3bcb7167baa0fae0a2546d9f2c72302b.ppt
- Количество слайдов: 43
 Defending the Digital Frontier
Defending the Digital Frontier
 Rudy Giuliani’s Call to Action The time has come for senior executives of U. S. corporations to follow the President's lead and make security a mainstream business critical, board-level issue…the time when security-related decisions could be left to persons at a mid -manager level or decided solely upon budgetary considerations has passed. Senior executives must now take the steps to plan, prepare and practice to address their organizational security threats and challenges. 2
Rudy Giuliani’s Call to Action The time has come for senior executives of U. S. corporations to follow the President's lead and make security a mainstream business critical, board-level issue…the time when security-related decisions could be left to persons at a mid -manager level or decided solely upon budgetary considerations has passed. Senior executives must now take the steps to plan, prepare and practice to address their organizational security threats and challenges. 2
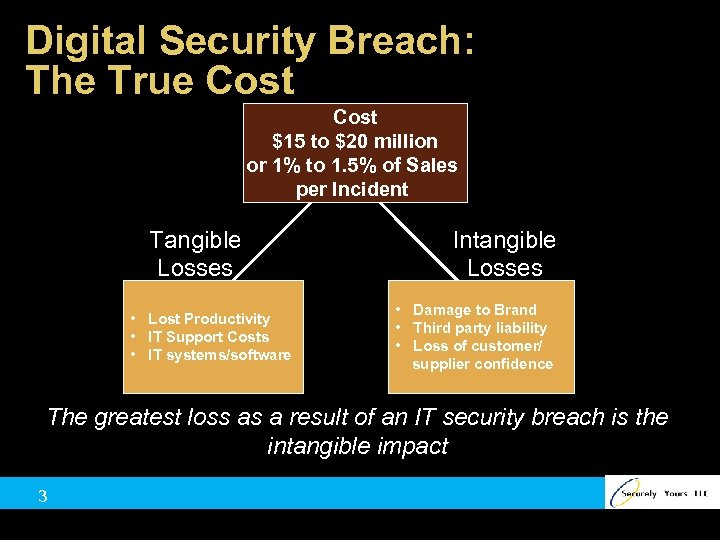 Digital Security Breach: The True Cost $15 to $20 million or 1% to 1. 5% of Sales per Incident Tangible Losses • Lost Productivity • IT Support Costs • IT systems/software Intangible Losses • Damage to Brand • Third party liability • Loss of customer/ supplier confidence The greatest loss as a result of an IT security breach is the intangible impact 3
Digital Security Breach: The True Cost $15 to $20 million or 1% to 1. 5% of Sales per Incident Tangible Losses • Lost Productivity • IT Support Costs • IT systems/software Intangible Losses • Damage to Brand • Third party liability • Loss of customer/ supplier confidence The greatest loss as a result of an IT security breach is the intangible impact 3
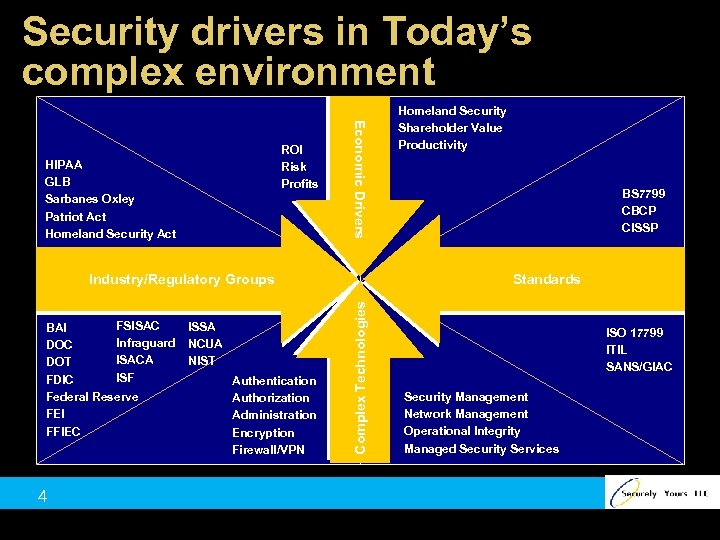 Security drivers in Today’s complex environment HIPAA GLB Sarbanes Oxley Patriot Act Homeland Security Act Economic Drivers ROI Risk Profits FSISAC BAI Infraguard DOC ISACA DOT ISF FDIC Federal Reserve FEI FFIEC 4 ISSA NCUA NIST Authentication Authorization Administration Encryption Firewall/VPN BS 7799 CBCP CISSP Standards Complex Technologies Industry/Regulatory Groups Homeland Security Shareholder Value Productivity ISO 17799 ITIL SANS/GIAC Security Management Network Management Operational Integrity Managed Security Services
Security drivers in Today’s complex environment HIPAA GLB Sarbanes Oxley Patriot Act Homeland Security Act Economic Drivers ROI Risk Profits FSISAC BAI Infraguard DOC ISACA DOT ISF FDIC Federal Reserve FEI FFIEC 4 ISSA NCUA NIST Authentication Authorization Administration Encryption Firewall/VPN BS 7799 CBCP CISSP Standards Complex Technologies Industry/Regulatory Groups Homeland Security Shareholder Value Productivity ISO 17799 ITIL SANS/GIAC Security Management Network Management Operational Integrity Managed Security Services
 Multiple Drivers Are Bringing Digital Security to the Boardroom Triple Witching Event Homeland Defense Privacy/Fraud (Homeland Security Act, USA Patriot Act) (CA 1386, GLB, HIPAA) tal igi rity D u ec S Sarbanes-Oxley 5
Multiple Drivers Are Bringing Digital Security to the Boardroom Triple Witching Event Homeland Defense Privacy/Fraud (Homeland Security Act, USA Patriot Act) (CA 1386, GLB, HIPAA) tal igi rity D u ec S Sarbanes-Oxley 5
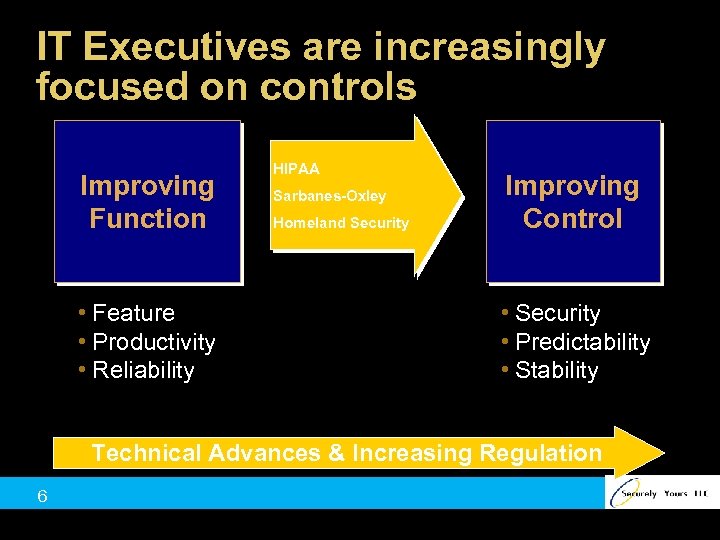 IT Executives are increasingly focused on controls Improving Function • Feature • Productivity • Reliability HIPAA Sarbanes-Oxley Homeland Security Improving Control • Security • Predictability • Stability Technical Advances & Increasing Regulation 6
IT Executives are increasingly focused on controls Improving Function • Feature • Productivity • Reliability HIPAA Sarbanes-Oxley Homeland Security Improving Control • Security • Predictability • Stability Technical Advances & Increasing Regulation 6
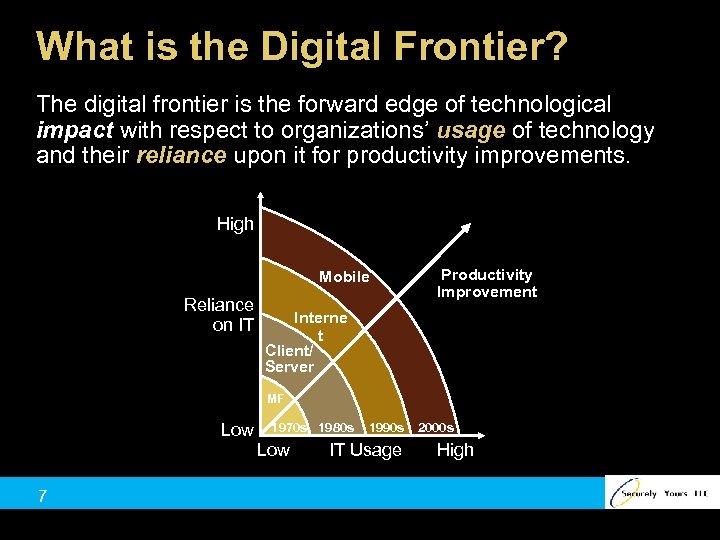 What is the Digital Frontier? The digital frontier is the forward edge of technological impact with respect to organizations’ usage of technology and their reliance upon it for productivity improvements. High Mobile Reliance on IT Productivity Improvement Interne t Client/ Server MF Low 1970 s 1980 s Low 7 1990 s 2000 s IT Usage High
What is the Digital Frontier? The digital frontier is the forward edge of technological impact with respect to organizations’ usage of technology and their reliance upon it for productivity improvements. High Mobile Reliance on IT Productivity Improvement Interne t Client/ Server MF Low 1970 s 1980 s Low 7 1990 s 2000 s IT Usage High
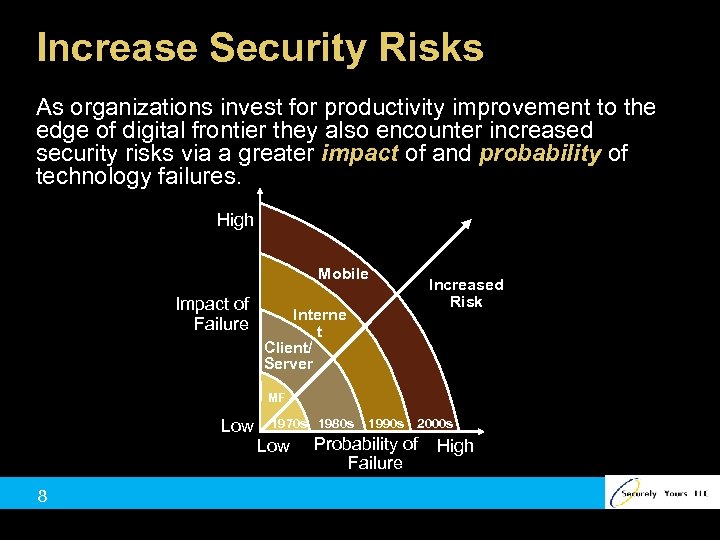 Increase Security Risks As organizations invest for productivity improvement to the edge of digital frontier they also encounter increased security risks via a greater impact of and probability of technology failures. High Mobile Impact of Failure Interne t Client/ Server Increased Risk MF Low 1970 s 1980 s Low 8 1990 s 2000 s Probability of Failure High
Increase Security Risks As organizations invest for productivity improvement to the edge of digital frontier they also encounter increased security risks via a greater impact of and probability of technology failures. High Mobile Impact of Failure Interne t Client/ Server Increased Risk MF Low 1970 s 1980 s Low 8 1990 s 2000 s Probability of Failure High
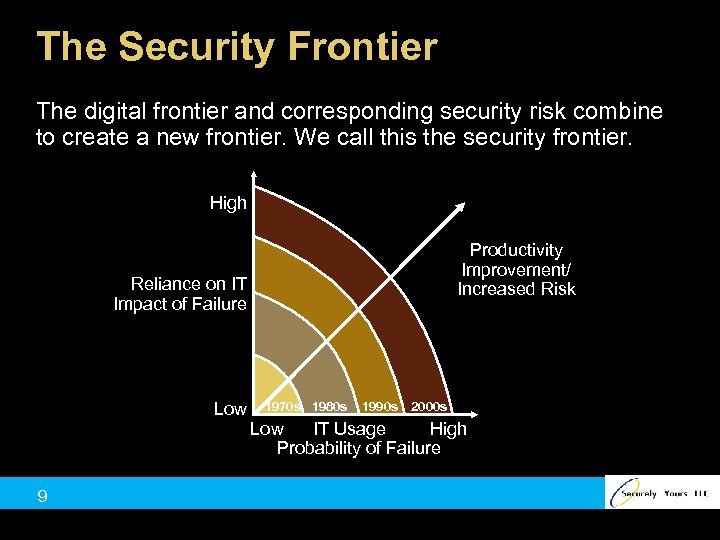 The Security Frontier The digital frontier and corresponding security risk combine to create a new frontier. We call this the security frontier. High Productivity Improvement/ Increased Risk Reliance on IT Impact of Failure Low 1970 s 1980 s 1990 s 2000 s Low IT Usage High Probability of Failure 9
The Security Frontier The digital frontier and corresponding security risk combine to create a new frontier. We call this the security frontier. High Productivity Improvement/ Increased Risk Reliance on IT Impact of Failure Low 1970 s 1980 s 1990 s 2000 s Low IT Usage High Probability of Failure 9
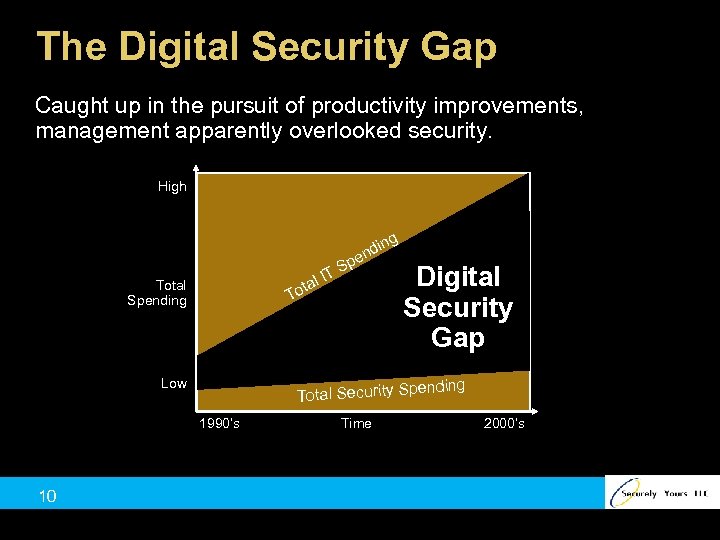 The Digital Security Gap Caught up in the pursuit of productivity improvements, management apparently overlooked security. High ta To Total Spending Low p Digital Security Gap ending Total Security Sp 1990’s 10 S l IT ing d en Time 2000’s
The Digital Security Gap Caught up in the pursuit of productivity improvements, management apparently overlooked security. High ta To Total Spending Low p Digital Security Gap ending Total Security Sp 1990’s 10 S l IT ing d en Time 2000’s
 6 Key Security Characteristics 11
6 Key Security Characteristics 11
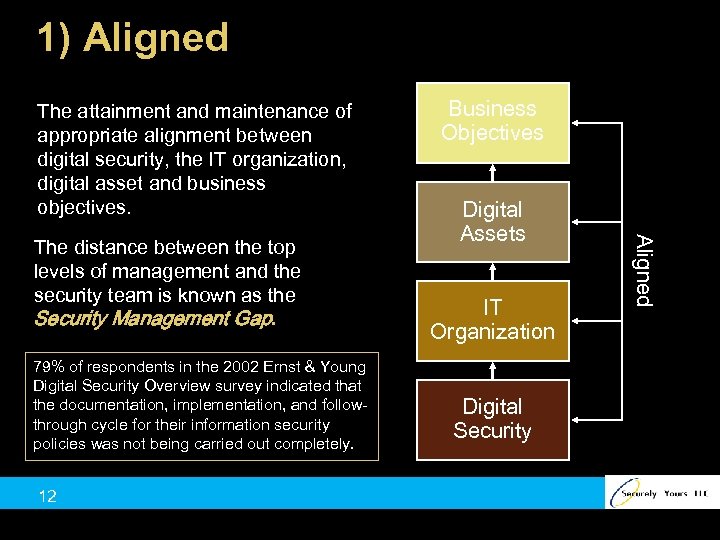 1) Aligned The attainment and maintenance of appropriate alignment between digital security, the IT organization, digital asset and business objectives. 79% of respondents in the 2002 Ernst & Young Digital Security Overview survey indicated that the documentation, implementation, and followthrough cycle for their information security policies was not being carried out completely. 12 Digital Assets IT Organization Digital Security Aligned The distance between the top levels of management and the security team is known as the Security Management Gap. Business Objectives
1) Aligned The attainment and maintenance of appropriate alignment between digital security, the IT organization, digital asset and business objectives. 79% of respondents in the 2002 Ernst & Young Digital Security Overview survey indicated that the documentation, implementation, and followthrough cycle for their information security policies was not being carried out completely. 12 Digital Assets IT Organization Digital Security Aligned The distance between the top levels of management and the security team is known as the Security Management Gap. Business Objectives
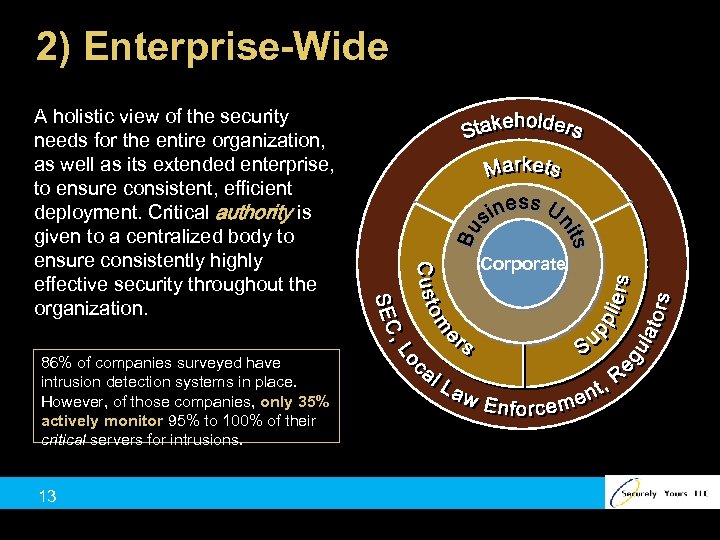 2) Enterprise-Wide A holistic view of the security needs for the entire organization, as well as its extended enterprise, to ensure consistent, efficient deployment. Critical authority is given to a centralized body to ensure consistently highly effective security throughout the organization. 86% of companies surveyed have intrusion detection systems in place. However, of those companies, only 35% actively monitor 95% to 100% of their critical servers for intrusions. 13 Corporate
2) Enterprise-Wide A holistic view of the security needs for the entire organization, as well as its extended enterprise, to ensure consistent, efficient deployment. Critical authority is given to a centralized body to ensure consistently highly effective security throughout the organization. 86% of companies surveyed have intrusion detection systems in place. However, of those companies, only 35% actively monitor 95% to 100% of their critical servers for intrusions. 13 Corporate
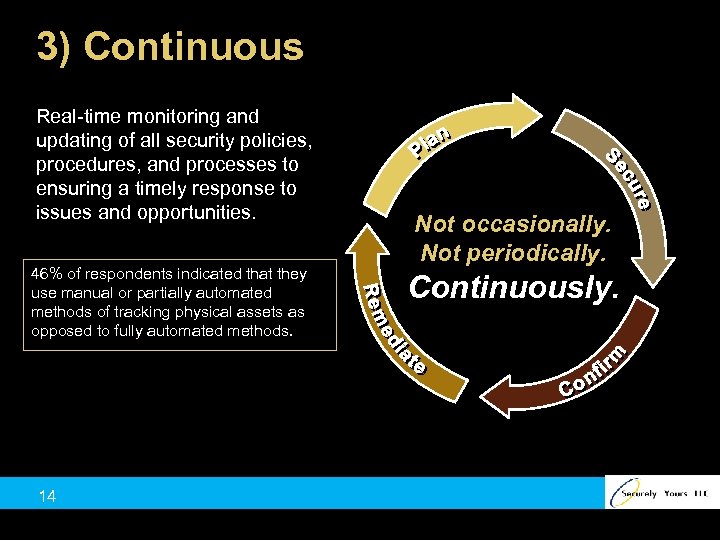 3) Continuous Real-time monitoring and updating of all security policies, procedures, and processes to ensuring a timely response to issues and opportunities. 46% of respondents indicated that they use manual or partially automated methods of tracking physical assets as opposed to fully automated methods. 14 Not occasionally. Not periodically. Continuously.
3) Continuous Real-time monitoring and updating of all security policies, procedures, and processes to ensuring a timely response to issues and opportunities. 46% of respondents indicated that they use manual or partially automated methods of tracking physical assets as opposed to fully automated methods. 14 Not occasionally. Not periodically. Continuously.
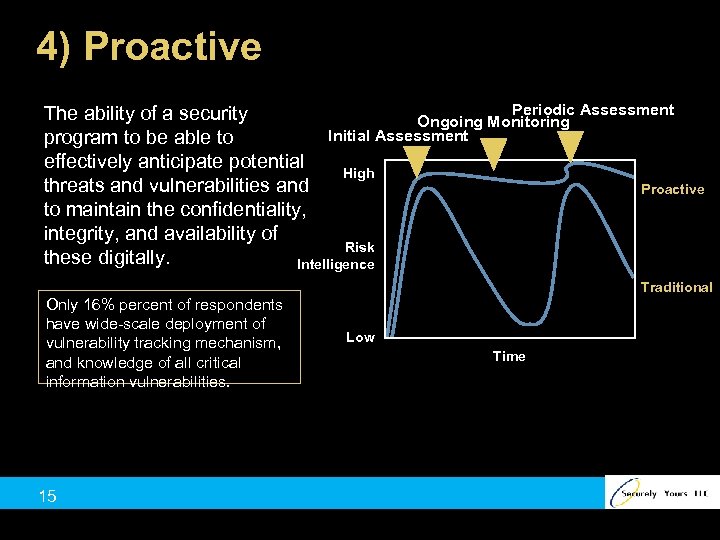 4) Proactive Periodic Assessment The ability of a security Ongoing Monitoring Initial Assessment program to be able to effectively anticipate potential High threats and vulnerabilities and Proactive to maintain the confidentiality, integrity, and availability of Risk these digitally. Intelligence Traditional Only 16% percent of respondents have wide-scale deployment of vulnerability tracking mechanism, and knowledge of all critical information vulnerabilities. 15 Low Time
4) Proactive Periodic Assessment The ability of a security Ongoing Monitoring Initial Assessment program to be able to effectively anticipate potential High threats and vulnerabilities and Proactive to maintain the confidentiality, integrity, and availability of Risk these digitally. Intelligence Traditional Only 16% percent of respondents have wide-scale deployment of vulnerability tracking mechanism, and knowledge of all critical information vulnerabilities. 15 Low Time
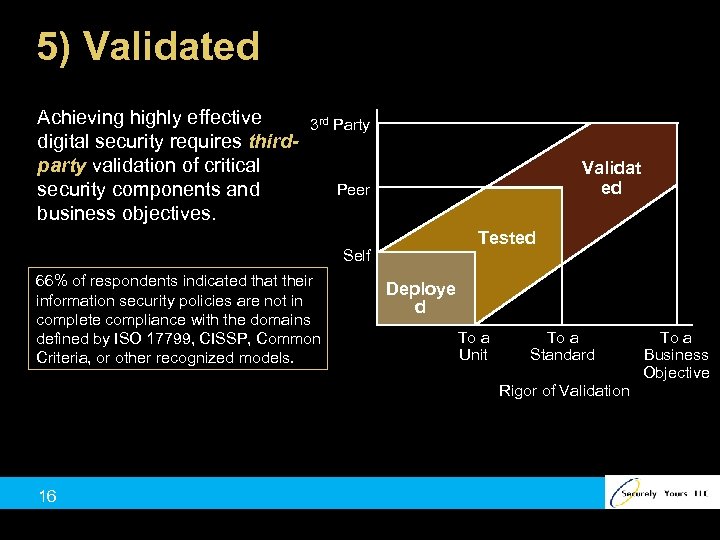 5) Validated Achieving highly effective digital security requires thirdparty validation of critical security components and business objectives. 3 rd Party Validat ed Peer Tested Self 66% of respondents indicated that their information security policies are not in complete compliance with the domains defined by ISO 17799, CISSP, Common Criteria, or other recognized models. Deploye d To a Unit To a Standard Rigor of Validation 16 To a Business Objective
5) Validated Achieving highly effective digital security requires thirdparty validation of critical security components and business objectives. 3 rd Party Validat ed Peer Tested Self 66% of respondents indicated that their information security policies are not in complete compliance with the domains defined by ISO 17799, CISSP, Common Criteria, or other recognized models. Deploye d To a Unit To a Standard Rigor of Validation 16 To a Business Objective
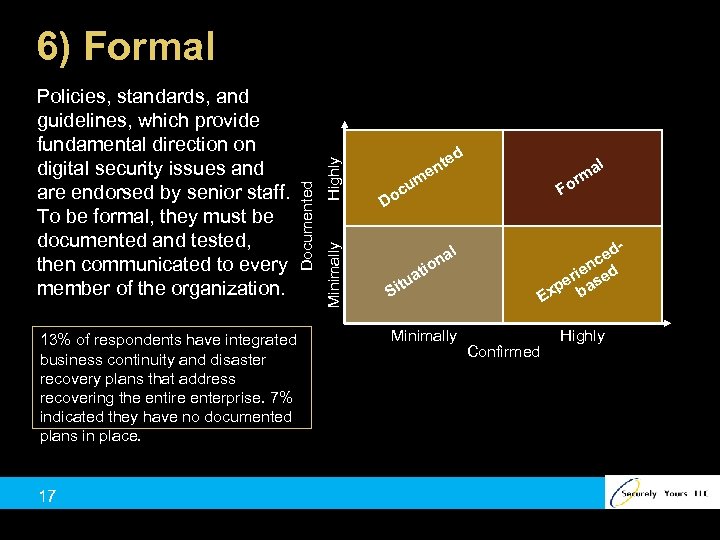 13% of respondents have integrated business continuity and disaster recovery plans that address recovering the entire enterprise. 7% indicated they have no documented plans in place. 17 Highly Minimally Policies, standards, and guidelines, which provide fundamental direction on digital security issues and are endorsed by senior staff. To be formal, they must be documented and tested, then communicated to every member of the organization. Documented 6) Formal t en ed l a rm m u oc D Fo ed c ien ed r pe bas Ex l na o ti ua t Si Minimally Confirmed Highly
13% of respondents have integrated business continuity and disaster recovery plans that address recovering the entire enterprise. 7% indicated they have no documented plans in place. 17 Highly Minimally Policies, standards, and guidelines, which provide fundamental direction on digital security issues and are endorsed by senior staff. To be formal, they must be documented and tested, then communicated to every member of the organization. Documented 6) Formal t en ed l a rm m u oc D Fo ed c ien ed r pe bas Ex l na o ti ua t Si Minimally Confirmed Highly
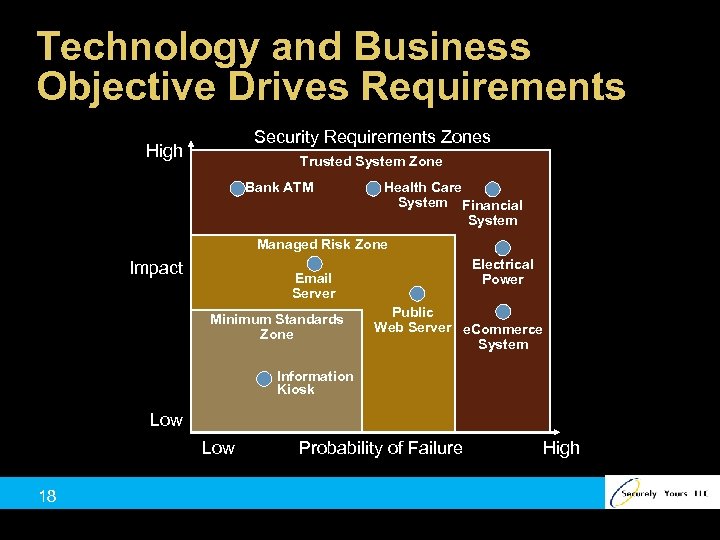 Technology and Business Objective Drives Requirements Security Requirements Zones High Trusted System Zone Bank ATM Health Care System Financial System Managed Risk Zone Impact Electrical Power Email Server Minimum Standards Zone Public Web Server e. Commerce System Information Kiosk Low 18 Probability of Failure High
Technology and Business Objective Drives Requirements Security Requirements Zones High Trusted System Zone Bank ATM Health Care System Financial System Managed Risk Zone Impact Electrical Power Email Server Minimum Standards Zone Public Web Server e. Commerce System Information Kiosk Low 18 Probability of Failure High
 The Security Agenda 19
The Security Agenda 19
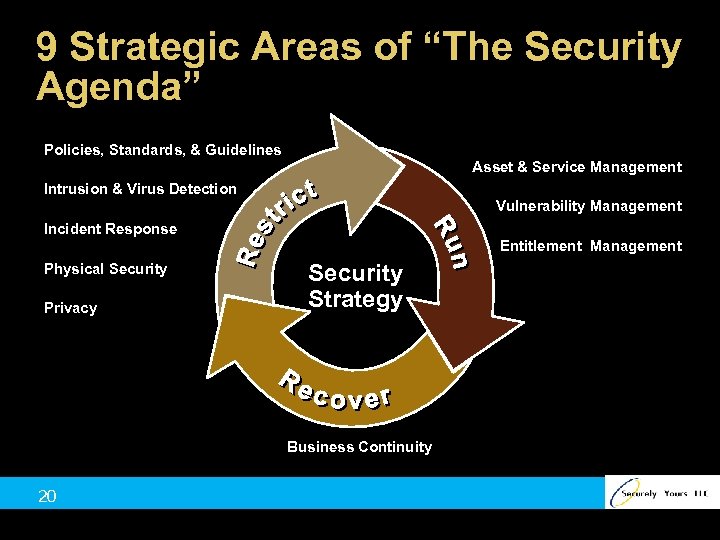 9 Strategic Areas of “The Security Agenda” Policies, Standards, & Guidelines Asset & Service Management Intrusion & Virus Detection Vulnerability Management Incident Response Entitlement Management Physical Security Privacy Security Strategy Business Continuity 20
9 Strategic Areas of “The Security Agenda” Policies, Standards, & Guidelines Asset & Service Management Intrusion & Virus Detection Vulnerability Management Incident Response Entitlement Management Physical Security Privacy Security Strategy Business Continuity 20
 TECHNOLOGY 21 S ES All 3 Components Needed OC PR PE OP LE Complex Organizational Transformation
TECHNOLOGY 21 S ES All 3 Components Needed OC PR PE OP LE Complex Organizational Transformation
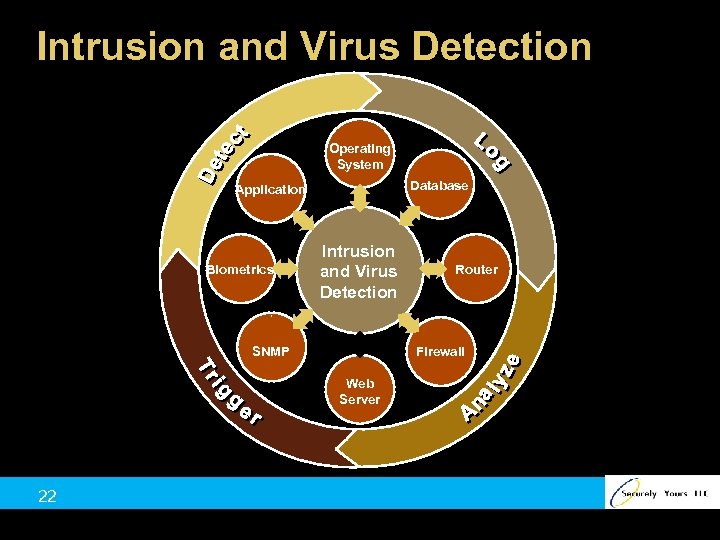 Intrusion and Virus Detection Operating System Database Application Biometrics Intrusion and Virus Detection SNMP Firewall Web Server 22 Router
Intrusion and Virus Detection Operating System Database Application Biometrics Intrusion and Virus Detection SNMP Firewall Web Server 22 Router
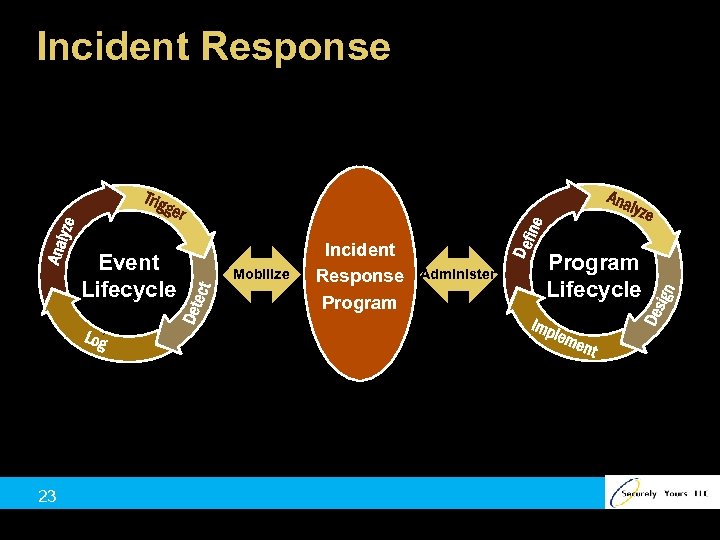 Incident Response Event Lifecycle 23 Mobilize Incident Response Program Administer Program Lifecycle
Incident Response Event Lifecycle 23 Mobilize Incident Response Program Administer Program Lifecycle
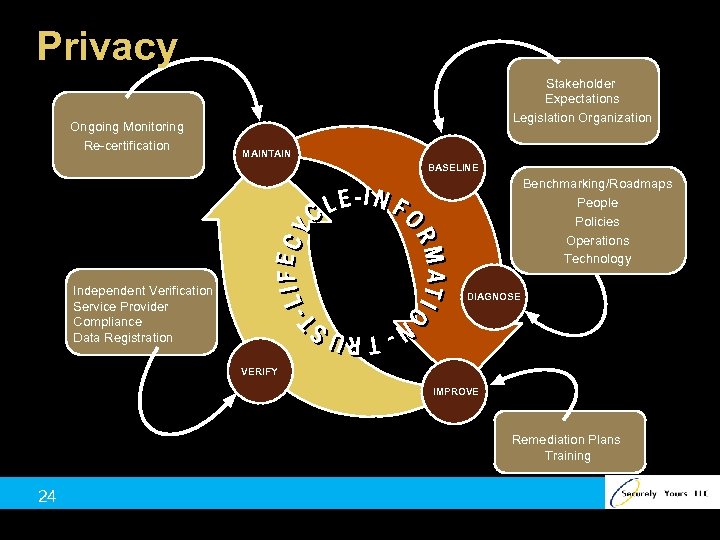 Privacy Ongoing Monitoring Re-certification Stakeholder Expectations Legislation Organization MAINTAIN BASELINE Benchmarking/Roadmaps People Policies Operations Technology Independent Verification Service Provider Compliance Data Registration DIAGNOSE VERIFY IMPROVE Remediation Plans Training 24
Privacy Ongoing Monitoring Re-certification Stakeholder Expectations Legislation Organization MAINTAIN BASELINE Benchmarking/Roadmaps People Policies Operations Technology Independent Verification Service Provider Compliance Data Registration DIAGNOSE VERIFY IMPROVE Remediation Plans Training 24
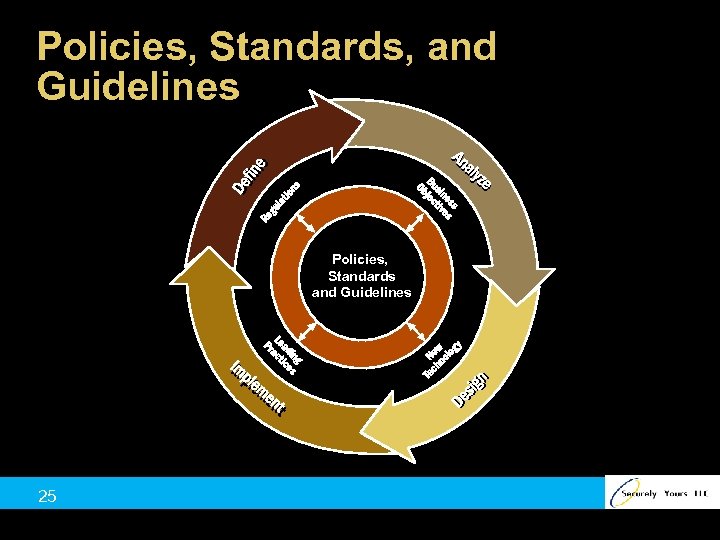 Policies, Standards, and Guidelines Policies, Standards and Guidelines 25
Policies, Standards, and Guidelines Policies, Standards and Guidelines 25
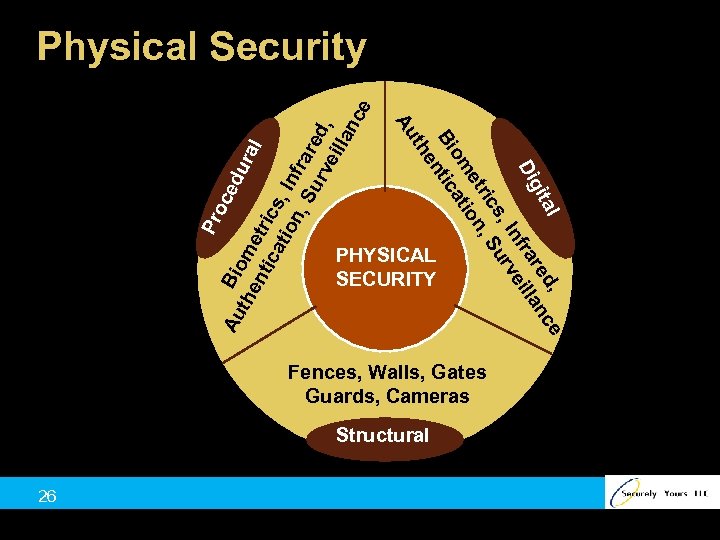 Pro l d, ce ita re an Dig fra ill In ve s, ur ric , S et ion om at Bi tic en th Au ce Au Bio du the m ral nti etri ca cs tio , In n, f Su rare rve d, illa nc e Physical Security PHYSICAL SECURITY Fences, Walls, Gates Guards, Cameras Structural 26
Pro l d, ce ita re an Dig fra ill In ve s, ur ric , S et ion om at Bi tic en th Au ce Au Bio du the m ral nti etri ca cs tio , In n, f Su rare rve d, illa nc e Physical Security PHYSICAL SECURITY Fences, Walls, Gates Guards, Cameras Structural 26
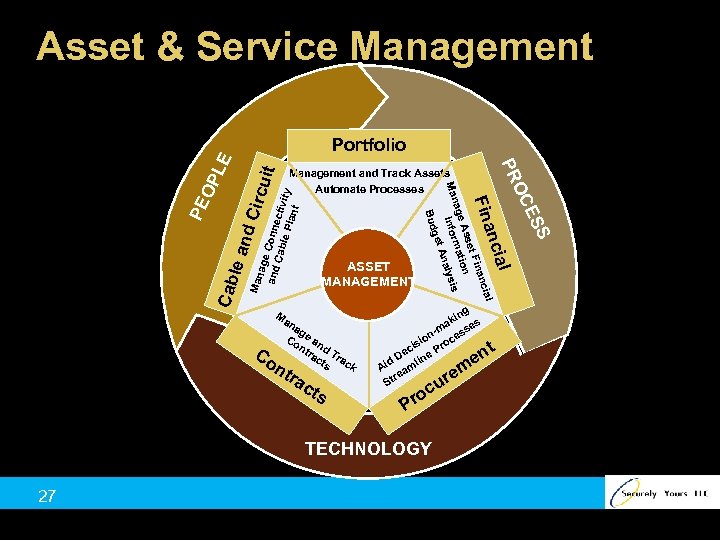 Asset & Service Management it Circ u age and Conne Cab c le P tivity lant OP and PE Cab le Man ts ing ak es m ss ne sio roc ci P e De id mlin A a re St e r cu o Pr TECHNOLOGY 27 t en m S ES ra c l nt ncia na g Co e an nt d ra Tr ct ac s k OC Bud ASSET MANAGEMENT Ma Co Fina cial inan et F Ass tion age rma ysis Man l Info Ana get Management and Track Assets Automate Processes PR LE Portfolio
Asset & Service Management it Circ u age and Conne Cab c le P tivity lant OP and PE Cab le Man ts ing ak es m ss ne sio roc ci P e De id mlin A a re St e r cu o Pr TECHNOLOGY 27 t en m S ES ra c l nt ncia na g Co e an nt d ra Tr ct ac s k OC Bud ASSET MANAGEMENT Ma Co Fina cial inan et F Ass tion age rma ysis Man l Info Ana get Management and Track Assets Automate Processes PR LE Portfolio
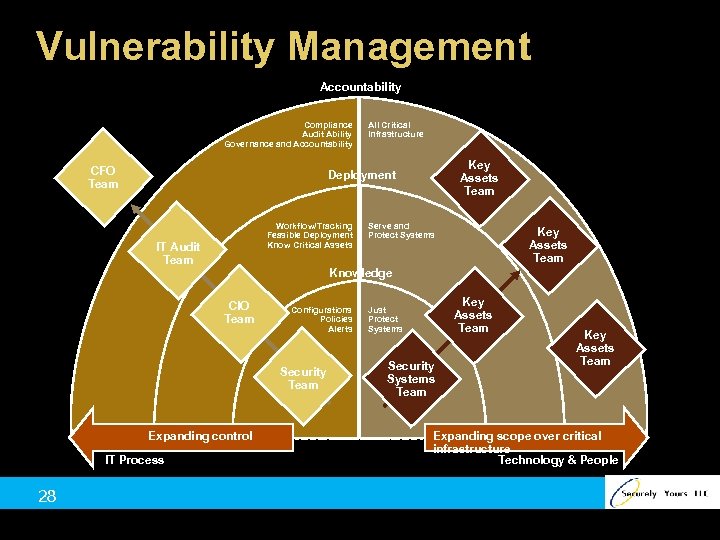 Vulnerability Management Accountability Compliance Audit Ability Governance and Accountability CFO Team Key Assets Team Deployment Workflow/Tracking Feasible Deployment Know Critical Assets IT Audit Team Configurations Policies Alerts Security Team Expanding control IT Process Serve and Protect Systems Key Assets Team Knowledge CIO Team 28 All Critical Infrastructure Key Assets Team Just Protect Systems Security Systems Team Key Assets Team Expanding scope over critical infrastructure Technology & People
Vulnerability Management Accountability Compliance Audit Ability Governance and Accountability CFO Team Key Assets Team Deployment Workflow/Tracking Feasible Deployment Know Critical Assets IT Audit Team Configurations Policies Alerts Security Team Expanding control IT Process Serve and Protect Systems Key Assets Team Knowledge CIO Team 28 All Critical Infrastructure Key Assets Team Just Protect Systems Security Systems Team Key Assets Team Expanding scope over critical infrastructure Technology & People
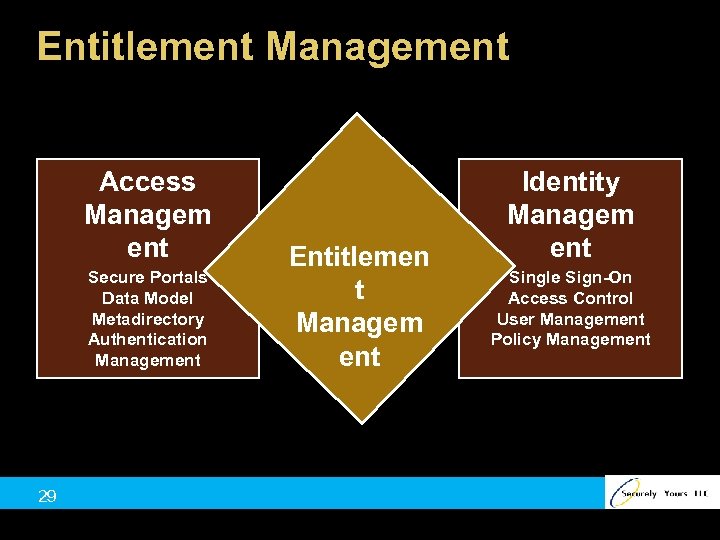 Entitlement Management Access Managem ent Secure Portals Data Model Metadirectory Authentication Management 29 Entitlemen t Managem ent Identity Managem ent Single Sign-On Access Control User Management Policy Management
Entitlement Management Access Managem ent Secure Portals Data Model Metadirectory Authentication Management 29 Entitlemen t Managem ent Identity Managem ent Single Sign-On Access Control User Management Policy Management
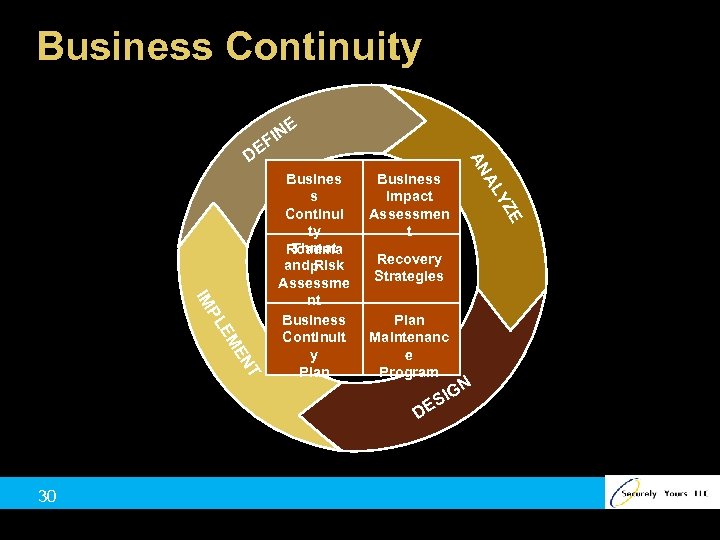 Business Continuity E N FI Business Impact Assessmen t AL E YZ T EN EM PL IM Busines s Continui ty Threat Roadma andp Risk Assessme nt Business Continuit y Plan AN DE Recovery Strategies Plan Maintenanc e Program N G SI DE 30
Business Continuity E N FI Business Impact Assessmen t AL E YZ T EN EM PL IM Busines s Continui ty Threat Roadma andp Risk Assessme nt Business Continuit y Plan AN DE Recovery Strategies Plan Maintenanc e Program N G SI DE 30
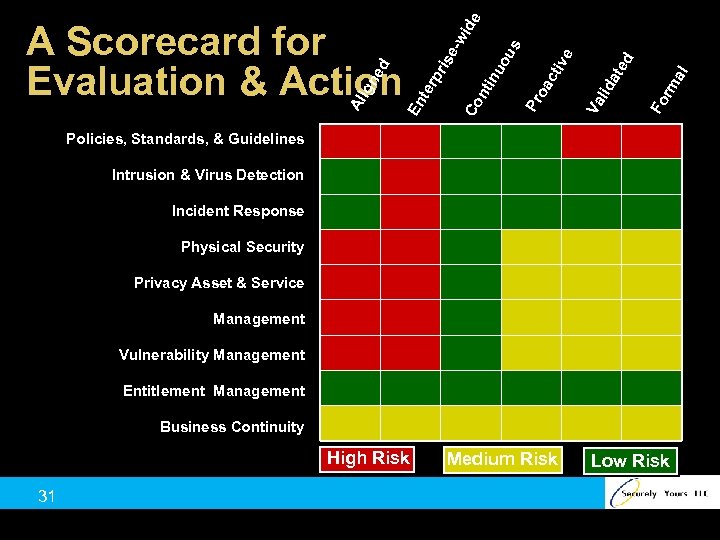 ide Co nt inu ou s Pr oa cti ve l ma Fo r Va li da te d -w pr ise er En t Al ig ne d A Scorecard for Evaluation & Action Policies, Standards, & Guidelines Intrusion & Virus Detection Incident Response Physical Security Privacy Asset & Service Management Vulnerability Management Entitlement Management Business Continuity High Risk 31 Medium Risk Low Risk
ide Co nt inu ou s Pr oa cti ve l ma Fo r Va li da te d -w pr ise er En t Al ig ne d A Scorecard for Evaluation & Action Policies, Standards, & Guidelines Intrusion & Virus Detection Incident Response Physical Security Privacy Asset & Service Management Vulnerability Management Entitlement Management Business Continuity High Risk 31 Medium Risk Low Risk
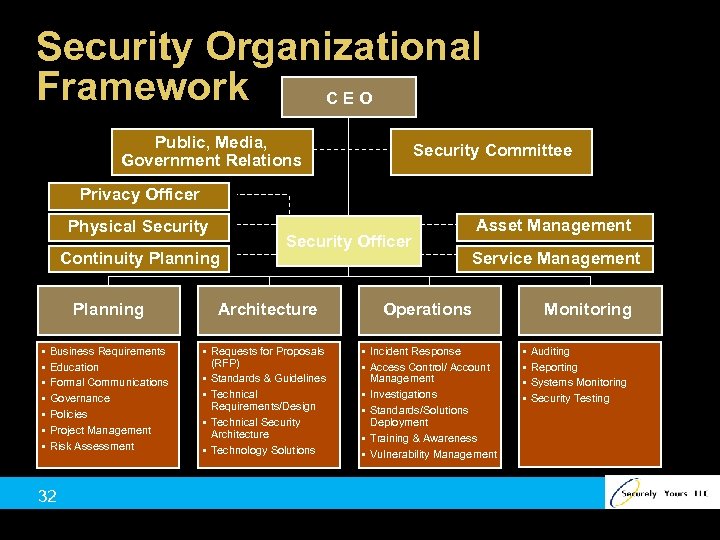 Security Organizational Framework CEO Public, Media, Government Relations Security Committee Privacy Officer Physical Security Continuity Planning § § § § Business Requirements Education Formal Communications Governance Policies Project Management Risk Assessment 32 Security Officer Architecture § Requests for Proposals (RFP) § Standards & Guidelines § Technical Requirements/Design § Technical Security Architecture § Technology Solutions Asset Management Service Management Operations § Incident Response § Access Control/ Account Management § Investigations § Standards/Solutions Deployment § Training & Awareness § Vulnerability Management Monitoring § § Auditing Reporting Systems Monitoring Security Testing
Security Organizational Framework CEO Public, Media, Government Relations Security Committee Privacy Officer Physical Security Continuity Planning § § § § Business Requirements Education Formal Communications Governance Policies Project Management Risk Assessment 32 Security Officer Architecture § Requests for Proposals (RFP) § Standards & Guidelines § Technical Requirements/Design § Technical Security Architecture § Technology Solutions Asset Management Service Management Operations § Incident Response § Access Control/ Account Management § Investigations § Standards/Solutions Deployment § Training & Awareness § Vulnerability Management Monitoring § § Auditing Reporting Systems Monitoring Security Testing
 The Roadmap for Success 33
The Roadmap for Success 33
 Executive management must understand § Scenario-based simulations – Table-Top Exercises § The organizations response § Critical roles and responsibilities § Actions plans to minimize the effect of an incident § Monitor and test responses 34
Executive management must understand § Scenario-based simulations – Table-Top Exercises § The organizations response § Critical roles and responsibilities § Actions plans to minimize the effect of an incident § Monitor and test responses 34
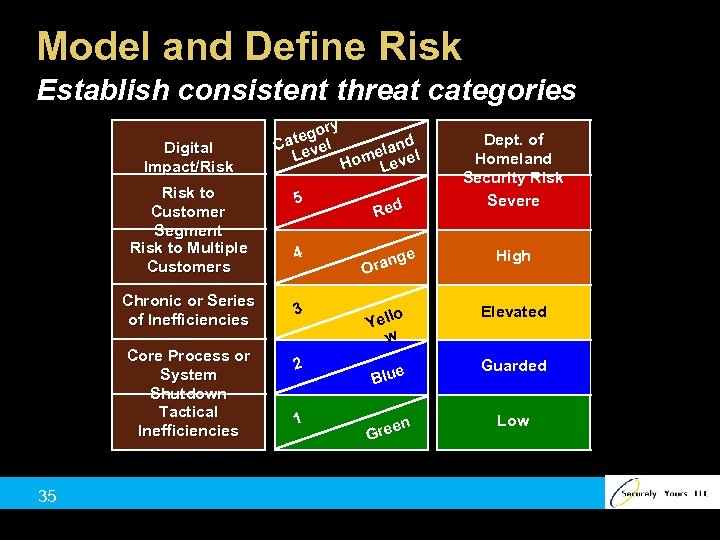 Model and Define Risk Establish consistent threat categories Digital Impact/Risk to Customer Segment Risk to Multiple Customers Chronic or Series of Inefficiencies Core Process or System Shutdown Tactical Inefficiencies 35 ry ego l d Cat eve elan el L Hom Lev 5 4 Red n Ora ge Dept. of Homeland Security Risk Severe High 3 lo Yel w Elevated 2 e Blu Guarded 1 en Gre Low
Model and Define Risk Establish consistent threat categories Digital Impact/Risk to Customer Segment Risk to Multiple Customers Chronic or Series of Inefficiencies Core Process or System Shutdown Tactical Inefficiencies 35 ry ego l d Cat eve elan el L Hom Lev 5 4 Red n Ora ge Dept. of Homeland Security Risk Severe High 3 lo Yel w Elevated 2 e Blu Guarded 1 en Gre Low
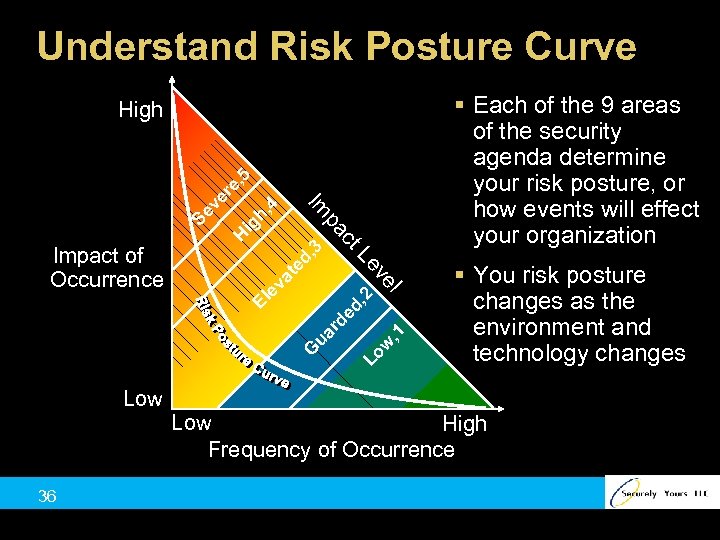 Understand Risk Posture Curve § Each of the 9 areas of the security agenda determine your risk posture, or how events will effect your organization 3 va te d, , 2 36 , 1 de d ua r G Low Lo w 4 h, ig H Se El e l ve Le Impact of Occurrence ct pa Im ve re , 5 High § You risk posture changes as the environment and technology changes Low High Frequency of Occurrence
Understand Risk Posture Curve § Each of the 9 areas of the security agenda determine your risk posture, or how events will effect your organization 3 va te d, , 2 36 , 1 de d ua r G Low Lo w 4 h, ig H Se El e l ve Le Impact of Occurrence ct pa Im ve re , 5 High § You risk posture changes as the environment and technology changes Low High Frequency of Occurrence
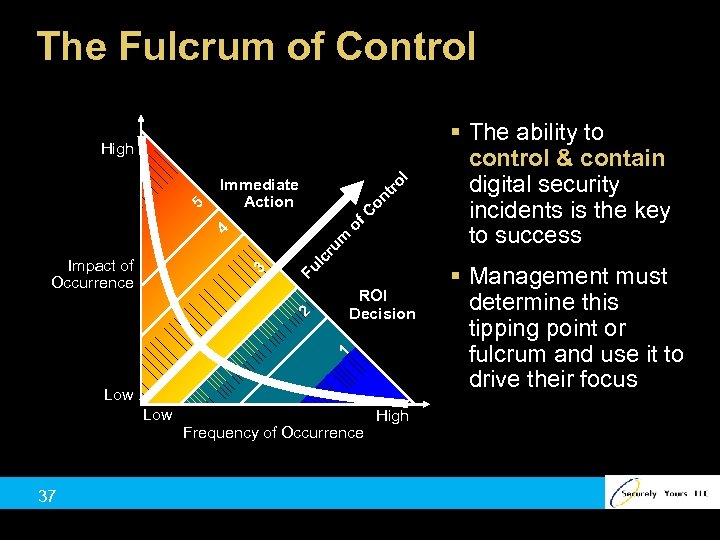 The Fulcrum of Control of C on tr ol Immediate Action ru m 4 5 High Fu ROI Decision 1 2 3 lc Impact of Occurrence Low 37 Frequency of Occurrence High § The ability to control & contain digital security incidents is the key to success § Management must determine this tipping point or fulcrum and use it to drive their focus
The Fulcrum of Control of C on tr ol Immediate Action ru m 4 5 High Fu ROI Decision 1 2 3 lc Impact of Occurrence Low 37 Frequency of Occurrence High § The ability to control & contain digital security incidents is the key to success § Management must determine this tipping point or fulcrum and use it to drive their focus
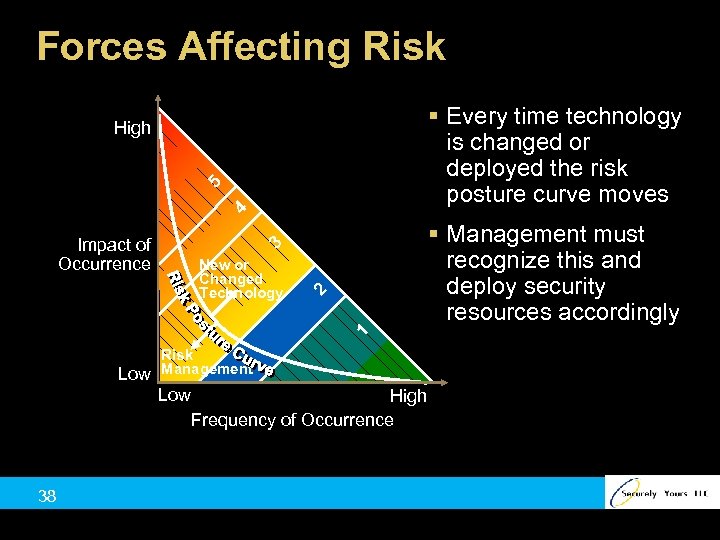 Forces Affecting Risk § Every time technology is changed or deployed the risk posture curve moves 4 5 High § Management must recognize this and deploy security resources accordingly 1 New or Changed Technology 2 3 Impact of Occurrence Low Risk Management Low High Frequency of Occurrence 38
Forces Affecting Risk § Every time technology is changed or deployed the risk posture curve moves 4 5 High § Management must recognize this and deploy security resources accordingly 1 New or Changed Technology 2 3 Impact of Occurrence Low Risk Management Low High Frequency of Occurrence 38
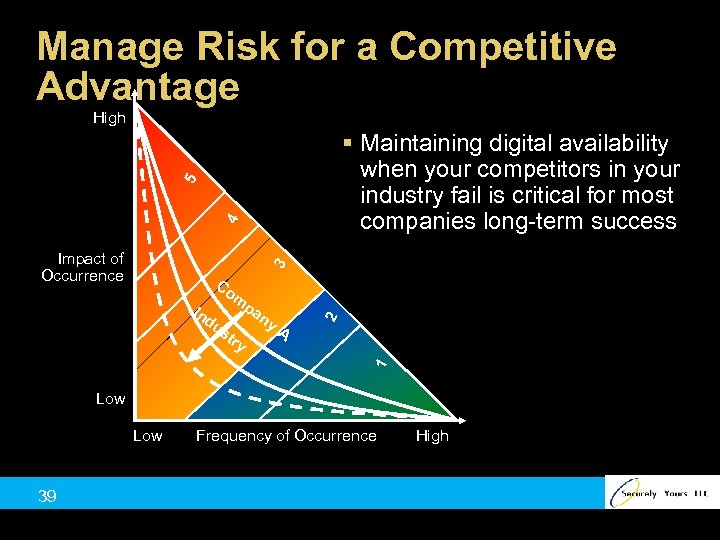 Manage Risk for a Competitive Advantage High 4 5 § Maintaining digital availability when your competitors in your industry fail is critical for most companies long-term success 3 Impact of Occurrence Co st ry pa ny A 1 du 2 m In Low 39 Frequency of Occurrence High
Manage Risk for a Competitive Advantage High 4 5 § Maintaining digital availability when your competitors in your industry fail is critical for most companies long-term success 3 Impact of Occurrence Co st ry pa ny A 1 du 2 m In Low 39 Frequency of Occurrence High
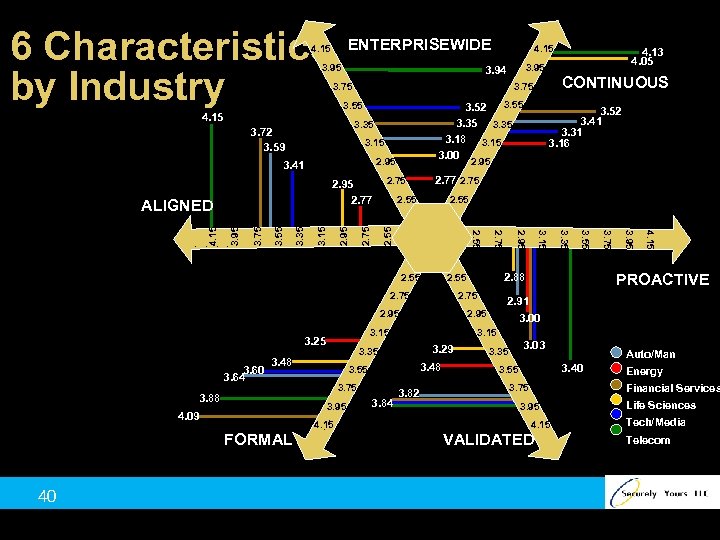 6 Characteristics by Industry ENTERPRISEWIDE 4. 15 3. 95 3. 35 3. 15 2. 95 3. 41 2. 55 3. 15 3. 35 2. 75 3. 84 4. 15 FORMAL 40 3. 55 3. 95 4. 09 3. 29 3. 48 3. 75 3. 95 3. 88 3. 15 3. 35 3. 48 2. 91 3. 00 2. 95 3. 15 3. 25 3. 75 2. 95 PROACTIVE 2. 88 2. 55 2. 75 3. 55 2. 55 3. 35 3. 55 2. 55 3. 15 3. 75 2. 55 2. 95 3. 95 2. 77 2. 75 2. 95 2. 77 3. 52 3. 41 3. 31 3. 16 2. 95 2. 55 4. 15 3. 52 3. 35 3. 18 3. 15 3. 00 4. 13 4. 05 CONTINUOUS 3. 75 3. 55 3. 72 3. 59 3. 60 3. 64 3. 95 3. 94 3. 75 4. 15 ALIGNED 4. 15 3. 82 3. 03 3. 35 Auto/Man 3. 40 3. 55 Energy Financial Services 3. 75 3. 95 4. 15 VALIDATED Life Sciences Tech/Media Telecom
6 Characteristics by Industry ENTERPRISEWIDE 4. 15 3. 95 3. 35 3. 15 2. 95 3. 41 2. 55 3. 15 3. 35 2. 75 3. 84 4. 15 FORMAL 40 3. 55 3. 95 4. 09 3. 29 3. 48 3. 75 3. 95 3. 88 3. 15 3. 35 3. 48 2. 91 3. 00 2. 95 3. 15 3. 25 3. 75 2. 95 PROACTIVE 2. 88 2. 55 2. 75 3. 55 2. 55 3. 35 3. 55 2. 55 3. 15 3. 75 2. 55 2. 95 3. 95 2. 77 2. 75 2. 95 2. 77 3. 52 3. 41 3. 31 3. 16 2. 95 2. 55 4. 15 3. 52 3. 35 3. 18 3. 15 3. 00 4. 13 4. 05 CONTINUOUS 3. 75 3. 55 3. 72 3. 59 3. 60 3. 64 3. 95 3. 94 3. 75 4. 15 ALIGNED 4. 15 3. 82 3. 03 3. 35 Auto/Man 3. 40 3. 55 Energy Financial Services 3. 75 3. 95 4. 15 VALIDATED Life Sciences Tech/Media Telecom
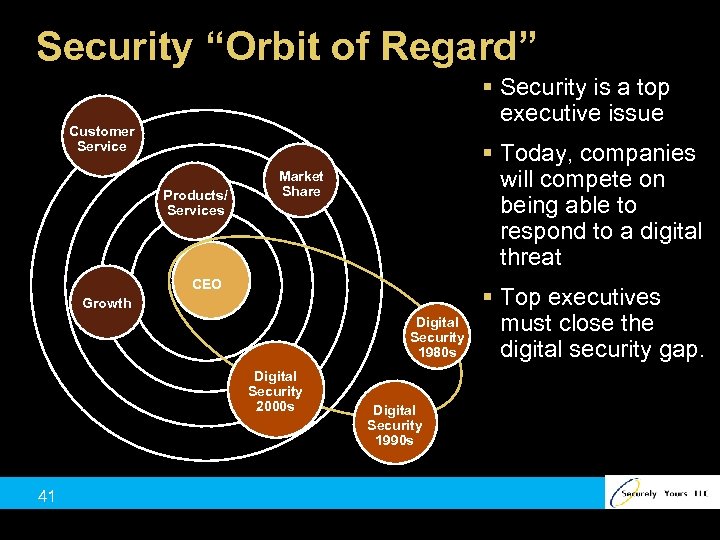 Security “Orbit of Regard” § Security is a top executive issue Customer Service Products/ Services § Today, companies will compete on being able to respond to a digital threat Market Share CEO Growth Digital Security 1980 s Digital Security 2000 s 41 Digital Security 1990 s § Top executives must close the digital security gap.
Security “Orbit of Regard” § Security is a top executive issue Customer Service Products/ Services § Today, companies will compete on being able to respond to a digital threat Market Share CEO Growth Digital Security 1980 s Digital Security 2000 s 41 Digital Security 1990 s § Top executives must close the digital security gap.
 Highly Effective Security Cultures: § are chief executive-driven § maintain a heightened sense of awareness § utilize a digital security guidance council § establish timetables for success and monitor progress § drive an enterprise-wide approach The level commitment of organization’s personnel to the principles of security will determine the success or failure of the digital security program. 42
Highly Effective Security Cultures: § are chief executive-driven § maintain a heightened sense of awareness § utilize a digital security guidance council § establish timetables for success and monitor progress § drive an enterprise-wide approach The level commitment of organization’s personnel to the principles of security will determine the success or failure of the digital security program. 42
 For More Information… Sajay Rai CEO and Managing Partner, Securely Yours LLC 248 -723 -5224 Sajayrai@securelyyoursllc. com 43
For More Information… Sajay Rai CEO and Managing Partner, Securely Yours LLC 248 -723 -5224 Sajayrai@securelyyoursllc. com 43


