1c41dfe321d7be14a4f71af5fa43fb65.ppt
- Количество слайдов: 23
Database Security S. Sudarshan Computer Science and Engg. Dept I. I. T. Bombay DB Security, Nov 11, 2003 1

Database Security - protection from malicious attempts to steal (view) or modify data. DB Security, Nov 11, 2003 2
Importance of Data in Databases Bank/Demat accounts Salary Income tax data Credit card University admissions, marks/grades DB Security, Nov 11, 2003 3
Levels of Data Security Human level: Corrupt/careless User Network/User Interface Database application program Database system Operating System Physical level DB Security, Nov 11, 2003 4
Levels of Security Outside of Database Physical level n n n Traditional lock-and-key security Protection from floods, fire, etc. Remote backup for disaster recovery Operating system level n n n Operating system administrators (also known as super-users) can do anything they want to the database! Good operating system level security is required Windows viruses allow intruders to become “superusers”! DB Security, Nov 11, 2003 5
Security (Cont. ) Network level: must use encryption to prevent n n Eavesdropping: unauthorized reading of messages Masquerading: w pretending to be an authorized user or legitimate site, or w sending messages supposedly from authorized users DB Security, Nov 11, 2003 6

Security at the Database/Application Program Authentication and authorization mechanisms to allow specific users access only to required data Authentication: who are you? Prove it! Authorization: what you are allowed to do DB Security, Nov 11, 2003 7
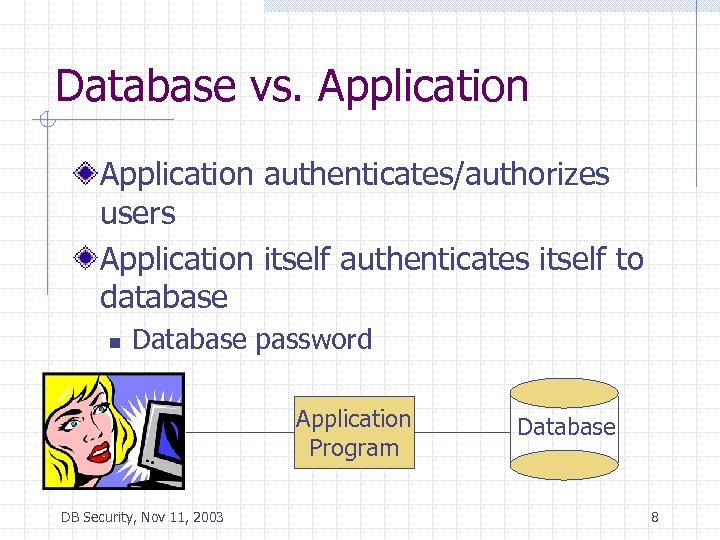
Database vs. Application authenticates/authorizes users Application itself authenticates itself to database n Database password Application Program DB Security, Nov 11, 2003 Database 8

User Authentication Password n Most users abuse passwords. For e. g. w Easy to guess password w Share passwords with others Smartcards n n Need smartcard + a PIN or password DB Security, Nov 11, 2003 Bill Gates 9
Authorization Different authorizations for different users n n n Accounts clerk vs. Accounts manager vs. End users DB Security, Nov 11, 2003 10

Authorization Forms of authorization on (parts of) the database: Read authorization - allows reading, but not modification of data. Insert authorization - allows insertion of new data, but not modification of existing data. Update authorization - allows modification, but not deletion of data. Delete authorization - allows deletion of data 11, 2003 DB Security, Nov 11
Application Authorization Applications authenticate end users and decide what interfaces to give to whom n Screen level authorization Central authentication systems allow users to be authenticated centrally n LDAP often used for this Single sign-on: authenticate once, and access multiple applications without fresh authentication n Microsoft passport, Pub. Cookie etc DB Security, Nov 11, 2003 12

Application Security Applications are often the biggest source of insecurity n n Poor coding of application may allow unauthorized access Application code may be very big, easy to make mistakes and leave security holes DB Security, Nov 11, 2003 13

Insider vs. Outsider Attack Most people worry about outsider attack Most organizations are also highly vulnerable to insider attacks n n E. g. Indira Gandhi Luckily most programmers are honest souls! DB Security, Nov 11, 2003 14

Almighty Application Programmers/Administrators Have password to database, can update anything! n Digital signatures can help in some situations w E. g. low update rate data such as land records, birth/death data n More people with access more danger Application program has database password n Anyone who manages to seize control of the application programme can do anything to the database. DB Security, Nov 11, 2003 15

Dealing with Insider Attacks Audit trails: record of all (update) activity on the database: who did what, when n Database needs to ensure these can’t be turned off, and turned on again after doing damage Supported by most commercial database systems Sys-admin should periodically review audit trail Don’t give database password to development team, keep it with a few system administrators Multiple copies for security DB Security, Nov 11, 2003 16

Anecdotes SQL/Slammer n Attacked SQLServer, brought our network down, luckily no data lost/stolen Database security workshop at IIT Bombay n Careless coding exposed database password to outside world Academic office application at IIT Bombay n n n Working on “check-sum” technique to ensure grades/marks are not changed Database will accept requests only from machine running application programme Other security loopholes no doubt exist DB Security, Nov 11, 2003 17

Summary Data security is critical Requires security at different levels Several technical solutions But human training is essential DB Security, Nov 11, 2003 18

Acknowledgments Pictures in this talk stolen from various web sources! DB Security, Nov 11, 2003 19

Extra Slides DB Security, Nov 11, 2003 20

Network Security All information must be encrypted to prevent eavesdropping n n Public/private key encryption widely used Handled by secure http - https: // Must prevent person-in-the-middle attacks n E. g. someone impersonates seller or bank/credit card company and fools buyer into revealing information w Encrypting messages alone doesn’t solve this problem w More on this in next slide DB Security, Nov 11, 2003 21

Site Authentication Digital certificates are used to prevent impersonation/man-in-the middle attack n Certification agency creates digital certificate by encrypting, e. g. , site’s public key using its own private key w Verifies site identity by external means first! n n Site sends certificate to buyer Customer uses public key of certification agency to decrypt certificate and find sites public key w Man-in-the-middle cannot send fake public key n Sites public key used for setting up secure communication DB Security, Nov 11, 2003 22

Secure Payment Three-way communication between seller, buyer and credit-card company to make payment n n Credit card company credits amount to seller Credit card company consolidates all payments from a buyer and collects them together w E. g. via buyer’s bank through physical/electronic check payment Several secure payment protocols n E. g. Secure Electronic Transaction (SET) DB Security, Nov 11, 2003 23
1c41dfe321d7be14a4f71af5fa43fb65.ppt