8884d0d5da9c90d6b0c155bd854b85b4.ppt
- Количество слайдов: 29
 DATA SECURITY: A Critical Factor in Cashless Economy Oct 28, 2015
DATA SECURITY: A Critical Factor in Cashless Economy Oct 28, 2015
 Pre-Cashless Era: Cash Everywhere A cash-based economy is a system in which financial transactions are carried out in cash rather than electronic means such as direct debit, standing order, bank transfer, or credit card. In 2011, it was estimated that 99% of over 215 million customer transactions in Nigerian banks were cash-related (i. e; through ATM and over-thecounter) and this was valued at about N 2. 1 trillion or 5% of GDP. It is estimated that an average Nigerian transacts about N 65 in cash out of every N 100 income earned. 2
Pre-Cashless Era: Cash Everywhere A cash-based economy is a system in which financial transactions are carried out in cash rather than electronic means such as direct debit, standing order, bank transfer, or credit card. In 2011, it was estimated that 99% of over 215 million customer transactions in Nigerian banks were cash-related (i. e; through ATM and over-thecounter) and this was valued at about N 2. 1 trillion or 5% of GDP. It is estimated that an average Nigerian transacts about N 65 in cash out of every N 100 income earned. 2
 Introduction of Cashless Economy The Nigeria‘s cashless policy took effect from April 1, 2012 in Lagos and later rolled out to other part of the Country. This policy set a platform for an efficient payment system anchored on electronic – based transactions. Mobile payment system introduced at the dawn of January 1, 2012 allows users to make payments with their GSM phones. The Point of Sale (Po. S) terminals were deployed by Banks, PTSPs and connected to the NIBSS for purposes of making payments. The essence of the policy is to shift the economy from a cash-based economy to a cashless one. 3
Introduction of Cashless Economy The Nigeria‘s cashless policy took effect from April 1, 2012 in Lagos and later rolled out to other part of the Country. This policy set a platform for an efficient payment system anchored on electronic – based transactions. Mobile payment system introduced at the dawn of January 1, 2012 allows users to make payments with their GSM phones. The Point of Sale (Po. S) terminals were deployed by Banks, PTSPs and connected to the NIBSS for purposes of making payments. The essence of the policy is to shift the economy from a cash-based economy to a cashless one. 3
 Cashless Economy: The Channels Reduce the over reliance on cash for transactions 4
Cashless Economy: The Channels Reduce the over reliance on cash for transactions 4
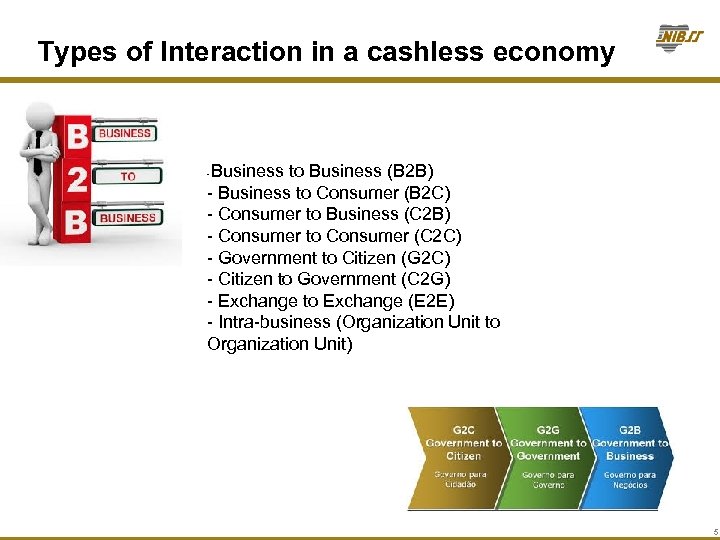 Types of Interaction in a cashless economy Business to Business (B 2 B) - Business to Consumer (B 2 C) - Consumer to Business (C 2 B) - Consumer to Consumer (C 2 C) - Government to Citizen (G 2 C) - Citizen to Government (C 2 G) - Exchange to Exchange (E 2 E) - Intra-business (Organization Unit to Organization Unit) - 5
Types of Interaction in a cashless economy Business to Business (B 2 B) - Business to Consumer (B 2 C) - Consumer to Business (C 2 B) - Consumer to Consumer (C 2 C) - Government to Citizen (G 2 C) - Citizen to Government (C 2 G) - Exchange to Exchange (E 2 E) - Intra-business (Organization Unit to Organization Unit) - 5
 The Nigeria Cashless Policy: Where we are Across all payment channels in the financial industry; including electronic and nonelectronic based platform, Nigeria has experienced a massive rise in the volume and value of transactions processed yearly. Year End Volume Value 2013 74, 059, 575 34, 191, 968, 951, 140 2014 113, 421, 933 43, 857, 678, 478, 941 % Change 53% Increase 28% Increase Table 1 Total transaction volume and value processed by the NCS (Nigeria Central Switch) In the year 2014, the Central Switch (NIBSS) alone processed over 100 million transactions in terms of volume with a corresponding value of over NGN 40 Trillion (over USD 208 Billion). Furthermore, The volume of transactions grew by over 50% between 2013 and 2014 with its value also growing by 28%. 6
The Nigeria Cashless Policy: Where we are Across all payment channels in the financial industry; including electronic and nonelectronic based platform, Nigeria has experienced a massive rise in the volume and value of transactions processed yearly. Year End Volume Value 2013 74, 059, 575 34, 191, 968, 951, 140 2014 113, 421, 933 43, 857, 678, 478, 941 % Change 53% Increase 28% Increase Table 1 Total transaction volume and value processed by the NCS (Nigeria Central Switch) In the year 2014, the Central Switch (NIBSS) alone processed over 100 million transactions in terms of volume with a corresponding value of over NGN 40 Trillion (over USD 208 Billion). Furthermore, The volume of transactions grew by over 50% between 2013 and 2014 with its value also growing by 28%. 6
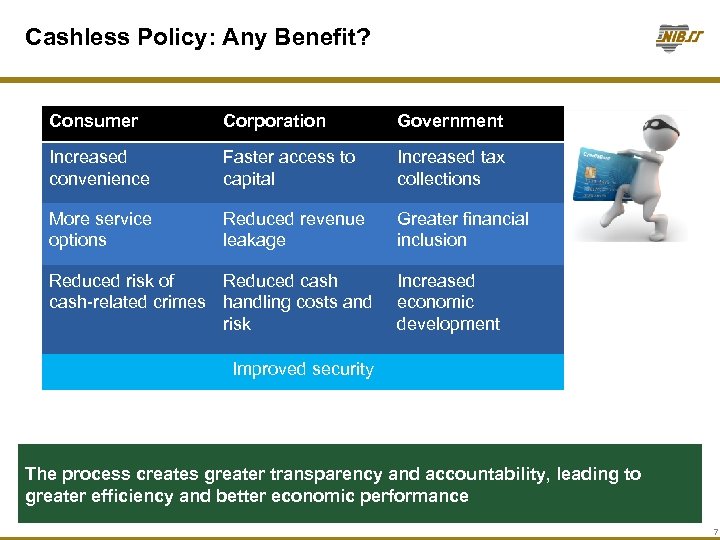 Cashless Policy: Any Benefit? Consumer Corporation Government Increased convenience Faster access to capital Increased tax collections More service options Reduced revenue leakage Greater financial inclusion Reduced risk of Reduced cash-related crimes handling costs and risk Increased economic development Improved security The process creates greater transparency and accountability, leading to greater efficiency and better economic performance 7
Cashless Policy: Any Benefit? Consumer Corporation Government Increased convenience Faster access to capital Increased tax collections More service options Reduced revenue leakage Greater financial inclusion Reduced risk of Reduced cash-related crimes handling costs and risk Increased economic development Improved security The process creates greater transparency and accountability, leading to greater efficiency and better economic performance 7
 Nigeria Cashless Economy: The Challenges q q q q Behavioural constraints Lack of confidence Low level of internet penetration Telecommunication issues Lack of suitable legal framework Required Huge Investments Reliable Communication Networks High rates of illiteracy Frequent power interruption More internal threats Prevalent social engineering attacks Identification issue Security Greater magnitude and impact of fraud Cashless policy, despites its numerous benefits comes with its own challenges even in the developed world. 8
Nigeria Cashless Economy: The Challenges q q q q Behavioural constraints Lack of confidence Low level of internet penetration Telecommunication issues Lack of suitable legal framework Required Huge Investments Reliable Communication Networks High rates of illiteracy Frequent power interruption More internal threats Prevalent social engineering attacks Identification issue Security Greater magnitude and impact of fraud Cashless policy, despites its numerous benefits comes with its own challenges even in the developed world. 8
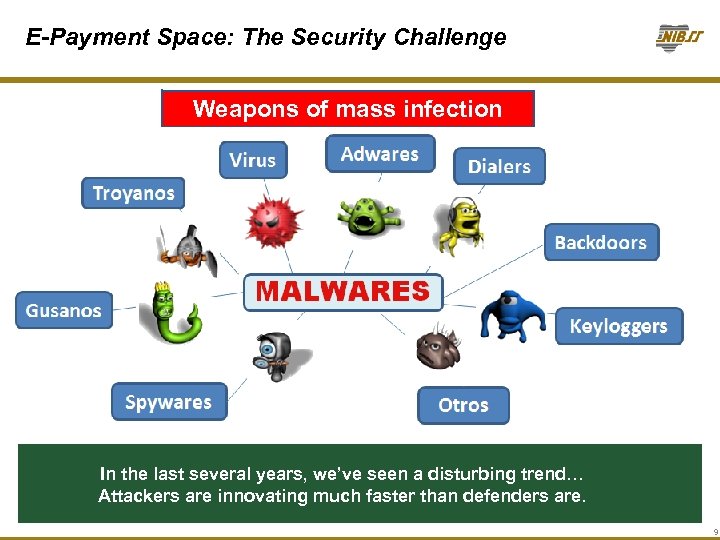 E-Payment Space: The Security Challenge Weapons of mass infection In the last several years, we’ve seen a disturbing trend… Attackers are innovating much faster than defenders are. 9
E-Payment Space: The Security Challenge Weapons of mass infection In the last several years, we’ve seen a disturbing trend… Attackers are innovating much faster than defenders are. 9
 10
10
 Cashless Economy: The Security Issues Online shopping, money transfers and online banking save us a lot of time and make our lives easier. However, these same technologies also make life easier for cybercriminals by offering them new, sophisticated and easy ways to steal personal data. Using stolen payment data is an effective and popular way of making a quick money. Although banks try to protect their customers, attacks against individual users are still quite common. Hacking a bank is more time-consuming and expensive and the risk of being caught is higher. By contrast, many individual customers use computers with numerous vulnerabilities, which are easier to compromise. By stealing a relatively small amount from each hijacked online banking account, a cybercriminal has a good chance of going undetected. 11
Cashless Economy: The Security Issues Online shopping, money transfers and online banking save us a lot of time and make our lives easier. However, these same technologies also make life easier for cybercriminals by offering them new, sophisticated and easy ways to steal personal data. Using stolen payment data is an effective and popular way of making a quick money. Although banks try to protect their customers, attacks against individual users are still quite common. Hacking a bank is more time-consuming and expensive and the risk of being caught is higher. By contrast, many individual customers use computers with numerous vulnerabilities, which are easier to compromise. By stealing a relatively small amount from each hijacked online banking account, a cybercriminal has a good chance of going undetected. 11
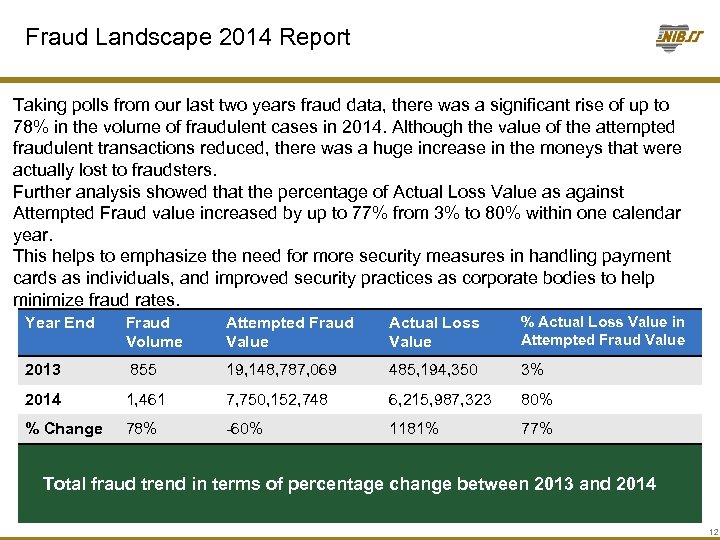 Fraud Landscape 2014 Report Taking polls from our last two years fraud data, there was a significant rise of up to 78% in the volume of fraudulent cases in 2014. Although the value of the attempted fraudulent transactions reduced, there was a huge increase in the moneys that were actually lost to fraudsters. Further analysis showed that the percentage of Actual Loss Value as against Attempted Fraud value increased by up to 77% from 3% to 80% within one calendar year. This helps to emphasize the need for more security measures in handling payment cards as individuals, and improved security practices as corporate bodies to help minimize fraud rates. Year End Fraud Volume Attempted Fraud Value Actual Loss Value % Actual Loss Value in Attempted Fraud Value 2013 855 19, 148, 787, 069 485, 194, 350 3% 2014 1, 461 7, 750, 152, 748 6, 215, 987, 323 80% % Change 78% -60% 1181% 77% Total fraud trend in terms of percentage change between 2013 and 2014 12
Fraud Landscape 2014 Report Taking polls from our last two years fraud data, there was a significant rise of up to 78% in the volume of fraudulent cases in 2014. Although the value of the attempted fraudulent transactions reduced, there was a huge increase in the moneys that were actually lost to fraudsters. Further analysis showed that the percentage of Actual Loss Value as against Attempted Fraud value increased by up to 77% from 3% to 80% within one calendar year. This helps to emphasize the need for more security measures in handling payment cards as individuals, and improved security practices as corporate bodies to help minimize fraud rates. Year End Fraud Volume Attempted Fraud Value Actual Loss Value % Actual Loss Value in Attempted Fraud Value 2013 855 19, 148, 787, 069 485, 194, 350 3% 2014 1, 461 7, 750, 152, 748 6, 215, 987, 323 80% % Change 78% -60% 1181% 77% Total fraud trend in terms of percentage change between 2013 and 2014 12
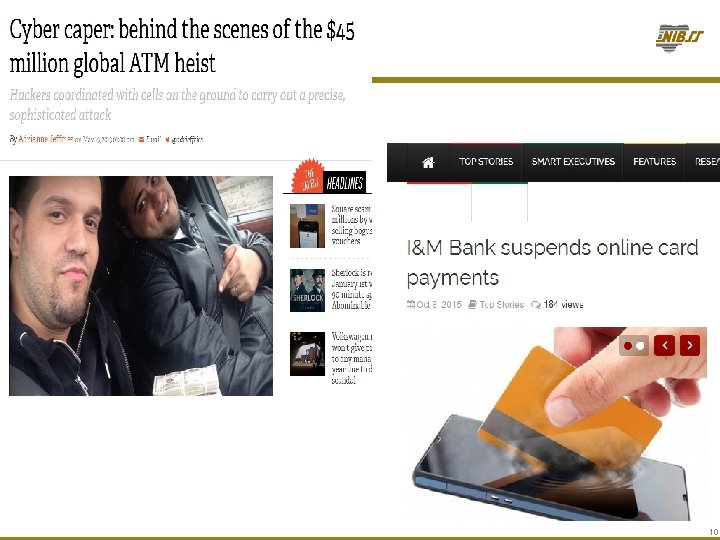
 Reporter Mitch Ohnstad : Why do you rob banks? Willie Sutton (Famous robber): “Because that's where the money is. " The money is now in e-Channels…. 13
Reporter Mitch Ohnstad : Why do you rob banks? Willie Sutton (Famous robber): “Because that's where the money is. " The money is now in e-Channels…. 13
 Then… … Now In 40 years Willie Sutton stole $2 million dollars In one day, Rodriguez stole $45 million dollars In 40 years Willie Sutton was able to steal only in one country In one day, Rodriguez stole in 27 countries AT THE SAME TIME Willie Sutton had to be present where ever he was stealing Rodriguez doesn’t need to be present where ever he was stealing Willie Sutton used guns and masks Rodriguez uses Laptop and Internet If Sutton were living today, he might have made the career move to hacker!!. 14
Then… … Now In 40 years Willie Sutton stole $2 million dollars In one day, Rodriguez stole $45 million dollars In 40 years Willie Sutton was able to steal only in one country In one day, Rodriguez stole in 27 countries AT THE SAME TIME Willie Sutton had to be present where ever he was stealing Rodriguez doesn’t need to be present where ever he was stealing Willie Sutton used guns and masks Rodriguez uses Laptop and Internet If Sutton were living today, he might have made the career move to hacker!!. 14
 Data Security Ø Data security refers to protective measures that are applied to prevent unauthorized access to computers, databases and websites. Data security also protects data from corruption. Data security is the main priority for organizations of every size and genre. Ø Data security is a key concern to the financial sector, being that a lot of customer’s data are processed and held. 15
Data Security Ø Data security refers to protective measures that are applied to prevent unauthorized access to computers, databases and websites. Data security also protects data from corruption. Data security is the main priority for organizations of every size and genre. Ø Data security is a key concern to the financial sector, being that a lot of customer’s data are processed and held. 15
 Data Security Facts Ø Consumers’ fears about data loss affect their willingness to use new service delivery channels; almost one in three internet users say they do not bank online because of concerns about security. Ø Some firms regard data security as the sole responsibility of IT staff, whose responsibilities include creating technical systems and controls to prevent data loss. While in the real sense of things data security is everybody's responsibility. 16
Data Security Facts Ø Consumers’ fears about data loss affect their willingness to use new service delivery channels; almost one in three internet users say they do not bank online because of concerns about security. Ø Some firms regard data security as the sole responsibility of IT staff, whose responsibilities include creating technical systems and controls to prevent data loss. While in the real sense of things data security is everybody's responsibility. 16
 Data Security Facts Cont’d Ø So it is in everyone’s interest to have a good awareness of data security and to establish effective controls to prevent their customer data from being used for financial crime 17
Data Security Facts Cont’d Ø So it is in everyone’s interest to have a good awareness of data security and to establish effective controls to prevent their customer data from being used for financial crime 17
 “Whollup”: How did they get my personal data? 18
“Whollup”: How did they get my personal data? 18
 Cashless Economy: How do we secure consumer’s Personal Data, What should we be doing? The financial industry manage the most sensitive, high-value information in the world. Our mandate is to protect it 19
Cashless Economy: How do we secure consumer’s Personal Data, What should we be doing? The financial industry manage the most sensitive, high-value information in the world. Our mandate is to protect it 19
 Securing the Consumer’s Data The Financial industry have always made frantic effort to improve data security across all channels within the e-Payment space. Security Standards are implemented to ensure service providers that “store”, “process” or “transmit” customer payment data adhere strictly to information security controls and processes that ensure data protection. Players across the payments processing chain must enhance payment data security globally, while embracing new technologies as they are developed. In an era of increasingly sophisticated attacks on systems, adhering to the global Security Standards is the best protection against network security threats and data breaches. 20
Securing the Consumer’s Data The Financial industry have always made frantic effort to improve data security across all channels within the e-Payment space. Security Standards are implemented to ensure service providers that “store”, “process” or “transmit” customer payment data adhere strictly to information security controls and processes that ensure data protection. Players across the payments processing chain must enhance payment data security globally, while embracing new technologies as they are developed. In an era of increasingly sophisticated attacks on systems, adhering to the global Security Standards is the best protection against network security threats and data breaches. 20
 Data Security: Policies and Standards (PCI, ISO, NIST. . ) To help prevent theft of card data and protect cardholder data, the five founding global payment brands, American Express, Discover Financial Services, JCB International, Master. Card Worldwide, and Visa Inc. launched the PCI Security Standards Council in 2006. PCI-DSS stands for Payment Card Industry (PCI) Data Security Standard (DSS). It is the technical requirements of each of the data security compliance programs intended to ensure that every card processing procedures meet certain security requirements. The PCI-DSS applies to all organizations that store, process or transmit cardholder data. EVERY business that accepts debit or credit card processing payments and stores, processes or transmits payment card data MUST MEET the PCI-DSS. With the rising incidence of security compromises, it is more important than ever to protect consumer data 21
Data Security: Policies and Standards (PCI, ISO, NIST. . ) To help prevent theft of card data and protect cardholder data, the five founding global payment brands, American Express, Discover Financial Services, JCB International, Master. Card Worldwide, and Visa Inc. launched the PCI Security Standards Council in 2006. PCI-DSS stands for Payment Card Industry (PCI) Data Security Standard (DSS). It is the technical requirements of each of the data security compliance programs intended to ensure that every card processing procedures meet certain security requirements. The PCI-DSS applies to all organizations that store, process or transmit cardholder data. EVERY business that accepts debit or credit card processing payments and stores, processes or transmits payment card data MUST MEET the PCI-DSS. With the rising incidence of security compromises, it is more important than ever to protect consumer data 21
 PCI DSS: Building Fence around Cardholder Data The following requirements comprise the PCI Data Security Standards: q Install and maintain a firewall configuration to protect Cardholder data q Do not use vendor-supplied defaults for system passwords and other security parameters q Protect stored cardholder data q Encrypt transmission of customer’s data across the networks q Use and regularly update anti-virus software or program q Develop and maintain secure systems and applications q Restrict access to cardholder data by business need-to-know q Assign a unique ID to each person with computer access q Restrict physical access to cardholder data q Track and monitor all access to network resources and cardholder data q Regularly test security systems and processes q Maintain a policy that addresses information security for all Personnel Protecting Cardholder Data is the business of every businesses 22
PCI DSS: Building Fence around Cardholder Data The following requirements comprise the PCI Data Security Standards: q Install and maintain a firewall configuration to protect Cardholder data q Do not use vendor-supplied defaults for system passwords and other security parameters q Protect stored cardholder data q Encrypt transmission of customer’s data across the networks q Use and regularly update anti-virus software or program q Develop and maintain secure systems and applications q Restrict access to cardholder data by business need-to-know q Assign a unique ID to each person with computer access q Restrict physical access to cardholder data q Track and monitor all access to network resources and cardholder data q Regularly test security systems and processes q Maintain a policy that addresses information security for all Personnel Protecting Cardholder Data is the business of every businesses 22
 Customer Data protection: the Banks Perspective Banks and payment platforms be actively protecting their users with the use of: q Sophisticated multi-factor authentication q The use of additional devices such as tokens to authenticate transactions q Various warnings of possible fraud q Implementation of short codes q Setup of fraud desk and dedicated phone lines q The industry should be ensuring a 360 -degree protection on the client side, securing user’s computer, communication channel and ensuring it connects to the right server. As attacks targeting corporate online banking applications grow more sophisticated, financial institutions need to strengthen their defenses. 23
Customer Data protection: the Banks Perspective Banks and payment platforms be actively protecting their users with the use of: q Sophisticated multi-factor authentication q The use of additional devices such as tokens to authenticate transactions q Various warnings of possible fraud q Implementation of short codes q Setup of fraud desk and dedicated phone lines q The industry should be ensuring a 360 -degree protection on the client side, securing user’s computer, communication channel and ensuring it connects to the right server. As attacks targeting corporate online banking applications grow more sophisticated, financial institutions need to strengthen their defenses. 23
 Encryption of Data (In Transit & At Rest) Once employed only for the most sensitive government secrets, encryption is today a common practice with strategic importance for businesses of all types. Financial institutions, retailers, healthcare providers, and others must protect customer information and are often bound by data breach disclosure laws. All types of businesses must keep private their diverse information about employees, customers, business operations, and intellectual property. Given that failure to protect confidential information may be not only embarrassing but also illegal, it’s easy to see why encryption is a core component in a broad data protection and IT security strategy. Encryption transforms data into an unusable form, reducing the risk in the case of unauthorized access. 24
Encryption of Data (In Transit & At Rest) Once employed only for the most sensitive government secrets, encryption is today a common practice with strategic importance for businesses of all types. Financial institutions, retailers, healthcare providers, and others must protect customer information and are often bound by data breach disclosure laws. All types of businesses must keep private their diverse information about employees, customers, business operations, and intellectual property. Given that failure to protect confidential information may be not only embarrassing but also illegal, it’s easy to see why encryption is a core component in a broad data protection and IT security strategy. Encryption transforms data into an unusable form, reducing the risk in the case of unauthorized access. 24
 Strong Authentication to secure today’s consumers One critical pillar in any security system is authentication—the process of verifying the identity of users, applications, or devices before giving them access to sensitive data or systems. Today’s authentication schemes range from a simple user ID and password to multi-factor approaches that include smart cards, PINs, mobile devices, and biometrics. The reason for this variety in authentication approaches is simple—applications require different degrees of assurance that users are who they claim to be. Financial institution should install Security Modules (HSMs, SSMs) to your current authentication processes, you can create high-assurance systems to authenticate users paying for products and services through web sites and mobile devices, employees using internal systems, and a variety of connected devices accessing the network. Financial institution must supports encrypted passwords, EMV authentication, smart cards, PKI based digital certificates, a wide range of one-time password (OTP) tokens, and SMS or mobile text based authentication. 25
Strong Authentication to secure today’s consumers One critical pillar in any security system is authentication—the process of verifying the identity of users, applications, or devices before giving them access to sensitive data or systems. Today’s authentication schemes range from a simple user ID and password to multi-factor approaches that include smart cards, PINs, mobile devices, and biometrics. The reason for this variety in authentication approaches is simple—applications require different degrees of assurance that users are who they claim to be. Financial institution should install Security Modules (HSMs, SSMs) to your current authentication processes, you can create high-assurance systems to authenticate users paying for products and services through web sites and mobile devices, employees using internal systems, and a variety of connected devices accessing the network. Financial institution must supports encrypted passwords, EMV authentication, smart cards, PKI based digital certificates, a wide range of one-time password (OTP) tokens, and SMS or mobile text based authentication. 25
 Data Security: Organizations and Its Roles q Educate employee on security threats and best practices for protecting consumers data. q Pre-employment screening q Ensure your business has a firewall, anti-virus, malware and spyware detection software. And don’t forget to regularly update the software. q Ensure tight measures and control on downloads, software installations, use of flash drives and public Wi-Fi connections on computers used for payment card processing. q Ensure dedicated and separate servers/networks for the processing of online financial transactions. q Change your passwords regularly q Ensure regularly back up your computers and the key data you want to protect. 26
Data Security: Organizations and Its Roles q Educate employee on security threats and best practices for protecting consumers data. q Pre-employment screening q Ensure your business has a firewall, anti-virus, malware and spyware detection software. And don’t forget to regularly update the software. q Ensure tight measures and control on downloads, software installations, use of flash drives and public Wi-Fi connections on computers used for payment card processing. q Ensure dedicated and separate servers/networks for the processing of online financial transactions. q Change your passwords regularly q Ensure regularly back up your computers and the key data you want to protect. 26
 E-Fraud: The Industry effort q q q q Education and Sensitization of the general public Establishment of Industry Fraud Desk(s) Regulatory and oversight functions by CBN Investment in huge infrastructure by major DMBs, Switches and Processors Introduction of Biometric Verification Number (BVN) Collaboration among key stakeholders Successful signing of the Cyber. Crime 2015 Act. 27
E-Fraud: The Industry effort q q q q Education and Sensitization of the general public Establishment of Industry Fraud Desk(s) Regulatory and oversight functions by CBN Investment in huge infrastructure by major DMBs, Switches and Processors Introduction of Biometric Verification Number (BVN) Collaboration among key stakeholders Successful signing of the Cyber. Crime 2015 Act. 27
 Final Thoughts If we do not implement Data security, we would fall prey to frauds. If we fall prey to frauds, people would loose confidence in electronic payments. If electronic payment fails, Cashless Economy fails. If cashless economy fails, we lost all the gains we have made in recent times. DATA SECURITY IS A MUST! http: //map. norsecorp. com/v 1/ ALL https: //www. fireeye. com/cyber-map/threat-map. html new attacks 28
Final Thoughts If we do not implement Data security, we would fall prey to frauds. If we fall prey to frauds, people would loose confidence in electronic payments. If electronic payment fails, Cashless Economy fails. If cashless economy fails, we lost all the gains we have made in recent times. DATA SECURITY IS A MUST! http: //map. norsecorp. com/v 1/ ALL https: //www. fireeye. com/cyber-map/threat-map. html new attacks 28
 THANK YOU Nigeria Inter-Bank Settlement System Plc … Improving the Nigeria Payments System 1230 b Ahmadu Bello Way Victoria Island, Lagos, Nigeria Tel: +234 1 2716071 -4 www. nibss-plc. com Olufemi Fadairo ofadairo@nibss-plc. com. ng 08025624929 29
THANK YOU Nigeria Inter-Bank Settlement System Plc … Improving the Nigeria Payments System 1230 b Ahmadu Bello Way Victoria Island, Lagos, Nigeria Tel: +234 1 2716071 -4 www. nibss-plc. com Olufemi Fadairo ofadairo@nibss-plc. com. ng 08025624929 29


