cdd7d4d87be7c240db940936ebe8b73f.ppt
- Количество слайдов: 31
 ® Data. Power SOA Appliances Acelerando el Valor Ricardo Fittipaldi Data. Power SOA Appliances, Latin. America Sales rfittipa@ve. ibm. com © 2007 IBM Corporation
® Data. Power SOA Appliances Acelerando el Valor Ricardo Fittipaldi Data. Power SOA Appliances, Latin. America Sales rfittipa@ve. ibm. com © 2007 IBM Corporation
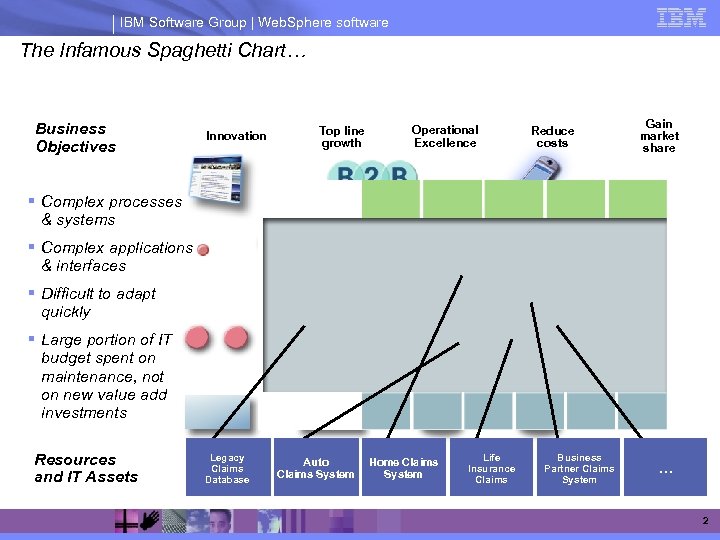 IBM Software Group | Web. Sphere software The Infamous Spaghetti Chart… Business Objectives Innovation Top line growth Operational Excellence Reduce costs Gain market share § Complex processes & systems § Complex applications & interfaces § Difficult to adapt quickly § Large portion of IT budget spent on maintenance, not on new value add investments Resources and IT Assets Legacy Claims Database Auto Claims System Home Claims System Life Insurance Claims Business Partner Claims System … 2
IBM Software Group | Web. Sphere software The Infamous Spaghetti Chart… Business Objectives Innovation Top line growth Operational Excellence Reduce costs Gain market share § Complex processes & systems § Complex applications & interfaces § Difficult to adapt quickly § Large portion of IT budget spent on maintenance, not on new value add investments Resources and IT Assets Legacy Claims Database Auto Claims System Home Claims System Life Insurance Claims Business Partner Claims System … 2
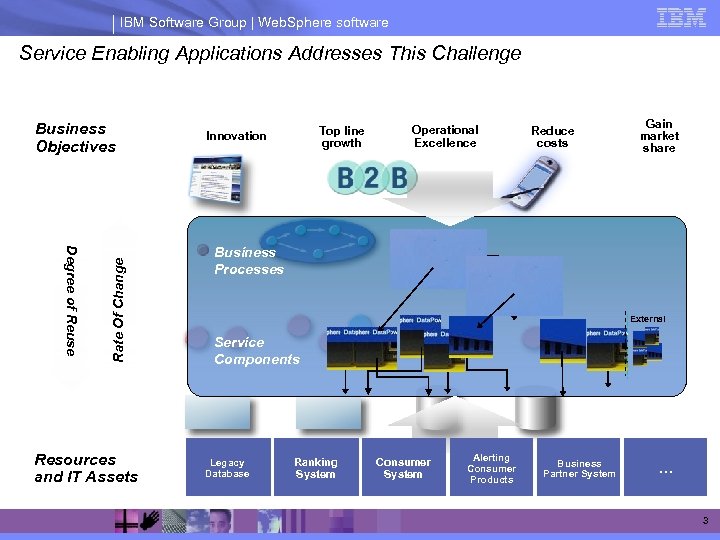 IBM Software Group | Web. Sphere software Service Enabling Applications Addresses This Challenge Degree of Reuse Rate Of Change Business Objectives Resources and IT Assets Top line growth Innovation Operational Excellence Reduce costs Gain market share Business Processes External Service Components Legacy Claims Database Ranking Auto System Claims System Consumer Home Claims System Life Alerting Insurance Consumer Claims Products Business Partner Claims Partner System … 3
IBM Software Group | Web. Sphere software Service Enabling Applications Addresses This Challenge Degree of Reuse Rate Of Change Business Objectives Resources and IT Assets Top line growth Innovation Operational Excellence Reduce costs Gain market share Business Processes External Service Components Legacy Claims Database Ranking Auto System Claims System Consumer Home Claims System Life Alerting Insurance Consumer Claims Products Business Partner Claims Partner System … 3
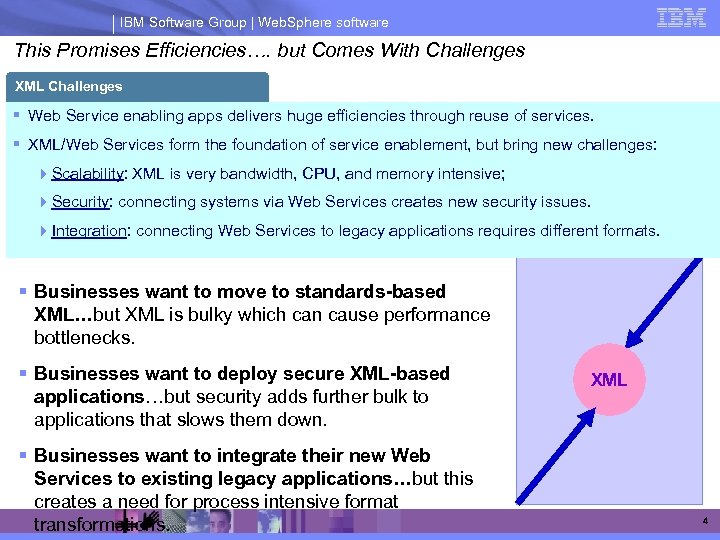 IBM Software Group | Web. Sphere software This Promises Efficiencies…. but Comes With Challenges XML Challenges § Web Service enabling apps delivers huge efficiencies through reuse of services. § XML/Web Services form the foundation of service enablement, but bring new challenges: 4 Scalability: XML is very bandwidth, CPU, and memory intensive; 4 Security: connecting systems via Web Services creates new security issues. 4 Integration: connecting Web Services to legacy applications requires different formats. § Businesses want to move to standards-based XML…but XML is bulky which can cause performance bottlenecks. § Businesses want to deploy secure XML-based applications…but security adds further bulk to applications that slows them down. § Businesses want to integrate their new Web Services to existing legacy applications…but this creates a need for process intensive format transformations. XML 4
IBM Software Group | Web. Sphere software This Promises Efficiencies…. but Comes With Challenges XML Challenges § Web Service enabling apps delivers huge efficiencies through reuse of services. § XML/Web Services form the foundation of service enablement, but bring new challenges: 4 Scalability: XML is very bandwidth, CPU, and memory intensive; 4 Security: connecting systems via Web Services creates new security issues. 4 Integration: connecting Web Services to legacy applications requires different formats. § Businesses want to move to standards-based XML…but XML is bulky which can cause performance bottlenecks. § Businesses want to deploy secure XML-based applications…but security adds further bulk to applications that slows them down. § Businesses want to integrate their new Web Services to existing legacy applications…but this creates a need for process intensive format transformations. XML 4
 IBM Software Group | Web. Sphere software “Commodity” Processes Migrate to Appliances § Historical trend is for software functions that are simple, yet require a lot of computing power, to move into dedicated appliances. § Part of a larger trend that initially started by moving functions such as Traffic Routing and Load Balancing into hardware. § XML/Web Services processing tasks such as Security, Application Routing, Transformation, Management are rather simple, but very CPU intensive. 5
IBM Software Group | Web. Sphere software “Commodity” Processes Migrate to Appliances § Historical trend is for software functions that are simple, yet require a lot of computing power, to move into dedicated appliances. § Part of a larger trend that initially started by moving functions such as Traffic Routing and Load Balancing into hardware. § XML/Web Services processing tasks such as Security, Application Routing, Transformation, Management are rather simple, but very CPU intensive. 5
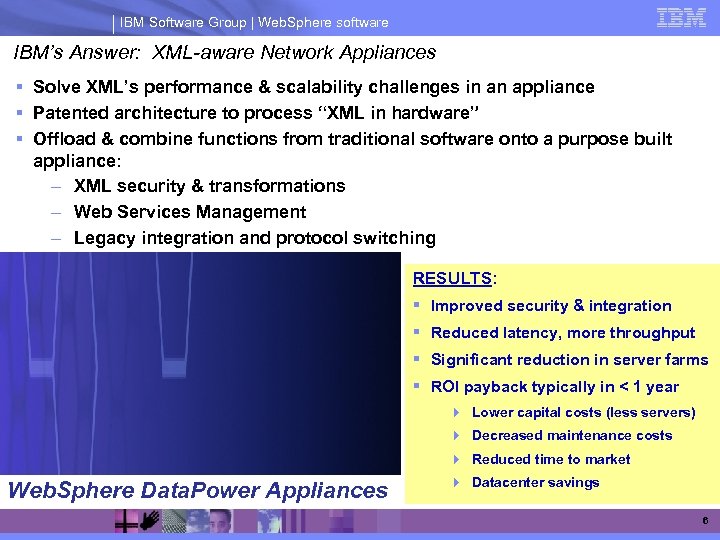 IBM Software Group | Web. Sphere software IBM’s Answer: XML-aware Network Appliances § Solve XML’s performance & scalability challenges in an appliance § Patented architecture to process “XML in hardware” § Offload & combine functions from traditional software onto a purpose built appliance: – XML security & transformations – Web Services Management – Legacy integration and protocol switching – Other resource intensive tasks RESULTS: § Improved security & integration § Reduced latency, more throughput § Significant reduction in server farms § ROI payback typically in < 1 year 4 Lower capital costs (less servers) 4 Decreased maintenance costs 4 Reduced time to market Web. Sphere Data. Power Appliances 4 Datacenter savings 6
IBM Software Group | Web. Sphere software IBM’s Answer: XML-aware Network Appliances § Solve XML’s performance & scalability challenges in an appliance § Patented architecture to process “XML in hardware” § Offload & combine functions from traditional software onto a purpose built appliance: – XML security & transformations – Web Services Management – Legacy integration and protocol switching – Other resource intensive tasks RESULTS: § Improved security & integration § Reduced latency, more throughput § Significant reduction in server farms § ROI payback typically in < 1 year 4 Lower capital costs (less servers) 4 Decreased maintenance costs 4 Reduced time to market Web. Sphere Data. Power Appliances 4 Datacenter savings 6
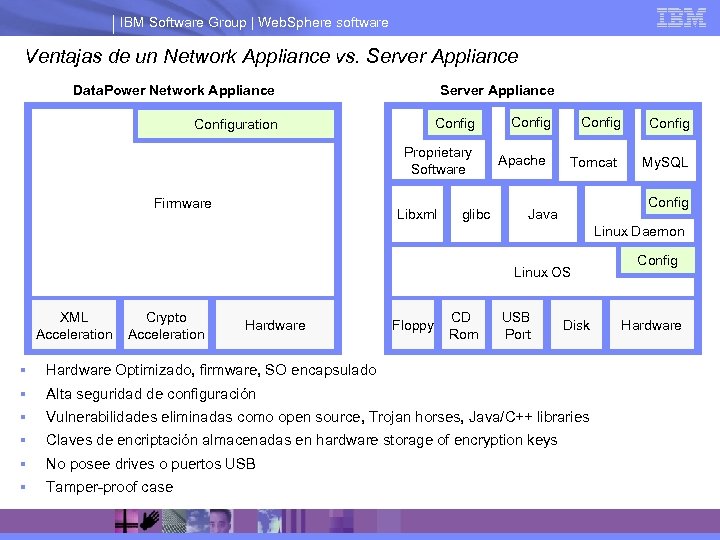 IBM Software Group | Web. Sphere software Ventajas de un Network Appliance vs. Server Appliance Data. Power Network Appliance Server Appliance Configuration Proprietary Software Firmware Libxml glibc Config Apache Config Tomcat Config My. SQL Config Java Linux Daemon Linux OS XML Acceleration Crypto Acceleration Hardware Floppy CD Rom USB Port Disk § Hardware Optimizado, firmware, SO encapsulado § Alta seguridad de configuración § Vulnerabilidades eliminadas como open source, Trojan horses, Java/C++ libraries § Claves de encriptación almacenadas en hardware storage of encryption keys § No posee drives o puertos USB § Tamper-proof case Config Hardware
IBM Software Group | Web. Sphere software Ventajas de un Network Appliance vs. Server Appliance Data. Power Network Appliance Server Appliance Configuration Proprietary Software Firmware Libxml glibc Config Apache Config Tomcat Config My. SQL Config Java Linux Daemon Linux OS XML Acceleration Crypto Acceleration Hardware Floppy CD Rom USB Port Disk § Hardware Optimizado, firmware, SO encapsulado § Alta seguridad de configuración § Vulnerabilidades eliminadas como open source, Trojan horses, Java/C++ libraries § Claves de encriptación almacenadas en hardware storage of encryption keys § No posee drives o puertos USB § Tamper-proof case Config Hardware
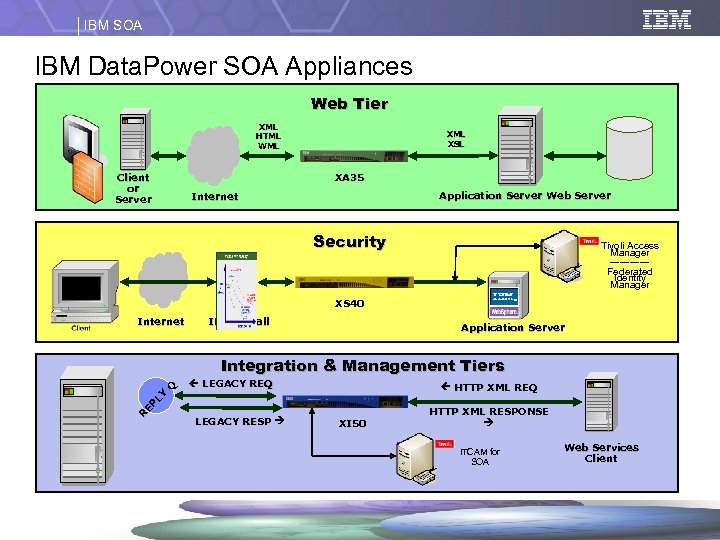 IBM SOA IBM Data. Power SOA Appliances Web Tier XML HTML WML XSL XA 35 Client or Server Application Server Web Server Internet Security Tivoli Access Manager ------Federated Identity Manager XS 40 Internet IP Firewall Application Server R EP LY Q Integration & Management Tiers LEGACY REQ LEGACY RESP HTTP XML REQ XI 50 HTTP XML RESPONSE ITCAM for SOA Web Services Client
IBM SOA IBM Data. Power SOA Appliances Web Tier XML HTML WML XSL XA 35 Client or Server Application Server Web Server Internet Security Tivoli Access Manager ------Federated Identity Manager XS 40 Internet IP Firewall Application Server R EP LY Q Integration & Management Tiers LEGACY REQ LEGACY RESP HTTP XML REQ XI 50 HTTP XML RESPONSE ITCAM for SOA Web Services Client
 ® Data. Power Customer Scenarios © 2007 IBM Corporation
® Data. Power Customer Scenarios © 2007 IBM Corporation
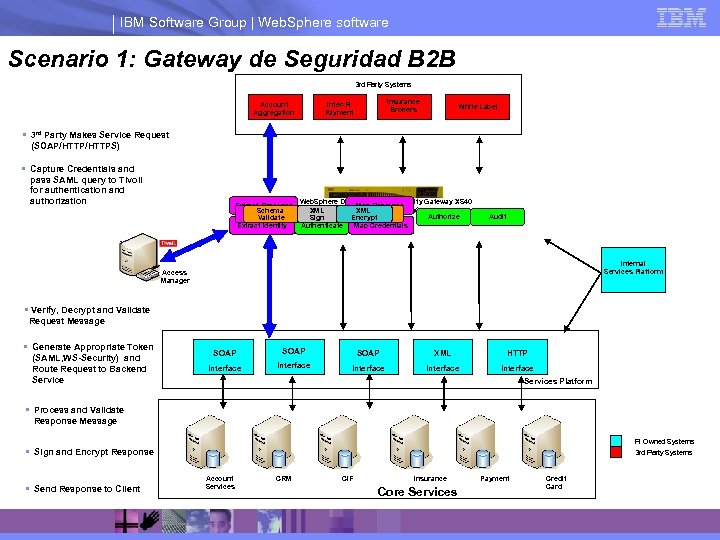 IBM Software Group | Web. Sphere software Scenario 1: Gateway de Seguridad B 2 B 3 rd Party Systems Account Aggregation Insurance Brokers Inter-FI Payment White Label § 3 rd Party Makes Service Request (SOAP/HTTPS) § Capture Credentials and pass SAML query to Tivoli for authentication and authorization Extract Resource Signature Schema XML Verify Validate Transform Extract Identity Web. Sphere Data. Power XML Security Gateway XS 40 Map Resource (XML/AAA Gateway) XML XML Schema Route Authorize Decrypt Sign Encrypt Validate Authenticate Map Credentials Audit Internal Services Platform Access Manager § Verify, Decrypt and Validate Request Message § Generate Appropriate Token (SAML, WS-Security) and Route Request to Backend Service SOAP XML HTTP Interface Interface Services Platform § Process and Validate Response Message FI Owned Systems § Sign and Encrypt Response § Send Response to Client 3 rd Party Systems Account Services CRM CIF Insurance Core Services Payment Credit Card
IBM Software Group | Web. Sphere software Scenario 1: Gateway de Seguridad B 2 B 3 rd Party Systems Account Aggregation Insurance Brokers Inter-FI Payment White Label § 3 rd Party Makes Service Request (SOAP/HTTPS) § Capture Credentials and pass SAML query to Tivoli for authentication and authorization Extract Resource Signature Schema XML Verify Validate Transform Extract Identity Web. Sphere Data. Power XML Security Gateway XS 40 Map Resource (XML/AAA Gateway) XML XML Schema Route Authorize Decrypt Sign Encrypt Validate Authenticate Map Credentials Audit Internal Services Platform Access Manager § Verify, Decrypt and Validate Request Message § Generate Appropriate Token (SAML, WS-Security) and Route Request to Backend Service SOAP XML HTTP Interface Interface Services Platform § Process and Validate Response Message FI Owned Systems § Sign and Encrypt Response § Send Response to Client 3 rd Party Systems Account Services CRM CIF Insurance Core Services Payment Credit Card
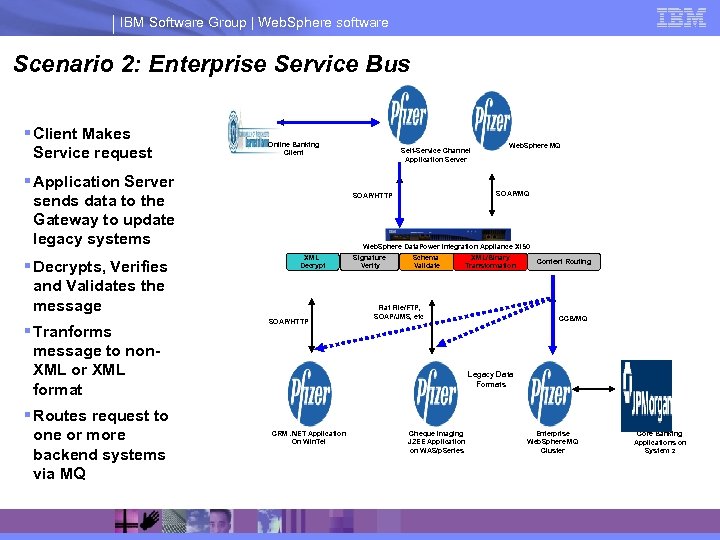 IBM Software Group | Web. Sphere software Scenario 2: Enterprise Service Bus § Client Makes Service request Online Banking Client § Application Server sends data to the Gateway to update legacy systems § Decrypts, Verifies and Validates the message § Tranforms message to non. XML or XML format § Routes request to one or more backend systems via MQ Self-Service Channel Application Server Web. Sphere MQ SOAP/HTTP Web. Sphere Data. Power Integration Appliance XI 50 XML Decrypt SOAP/HTTP Signature Verify Schema Validate XML/Binary Transformation Flat File/FTP, SOAP/JMS, etc Context Routing CCB/MQ Legacy Data Formats CRM. NET Application On Win. Tel Cheque Imaging J 2 EE Application on WAS/p. Series Enterprise Web. Sphere MQ Cluster Core Banking Applications on System z
IBM Software Group | Web. Sphere software Scenario 2: Enterprise Service Bus § Client Makes Service request Online Banking Client § Application Server sends data to the Gateway to update legacy systems § Decrypts, Verifies and Validates the message § Tranforms message to non. XML or XML format § Routes request to one or more backend systems via MQ Self-Service Channel Application Server Web. Sphere MQ SOAP/HTTP Web. Sphere Data. Power Integration Appliance XI 50 XML Decrypt SOAP/HTTP Signature Verify Schema Validate XML/Binary Transformation Flat File/FTP, SOAP/JMS, etc Context Routing CCB/MQ Legacy Data Formats CRM. NET Application On Win. Tel Cheque Imaging J 2 EE Application on WAS/p. Series Enterprise Web. Sphere MQ Cluster Core Banking Applications on System z
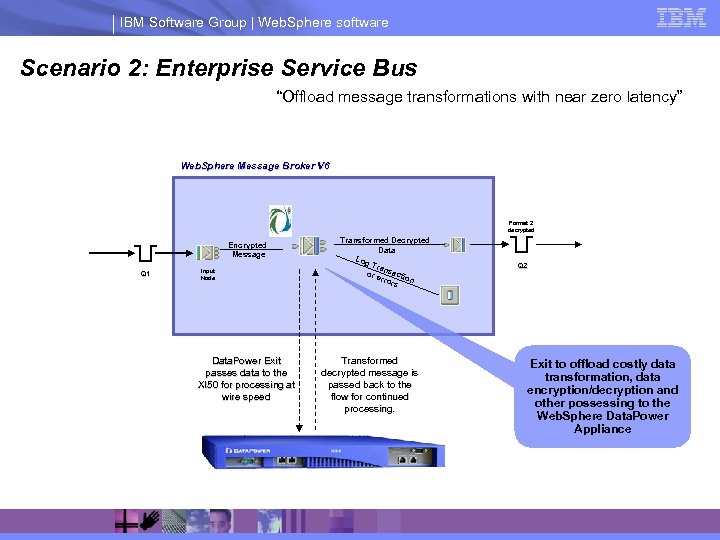 IBM Software Group | Web. Sphere software Scenario 2: Enterprise Service Bus “Offload message transformations with near zero latency” Web. Sphere Message Broker V 6 Format 2 decrypted Encrypted Message Q 1 Input Node Data. Power Exit passes data to the XI 50 for processing at wire speed Transformed Decrypted Data Log Tra n or e sacti rror on s Transformed decrypted message is passed back to the flow for continued processing. Q 2 Exit to offload costly data transformation, data encryption/decryption and other possessing to the Web. Sphere Data. Power Appliance
IBM Software Group | Web. Sphere software Scenario 2: Enterprise Service Bus “Offload message transformations with near zero latency” Web. Sphere Message Broker V 6 Format 2 decrypted Encrypted Message Q 1 Input Node Data. Power Exit passes data to the XI 50 for processing at wire speed Transformed Decrypted Data Log Tra n or e sacti rror on s Transformed decrypted message is passed back to the flow for continued processing. Q 2 Exit to offload costly data transformation, data encryption/decryption and other possessing to the Web. Sphere Data. Power Appliance
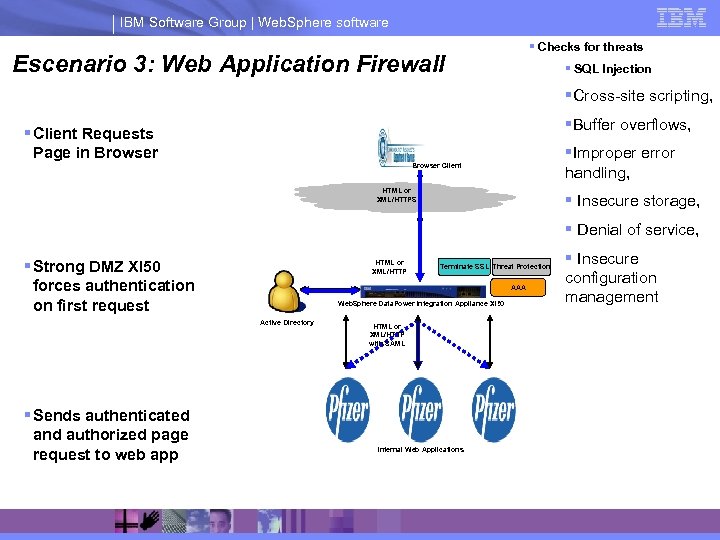 IBM Software Group | Web. Sphere software § Checks for threats Escenario 3: Web Application Firewall § SQL Injection §Cross-site scripting, §Buffer overflows, § Client Requests Page in Browser §Improper error handling, Browser Client HTML or XML/HTTPS § Insecure storage, § Denial of service, § Strong DMZ XI 50 forces authentication on first request HTML or XML/HTTP AAA Web. Sphere Data. Power Integration Appliance XI 50 Active Directory § Sends authenticated and authorized page request to web app Terminate SSL Threat Protection HTML or XML/HTTP with SAML Internal Web Applications § Insecure configuration management
IBM Software Group | Web. Sphere software § Checks for threats Escenario 3: Web Application Firewall § SQL Injection §Cross-site scripting, §Buffer overflows, § Client Requests Page in Browser §Improper error handling, Browser Client HTML or XML/HTTPS § Insecure storage, § Denial of service, § Strong DMZ XI 50 forces authentication on first request HTML or XML/HTTP AAA Web. Sphere Data. Power Integration Appliance XI 50 Active Directory § Sends authenticated and authorized page request to web app Terminate SSL Threat Protection HTML or XML/HTTP with SAML Internal Web Applications § Insecure configuration management
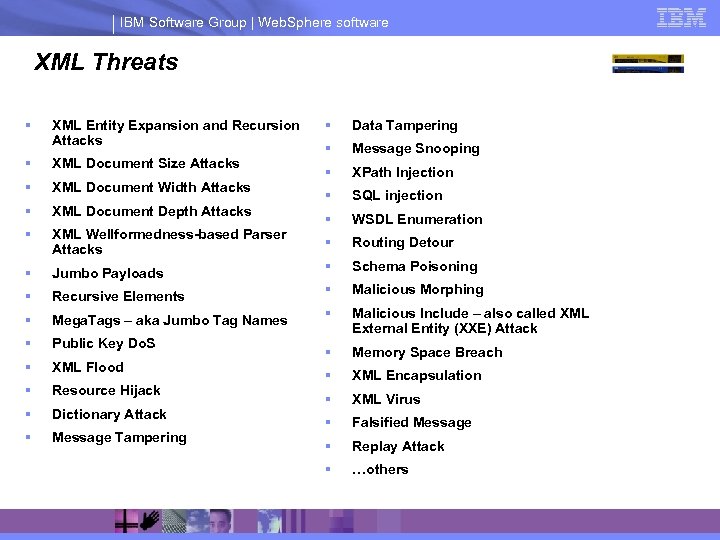 IBM Software Group | Web. Sphere software XML Threats § XML Entity Expansion and Recursion Attacks § Data Tampering § Message Snooping § XPath Injection § SQL injection § WSDL Enumeration § Routing Detour § XML Document Size Attacks § XML Document Width Attacks § XML Document Depth Attacks § XML Wellformedness-based Parser Attacks § Jumbo Payloads § Schema Poisoning § Recursive Elements § Malicious Morphing § Mega. Tags – aka Jumbo Tag Names § § Public Key Do. S Malicious Include – also called XML External Entity (XXE) Attack § XML Flood § Memory Space Breach § Resource Hijack § XML Encapsulation § Dictionary Attack § XML Virus § Message Tampering § Falsified Message § Replay Attack § …others
IBM Software Group | Web. Sphere software XML Threats § XML Entity Expansion and Recursion Attacks § Data Tampering § Message Snooping § XPath Injection § SQL injection § WSDL Enumeration § Routing Detour § XML Document Size Attacks § XML Document Width Attacks § XML Document Depth Attacks § XML Wellformedness-based Parser Attacks § Jumbo Payloads § Schema Poisoning § Recursive Elements § Malicious Morphing § Mega. Tags – aka Jumbo Tag Names § § Public Key Do. S Malicious Include – also called XML External Entity (XXE) Attack § XML Flood § Memory Space Breach § Resource Hijack § XML Encapsulation § Dictionary Attack § XML Virus § Message Tampering § Falsified Message § Replay Attack § …others
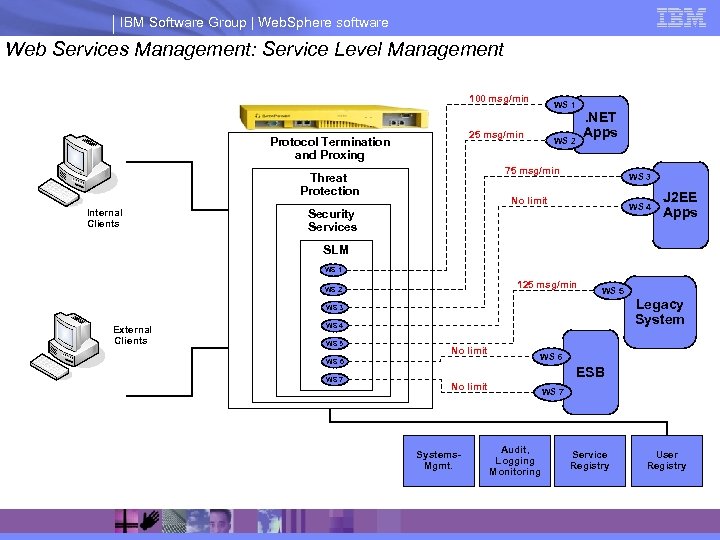 IBM Software Group | Web. Sphere software Web Services Management: Service Level Management 100 msg/min 25 msg/min Protocol Termination and Proxing . NET Apps WS 2 75 msg/min Threat Protection Internal Clients WS 1 WS 3 No limit WS 4 Security Services J 2 EE Apps SLM WS 1 125 msg/min WS 2 WS 5 Legacy System WS 3 External Clients WS 4 WS 5 No limit WS 6 WS 7 WS 6 ESB No limit Systems. Mgmt. WS 7 Audit, Logging Monitoring Service Registry User Registry
IBM Software Group | Web. Sphere software Web Services Management: Service Level Management 100 msg/min 25 msg/min Protocol Termination and Proxing . NET Apps WS 2 75 msg/min Threat Protection Internal Clients WS 1 WS 3 No limit WS 4 Security Services J 2 EE Apps SLM WS 1 125 msg/min WS 2 WS 5 Legacy System WS 3 External Clients WS 4 WS 5 No limit WS 6 WS 7 WS 6 ESB No limit Systems. Mgmt. WS 7 Audit, Logging Monitoring Service Registry User Registry
 ® Data. Power Deployment Models © 2007 IBM Corporation
® Data. Power Deployment Models © 2007 IBM Corporation
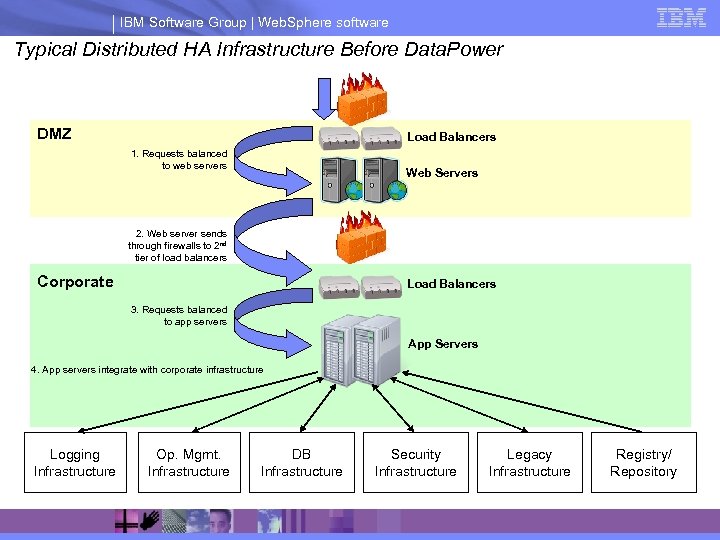 IBM Software Group | Web. Sphere software Typical Distributed HA Infrastructure Before Data. Power DMZ Load Balancers 1. Requests balanced to web servers Web Servers 2. Web server sends through firewalls to 2 nd tier of load balancers Corporate Load Balancers 3. Requests balanced to app servers App Servers 4. App servers integrate with corporate infrastructure Logging Infrastructure Op. Mgmt. Infrastructure DB Infrastructure Security Infrastructure Legacy Infrastructure Registry/ Repository
IBM Software Group | Web. Sphere software Typical Distributed HA Infrastructure Before Data. Power DMZ Load Balancers 1. Requests balanced to web servers Web Servers 2. Web server sends through firewalls to 2 nd tier of load balancers Corporate Load Balancers 3. Requests balanced to app servers App Servers 4. App servers integrate with corporate infrastructure Logging Infrastructure Op. Mgmt. Infrastructure DB Infrastructure Security Infrastructure Legacy Infrastructure Registry/ Repository
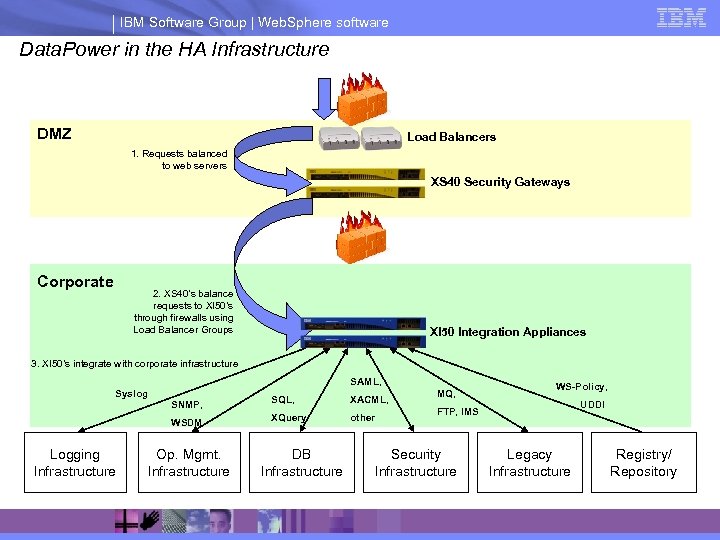 IBM Software Group | Web. Sphere software Data. Power in the HA Infrastructure DMZ Load Balancers 1. Requests balanced to web servers XS 40 Security Gateways Corporate 2. XS 40’s balance requests to XI 50’s through firewalls using Load Balancer Groups XI 50 Integration Appliances 3. XI 50’s integrate with corporate infrastructure SAML, Syslog XACML, WSDM Logging Infrastructure SNMP, SQL, XQuery other Op. Mgmt. Infrastructure DB Infrastructure MQ, WS-Policy, UDDI FTP, IMS Security Infrastructure Legacy Infrastructure Registry/ Repository
IBM Software Group | Web. Sphere software Data. Power in the HA Infrastructure DMZ Load Balancers 1. Requests balanced to web servers XS 40 Security Gateways Corporate 2. XS 40’s balance requests to XI 50’s through firewalls using Load Balancer Groups XI 50 Integration Appliances 3. XI 50’s integrate with corporate infrastructure SAML, Syslog XACML, WSDM Logging Infrastructure SNMP, SQL, XQuery other Op. Mgmt. Infrastructure DB Infrastructure MQ, WS-Policy, UDDI FTP, IMS Security Infrastructure Legacy Infrastructure Registry/ Repository
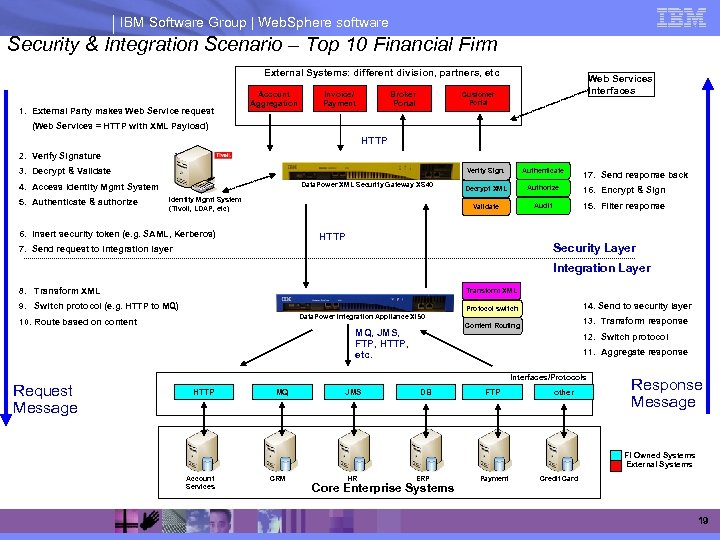 IBM Software Group | Web. Sphere software Security & Integration Scenario – Top 10 Financial Firm External Systems: different division, partners, etc 1. External Party makes Web Service request Account Aggregation Invoice/ Payment Broker Portal Web Services Interfaces Customer Portal (Web Services = HTTP with XML Payload) HTTP 2. Verify Signature 3. Decrypt & Validate Verify Sign. 4. Access Identity Mgmt System 5. Authenticate & authorize Identity Mgmt System (Tivoli, LDAP, etc) 6. Insert security token (e. g. SAML, Kerberos) Authenticate Decrypt XML Authorize 16. Encrypt & Sign Validate Data. Power XML Security Gateway XS 40 Audit 15. Filter response HTTP 17. Send response back Security Layer 7. Send request to integration layer Integration Layer 8. Transform XML Protocol switch 13. Transform response Data. Power Integration Appliance XI 50 10. Route based on content MQ, JMS, FTP, HTTP, etc. Request Message 14. Send to security layer Content Routing 9. Switch protocol (e. g. HTTP to MQ) 12. Switch protocol 11. Aggregate response Interfaces/Protocols HTTP MQ JMS DB FTP other Response Message FI Owned Systems External Systems Account Services CRM HR ERP Core Enterprise Systems Payment Credit Card 19
IBM Software Group | Web. Sphere software Security & Integration Scenario – Top 10 Financial Firm External Systems: different division, partners, etc 1. External Party makes Web Service request Account Aggregation Invoice/ Payment Broker Portal Web Services Interfaces Customer Portal (Web Services = HTTP with XML Payload) HTTP 2. Verify Signature 3. Decrypt & Validate Verify Sign. 4. Access Identity Mgmt System 5. Authenticate & authorize Identity Mgmt System (Tivoli, LDAP, etc) 6. Insert security token (e. g. SAML, Kerberos) Authenticate Decrypt XML Authorize 16. Encrypt & Sign Validate Data. Power XML Security Gateway XS 40 Audit 15. Filter response HTTP 17. Send response back Security Layer 7. Send request to integration layer Integration Layer 8. Transform XML Protocol switch 13. Transform response Data. Power Integration Appliance XI 50 10. Route based on content MQ, JMS, FTP, HTTP, etc. Request Message 14. Send to security layer Content Routing 9. Switch protocol (e. g. HTTP to MQ) 12. Switch protocol 11. Aggregate response Interfaces/Protocols HTTP MQ JMS DB FTP other Response Message FI Owned Systems External Systems Account Services CRM HR ERP Core Enterprise Systems Payment Credit Card 19
 ® Leveraging Data. Power Appliances for PCI Compliance © 2007 IBM Corporation
® Leveraging Data. Power Appliances for PCI Compliance © 2007 IBM Corporation
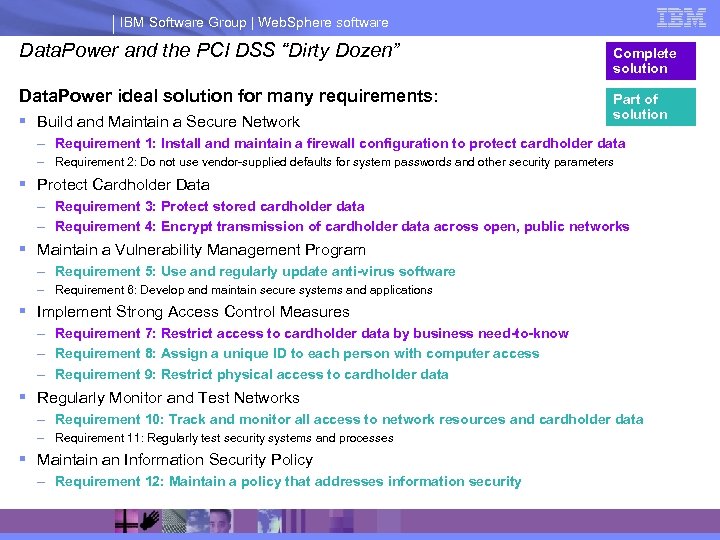 IBM Software Group | Web. Sphere software Data. Power and the PCI DSS “Dirty Dozen” Complete solution Data. Power ideal solution for many requirements: Part of solution § Build and Maintain a Secure Network – Requirement 1: Install and maintain a firewall configuration to protect cardholder data – Requirement 2: Do not use vendor-supplied defaults for system passwords and other security parameters § Protect Cardholder Data – Requirement 3: Protect stored cardholder data – Requirement 4: Encrypt transmission of cardholder data across open, public networks § Maintain a Vulnerability Management Program – Requirement 5: Use and regularly update anti-virus software – Requirement 6: Develop and maintain secure systems and applications § Implement Strong Access Control Measures – Requirement 7: Restrict access to cardholder data by business need-to-know – Requirement 8: Assign a unique ID to each person with computer access – Requirement 9: Restrict physical access to cardholder data § Regularly Monitor and Test Networks – Requirement 10: Track and monitor all access to network resources and cardholder data – Requirement 11: Regularly test security systems and processes § Maintain an Information Security Policy – Requirement 12: Maintain a policy that addresses information security
IBM Software Group | Web. Sphere software Data. Power and the PCI DSS “Dirty Dozen” Complete solution Data. Power ideal solution for many requirements: Part of solution § Build and Maintain a Secure Network – Requirement 1: Install and maintain a firewall configuration to protect cardholder data – Requirement 2: Do not use vendor-supplied defaults for system passwords and other security parameters § Protect Cardholder Data – Requirement 3: Protect stored cardholder data – Requirement 4: Encrypt transmission of cardholder data across open, public networks § Maintain a Vulnerability Management Program – Requirement 5: Use and regularly update anti-virus software – Requirement 6: Develop and maintain secure systems and applications § Implement Strong Access Control Measures – Requirement 7: Restrict access to cardholder data by business need-to-know – Requirement 8: Assign a unique ID to each person with computer access – Requirement 9: Restrict physical access to cardholder data § Regularly Monitor and Test Networks – Requirement 10: Track and monitor all access to network resources and cardholder data – Requirement 11: Regularly test security systems and processes § Maintain an Information Security Policy – Requirement 12: Maintain a policy that addresses information security
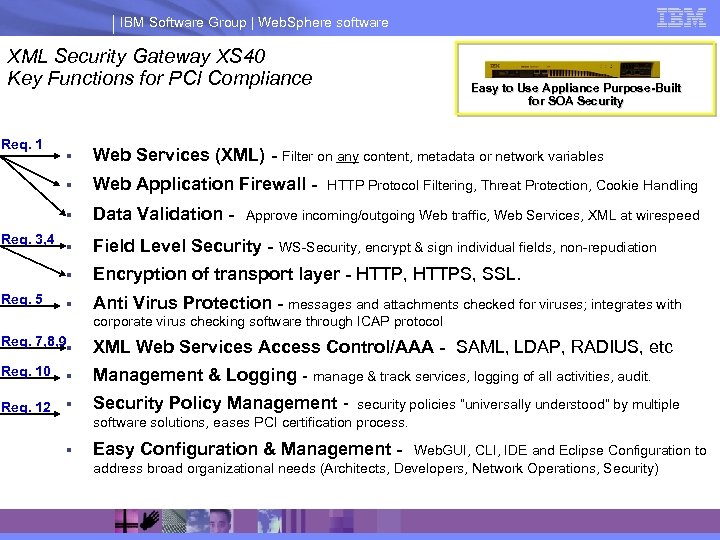 IBM Software Group | Web. Sphere software XML Security Gateway XS 40 Key Functions for PCI Compliance Req. 1 Easy to Use Appliance Purpose-Built for SOA Security Web Application Firewall - § Data Validation - § Field Level Security - § Req. 5 Web Services (XML) - Filter on any content, metadata or network variables § Req. 3, 4 § Encryption of transport layer - HTTP, HTTPS, SSL. § Anti Virus Protection - messages and attachments checked for viruses; integrates with HTTP Protocol Filtering, Threat Protection, Cookie Handling Approve incoming/outgoing Web traffic, Web Services, XML at wirespeed WS-Security, encrypt & sign individual fields, non-repudiation corporate virus checking software through ICAP protocol Req. 7, 8, 9§ XML Web Services Access Control/AAA - SAML, LDAP, RADIUS, etc Req. 10 § Management & Logging - manage & track services, logging of all activities, audit. Req. 12 § Security Policy Management - § Easy Configuration & Management - security policies “universally understood” by multiple software solutions, eases PCI certification process. Web. GUI, CLI, IDE and Eclipse Configuration to address broad organizational needs (Architects, Developers, Network Operations, Security)
IBM Software Group | Web. Sphere software XML Security Gateway XS 40 Key Functions for PCI Compliance Req. 1 Easy to Use Appliance Purpose-Built for SOA Security Web Application Firewall - § Data Validation - § Field Level Security - § Req. 5 Web Services (XML) - Filter on any content, metadata or network variables § Req. 3, 4 § Encryption of transport layer - HTTP, HTTPS, SSL. § Anti Virus Protection - messages and attachments checked for viruses; integrates with HTTP Protocol Filtering, Threat Protection, Cookie Handling Approve incoming/outgoing Web traffic, Web Services, XML at wirespeed WS-Security, encrypt & sign individual fields, non-repudiation corporate virus checking software through ICAP protocol Req. 7, 8, 9§ XML Web Services Access Control/AAA - SAML, LDAP, RADIUS, etc Req. 10 § Management & Logging - manage & track services, logging of all activities, audit. Req. 12 § Security Policy Management - § Easy Configuration & Management - security policies “universally understood” by multiple software solutions, eases PCI certification process. Web. GUI, CLI, IDE and Eclipse Configuration to address broad organizational needs (Architects, Developers, Network Operations, Security)
 ® Data. Power Configuration © 2007 IBM Corporation
® Data. Power Configuration © 2007 IBM Corporation
 IBM Software Group | Web. Sphere software Configuration Driven, NO Programming
IBM Software Group | Web. Sphere software Configuration Driven, NO Programming
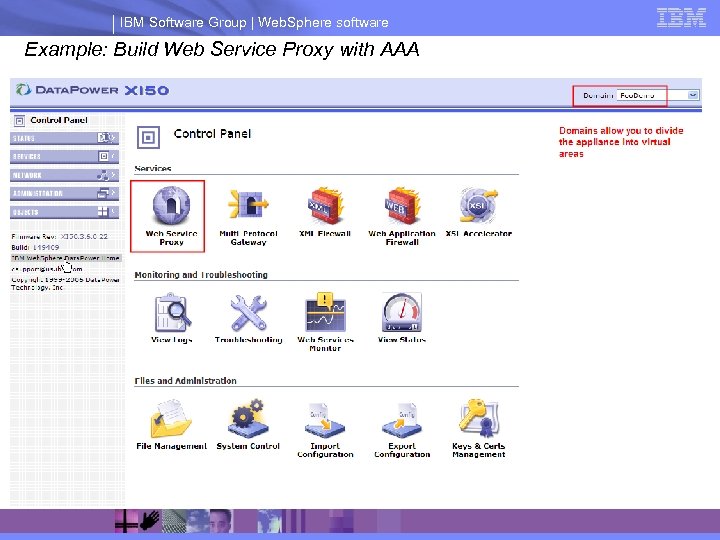 IBM Software Group | Web. Sphere software Example: Build Web Service Proxy with AAA
IBM Software Group | Web. Sphere software Example: Build Web Service Proxy with AAA
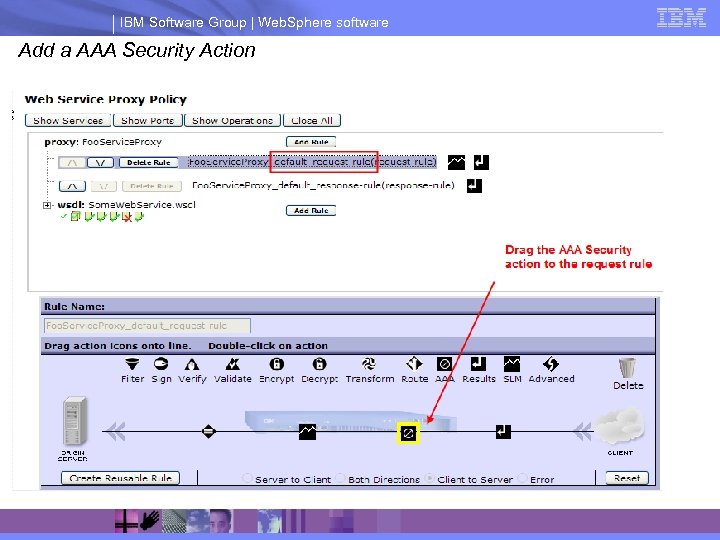 IBM Software Group | Web. Sphere software Add a AAA Security Action
IBM Software Group | Web. Sphere software Add a AAA Security Action
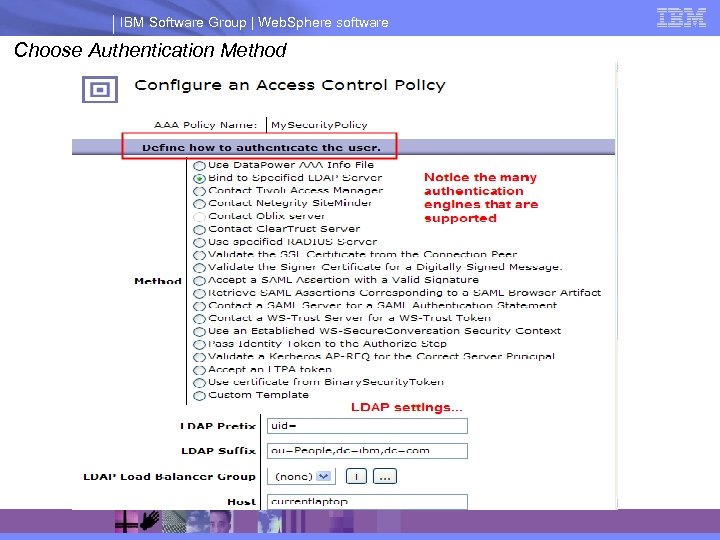 IBM Software Group | Web. Sphere software Choose Authentication Method
IBM Software Group | Web. Sphere software Choose Authentication Method
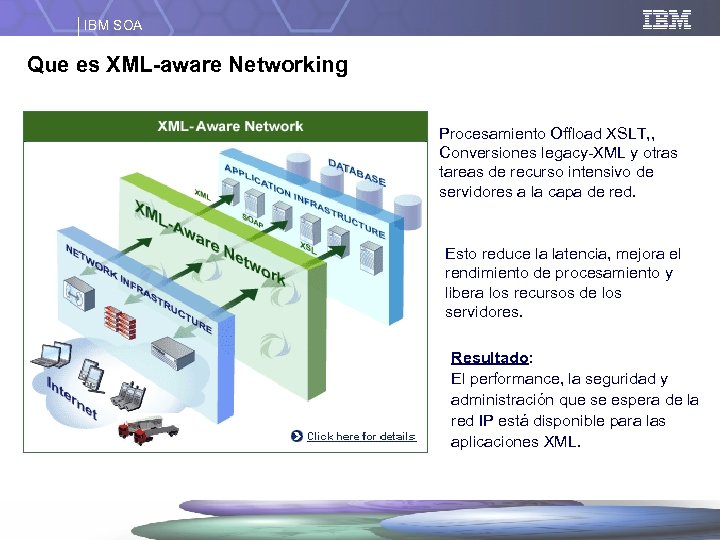 IBM SOA Que es XML-aware Networking Procesamiento Offload XSLT, , Conversiones legacy-XML y otras tareas de recurso intensivo de servidores a la capa de red. Esto reduce la latencia, mejora el rendimiento de procesamiento y libera los recursos de los servidores. Resultado: El performance, la seguridad y administración que se espera de la red IP está disponible para las aplicaciones XML.
IBM SOA Que es XML-aware Networking Procesamiento Offload XSLT, , Conversiones legacy-XML y otras tareas de recurso intensivo de servidores a la capa de red. Esto reduce la latencia, mejora el rendimiento de procesamiento y libera los recursos de los servidores. Resultado: El performance, la seguridad y administración que se espera de la red IP está disponible para las aplicaciones XML.
 IBM SOA a division of Mc. Graw-Hill
IBM SOA a division of Mc. Graw-Hill
 IBM SOA Clientes en Latinoamerica
IBM SOA Clientes en Latinoamerica
 ® Muchas Gracias! © 2007 IBM Corporation
® Muchas Gracias! © 2007 IBM Corporation


