13f4841983e852cb5a47a026e68bbbc2.ppt
- Количество слайдов: 28
Department of Computer Science Policy Management Elisa Bertino, Ninghui Li (Purdue U. ) Anupam Joshi (UMBC) Ravi Sandhu (UTSA)

Department of Computer Science Research Goals • Identify the types of policy relevant to AISL • Develop corresponding languages and formal models • Implement policy languages • Develop relevant policy tools to support the policy lifecycle • Develop policy scenarios
Department of Computer Science Types of Policy – Access control policies • Controlling who is accessing which data – Accountability policies • Controlling how data is used and modified – Trust policies • Specifying criteria to determine which party to trust for what data/resource
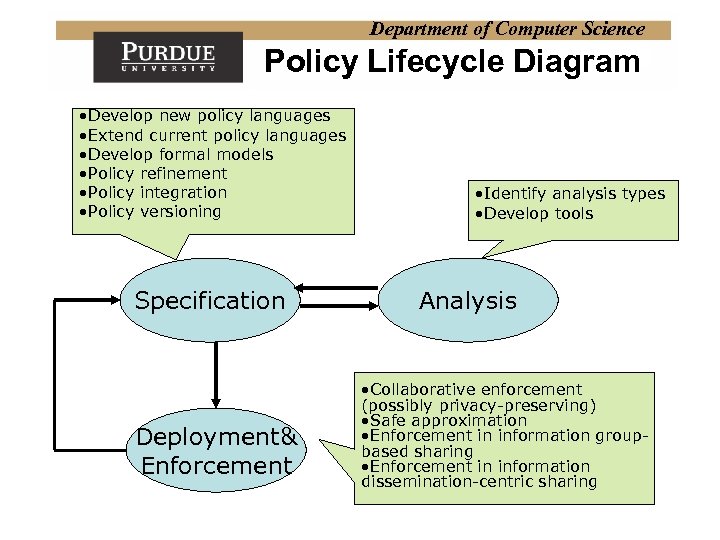
Department of Computer Science Policy Lifecycle Diagram • Develop new policy languages • Extend current policy languages • Develop formal models • Policy refinement • Policy integration • Policy versioning Specification Deployment& Enforcement • Identify analysis types • Develop tools Analysis • Collaborative enforcement (possibly privacy-preserving) • Safe approximation • Enforcement in information groupbased sharing • Enforcement in information dissemination-centric sharing
Department of Computer Science Policy Refinement Each refinement step must meet the following criteria [Karat 08]: • Correct — The set of refined policies correctly implements the higher-level policy. • Consistent — The refinement must not lead to conflicts between the derived policies or the other policies existing in the system. • Valid — The policies must be able to be enforced in the system context to which they will be applied. • Minimal — All policies in the derived policy set must be required for the correctness of the refinement. J. Karat, C. M. Karat, E. Bertino, N. Li, Q. Ni, C. Brodie, J. Lobo, S. B. Calo, L. F. Cranor, P. Kamaraguru, P. Reerder, “Policy Framework for Security and Privacy Management”, To appear in IBM Systems Journal, 2008.
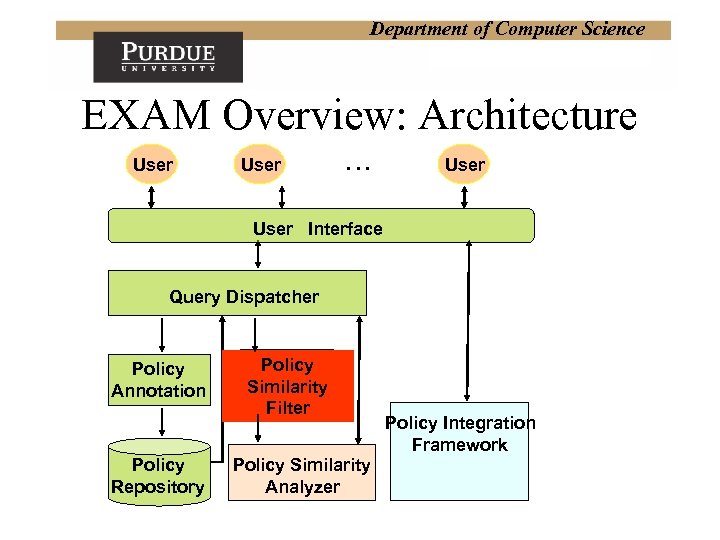
Department of Computer Science Current Results EXAM Environment for Xacml policy Analysis & Management EXAM is a comprehensive environment for analyzing and managing access control policies. It supports acquisition, editing and retrieval of policies in addition to policy property analysis, policy similarity analysis and policy integration.
Department of Computer Science Motivation Proliferation of Policies !! Need for tools for managing and analyzing policies !

Department of Computer Science XACML • EXtensible Access Control Markup Language. – XML based – OASIS standard language for specification of access control policies. – Express many policies of interest to real world application
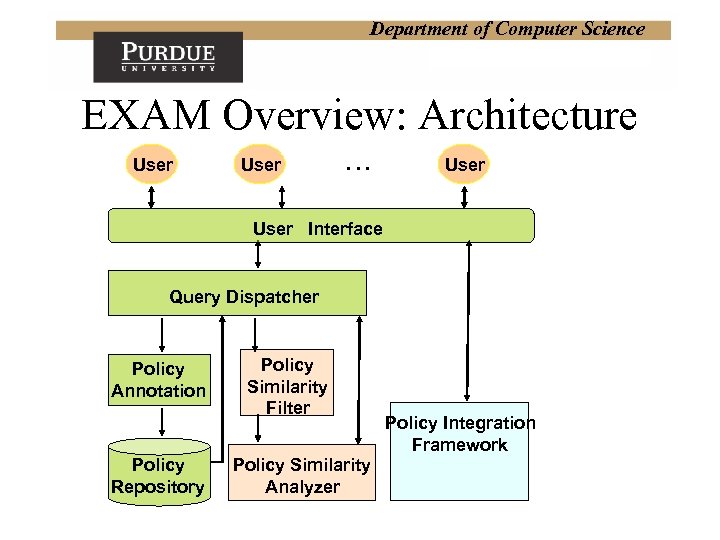
Department of Computer Science EXAM Overview: Architecture User … User Interface Query Dispatcher Policy Annotation Policy Repository Policy Similarity Filter Policy Similarity Analyzer Policy Integration Framework
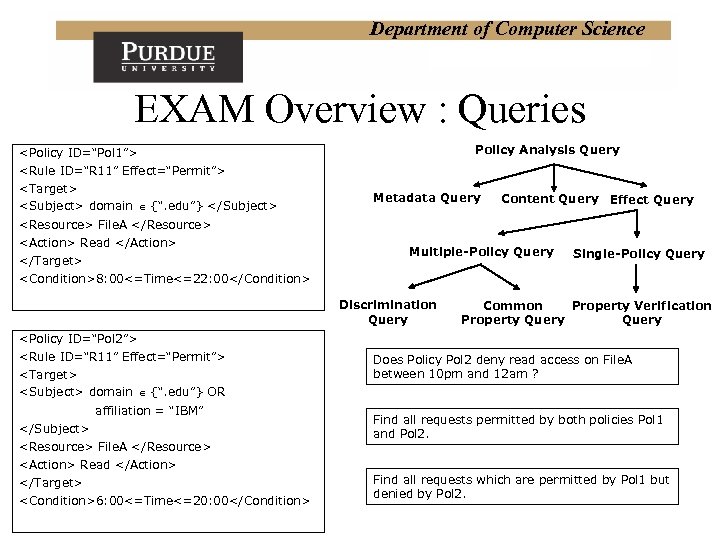
Department of Computer Science EXAM Overview : Queries Policy Analysis Query <Policy ID=“Pol 1”> <Rule ID=“R 11” Effect=“Permit”> <Target> <Subject> domain {“. edu”} </Subject> <Resource> File. A </Resource> <Action> Read </Action> </Target> <Condition>8: 00<=Time<=22: 00</Condition> Metadata Query Content Query Effect Query Multiple-Policy Query Discrimination Query Single-Policy Query Common Property Verification Property Query <Policy ID=“Pol 2”> <Rule ID=“R 11” Effect=“Permit”> <Target> <Subject> domain {“. edu”} OR affiliation = “IBM” </Subject> <Resource> File. A </Resource> <Action> Read </Action> </Target> <Condition>6: 00<=Time<=20: 00</Condition> Does Policy Pol 2 deny read access on File. A between 10 pm and 12 am ? Find all requests permitted by both policies Pol 1 and Pol 2. Find all requests which are permitted by Pol 1 but denied by Pol 2.

Department of Computer Science Policy Similarity Analysis • Goal – Characterize the relationships among the sets of requests respectively authorized by a set of policies. • Two techniques – Policy Similarity Filter • Less precise, faster. – Policy Similarity Analyzer • Precise, slower.
Department of Computer Science EXAM Overview: Architecture User … User Interface Query Dispatcher Policy Annotation Policy Repository Policy Similarity Filter Policy Similarity Analyzer Policy Integration Framework

Department of Computer Science Policy Similarity Filter • Quick and less precise. • Inspired by Information Retrieval (IR) techniques. • Policy similarity measure – Assign a similarity score between two policies. • Typical applications – A quick filter phase to prune the set of policies to be analyzed by the precise policy similarity technique. – A distance function for clustering policies.

Department of Computer Science DATA OWNER POLICY 2 DATA OWNER POLICY 1 Example 0 0. 71
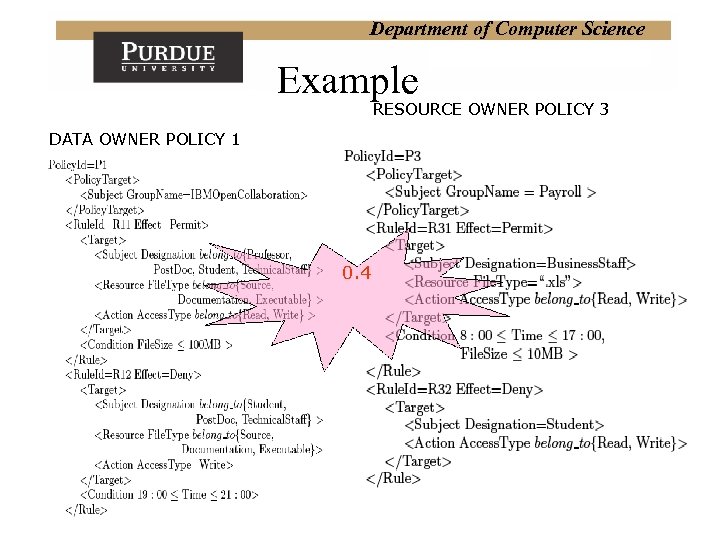
Department of Computer Science Example RESOURCE OWNER POLICY 3 DATA OWNER POLICY 1 0. 4
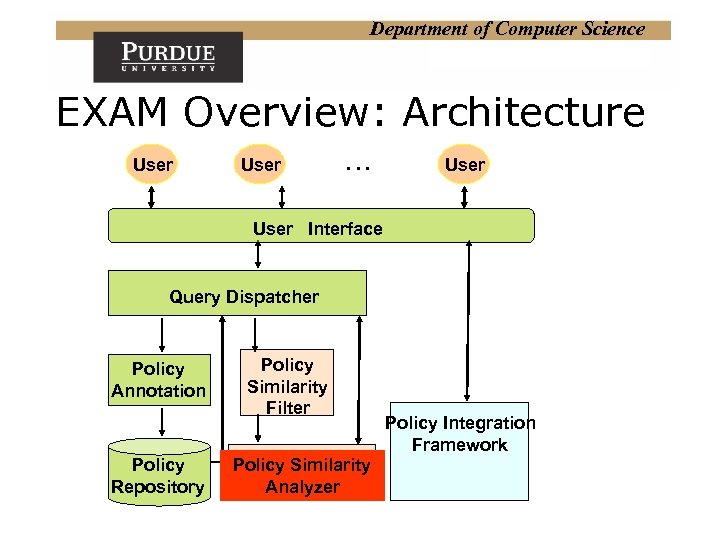
Department of Computer Science EXAM Overview: Architecture User … User Interface Query Dispatcher Policy Annotation Policy Repository Policy Similarity Filter Policy Similarity Analyzer Policy Integration Framework
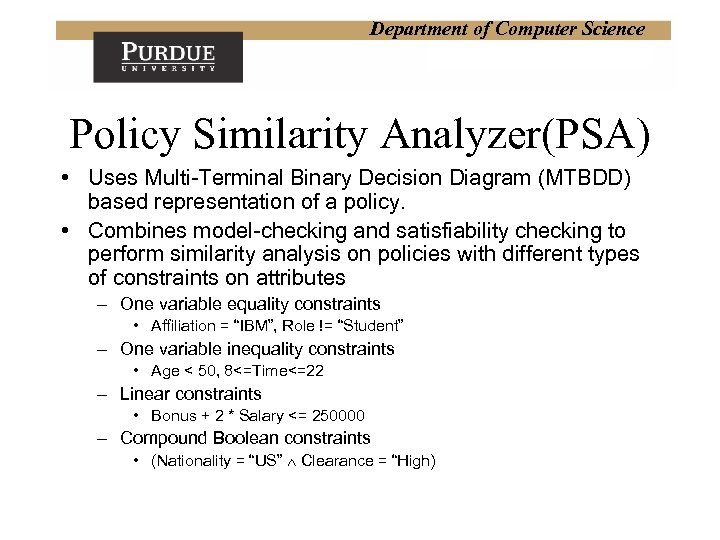
Department of Computer Science Policy Similarity Analyzer(PSA) • Uses Multi-Terminal Binary Decision Diagram (MTBDD) based representation of a policy. • Combines model-checking and satisfiability checking to perform similarity analysis on policies with different types of constraints on attributes – One variable equality constraints • Affiliation = “IBM”, Role != “Student” – One variable inequality constraints • Age < 50, 8<=Time<=22 – Linear constraints • Bonus + 2 * Salary <= 250000 – Compound Boolean constraints • (Nationality = “US” Clearance = “High)
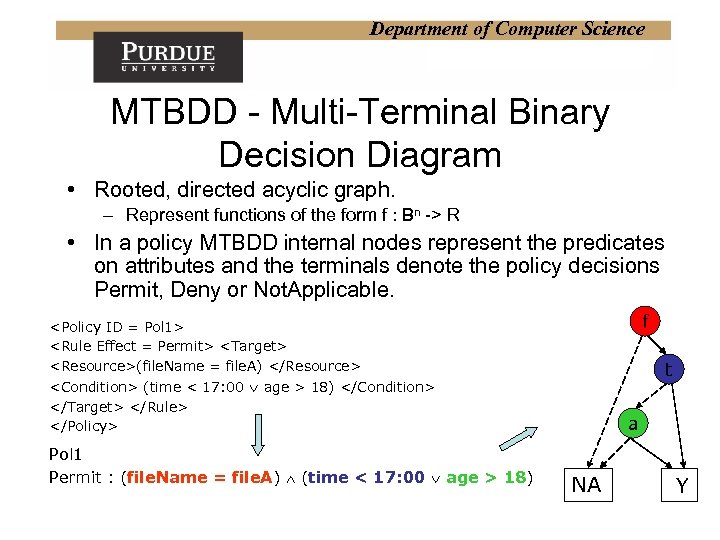
Department of Computer Science MTBDD - Multi-Terminal Binary Decision Diagram • Rooted, directed acyclic graph. – Represent functions of the form f : Bn -> R • In a policy MTBDD internal nodes represent the predicates on attributes and the terminals denote the policy decisions Permit, Deny or Not. Applicable. f <Policy ID = Pol 1> <Rule Effect = Permit> <Target> <Resource>(file. Name = file. A) </Resource> t <Condition> (time < 17: 00 age > 18) </Condition> </Target> </Rule> </Policy> Pol 1 Permit : (file. Name = file. A) (time < 17: 00 age > 18) a NA Y
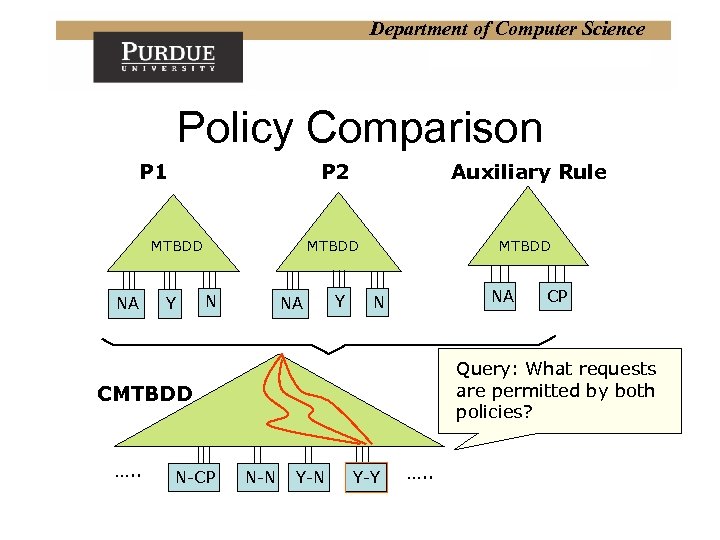
Department of Computer Science Policy Comparison P 2 P 1 MTBDD NA Y Auxiliary Rule MTBDD N NA Y MTBDD NA N Query: What requests are permitted by both policies? CMTBDD …. . N-CP CP N-N Y-Y …. .
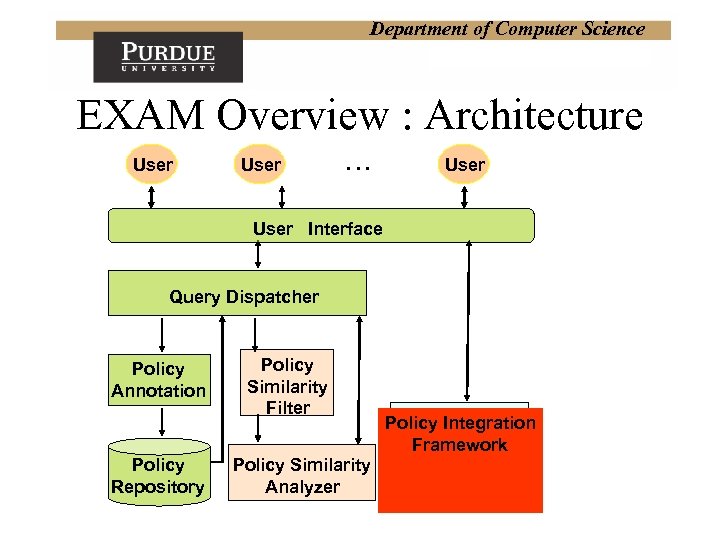
Department of Computer Science EXAM Overview : Architecture User … User Interface Query Dispatcher Policy Annotation Policy Repository Policy Similarity Filter Policy Similarity Analyzer Policy Integration Framework
Department of Computer Science Policy Integration • A Fine-grained Integration Algebra (FIA) – – 3 -valued (Permit, Deny, Not. Applicable) Specify behavior at the granularity of requests and effects Restrict domain of applicability Support expressive policy languages like XACML • Framework for specifying integration constraints and generating integrated policies. – MTBDD based implementation of FIA – Generation of integrated policy in XACML syntax.

Department of Computer Science Fine-grained Integration Algebra (FIA) Vocabulary of attribute names and domains Policy constants Permit policy Deny policy Binary operators Addition Intersection Unary operators Negation Domain Projection

Department of Computer Science FIA - Theoretical Results • Expressivity – FIA can express all XACML policy combining algorithms – FIA can express policy “jumps” – FIA can model closed policies and open policies • Completeness – A completeness notion has been developed, based on the concept of policy combination matrix, and FIA is complete with respect to such notion • Minimality – Identification of the minimal complete subsets of the FIA operators
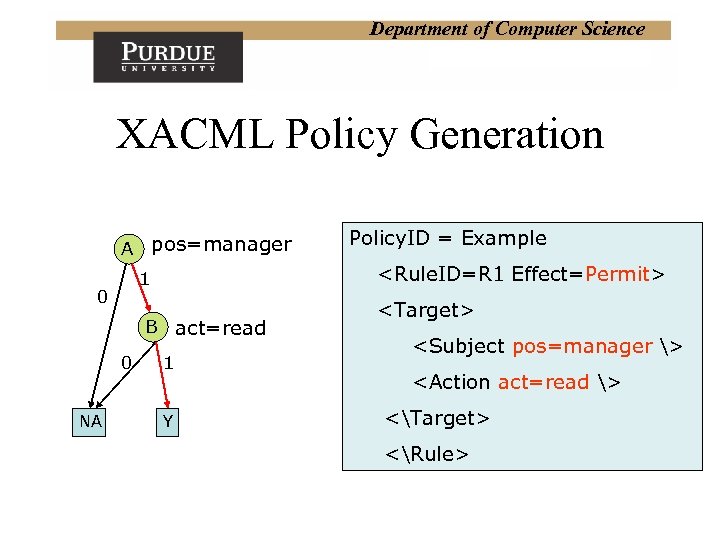
Department of Computer Science XACML Policy Generation A pos=manager <Rule. ID=R 1 Effect=Permit> 1 0 B act=read 0 NA Policy. ID = Example 1 Y <Target> <Subject pos=manager > <Action act=read > <Target> <Rule>

Department of Computer Science Next Steps • Develop visualization techniques for policy analysis results • Extend EXAM with a tool for synonym dictionary management, ontologies
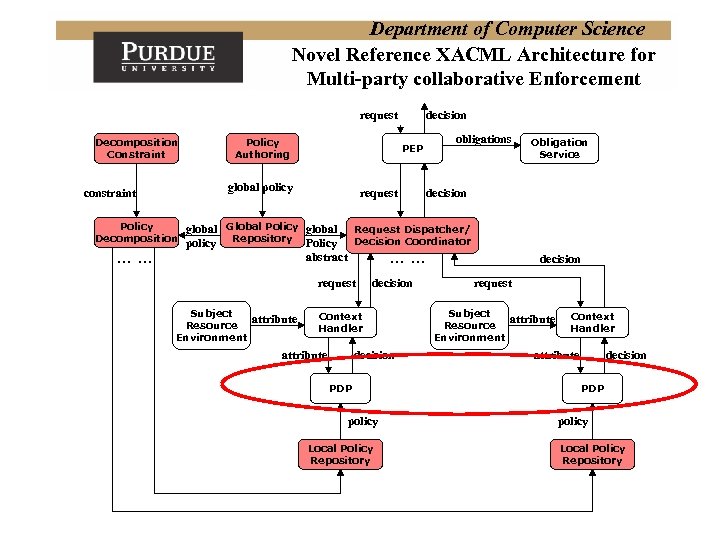
Department of Computer Science Novel Reference XACML Architecture for Multi-party collaborative Enforcement request Decomposition Constraint PEP global policy constraint Policy Decomposition …… Policy Authoring decision request obligations decision global Global Policy global Request Dispatcher/ policy Repository Policy Decision Coordinator abstract …… request Subject Resource Environment attribute decision Context Handler attribute decision PDP policy Local Policy Repository Obligation Service decision request Subject Resource Environment attribute Context Handler attribute decision PDP policy Local Policy Repository

Department of Computer Science Extending XACML for Multi-party collaborative Enforcement • Combining policies is necessary in AISL • XACML has several fixed Policy Combining Algorithms (PCAs) for combining policies – deny-overrides, permit-overrides, first-applicable, only-oneapplicable • We propose the Policy Combining Language (PCL) – allows expression of useful new PCAs • e. g. , weak consensus, strong consensus, weak majority, and strong majority – elegantly handles policy evaluation errors – is fully backward compatible with XACML – enables optimized evaluation using automata theory

Department of Computer Science Next Steps • Develop an implementation of the extended XACML algorithms and of the policy distribution and enforcement algorithms • Investigate cryptographic approaches
13f4841983e852cb5a47a026e68bbbc2.ppt