62c9882666883edc76f13dc37cf73e63.ppt
- Количество слайдов: 44
 Data Protection in a Workplace Context
Data Protection in a Workplace Context
 Layout of Presentation • • • Background to Data Protection Role of Data Protection Commissioner Principles of Data Protection Key Responsibilities of Data Controllers Key points of information
Layout of Presentation • • • Background to Data Protection Role of Data Protection Commissioner Principles of Data Protection Key Responsibilities of Data Controllers Key points of information
 Data Protection: Background • Human Right to Privacy • Unenumerated right under Irish Constitution • Explicit right under European Convention on Human Rights ECHR Act 2003 • EU Data Protection Directives
Data Protection: Background • Human Right to Privacy • Unenumerated right under Irish Constitution • Explicit right under European Convention on Human Rights ECHR Act 2003 • EU Data Protection Directives
 EU & Irish Legislation • Data Protection Directive • Data Protection Acts 95/46/EC 1988 & 2003 • Electronic Privacy • EC Electronic Privacy Directive 2002/58/EC Regulations 2003 (SI 535/2003) • Corresponding Acts • EUROPOL etc • Good Friday Agreement • Disability Act 2005
EU & Irish Legislation • Data Protection Directive • Data Protection Acts 95/46/EC 1988 & 2003 • Electronic Privacy • EC Electronic Privacy Directive 2002/58/EC Regulations 2003 (SI 535/2003) • Corresponding Acts • EUROPOL etc • Good Friday Agreement • Disability Act 2005
 Definitions • Data Ø Includes automated and structured manual data • Personal Data Ø Data relating to a living identifiable individual • Sensitive Personal Data (more protection) Ø Racial/ethnic origin; political opinions; religious/philosophical beliefs; trade union membership; health; sexual life; criminal record
Definitions • Data Ø Includes automated and structured manual data • Personal Data Ø Data relating to a living identifiable individual • Sensitive Personal Data (more protection) Ø Racial/ethnic origin; political opinions; religious/philosophical beliefs; trade union membership; health; sexual life; criminal record
 Definitions • Data Controller Ø a person who controls the contents and use of personal data • Data Processor Ø A person who processes personal data on behalf of a data controller
Definitions • Data Controller Ø a person who controls the contents and use of personal data • Data Processor Ø A person who processes personal data on behalf of a data controller
 Layout of Presentation • Background to Data Protection • Role of Data Protection Commissioner • Principles of Data Protection • Key Responsibilities of Data Controllers • Key points of information
Layout of Presentation • Background to Data Protection • Role of Data Protection Commissioner • Principles of Data Protection • Key Responsibilities of Data Controllers • Key points of information
 Role of the Data Protection Commissioner • Ombudsman Role: resolution of disputes between data subjects and data controllers or processors • Enforcer Role: compliance by data controllers & processors • Educational Role: Promotes DP rights and good practice • Registration Authority: obligation on major holders of personal data to be placed on public register
Role of the Data Protection Commissioner • Ombudsman Role: resolution of disputes between data subjects and data controllers or processors • Enforcer Role: compliance by data controllers & processors • Educational Role: Promotes DP rights and good practice • Registration Authority: obligation on major holders of personal data to be placed on public register
 How does DPC fulfill role? • Investigations/Audits Ø Ø Arising from complaints On own initiative • Maintains public register • Codes of Practice • Guidance booklets, website, presentations, advice, Annual Report
How does DPC fulfill role? • Investigations/Audits Ø Ø Arising from complaints On own initiative • Maintains public register • Codes of Practice • Guidance booklets, website, presentations, advice, Annual Report
 Penalties • Fine of up to € 100, 000 • Court may order deletion • Enforcement notice prohibiting processing • Data subject could pursue civil action for damages under section 7 of the Act
Penalties • Fine of up to € 100, 000 • Court may order deletion • Enforcement notice prohibiting processing • Data subject could pursue civil action for damages under section 7 of the Act
 The Data Protection Rules 1. Fair obtaining & processing • Consent 2. Specified purpose 3. No disclosure • unless “compatible” 4. Safe and secure 5. 6. 7. 8. Accurate, up-to-date Relevant, not excessive Retention period Right of access
The Data Protection Rules 1. Fair obtaining & processing • Consent 2. Specified purpose 3. No disclosure • unless “compatible” 4. Safe and secure 5. 6. 7. 8. Accurate, up-to-date Relevant, not excessive Retention period Right of access
 Responsibilities on Data Controllers at the different stages Beginning Middle End Getting the Data While you have the data Disposing of data
Responsibilities on Data Controllers at the different stages Beginning Middle End Getting the Data While you have the data Disposing of data
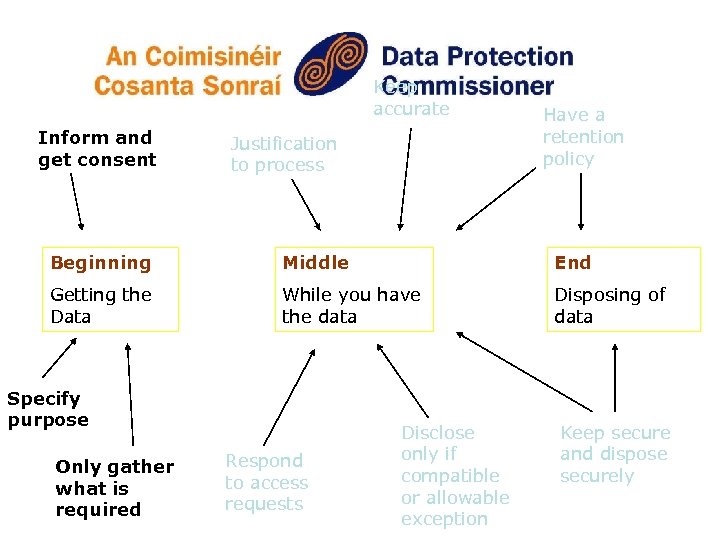 Keep accurate Inform and get consent Justification to process Have a retention policy Beginning Middle End Getting the Data While you have the data Disposing of data Specify purpose Only gather what is required Respond to access requests Disclose only if compatible or allowable exception Keep secure and dispose securely
Keep accurate Inform and get consent Justification to process Have a retention policy Beginning Middle End Getting the Data While you have the data Disposing of data Specify purpose Only gather what is required Respond to access requests Disclose only if compatible or allowable exception Keep secure and dispose securely
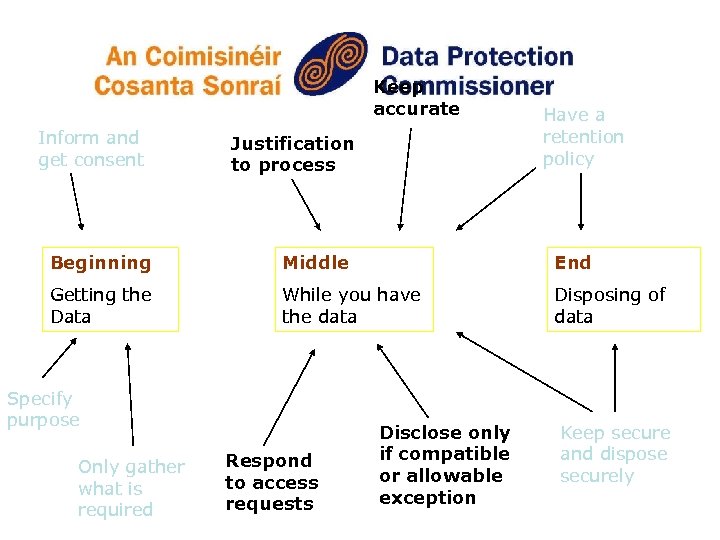 Keep accurate Inform and get consent Justification to process Have a retention policy Beginning Middle End Getting the Data While you have the data Disposing of data Specify purpose Only gather what is required Respond to access requests Disclose only if compatible or allowable exception Keep secure and dispose securely
Keep accurate Inform and get consent Justification to process Have a retention policy Beginning Middle End Getting the Data While you have the data Disposing of data Specify purpose Only gather what is required Respond to access requests Disclose only if compatible or allowable exception Keep secure and dispose securely
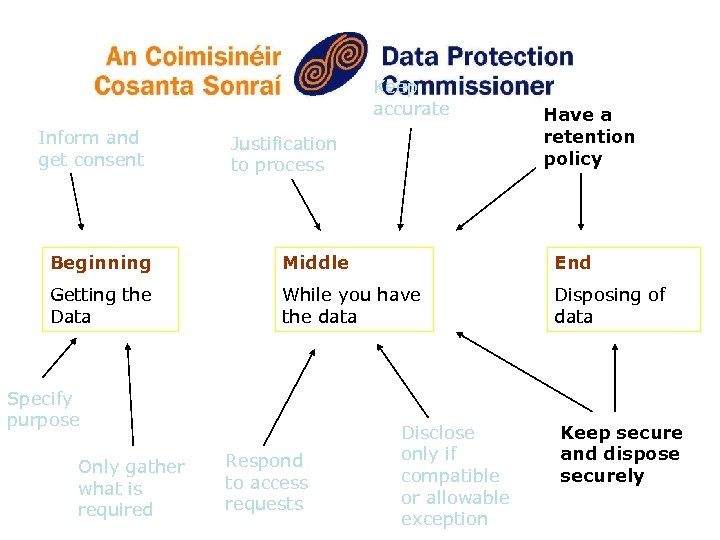 Keep accurate Inform and get consent Justification to process Have a retention policy Beginning Middle End Getting the Data While you have the data Disposing of data Specify purpose Only gather what is required Respond to access requests Disclose only if compatible or allowable exception Keep secure and dispose securely
Keep accurate Inform and get consent Justification to process Have a retention policy Beginning Middle End Getting the Data While you have the data Disposing of data Specify purpose Only gather what is required Respond to access requests Disclose only if compatible or allowable exception Keep secure and dispose securely
 Layout of Presentation • • Background to Data Protection Role of Data Protection Commissioner Principles of Data Protection Key Responsibilities of Data Controllers • Key points of information
Layout of Presentation • • Background to Data Protection Role of Data Protection Commissioner Principles of Data Protection Key Responsibilities of Data Controllers • Key points of information
 Key Responsibilities • Keep Information Accurate • Disclose only if compatible with purpose for which given • Keep secure • Have a retention policy • Dispose and retain in line with retention policy • Respond to Requests for Access/Deletion • Manual data requirements from 24 October 2007
Key Responsibilities • Keep Information Accurate • Disclose only if compatible with purpose for which given • Keep secure • Have a retention policy • Dispose and retain in line with retention policy • Respond to Requests for Access/Deletion • Manual data requirements from 24 October 2007
 1. Accurate • Good business practice • Best achieved at point of collection • Ongoing requirement if intended to be used. • Ask the data subject if needed
1. Accurate • Good business practice • Best achieved at point of collection • Ongoing requirement if intended to be used. • Ask the data subject if needed
 2. Non-Disclosure • General rule – no disclosure for different purpose • Exceptions made, to balance other interests of society • Stricter conditions for sensitive data • Main exceptions: Ø Ø Ø Ø Investigation of crime Collection of taxes Security of the State Protect life & limb Required by Law Intl Relations Consent
2. Non-Disclosure • General rule – no disclosure for different purpose • Exceptions made, to balance other interests of society • Stricter conditions for sensitive data • Main exceptions: Ø Ø Ø Ø Investigation of crime Collection of taxes Security of the State Protect life & limb Required by Law Intl Relations Consent
 2. Non-Disclosure • The Data Controller should have a policy in place to determine how requests for data from third parties are handled. • This policy should be consulted by appropriate staff members
2. Non-Disclosure • The Data Controller should have a policy in place to determine how requests for data from third parties are handled. • This policy should be consulted by appropriate staff members
 2. Non- Disclosure -Data Transfer • Data Controller to Data Processor Ø Must have contract in place: Data Controller remains responsible • International Data Transfers Ø Ø ‘white list’ countries Model Contracts Binding Corporate Rules Exceptions: individual consent etc (avoid for regular transfers)
2. Non- Disclosure -Data Transfer • Data Controller to Data Processor Ø Must have contract in place: Data Controller remains responsible • International Data Transfers Ø Ø ‘white list’ countries Model Contracts Binding Corporate Rules Exceptions: individual consent etc (avoid for regular transfers)
 3. Keep secure • Internal Access controls– physical, technical, • Tracking of activity on files– to see if appropriate • Internet Connectivity/networks -anti-virus software/firewalls/encryption • Access- need to know and relevant to purpose • Third party interception
3. Keep secure • Internal Access controls– physical, technical, • Tracking of activity on files– to see if appropriate • Internet Connectivity/networks -anti-virus software/firewalls/encryption • Access- need to know and relevant to purpose • Third party interception
 3. Keep secure • Accidental disclosure to third parties, PC in public area, non-secure fax • External-robust encryption, online forms, technical measures • Audit trails, reviews, logs, unusual events • Manual Files ! • Individual is the biggest risk- NB Training
3. Keep secure • Accidental disclosure to third parties, PC in public area, non-secure fax • External-robust encryption, online forms, technical measures • Audit trails, reviews, logs, unusual events • Manual Files ! • Individual is the biggest risk- NB Training
 4. Retention Policy • Legal obligations to hold data? • Customer files Ø Do you need to hold all that data? • Personnel files Ø Revenue requirement? • Must have policy thought through Ø Defend retention as necessary for purpose.
4. Retention Policy • Legal obligations to hold data? • Customer files Ø Do you need to hold all that data? • Personnel files Ø Revenue requirement? • Must have policy thought through Ø Defend retention as necessary for purpose.
 5. Follow Retention Policy • A method appropriate to each organisation to review files • Assign Responsibility • Reporting structure • Delete personal data that is outside terms of policy. • Keep a record of deletions
5. Follow Retention Policy • A method appropriate to each organisation to review files • Assign Responsibility • Reporting structure • Delete personal data that is outside terms of policy. • Keep a record of deletions
 6. Right of Access • A fundamental right granted to individuals as a means of granting them control over how their data are processed – transparency • Applies to all manual and electronic records in existence at the time of receipt of an access request – regardless of when the record was created.
6. Right of Access • A fundamental right granted to individuals as a means of granting them control over how their data are processed – transparency • Applies to all manual and electronic records in existence at the time of receipt of an access request – regardless of when the record was created.
 6. Right of Access • Every person has the right to access their data held by any organisation subject to very limited exemption outlined in Sections 4 & 5 of the Data Protection Acts • Standard maximum fee of € 6. 35. Must reply within 40 days or indicate reasons why cannot comply • Commissioner takes this right very seriously and is now using legal enforcement powers to enforce rights
6. Right of Access • Every person has the right to access their data held by any organisation subject to very limited exemption outlined in Sections 4 & 5 of the Data Protection Acts • Standard maximum fee of € 6. 35. Must reply within 40 days or indicate reasons why cannot comply • Commissioner takes this right very seriously and is now using legal enforcement powers to enforce rights
 6. Right of correction/erasure • Section 6 of the Act • Data Subject makes a written request • Personal data must be: Ø Ø Corrected, if inaccurate; or Deleted, if should not be held. • Data Controller has 40 days to respond • No fee
6. Right of correction/erasure • Section 6 of the Act • Data Subject makes a written request • Personal data must be: Ø Ø Corrected, if inaccurate; or Deleted, if should not be held. • Data Controller has 40 days to respond • No fee
 7. Manual data • Manual data on file on October 2003 has been exempt from some rules until 24 October 2007 Ø Ø Ø section 2 (identity of Data Controller, purposes of processing, any disclosees) sections 2 A (legitimate processing) and 2 B (sensitive data) – see over All other provisions – including right of access and correction – apply already
7. Manual data • Manual data on file on October 2003 has been exempt from some rules until 24 October 2007 Ø Ø Ø section 2 (identity of Data Controller, purposes of processing, any disclosees) sections 2 A (legitimate processing) and 2 B (sensitive data) – see over All other provisions – including right of access and correction – apply already
 7. Manual Data -Process Fairly One of these conditions required: Ø Consent Ø Legal obligation Ø Contract with individual Ø Necessary to protect vital interests Ø Necessary for a public function (Justice) Ø necessary for ‘legitimate interests’
7. Manual Data -Process Fairly One of these conditions required: Ø Consent Ø Legal obligation Ø Contract with individual Ø Necessary to protect vital interests Ø Necessary for a public function (Justice) Ø necessary for ‘legitimate interests’
 7. Manual Data - Process Sensitive Data fairly One of these additional conditions is required Ø Explicit consent Ø Necessary under employment law Ø To prevent injury or protect vital interests Ø Process the data of members/clients of nonprofit orgs. Ø Legal advice Ø For Medical Purposes Ø Statutory function
7. Manual Data - Process Sensitive Data fairly One of these additional conditions is required Ø Explicit consent Ø Necessary under employment law Ø To prevent injury or protect vital interests Ø Process the data of members/clients of nonprofit orgs. Ø Legal advice Ø For Medical Purposes Ø Statutory function
 Layout of Presentation • • • Background to Data Protection Role of Data Protection Commissioner Principles of Data Protection Key Responsibilities of Data Controllers Key Points of Information
Layout of Presentation • • • Background to Data Protection Role of Data Protection Commissioner Principles of Data Protection Key Responsibilities of Data Controllers Key Points of Information
 Key Points of Information • • Workplace Monitoring Biometrics in the Workplace Internal Directories Monitoring outside of Workplace Interview/Exit Interview Notes References Access to appraisal forms
Key Points of Information • • Workplace Monitoring Biometrics in the Workplace Internal Directories Monitoring outside of Workplace Interview/Exit Interview Notes References Access to appraisal forms
 CCTV/Email/Internet monitoring • organisations have a legitimate interest to protect their business, reputation, resources and equipment. • acceptable usage policy is key • Make employees aware of monitoring
CCTV/Email/Internet monitoring • organisations have a legitimate interest to protect their business, reputation, resources and equipment. • acceptable usage policy is key • Make employees aware of monitoring
 CCTV/Email/Internet monitoring (Ctd) • Access to any material being monitored needs to be strictly controlled • Only access/disclose for uses indicated • E. g. If CCTV for security, can only be accessed and disclosed for that purpose
CCTV/Email/Internet monitoring (Ctd) • Access to any material being monitored needs to be strictly controlled • Only access/disclose for uses indicated • E. g. If CCTV for security, can only be accessed and disclosed for that purpose
 Biometrics in the Workplace • Proportionality • Section 2(1)(c)(iii) states that data • “shall be adequate, relevant and not excessive in relation to the purpose or purposes for which they were collected or are further processed. ” • Assess the need for a system and evaluate the different types of system before introduction.
Biometrics in the Workplace • Proportionality • Section 2(1)(c)(iii) states that data • “shall be adequate, relevant and not excessive in relation to the purpose or purposes for which they were collected or are further processed. ” • Assess the need for a system and evaluate the different types of system before introduction.
 Biometrics in the Workplace What are the considerations: • Environment. The nature of the workplace may require high levels of security. • Purpose. Can the intended purpose be achieved in a less intrusive way? • Efficiency. Ease of administration may necessitate the introduction of a system where other less invasive systems have failed, or proved to be prohibitively expensive to run. • Reliability. a system may be justified as long as other less invasive ones have been assessed and reasonably rejected.
Biometrics in the Workplace What are the considerations: • Environment. The nature of the workplace may require high levels of security. • Purpose. Can the intended purpose be achieved in a less intrusive way? • Efficiency. Ease of administration may necessitate the introduction of a system where other less invasive systems have failed, or proved to be prohibitively expensive to run. • Reliability. a system may be justified as long as other less invasive ones have been assessed and reasonably rejected.
 Monitoring outside of Workplace • Same general principles apply • Must be proportionate and not intrusive into privacy • Employee should be aware that could occur • Right of access to material applies
Monitoring outside of Workplace • Same general principles apply • Must be proportionate and not intrusive into privacy • Employee should be aware that could occur • Right of access to material applies
 Internal Directories • A photograph is sensitive data • Any proposal to have a corporate directory including photographs should be discussed with employees • Explicit consent not as relevant in workplace • Any requests from employees for the removal of images must be accepted. • Legitimate interest of employer? • Inform all employees that photographs must not be used for any other purpose
Internal Directories • A photograph is sensitive data • Any proposal to have a corporate directory including photographs should be discussed with employees • Explicit consent not as relevant in workplace • Any requests from employees for the removal of images must be accepted. • Legitimate interest of employer? • Inform all employees that photographs must not be used for any other purpose
 Interview/Exit Interview Notes • • • Must be relevant and necessary Accuracy. Relevance Opinion –v- Fact. Available as part of an Access Request. Third party details removed?
Interview/Exit Interview Notes • • • Must be relevant and necessary Accuracy. Relevance Opinion –v- Fact. Available as part of an Access Request. Third party details removed?
 References • References obtained may be provided to the person as part of the response to a subject access request, unless in confidence. Even then if fundamental rights of the person take precedence then release • Be able to stand over data.
References • References obtained may be provided to the person as part of the response to a subject access request, unless in confidence. Even then if fundamental rights of the person take precedence then release • Be able to stand over data.
 Access to appraisal forms • Typically made available to staff as part of process • Where not, staff likely to have a right of access
Access to appraisal forms • Typically made available to staff as part of process • Where not, staff likely to have a right of access
 General points of advice • Appropriate data retention policy in place in relation to spent disciplinary notices on file • Be clear as to the basis on which an employee is referred to a doctor for consultation. Any resulting report should be made available to the employee and can only be used for the purpose indicated
General points of advice • Appropriate data retention policy in place in relation to spent disciplinary notices on file • Be clear as to the basis on which an employee is referred to a doctor for consultation. Any resulting report should be made available to the employee and can only be used for the purpose indicated
 General points of advice (ctd) • Workplace accidents. Sometimes reports complied by insurance companies seem to find their way back to the employer. What is the basis? • Disciplinary proceedings including labour court etc, person has a right of access to personal data • Note boundaries of legal professional privilege. Must be genuinely legal advice. Not just because it was written or amended by a legal person
General points of advice (ctd) • Workplace accidents. Sometimes reports complied by insurance companies seem to find their way back to the employer. What is the basis? • Disciplinary proceedings including labour court etc, person has a right of access to personal data • Note boundaries of legal professional privilege. Must be genuinely legal advice. Not just because it was written or amended by a legal person


