29742dd89b5e0eff1c9bbee5b6bdd112.ppt
- Количество слайдов: 53

Demystifying PKI: Introduction to The Cryptography Behind Public Key Infrastructure

Security Services • Data Integrity – Verification that the data has not been modified • Authentication – e. g. , your personal signature • Non-Repudiation – e. g. , Sender/Receiver in a financial transaction • Confidentiality – i. e. , scrambled text

Data Integrity • The Assurance That the Data Has Arrived Intact, With No Tampering or Corruption of the Bits. • Data Integrity Is Achieved Electronically Through the Use of Cryptographic Checksums (One-way Hashes) Over the Data.
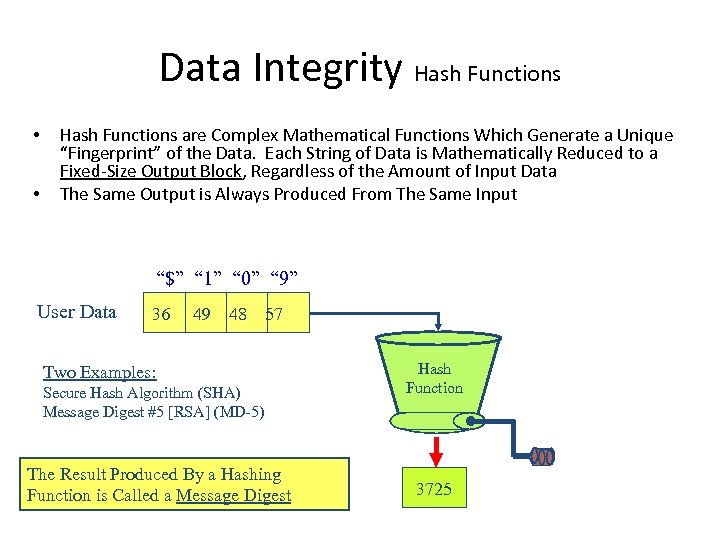
Data Integrity Hash Functions • • Hash Functions are Complex Mathematical Functions Which Generate a Unique “Fingerprint” of the Data. Each String of Data is Mathematically Reduced to a Fixed-Size Output Block, Regardless of the Amount of Input Data The Same Output is Always Produced From The Same Input “$” “ 1” “ 0” “ 9” User Data 36 49 48 57 Two Examples: Secure Hash Algorithm (SHA) Message Digest #5 [RSA] (MD-5) The Result Produced By a Hashing Function is Called a Message Digest Hash Function 3725

Authentication • The Binding of the Sender’s (or Issuer’s) Credentials to the Data. This Process Can Be Likened to Your Personal Signature – It Is Unique to You and Can Be Recognized (Verified) Later by All Parties Involved

Non-Repudiation • The Fact That a Third Party Can Verify Your Authentication (e. g. , Your Signature) on a Transaction Means That You Cannot Deny Participation in the Transaction

Confidentiality/Privacy • Encryption (scrambling) of the data to prevent unauthorized disclosure.
Mechanics of Security • Cryptographic algorithms (mathematical processes) used to implement security • Symmetric vs. Asymmetric • Key Generation • Digital Signatures • Encryption • Public Key Infrastructure

Symmetric Cryptography

Encryption Algorithms • Encryption Has Historically Been Used in Military Applications to Secure Tactical or Intelligence Related Information During Wartime. For This Reason, Encryption Is Classified As a Munition or Instrument of War by Most Countries. The Improper Use of Encryption Is Often Considered a Terrorist Act. Many Countries Place Restrictions on the Import and Export of Encryption, as Well as the Use of Encryption Within the Country.
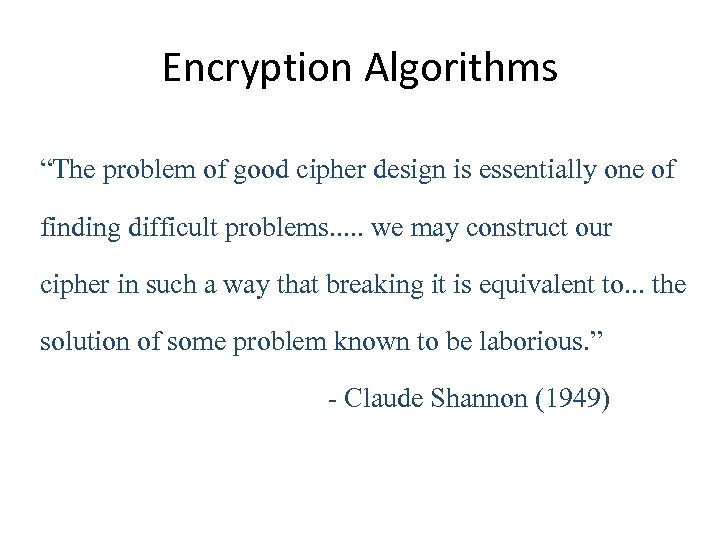
Encryption Algorithms “The problem of good cipher design is essentially one of finding difficult problems. . . we may construct our cipher in such a way that breaking it is equivalent to. . . the solution of some problem known to be laborious. ” - Claude Shannon (1949)
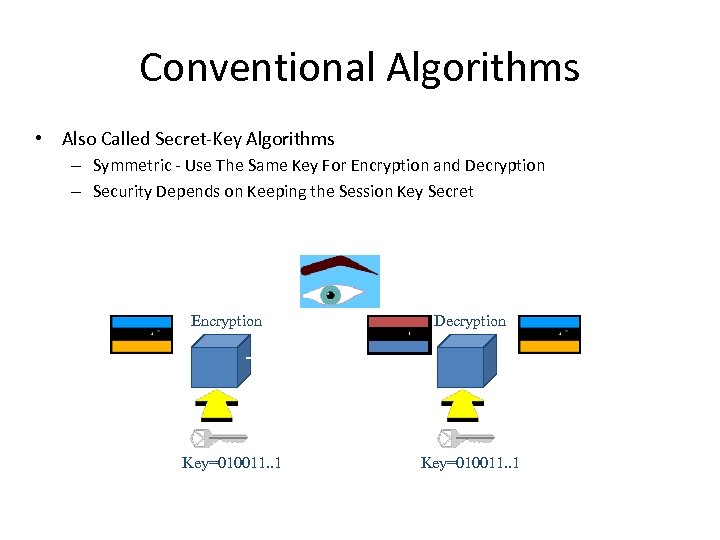
Conventional Algorithms • Also Called Secret-Key Algorithms – Symmetric - Use The Same Key For Encryption and Decryption – Security Depends on Keeping the Session Key Secret Encryption Key=010011. . 1 Decryption Key=010011. . 1
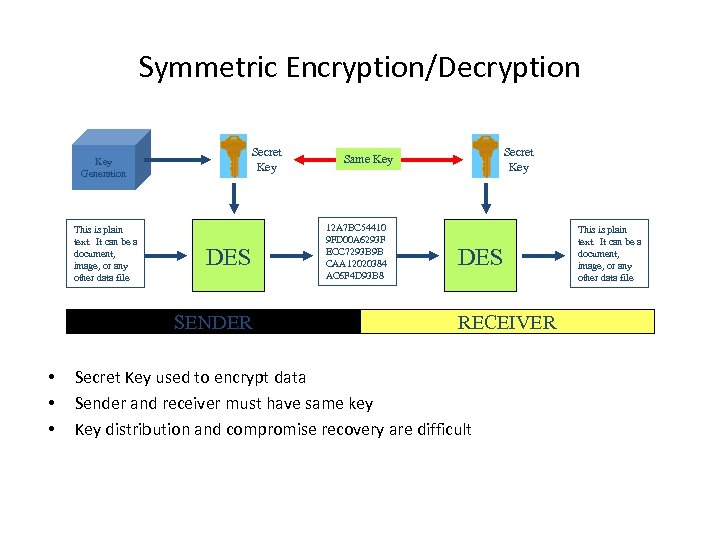
Symmetric Encryption/Decryption Secret Key Generation This is plain text. It can be a document, image, or any other data file DES SENDER • • • Secret Key Same Key 12 A 7 BC 54410 9 FD 00 A 6293 F ECC 7293 B 9 B CAA 12020384 AC 6 F 4 D 93 B 8 DES RECEIVER Secret Key used to encrypt data Sender and receiver must have same key Key distribution and compromise recovery are difficult This is plain text. It can be a document, image, or any other data file
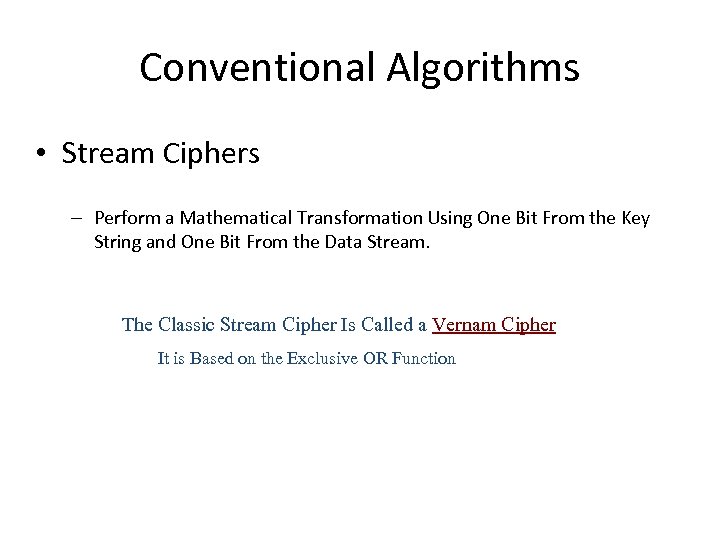
Conventional Algorithms • Stream Ciphers – Perform a Mathematical Transformation Using One Bit From the Key String and One Bit From the Data Stream. n The Classic Stream Cipher Is Called a Vernam Cipher s It is Based on the Exclusive OR Function
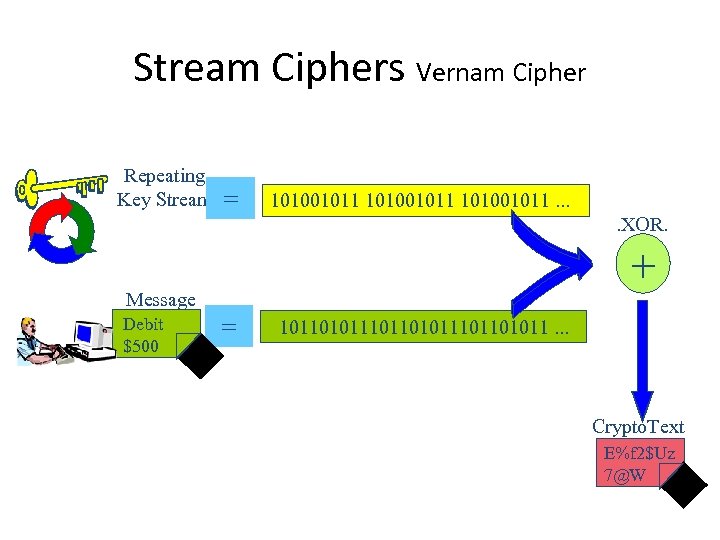
Stream Ciphers Vernam Cipher Repeating Key Stream = 101001011. . XOR. + Message Debit $500 = 101101011101101011. . . Crypto. Text E%f 2$Uz 7@W
Block Ciphers • Perform a Mathematical Transformation On Data In Fixed-Size Blocks, One At a Time. • The Cipher Mode Determines How The Algorithm Is Applied To Data Streams, Block-By-Block • Block Ciphers are Fairly Similar From a Functional Point-of-View • We’ll Now Look at an Example of One Well-Known Block Cipher in Detail. . .
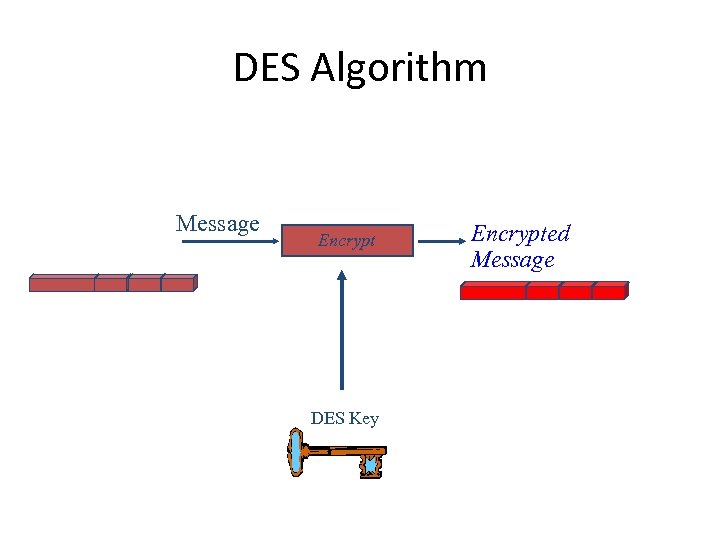
DES Algorithm Message Encrypt DES Key Encrypted Message
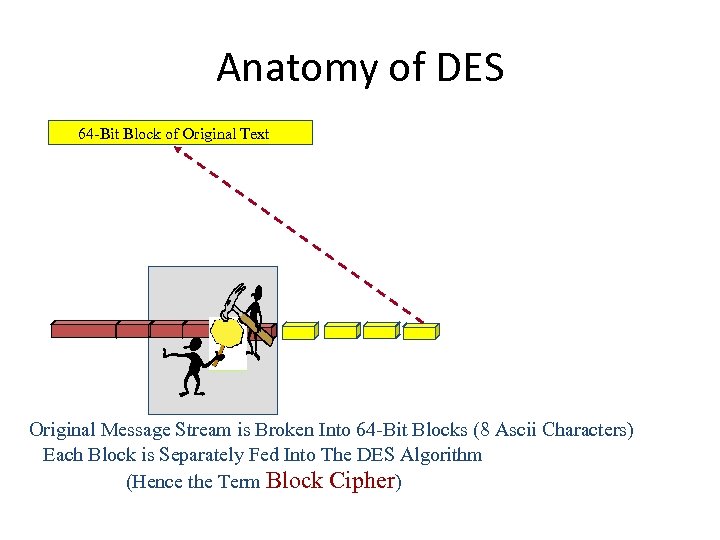
Anatomy of DES 64 -Bit Block of Original Text Original Message Stream is Broken Into 64 -Bit Blocks (8 Ascii Characters) Each Block is Separately Fed Into The DES Algorithm (Hence the Term Block Cipher)

Anatomy of DES 64 -Bit Block of Original Text 56 -Bit Key The Original DES Key is 64 Bits The Keysize is Reduced to 56 Bits During The Initial Permutation Bits 8, 16, 24, 32, 40, 48, 56, 64 The Reduced 56 -Bit Key Becomes The Working DES Session Key
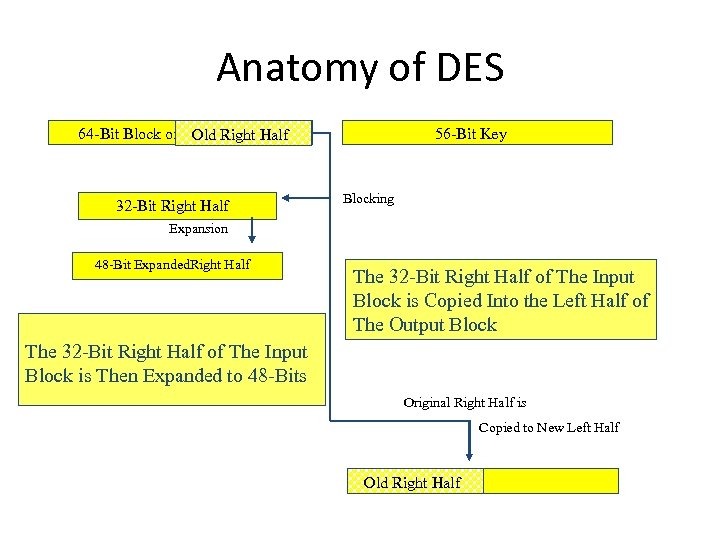
Anatomy of DES 64 -Bit Block of Original Text Old Right Half 32 -Bit Right Half 56 -Bit Key Blocking Expansion 48 -Bit Expanded. Right Half The 32 -Bit Right Half of The Input Block is Copied Into the Left Half of The Output Block The 32 -Bit Right Half of The Input Block is Then Expanded to 48 -Bits Original Right Half is Copied to New Left Half Old Right Half
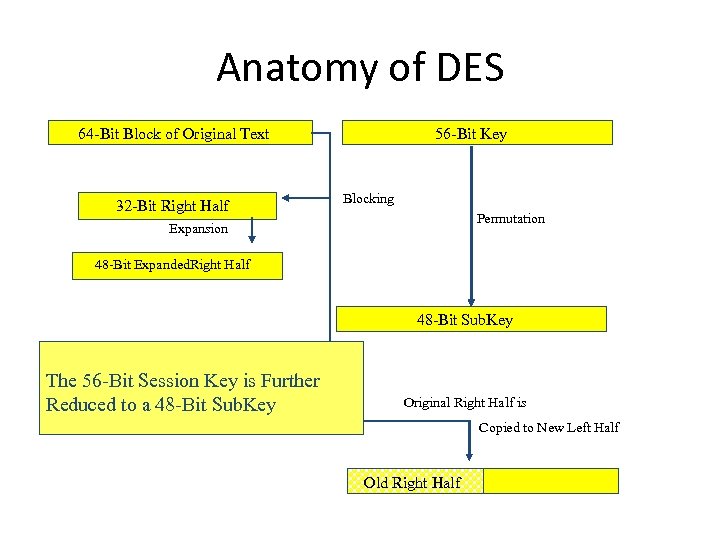
Anatomy of DES 64 -Bit Block of Original Text 32 -Bit Right Half 56 -Bit Key Blocking Permutation Expansion 48 -Bit Expanded. Right Half 48 -Bit Sub. Key The 56 -Bit Session Key is Further Reduced to a 48 -Bit Sub. Key Original Right Half is Copied to New Left Half Old Right Half
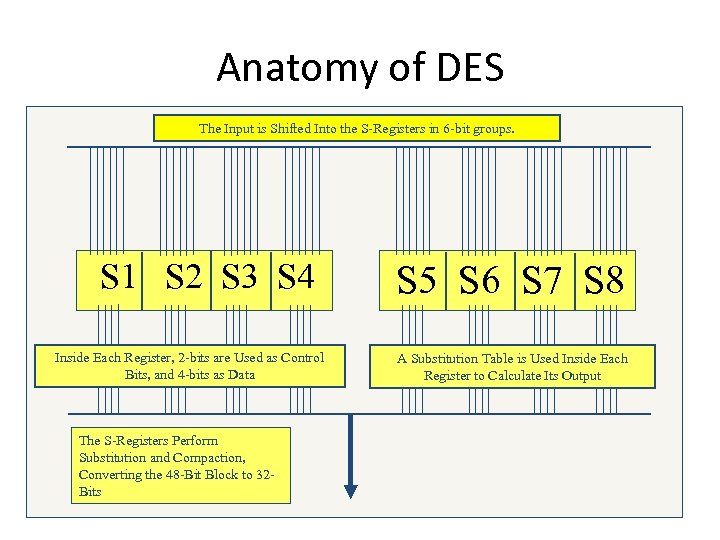
Anatomy of DES The Input is Shifted Into the S-Registers in 6 -bit groups. S 1 S 2 S 3 S 4 Inside Each Register, 2 -bits are Used as Control Bits, and 4 -bits as Data The S-Registers Perform Substitution and Compaction, Converting the 48 -Bit Block to 32 Bits S 5 S 6 S 7 S 8 A Substitution Table is Used Inside Each Register to Calculate Its Output
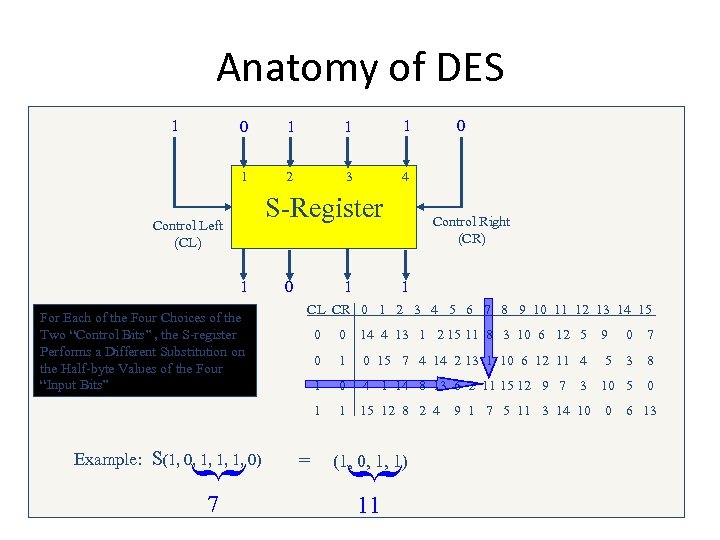
Anatomy of DES 1 0 1 1 1 2 3 0 1 4 S-Register Control Left (CL) 1 For Each of the Four Choices of the Two “Control Bits” , the S-register Performs a Different Substitution on the Half-byte Values of the Four “Input Bits” 0 Control Right (CR) 1 1 CL CR 0 1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 9 0 7 1 0 15 7 4 14 2 13 1 10 6 12 11 4 5 3 8 1 0 4 1 14 8 13 6 2 11 15 12 9 7 10 5 0 1 15 12 8 2 4 (1, 0, 1, 1) { { 7 14 4 13 1 2 15 11 8 3 10 6 12 5 0 = 0 1 Example: S(1, 0, 1, 1, 1, 0) 0 11 3 9 1 7 5 11 3 14 10 0 6 13
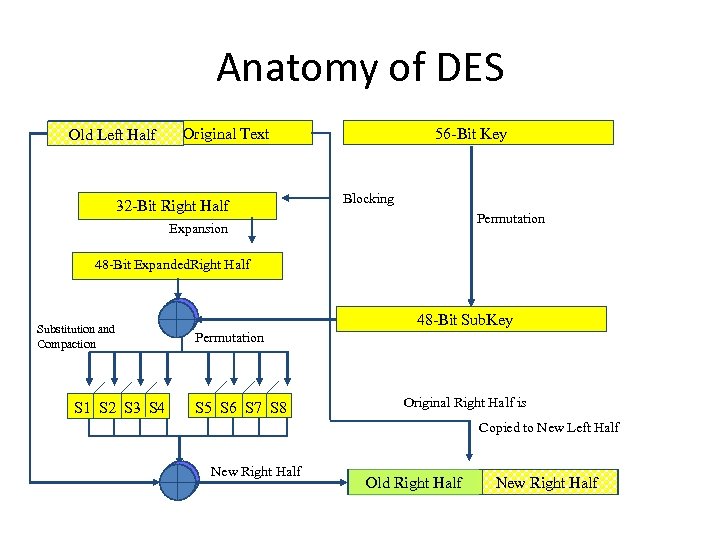
Anatomy of DES 64 -Bit Half Old Left. Block of Original Text 32 -Bit Right Half 56 -Bit Key Blocking Permutation Expansion 48 -Bit Expanded. Right Half Substitution and Compaction S 1 S 2 S 3 S 4 48 -Bit Sub. Key Permutation S 5 S 6 S 7 S 8 Original Right Half is Copied to New Left Half New Right Half Old Right Half New Right Half
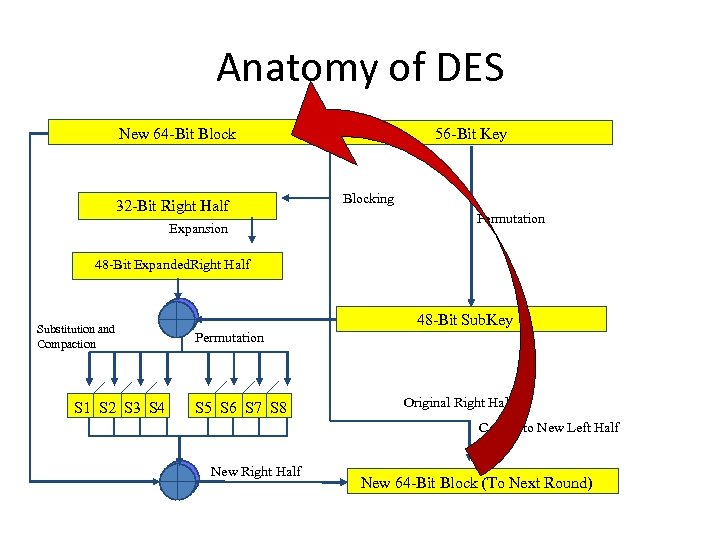
Anatomy of DES 64 -Bit. New 64 -Bit Block Text Block of Original 32 -Bit Right Half Expansion 56 -Bit Key Blocking Permutation 48 -Bit Expanded. Right Half Substitution and Compaction S 1 S 2 S 3 S 4 48 -Bit Sub. Key Permutation S 5 S 6 S 7 S 8 Original Right Half is Copied to New Left Half New Right Half New 64 -Bit Block (To Next Round)
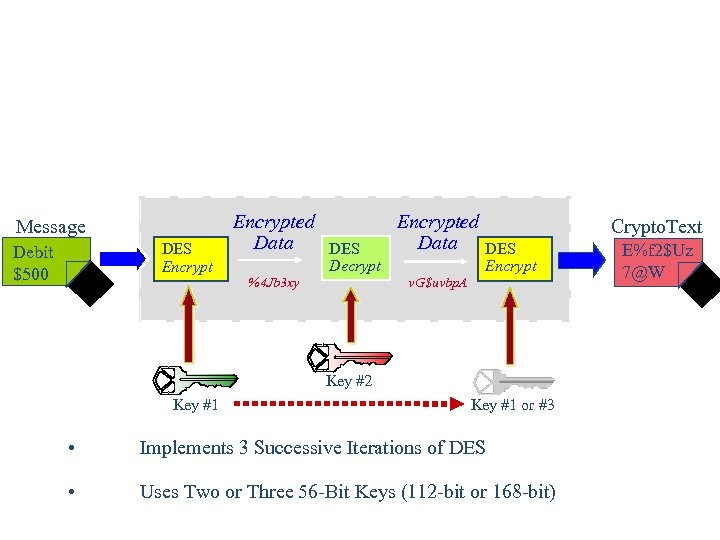
Triple Des Algorithm (TDES) Message DES Encrypt Debit $500 Encrypted Data DES Decrypt %4 Jb 3 xy Encrypted Data v. G$uvbp. A Crypto. Text DES Encrypt Key #2 Key #1 or #3 • Implements 3 Successive Iterations of DES • Uses Two or Three 56 -Bit Keys (112 -bit or 168 -bit) E%f 2$Uz 7@W
Encryption Algorithms • Strengthening Encryption Algorithms – Strength of an Algorithm Measures How Long It Would Take an Adversary to Deduce the Key s s The Longer the Key, the Stronger the Algorithm s n The More Difficult the Mathematics, the Stronger the Algorithm The More Often the Key Is Changed, the Stronger the Security The Stronger the Algorithm, the Slower it Usually is Due to the Mathematical Overhead Required

Asymmetric Cryptography Most commonly known as Public Key Cryptography
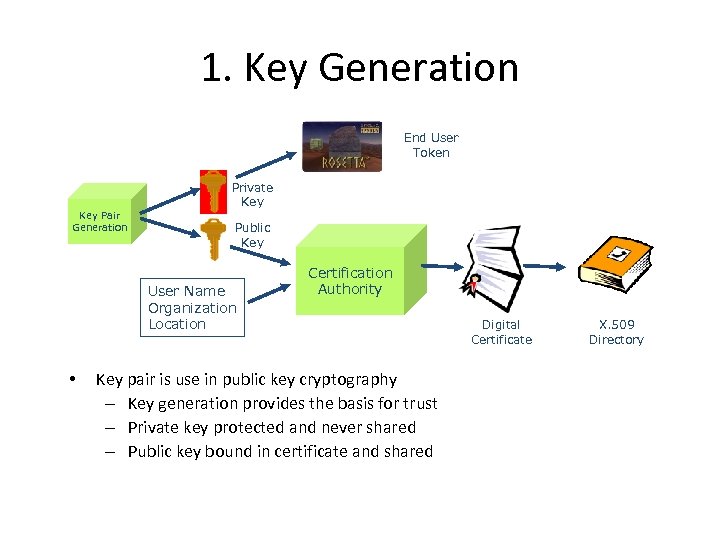
1. Key Generation End User Token Key Pair Generation Private Key Public Key User Name Organization Location • Certification Authority Key pair is use in public key cryptography – Key generation provides the basis for trust – Private key protected and never shared – Public key bound in certificate and shared Digital Certificate X. 509 Directory
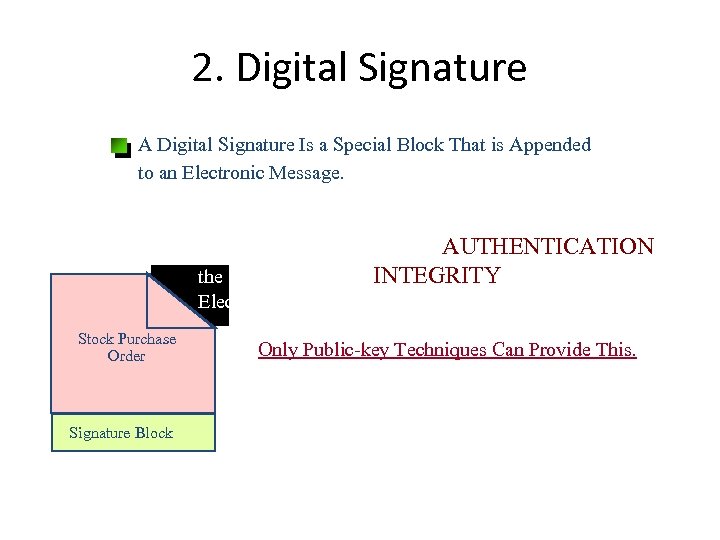
2. Digital Signature A Digital Signature Is a Special Block That is Appended to an Electronic Message. Allows for Verification of the AUTHENTICATION of the Sender and of the INTEGRITY of the content of an Electronic Message. Stock Purchase Order Signature Block Only Public-key Techniques Can Provide This.
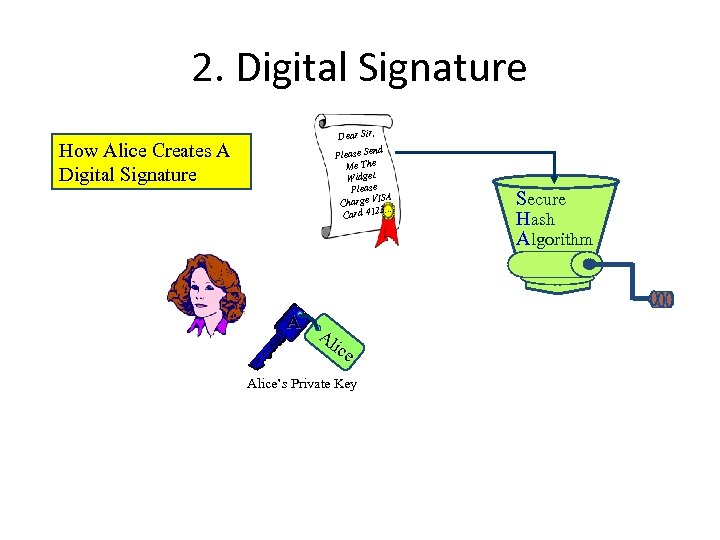
2. Digital Signature How Alice Creates A Digital Signature Dear Sir, nd Please Se The Me Widget. Please ISA Charge V 4123. . . Card A Al ice Alice’s Private Key Secure Hash Algorithm
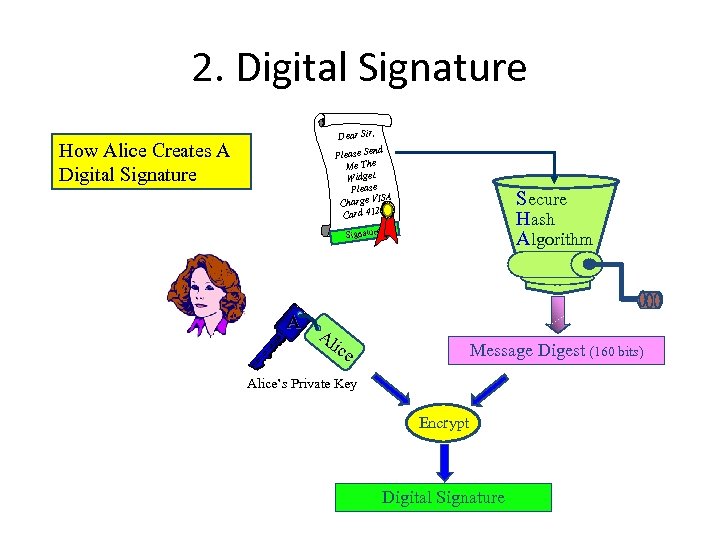
2. Digital Signature How Alice Creates A Digital Signature Dear Sir, nd Please Se The Me Widget. Please ISA Charge V 4123. . . Card Secure Hash Algorithm Signature A Al ice Message Digest (160 bits) Alice’s Private Key Encrypt Digital Signature
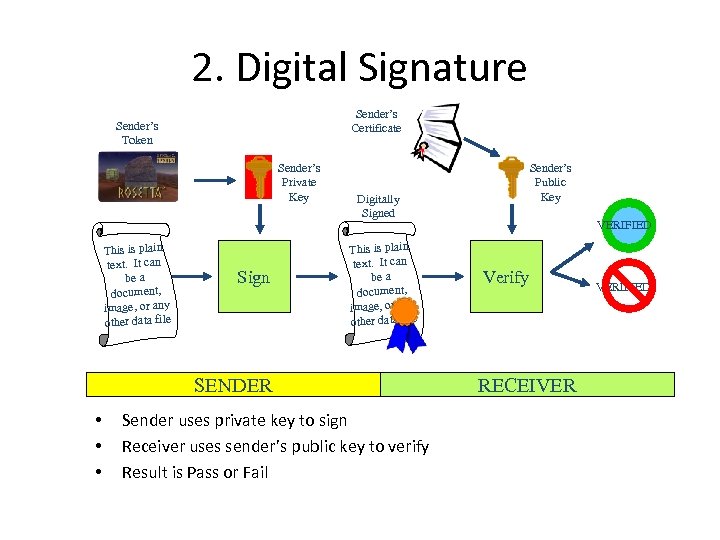
2. Digital Signature Sender’s Certificate Sender’s Token Sender’s Private Key This is plain text. It can be a document, image, or any other data file Sign Digitally Signed This is plain text. It can be a cument, do image, or any other data file SENDER • • • Sender’s Public Key Sender uses private key to sign Receiver uses sender’s public key to verify Result is Pass or Fail VERIFIED Verify RECEIVER VERIFIED
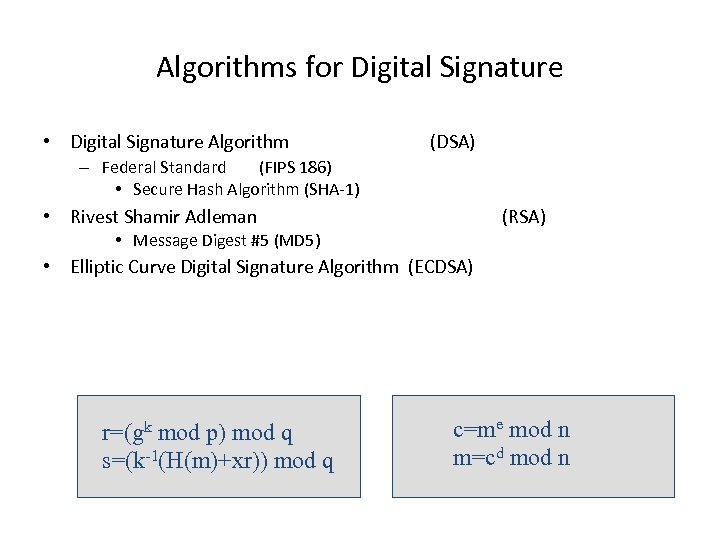
Algorithms for Digital Signature • Digital Signature Algorithm (DSA) – Federal Standard (FIPS 186) • Secure Hash Algorithm (SHA-1) • Rivest Shamir Adleman (RSA) • Message Digest #5 (MD 5) • Elliptic Curve Digital Signature Algorithm (ECDSA) r=(gk mod p) mod q s=(k-1(H(m)+xr)) mod q c=me mod n m=cd mod n
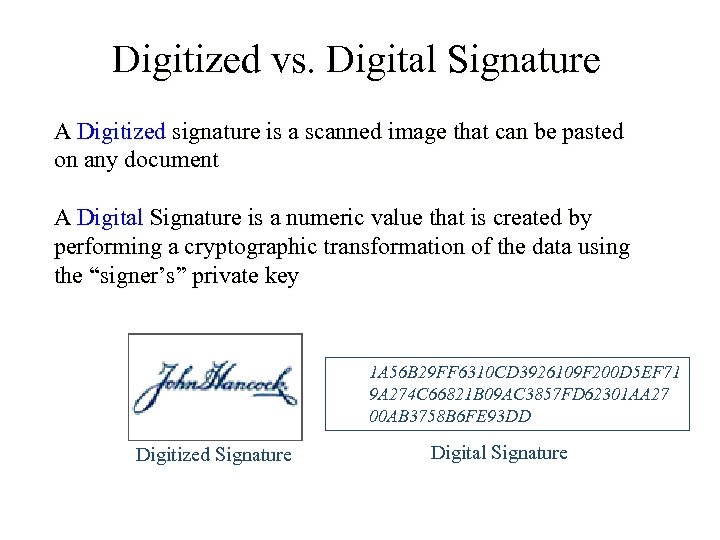
Digitized vs. Digital Signature A Digitized signature is a scanned image that can be pasted on any document A Digital Signature is a numeric value that is created by performing a cryptographic transformation of the data using the “signer’s” private key 1 A 56 B 29 FF 6310 CD 3926109 F 200 D 5 EF 71 9 A 274 C 66821 B 09 AC 3857 FD 62301 AA 27 00 AB 3758 B 6 FE 93 DD Digitized Signature Digital Signature

Digital Certificates • Analogous to a Driver’s License or Employee Badge – Issued By Some Authority That Members Have in Common – Issued Under Some Set of Rules (Policies) – Document Issued Contains Public Information • Not Sensitive • Not Compromising – Provides Trust to Peers, Identification to Others
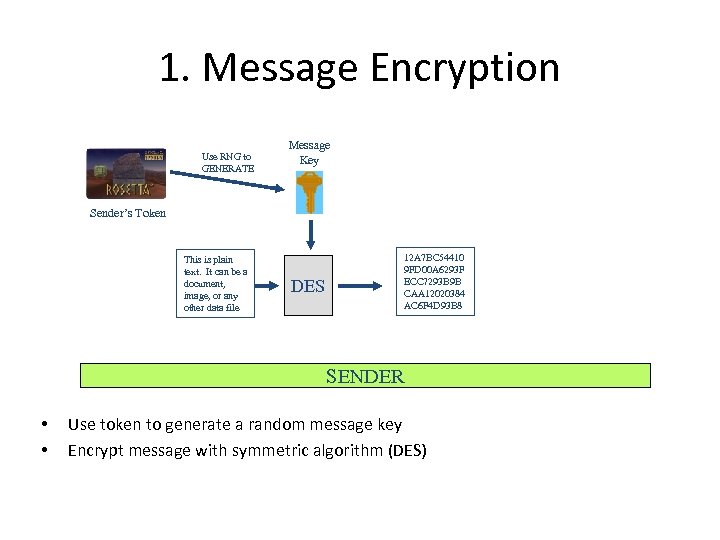
1. Message Encryption Use RNG to GENERATE Message Key Sender’s Token This is plain text. It can be a document, image, or any other data file DES 12 A 7 BC 54410 9 FD 00 A 6293 F ECC 7293 B 9 B CAA 12020384 AC 6 F 4 D 93 B 8 SENDER • • Use token to generate a random message key Encrypt message with symmetric algorithm (DES)
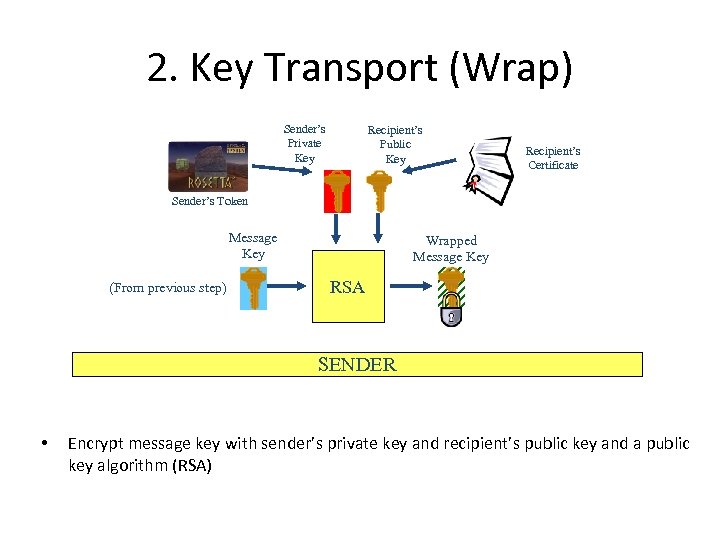
2. Key Transport (Wrap) Sender’s Private Key Recipient’s Public Key Recipient’s Certificate Sender’s Token Message Key (From previous step) Wrapped Message Key RSA SENDER • Encrypt message key with sender’s private key and recipient’s public key and a public key algorithm (RSA)
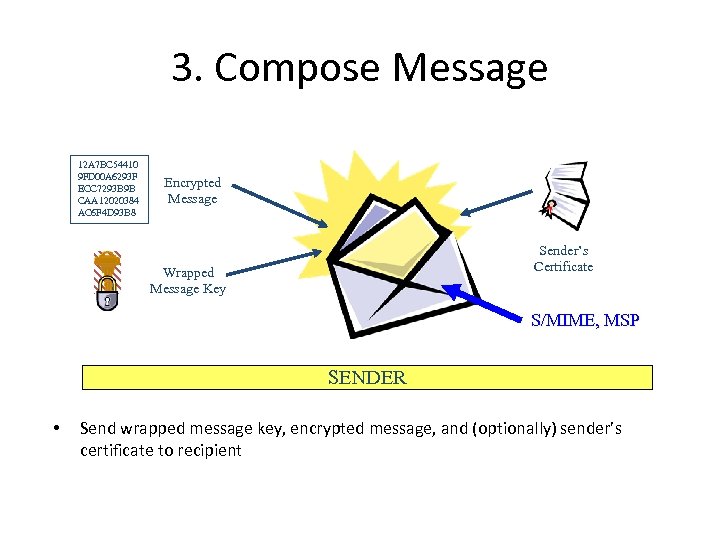
3. Compose Message 12 A 7 BC 54410 9 FD 00 A 6293 F ECC 7293 B 9 B CAA 12020384 AC 6 F 4 D 93 B 8 Encrypted Message Sender’s Certificate Wrapped Message Key S/MIME, MSP SENDER • Send wrapped message key, encrypted message, and (optionally) sender’s certificate to recipient
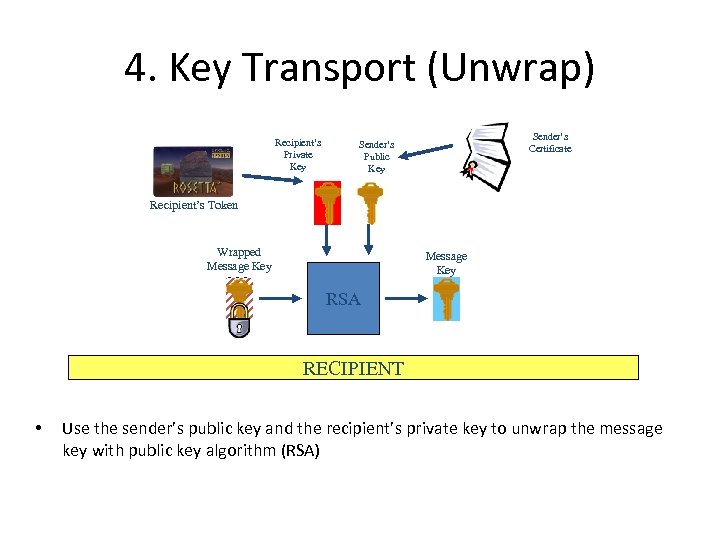
4. Key Transport (Unwrap) Recipient’s Private Key Sender’s Certificate Sender’s Public Key Recipient’s Token Wrapped Message Key RSA RECIPIENT • Use the sender’s public key and the recipient’s private key to unwrap the message key with public key algorithm (RSA)
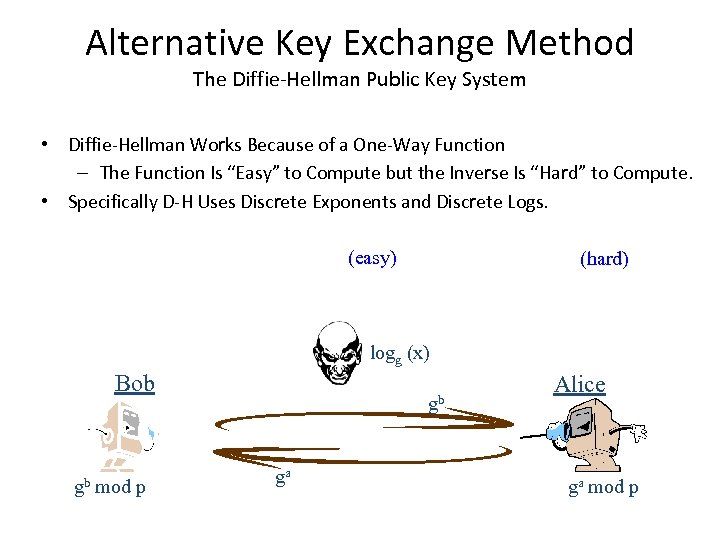
Alternative Key Exchange Method The Diffie-Hellman Public Key System • Diffie-Hellman Works Because of a One-Way Function – The Function Is “Easy” to Compute but the Inverse Is “Hard” to Compute. • Specifically D-H Uses Discrete Exponents and Discrete Logs. (easy) (hard) logg (x) Bob gb mod p gb ga Alice ga mod p
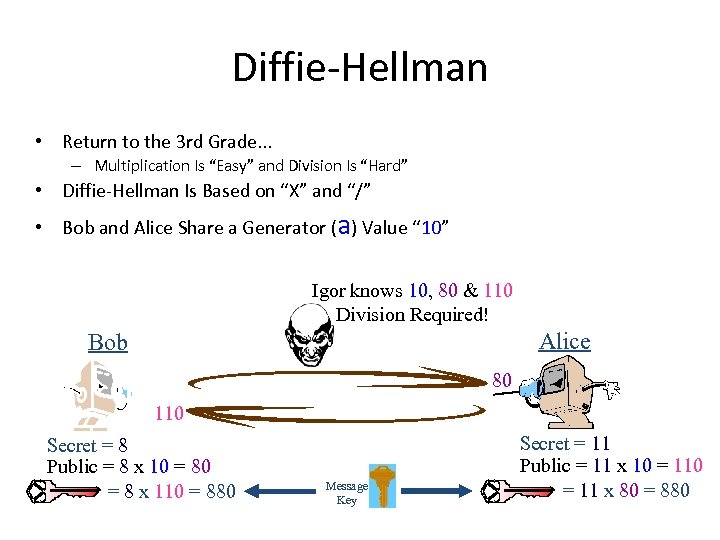
Diffie-Hellman • Return to the 3 rd Grade. . . – Multiplication Is “Easy” and Division Is “Hard” • Diffie-Hellman Is Based on “X” and “/” • Bob and Alice Share a Generator (a) Value “ 10” Igor knows 10, 80 & 110 10 Division Required! Alice Bob 80 110 Secret = 8 Public = 8 x 10 = 8 x 110 = 880 Message Key Secret = 11 Public = 11 x 10 = 11 x 80 = 880
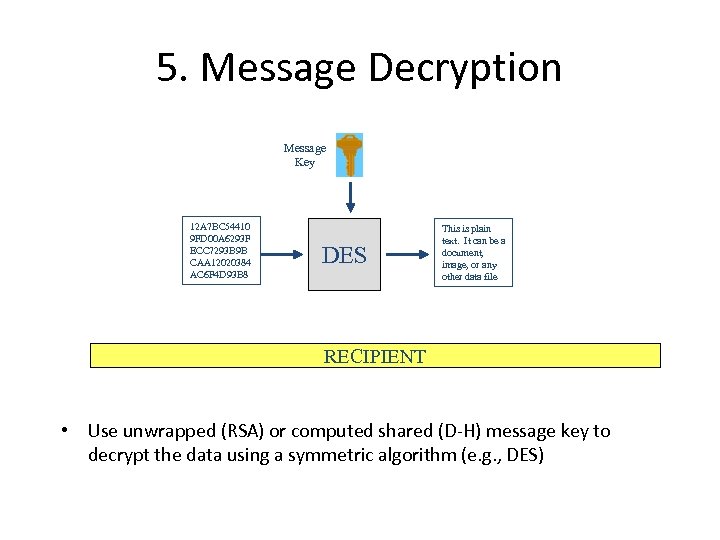
5. Message Decryption Message Key 12 A 7 BC 54410 9 FD 00 A 6293 F ECC 7293 B 9 B CAA 12020384 AC 6 F 4 D 93 B 8 DES This is plain text. It can be a document, image, or any other data file RECIPIENT • Use unwrapped (RSA) or computed shared (D-H) message key to decrypt the data using a symmetric algorithm (e. g. , DES)
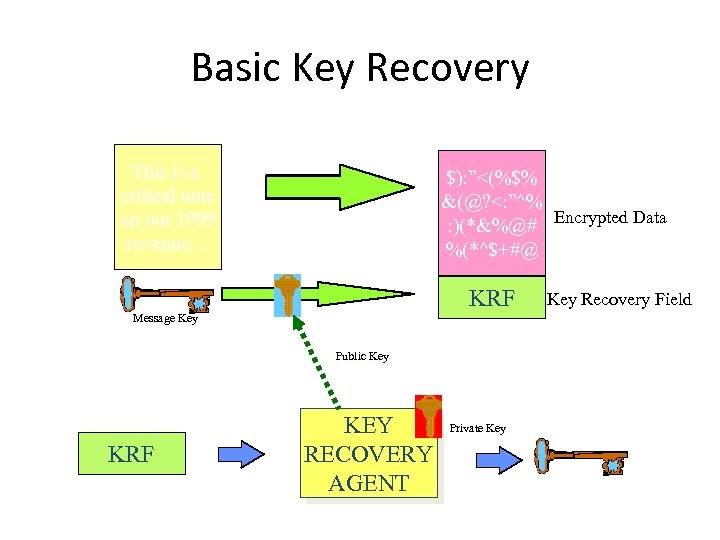
Basic Key Recovery This is a critical note on our 1999 revenue. . . $): ”<(%$% &(@? <: ”^% : )(*&%@# Encrypted Data %(*^$+#@ KRF Message Key Public Key KRF KEY RECOVERY AGENT Private Key Recovery Field

Using Security Services

Using Security Services s Digital Signatures • Client Authentication on a Web Server – Netscape, Microsoft – Compared to Access Control List on Server • Server Authentication on a Web Client – Netscape, Microsoft – Stops Man-in-the-middle Attack • Message Authentication – S/MIME E-mail Message – Netscape, MS Outlook Express 98 • Audit – Authentication of User Provides Non-repudiation of Client Access – May Provide Legal Proof for Later Arbitration
Using Security Services • Confidentiality – Link Encryption • IPSec (Layers 2/3) – Secure tunnel between VPN boxes • SSL (Layers 4/5) – Secure “tunnel” to web server – Netscape, Microsoft • FTP (Layers 6/7) – Secure file transfer

PKI Public Key Infrastructure
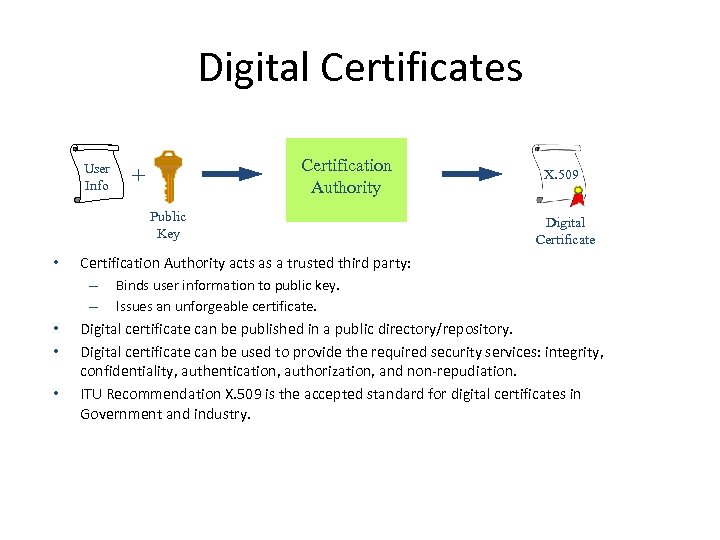
Digital Certificates User Info Certification Authority + Public Key • • X. 509 Digital Certificate Certification Authority acts as a trusted third party: – Binds user information to public key. – Issues an unforgeable certificate. Digital certificate can be published in a public directory/repository. Digital certificate can be used to provide the required security services: integrity, confidentiality, authentication, authorization, and non-repudiation. ITU Recommendation X. 509 is the accepted standard for digital certificates in Government and industry.

X. 509 Certificates (cont. ) • X. 509 Version 3 certificates: – Defined extensions that can be added to the base certificate: • • • public key information policy information additional subject attribute information constraint information CRL information – Widely accepted in Gov’t and industry. – Commercial and Gov’t implementations.
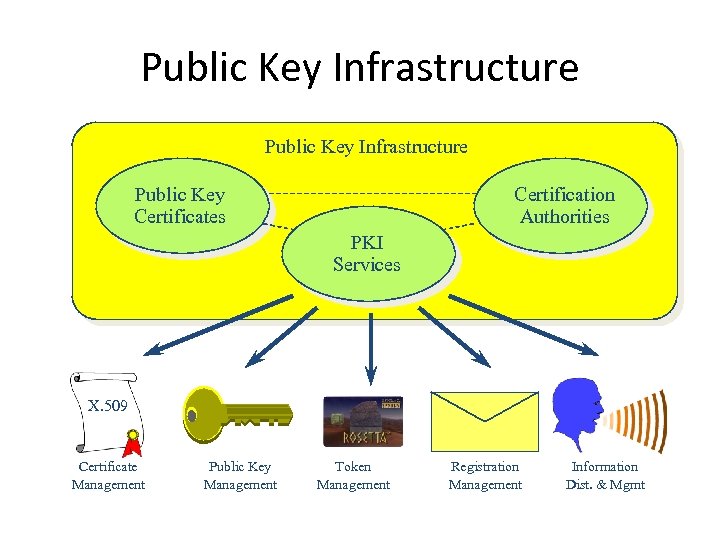
Public Key Infrastructure Public Key Certificates Certification Authorities PKI Services X. 509 Certificate Management Public Key Management Token Management Registration Management Information Dist. & Mgmt
Risk Reduction and PKI Business Requirements Legal Requirements X. 509 Technology Requirements

Summary n Cryptographic Security Solutions: â Provide Security Assurances: â Privacy/Confidentiality â Data Integrity â Source and Destination (Client/Server/User) Authentication â Access Control â Non-Repudiation â Support The Emerging PKI Marketplace n PKI Security Solutions: â Enable Enterprise E-Commerce â Issue, Manage, Revoke Certificates â Apply Enterprise Certificate Policies and Procedures
29742dd89b5e0eff1c9bbee5b6bdd112.ppt