66485810e37fd41a68dcc0957207a756.ppt
- Количество слайдов: 95

Defending Layer 8 How to recognize and combat social engineering Steve Riley Senior Security Strategist, Trustworthy Computing steve. riley@microsoft. com http: //blogs. technet. com/steriley

When was the last time you… Heard about social engineering? Or physical security even?

The OSI model 7. application n atio 6. presentation ic ppl 7. a 6. pre 5. session sen 7. applica tion t 5. seatio ssion n 6. pres 4. transport entatio 4. tr n ansp 3. network ort 3. net wo t 2. porrk link ans 4. tr 1. physical 2. link (cyberspace) 2. link 1. physical (cyberspace) 5. se 3. n ssi etw on ork

The OSI model 8. human 7. application 6. presentation 5. session 4. transport 3. network 2. link 1. physical (cyberspace) 0. physical (meatspace)

The OSI model 8. human 7. application n atio 6. presentation ic ppl 7. a 6. pre 5. session sen 7. applica tion t 5. seatio ssion n 6. pres 4. transport entatio 4. tr n ansp 3. network ort 3. net wo t 2. porrk link ans 4. tr 1. physical 2. link (cyberspace) 2. link 0. physical (meatspace) 1. physical (cyberspace) 5. se 3. n ssi etw on ork

The problem People spend a fortune on technology and are still vulnerable to old-fashioned manipulation!

Don’t believe me? Hired pen test example Physical and electronic Help desk example Betty is a bit too helpful Get a credit card number easily Call “friend” at cross-town store No Secur. ID? No problem! Show me yours

Try it yourself! 1. Be professional. 2. Be calm. 3. Know your mark. 4. Do not fool a superior scammer. 5. Plan your escape from your scam. 6. Be a woman. 7. Use watermarks. 8. Make business cards and fake names. 9. Manipulate the less fortunate, the unaware, and the stupid. 10. Use a team if you have to.
Exploits “layer 8” There is no computer system on Earth that does not rely on humans S. E. completely bypasses all information controls and goes directly after the weakest link:

Social engineering The art and science of getting people to comply to your wishes. Not a form of mind control Lots of groundwork Information-gathering Idle chit-chat Amusing accents Most of the work is in preparation
Uh, isn’t that what selling is? To sell: create a spark Predict What the eye will see What the ear will hear What the mind will think The highest form of selling: In a way that the consumer is unaware she is being sold

Social engineering The art and science of getting people to comply to your wishes. Is the highest form of hacking Can be very easy Often yields largest rewards Natural human desire to help leaves us vulnerable And can undermine all technical countermeasures

Suave and sophisticated Only amateurs ask for passwords Build emotional bond—even trust Administrators Security personnel Any likely possessor of information Anyone with access is a potential risk Electronic or physical Includes people outside the policy

Types of exploits Diffusion of responsibility “The veep says you won’t bear any responsibility…” Chance for ingratiation “Look at what you might get out of this!” Trust relationships “He’s a good guy, I think I can trust him” Moral duty “You must help me! Aren’t you so mad about it? ”

Types of exploits Guilt “What, you don’t want to help me? ” Identification “You and I are really two of a kind, huh? ” Desire to be helpful “Would you help me here, please? ” Cooperation “Let’s work together. We can do so much!”

Categories of exploits Direct request Usually the least likely to succeed Contrived situation Additional factors the target must consider Dressing the part Service person, employee, carry clipboard Personal persuasion Increase voluntary compliance Make target believe he/she is in control
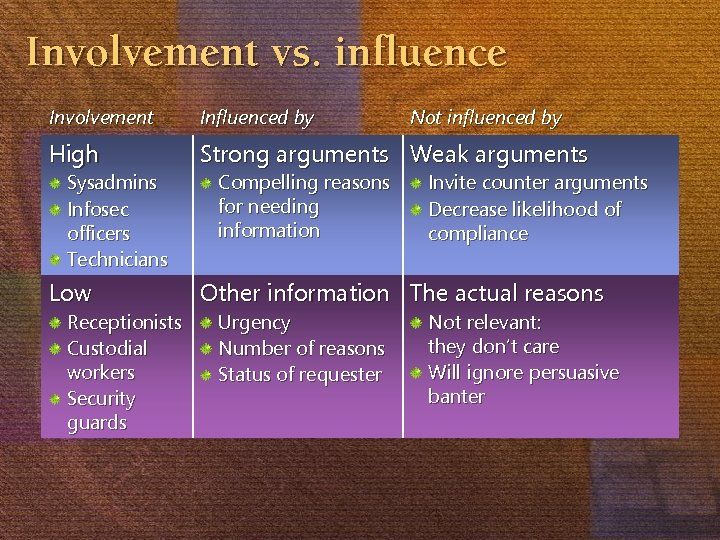
Involvement vs. influence Involvement Influenced by High Strong arguments Weak arguments Low Other information The actual reasons Sysadmins Infosec officers Technicians Receptionists Custodial workers Security guards Compelling reasons for needing information Urgency Number of reasons Status of requester Not influenced by Invite counter arguments Decrease likelihood of compliance Not relevant: they don’t care Will ignore persuasive banter

The help desk People are naturally helpful Its function is to help—to provide answers Like all customer service Generally not trained to question the validity of each call Minimally-educated about security Don’t get paid much Objective: move on to next call

Public access terminals: gold!

Why It Succeeds

People vs. machines Six problems that show the inherent conflict between carbon and silicon How do people perceive risk? How do people handle exceptions? Why do people trust computers? Why do we think people can make intelligent security decisions? Are there malicious insiders? Why are people vulnerable to social engineering?


Poor perceivers of risk Overestimate risk for things that are Out of their control Sensationalized in the media Underestimate risk for things that are Mundane Ordinary

Damn, this new Whyte Ryce album kicks! Hell not again… we gotta fix that stupid alarm George’ll shut it off when he looks up, he always does

Awkward exception handlnig Computer mistakes are rare; people don’t know how to deal with them Sometimes we just ignore or disable the alarm Attackers take advantage of mistakes Drills ensure people know what to do “This computer never makes mistakes, so you must be lying”


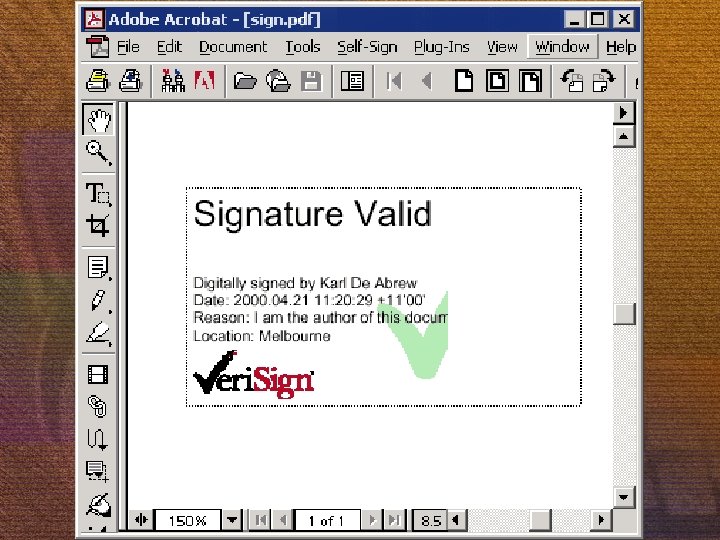

Trusting the computer People don’t sign or encrypt stuff… software does! Necessary to securely transfer human volition to computer action Volition can be forged…make the computer lie Trojan horse feeds malicious document into signing system when key is opened to sign something else
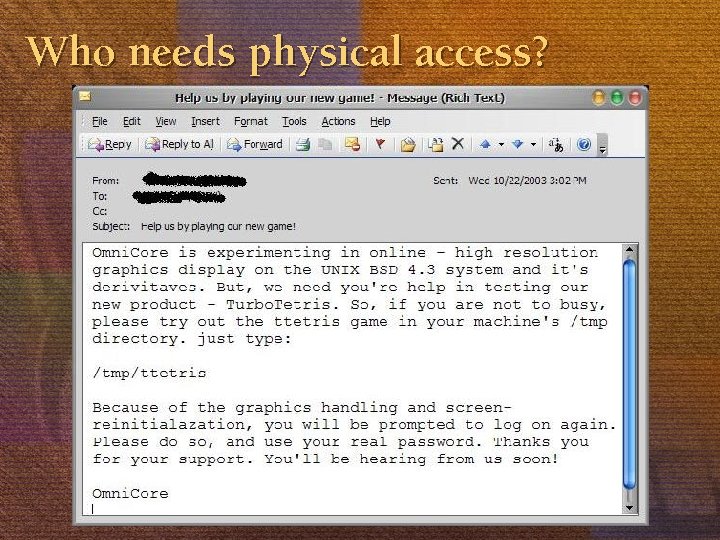
Who needs physical access?
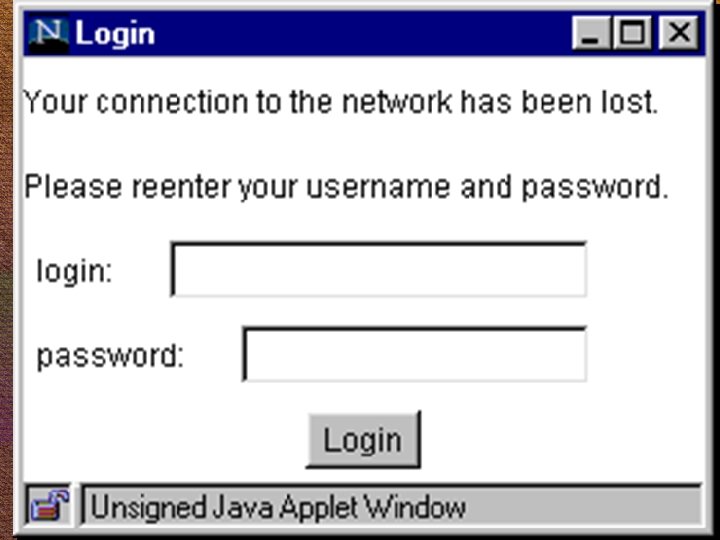
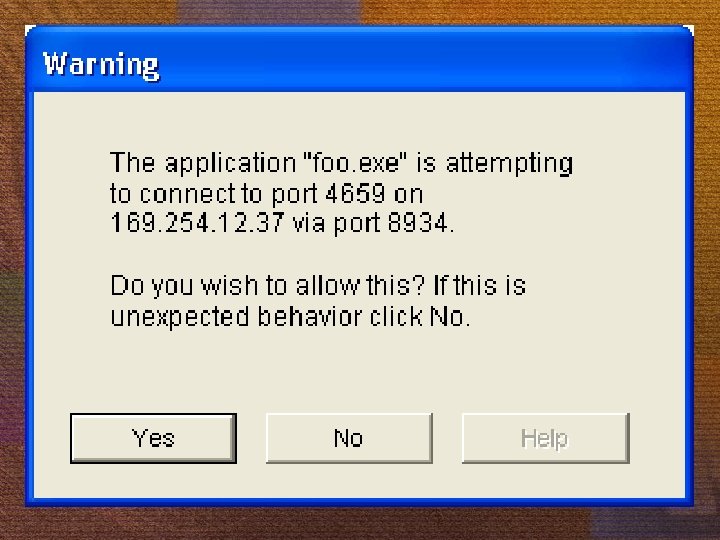


Making security decisions People want security… …but they don’t want to see it working And will disable or circumvent it if it gets in the way of work Yet good security relies on interaction Checking the name on a digital certificate The allure of email worms with sexy subject lines Java. Script warning dialogs




Malicious insiders Implicitly trusted Digital world is rife with insider knowledge Authors of security programs Installers of firewalls Auditors Hire honest people Integrity screening Diffuse trust Public code reviews

Tools And Techniques

So you wanna be social engineer You need two things: A telephone A “mark” —maybe a former best friend

Other useful bits ANI (caller ID) if planning a callback scam Voice changer Ability to think quickly

Fingering the mark Need collection of information tidbits to create sense of authenticity Obtain a list of employee and computer names whois finger Domain registration records Target organization’s own web site Google, anyone?

Make a site visit Look good!—blend in Fake ID badge Observe typical entry/exit behavior Stride with confidence; pretend you belong Private offices are best Computer connections Posted lists and notes Ask low-level employees

Dumpster diving Memos Phone books Policy manuals Calendars System manuals Disks and tapes Organizational charts Printouts of names and passwords Printouts of source code Old discarded hardware

Building the picture Faking a phone rep could work… Try the written word: built-in trust “You might already be a winner!” “We value your opinion…” Be official-looking mass mail “We will need a password to verify…” Follow up with a phone call Ask for the password and other data Listen to speech pattern

Fingerprinting a system NMAP ICMP (Ofir Arkin’s paper) Telnet for banners Domain records and job web sites Portscanning

Mounting the attack You’ve got information on— Your mark The computer system Call organization’s help desk Feign inability to log on Can pass verification checks with info you’ve gathered Prey on lack of social skills “I’ve seen you at work…” Be judicious—don’t ask for too much

Reverse social engineering Sabotage Cause a problem on target’s network Advertising Leave business card around Incorporate contact info in error message Assistance Fix the problem while obtaining info Don’t forget to leave a back door or two…

Protecting Yourself

Want an easy way out?

S. E. usually ignored S. E. viewed as attack against intelligence No one wants to admit they were duped Technical people are proud of their knowledge Often like to share Everyone is susceptible, given a sufficiently persuasive social engineer

Don’t encourage bad behavior!

Don’t encourage bad behavior!

Be willing to change

A multi-level defense Level Defense Foundational Parameter Fortress Persistence Gotcha Offensive Policies Security awareness and education Resistance training Ongoing reminders Social engineering land mines Incident response

Foundational: Policies Enables management to make statement about value of information to the business Provides legal foundataion for personnel decisions Defines things people should (not) do Lists penalties for violations Targets people who regularly respond to requests Helps people feel as if only choice is to resist Be realistic Be regularly reviewed

Foundational: Policy elements Account setup and maintenance Password change policy Help desk procedures Access privileges Violations User IDs Privacy policy Paper documents Controlled access Information dissemination System hiding

Policies have natural weaknesses Four common pitfalls that limit the effectiveness of any security policy Security is a barrier to progress Security is a learned behavior Expect the unexpected There’s no perfect mousetrap

Security is a barrier to progress Protective measures are (by definition) either obstacles or impediments to commerce Typically add zero benefit Sometimes mitigate specific threats Always reduce the ability to freely share information Balance between security and disruption varies Human nature begets desire (more! faster!) Traffic lights exist for safety, but they’re just annoying at vacant intersections At some point our patience runs out Network users experience the same limit No perceived benefit in compliance Disparate compliance security breach


Security is a learned behavior Self-preservation is instinctual; security isn’t Higher-level function requiring initial learning and occasional reinforcement Teach and preach the policy; tailor for audience Infosec procedures are often unintuitive How to recognize value of assets? How to evaluate risks? How to estimate costs of compromise? “This is a stupid policy” Applies to management, too Want commitment and funding? Better justify each component of the policy


Expect the unexpected Processes designed for global enterprises will process transactions at all hours for many users As complexity of procedures increases, so does the chance they will fail Expect failures and disasters—look for signs Keep skills current Prepare, plan, practice Weeds out faults and loopholes before they’re exploited



There’s no perfect mousetrap You can never be finished Securing is on-going Technology changes Systems become outdated, fail, lose effectiveness Threats always exist And morph as attackers practice and improve Policies and processes require regular maintenance

Parameter: Security awareness Don’t allow trust to be exploited Know what has value What to do if you suddenly lost all access? Friends aren’t always friends Over-the-phone friendships lack trust Passwords are personal And always undervalued Uniforms are cheap Mutually authenticate when your bank calls you!
“A” Attention-getting It’s a prerequisite to learning Use clever slogans, eye-catching images Appeal to target audience Know their existing values and motivations Start where they are, move to where you want them

“B” Basic (simple, memorable) Sets stage for training, shouldn’t be complex Take away fear and ignorance Foster recognition there’s a problem and that people are the solution Buy-in is better than coercion Contributors to awareness program are more likely to accept and follow controls Get feedback for every suggestion; lack implies “no management interest”
“C” Current Material must always be fresh “Smell like the tide, not like the fish” Credible Clear, relevant, appropriate Have 15 passwords? Write them down—and protect the list Continuing Persistence and repetition are important Vary methods used


Reactions “I never thought of it that way. ” “That surprises me!” “What a great idea!” “I’d almost forgot about that…” “I can use this. ”

Start with a bang Not with a long dry boring introduction That enumerates every law reglation policy standard guideline or requirement

Logos and images Images have more power than words Look for colorful designs that catch the eye and burn into the brain Even animation can help

What would Wyad cinx safper ef happen if stmxune someone khopgel changed joor deko? your data?
Themes Unite several concepts into a related message Choose one that’s reflective of your business Incorporate design elements into posters Hospital “Prevention is better than a cure” US Nuclear Regulatory Agency “Keep it clean” “Cyber Tyger” “It’s a bug’s life” “PC Doctor”

Posters 85 Incidents 3 , 000 Financial loss

Stories and examples Real people, real consequences Long-time employees (“corporate memory”) News events Internet message boards Security personnel Again, tailor to audience Theft of medical records: healthcare data processing Fraud/impersonation: financial and accounting groups

Use failure It’s a learning accelerator Online awareness training— Should provide immediate feedback No need to record answers Give staff something to think about

Example The building is on fire. As you exit the building in a safe and orderly manner, you are able to take either the data backups or the backup of your custom built application. Which do you take? A. The data B. The backup Either answer is correct; training module should inform users of this Just like real life—not everything is easy

Encourage audience involvement Use questions— “Did you know…? ” “What would you do if…” Counter-intuitive facts work wonders In the United States, which of the following activities is illegal? A. Creating an e-mail virus B. Disrupting Internet communications C. Failing to make daily backups

Be surprising Just like a piñata—good material is full of surprises Role-play is excellent Manager who doesn’t want to follow the “no tailgating” policy Entertain, lead by example Retention is long lasting

Parameter: Signs of an attack Learn to recognize Refusal by caller to give contact information Rushing Name-dropping Intimidation Misspellings Odd questions Learn to say “no” Needs backing of management

Parameter: User education Security management campaign Periodic refreshers Newsletters Group meetings Screensavers Signatures on acceptable use policies Shredders and bulk erasers Updated erasers—old ones are too weak Consider: the band saw Regular audits

Fortress: Resistance training Harden the people! Inoculation Teach possible arguments and counter-arguments Forewarning Both content and persuasive intent Understand that attacker’s intent is criminal Reality check 1. It’s out there 2. It can happen to others 3. It can happen to me—experiential

Resistance: Ongoing reminders Regular reminders to keep people aware One training session won’t last forever Police departments do this continually Be creative Don’t become yet another source of noise to be ignored

Gotcha: Social engineering land mines Justified “know-it-all” Who are you? I’m escorting you out Centralized security log Helps defeat foot-in-the-door techniques Call-backs by policy Defeats PBX trickery “Please hold” by policy Time to consider and validate request Key questions Three questions rule Bogus question

Offensive: Incident response Well-defined process that— Mitigates attackers activities Alert other potential victims Notify security personnel Who to notify? Log monitors Corporate security Regularly test and modify
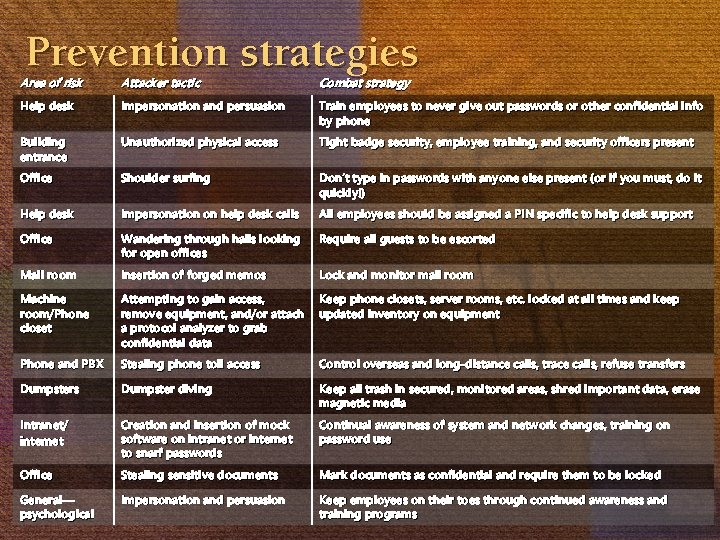
Prevention strategies Area of risk Attacker tactic Combat strategy Help desk Impersonation and persuasion Train employees to never give out passwords or other confidential info by phone Building entrance Unauthorized physical access Tight badge security, employee training, and security officers present Office Shoulder surfing Don’t type in passwords with anyone else present (or if you must, do it quickly!) Help desk Impersonation on help desk calls All employees should be assigned a PIN specific to help desk support Office Wandering through halls looking for open offices Require all guests to be escorted Mail room Insertion of forged memos Lock and monitor mail room Machine room/Phone closet Attempting to gain access, remove equipment, and/or attach a protocol analyzer to grab confidential data Keep phone closets, server rooms, etc. locked at all times and keep updated inventory on equipment Phone and PBX Stealing phone toll access Control overseas and long-distance calls, trace calls, refuse transfers Dumpster diving Keep all trash in secured, monitored areas, shred important data, erase magnetic media Intranet/ internet Creation and insertion of mock software on intranet or internet to snarf passwords Continual awareness of system and network changes, training on password use Office Stealing sensitive documents Mark documents as confidential and require them to be locked General— psychological Impersonation and persuasion Keep employees on their toes through continued awareness and training programs
Where to learn more? No MS Press titles or courseware available on social engineering Make your own page of links! http: //www. google. com/search? q=social+engineering

Steve Riley steve. riley@microsoft. com http: //blogs. technet. com/steriley www. protectyourwindowsnetwork. co m Thanks very much!

© 2006 Microsoft Corporation. All rights reserved. Microsoft, Windows Vista and other product names are or may be registered trademarks and/or trademarks in the U. S. and/or other countries. The information herein is for informational purposes only and represents the current view of Microsoft Corporation as of the date of this presentation. Because Microsoft must respond to changing market conditions, it should not be interpreted to be a commitment on the part of Microsoft, and Microsoft cannot guarantee the accuracy of any information provided after the date of this presentation. MICROSOFT MAKES NO WARRANTIES, EXPRESS, IMPLIED OR STATUTORY, AS TO THE INFORMATION IN THIS PRESENTATION.
66485810e37fd41a68dcc0957207a756.ppt