris 9234567890 Smith. John. C. 1234567890 Level 3 Jones. Alice. B. 0987654321 ECA 2 . . . …. . ECA m Lambert 9934567890 Gilbert. Sally. K. 6789012345 Certificates signed by Commercial CA • ECA may be certified by DOD root • Applications will not have to handle multiple roots • 18
DOD PKI Trust Model in ECA Environment (DRAFT) DOD PKI Med Root CA Level 1 Med CA-1 Level 2 Med CA-n Harris 9234567890 Smith. John. C. 1234567890 Level 3 Jones. Alice. B. 0987654321 ECA 2 . . . …. . ECA m Lambert 9934567890 Gilbert. Sally. K. 6789012345 Certificates signed by Commercial CA • ECA may be certified by DOD root • Applications will not have to handle multiple roots • 18
 IECA Vendors • Operational Research Consultants (ORC): Daniel Turissini; (703) 535 -5301; turissd@orc. com • Digital Signature Trust (DST): Keren Cummins; (301) 379 -2493; kcummins@digsigtrust. com • Veri. Sign: James Brandt; (410) 691 -2100; jbrandt@verisign. com • General Dynamics: Sandra Wheeler; (781) 455 -5958; sandra. wheeler@gd-cs. com 19
IECA Vendors • Operational Research Consultants (ORC): Daniel Turissini; (703) 535 -5301; turissd@orc. com • Digital Signature Trust (DST): Keren Cummins; (301) 379 -2493; kcummins@digsigtrust. com • Veri. Sign: James Brandt; (410) 691 -2100; jbrandt@verisign. com • General Dynamics: Sandra Wheeler; (781) 455 -5958; sandra. wheeler@gd-cs. com 19
 IECA Status Update • IECA Pilot has been extended for one more year (until September 2001) • All four IECAs are currently signing new MOAs • Do. D contributed to four programs/organizations for the purchase of IECA certificates – Medium Grade Services (MGS) – Joint Electronic Commerce Program Office (JECPO) – Defense Technical Information Center (DTIC) – Military Traffic Management Command (MTMC) • As demand/activity increases expect certificate cost to substantially decrease 20
IECA Status Update • IECA Pilot has been extended for one more year (until September 2001) • All four IECAs are currently signing new MOAs • Do. D contributed to four programs/organizations for the purchase of IECA certificates – Medium Grade Services (MGS) – Joint Electronic Commerce Program Office (JECPO) – Defense Technical Information Center (DTIC) – Military Traffic Management Command (MTMC) • As demand/activity increases expect certificate cost to substantially decrease 20
 Using the Do. D PKI An Example 21
Using the Do. D PKI An Example 21
 The I Assure Advantage http: //www. disa. mil/D 4/diioss/iachar. html Key Points: • Contract supports up to TS / SCI security requirements • 7 year multi-award contract • All tasks MUST BE competed, no follow-on work from previous contracts Most of the work awarded under this contract will be professional services, however, …. the contract is structured to permit purchase of a full range of Information Assurance (IA) solutions, including the hardware, software and enabling products necessary to implement these solutions. Solutions-based: Contractors can tailor services and products for each task order proposal; Complements Enterprise Software Initiative: I Assure vendors can provide integration services for ESI products Task Areas: • Policy, planning, process, program and project management support • Standards, Architecture, Engineering and Integration support • Solution Fielding / Implementation and operations • Education, training, and awareness; certification and accreditation; and IA support 22
The I Assure Advantage http: //www. disa. mil/D 4/diioss/iachar. html Key Points: • Contract supports up to TS / SCI security requirements • 7 year multi-award contract • All tasks MUST BE competed, no follow-on work from previous contracts Most of the work awarded under this contract will be professional services, however, …. the contract is structured to permit purchase of a full range of Information Assurance (IA) solutions, including the hardware, software and enabling products necessary to implement these solutions. Solutions-based: Contractors can tailor services and products for each task order proposal; Complements Enterprise Software Initiative: I Assure vendors can provide integration services for ESI products Task Areas: • Policy, planning, process, program and project management support • Standards, Architecture, Engineering and Integration support • Solution Fielding / Implementation and operations • Education, training, and awareness; certification and accreditation; and IA support 22
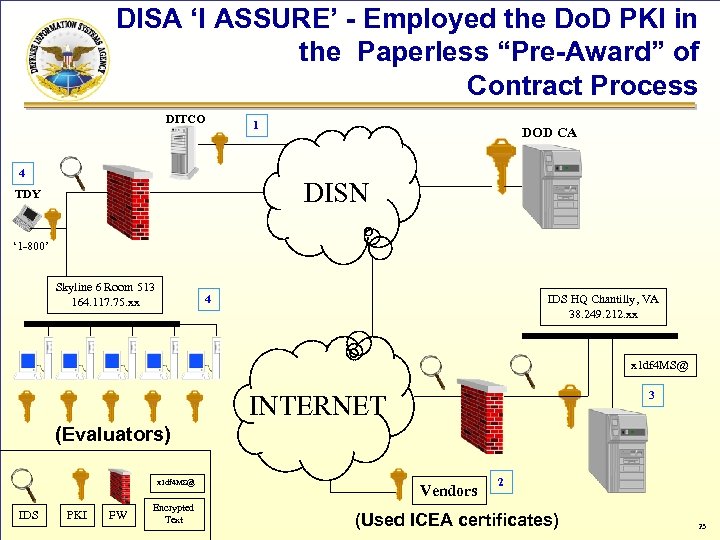 DISA ‘I ASSURE’ - Employed the Do. D PKI in the Paperless “Pre-Award” of Contract Process DITCO 4 1 DOD CA DISN TDY ‘ 1 -800’ Skyline 6 Room 513 164. 117. 75. xx 4 IDS HQ Chantilly, VA 38. 249. 212. xx x 1 df 4 MS@ 3 INTERNET (Evaluators) x 1 df 4 MS@ IDS PKI FW Encrypted Text Vendors 2 (Used ICEA certificates) 23
DISA ‘I ASSURE’ - Employed the Do. D PKI in the Paperless “Pre-Award” of Contract Process DITCO 4 1 DOD CA DISN TDY ‘ 1 -800’ Skyline 6 Room 513 164. 117. 75. xx 4 IDS HQ Chantilly, VA 38. 249. 212. xx x 1 df 4 MS@ 3 INTERNET (Evaluators) x 1 df 4 MS@ IDS PKI FW Encrypted Text Vendors 2 (Used ICEA certificates) 23
 The Way Ahead • Provide support to Common Access Card (CAC) Beta and Release 3. 0 • Expand use of SIPRNET PKI • Continue development of application enabling guidance and enabling templates • Continue incremental releases of DOD PKI to improve product, service, and availability • Envision seamless transition to Target PKI Continue Satisfying The Warfighter Requirements! 24
The Way Ahead • Provide support to Common Access Card (CAC) Beta and Release 3. 0 • Expand use of SIPRNET PKI • Continue development of application enabling guidance and enabling templates • Continue incremental releases of DOD PKI to improve product, service, and availability • Envision seamless transition to Target PKI Continue Satisfying The Warfighter Requirements! 24
 DOD PKI Working Groups • DOD PKI Certificate Policy Management Working Group: – co-chair - NSA - Mr. Gary Dahlquist gndahlq@missi. ncsc. mil – co-chair - DOD GC - Ms. Shauna Russell - russels@osdgc. osd. mil • DOD PKI Business Working Group (BWG): – co-chair - NSA - Ms. Debra Grempler - DAGremp@missi. ncsc. mil – co-chair - DISA - Ms. Gilda Mc. Kinnon - Mc. Kinnog@ncr. disa. mil • DOD PKI Technical Working Group (TWG): – co-chair - DISA - Mr. Adam Britt - britta@ncr. disa. mil – co-chair - NSA - Mr. Dave Fillingham dwfilli@missi. ncsc. mil 25
DOD PKI Working Groups • DOD PKI Certificate Policy Management Working Group: – co-chair - NSA - Mr. Gary Dahlquist gndahlq@missi. ncsc. mil – co-chair - DOD GC - Ms. Shauna Russell - russels@osdgc. osd. mil • DOD PKI Business Working Group (BWG): – co-chair - NSA - Ms. Debra Grempler - DAGremp@missi. ncsc. mil – co-chair - DISA - Ms. Gilda Mc. Kinnon - Mc. Kinnog@ncr. disa. mil • DOD PKI Technical Working Group (TWG): – co-chair - DISA - Mr. Adam Britt - britta@ncr. disa. mil – co-chair - NSA - Mr. Dave Fillingham dwfilli@missi. ncsc. mil 25
 PKI Website Information • http: //iase. disa. mil – Information Assurance Support Environment • available to. mil; and. gov • http: //www. disa. mil/infosec/pkieca – External Certification Authorities • http: //www. disa. mil/infosec/pki-int. html – DOD PKI Medium Assurance Interoperability • DOD PKI Medium Assurance X. 509 v 3 certificate standard profiles (formats and examples) 26
PKI Website Information • http: //iase. disa. mil – Information Assurance Support Environment • available to. mil; and. gov • http: //www. disa. mil/infosec/pkieca – External Certification Authorities • http: //www. disa. mil/infosec/pki-int. html – DOD PKI Medium Assurance Interoperability • DOD PKI Medium Assurance X. 509 v 3 certificate standard profiles (formats and examples) 26


