0ae8f07e84e003cc2703237eeddcc631.ppt
- Количество слайдов: 25
 Defense-in-Depth: Turning the Network Inside Out Joel Snyder, Ph. D. Senior Partner Opus One jms@opus 1. com
Defense-in-Depth: Turning the Network Inside Out Joel Snyder, Ph. D. Senior Partner Opus One jms@opus 1. com
 2 -Part Presentation l PART 1 (now): Building a “Crunchy” Network • 802. 1 X, Digital Certificates, VLANs, Multiple levels of ACLs, Firewall/VPN on the NIC, NIDS/NIPS l PART 2 (at 11: 15 a. m. ): Emerging Technologies • Application-aware firewalls, Rate/Content-based IPS, “target”-based IDS
2 -Part Presentation l PART 1 (now): Building a “Crunchy” Network • 802. 1 X, Digital Certificates, VLANs, Multiple levels of ACLs, Firewall/VPN on the NIC, NIDS/NIPS l PART 2 (at 11: 15 a. m. ): Emerging Technologies • Application-aware firewalls, Rate/Content-based IPS, “target”-based IDS
![Most networks focus on perimeter defense l “[AT&T’s gateway creates] a sort of crunchy Most networks focus on perimeter defense l “[AT&T’s gateway creates] a sort of crunchy](https://present5.com/presentation/0ae8f07e84e003cc2703237eeddcc631/image-3.jpg) Most networks focus on perimeter defense l “[AT&T’s gateway creates] a sort of crunchy shell around a soft, chewy center. ” (Bill Cheswick, Design of a Secure Internet Gateway, April, 1990) Big Bad Internet
Most networks focus on perimeter defense l “[AT&T’s gateway creates] a sort of crunchy shell around a soft, chewy center. ” (Bill Cheswick, Design of a Secure Internet Gateway, April, 1990) Big Bad Internet
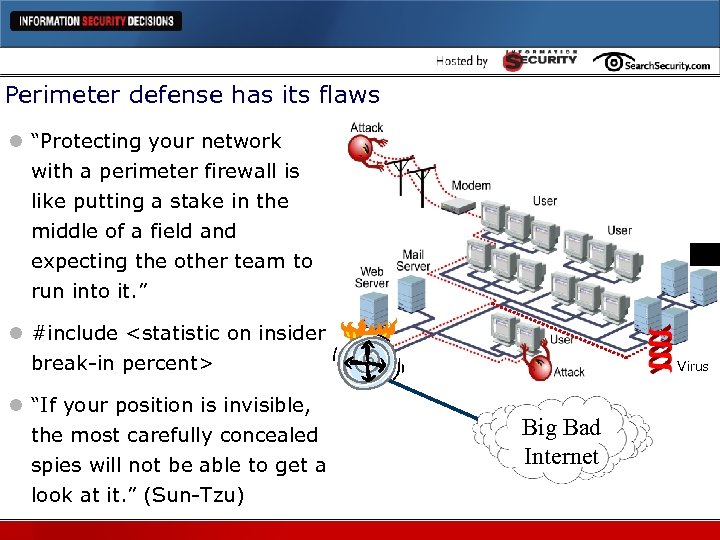 Perimeter defense has its flaws l “Protecting your network with a perimeter firewall is like putting a stake in the middle of a field and expecting the other team to run into it. ” l #include
Perimeter defense has its flaws l “Protecting your network with a perimeter firewall is like putting a stake in the middle of a field and expecting the other team to run into it. ” l #include
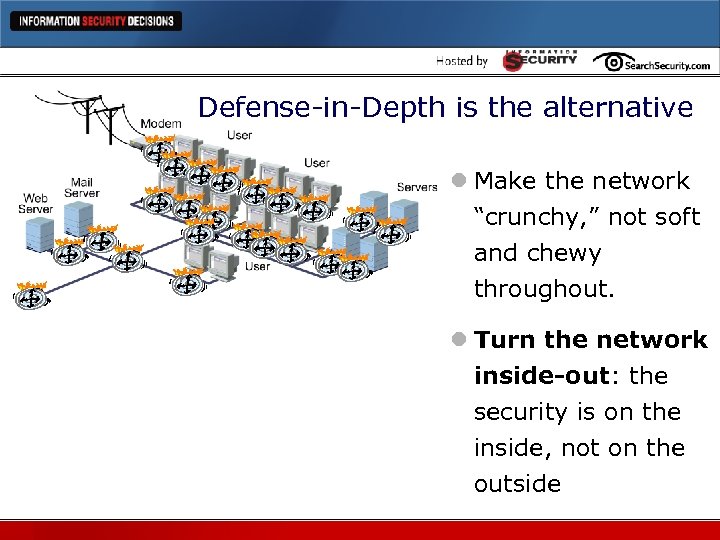 Defense-in-Depth is the alternative l Make the network “crunchy, ” not soft and chewy throughout. l Turn the network inside-out: the security is on the inside, not on the outside
Defense-in-Depth is the alternative l Make the network “crunchy, ” not soft and chewy throughout. l Turn the network inside-out: the security is on the inside, not on the outside
 We don’t do defense-in-depth because. . . l Cost • The cost of adding firewall “brains” has been prohibitive l Authentication • l Performance • Firewalls are slower than Gigabit switches l Management • Determining the “manyto-many” relationships are difficult How do you know who has that IP address anyway? What about NATed users? l Policy • It’s hard to describe the security policy for inside users; it’s much easier to describe the Internet-oriented policy
We don’t do defense-in-depth because. . . l Cost • The cost of adding firewall “brains” has been prohibitive l Authentication • l Performance • Firewalls are slower than Gigabit switches l Management • Determining the “manyto-many” relationships are difficult How do you know who has that IP address anyway? What about NATed users? l Policy • It’s hard to describe the security policy for inside users; it’s much easier to describe the Internet-oriented policy
 Whoops. I lied. My bad. l. Cost • dropping l. Performance • increasing l. Management • getting better l. Authentication • solved l. Policy • OK, there had to be something we couldn’t solve with technology
Whoops. I lied. My bad. l. Cost • dropping l. Performance • increasing l. Management • getting better l. Authentication • solved l. Policy • OK, there had to be something we couldn’t solve with technology
 You can implement Defense-in-Depth New and Exciting l 802. 1 X Authentication l Digital Certificates l VLANs as Security Barriers Not-so-bleeding-edge l MAC lock-down on ports l Authenticated routing l Rate-limiting (Do. S resistance) l Host-based IDS l Multiple levels of ACLs l RADIUS authentication l Firewall/VPN on the NIC l SSH for management l Network Intrusion Detection/Prevention Systems l SNMPv 3 and not SNMPv 2 l “Access Ethernet” dedicated management network
You can implement Defense-in-Depth New and Exciting l 802. 1 X Authentication l Digital Certificates l VLANs as Security Barriers Not-so-bleeding-edge l MAC lock-down on ports l Authenticated routing l Rate-limiting (Do. S resistance) l Host-based IDS l Multiple levels of ACLs l RADIUS authentication l Firewall/VPN on the NIC l SSH for management l Network Intrusion Detection/Prevention Systems l SNMPv 3 and not SNMPv 2 l “Access Ethernet” dedicated management network
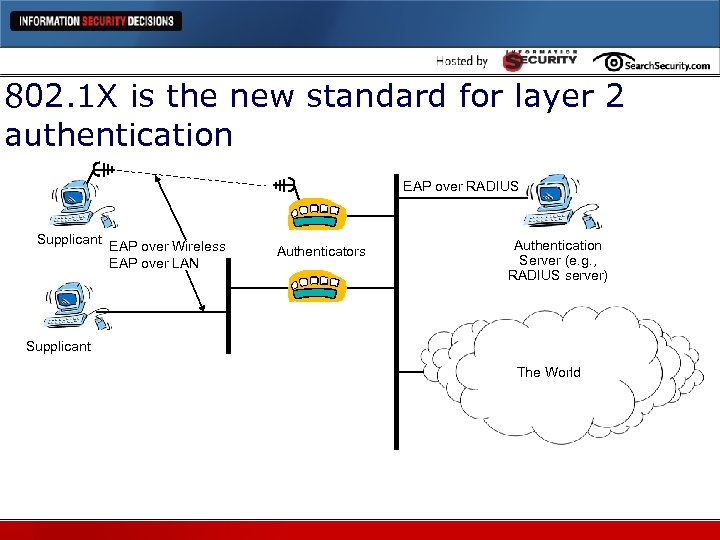 802. 1 X is the new standard for layer 2 authentication EAP over RADIUS Supplicant EAP over Wireless EAP over LAN Authenticators Authentication Server (e. g. , RADIUS server) Supplicant The World
802. 1 X is the new standard for layer 2 authentication EAP over RADIUS Supplicant EAP over Wireless EAP over LAN Authenticators Authentication Server (e. g. , RADIUS server) Supplicant The World
 802. 1 X on every port adds security l In the wireless environment, 802. 1 X is absolutely required • 802. 11 i and WPA (Wi-Fi Protected Access) use 802. 1 X • Pure 802. 1 X for authentication solves most WEP problems l In the wired environment, 802. 1 X adds security • Microsoft and Apple give it to you for free l 802. 1 X ties to RADIUS which means… • You can use RADIUS to push authorization information to wired and wireless equipment § VLANs & Filters “Here’s your WEP key for the next 30 seconds. . . ” EAP over RADIUS “Put the user on VLAN x and here’s what he has access to. . . ”
802. 1 X on every port adds security l In the wireless environment, 802. 1 X is absolutely required • 802. 11 i and WPA (Wi-Fi Protected Access) use 802. 1 X • Pure 802. 1 X for authentication solves most WEP problems l In the wired environment, 802. 1 X adds security • Microsoft and Apple give it to you for free l 802. 1 X ties to RADIUS which means… • You can use RADIUS to push authorization information to wired and wireless equipment § VLANs & Filters “Here’s your WEP key for the next 30 seconds. . . ” EAP over RADIUS “Put the user on VLAN x and here’s what he has access to. . . ”
 What are pitfalls and caveats with 802. 1 X? l 802. 1 X does not mandate an authentication method • • So you have to pick one (TLS, TTLS, or PEAP) • Strategy: hold off until this battle is settled by the IETF There a bunch of choices and a bunch of interoperability problems (TTLS vs. PEAP) l 802. 1 X does not require you to swap out your RADIUS infrastructure • You can get a new, small server which will proxy to your existing RADIUS servers l 802. 1 X will not immediately be “full featured” • Authorization information, such as ACLs and VLANs, is still awaiting “industry agreement”
What are pitfalls and caveats with 802. 1 X? l 802. 1 X does not mandate an authentication method • • So you have to pick one (TLS, TTLS, or PEAP) • Strategy: hold off until this battle is settled by the IETF There a bunch of choices and a bunch of interoperability problems (TTLS vs. PEAP) l 802. 1 X does not require you to swap out your RADIUS infrastructure • You can get a new, small server which will proxy to your existing RADIUS servers l 802. 1 X will not immediately be “full featured” • Authorization information, such as ACLs and VLANs, is still awaiting “industry agreement”
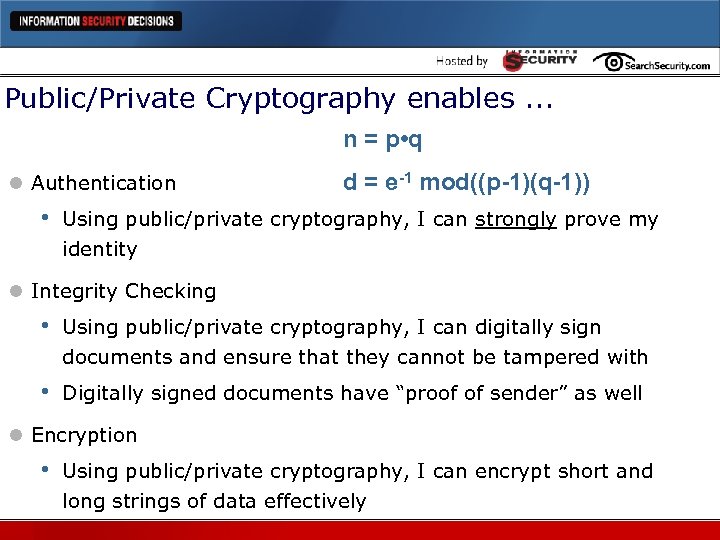 Public/Private Cryptography enables. . . n = p • q l Authentication • d = e-1 mod((p-1)(q-1)) Using public/private cryptography, I can strongly prove my identity l Integrity Checking • Using public/private cryptography, I can digitally sign documents and ensure that they cannot be tampered with • Digitally signed documents have “proof of sender” as well l Encryption • Using public/private cryptography, I can encrypt short and long strings of data effectively
Public/Private Cryptography enables. . . n = p • q l Authentication • d = e-1 mod((p-1)(q-1)) Using public/private cryptography, I can strongly prove my identity l Integrity Checking • Using public/private cryptography, I can digitally sign documents and ensure that they cannot be tampered with • Digitally signed documents have “proof of sender” as well l Encryption • Using public/private cryptography, I can encrypt short and long strings of data effectively
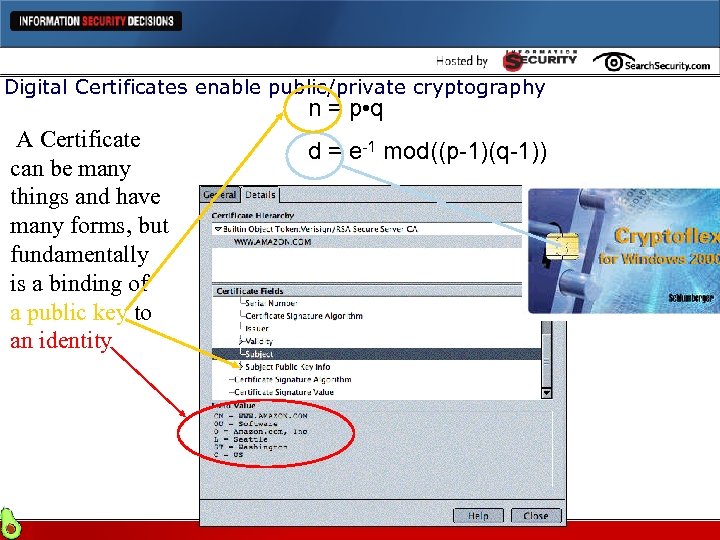 Digital Certificates enable public/private cryptography n = p • q A Certificate can be many things and have many forms, but fundamentally is a binding of a public key to an identity d = e-1 mod((p-1)(q-1))
Digital Certificates enable public/private cryptography n = p • q A Certificate can be many things and have many forms, but fundamentally is a binding of a public key to an identity d = e-1 mod((p-1)(q-1))
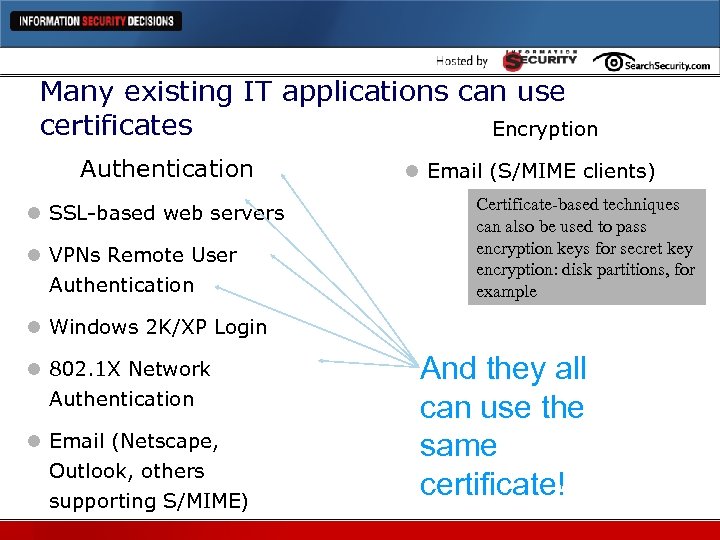 Many existing IT applications can use certificates Encryption Authentication l SSL-based web servers l VPNs Remote User Authentication l Email (S/MIME clients) Certificate-based techniques can also be used to pass encryption keys for secret key encryption: disk partitions, for example l Windows 2 K/XP Login l 802. 1 X Network Authentication l Email (Netscape, Outlook, others supporting S/MIME) And they all can use the same certificate!
Many existing IT applications can use certificates Encryption Authentication l SSL-based web servers l VPNs Remote User Authentication l Email (S/MIME clients) Certificate-based techniques can also be used to pass encryption keys for secret key encryption: disk partitions, for example l Windows 2 K/XP Login l 802. 1 X Network Authentication l Email (Netscape, Outlook, others supporting S/MIME) And they all can use the same certificate!
 So why isn’t everyone using them? l PKI manufacturers have made it more complex than it needs to be • “Solve all the problems up front, for country-wise deployments” seems to be their strategy l And expensive! l Certificate Revocation List strategies have not been coherent • Online Certificate Status Protocol may help l Certificate Enrollment is chaotic • • Four different protocols in common use Plus a few proprietary ones
So why isn’t everyone using them? l PKI manufacturers have made it more complex than it needs to be • “Solve all the problems up front, for country-wise deployments” seems to be their strategy l And expensive! l Certificate Revocation List strategies have not been coherent • Online Certificate Status Protocol may help l Certificate Enrollment is chaotic • • Four different protocols in common use Plus a few proprietary ones
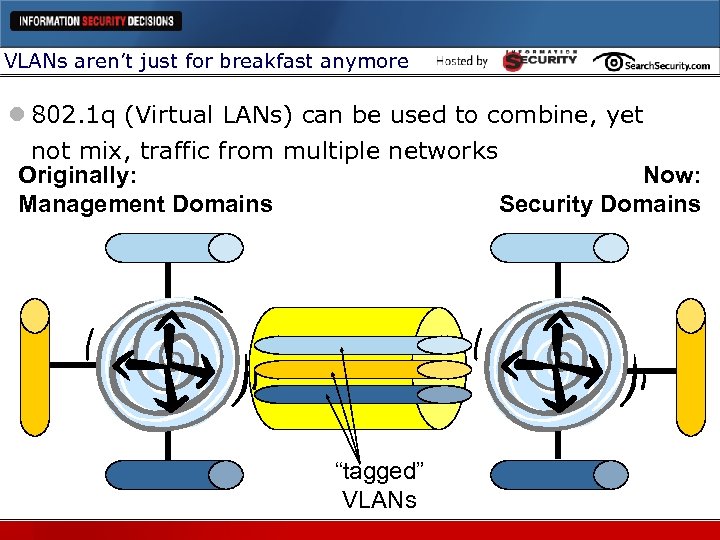 VLANs aren’t just for breakfast anymore l 802. 1 q (Virtual LANs) can be used to combine, yet not mix, traffic from multiple networks Originally: Now: Management Domains Security Domains “tagged” VLANs
VLANs aren’t just for breakfast anymore l 802. 1 q (Virtual LANs) can be used to combine, yet not mix, traffic from multiple networks Originally: Now: Management Domains Security Domains “tagged” VLANs
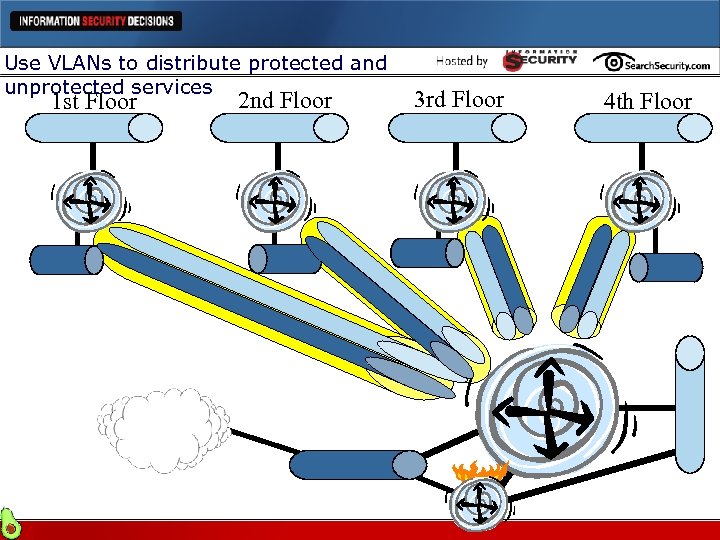 Use VLANs to distribute protected and unprotected services 1 st Floor 2 nd Floor 3 rd Floor 4 th Floor
Use VLANs to distribute protected and unprotected services 1 st Floor 2 nd Floor 3 rd Floor 4 th Floor
 Using VLANs for security has its risks l If packets jump from one VLAN to the other. . . the game is over l Management of switching infrastructure is now as important as management of firewalls l Your switches are your weak links • • Attacks Bugs l Switch vendors have a very bad reputation in this area Risk/Benefit Analysis
Using VLANs for security has its risks l If packets jump from one VLAN to the other. . . the game is over l Management of switching infrastructure is now as important as management of firewalls l Your switches are your weak links • • Attacks Bugs l Switch vendors have a very bad reputation in this area Risk/Benefit Analysis
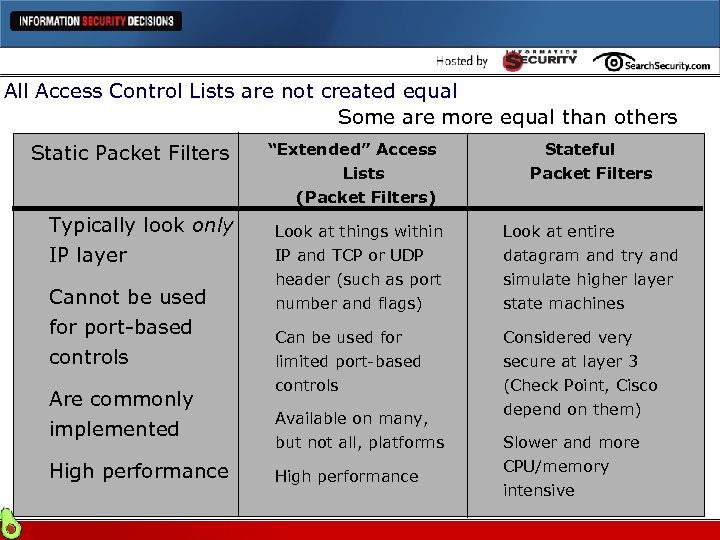 All Access Control Lists are not created equal Some are more equal than others “Extended” Access Lists Static Packet Filters Stateful Packet Filters (Packet Filters) l Typically look only l IP layer l Cannot be used for port-based controls l Are commonly implemented l High performance Look at things within IP and TCP or UDP header (such as port number and flags) l Can be used for limited port-based controls l Available on many, but not all, platforms l High performance l Look at entire datagram and try and simulate higher layer state machines l Considered very secure at layer 3 (Check Point, Cisco depend on them) l Slower and more CPU/memory intensive
All Access Control Lists are not created equal Some are more equal than others “Extended” Access Lists Static Packet Filters Stateful Packet Filters (Packet Filters) l Typically look only l IP layer l Cannot be used for port-based controls l Are commonly implemented l High performance Look at things within IP and TCP or UDP header (such as port number and flags) l Can be used for limited port-based controls l Available on many, but not all, platforms l High performance l Look at entire datagram and try and simulate higher layer state machines l Considered very secure at layer 3 (Check Point, Cisco depend on them) l Slower and more CPU/memory intensive
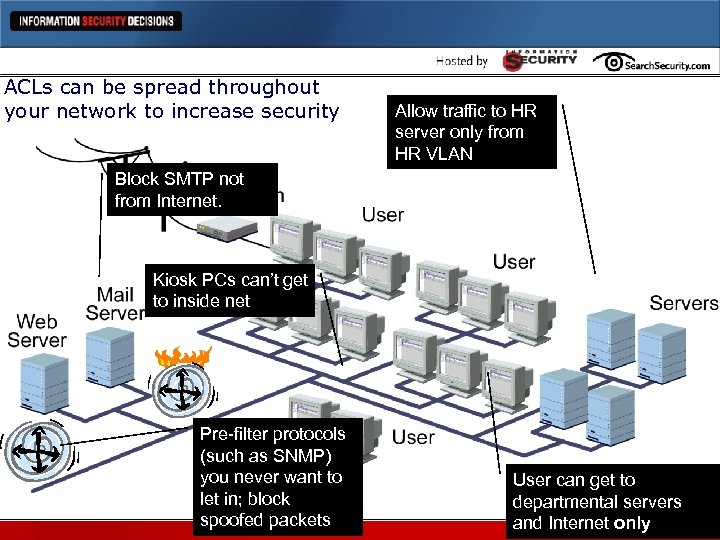 ACLs can be spread throughout your network to increase security Allow traffic to HR server only from HR VLAN Block SMTP not from Internet. Kiosk PCs can’t get to inside net Pre-filter protocols (such as SNMP) you never want to let in; block spoofed packets User can get to departmental servers and Internet only
ACLs can be spread throughout your network to increase security Allow traffic to HR server only from HR VLAN Block SMTP not from Internet. Kiosk PCs can’t get to inside net Pre-filter protocols (such as SNMP) you never want to let in; block spoofed packets User can get to departmental servers and Internet only
 ACLs everywhere is a tricky situation l Static ACLs on ports can be difficult to manage and maintain (at this time) l 802. 1 X-derived ACLs don’t have sufficient context to work at IP layer (yet) l Not every device has the capability l Not every policy-based security server has the ability But this is a technology coming very soon to a theatre near you! “Put the user on VLAN x and here’s what he has access to. . . ”
ACLs everywhere is a tricky situation l Static ACLs on ports can be difficult to manage and maintain (at this time) l 802. 1 X-derived ACLs don’t have sufficient context to work at IP layer (yet) l Not every device has the capability l Not every policy-based security server has the ability But this is a technology coming very soon to a theatre near you! “Put the user on VLAN x and here’s what he has access to. . . ”
 You can put a firewall on a NIC l Technically, this is not making the network itself crunchy and more secure l “Defense in Depth” isn’t too concerned with labels y lic Po Po lic y Policy Server Vendors: 3 COM, Snap, Omni. Cluster, Net. Master, Corrent
You can put a firewall on a NIC l Technically, this is not making the network itself crunchy and more secure l “Defense in Depth” isn’t too concerned with labels y lic Po Po lic y Policy Server Vendors: 3 COM, Snap, Omni. Cluster, Net. Master, Corrent
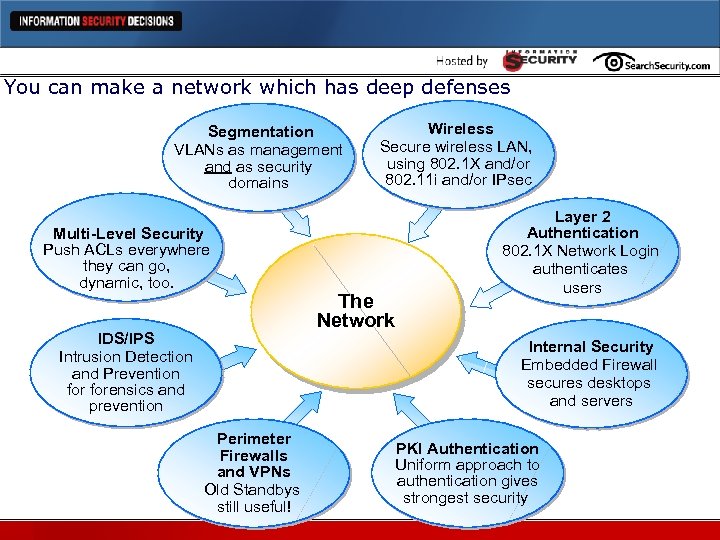 You can make a network which has deep defenses Segmentation VLANs as management and as security domains Multi-Level Security Push ACLs everywhere they can go, dynamic, too. IDS/IPS Intrusion Detection and Prevention forensics and prevention Wireless Secure wireless LAN, using 802. 1 X and/or 802. 11 i and/or IPsec The Network Layer 2 Authentication 802. 1 X Network Login authenticates users Internal Security Embedded Firewall secures desktops and servers Perimeter Firewalls and VPNs Old Standbys still useful! PKI Authentication Uniform approach to authentication gives strongest security
You can make a network which has deep defenses Segmentation VLANs as management and as security domains Multi-Level Security Push ACLs everywhere they can go, dynamic, too. IDS/IPS Intrusion Detection and Prevention forensics and prevention Wireless Secure wireless LAN, using 802. 1 X and/or 802. 11 i and/or IPsec The Network Layer 2 Authentication 802. 1 X Network Login authenticates users Internal Security Embedded Firewall secures desktops and servers Perimeter Firewalls and VPNs Old Standbys still useful! PKI Authentication Uniform approach to authentication gives strongest security
 Questions, comments? Be sure to join me in 15 minutes for the second half of this presentation! Right here!
Questions, comments? Be sure to join me in 15 minutes for the second half of this presentation! Right here!
 Featured Topic: Defense-in-depth Includes an on demand webcast with Joel titled Defense-in-Depth: Turning the Network Inside-Out, and resources from both Information Security and Search. Security. http: //searchsecurity. com/Featured. Topic/ defenseindepth
Featured Topic: Defense-in-depth Includes an on demand webcast with Joel titled Defense-in-Depth: Turning the Network Inside-Out, and resources from both Information Security and Search. Security. http: //searchsecurity. com/Featured. Topic/ defenseindepth


