30566a6a68044f698b978e8f72628632.ppt
- Количество слайдов: 56

Data Networks Second Edition Dimitri Bertsekas / Robert Gallager
Chapter 1 Introduction and Layered Network Architecture

Section 1. 1 Historical Overview
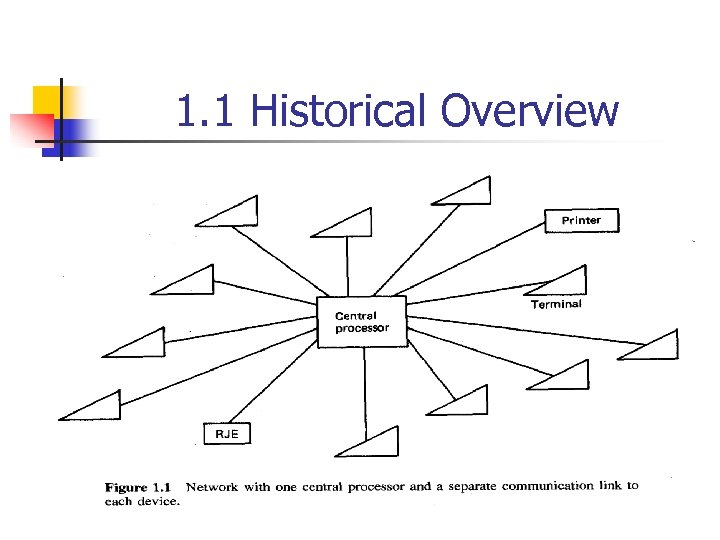
1. 1 Historical Overview
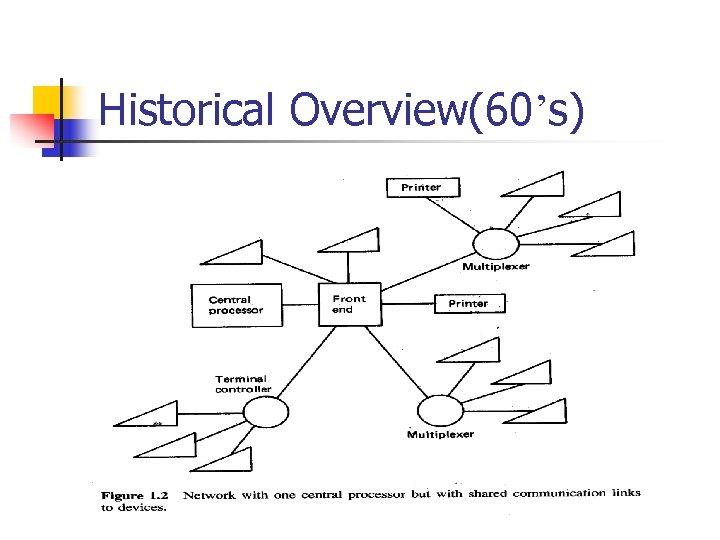
Historical Overview(60’s)
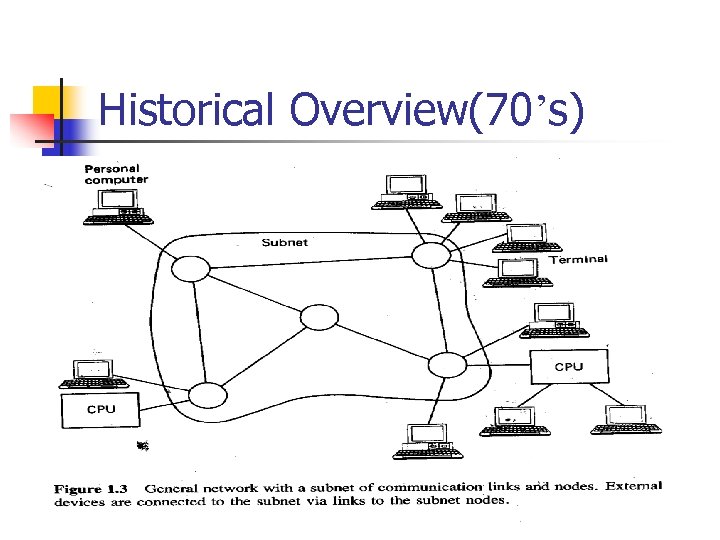
Historical Overview(70’s)
Historical Overview(70’s) n Inside subnet, nodes & communication links. n n n IMP(Interface message processors) : to route message through subnets. – called also switches. wide area network local area network
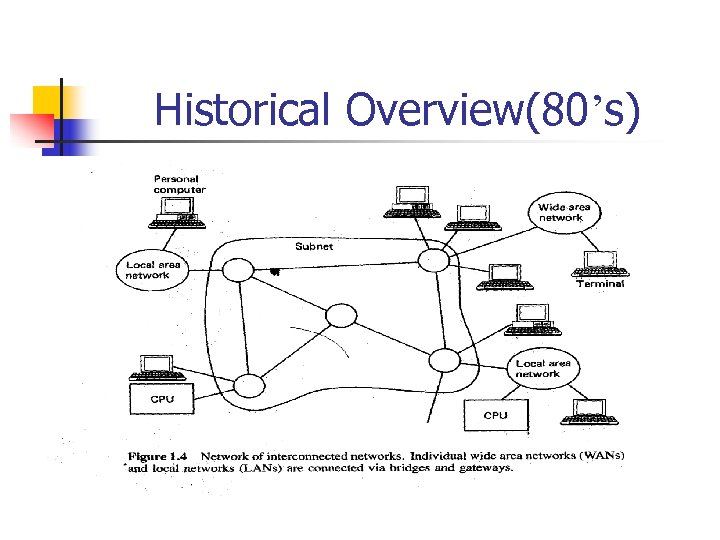
Historical Overview(80’s)

Historical Overview(80’s) n n 1980‘s, more and more networks connected via gateways and bridges Each subnet has its own conventions and control algorithms (protocols) for handling data – gateways and bridges must deal with this inhomogeneity.

Historical Overview n In the future, data network, voice networks, cable networks will be integrated more. n n ISDN(integrated services digital network) Broadband ISDN : greater data rates.

Section 1. 2 Messages and Switching

1. 2. 1 Messages and Packets n message: n n n Airline reservation system : data, flight no# … Email : document File system : file Image transmission system : image …

1. 2. 1 Messages and Packets n n n A message is usually a string of binary symbols, 0 or 1 (bit). Sender → message → recipient compression Compression can reduce expected length of representation.

Messages and Packets n n Control overhead : ensure reliable communication route control congestion, etc. Usually broken into shorter bit strings(packets) ※ transmit long messages is harmful , (e. g. delay, buffer management, congestion control)

1. 2. 2 Sessions n In larger transaction : a message sequence is called a session. n Requires many messages over a considerable time period. n n n Setup procedure(similar to setting up a call) A connection In other networks, no such setup is required. Each message is treated independently → connectionless

Sessions n Messages within a session are triggered by events. n n n Message initiation times are arbitrary, unpredictable. Model messages / packets arrival for a given session as a random process. Poisson process On/Off flow model Application are rapidly changing → model complex

Sessions n Detailed characteristics for applications. 1. 2. 3. 4. Message arrival rate and variability of arrivals. Session holding time. Expected message length and length distribution. Allowable delay : 10 ms ~ 1 ms

Sessions 5. 6. Reliability : error-free 、 occasional loss. Message and packet ordering e. g. file transfer : message arrival rate : 10 w delay requirement : relaxed reliability : high
1. 2. 3 Circuit Switching and Store-and-Forward Switching n Circuit switching n n n Inefficient utilization When a session s is initialed, allocated a given transmission rate rs (bits per second) A path is created from transmitting site through the subnet to destination site.
Circuit switching n Each communication link on this path allocates a portion of rs of its total transmission capacity. (done by TDM or FDM multiplexing) n n n Note : sum of rates for all sessions cannot exceed total capacity of links, otherwise, new session is rejected. Guaranteed transmission rate rs similar to telephone network. But, in a data network, required transmission rates are different and vary over a wide range
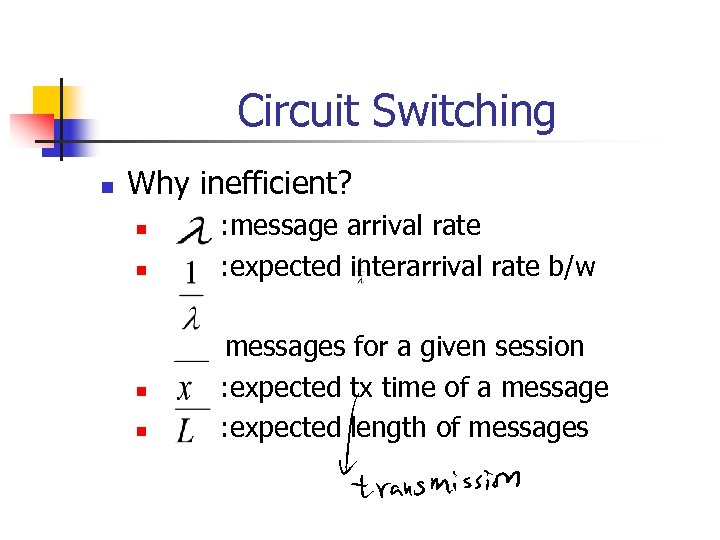
Circuit Switching n Why inefficient? n n : message arrival rate : expected interarrival rate b/w messages for a given session : expected tx time of a message : expected length of messages
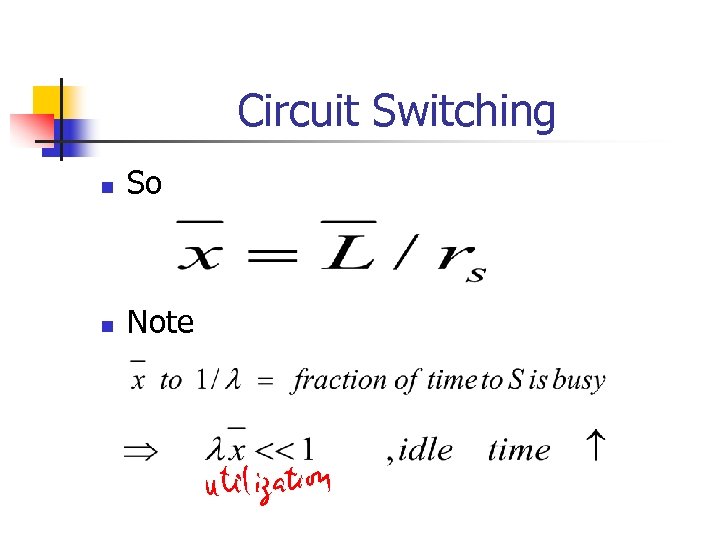
Circuit Switching n So n Note
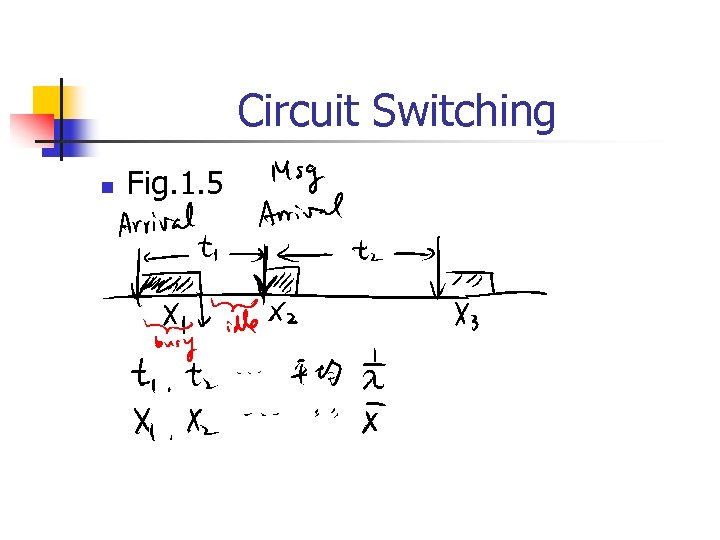
Circuit Switching n Fig. 1. 5
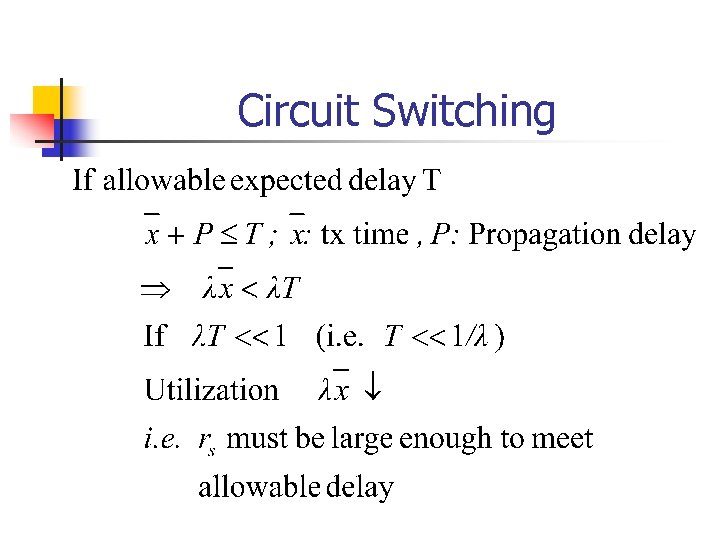
Circuit Switching
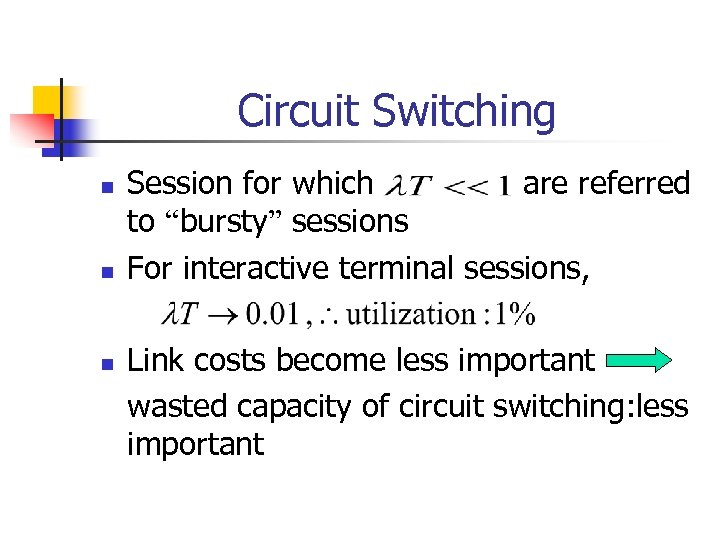
Circuit Switching n n n Session for which are referred to “bursty” sessions For interactive terminal sessions, Link costs become less important wasted capacity of circuit switching: less important
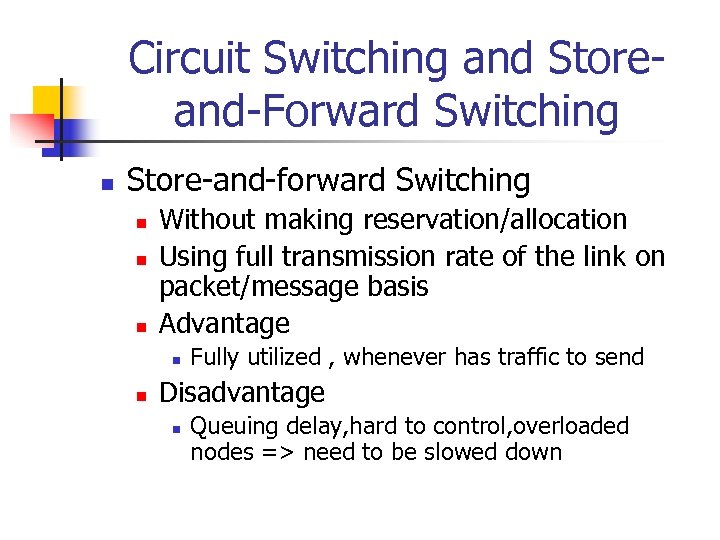
Circuit Switching and Storeand-Forward Switching n Store-and-forward Switching n n n Without making reservation/allocation Using full transmission rate of the link on packet/message basis Advantage n n Fully utilized , whenever has traffic to send Disadvantage n Queuing delay, hard to control, overloaded nodes => need to be slowed down

Store-and-Forward Switching n Message Switching n n Store-and-forwarding, messages basis Packet Switching n Store-and-forwarding, packets basis
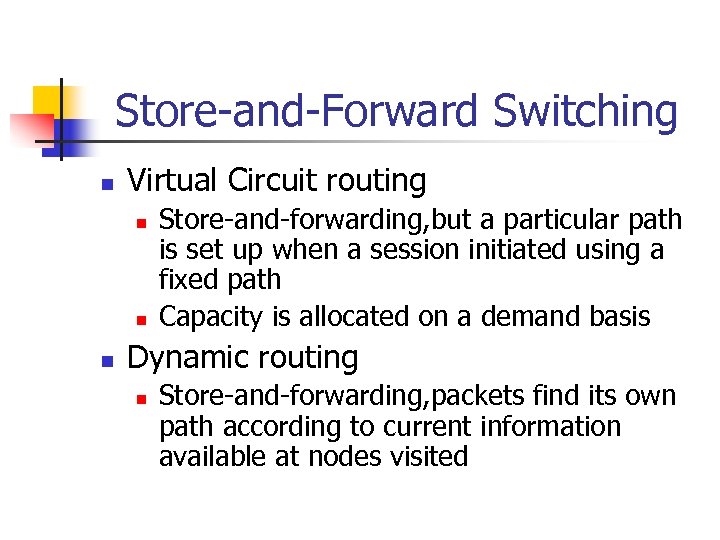
Store-and-Forward Switching n Virtual Circuit routing n n n Store-and-forwarding, but a particular path is set up when a session initiated using a fixed path Capacity is allocated on a demand basis Dynamic routing n Store-and-forwarding, packets find its own path according to current information available at nodes visited
Section 1. 3 Layering
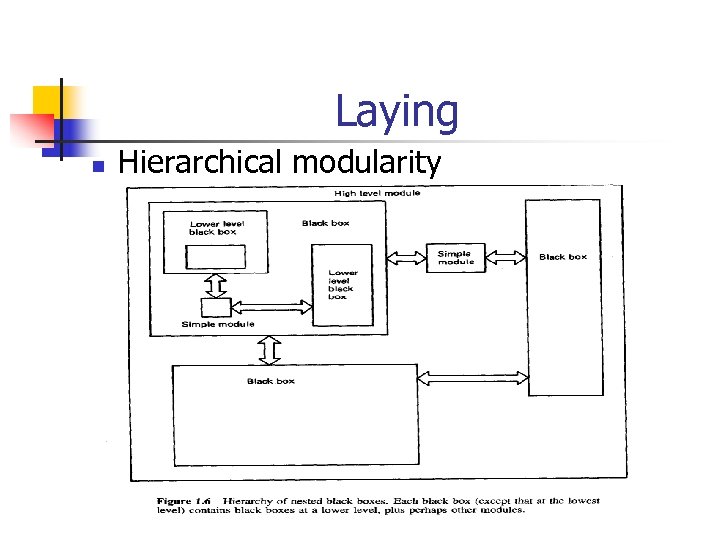
Laying n Hierarchical modularity
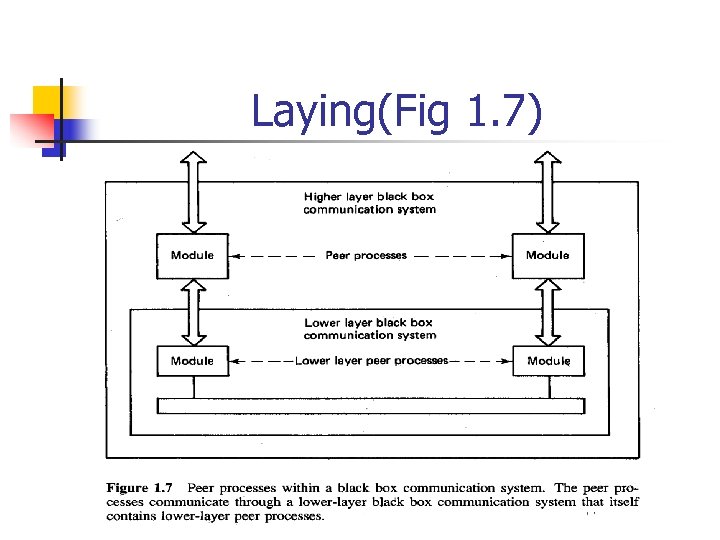
Laying(Fig 1. 7)

Laying n OSI(Open System Interconnection) model by ISO(International Standards Organization)
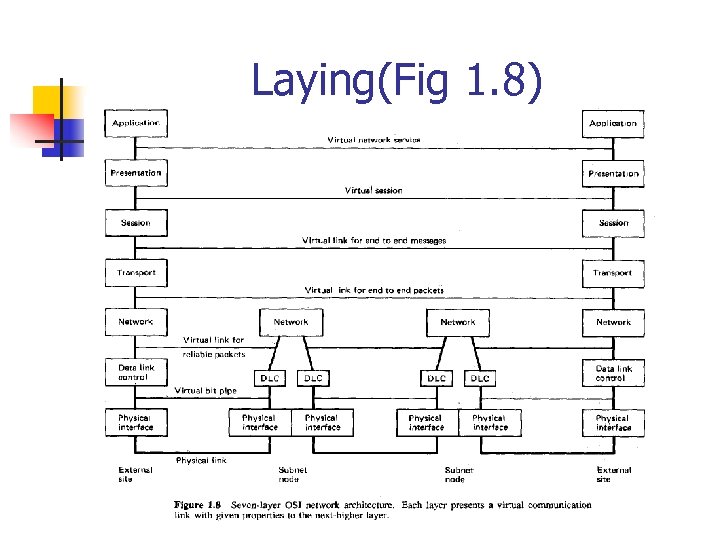
Laying(Fig 1. 8)
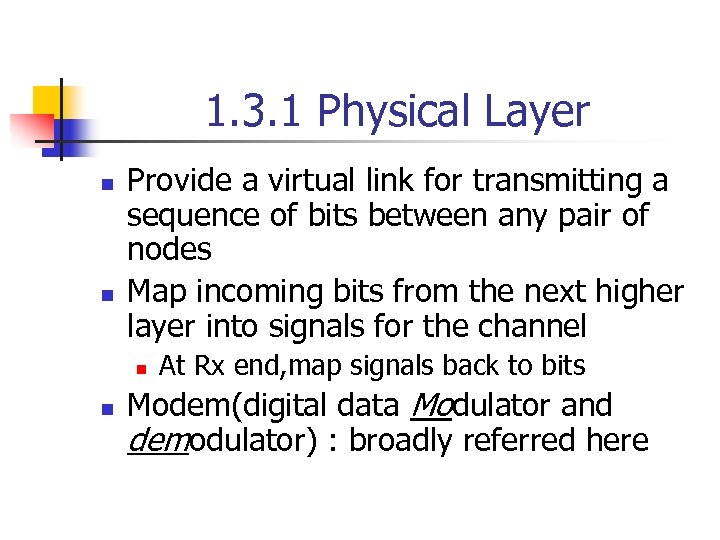
1. 3. 1 Physical Layer n n Provide a virtual link for transmitting a sequence of bits between any pair of nodes Map incoming bits from the next higher layer into signals for the channel n n At Rx end, map signals back to bits Modem(digital data Modulator and demodulator) : broadly referred here
Physical Layer n compare n Synchronous bit pipe n n Intermittent synchronous bit pipe n n 1 bit per t second DLC module supplies bits at a synchronous rate when has data Asynchronous characters n Map into fixed-length bit strings and transmitted asynchronously as they are generated
Physical Layer n Interface between DLC n n n Module on one end might be temporarily inoperable Some initialization is required For synchronous operation , must provide timing
Physical Layer n RS-232 -C & physical layer of X. 21 n n DCE: Data Communication Equipment DTE: Data Terminal Equipment DTE sends a signal to DCE “request-tosend”. DCE replies with “clear-to-send” The interchange is a very simple example of a protocol or distributed algorithm
1. 3. 2 Data Link Control (DLC) Layer n n To convert unreliable bit pipe at layer 1 into higher-layer Sending packets asynchronously but errorfree n n n Variable delay b/w packet into DLC exit from the other end Need to correct errors Overhead control bits n n Header trailer
Data Link Control (DLC) Layer n n n Some request retransmissions when error occur For some LAN, multi-access may take place. The signal received is a function of the signals from a multiplicity of transmitting nodes
MAC(Medium Access Control) Sublayer n n Considered as lower sublayer of layer 2 Allocate multi-access channel , so that each node can successfully transmit its frame without interference from other nodes
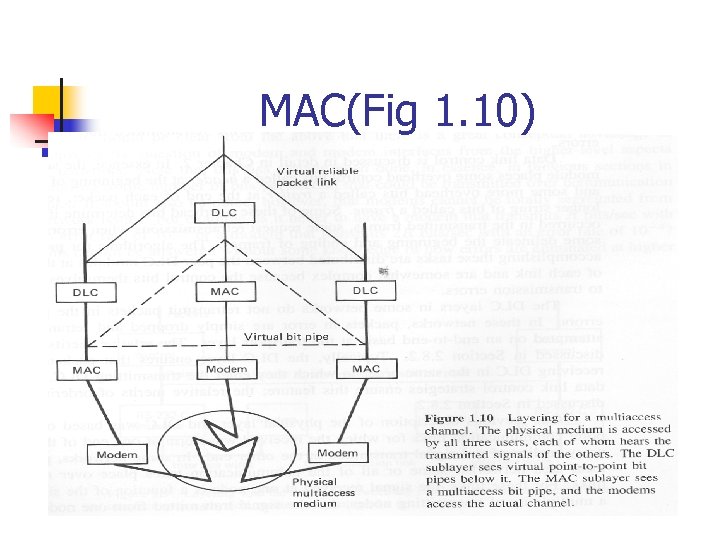
MAC(Fig 1. 10)
1. 3. 3 Network Layer n n n Implementing routing and flow control for its network Use packet header along with stored information to accomplish these functions Transport layer also provides additional information as a set of parameters in accordance with interface protocol
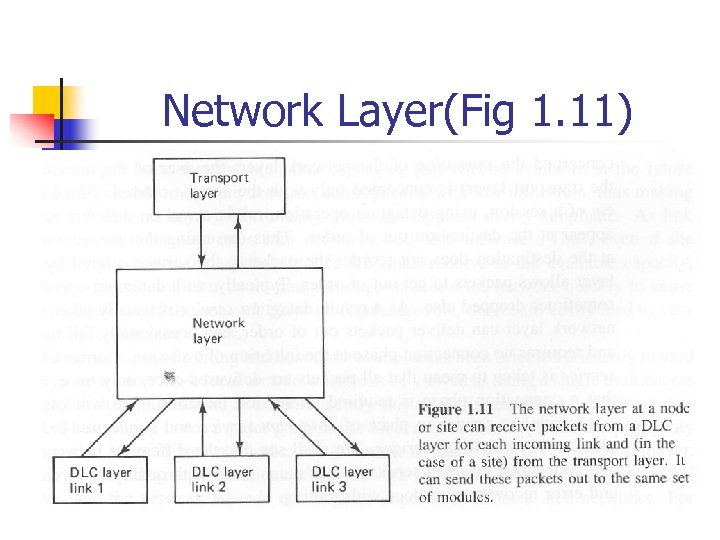
Network Layer(Fig 1. 11)
Network Layer n n Along with transmit packets from lower layer and new packets from higher layer, the network layer generates its own control packets For virtual circuit routing n n Select a route when VC being generated(distributed way or by source node) Ensure each packet of the session follows the assigned route(by placing enough information in the header)
Network Layer n n For datagram network, each packet is routed individually Service offered n Using VC n n Packet in order, connection - oriented Using datagram n Packets out of order, connectionless service
Network Layer n Flow control n n Congestion control n n Avoid sending data too fast Avoid congestion within subnet Solution n Good route Good buffer management Control flow of packet into network s. t. congestion control
Network Layer n Connection – oriented service n n Possible to negotiate => guarantee service at setup Connectionless service n No opportunity for negotiate
Network Layer n n High link capacities in the future will make it possible to operate network economically with low utilization and make flow control unnecessary Unfortunately, as link capacity increase, access rate into networks also increase n e. g. malfunctioning user could dump enough data into network quickly to cause congestion => still need some regulatry rule
Network Layer n Routing & flow control n n Primarily for WAN For LAN , routing is not a major problem, congestion is possible n n n Could be dealt with in MAC sublayer Major functions of network layer are accomplished in MAC sublayer. Thus, connectionless service is common here.

Network Layer n Note n n Network layer delivering every packet may be reliable or might be unreliable. The higher layer might have to recover errors
Internet Sublayer n To connect different subnetworks together n n Solution: create a new sublayer: internet sublayer top part of network layer A gateway connecting two subnets will interface Internet modules also : routing & flow control Note n Bridges interface at DLC layer. For LAN , routing & flow control are done in MAC.
1. 3. 4 Transport layer n n n Break messages into packets , and reassembles packets Might multiplex several low-rate sessions all from same source and going to same destination Might split one high-rate session into multiple sessions(flow control) If network layer is unreliable, achieve reliable end-to-end connection End-to-end flow control

1. 3. 5 Session layer n n n Provide transport layer with information needed to establish the session Achieve load sharing b/w many processors Access rights in setting up sessions Who pay for the service Handle interaction b/w 2 end points
1. 3. 6 Presentation layer n n n Data encryption Data compression Code conversion
1. 3. 7 Application layer n n Consideration variation in service offered by various layers Sometimes , not conform to OSI model n e. g. ATM ( Asynchronous Transfer Mode ) , broadband ISDN
Section 1. 4 A Simple Distributed Algorithm problem
30566a6a68044f698b978e8f72628632.ppt