ca3e021c61a53c7f3a8789ff53a3d9b6.ppt
- Количество слайдов: 88
 Department of Computer and IT Engineering University of Kurdistan Computer Networks II Application Layer By: Dr. Alireza Abdollahpouri
Department of Computer and IT Engineering University of Kurdistan Computer Networks II Application Layer By: Dr. Alireza Abdollahpouri
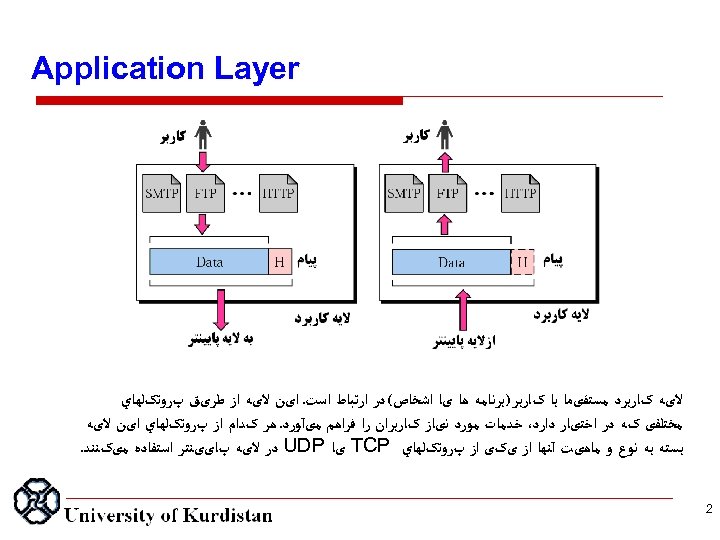 Application Layer ﻻیﻪ کﺎﺭﺑﺮﺩ ﻣﺴﺘﻘیﻤﺎ ﺑﺎ کﺎﺭﺑﺮ )ﺑﺮﻧﺎﻣﻪ ﻫﺎ یﺎ ﺍﺷﺨﺎﺹ( ﺩﺭ ﺍﺭﺗﺒﺎﻁ ﺍﺳﺖ. ﺍیﻦ ﻻیﻪ ﺍﺯ ﻃﺮیﻖ پﺮﻭﺗکﻠﻬﺎﻱ ﻣﺨﺘﻠﻔی کﻪ ﺩﺭ ﺍﺧﺘیﺎﺭ ﺩﺍﺭﺩ، ﺧﺪﻣﺎﺕ ﻣﻮﺭﺩ ﻧیﺎﺯ کﺎﺭﺑﺮﺍﻥ ﺭﺍ ﻓﺮﺍﻫﻢ ﻣیآﻮﺭﺩ. ﻫﺮ کﺪﺍﻡ ﺍﺯ پﺮﻭﺗکﻠﻬﺎﻱ ﺍیﻦ ﻻیﻪ ﺑﺴﺘﻪ ﺑﻪ ﻧﻮﻉ ﻭ ﻣﺎﻫیﺖ آﻨﻬﺎ ﺍﺯ یکی ﺍﺯ پﺮﻭﺗکﻠﻬﺎﻱ TCP یﺎ UDP ﺩﺭ ﻻیﻪ پﺎییﻨﺘﺮ ﺍﺳﺘﻔﺎﺩﻩ ﻣیکﻨﻨﺪ. 2
Application Layer ﻻیﻪ کﺎﺭﺑﺮﺩ ﻣﺴﺘﻘیﻤﺎ ﺑﺎ کﺎﺭﺑﺮ )ﺑﺮﻧﺎﻣﻪ ﻫﺎ یﺎ ﺍﺷﺨﺎﺹ( ﺩﺭ ﺍﺭﺗﺒﺎﻁ ﺍﺳﺖ. ﺍیﻦ ﻻیﻪ ﺍﺯ ﻃﺮیﻖ پﺮﻭﺗکﻠﻬﺎﻱ ﻣﺨﺘﻠﻔی کﻪ ﺩﺭ ﺍﺧﺘیﺎﺭ ﺩﺍﺭﺩ، ﺧﺪﻣﺎﺕ ﻣﻮﺭﺩ ﻧیﺎﺯ کﺎﺭﺑﺮﺍﻥ ﺭﺍ ﻓﺮﺍﻫﻢ ﻣیآﻮﺭﺩ. ﻫﺮ کﺪﺍﻡ ﺍﺯ پﺮﻭﺗکﻠﻬﺎﻱ ﺍیﻦ ﻻیﻪ ﺑﺴﺘﻪ ﺑﻪ ﻧﻮﻉ ﻭ ﻣﺎﻫیﺖ آﻨﻬﺎ ﺍﺯ یکی ﺍﺯ پﺮﻭﺗکﻠﻬﺎﻱ TCP یﺎ UDP ﺩﺭ ﻻیﻪ پﺎییﻨﺘﺮ ﺍﺳﺘﻔﺎﺩﻩ ﻣیکﻨﻨﺪ. 2
 3
3
 Application Layer Protocols ﻣﺸﻬﻮﺭﺗﺮیﻦ پﺮﻭﺗﻜﻠﻬﺎﻱ ﺍﻳﻦ ﻻﻳﻪ ﻋﺒﺎﺭﺗﻨﺪ ﺍﺯ: : FTP پﺮﻭﺗﻜﻠﻲ ﺑﺮﺍﻱ ﺍﻧﺘﻘﺎﻝ ﻓﺎﻳﻞ : HTTP پﺮﻭﺗﻜﻠﻲ ﺑﺮﺍﻱ ﺩﺳﺘﺮﺳﻲ ﺑﻪ ﺻﻔﺤﺎﺕ ﻭﺏ : DNS پﺮﻭﺗﻜﻠﻲ ﺑﺮﺍﻱ ﺗﺮﺟﻤﻪ ﻧﺎﻣﻬﺎﻱ ﻧﻤﺎﺩﻳﻦ ﺑﻪ آﺪﺭﺳﻬﺎﻱ IP : Telnet پﺮﻭﺗﻜﻠﻲ ﺑﺮﺍﻱ ﻭﺭﻭﺩ ﺑﻪ ﺳﻴﺴﺘﻢ ﺍﺯ ﺭﺍﻩ ﺩﻭﺭ SMTP ﻭ 3 : POP پﺮﻭﺗﻜﻠﻬﺎﻳﻲ ﺑﺮﺍﻱ ﺍﺭﺳﺎﻝ ﻭ ﺩﺭﻳﺎﻓﺖ - E mail 4
Application Layer Protocols ﻣﺸﻬﻮﺭﺗﺮیﻦ پﺮﻭﺗﻜﻠﻬﺎﻱ ﺍﻳﻦ ﻻﻳﻪ ﻋﺒﺎﺭﺗﻨﺪ ﺍﺯ: : FTP پﺮﻭﺗﻜﻠﻲ ﺑﺮﺍﻱ ﺍﻧﺘﻘﺎﻝ ﻓﺎﻳﻞ : HTTP پﺮﻭﺗﻜﻠﻲ ﺑﺮﺍﻱ ﺩﺳﺘﺮﺳﻲ ﺑﻪ ﺻﻔﺤﺎﺕ ﻭﺏ : DNS پﺮﻭﺗﻜﻠﻲ ﺑﺮﺍﻱ ﺗﺮﺟﻤﻪ ﻧﺎﻣﻬﺎﻱ ﻧﻤﺎﺩﻳﻦ ﺑﻪ آﺪﺭﺳﻬﺎﻱ IP : Telnet پﺮﻭﺗﻜﻠﻲ ﺑﺮﺍﻱ ﻭﺭﻭﺩ ﺑﻪ ﺳﻴﺴﺘﻢ ﺍﺯ ﺭﺍﻩ ﺩﻭﺭ SMTP ﻭ 3 : POP پﺮﻭﺗﻜﻠﻬﺎﻳﻲ ﺑﺮﺍﻱ ﺍﺭﺳﺎﻝ ﻭ ﺩﺭﻳﺎﻓﺖ - E mail 4
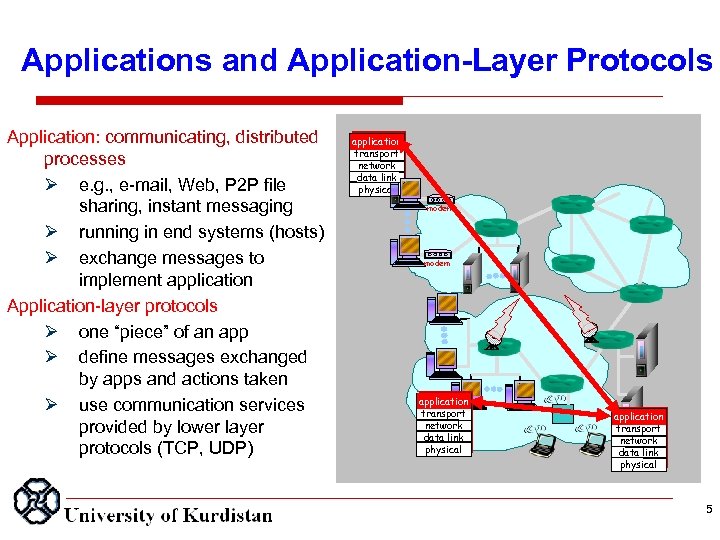 Applications and Application Layer Protocols Application: communicating, distributed processes e. g. , e-mail, Web, P 2 P file sharing, instant messaging running in end systems (hosts) exchange messages to implement application Application-layer protocols one “piece” of an app define messages exchanged by apps and actions taken use communication services provided by lower layer protocols (TCP, UDP) application transport network data link physical modem application transport network data link physical 5
Applications and Application Layer Protocols Application: communicating, distributed processes e. g. , e-mail, Web, P 2 P file sharing, instant messaging running in end systems (hosts) exchange messages to implement application Application-layer protocols one “piece” of an app define messages exchanged by apps and actions taken use communication services provided by lower layer protocols (TCP, UDP) application transport network data link physical modem application transport network data link physical 5
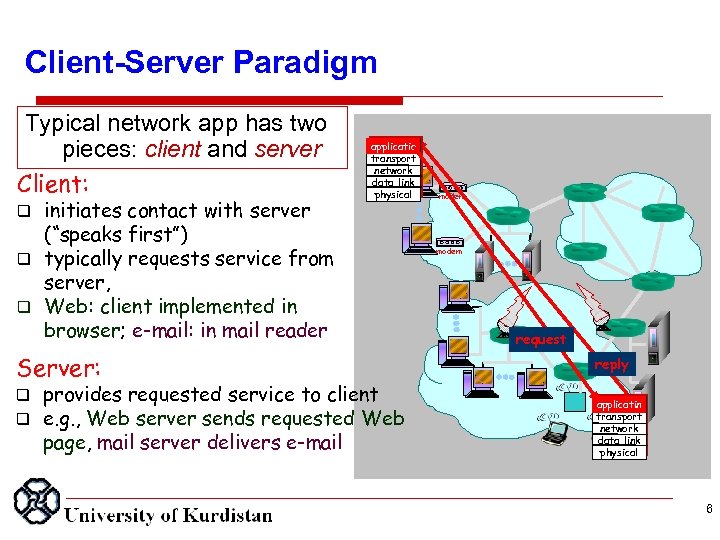 Client Server Paradigm Typical network app has two pieces: client and server Client: initiates contact with server (“speaks first”) q typically requests service from server, q Web: client implemented in browser; e-mail: in mail reader applicatio transport network data link physical modem q Server: q q provides requested service to client e. g. , Web server sends requested Web page, mail server delivers e-mail modem request reply applicatin transport network data link physical 6
Client Server Paradigm Typical network app has two pieces: client and server Client: initiates contact with server (“speaks first”) q typically requests service from server, q Web: client implemented in browser; e-mail: in mail reader applicatio transport network data link physical modem q Server: q q provides requested service to client e. g. , Web server sends requested Web page, mail server delivers e-mail modem request reply applicatin transport network data link physical 6
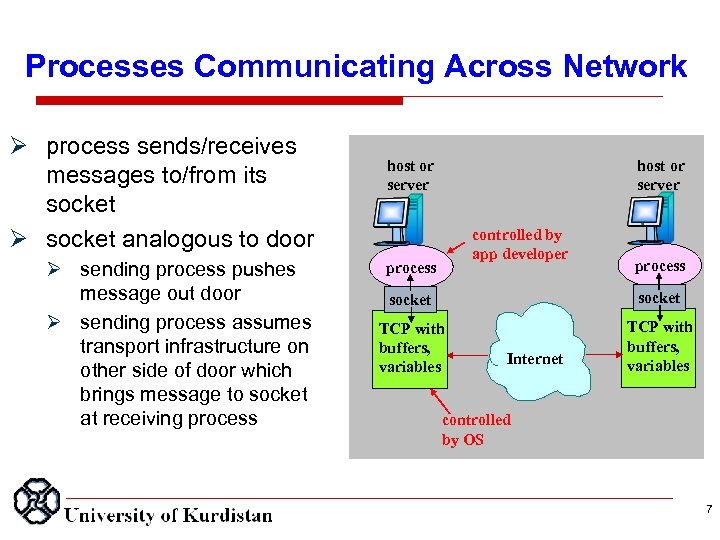 Processes Communicating Across Network process sends/receives messages to/from its socket analogous to door sending process pushes message out door sending process assumes transport infrastructure on other side of door which brings message to socket at receiving process host or server controlled by app developer process socket TCP with buffers, variables Internet controlled by OS 7
Processes Communicating Across Network process sends/receives messages to/from its socket analogous to door sending process pushes message out door sending process assumes transport infrastructure on other side of door which brings message to socket at receiving process host or server controlled by app developer process socket TCP with buffers, variables Internet controlled by OS 7
 What transport service does an app need? Data loss some apps (e. g. , audio) can tolerate some loss other apps (e. g. , file transfer, telnet) require 100% reliable data transfer Timing some apps (e. g. , Internet telephony, interactive games) require low delay to be “effective” Bandwidth q some apps (e. g. , multimedia) require minimum amount of bandwidth to be “effective” q other apps (“elastic apps”) make use of whatever bandwidth they get 8
What transport service does an app need? Data loss some apps (e. g. , audio) can tolerate some loss other apps (e. g. , file transfer, telnet) require 100% reliable data transfer Timing some apps (e. g. , Internet telephony, interactive games) require low delay to be “effective” Bandwidth q some apps (e. g. , multimedia) require minimum amount of bandwidth to be “effective” q other apps (“elastic apps”) make use of whatever bandwidth they get 8
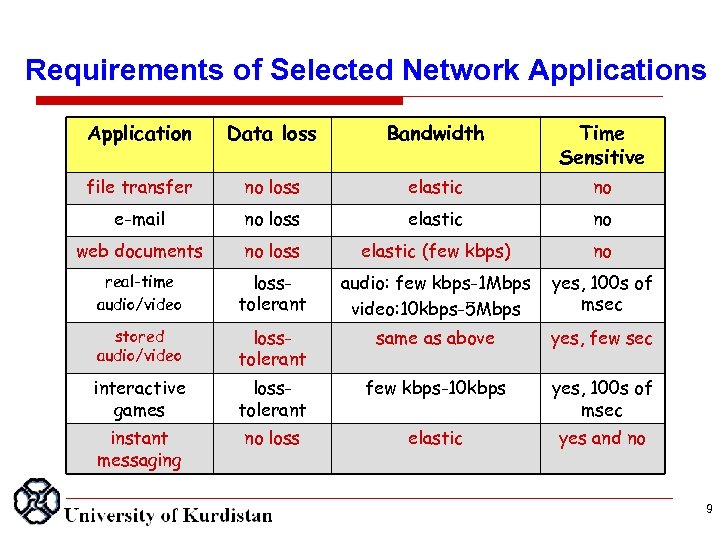 Requirements of Selected Network Applications Application Data loss Bandwidth Time Sensitive file transfer no loss elastic no e-mail no loss elastic no web documents no loss elastic (few kbps) no real-time audio/video losstolerant audio: few kbps-1 Mbps video: 10 kbps-5 Mbps yes, 100 s of msec stored audio/video losstolerant same as above yes, few sec interactive games losstolerant few kbps-10 kbps yes, 100 s of msec instant messaging no loss elastic yes and no 9
Requirements of Selected Network Applications Application Data loss Bandwidth Time Sensitive file transfer no loss elastic no e-mail no loss elastic no web documents no loss elastic (few kbps) no real-time audio/video losstolerant audio: few kbps-1 Mbps video: 10 kbps-5 Mbps yes, 100 s of msec stored audio/video losstolerant same as above yes, few sec interactive games losstolerant few kbps-10 kbps yes, 100 s of msec instant messaging no loss elastic yes and no 9
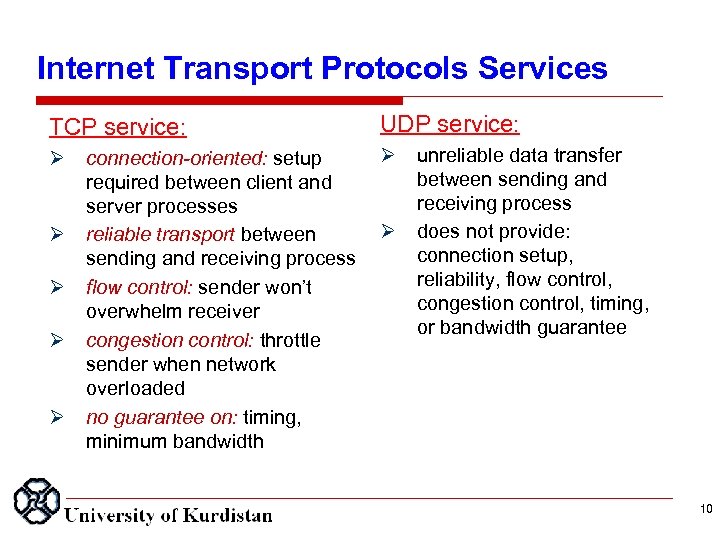 Internet Transport Protocols Services TCP service: UDP service: connection-oriented: setup required between client and server processes reliable transport between sending and receiving process flow control: sender won’t overwhelm receiver congestion control: throttle sender when network overloaded no guarantee on: timing, minimum bandwidth unreliable data transfer between sending and receiving process does not provide: connection setup, reliability, flow control, congestion control, timing, or bandwidth guarantee 10
Internet Transport Protocols Services TCP service: UDP service: connection-oriented: setup required between client and server processes reliable transport between sending and receiving process flow control: sender won’t overwhelm receiver congestion control: throttle sender when network overloaded no guarantee on: timing, minimum bandwidth unreliable data transfer between sending and receiving process does not provide: connection setup, reliability, flow control, congestion control, timing, or bandwidth guarantee 10
![Internet apps: application, transport protocols application-layer underlying transport protocol e-mail SMTP [RFC 2821] TCP Internet apps: application, transport protocols application-layer underlying transport protocol e-mail SMTP [RFC 2821] TCP](https://present5.com/presentation/ca3e021c61a53c7f3a8789ff53a3d9b6/image-11.jpg) Internet apps: application, transport protocols application-layer underlying transport protocol e-mail SMTP [RFC 2821] TCP remote terminal access Telnet [RFC 854] TCP web HTTP [RFC 2616] TCP file transfer FTP [RFC 959] TCP Name server DNS [ RFC 1034] UDP or TCP streaming multimedia proprietary (e. g. , youtube) Typically UDP 11
Internet apps: application, transport protocols application-layer underlying transport protocol e-mail SMTP [RFC 2821] TCP remote terminal access Telnet [RFC 854] TCP web HTTP [RFC 2616] TCP file transfer FTP [RFC 959] TCP Name server DNS [ RFC 1034] UDP or TCP streaming multimedia proprietary (e. g. , youtube) Typically UDP 11
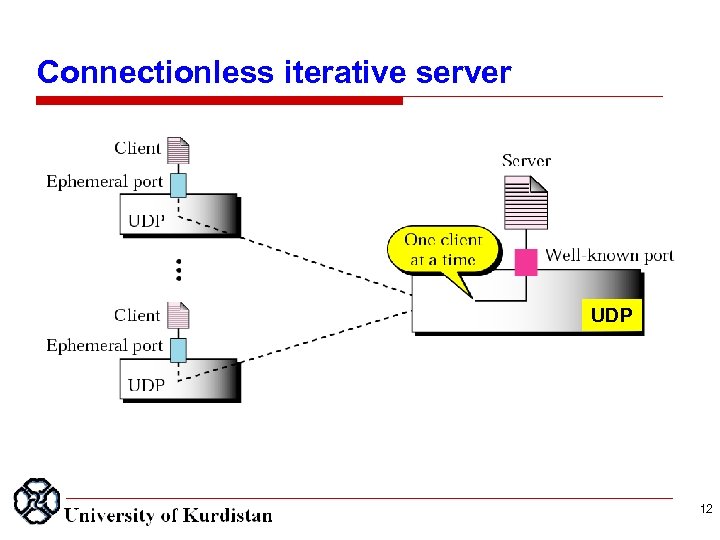 Connectionless iterative server UDP 12
Connectionless iterative server UDP 12
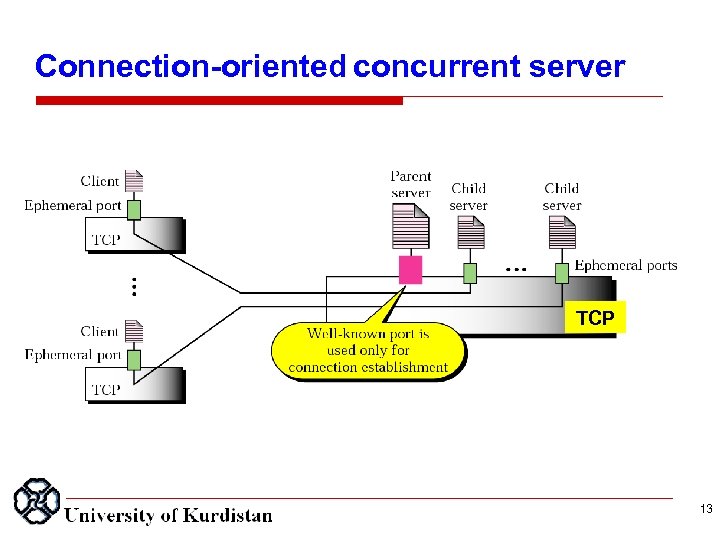 Connection oriented concurrent server TCP 13
Connection oriented concurrent server TCP 13
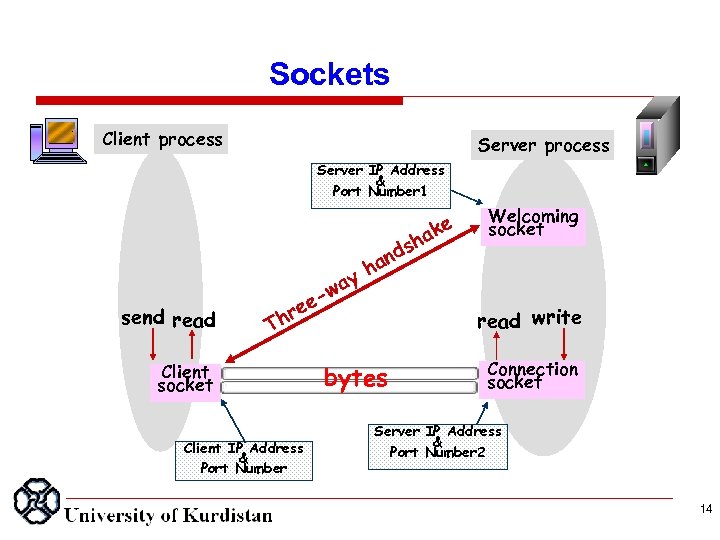 Sockets Client process Server IP Address & Port Number 1 n h ds send read ha y wa ee r Th Client socket bytes Client IP Address & Port Number a ke Welcoming socket read write Connection socket Server IP Address & Port Number 2 14
Sockets Client process Server IP Address & Port Number 1 n h ds send read ha y wa ee r Th Client socket bytes Client IP Address & Port Number a ke Welcoming socket read write Connection socket Server IP Address & Port Number 2 14
 Domain Name System (DNS) 15
Domain Name System (DNS) 15
 ﺩﺭ ﺍﻭﻟﻴﻦ ﺳﺎﻟﻬﺎﻱ ﺭﺍﻩ ﺍﻧﺪﺍﺯﻱ ﺷﺒﻜﻪ ﺍﻳﻨﺘﺮﻧﺖ، ﺭﺍﻩ ﺣﻞ ﺑﺴﻴﺎﺭ ﺳﺎﺩﻩ ﺍﻱ ﺑﺮﺍﻱ ﺗﺮﺟﻤﻪ ﻧﺎﻣﻬﺎﻱ ﻧﻤﺎﺩﻳﻦ ﺑﻪ آﺪﺭﺱ IP ﻭﺟﻮﺩ ﺩﺍﺷﺖ ﻭ آﻦ ﺗﻌﺮﻳﻒ ﺗﻤﺎﻡ ﻧﺎﻣﻬﺎ ﻭ آﺪﺭﺳﻬﺎﻱ IP ﻣﻌﺎﺩﻝ، ﺩﺭ ﻳﻚ ﻓﺎﻳﻞ ﺑﻨﺎﻡ hosts. txt ﺑﻮﺩ. ﺍﻳﻦ ﻓﺎﻳﻞ ﺩﺍﺭﺍﻱ ﺩﻭ ﺳﺘﻮﻥ ﺑﻮﺩ ﻛﻪ ﺩﺭ ﻳﻚ ﻃﺮﻑ آﺪﺭﺱ ﻧﻤﺎﺩﻳﻦ ﻭ ﺩﺭ ﻃﺮﻑ ﺩﻳگﺮ آﺪﺭﺱ IP ﻣﻌﺎﺩﻝ آﻦ ﻧﻮﺷﺘﻪ ﺷﺪﻩ ﺑﻮﺩ. ﺑﻪ ﺩﻟﻴﻞ ﺍﻳﻨﻜﻪ ﺩﺭ آﻦ ﺗﺎﺭﻳﺦ ﺗﻌﺪﺍﺩ آﺪﺭﺳﻬﺎ ﺯﻳﺎﺩ ﻧﺒﻮﺩ، ﺣﺠﻢ چﻨﻴﻦ ﻓﺎﻳﻠﻲ چﻨﺪﺍﻥ ﺑﺰﺭگ ﻧﻤﻲﺷﺪ ﻭ ﻫﺮ ﻣﺎﺷﻴﻦ ﻣﻴﺰﺑﺎﻥ ﻣﻲ ﺗﻮﺍﻧﺴﺖ ﻳﻚ ﻧﺴﺨﻪ ﺍﺯ ﺍﻳﻦ ﻓﺎﻳﻞ ﺭﺍ ﺩﺭ ﺍﺧﺘﻴﺎﺭ ﺩﺍﺷﺘﻪ ﺑﺎﺷﺪ ﻭ ﺳـﺎﻋﺖ 42 ﻫﺮ ﺷﺐ ﺍﻳﻦ ﻓﺎﻳﻞ ﺭﺍ ﺍﺯ ﺭﻭﻱ ﻓﺎﻳﻞ ﻣﺮﺟﻊ ﺗﺎﺯﻩﺳﺎﺯﻱ ﻭ ﺑﻪﺭﻭﺯ ﻣﻲﻛﺮﺩ ﺗﺎ ﻫﺮ گﻮﻧﻪ ﺗﻐﻴﻴﺮ ﺍﺣﺘﻤﺎﻟﻲ ﻭ ﺗﻌﺮﻳﻒ آﺪﺭﺳﻬﺎﻱ ﺟﺪﻳﺪ ﺍﻋﻤﺎﻝ ﺷﻮﺩ. ﺑﺪﻳﻬﻲ ﺍﺳﺖ ﻛﻪ ﺍﻣﺮﻭﺯﻩ ﺑﺎ ﺣﺠﻢ ﻣﻴﻠﻴﻮﻧﻲ آﺪﺭﺳﻬﺎ ﺩﺭ ﺍﻳﻨﺘﺮﻧﺖ، ﺩﺍﺷﺘﻦ ﻳﻚ ﻓﺎﻳﻞ ﻣﺘﻤﺮﻛﺰ ﻭ ﻗﺮﺍﺭ ﺩﺍﺩﻥ ﺗﻤﺎﻡ آﺪﺭﺳﻬﺎ ﻭ ﻣﻌﺎﺩﻝ آﺪﺭﺱ IP ﺩﺭ آﻦ، ﺍﻣﻜﺎﻥ پﺬﻳﺮ ﻧﻴﺴﺖ. ﺭﺍﻩ ﺣﻞ: ﺍﺳﺘﻔﺎﺩﻩ ﺍﺯ یک پﺎیگﺎﻩ ﺩﺍﺩﻩ ﺳﻠﺴﻠﻪ ﻣﺮﺍﺗﺒی ﺗﻮﺯیﻊ ﺷﺪﻩ 61
ﺩﺭ ﺍﻭﻟﻴﻦ ﺳﺎﻟﻬﺎﻱ ﺭﺍﻩ ﺍﻧﺪﺍﺯﻱ ﺷﺒﻜﻪ ﺍﻳﻨﺘﺮﻧﺖ، ﺭﺍﻩ ﺣﻞ ﺑﺴﻴﺎﺭ ﺳﺎﺩﻩ ﺍﻱ ﺑﺮﺍﻱ ﺗﺮﺟﻤﻪ ﻧﺎﻣﻬﺎﻱ ﻧﻤﺎﺩﻳﻦ ﺑﻪ آﺪﺭﺱ IP ﻭﺟﻮﺩ ﺩﺍﺷﺖ ﻭ آﻦ ﺗﻌﺮﻳﻒ ﺗﻤﺎﻡ ﻧﺎﻣﻬﺎ ﻭ آﺪﺭﺳﻬﺎﻱ IP ﻣﻌﺎﺩﻝ، ﺩﺭ ﻳﻚ ﻓﺎﻳﻞ ﺑﻨﺎﻡ hosts. txt ﺑﻮﺩ. ﺍﻳﻦ ﻓﺎﻳﻞ ﺩﺍﺭﺍﻱ ﺩﻭ ﺳﺘﻮﻥ ﺑﻮﺩ ﻛﻪ ﺩﺭ ﻳﻚ ﻃﺮﻑ آﺪﺭﺱ ﻧﻤﺎﺩﻳﻦ ﻭ ﺩﺭ ﻃﺮﻑ ﺩﻳگﺮ آﺪﺭﺱ IP ﻣﻌﺎﺩﻝ آﻦ ﻧﻮﺷﺘﻪ ﺷﺪﻩ ﺑﻮﺩ. ﺑﻪ ﺩﻟﻴﻞ ﺍﻳﻨﻜﻪ ﺩﺭ آﻦ ﺗﺎﺭﻳﺦ ﺗﻌﺪﺍﺩ آﺪﺭﺳﻬﺎ ﺯﻳﺎﺩ ﻧﺒﻮﺩ، ﺣﺠﻢ چﻨﻴﻦ ﻓﺎﻳﻠﻲ چﻨﺪﺍﻥ ﺑﺰﺭگ ﻧﻤﻲﺷﺪ ﻭ ﻫﺮ ﻣﺎﺷﻴﻦ ﻣﻴﺰﺑﺎﻥ ﻣﻲ ﺗﻮﺍﻧﺴﺖ ﻳﻚ ﻧﺴﺨﻪ ﺍﺯ ﺍﻳﻦ ﻓﺎﻳﻞ ﺭﺍ ﺩﺭ ﺍﺧﺘﻴﺎﺭ ﺩﺍﺷﺘﻪ ﺑﺎﺷﺪ ﻭ ﺳـﺎﻋﺖ 42 ﻫﺮ ﺷﺐ ﺍﻳﻦ ﻓﺎﻳﻞ ﺭﺍ ﺍﺯ ﺭﻭﻱ ﻓﺎﻳﻞ ﻣﺮﺟﻊ ﺗﺎﺯﻩﺳﺎﺯﻱ ﻭ ﺑﻪﺭﻭﺯ ﻣﻲﻛﺮﺩ ﺗﺎ ﻫﺮ گﻮﻧﻪ ﺗﻐﻴﻴﺮ ﺍﺣﺘﻤﺎﻟﻲ ﻭ ﺗﻌﺮﻳﻒ آﺪﺭﺳﻬﺎﻱ ﺟﺪﻳﺪ ﺍﻋﻤﺎﻝ ﺷﻮﺩ. ﺑﺪﻳﻬﻲ ﺍﺳﺖ ﻛﻪ ﺍﻣﺮﻭﺯﻩ ﺑﺎ ﺣﺠﻢ ﻣﻴﻠﻴﻮﻧﻲ آﺪﺭﺳﻬﺎ ﺩﺭ ﺍﻳﻨﺘﺮﻧﺖ، ﺩﺍﺷﺘﻦ ﻳﻚ ﻓﺎﻳﻞ ﻣﺘﻤﺮﻛﺰ ﻭ ﻗﺮﺍﺭ ﺩﺍﺩﻥ ﺗﻤﺎﻡ آﺪﺭﺳﻬﺎ ﻭ ﻣﻌﺎﺩﻝ آﺪﺭﺱ IP ﺩﺭ آﻦ، ﺍﻣﻜﺎﻥ پﺬﻳﺮ ﻧﻴﺴﺖ. ﺭﺍﻩ ﺣﻞ: ﺍﺳﺘﻔﺎﺩﻩ ﺍﺯ یک پﺎیگﺎﻩ ﺩﺍﺩﻩ ﺳﻠﺴﻠﻪ ﻣﺮﺍﺗﺒی ﺗﻮﺯیﻊ ﺷﺪﻩ 61
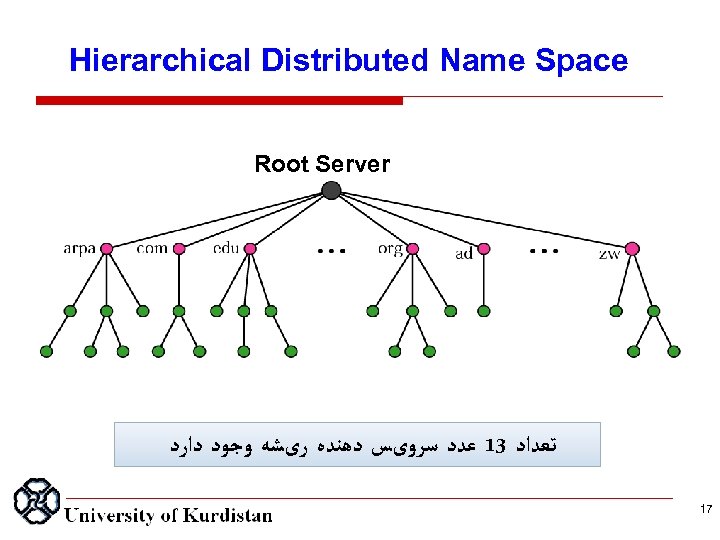 Hierarchical Distributed Name Space Root Server ﺗﻌﺪﺍﺩ 31 ﻋﺪﺩ ﺳﺮﻭیﺲ ﺩﻫﻨﺪﻩ ﺭیﺸﻪ ﻭﺟﻮﺩ ﺩﺍﺭﺩ 17
Hierarchical Distributed Name Space Root Server ﺗﻌﺪﺍﺩ 31 ﻋﺪﺩ ﺳﺮﻭیﺲ ﺩﻫﻨﺪﻩ ﺭیﺸﻪ ﻭﺟﻮﺩ ﺩﺍﺭﺩ 17
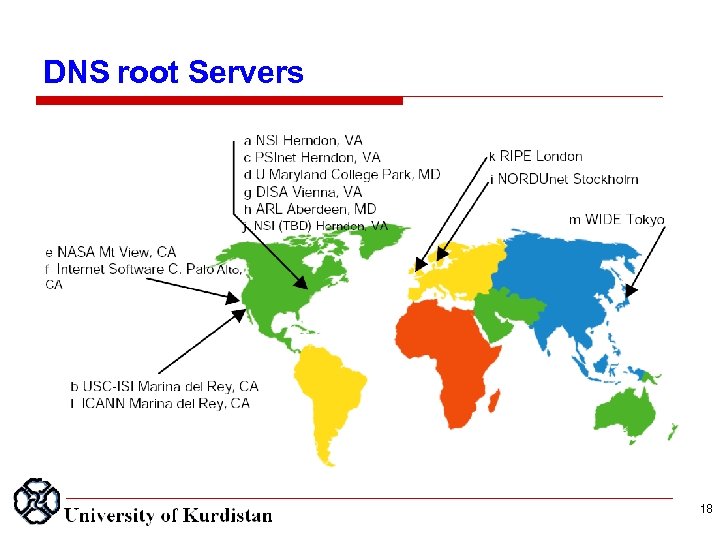 DNS root Servers 18
DNS root Servers 18
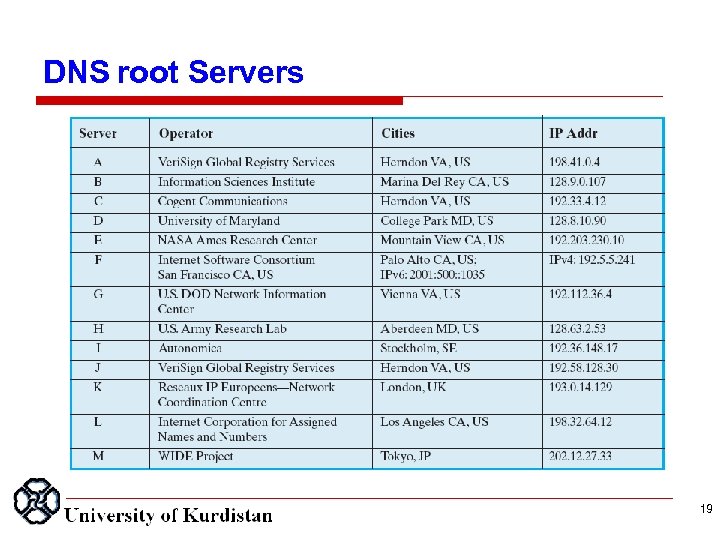 DNS root Servers 19
DNS root Servers 19
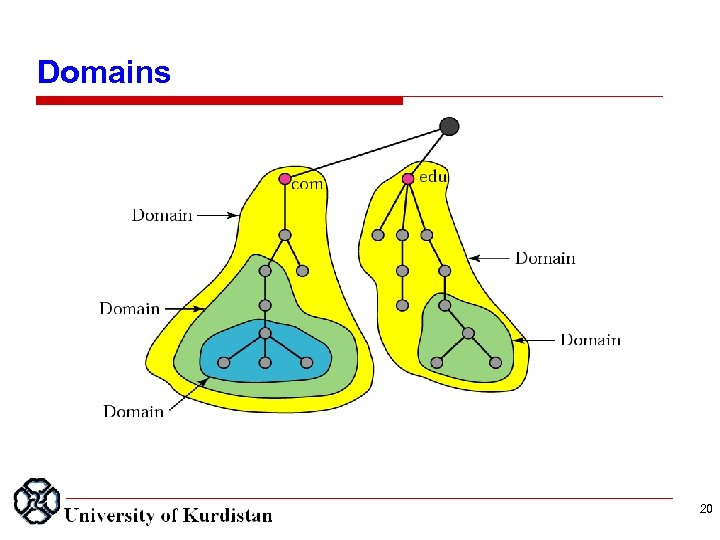 Domains 20
Domains 20
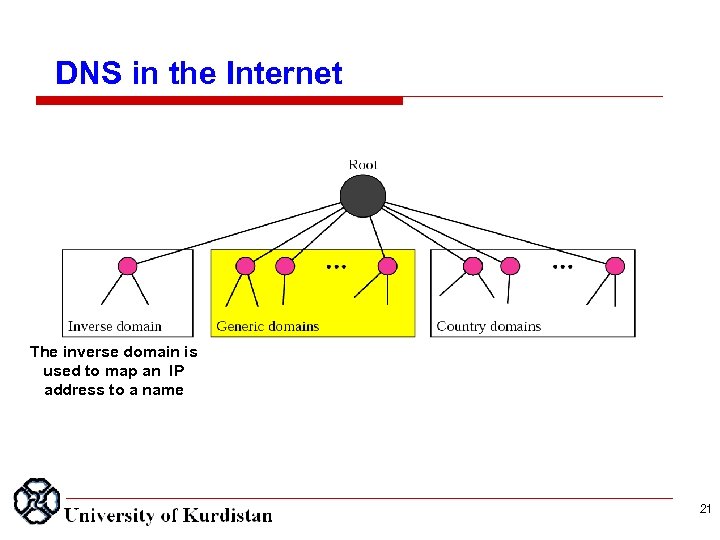 DNS in the Internet The inverse domain is used to map an IP address to a name 21
DNS in the Internet The inverse domain is used to map an IP address to a name 21
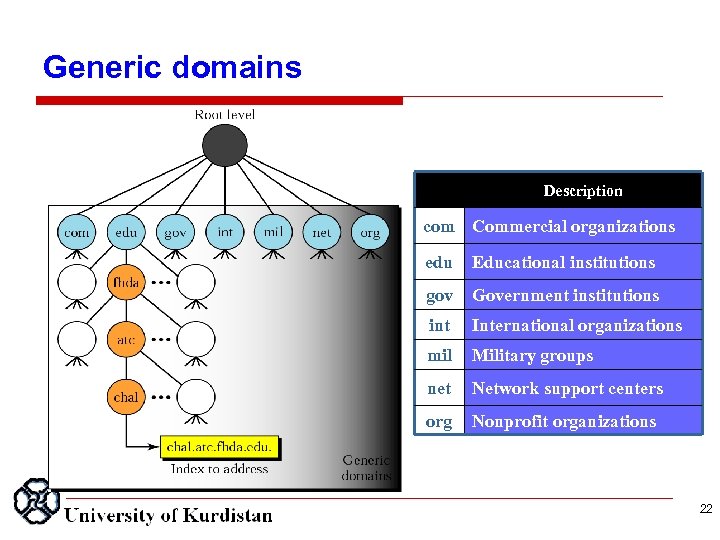 Generic domains Description com Commercial organizations edu Educational institutions gov Government institutions int International organizations mil Military groups net Network support centers org Nonprofit organizations 22
Generic domains Description com Commercial organizations edu Educational institutions gov Government institutions int International organizations mil Military groups net Network support centers org Nonprofit organizations 22
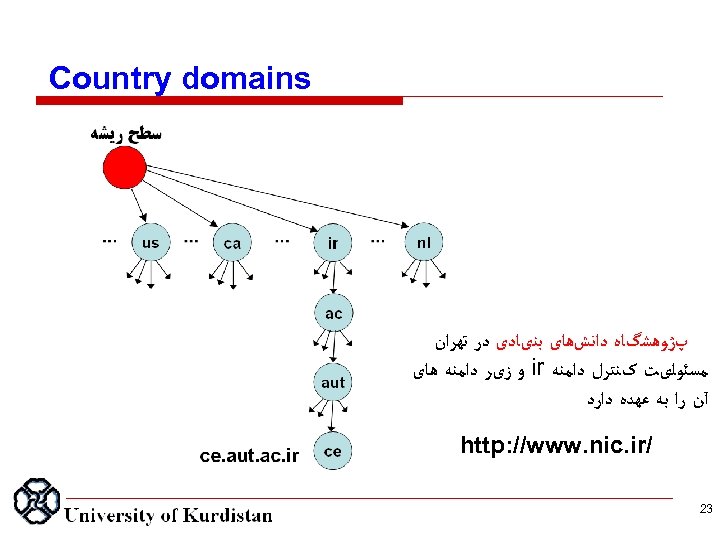 Country domains پژﻮﻫﺸگﺎﻩ ﺩﺍﻧﺶﻫﺎی ﺑﻨیﺎﺩی ﺩﺭ ﺗﻬﺮﺍﻥ ﻣﺴﺌﻮﻟیﺖ کﻨﺘﺮﻝ ﺩﺍﻣﻨﻪ ir ﻭ ﺯیﺮ ﺩﺍﻣﻨﻪ ﻫﺎی آﻦ ﺭﺍ ﺑﻪ ﻋﻬﺪﻩ ﺩﺍﺭﺩ / http: //www. nic. ir 32
Country domains پژﻮﻫﺸگﺎﻩ ﺩﺍﻧﺶﻫﺎی ﺑﻨیﺎﺩی ﺩﺭ ﺗﻬﺮﺍﻥ ﻣﺴﺌﻮﻟیﺖ کﻨﺘﺮﻝ ﺩﺍﻣﻨﻪ ir ﻭ ﺯیﺮ ﺩﺍﻣﻨﻪ ﻫﺎی آﻦ ﺭﺍ ﺑﻪ ﻋﻬﺪﻩ ﺩﺍﺭﺩ / http: //www. nic. ir 32
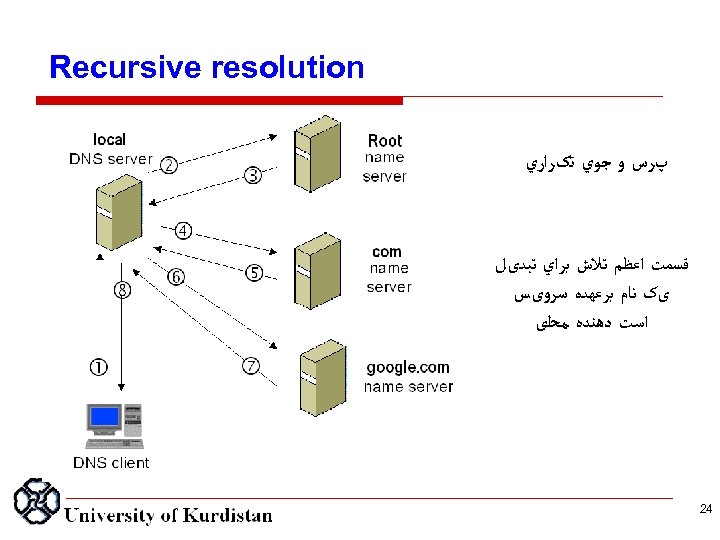 Recursive resolution پﺮﺱ ﻭ ﺟﻮﻱ ﺗکﺮﺍﺭﻱ ﻗﺴﻤﺖ ﺍﻋﻈﻢ ﺗﻼﺵ ﺑﺮﺍﻱ ﺗﺒﺪیﻞ یک ﻧﺎﻡ ﺑﺮﻋﻬﺪﻩ ﺳﺮﻭیﺲ ﺍﺳﺖ ﺩﻫﻨﺪﻩ ﻣﺤﻠی 42
Recursive resolution پﺮﺱ ﻭ ﺟﻮﻱ ﺗکﺮﺍﺭﻱ ﻗﺴﻤﺖ ﺍﻋﻈﻢ ﺗﻼﺵ ﺑﺮﺍﻱ ﺗﺒﺪیﻞ یک ﻧﺎﻡ ﺑﺮﻋﻬﺪﻩ ﺳﺮﻭیﺲ ﺍﺳﺖ ﺩﻫﻨﺪﻩ ﻣﺤﻠی 42
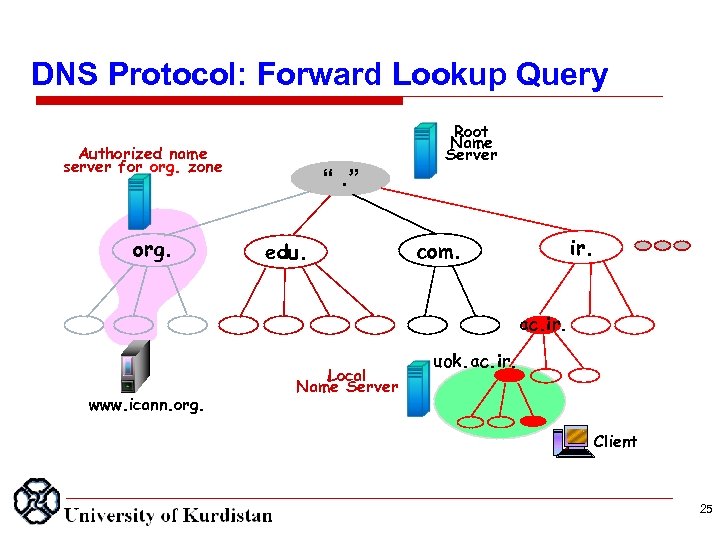 DNS Protocol: Forward Lookup Query IP Address of www. icann. org is 142. 12. 01. 23 Authorized name server for org. zone org. “. ” edu. Root Name Server ir. com. ac. ir. www. icann. org. Local Name Server uok. ac. ir. Client Forward Lookup Query: What is IP Address of www. icann. org 25
DNS Protocol: Forward Lookup Query IP Address of www. icann. org is 142. 12. 01. 23 Authorized name server for org. zone org. “. ” edu. Root Name Server ir. com. ac. ir. www. icann. org. Local Name Server uok. ac. ir. Client Forward Lookup Query: What is IP Address of www. icann. org 25
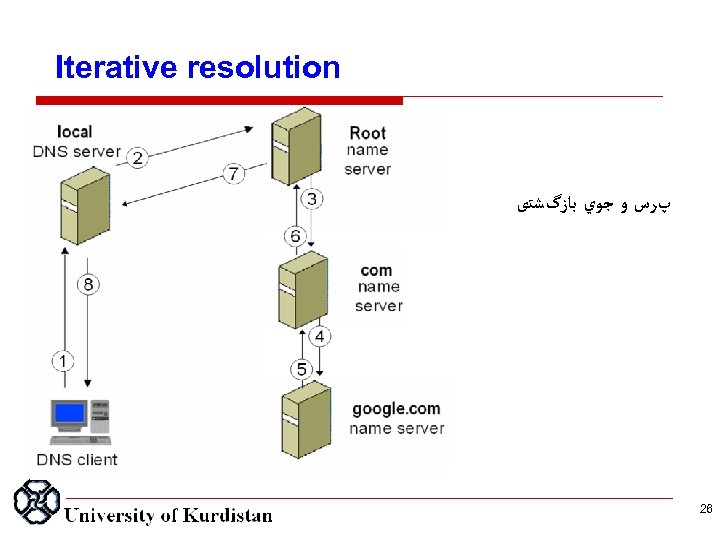 Iterative resolution پﺮﺱ ﻭ ﺟﻮﻱ ﺑﺎﺯگﺸﺘی 26
Iterative resolution پﺮﺱ ﻭ ﺟﻮﻱ ﺑﺎﺯگﺸﺘی 26
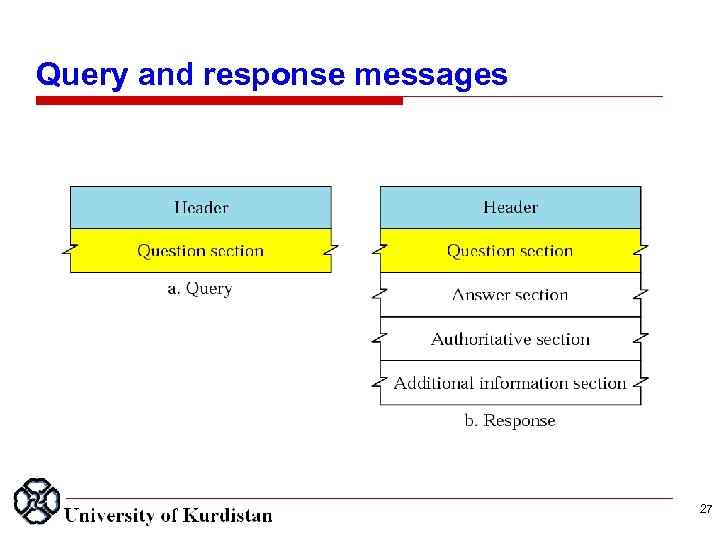 Query and response messages 27
Query and response messages 27
 Note: DNS can use the services of UDP or TCP, using the well-known port 53. 28
Note: DNS can use the services of UDP or TCP, using the well-known port 53. 28
 HTTP and WWW ﻭﺏ ﺟﻬﺎﻥ گﺴﺘﺮ ﻭ پﺮﻭﺗکﻞ ﺍﻧﺘﻘﺎﻝ ﺻﻔﺤﺎﺕ ﺍﺑﺮﻣﺘﻦ 92
HTTP and WWW ﻭﺏ ﺟﻬﺎﻥ گﺴﺘﺮ ﻭ پﺮﻭﺗکﻞ ﺍﻧﺘﻘﺎﻝ ﺻﻔﺤﺎﺕ ﺍﺑﺮﻣﺘﻦ 92
 World Wide Web Distributed services 30
World Wide Web Distributed services 30
 Hypertext 31
Hypertext 31
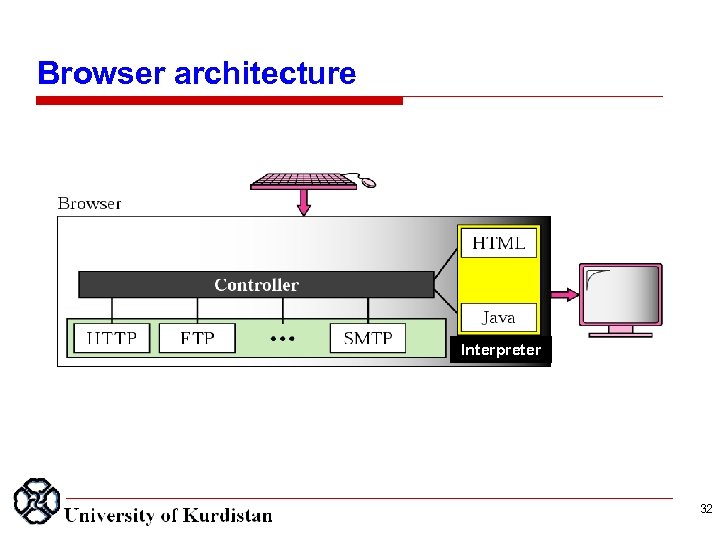 Browser architecture Interpreter 32
Browser architecture Interpreter 32
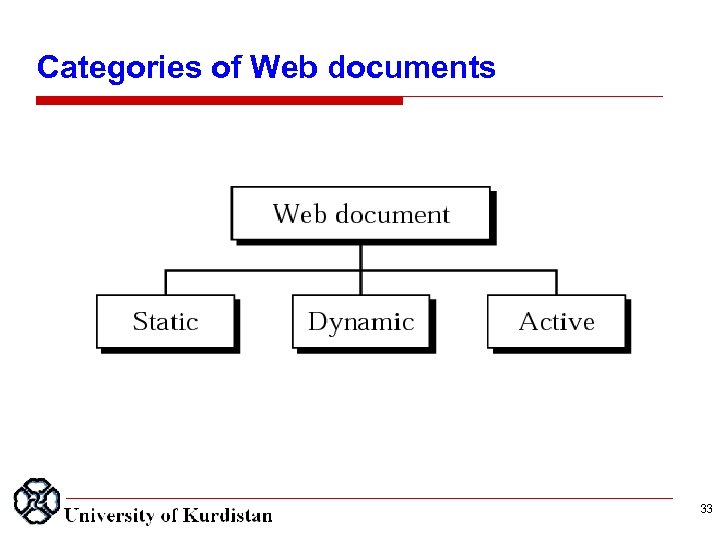 Categories of Web documents 33
Categories of Web documents 33
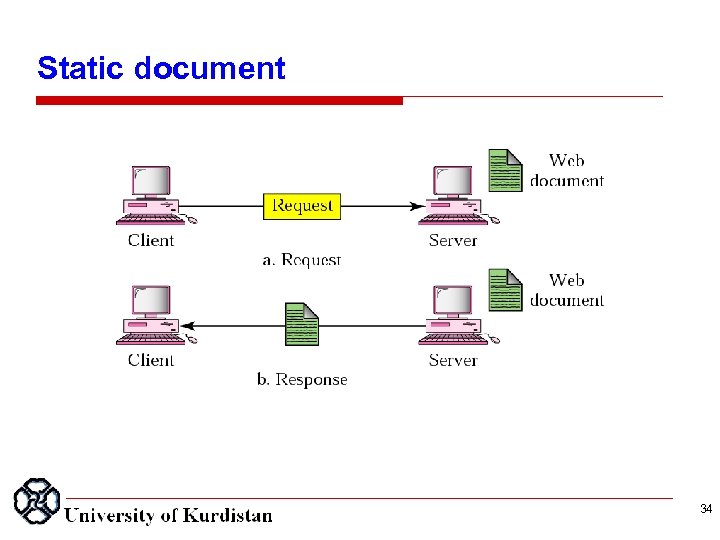 Static document 34
Static document 34
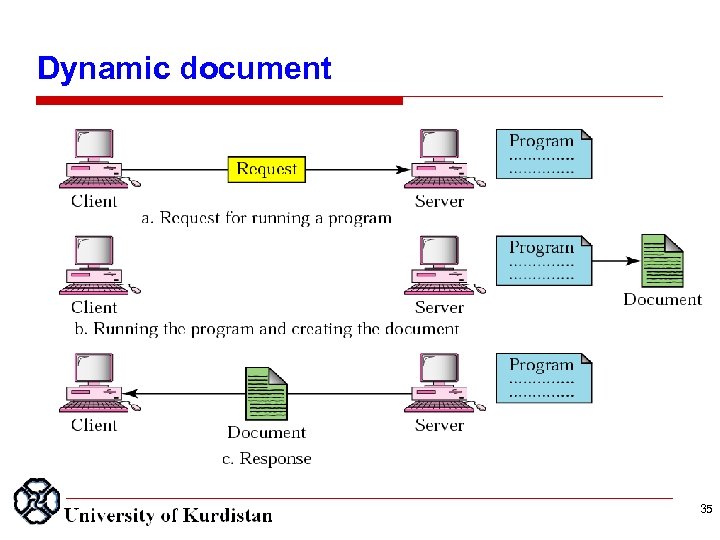 Dynamic document 35
Dynamic document 35
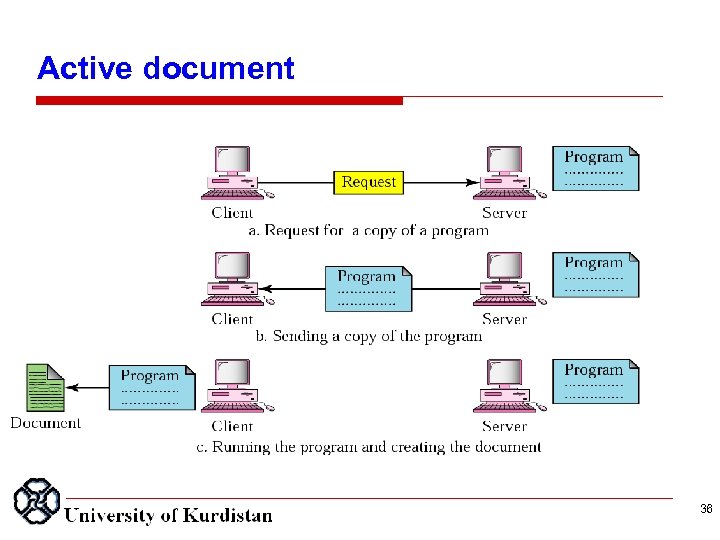 Active document 36
Active document 36
 Web and HTTP Web page consists of objects Object can be HTML file, JPEG image, Java applet, audio file, … Web page consists of base HTML-file which includes several referenced objects Each object is addressable by a URL Example URL: eng. uok. ac. ir/abdollahpouri/index. html host name path name 37
Web and HTTP Web page consists of objects Object can be HTML file, JPEG image, Java applet, audio file, … Web page consists of base HTML-file which includes several referenced objects Each object is addressable by a URL Example URL: eng. uok. ac. ir/abdollahpouri/index. html host name path name 37
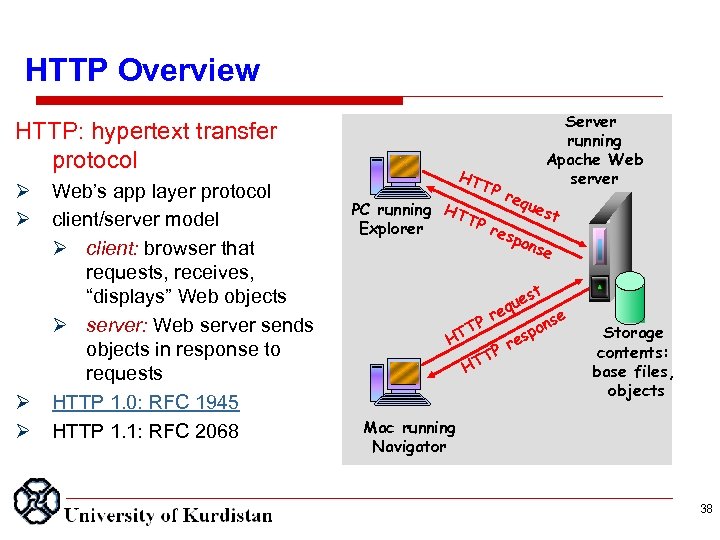 HTTP Overview HTTP: hypertext transfer protocol Web’s app layer protocol client/server model client: browser that requests, receives, “displays” Web objects server: Web server sends objects in response to requests HTTP 1. 0: RFC 1945 HTTP 1. 1: RFC 2068 Server running Apache Web server HT TP req ues PC running HT t TP res Explorer pon se st e qu e Pr T HT n spo se Storage contents: base files, objects Mac running Navigator 38
HTTP Overview HTTP: hypertext transfer protocol Web’s app layer protocol client/server model client: browser that requests, receives, “displays” Web objects server: Web server sends objects in response to requests HTTP 1. 0: RFC 1945 HTTP 1. 1: RFC 2068 Server running Apache Web server HT TP req ues PC running HT t TP res Explorer pon se st e qu e Pr T HT n spo se Storage contents: base files, objects Mac running Navigator 38
 Note: HTTP uses the services of TCP on well -known port 80. 39
Note: HTTP uses the services of TCP on well -known port 80. 39
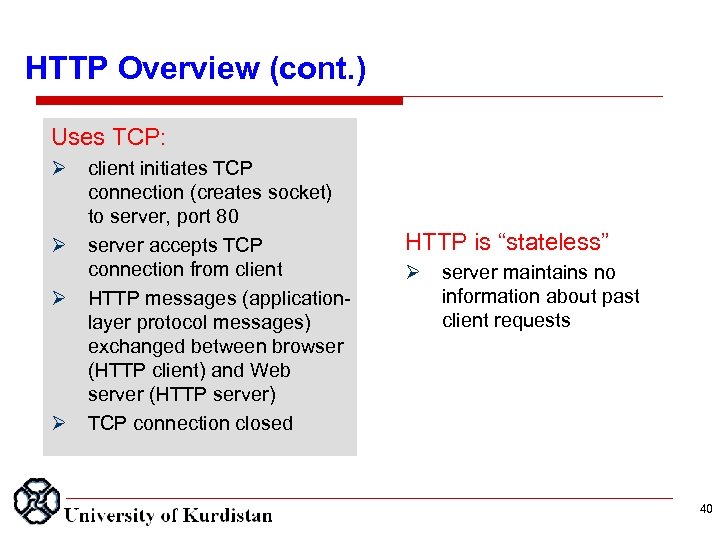 HTTP Overview (cont. ) Uses TCP: client initiates TCP connection (creates socket) to server, port 80 server accepts TCP connection from client HTTP messages (applicationlayer protocol messages) exchanged between browser (HTTP client) and Web server (HTTP server) TCP connection closed HTTP is “stateless” server maintains no information about past client requests 40
HTTP Overview (cont. ) Uses TCP: client initiates TCP connection (creates socket) to server, port 80 server accepts TCP connection from client HTTP messages (applicationlayer protocol messages) exchanged between browser (HTTP client) and Web server (HTTP server) TCP connection closed HTTP is “stateless” server maintains no information about past client requests 40
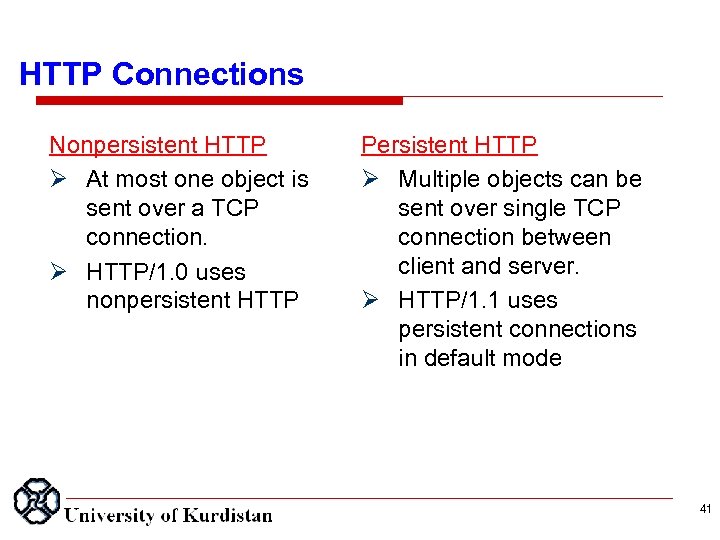 HTTP Connections Nonpersistent HTTP At most one object is sent over a TCP connection. HTTP/1. 0 uses nonpersistent HTTP Persistent HTTP Multiple objects can be sent over single TCP connection between client and server. HTTP/1. 1 uses persistent connections in default mode 41
HTTP Connections Nonpersistent HTTP At most one object is sent over a TCP connection. HTTP/1. 0 uses nonpersistent HTTP Persistent HTTP Multiple objects can be sent over single TCP connection between client and server. HTTP/1. 1 uses persistent connections in default mode 41
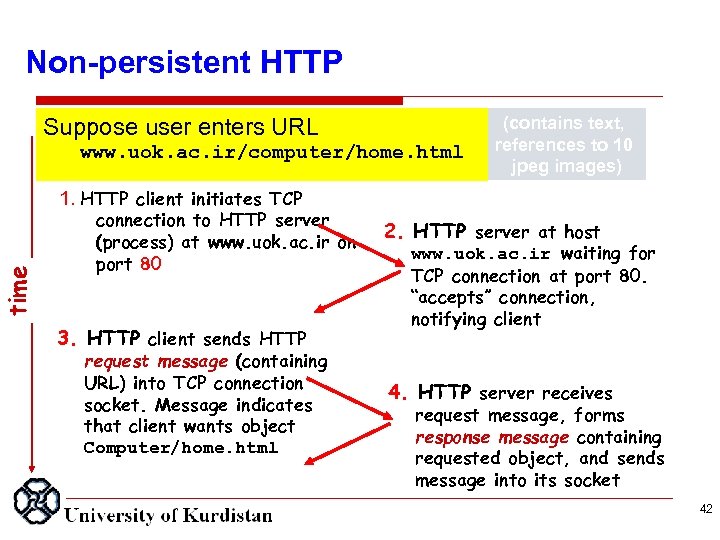 time Non persistent HTTP Suppose user enters URL www. uok. ac. ir/computer/home. html (contains text, references to 10 jpeg images) 1. HTTP client initiates TCP connection to HTTP server (process) at www. uok. ac. ir on port 80 3. HTTP client sends HTTP request message (containing URL) into TCP connection socket. Message indicates that client wants object Computer/home. html 2. HTTP server at host www. uok. ac. ir waiting for TCP connection at port 80. “accepts” connection, notifying client 4. HTTP server receives request message, forms response message containing requested object, and sends message into its socket 42
time Non persistent HTTP Suppose user enters URL www. uok. ac. ir/computer/home. html (contains text, references to 10 jpeg images) 1. HTTP client initiates TCP connection to HTTP server (process) at www. uok. ac. ir on port 80 3. HTTP client sends HTTP request message (containing URL) into TCP connection socket. Message indicates that client wants object Computer/home. html 2. HTTP server at host www. uok. ac. ir waiting for TCP connection at port 80. “accepts” connection, notifying client 4. HTTP server receives request message, forms response message containing requested object, and sends message into its socket 42
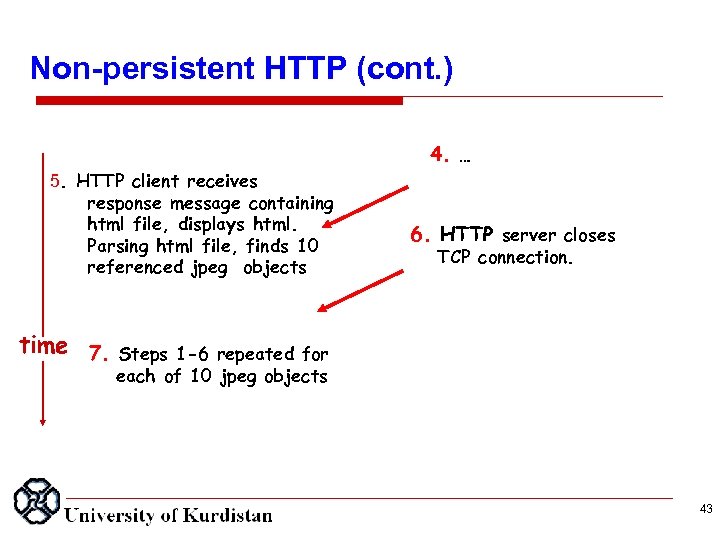 Non persistent HTTP (cont. ) 5. HTTP client receives response message containing html file, displays html. Parsing html file, finds 10 referenced jpeg objects time 7. 4. … 6. HTTP server closes TCP connection. Steps 1 -6 repeated for each of 10 jpeg objects 43
Non persistent HTTP (cont. ) 5. HTTP client receives response message containing html file, displays html. Parsing html file, finds 10 referenced jpeg objects time 7. 4. … 6. HTTP server closes TCP connection. Steps 1 -6 repeated for each of 10 jpeg objects 43
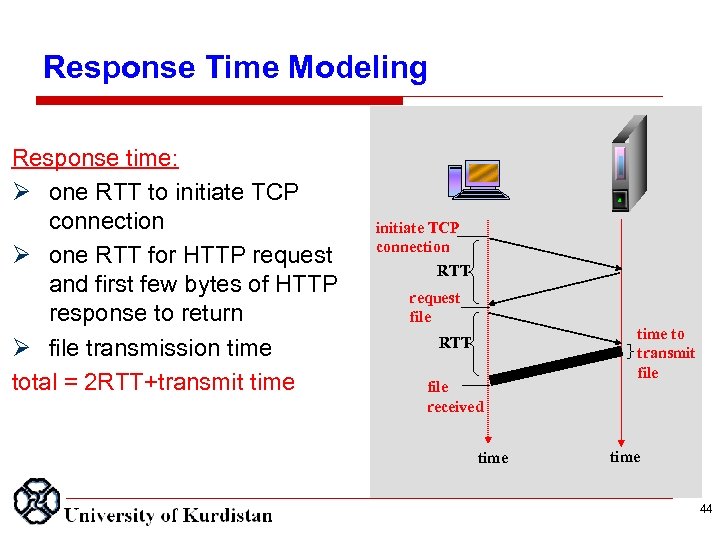 Response Time Modeling Response time: one RTT to initiate TCP connection one RTT for HTTP request and first few bytes of HTTP response to return file transmission time total = 2 RTT+transmit time initiate TCP connection RTT request file RTT file received time to transmit file time 44
Response Time Modeling Response time: one RTT to initiate TCP connection one RTT for HTTP request and first few bytes of HTTP response to return file transmission time total = 2 RTT+transmit time initiate TCP connection RTT request file RTT file received time to transmit file time 44
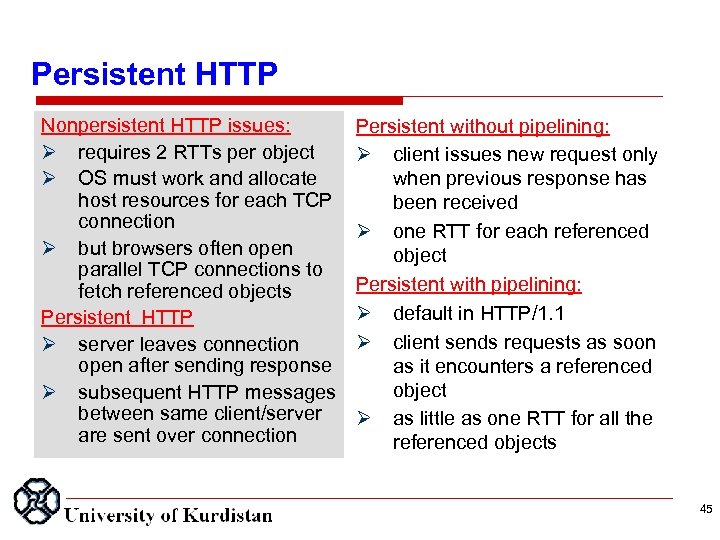 Persistent HTTP Nonpersistent HTTP issues: requires 2 RTTs per object OS must work and allocate host resources for each TCP connection but browsers often open parallel TCP connections to fetch referenced objects Persistent HTTP server leaves connection open after sending response subsequent HTTP messages between same client/server are sent over connection Persistent without pipelining: client issues new request only when previous response has been received one RTT for each referenced object Persistent with pipelining: default in HTTP/1. 1 client sends requests as soon as it encounters a referenced object as little as one RTT for all the referenced objects 45
Persistent HTTP Nonpersistent HTTP issues: requires 2 RTTs per object OS must work and allocate host resources for each TCP connection but browsers often open parallel TCP connections to fetch referenced objects Persistent HTTP server leaves connection open after sending response subsequent HTTP messages between same client/server are sent over connection Persistent without pipelining: client issues new request only when previous response has been received one RTT for each referenced object Persistent with pipelining: default in HTTP/1. 1 client sends requests as soon as it encounters a referenced object as little as one RTT for all the referenced objects 45
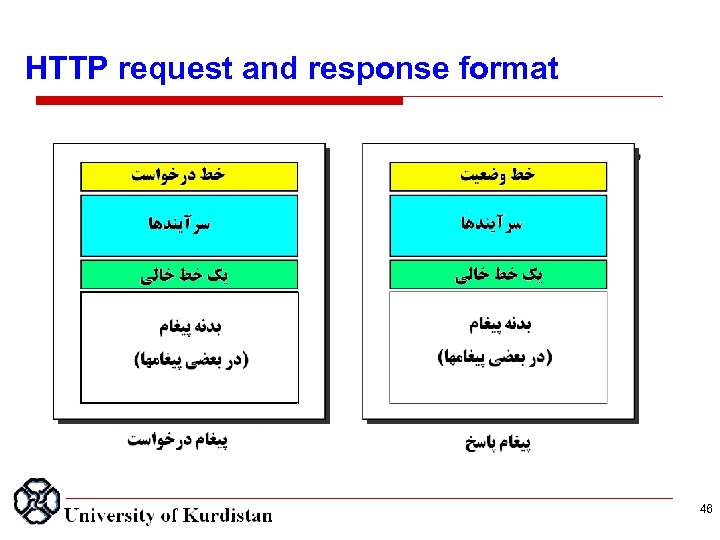 HTTP request and response format 46
HTTP request and response format 46
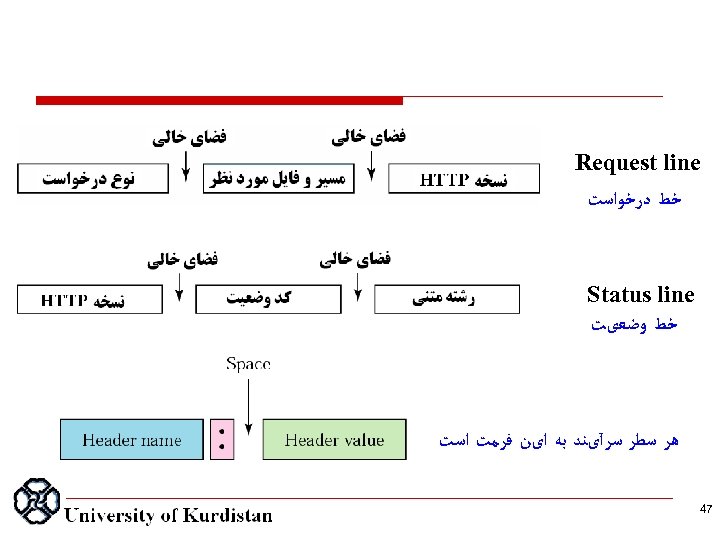 Request line ﺧﻂ ﺩﺭﺧﻮﺍﺳﺖ Status line ﺧﻂ ﻭﺿﻌیﺖ ﻫﺮ ﺳﻄﺮ ﺳﺮآیﻨﺪ ﺑﻪ ﺍیﻦ ﻓﺮﻣﺖ ﺍﺳﺖ 74
Request line ﺧﻂ ﺩﺭﺧﻮﺍﺳﺖ Status line ﺧﻂ ﻭﺿﻌیﺖ ﻫﺮ ﺳﻄﺮ ﺳﺮآیﻨﺪ ﺑﻪ ﺍیﻦ ﻓﺮﻣﺖ ﺍﺳﺖ 74
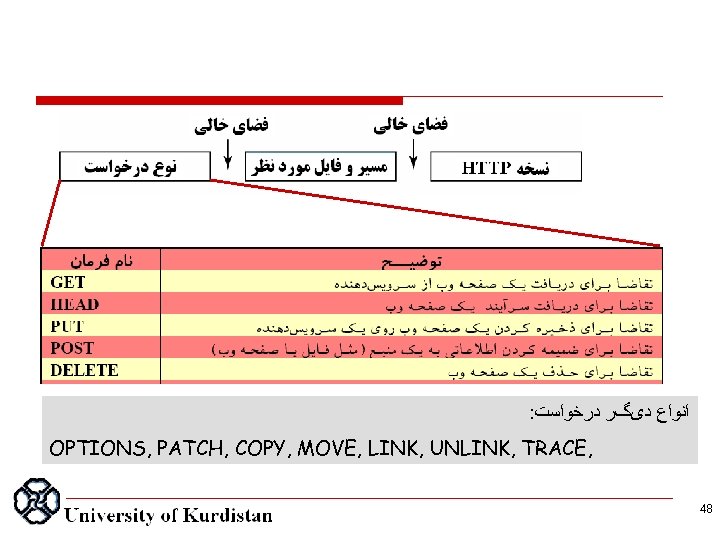 : ﺍﻧﻮﺍﻉ ﺩیگﺮ ﺩﺭﺧﻮﺍﺳﺖ OPTIONS, PATCH, COPY, MOVE, LINK, UNLINK, TRACE, 48
: ﺍﻧﻮﺍﻉ ﺩیگﺮ ﺩﺭﺧﻮﺍﺳﺖ OPTIONS, PATCH, COPY, MOVE, LINK, UNLINK, TRACE, 48
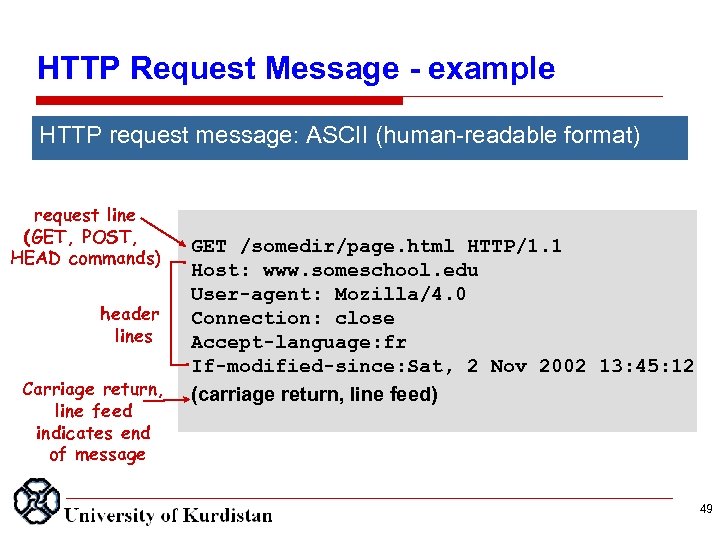 HTTP Request Message example HTTP request message: ASCII (human-readable format) request line (GET, POST, HEAD commands) header lines Carriage return, line feed indicates end of message GET /somedir/page. html HTTP/1. 1 Host: www. someschool. edu User-agent: Mozilla/4. 0 Connection: close Accept-language: fr If-modified-since: Sat, 2 Nov 2002 13: 45: 12 (carriage return, line feed) 49
HTTP Request Message example HTTP request message: ASCII (human-readable format) request line (GET, POST, HEAD commands) header lines Carriage return, line feed indicates end of message GET /somedir/page. html HTTP/1. 1 Host: www. someschool. edu User-agent: Mozilla/4. 0 Connection: close Accept-language: fr If-modified-since: Sat, 2 Nov 2002 13: 45: 12 (carriage return, line feed) 49
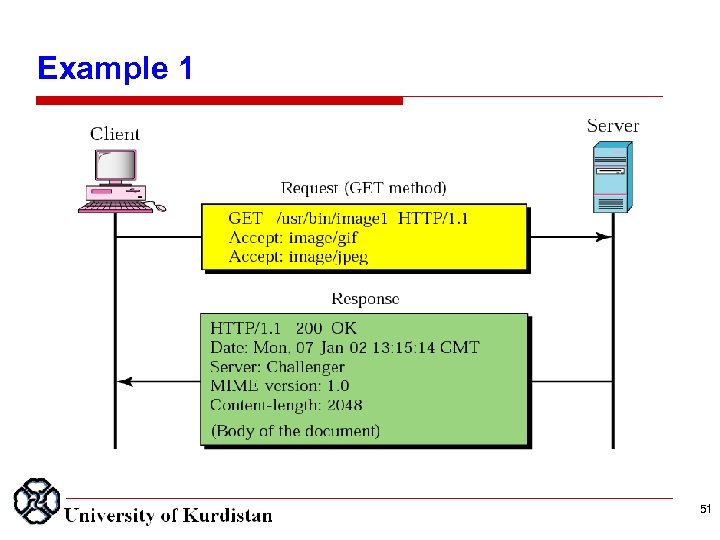
 Example 1 This example retrieves a document. We use the GET method to retrieve an image with the path /usr/bin/image 1. The request line shows the method (GET), the URL, and the HTTP version (1. 1). The header has two lines that show that the client can accept images in GIF and JPEG format. The request does not have a body. The response message contains the status line and four lines of header. The header lines define the date, server, MIME version, and length of the document. The body of the document follows the header (see next slide). 50
Example 1 This example retrieves a document. We use the GET method to retrieve an image with the path /usr/bin/image 1. The request line shows the method (GET), the URL, and the HTTP version (1. 1). The header has two lines that show that the client can accept images in GIF and JPEG format. The request does not have a body. The response message contains the status line and four lines of header. The header lines define the date, server, MIME version, and length of the document. The body of the document follows the header (see next slide). 50
 Example 1 51
Example 1 51
 Example 2 This example retrieves information about a document. We use the HEAD method to retrieve information about an HTML document. The request line shows the method (HEAD), URL, and HTTP version (1. 1). The header is one line showing that the client can accept the document in any format (wild card). The request does not have a body. The response message contains the status line and five lines of header. The header lines define the date, server, MIME version, type of document, and length of the document (see next slide). Note that the response message does not contain a body. 52
Example 2 This example retrieves information about a document. We use the HEAD method to retrieve information about an HTML document. The request line shows the method (HEAD), URL, and HTTP version (1. 1). The header is one line showing that the client can accept the document in any format (wild card). The request does not have a body. The response message contains the status line and five lines of header. The header lines define the date, server, MIME version, type of document, and length of the document (see next slide). Note that the response message does not contain a body. 52
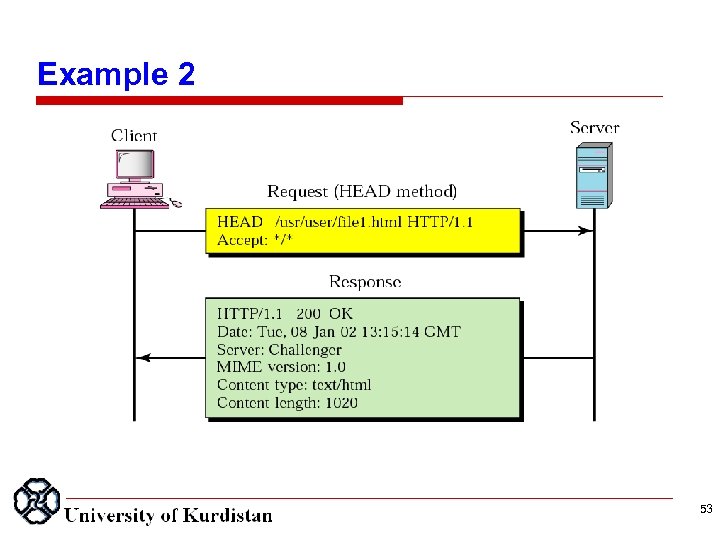 Example 2 53
Example 2 53
 ﻓﺮﺽ ﻛﻨﻴﺪ ﻛﺎﺭﺑﺮ، آﺪﺭﺱ ﺯﻳﺮ ﺭﺍ ﺩﺭ ﻣﺮﻭﺭگﺮ ﺧﻮﺩ ﻭﺍﺭﺩ ﻣﻲﻛﻨﺪ: http: //www. w 3. org/hyper/www/project. html ﻣﺮﻭﺭگﺮ ﺑﺎ ﺗﺤﻠﻴﻞ آﺪﺭﺱ ﻣﺘﻮﺟﻪ ﻣﻴﺸﻮﺩ ﻛﻪ ﺑﺎﻳﺪ ﺗﻘﺎﺿﺎﻱ ﻓﺎﻳﻠﻲ ﺭﺍ ﻃﺒﻖ پﺮﻭﺗﻜﻞ HTTP ﺑﻪ ﺳﻤﺖ ﺳﺮﻭﻳﺲ ﺩﻫﻨﺪﻩ ﺑﻔﺮﺳﺘﺪ. ﻣﺮﺍﺣﻠﻲ ﻛﻪ ﺍﺗﻔﺎﻕ ﻣﻲ ﺍﻓﺘﻨﺪ ﺑﻪ ﺷﺮﺡ ﺯﻳﺮ ﺧﻮﺍﻫﻨﺪ ﺑﻮﺩ: 1( ﻣﺮﻭﺭگﺮ آﺪﺭﺱ ﺭﺍ ﺗﺤﻠﻴﻞ ﻛﺮﺩﻩ ﻭ ﻗﺴﻤﺘﻬﺎﻱ پﺮﻭﺗﻜﻞ، آﺪﺭﺱ ﻧﺎﻡ ﺣﻮﺯﻩ، ﺷﺎﺧﻪ ﻭ ﻧﺎﻡ ﻓﺎﻳﻞ ﺭﺍ ﺍﺯ آﻦ ﺍﺳﺘﺨﺮﺍﺝ ﻣﻴﻜﻨﺪ. 2( ﻣﺮﻭﺭگﺮ ﻳﻚ ﺍﺗﺼﺎﻝ UDP ﺑﺎ پﻮﺭﺕ 35 ﺳﺮﻭﻳﺲ ﺩﻫﻨﺪﻩ DNS ﺑﺮﻗﺮﺍﺭ ﻧﻤﻮﺩﻩ ﻭ ﺗﻘﺎﺿﺎﻱ ﺗﺮﺟﻤﻪ آﺪﺭﺱ ﻧﺎﻡ ﺣﻮﺯﻩ ﺭﺍ ﺑﻪ آﻦ ﺍﺭﺳﺎﻝ ﻣﻲ ﻧﻤﺎﻳﺪ ﺗﺎ آﺪﺭﺱ IP ﻣﺎﺷﻴﻦ ﺳﺮﻭﻳﺲ ﺩﻫﻨﺪﻩ ﺑﺪﺳﺖ آﻴﺪ. ﺩﺭ ﺍﻳﻦ ﻣﺜﺎﻝ ﻣﺮﻭﺭگﺮ ﺗﻘﺎﺿﺎﻱ ﺗﺮﺟﻤﻪ ﻧﺎﻡ www. w 3. org ﺭﺍ ﺑﻪ DNS ﺍﺭﺳﺎﻝ ﻣﻴﻜﻨﺪ. 45
ﻓﺮﺽ ﻛﻨﻴﺪ ﻛﺎﺭﺑﺮ، آﺪﺭﺱ ﺯﻳﺮ ﺭﺍ ﺩﺭ ﻣﺮﻭﺭگﺮ ﺧﻮﺩ ﻭﺍﺭﺩ ﻣﻲﻛﻨﺪ: http: //www. w 3. org/hyper/www/project. html ﻣﺮﻭﺭگﺮ ﺑﺎ ﺗﺤﻠﻴﻞ آﺪﺭﺱ ﻣﺘﻮﺟﻪ ﻣﻴﺸﻮﺩ ﻛﻪ ﺑﺎﻳﺪ ﺗﻘﺎﺿﺎﻱ ﻓﺎﻳﻠﻲ ﺭﺍ ﻃﺒﻖ پﺮﻭﺗﻜﻞ HTTP ﺑﻪ ﺳﻤﺖ ﺳﺮﻭﻳﺲ ﺩﻫﻨﺪﻩ ﺑﻔﺮﺳﺘﺪ. ﻣﺮﺍﺣﻠﻲ ﻛﻪ ﺍﺗﻔﺎﻕ ﻣﻲ ﺍﻓﺘﻨﺪ ﺑﻪ ﺷﺮﺡ ﺯﻳﺮ ﺧﻮﺍﻫﻨﺪ ﺑﻮﺩ: 1( ﻣﺮﻭﺭگﺮ آﺪﺭﺱ ﺭﺍ ﺗﺤﻠﻴﻞ ﻛﺮﺩﻩ ﻭ ﻗﺴﻤﺘﻬﺎﻱ پﺮﻭﺗﻜﻞ، آﺪﺭﺱ ﻧﺎﻡ ﺣﻮﺯﻩ، ﺷﺎﺧﻪ ﻭ ﻧﺎﻡ ﻓﺎﻳﻞ ﺭﺍ ﺍﺯ آﻦ ﺍﺳﺘﺨﺮﺍﺝ ﻣﻴﻜﻨﺪ. 2( ﻣﺮﻭﺭگﺮ ﻳﻚ ﺍﺗﺼﺎﻝ UDP ﺑﺎ پﻮﺭﺕ 35 ﺳﺮﻭﻳﺲ ﺩﻫﻨﺪﻩ DNS ﺑﺮﻗﺮﺍﺭ ﻧﻤﻮﺩﻩ ﻭ ﺗﻘﺎﺿﺎﻱ ﺗﺮﺟﻤﻪ آﺪﺭﺱ ﻧﺎﻡ ﺣﻮﺯﻩ ﺭﺍ ﺑﻪ آﻦ ﺍﺭﺳﺎﻝ ﻣﻲ ﻧﻤﺎﻳﺪ ﺗﺎ آﺪﺭﺱ IP ﻣﺎﺷﻴﻦ ﺳﺮﻭﻳﺲ ﺩﻫﻨﺪﻩ ﺑﺪﺳﺖ آﻴﺪ. ﺩﺭ ﺍﻳﻦ ﻣﺜﺎﻝ ﻣﺮﻭﺭگﺮ ﺗﻘﺎﺿﺎﻱ ﺗﺮﺟﻤﻪ ﻧﺎﻡ www. w 3. org ﺭﺍ ﺑﻪ DNS ﺍﺭﺳﺎﻝ ﻣﻴﻜﻨﺪ. 45
 3( DNS ﺩﺭ پﺎﺳﺦ، آﺪﺭﺱ IP ﻣﻌﺎﺩﻝ ﺑﺎ ﻧﺎﻡ ﺣﻮﺯﻩ ﺭﺍ ﺑﺮﻣﻴگﺮﺩﺍﻧﺪ. ﻓﺮﺽ ﻛﻨﻴﺪ ﺩﺭ ﺍﻳﻦ ﻣﺜﺎﻝ DNS آﺪﺭﺱ IP ﺭﺍ 13. 25. 03. 821ﺑﺮگﺮﺩﺍﻧﺪﻩ ﺍﺳﺖ. 4( ﻣﺮﻭﺭگﺮ ﻳﻚ ﺍﺭﺗﺒﺎﻁ TCP ﺑﺎ آﺪﺭﺱ 13. 25. 03. 821ﻭ پﻮﺭﺕ 08 ﺑﺮﻗﺮﺍﺭ ﻣﻴﻜﻨﺪ. 5( پﺲ ﺍﺯ ﺑﺮﻗﺮﺍﺭﻱ ﺍﺭﺗﺒﺎﻁ، ﻳﻚ پﻴﻐﺎﻡ ﺩﺭﺧﻮﺍﺳﺖ ﺑﻪ ﺻﻮﺭﺕ ﺯﻳﺮ ﺑﻪ ﺳﻤﺖ ﺳﺮﻭﻳﺲ ﺩﻫﻨﺪﻩ ﺍﺭﺳﺎﻝ ﻣﻴﺸﻮﺩ: ” 1. 1/ “GET /hyper/www/project. html http 6( ﺳﺮﻭﻳﺲ ﺩﻫﻨﺪﻩ ﺍﻳﻦ ﺭﺷﺘﻪ ﺭﺍ ﺩﺭﻳﺎﻓﺖ ﻭ پﺲ ﺍﺯ پﺮﺩﺍﺯﺵ آﻦ، ﻓﺎﻳﻞ project. html ﺭﺍ ﺍﺯ ﺷﺎﺧﻪ / /hyper/www ﺍﺳﺘﺨﺮﺍﺝ ﻛﺮﺩﻩ ﻭ ﺑﺮﺍﻱ ﻣﺮﻭﺭگﺮ ﺍﺭﺳﺎﻝ ﻣﻲ ﻧﻤﺎﻳﺪ. 7( ﻣﺮﻭﺭگﺮ ﻓﺎﻳﻞ ﺭﺍ ﺩﺭﻳﺎﻓﺖ ﻛﺮﺩﻩ ﻭ پﺲ ﺍﺯ ﺧﺎﺗﻤﻪ ﺩﺭﻳﺎﻓﺖ ﺍﺭﺗﺒﺎﻁ TCP ﺭﺍ ﻗﻄﻊ ﻣﻴﻜﻨﺪ. 8( ﻣﺮﻭﺭگﺮ ﻓﺎﻳﻞ ﺍﺑﺮﻣﺘﻨﻲ ﺭﺍ ﺗﻔﺴﻴﺮ ﻛﺮﺩﻩ ﻭ آﻨﺮﺍ ﺭﻭﻱ ﺧﺮﻭﺟﻲ ﻧﻤﺎﻳﺶ ﻣﻴﺪﻫﺪ. 1 ﺗﺎ 8 ﺭﺍ 9( ﺍگﺮ ﻓﺎﻳﻞ ﺍﺑﺮﻣﺘﻨﻲ ﺩﺭ ﺟﺎﻳﻲ ﺩﺍﺭﺍﻱ ﺻﺪﺍ ﻳﺎ ﺗﺼﻮﻳﺮ ﺑﺎﺷﺪ ﺑﻪ ﺍﺯﺍﻱ ﺗﻚ ﺗﻚ آﻨﻬﺎ ﻣﺮﺍﺣﻞ ﺗﻜﺮﺍﺭ ﻧﻤﻮﺩﻩ ﻭ آﻨﻬﺎ ﺭﺍ ﺑﺘﺮﺗﻴﺐ ﺩﺭﻳﺎﻓﺖ ﻣﻲ ﻛﻨﺪ )ﺑﺎ ﻓﺮﺽ (persistent http 55
3( DNS ﺩﺭ پﺎﺳﺦ، آﺪﺭﺱ IP ﻣﻌﺎﺩﻝ ﺑﺎ ﻧﺎﻡ ﺣﻮﺯﻩ ﺭﺍ ﺑﺮﻣﻴگﺮﺩﺍﻧﺪ. ﻓﺮﺽ ﻛﻨﻴﺪ ﺩﺭ ﺍﻳﻦ ﻣﺜﺎﻝ DNS آﺪﺭﺱ IP ﺭﺍ 13. 25. 03. 821ﺑﺮگﺮﺩﺍﻧﺪﻩ ﺍﺳﺖ. 4( ﻣﺮﻭﺭگﺮ ﻳﻚ ﺍﺭﺗﺒﺎﻁ TCP ﺑﺎ آﺪﺭﺱ 13. 25. 03. 821ﻭ پﻮﺭﺕ 08 ﺑﺮﻗﺮﺍﺭ ﻣﻴﻜﻨﺪ. 5( پﺲ ﺍﺯ ﺑﺮﻗﺮﺍﺭﻱ ﺍﺭﺗﺒﺎﻁ، ﻳﻚ پﻴﻐﺎﻡ ﺩﺭﺧﻮﺍﺳﺖ ﺑﻪ ﺻﻮﺭﺕ ﺯﻳﺮ ﺑﻪ ﺳﻤﺖ ﺳﺮﻭﻳﺲ ﺩﻫﻨﺪﻩ ﺍﺭﺳﺎﻝ ﻣﻴﺸﻮﺩ: ” 1. 1/ “GET /hyper/www/project. html http 6( ﺳﺮﻭﻳﺲ ﺩﻫﻨﺪﻩ ﺍﻳﻦ ﺭﺷﺘﻪ ﺭﺍ ﺩﺭﻳﺎﻓﺖ ﻭ پﺲ ﺍﺯ پﺮﺩﺍﺯﺵ آﻦ، ﻓﺎﻳﻞ project. html ﺭﺍ ﺍﺯ ﺷﺎﺧﻪ / /hyper/www ﺍﺳﺘﺨﺮﺍﺝ ﻛﺮﺩﻩ ﻭ ﺑﺮﺍﻱ ﻣﺮﻭﺭگﺮ ﺍﺭﺳﺎﻝ ﻣﻲ ﻧﻤﺎﻳﺪ. 7( ﻣﺮﻭﺭگﺮ ﻓﺎﻳﻞ ﺭﺍ ﺩﺭﻳﺎﻓﺖ ﻛﺮﺩﻩ ﻭ پﺲ ﺍﺯ ﺧﺎﺗﻤﻪ ﺩﺭﻳﺎﻓﺖ ﺍﺭﺗﺒﺎﻁ TCP ﺭﺍ ﻗﻄﻊ ﻣﻴﻜﻨﺪ. 8( ﻣﺮﻭﺭگﺮ ﻓﺎﻳﻞ ﺍﺑﺮﻣﺘﻨﻲ ﺭﺍ ﺗﻔﺴﻴﺮ ﻛﺮﺩﻩ ﻭ آﻨﺮﺍ ﺭﻭﻱ ﺧﺮﻭﺟﻲ ﻧﻤﺎﻳﺶ ﻣﻴﺪﻫﺪ. 1 ﺗﺎ 8 ﺭﺍ 9( ﺍگﺮ ﻓﺎﻳﻞ ﺍﺑﺮﻣﺘﻨﻲ ﺩﺭ ﺟﺎﻳﻲ ﺩﺍﺭﺍﻱ ﺻﺪﺍ ﻳﺎ ﺗﺼﻮﻳﺮ ﺑﺎﺷﺪ ﺑﻪ ﺍﺯﺍﻱ ﺗﻚ ﺗﻚ آﻨﻬﺎ ﻣﺮﺍﺣﻞ ﺗﻜﺮﺍﺭ ﻧﻤﻮﺩﻩ ﻭ آﻨﻬﺎ ﺭﺍ ﺑﺘﺮﺗﻴﺐ ﺩﺭﻳﺎﻓﺖ ﻣﻲ ﻛﻨﺪ )ﺑﺎ ﻓﺮﺽ (persistent http 55
 SMTP 3 and POP پﺮﻭﺗکﻠﻬﺎی ﺍﻧﺘﻘﺎﻝ ﻭ ﺩﺭیﺎﻓﺖ ﺍیﻤیﻞ 65
SMTP 3 and POP پﺮﻭﺗکﻠﻬﺎی ﺍﻧﺘﻘﺎﻝ ﻭ ﺩﺭیﺎﻓﺖ ﺍیﻤیﻞ 65
 Electronic Mail Sending/Receiving Mail Addresses User Agent MIME Mail Transfer Agent Mail Access Protocols
Electronic Mail Sending/Receiving Mail Addresses User Agent MIME Mail Transfer Agent Mail Access Protocols
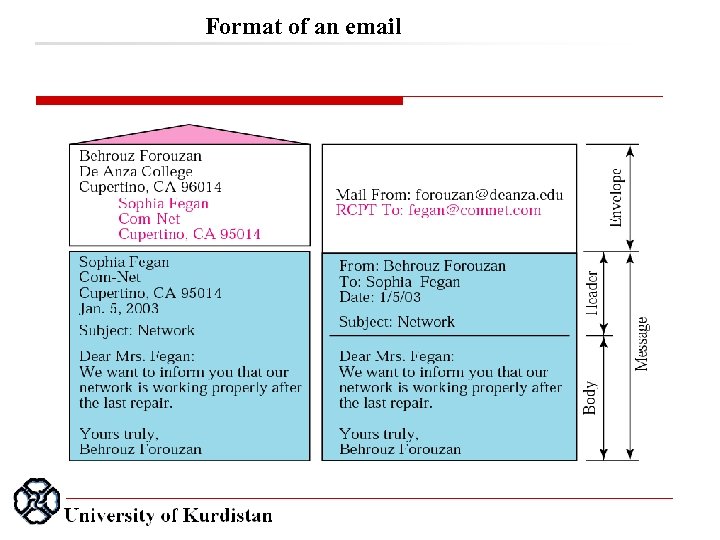 Format of an email
Format of an email
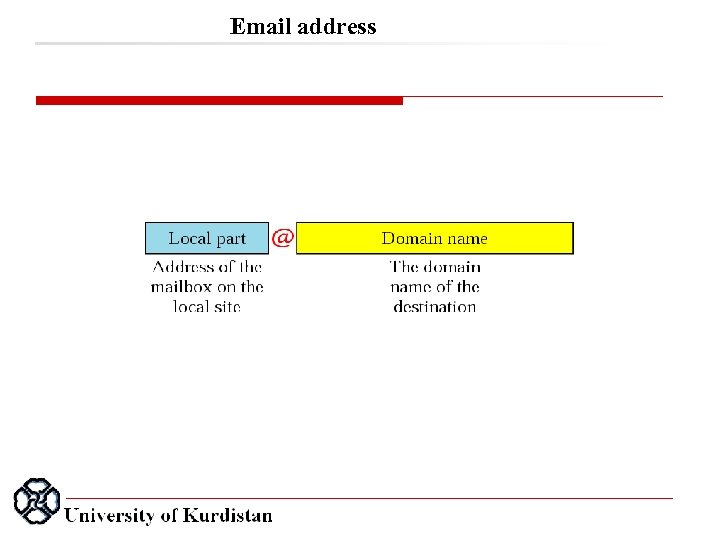 Email address
Email address
 User agent
User agent
 Note: Some examples of command-driven user agents are mail, pine, and elm.
Note: Some examples of command-driven user agents are mail, pine, and elm.
 Note: Some examples of GUI-based user agents are Eudora, Outlook, and Netscape.
Note: Some examples of GUI-based user agents are Eudora, Outlook, and Netscape.
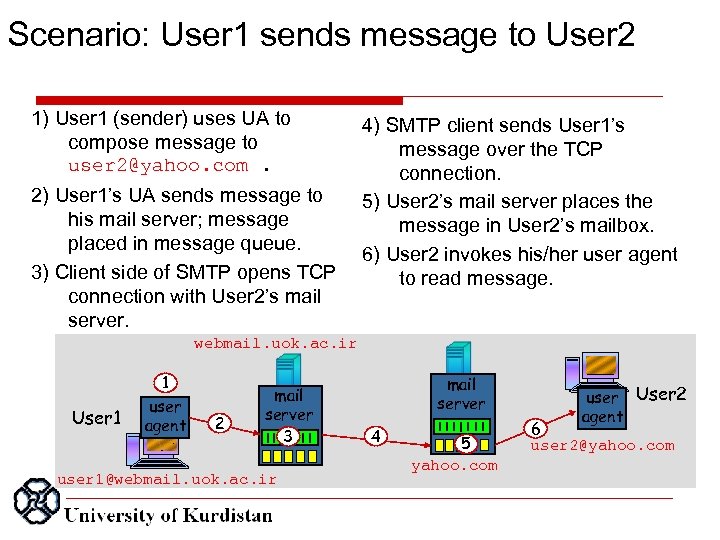 Scenario: User 1 sends message to User 2 1) User 1 (sender) uses UA to compose message to user 2@yahoo. com. 2) User 1’s UA sends message to his mail server; message placed in message queue. 3) Client side of SMTP opens TCP connection with User 2’s mail server. 4) SMTP client sends User 1’s message over the TCP connection. 5) User 2’s mail server places the message in User 2’s mailbox. 6) User 2 invokes his/her user agent to read message. webmail. uok. ac. ir User 1 1 user agent 2 mail server 3 user 1@webmail. uok. ac. ir mail server 4 5 yahoo. com user User 2 agent 6 user 2@yahoo. com
Scenario: User 1 sends message to User 2 1) User 1 (sender) uses UA to compose message to user 2@yahoo. com. 2) User 1’s UA sends message to his mail server; message placed in message queue. 3) Client side of SMTP opens TCP connection with User 2’s mail server. 4) SMTP client sends User 1’s message over the TCP connection. 5) User 2’s mail server places the message in User 2’s mailbox. 6) User 2 invokes his/her user agent to read message. webmail. uok. ac. ir User 1 1 user agent 2 mail server 3 user 1@webmail. uok. ac. ir mail server 4 5 yahoo. com user User 2 agent 6 user 2@yahoo. com
 MIME ﻳﻚ پﺮﻭﺗﻜﻞ ﺗﻜﻤﻴﻠﻲ ﺍﺳﺖ ﻛﻪ ﺍﺟﺎﺯﻩ ﻣﻲ ﺩﻫﺪ ﻛﺎﺭﺍﻛﺘﺮﻫﺎﻱ ﻏﻴﺮ ASCII ﻧﻴﺰ ﺍﺯ ﻃﺮﻳﻖ SMTP ﻣﻨﺘﻘﻞ ﺷﻮﻧﺪ. ﺩﻗﺖ ﻛﻨﻴﺪ ﻛﻪ MIME ﻳﻚ پﺮﻭﺗﻜﻞ ﺟﺎﻳگﺰﻳﻦ ﺑﺮﺍﻱ SMTP ﻧﻴﺴﺖ ﻭ ﻗﺎﺩﺭ ﺑﻪ ﺍﺭﺳﺎﻝ ﻧﺎﻣﻪ ﻧﻤﻲ ﺑﺎﺷﺪ ﺑﻠﻜﻪ ﺗﻮﺳﻌﻪ ﺍﻱ ﺑﺮﺍﻱ پﺮﻭﺗﻜﻞ SMTP ﻣﺤﺴﻮﺏ ﻣﻲ ﺷﻮﺩ. ﻣﻴﺘﻮﺍﻥ MIME ﺭﺍ ﺑﻪ ﺻﻮﺭﺕ ﺑﺮﻧﺎﻣﻪ ﺍﻱ ﺗﺼﻮﺭ ﻧﻤﻮﺩ ﻛﻪ ﺩﺍﺩﻩ ﻏﻴﺮ ASCII ﺭﺍ ﺑﻪ ﺩﺍﺩﻩ ASCII ﻭ ﺑﺎﻟﻌﻜﺲ ﺗﺮﺟﻤﻪ ﻣﻴﻜﻨﺪ
MIME ﻳﻚ پﺮﻭﺗﻜﻞ ﺗﻜﻤﻴﻠﻲ ﺍﺳﺖ ﻛﻪ ﺍﺟﺎﺯﻩ ﻣﻲ ﺩﻫﺪ ﻛﺎﺭﺍﻛﺘﺮﻫﺎﻱ ﻏﻴﺮ ASCII ﻧﻴﺰ ﺍﺯ ﻃﺮﻳﻖ SMTP ﻣﻨﺘﻘﻞ ﺷﻮﻧﺪ. ﺩﻗﺖ ﻛﻨﻴﺪ ﻛﻪ MIME ﻳﻚ پﺮﻭﺗﻜﻞ ﺟﺎﻳگﺰﻳﻦ ﺑﺮﺍﻱ SMTP ﻧﻴﺴﺖ ﻭ ﻗﺎﺩﺭ ﺑﻪ ﺍﺭﺳﺎﻝ ﻧﺎﻣﻪ ﻧﻤﻲ ﺑﺎﺷﺪ ﺑﻠﻜﻪ ﺗﻮﺳﻌﻪ ﺍﻱ ﺑﺮﺍﻱ پﺮﻭﺗﻜﻞ SMTP ﻣﺤﺴﻮﺏ ﻣﻲ ﺷﻮﺩ. ﻣﻴﺘﻮﺍﻥ MIME ﺭﺍ ﺑﻪ ﺻﻮﺭﺕ ﺑﺮﻧﺎﻣﻪ ﺍﻱ ﺗﺼﻮﺭ ﻧﻤﻮﺩ ﻛﻪ ﺩﺍﺩﻩ ﻏﻴﺮ ASCII ﺭﺍ ﺑﻪ ﺩﺍﺩﻩ ASCII ﻭ ﺑﺎﻟﻌﻜﺲ ﺗﺮﺟﻤﻪ ﻣﻴﻜﻨﺪ
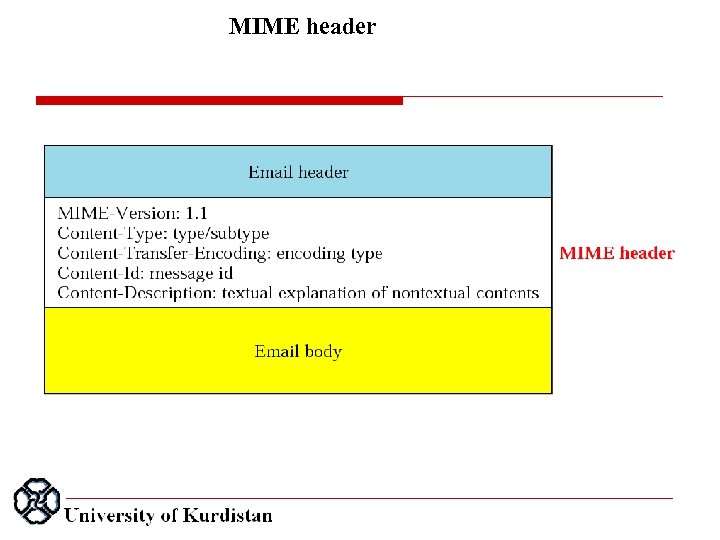 MIME header
MIME header
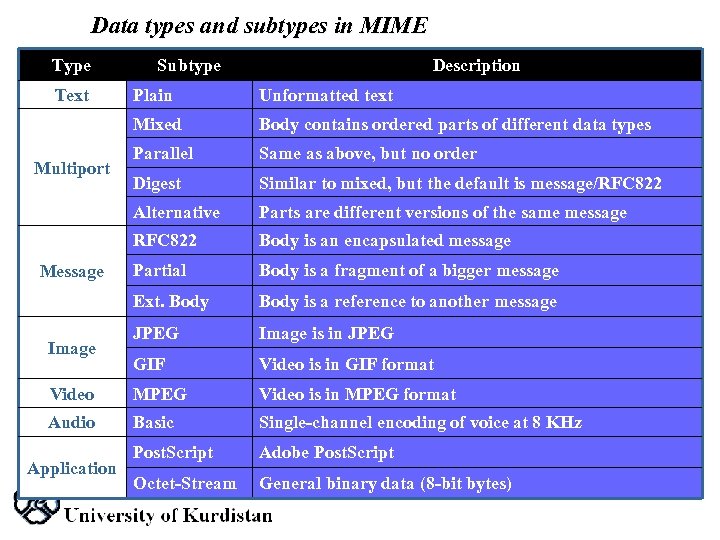 Data types and subtypes in MIME Type Text Subtype Description Plain Unformatted text Mixed Body contains ordered parts of different data types Parallel Same as above, but no order Digest Similar to mixed, but the default is message/RFC 822 Alternative Parts are different versions of the same message RFC 822 Body is an encapsulated message Partial Body is a fragment of a bigger message Ext. Body is a reference to another message JPEG Image is in JPEG GIF Video is in GIF format Video MPEG Video is in MPEG format Audio Basic Single channel encoding of voice at 8 KHz Post. Script Adobe Post. Script Octet Stream General binary data (8 bit bytes) Multiport Message Image Application
Data types and subtypes in MIME Type Text Subtype Description Plain Unformatted text Mixed Body contains ordered parts of different data types Parallel Same as above, but no order Digest Similar to mixed, but the default is message/RFC 822 Alternative Parts are different versions of the same message RFC 822 Body is an encapsulated message Partial Body is a fragment of a bigger message Ext. Body is a reference to another message JPEG Image is in JPEG GIF Video is in GIF format Video MPEG Video is in MPEG format Audio Basic Single channel encoding of voice at 8 KHz Post. Script Adobe Post. Script Octet Stream General binary data (8 bit bytes) Multiport Message Image Application
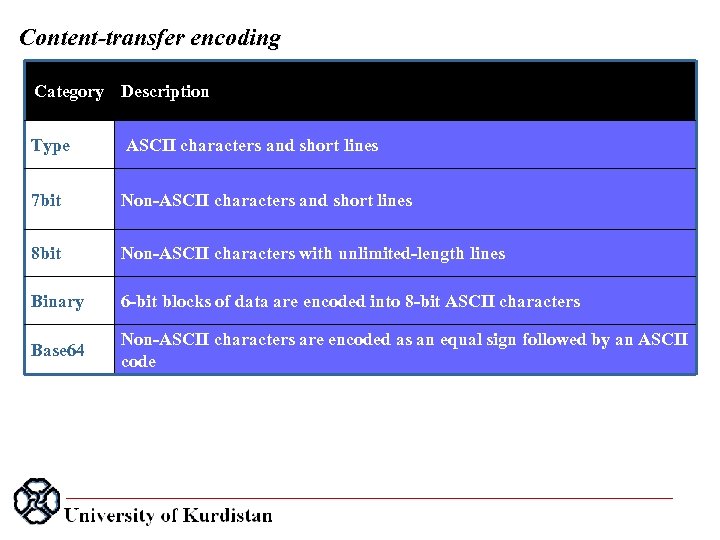 Content-transfer encoding Category Description Type ASCII characters and short lines 7 bit Non ASCII characters and short lines 8 bit Non ASCII characters with unlimited length lines Binary 6 bit blocks of data are encoded into 8 bit ASCII characters Base 64 Non ASCII characters are encoded as an equal sign followed by an ASCII code
Content-transfer encoding Category Description Type ASCII characters and short lines 7 bit Non ASCII characters and short lines 8 bit Non ASCII characters with unlimited length lines Binary 6 bit blocks of data are encoded into 8 bit ASCII characters Base 64 Non ASCII characters are encoded as an equal sign followed by an ASCII code
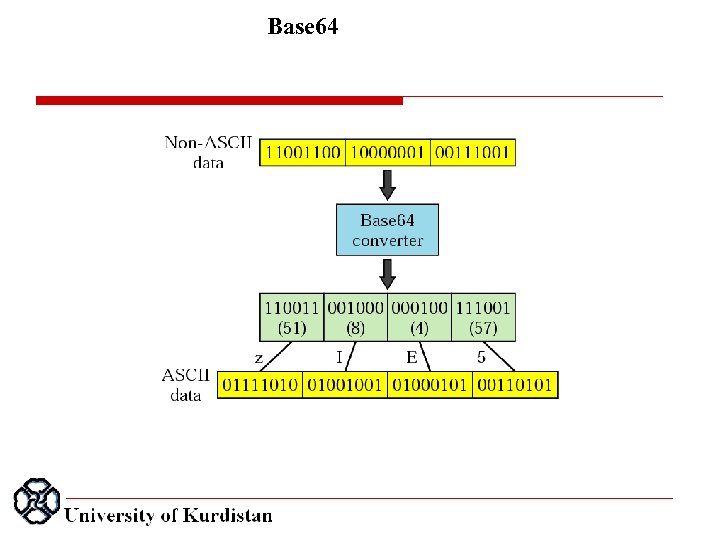 Base 64
Base 64
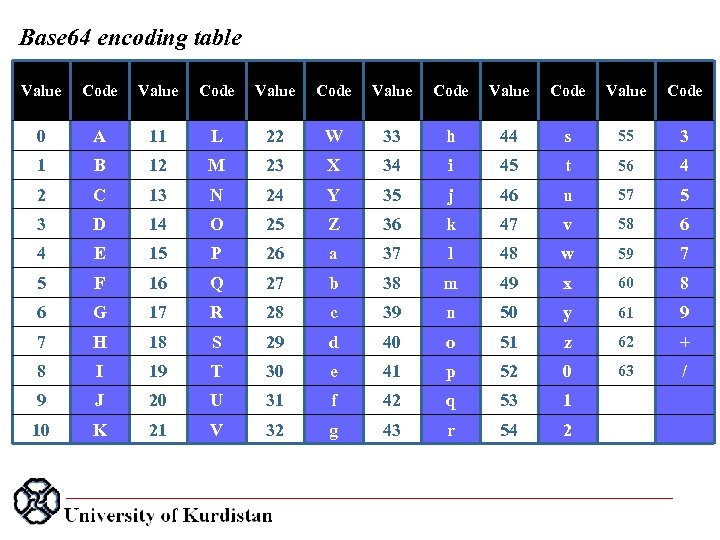 Base 64 encoding table Value Code Value Code 0 A 11 L 22 W 33 h 44 s 55 3 1 B 12 M 23 X 34 i 45 t 56 4 2 C 13 N 24 Y 35 j 46 u 57 5 3 D 14 O 25 Z 36 k 47 v 58 6 4 E 15 P 26 a 37 l 48 w 59 7 5 F 16 Q 27 b 38 m 49 x 60 8 6 G 17 R 28 c 39 n 50 y 61 9 7 H 18 S 29 d 40 o 51 z 62 + 8 I 19 T 30 e 41 p 52 0 63 / 9 J 20 U 31 f 42 q 53 1 10 K 21 V 32 g 43 r 54 2
Base 64 encoding table Value Code Value Code 0 A 11 L 22 W 33 h 44 s 55 3 1 B 12 M 23 X 34 i 45 t 56 4 2 C 13 N 24 Y 35 j 46 u 57 5 3 D 14 O 25 Z 36 k 47 v 58 6 4 E 15 P 26 a 37 l 48 w 59 7 5 F 16 Q 27 b 38 m 49 x 60 8 6 G 17 R 28 c 39 n 50 y 61 9 7 H 18 S 29 d 40 o 51 z 62 + 8 I 19 T 30 e 41 p 52 0 63 / 9 J 20 U 31 f 42 q 53 1 10 K 21 V 32 g 43 r 54 2
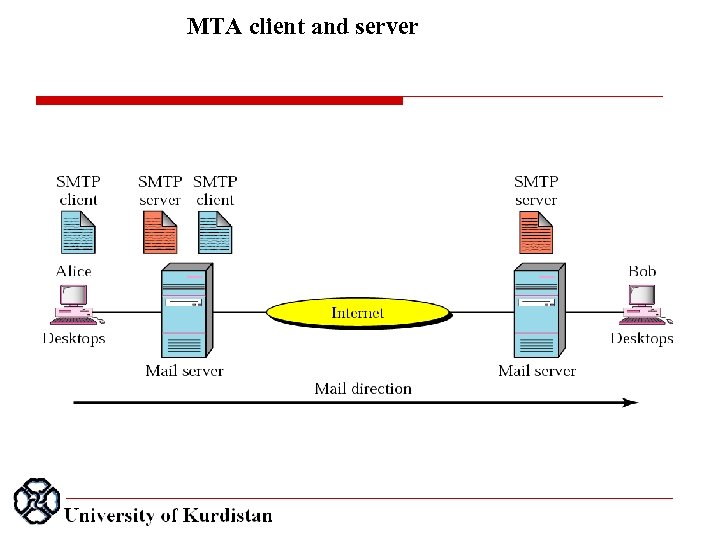 MTA client and server
MTA client and server
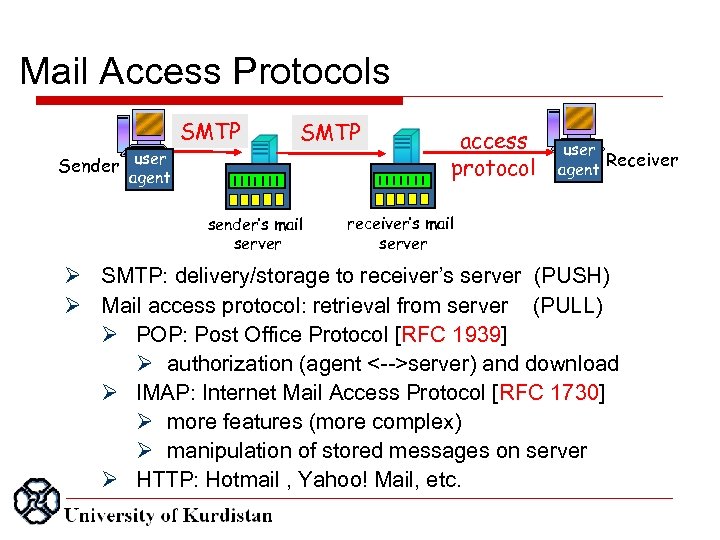 Mail Access Protocols SMTP Sender user agent SMTP sender’s mail server access protocol user Receiver agent receiver’s mail server SMTP: delivery/storage to receiver’s server (PUSH) Mail access protocol: retrieval from server (PULL) POP: Post Office Protocol [RFC 1939] authorization (agent <-->server) and download IMAP: Internet Mail Access Protocol [RFC 1730] more features (more complex) manipulation of stored messages on server HTTP: Hotmail , Yahoo! Mail, etc.
Mail Access Protocols SMTP Sender user agent SMTP sender’s mail server access protocol user Receiver agent receiver’s mail server SMTP: delivery/storage to receiver’s server (PUSH) Mail access protocol: retrieval from server (PULL) POP: Post Office Protocol [RFC 1939] authorization (agent <-->server) and download IMAP: Internet Mail Access Protocol [RFC 1730] more features (more complex) manipulation of stored messages on server HTTP: Hotmail , Yahoo! Mail, etc.
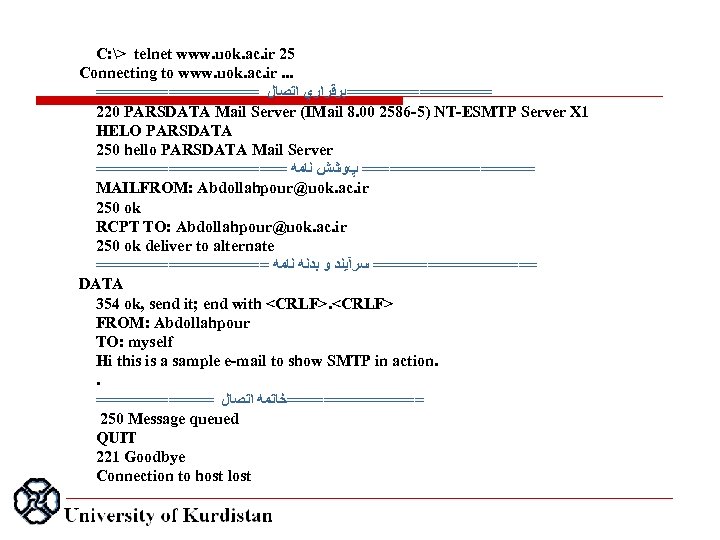 C: > telnet www. uok. ac. ir 25 Connecting to www. uok. ac. ir. . . =========ﺑﺮﻗﺮﺍﺭﻱ ﺍﺗﺼﺎﻝ 220 PARSDATA Mail Server (IMail 8. 00 2586 5) NT ESMTP Server X 1 HELO PARSDATA 250 hello PARSDATA Mail Server =========== پﻮﺷﺶ ﻧﺎﻣﻪ MAILFROM: Abdollahpour@uok. ac. ir 250 ok RCPT TO: Abdollahpour@uok. ac. ir 250 ok deliver to alternate ========== ﺳﺮآﻴﻨﺪ ﻭ ﺑﺪﻧﻪ ﻧﺎﻣﻪ DATA 354 ok, send it; end with
C: > telnet www. uok. ac. ir 25 Connecting to www. uok. ac. ir. . . =========ﺑﺮﻗﺮﺍﺭﻱ ﺍﺗﺼﺎﻝ 220 PARSDATA Mail Server (IMail 8. 00 2586 5) NT ESMTP Server X 1 HELO PARSDATA 250 hello PARSDATA Mail Server =========== پﻮﺷﺶ ﻧﺎﻣﻪ MAILFROM: Abdollahpour@uok. ac. ir 250 ok RCPT TO: Abdollahpour@uok. ac. ir 250 ok deliver to alternate ========== ﺳﺮآﻴﻨﺪ ﻭ ﺑﺪﻧﻪ ﻧﺎﻣﻪ DATA 354 ok, send it; end with
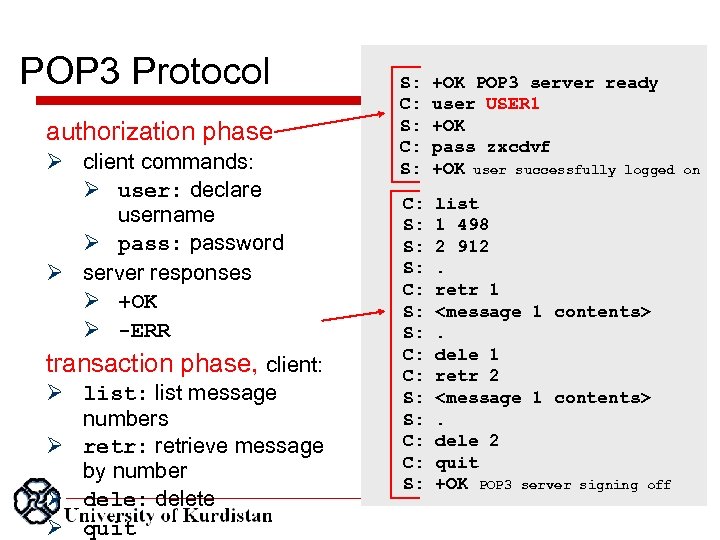 POP 3 Protocol authorization phase client commands: user: declare username pass: password server responses +OK -ERR transaction phase, client: list: list message numbers retr: retrieve message by number dele: delete quit S: C: S: +OK POP 3 server ready user USER 1 +OK pass zxcdvf +OK user successfully logged C: S: S: S: C: C: S: list 1 498 2 912. retr 1
POP 3 Protocol authorization phase client commands: user: declare username pass: password server responses +OK -ERR transaction phase, client: list: list message numbers retr: retrieve message by number dele: delete quit S: C: S: +OK POP 3 server ready user USER 1 +OK pass zxcdvf +OK user successfully logged C: S: S: S: C: C: S: list 1 498 2 912. retr 1
 File Transfer Connections Communication File Transfer User Interface Anonymous
File Transfer Connections Communication File Transfer User Interface Anonymous
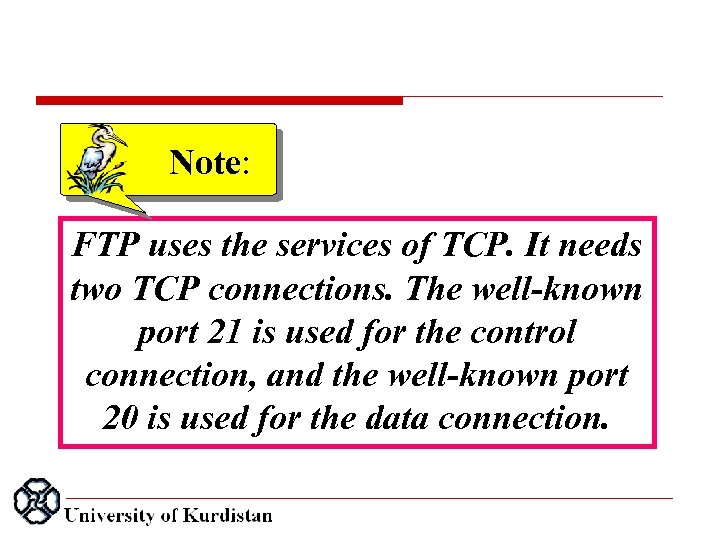 Note: FTP uses the services of TCP. It needs two TCP connections. The well-known port 21 is used for the control connection, and the well-known port 20 is used for the data connection.
Note: FTP uses the services of TCP. It needs two TCP connections. The well-known port 21 is used for the control connection, and the well-known port 20 is used for the data connection.
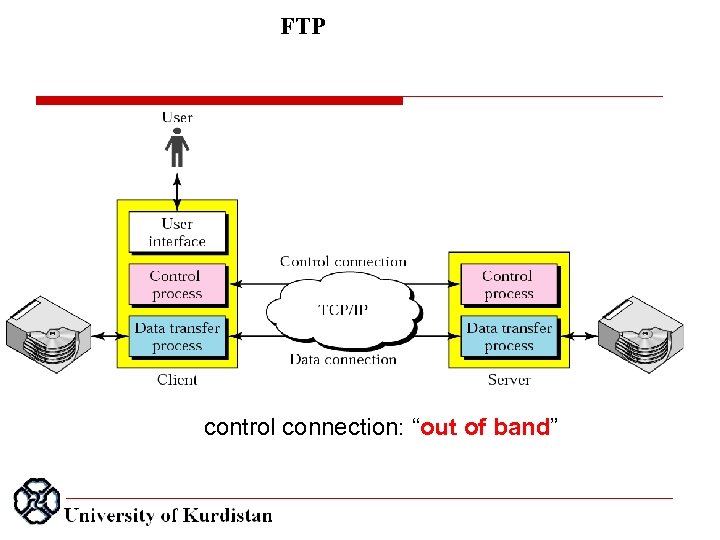 FTP control connection: “out of band”
FTP control connection: “out of band”
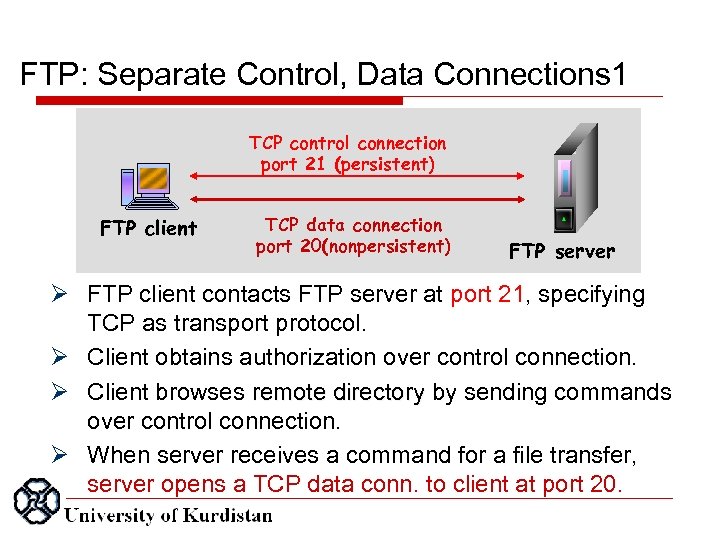 FTP: Separate Control, Data Connections 1 TCP control connection port 21 (persistent) FTP client TCP data connection port 20(nonpersistent) FTP server FTP client contacts FTP server at port 21, specifying TCP as transport protocol. Client obtains authorization over control connection. Client browses remote directory by sending commands over control connection. When server receives a command for a file transfer, server opens a TCP data conn. to client at port 20.
FTP: Separate Control, Data Connections 1 TCP control connection port 21 (persistent) FTP client TCP data connection port 20(nonpersistent) FTP server FTP client contacts FTP server at port 21, specifying TCP as transport protocol. Client obtains authorization over control connection. Client browses remote directory by sending commands over control connection. When server receives a command for a file transfer, server opens a TCP data conn. to client at port 20.
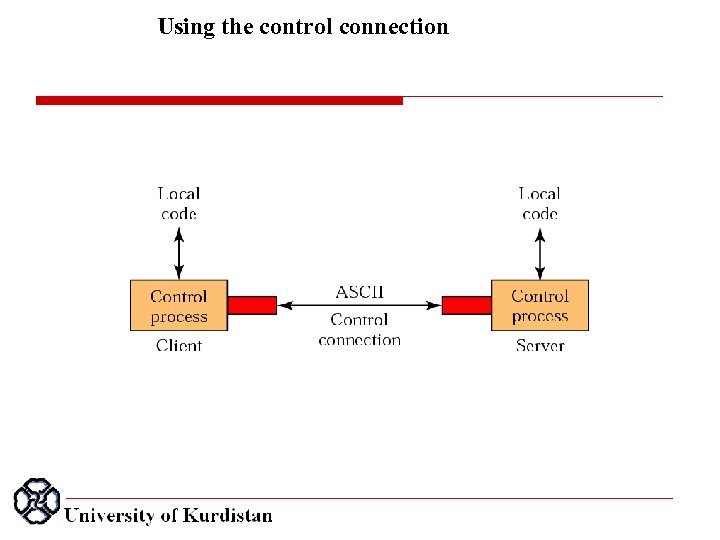 Using the control connection
Using the control connection
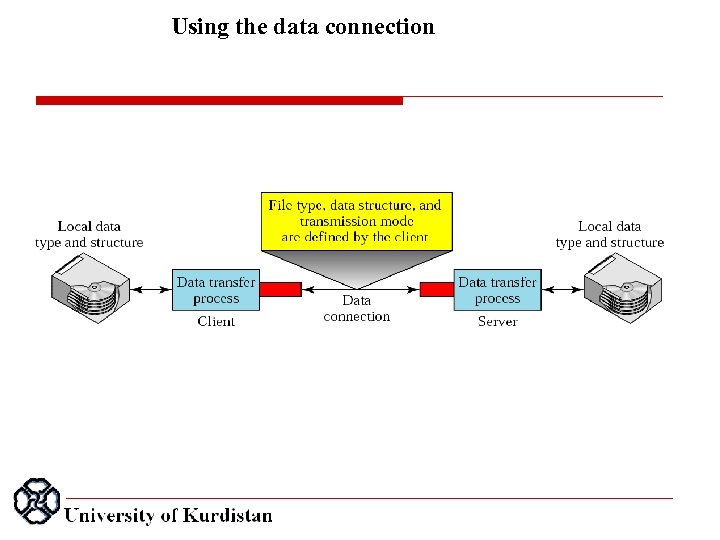 Using the data connection
Using the data connection
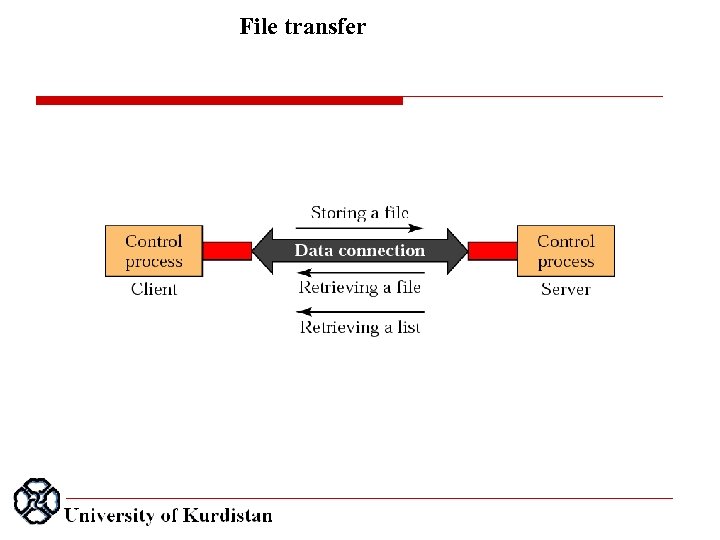 File transfer
File transfer
 Example 1 Figure 26. 16 (next slide) shows an example of how a file is stored. 1. The control connection is created, and several control commands and responses are exchanged. 2. Data are transferred record by record. 3. A few commands and responses are exchanged to close the connection.
Example 1 Figure 26. 16 (next slide) shows an example of how a file is stored. 1. The control connection is created, and several control commands and responses are exchanged. 2. Data are transferred record by record. 3. A few commands and responses are exchanged to close the connection.
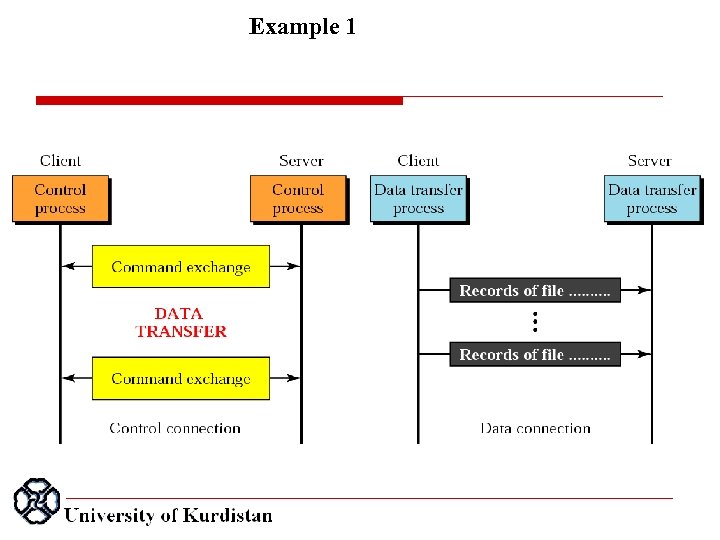 Example 1
Example 1
 List of FTP commands in UNIX Commands !, $, account, append, ascii, bell, binary, bye, case, cdup, close, cr, delete, debug, dir, discount, form, get, glob, hash, help, lcd, ls, macdef, mdelete, mdir, mget, mkdir, mls, mode, mput, nmap, ntrans, open, prompt, proxy, sendport, put, pwd, quit, quote, recv, remotehelp, rename, reset, rmdir, runique, send, status, struct, sunique, tenex, trace, type, user, verbose, ?
List of FTP commands in UNIX Commands !, $, account, append, ascii, bell, binary, bye, case, cdup, close, cr, delete, debug, dir, discount, form, get, glob, hash, help, lcd, ls, macdef, mdelete, mdir, mget, mkdir, mls, mode, mput, nmap, ntrans, open, prompt, proxy, sendport, put, pwd, quit, quote, recv, remotehelp, rename, reset, rmdir, runique, send, status, struct, sunique, tenex, trace, type, user, verbose, ?
 Example 2 We show some of the user interface commands that accomplish the same task as in Example 1. The user input is shown in boldface. As shown below, some of the commands are provided automatically by the interface. The user receives a prompt and provides only the $ ftp challenger. atc. fhda. edu arguments. Connected to challenger. atc. fhda. edu 220 Server ready Name: forouzan Password: xxxxxxx ftp > ls /usr/user/report 200 OK 150 Opening ASCII mode. . . . . 226 transfer complete ftp > close 221 Goodbye ftp > quit
Example 2 We show some of the user interface commands that accomplish the same task as in Example 1. The user input is shown in boldface. As shown below, some of the commands are provided automatically by the interface. The user receives a prompt and provides only the $ ftp challenger. atc. fhda. edu arguments. Connected to challenger. atc. fhda. edu 220 Server ready Name: forouzan Password: xxxxxxx ftp > ls /usr/user/report 200 OK 150 Opening ASCII mode. . . . . 226 transfer complete ftp > close 221 Goodbye ftp > quit
 Example 3 We show an example of using anonymous FTP. We connect to internic. net, where we assume there are some public data available. $ ftp internic. net Connected to internic. net 220 Server ready Name: anonymous 331 Guest login OK, send "guest" as password Password: guest ftp > pwd 257 '/' is current directory ftp > ls 200 OK 150 Opening ASCII mode bin. . . ftp > close 221 Goodbye ftp > quit
Example 3 We show an example of using anonymous FTP. We connect to internic. net, where we assume there are some public data available. $ ftp internic. net Connected to internic. net 220 Server ready Name: anonymous 331 Guest login OK, send "guest" as password Password: guest ftp > pwd 257 '/' is current directory ftp > ls 200 OK 150 Opening ASCII mode bin. . . ftp > close 221 Goodbye ftp > quit
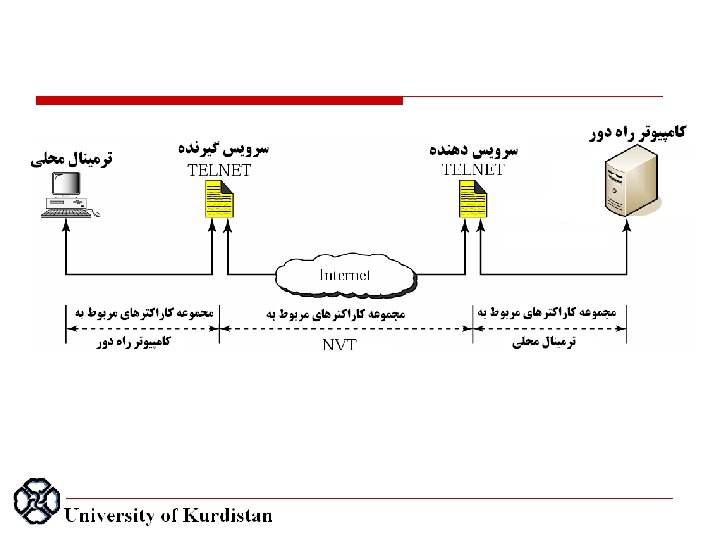
 Remote Login: Telnet
Remote Login: Telnet
 Questions 88
Questions 88


