bbc7baaf7e2b3bf9e1ace7ad5dbfe0bf.ppt
- Количество слайдов: 102
 Data Loss – Prevention and Controls Mark Lachniet, Solutions Architect – Analysts International Bret Straffon, PSS Security – Cisco Systems Lansing, MI July 15 th, 2008
Data Loss – Prevention and Controls Mark Lachniet, Solutions Architect – Analysts International Bret Straffon, PSS Security – Cisco Systems Lansing, MI July 15 th, 2008
 Presentation Overview • This presentation will provide an overview of issues surrounding Data Loss Prevention (DLP) and provide a roadmap for understanding: – – How it impacts YOUR organization Regulations and standards (e. g. PCI and GLBA) that address it How it is affecting industry and the economy in general Some vendor-agnostic approaches to dealing with data loss and breaches – How Cisco’s product line can help you address DLP concerns in a cost effective and scalable manner – How Analysts International’s expertise and services can help to prevent and recover from incidents • CAVEAT EMPTOR: Many of the topics discussed in this seminar cover legal topics. You should consult your own legal counsel! 2
Presentation Overview • This presentation will provide an overview of issues surrounding Data Loss Prevention (DLP) and provide a roadmap for understanding: – – How it impacts YOUR organization Regulations and standards (e. g. PCI and GLBA) that address it How it is affecting industry and the economy in general Some vendor-agnostic approaches to dealing with data loss and breaches – How Cisco’s product line can help you address DLP concerns in a cost effective and scalable manner – How Analysts International’s expertise and services can help to prevent and recover from incidents • CAVEAT EMPTOR: Many of the topics discussed in this seminar cover legal topics. You should consult your own legal counsel! 2
 Introductions – Mark Lachniet • • • Mark Lachniet from Analysts International Solutions Architect with Analysts International’s security group With Analysts International for approximately 8 years Previously an I. T. director at a K-12 school district and instructor for Walsh College’s NSA-certified Masters in Information Assurance (MSIA) Program Provide oversight on all security services Perform hands-on work in most areas with a focus on “holistic” security such as policies and procedures, regulatory compliance, Business Continuity Planning, and technical areas such as forensics, incident response, web app security, etc. Member of the International High Technology Crime Investigation Association (HTCIA) GIAC Gold Certified Forensic Analyst (GCFA) Certified Information Systems Security Professional (CISSP) Certified Information Systems Auditor (CISA) 3
Introductions – Mark Lachniet • • • Mark Lachniet from Analysts International Solutions Architect with Analysts International’s security group With Analysts International for approximately 8 years Previously an I. T. director at a K-12 school district and instructor for Walsh College’s NSA-certified Masters in Information Assurance (MSIA) Program Provide oversight on all security services Perform hands-on work in most areas with a focus on “holistic” security such as policies and procedures, regulatory compliance, Business Continuity Planning, and technical areas such as forensics, incident response, web app security, etc. Member of the International High Technology Crime Investigation Association (HTCIA) GIAC Gold Certified Forensic Analyst (GCFA) Certified Information Systems Security Professional (CISSP) Certified Information Systems Auditor (CISA) 3
 Introductions – Bret Straffon • • Bret Straffon, bstraffo@cisco. com Product Sales Specialist – Security Solutions With Cisco for approximately 3 years Prior to Cisco – spent time at Cybertrust, Open Service, Trend Micro, ISS, Deloitte and Touche. • Total of 9 years experience selling Security solutions • BSBA - Management Information System – CMU ‘ 94 4
Introductions – Bret Straffon • • Bret Straffon, bstraffo@cisco. com Product Sales Specialist – Security Solutions With Cisco for approximately 3 years Prior to Cisco – spent time at Cybertrust, Open Service, Trend Micro, ISS, Deloitte and Touche. • Total of 9 years experience selling Security solutions • BSBA - Management Information System – CMU ‘ 94 4
 Agenda 11: 00 am 11: 45 am 12: 05 pm 12: 50 pm 1: 35 pm 1: 55 pm Section 0 &1 (Mark Lachniet) (45 mins) Lunch is distributed (20 mins) Section 2 (Mark Lachniet) (45 mins) Section 3 (Cisco) (45 mins) Section 4 (Mark Lachniet) (20 mins) Q&A (all) (5 minutes or as needed) 5
Agenda 11: 00 am 11: 45 am 12: 05 pm 12: 50 pm 1: 35 pm 1: 55 pm Section 0 &1 (Mark Lachniet) (45 mins) Lunch is distributed (20 mins) Section 2 (Mark Lachniet) (45 mins) Section 3 (Cisco) (45 mins) Section 4 (Mark Lachniet) (20 mins) Q&A (all) (5 minutes or as needed) 5
 Section 1 – Data Loss Overview Mark Lachniet, Solutions Architect – Analysts International Lansing, MI July 15 th, 2008
Section 1 – Data Loss Overview Mark Lachniet, Solutions Architect – Analysts International Lansing, MI July 15 th, 2008
 Overview of Data Loss Prevention • There have been hundreds of significant breaches in the last few years, and public (as well as legislative) attention is now on the problem so it will only get more important over time • Failure to control data leakage has very public and painful ramifications (bad press, plummeting stock prices, fees and penalties, lawsuits, regulatory non-compliance, etc. ) • We must be concerned about controlling our sensitive data throughout its entire life-cycle (from creation to destruction) • History has shown that being “out in front” of, and prepared for, upcoming (and inevitable) trends such as data breach disclosure laws is more cost effective than a late response 7
Overview of Data Loss Prevention • There have been hundreds of significant breaches in the last few years, and public (as well as legislative) attention is now on the problem so it will only get more important over time • Failure to control data leakage has very public and painful ramifications (bad press, plummeting stock prices, fees and penalties, lawsuits, regulatory non-compliance, etc. ) • We must be concerned about controlling our sensitive data throughout its entire life-cycle (from creation to destruction) • History has shown that being “out in front” of, and prepared for, upcoming (and inevitable) trends such as data breach disclosure laws is more cost effective than a late response 7
 Types of Data To Protect • The type of data you need to protect will obviously depend upon your industry, and some are more susceptible than others – Personally Identifiable Information (PII) such as addresses, phone numbers, etc. – Personal Financial Information (PFI) such as account numbers and balances, purchasing history, credit card information – Personal Health Information (PHI), includes personal health records, billing, etc. Covered by the Health Insurance Portability and Accountability Act of 1996 (HIPAA) – Internal secrets (marketing, payroll, passwords, etc) 8
Types of Data To Protect • The type of data you need to protect will obviously depend upon your industry, and some are more susceptible than others – Personally Identifiable Information (PII) such as addresses, phone numbers, etc. – Personal Financial Information (PFI) such as account numbers and balances, purchasing history, credit card information – Personal Health Information (PHI), includes personal health records, billing, etc. Covered by the Health Insurance Portability and Accountability Act of 1996 (HIPAA) – Internal secrets (marketing, payroll, passwords, etc) 8
 The Pain of a Breach • If you have a breach, the impact could be significant, possibly even going out of business – Loss of stakeholder confidence (the public, customers, investors, partners, etc. ) – Lost productivity (inability to work, servers down, people reassigned for clean-up, data recovery costs) – Fees for not meeting Service Level Agreements (e. g. in manufacturing industries) – Costs associated with notification (sending “oops” letters, staffing a toll free information line, providing credit counseling to victims, etc. ) – Internal and external consultant costs – Blackmail and extortion attempts – Submitting to mandatory audits 9
The Pain of a Breach • If you have a breach, the impact could be significant, possibly even going out of business – Loss of stakeholder confidence (the public, customers, investors, partners, etc. ) – Lost productivity (inability to work, servers down, people reassigned for clean-up, data recovery costs) – Fees for not meeting Service Level Agreements (e. g. in manufacturing industries) – Costs associated with notification (sending “oops” letters, staffing a toll free information line, providing credit counseling to victims, etc. ) – Internal and external consultant costs – Blackmail and extortion attempts – Submitting to mandatory audits 9
 The Pain of a Breach – Examples 8 August 2002 Microsoft and FTC Reach Passport Privacy and Security Settlement A Federal Trade Commission (FTC) investigation found that Microsoft misrepresented both the level of security provided and amount of data collected by its Passport services. As part of a settlement with the government, Microsoft will refrain from making false claims about the information it collects and will submit to an independent audit of its security program every two years. Microsoft could face fines of $11, 000 a day if it fails to comply with the agreement. Choice. Point In January 2006, consumer data provider Choice. Point Inc. agreed to pay $15 million to settle FTC charges that its security and record-handling procedures violated consumers' privacy rights when thieves breached its database. 10
The Pain of a Breach – Examples 8 August 2002 Microsoft and FTC Reach Passport Privacy and Security Settlement A Federal Trade Commission (FTC) investigation found that Microsoft misrepresented both the level of security provided and amount of data collected by its Passport services. As part of a settlement with the government, Microsoft will refrain from making false claims about the information it collects and will submit to an independent audit of its security program every two years. Microsoft could face fines of $11, 000 a day if it fails to comply with the agreement. Choice. Point In January 2006, consumer data provider Choice. Point Inc. agreed to pay $15 million to settle FTC charges that its security and record-handling procedures violated consumers' privacy rights when thieves breached its database. 10
 The Pain of a Breach – Examples “T. J. Maxx Parent Company Data Theft Is The Worst Ever” The intrusion hands the retailer the dubious honor of surpassing the 40 million stolen customers record mark, something that only Card. Systems had been able to achieve. TJX later settled Visa's charges against it for $41 million in November 2007, and paid an undisclosed amount to settle a group of lawsuits brought against it by Massachusetts-based banks in December 2007. The FTC ordered TJX to designate an individual responsible for information security, identify risks to personal data, deploy safeguards to mitigate that risk, work out agreements with service providers that handle customer data, and evaluate and adjust its security program to meet operation changes. In addition, TJX must submit to a third-party audit of its security program every two years for the next two decades. 11
The Pain of a Breach – Examples “T. J. Maxx Parent Company Data Theft Is The Worst Ever” The intrusion hands the retailer the dubious honor of surpassing the 40 million stolen customers record mark, something that only Card. Systems had been able to achieve. TJX later settled Visa's charges against it for $41 million in November 2007, and paid an undisclosed amount to settle a group of lawsuits brought against it by Massachusetts-based banks in December 2007. The FTC ordered TJX to designate an individual responsible for information security, identify risks to personal data, deploy safeguards to mitigate that risk, work out agreements with service providers that handle customer data, and evaluate and adjust its security program to meet operation changes. In addition, TJX must submit to a third-party audit of its security program every two years for the next two decades. 11
 The Pain of a Breach – Examples • Egg. Head. com – 3. 7 million customer records were stolen (including mine) – End consumers were covered – we just had to fill out a form for the credit card company, and would have only been liable for $50 max – However, it was necessary for consumers to actually identify and contest the charges – Egghead actually informed customers (this is before this was a common practice) and hence were able to keep some stakeholder confidence – Credit card companies were not happy – they had to re-issue cards and sued egghead for costs – Egghead was apparently forced out of business due to these lawsuits from the credit card companies – Eventually re-branded themselves as newegg. com, a company which I actually purchase from (can lightning strike twice? ) 12
The Pain of a Breach – Examples • Egg. Head. com – 3. 7 million customer records were stolen (including mine) – End consumers were covered – we just had to fill out a form for the credit card company, and would have only been liable for $50 max – However, it was necessary for consumers to actually identify and contest the charges – Egghead actually informed customers (this is before this was a common practice) and hence were able to keep some stakeholder confidence – Credit card companies were not happy – they had to re-issue cards and sued egghead for costs – Egghead was apparently forced out of business due to these lawsuits from the credit card companies – Eventually re-branded themselves as newegg. com, a company which I actually purchase from (can lightning strike twice? ) 12
 Other Penalties for Breaches • In addition, there may be other types of damages for failure to maintain good security and/or alert victims • By law: – In the State of New York, can be fined $10 per instance of failed notification not to exceed $150, 000 – Many other states have similar fines on the books, and more states are passing breach notification laws. See http: //www. csoonline. com/article/221322 for an interactive map – At a federal level, the FTC or SEC may step in • By civil suit: – Choicepoint: $10 million in civil penalties and $5 million in consumer redress to settle Federal Trade Commission charges • Disciplinary action: – Lose job or vacation time – An Ohio Department of Administrative Services employee lost a week of vacation! 13
Other Penalties for Breaches • In addition, there may be other types of damages for failure to maintain good security and/or alert victims • By law: – In the State of New York, can be fined $10 per instance of failed notification not to exceed $150, 000 – Many other states have similar fines on the books, and more states are passing breach notification laws. See http: //www. csoonline. com/article/221322 for an interactive map – At a federal level, the FTC or SEC may step in • By civil suit: – Choicepoint: $10 million in civil penalties and $5 million in consumer redress to settle Federal Trade Commission charges • Disciplinary action: – Lose job or vacation time – An Ohio Department of Administrative Services employee lost a week of vacation! 13
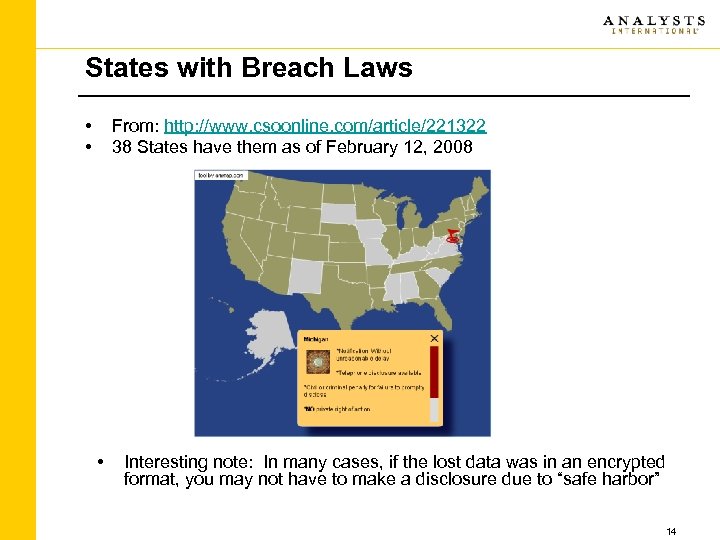 States with Breach Laws • • From: http: //www. csoonline. com/article/221322 38 States have them as of February 12, 2008 • Interesting note: In many cases, if the lost data was in an encrypted format, you may not have to make a disclosure due to “safe harbor” 14
States with Breach Laws • • From: http: //www. csoonline. com/article/221322 38 States have them as of February 12, 2008 • Interesting note: In many cases, if the lost data was in an encrypted format, you may not have to make a disclosure due to “safe harbor” 14
 What Happens to that Lost Data? ? ? • A lot of times, nothing – the tape or laptop was lost or stolen, and never heard of again. No direct impact was known (but they still had to report it) • In some cases, it may be used for identity theft, which is a real problem, but in many cases, it is sold on the black market • Computer crime is now within the domain of organized crime such as the “Russian Business Network” • There is an entire community and hierarchy of traffickers 15
What Happens to that Lost Data? ? ? • A lot of times, nothing – the tape or laptop was lost or stolen, and never heard of again. No direct impact was known (but they still had to report it) • In some cases, it may be used for identity theft, which is a real problem, but in many cases, it is sold on the black market • Computer crime is now within the domain of organized crime such as the “Russian Business Network” • There is an entire community and hierarchy of traffickers 15
 The Lucrative World of Malware and “Bot Herding” • People are making money! Millions of dollars! • There are entire economies based on computer crime: – Hackers: Produce new exploits in common software and sell the “ 0 day” exploits to Bot Herders – Bot Herders: Use the new exploits to distribute malware to end users. These are used for Denial of Service extortion, spamming, stealing network or PII information, click advertisement abuse, etc. They sell their harvested information to criminals. – Criminals: Use their obtained credit card and bank account information to perpetuate financial crimes and pay for further development • Finding ways to identify, control and remove malware (especially unidentified malware) is a boom market • Limiting exposure (for example through good system security and products such as Cisco’s Iron Port appliances) can minimize this risk 16
The Lucrative World of Malware and “Bot Herding” • People are making money! Millions of dollars! • There are entire economies based on computer crime: – Hackers: Produce new exploits in common software and sell the “ 0 day” exploits to Bot Herders – Bot Herders: Use the new exploits to distribute malware to end users. These are used for Denial of Service extortion, spamming, stealing network or PII information, click advertisement abuse, etc. They sell their harvested information to criminals. – Criminals: Use their obtained credit card and bank account information to perpetuate financial crimes and pay for further development • Finding ways to identify, control and remove malware (especially unidentified malware) is a boom market • Limiting exposure (for example through good system security and products such as Cisco’s Iron Port appliances) can minimize this risk 16
 Malicious Code Threats (2007) • One very real problem is that there is a proliferation of malware, and Anti-Virus simply cannot keep up with all the new versions 17
Malicious Code Threats (2007) • One very real problem is that there is a proliferation of malware, and Anti-Virus simply cannot keep up with all the new versions 17
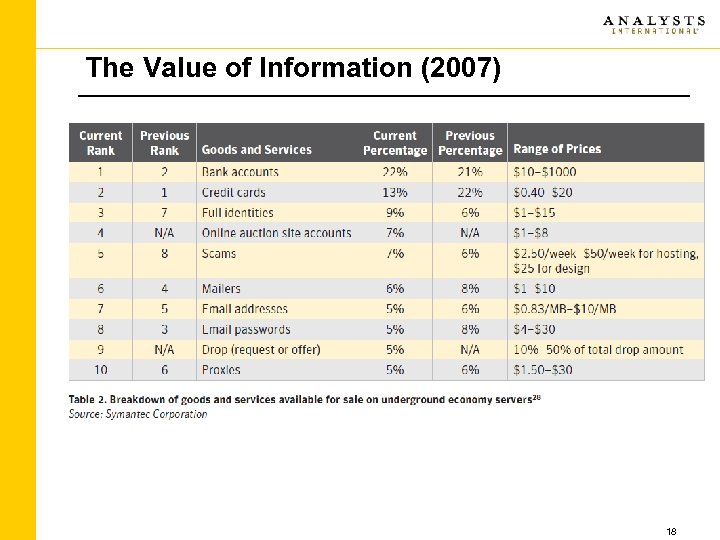 The Value of Information (2007) 18
The Value of Information (2007) 18
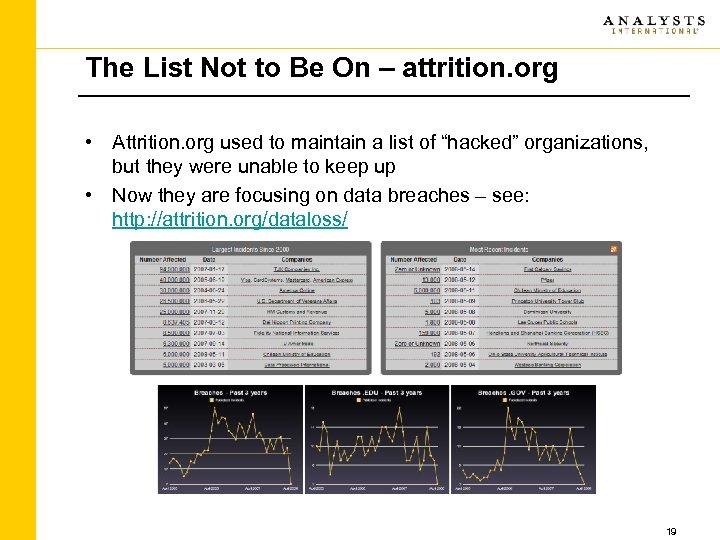 The List Not to Be On – attrition. org • Attrition. org used to maintain a list of “hacked” organizations, but they were unable to keep up • Now they are focusing on data breaches – see: http: //attrition. org/dataloss/ 19
The List Not to Be On – attrition. org • Attrition. org used to maintain a list of “hacked” organizations, but they were unable to keep up • Now they are focusing on data breaches – see: http: //attrition. org/dataloss/ 19
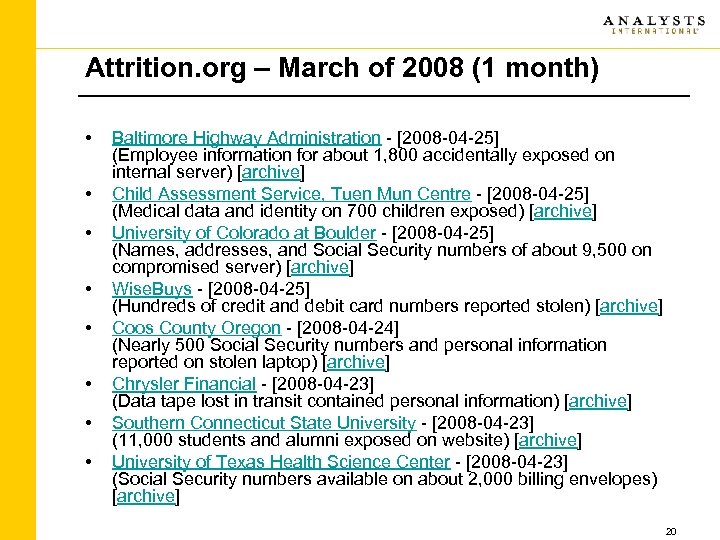 Attrition. org – March of 2008 (1 month) • • Baltimore Highway Administration - [2008 -04 -25] (Employee information for about 1, 800 accidentally exposed on internal server) [archive] Child Assessment Service, Tuen Mun Centre - [2008 -04 -25] (Medical data and identity on 700 children exposed) [archive] University of Colorado at Boulder - [2008 -04 -25] (Names, addresses, and Social Security numbers of about 9, 500 on compromised server) [archive] Wise. Buys - [2008 -04 -25] (Hundreds of credit and debit card numbers reported stolen) [archive] Coos County Oregon - [2008 -04 -24] (Nearly 500 Social Security numbers and personal information reported on stolen laptop) [archive] Chrysler Financial - [2008 -04 -23] (Data tape lost in transit contained personal information) [archive] Southern Connecticut State University - [2008 -04 -23] (11, 000 students and alumni exposed on website) [archive] University of Texas Health Science Center - [2008 -04 -23] (Social Security numbers available on about 2, 000 billing envelopes) [archive] 20
Attrition. org – March of 2008 (1 month) • • Baltimore Highway Administration - [2008 -04 -25] (Employee information for about 1, 800 accidentally exposed on internal server) [archive] Child Assessment Service, Tuen Mun Centre - [2008 -04 -25] (Medical data and identity on 700 children exposed) [archive] University of Colorado at Boulder - [2008 -04 -25] (Names, addresses, and Social Security numbers of about 9, 500 on compromised server) [archive] Wise. Buys - [2008 -04 -25] (Hundreds of credit and debit card numbers reported stolen) [archive] Coos County Oregon - [2008 -04 -24] (Nearly 500 Social Security numbers and personal information reported on stolen laptop) [archive] Chrysler Financial - [2008 -04 -23] (Data tape lost in transit contained personal information) [archive] Southern Connecticut State University - [2008 -04 -23] (11, 000 students and alumni exposed on website) [archive] University of Texas Health Science Center - [2008 -04 -23] (Social Security numbers available on about 2, 000 billing envelopes) [archive] 20
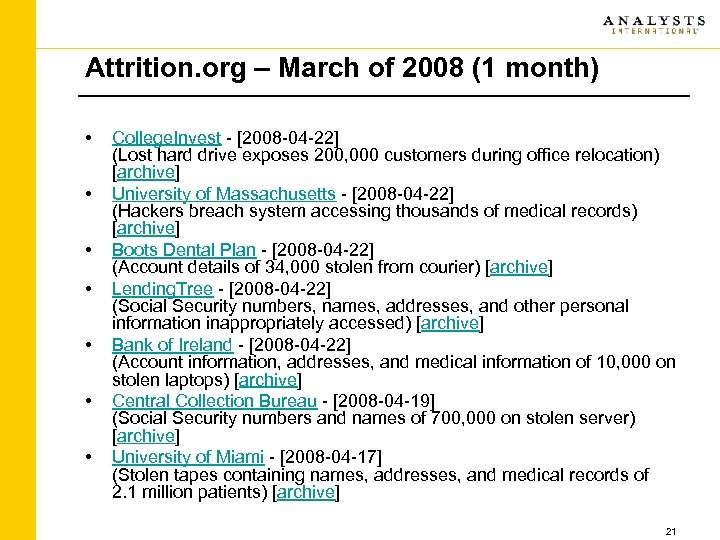 Attrition. org – March of 2008 (1 month) • • College. Invest - [2008 -04 -22] (Lost hard drive exposes 200, 000 customers during office relocation) [archive] University of Massachusetts - [2008 -04 -22] (Hackers breach system accessing thousands of medical records) [archive] Boots Dental Plan - [2008 -04 -22] (Account details of 34, 000 stolen from courier) [archive] Lending. Tree - [2008 -04 -22] (Social Security numbers, names, addresses, and other personal information inappropriately accessed) [archive] Bank of Ireland - [2008 -04 -22] (Account information, addresses, and medical information of 10, 000 on stolen laptops) [archive] Central Collection Bureau - [2008 -04 -19] (Social Security numbers and names of 700, 000 on stolen server) [archive] University of Miami - [2008 -04 -17] (Stolen tapes containing names, addresses, and medical records of 2. 1 million patients) [archive] 21
Attrition. org – March of 2008 (1 month) • • College. Invest - [2008 -04 -22] (Lost hard drive exposes 200, 000 customers during office relocation) [archive] University of Massachusetts - [2008 -04 -22] (Hackers breach system accessing thousands of medical records) [archive] Boots Dental Plan - [2008 -04 -22] (Account details of 34, 000 stolen from courier) [archive] Lending. Tree - [2008 -04 -22] (Social Security numbers, names, addresses, and other personal information inappropriately accessed) [archive] Bank of Ireland - [2008 -04 -22] (Account information, addresses, and medical information of 10, 000 on stolen laptops) [archive] Central Collection Bureau - [2008 -04 -19] (Social Security numbers and names of 700, 000 on stolen server) [archive] University of Miami - [2008 -04 -17] (Stolen tapes containing names, addresses, and medical records of 2. 1 million patients) [archive] 21
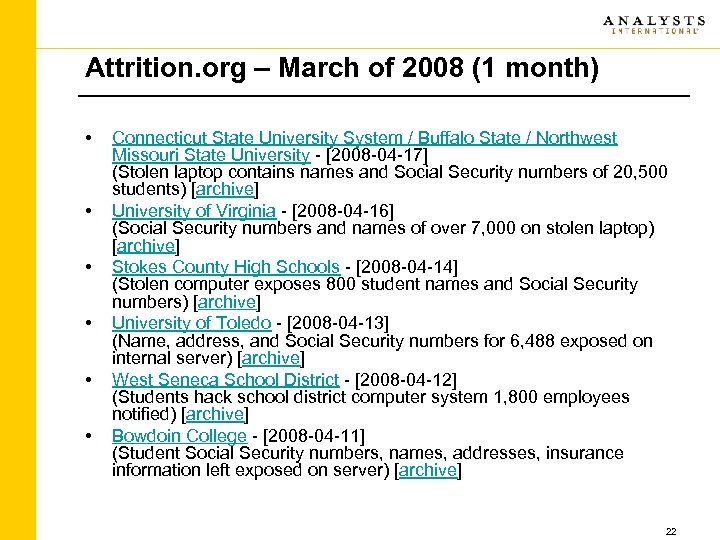 Attrition. org – March of 2008 (1 month) • • • Connecticut State University System / Buffalo State / Northwest Missouri State University - [2008 -04 -17] (Stolen laptop contains names and Social Security numbers of 20, 500 students) [archive] University of Virginia - [2008 -04 -16] (Social Security numbers and names of over 7, 000 on stolen laptop) [archive] Stokes County High Schools - [2008 -04 -14] (Stolen computer exposes 800 student names and Social Security numbers) [archive] University of Toledo - [2008 -04 -13] (Name, address, and Social Security numbers for 6, 488 exposed on internal server) [archive] West Seneca School District - [2008 -04 -12] (Students hack school district computer system 1, 800 employees notified) [archive] Bowdoin College - [2008 -04 -11] (Student Social Security numbers, names, addresses, insurance information left exposed on server) [archive] 22
Attrition. org – March of 2008 (1 month) • • • Connecticut State University System / Buffalo State / Northwest Missouri State University - [2008 -04 -17] (Stolen laptop contains names and Social Security numbers of 20, 500 students) [archive] University of Virginia - [2008 -04 -16] (Social Security numbers and names of over 7, 000 on stolen laptop) [archive] Stokes County High Schools - [2008 -04 -14] (Stolen computer exposes 800 student names and Social Security numbers) [archive] University of Toledo - [2008 -04 -13] (Name, address, and Social Security numbers for 6, 488 exposed on internal server) [archive] West Seneca School District - [2008 -04 -12] (Students hack school district computer system 1, 800 employees notified) [archive] Bowdoin College - [2008 -04 -11] (Student Social Security numbers, names, addresses, insurance information left exposed on server) [archive] 22
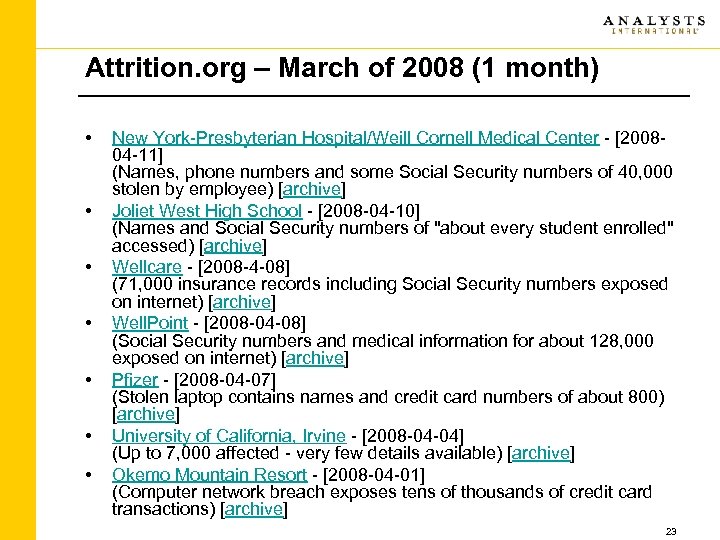 Attrition. org – March of 2008 (1 month) • • New York-Presbyterian Hospital/Weill Cornell Medical Center - [200804 -11] (Names, phone numbers and some Social Security numbers of 40, 000 stolen by employee) [archive] Joliet West High School - [2008 -04 -10] (Names and Social Security numbers of "about every student enrolled" accessed) [archive] Wellcare - [2008 -4 -08] (71, 000 insurance records including Social Security numbers exposed on internet) [archive] Well. Point - [2008 -04 -08] (Social Security numbers and medical information for about 128, 000 exposed on internet) [archive] Pfizer - [2008 -04 -07] (Stolen laptop contains names and credit card numbers of about 800) [archive] University of California, Irvine - [2008 -04 -04] (Up to 7, 000 affected - very few details available) [archive] Okemo Mountain Resort - [2008 -04 -01] (Computer network breach exposes tens of thousands of credit card transactions) [archive] 23
Attrition. org – March of 2008 (1 month) • • New York-Presbyterian Hospital/Weill Cornell Medical Center - [200804 -11] (Names, phone numbers and some Social Security numbers of 40, 000 stolen by employee) [archive] Joliet West High School - [2008 -04 -10] (Names and Social Security numbers of "about every student enrolled" accessed) [archive] Wellcare - [2008 -4 -08] (71, 000 insurance records including Social Security numbers exposed on internet) [archive] Well. Point - [2008 -04 -08] (Social Security numbers and medical information for about 128, 000 exposed on internet) [archive] Pfizer - [2008 -04 -07] (Stolen laptop contains names and credit card numbers of about 800) [archive] University of California, Irvine - [2008 -04 -04] (Up to 7, 000 affected - very few details available) [archive] Okemo Mountain Resort - [2008 -04 -01] (Computer network breach exposes tens of thousands of credit card transactions) [archive] 23
 Managing the Societal Impact of High-Tech Crime • And those were only the incidents that were reported, and for which someone bothered to make an entry in the database • Obviously, this is a problem that is costly both to the people affected and to the economy in general • “Computer Economics” estimates $13 Billion world-wide in 2006, and its getting worse • To mitigate this, government (through regulations and laws) and industries (through self-regulation) are starting to develop standards and controls • Some standards are proactive, some reactive • We will discuss a couple – the Payment Card Industry (PCI) and Gramm-Leach-Bliley Act (GLBA) 24
Managing the Societal Impact of High-Tech Crime • And those were only the incidents that were reported, and for which someone bothered to make an entry in the database • Obviously, this is a problem that is costly both to the people affected and to the economy in general • “Computer Economics” estimates $13 Billion world-wide in 2006, and its getting worse • To mitigate this, government (through regulations and laws) and industries (through self-regulation) are starting to develop standards and controls • Some standards are proactive, some reactive • We will discuss a couple – the Payment Card Industry (PCI) and Gramm-Leach-Bliley Act (GLBA) 24
 The Payment Card Industry (PCI) • A consortium of credit card companies including Visa and Mastercard • Has implemented the PCI Data Security Standard (PCI DSS) • This affects anyone who stores or processes credit card information, though there are different categories: – https: //www. pcisecuritystandards. org/pdfs/instructions_guidelines_v 1 -1. pdf – “According to payment brand rules, all merchants and service providers are required to comply with the PCI Data Security Standard in its entirety. ” 25
The Payment Card Industry (PCI) • A consortium of credit card companies including Visa and Mastercard • Has implemented the PCI Data Security Standard (PCI DSS) • This affects anyone who stores or processes credit card information, though there are different categories: – https: //www. pcisecuritystandards. org/pdfs/instructions_guidelines_v 1 -1. pdf – “According to payment brand rules, all merchants and service providers are required to comply with the PCI Data Security Standard in its entirety. ” 25
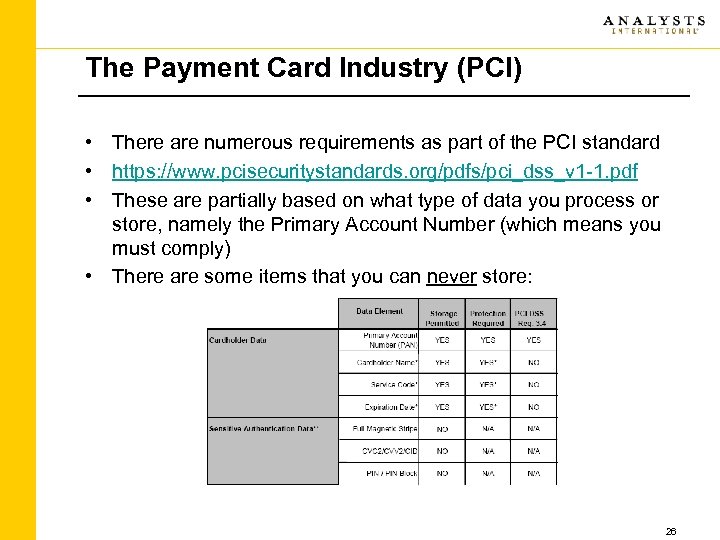 The Payment Card Industry (PCI) • There are numerous requirements as part of the PCI standard • https: //www. pcisecuritystandards. org/pdfs/pci_dss_v 1 -1. pdf • These are partially based on what type of data you process or store, namely the Primary Account Number (which means you must comply) • There are some items that you can never store: 26
The Payment Card Industry (PCI) • There are numerous requirements as part of the PCI standard • https: //www. pcisecuritystandards. org/pdfs/pci_dss_v 1 -1. pdf • These are partially based on what type of data you process or store, namely the Primary Account Number (which means you must comply) • There are some items that you can never store: 26
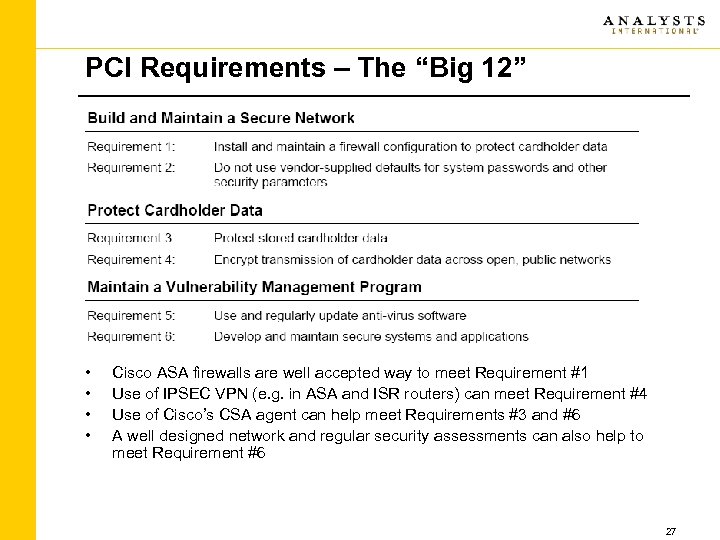 PCI Requirements – The “Big 12” • • Cisco ASA firewalls are well accepted way to meet Requirement #1 Use of IPSEC VPN (e. g. in ASA and ISR routers) can meet Requirement #4 Use of Cisco’s CSA agent can help meet Requirements #3 and #6 A well designed network and regular security assessments can also help to meet Requirement #6 27
PCI Requirements – The “Big 12” • • Cisco ASA firewalls are well accepted way to meet Requirement #1 Use of IPSEC VPN (e. g. in ASA and ISR routers) can meet Requirement #4 Use of Cisco’s CSA agent can help meet Requirements #3 and #6 A well designed network and regular security assessments can also help to meet Requirement #6 27
 PCI Requirements – The “Big 12” • • Cisco’s MARS Appliance can help to meet Requirement #10 Regular vulnerability assessments (e. g. Analysts ISAS, OSAS and WASA services) can help address Requirement #11 Analysts policy development services can help to address Requirement #12 OF COURSE a mature and well-run organization with proper practices and procedures is the essential glue that pulls together all of the external products and services, and is without a doubt the MOST important part 28
PCI Requirements – The “Big 12” • • Cisco’s MARS Appliance can help to meet Requirement #10 Regular vulnerability assessments (e. g. Analysts ISAS, OSAS and WASA services) can help address Requirement #11 Analysts policy development services can help to address Requirement #12 OF COURSE a mature and well-run organization with proper practices and procedures is the essential glue that pulls together all of the external products and services, and is without a doubt the MOST important part 28
 The Gramm-Leach Bliley Act (GLBA) • Includes three primary components: – The Financial Privacy Rule governs the collection and disclosure of customers' personal financial information by financial institutions. It also applies to companies, whether or not they are financial institutions, who receive such information. – The Safeguards Rule requires all financial institutions to design, implement and maintain safeguards to protect customer information. The Safeguards Rule applies not only to financial institutions that collect information from their own customers, but also to financial institutions "such as credit reporting agencies" that receive customer information from other financial institutions. – The Pretexting provisions of the GLB Act protect consumers from individuals and companies that obtain their personal financial information under false pretenses, a practice known as "pretexting. " 29
The Gramm-Leach Bliley Act (GLBA) • Includes three primary components: – The Financial Privacy Rule governs the collection and disclosure of customers' personal financial information by financial institutions. It also applies to companies, whether or not they are financial institutions, who receive such information. – The Safeguards Rule requires all financial institutions to design, implement and maintain safeguards to protect customer information. The Safeguards Rule applies not only to financial institutions that collect information from their own customers, but also to financial institutions "such as credit reporting agencies" that receive customer information from other financial institutions. – The Pretexting provisions of the GLB Act protect consumers from individuals and companies that obtain their personal financial information under false pretenses, a practice known as "pretexting. " 29
 The GLBA Privacy Rule 313 • Is primarily concerned with how you process and use information, and most notably that organizations have implemented a privacy policy and protection plan • Past analysis by Analysts International has identified several specific provisions as part of our Security Needs Analysis Service (but you should consult your own legal counsel before accepting these as gospel): – A formal information privacy policy has been created – The information privacy is regularly communicated to internal and external stakeholders – The privacy policy includes an inventory of existing data collection practices – The privacy policy makes a distinction between Consumers (e. g. any NON-individual seeking a financial product or service) and a Customer (e. g. any individual with an established relationship) 30
The GLBA Privacy Rule 313 • Is primarily concerned with how you process and use information, and most notably that organizations have implemented a privacy policy and protection plan • Past analysis by Analysts International has identified several specific provisions as part of our Security Needs Analysis Service (but you should consult your own legal counsel before accepting these as gospel): – A formal information privacy policy has been created – The information privacy is regularly communicated to internal and external stakeholders – The privacy policy includes an inventory of existing data collection practices – The privacy policy makes a distinction between Consumers (e. g. any NON-individual seeking a financial product or service) and a Customer (e. g. any individual with an established relationship) 30
 The GLBA Protection Rule 314 • Is concerned with how you protect sensitive data – Encrypt the data – Properly dispose of it (and require outsourced service providers to do so as well) – Have a formal incident response plan to detect and respond to threats – Have a formal risk assessment program is in place and someone designated to maintain it – A formal “administrator termination” process is used to remove all access rights from former employees – Safeguards are regularly monitored and tested 31
The GLBA Protection Rule 314 • Is concerned with how you protect sensitive data – Encrypt the data – Properly dispose of it (and require outsourced service providers to do so as well) – Have a formal incident response plan to detect and respond to threats – Have a formal risk assessment program is in place and someone designated to maintain it – A formal “administrator termination” process is used to remove all access rights from former employees – Safeguards are regularly monitored and tested 31
 Summary – Data Loss Prevention • • • Data disclosures are bad, and getting worse It is difficult to identify requirements, to whom and how they apply, and how to address them in a cost effective manner Difficult to manage and monitor large I. T. infrastructures, products are needed Expertise in security and regulatory compliance is difficult to come by, and Subject Matter Experts are expensive to hire, train and keep on staff A high level of organizational maturity is required to pass audits, let alone truly comply with the “spirit” if the laws 32
Summary – Data Loss Prevention • • • Data disclosures are bad, and getting worse It is difficult to identify requirements, to whom and how they apply, and how to address them in a cost effective manner Difficult to manage and monitor large I. T. infrastructures, products are needed Expertise in security and regulatory compliance is difficult to come by, and Subject Matter Experts are expensive to hire, train and keep on staff A high level of organizational maturity is required to pass audits, let alone truly comply with the “spirit” if the laws 32
 Section 2 – Threat Vectors and Internal Controls Mark Lachniet, Solutions Architect – Analysts International Lansing, MI July 15 th, 2008
Section 2 – Threat Vectors and Internal Controls Mark Lachniet, Solutions Architect – Analysts International Lansing, MI July 15 th, 2008
 Data Loss Threat Vectors and Controls • Many controls are best done internally, such as creating a formal I. T. security management framework, or identifying the type of data you need to protect • Some controls are most efficient when automated with products – for example aggregating logs from a large number of systems and analyzing them for incidents • Some controls require significant security expertise, or require “third party independence” such as doing security audits, and may need to be outsourced for cost reasons • In the next section, we will discuss a number of threats (though not a complete list) that pertain to DLP and propose some appropriate controls that can be done internally, with Cisco Products, or Analysts’ services 34
Data Loss Threat Vectors and Controls • Many controls are best done internally, such as creating a formal I. T. security management framework, or identifying the type of data you need to protect • Some controls are most efficient when automated with products – for example aggregating logs from a large number of systems and analyzing them for incidents • Some controls require significant security expertise, or require “third party independence” such as doing security audits, and may need to be outsourced for cost reasons • In the next section, we will discuss a number of threats (though not a complete list) that pertain to DLP and propose some appropriate controls that can be done internally, with Cisco Products, or Analysts’ services 34
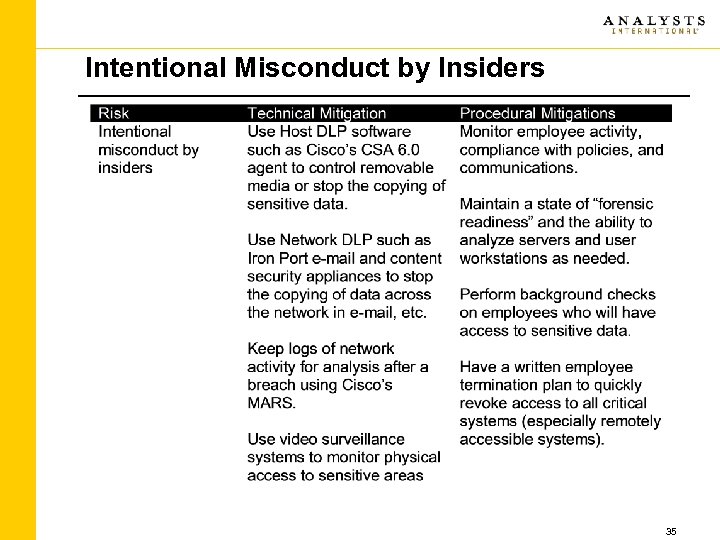 Intentional Misconduct by Insiders 35
Intentional Misconduct by Insiders 35
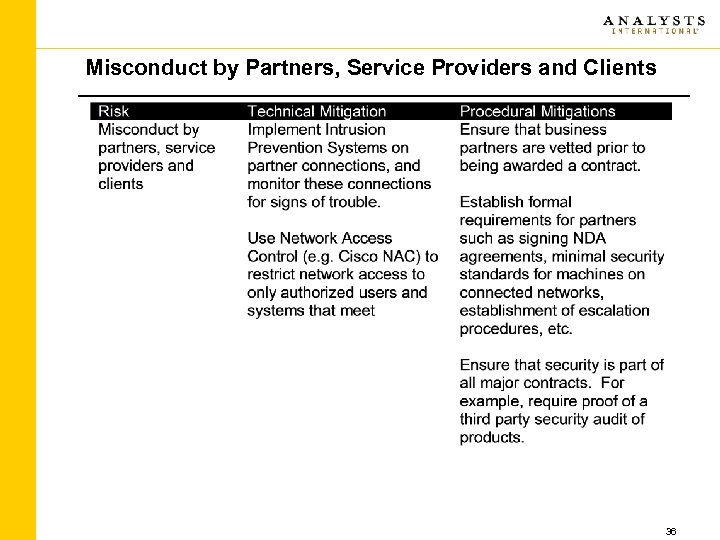 Misconduct by Partners, Service Providers and Clients 36
Misconduct by Partners, Service Providers and Clients 36
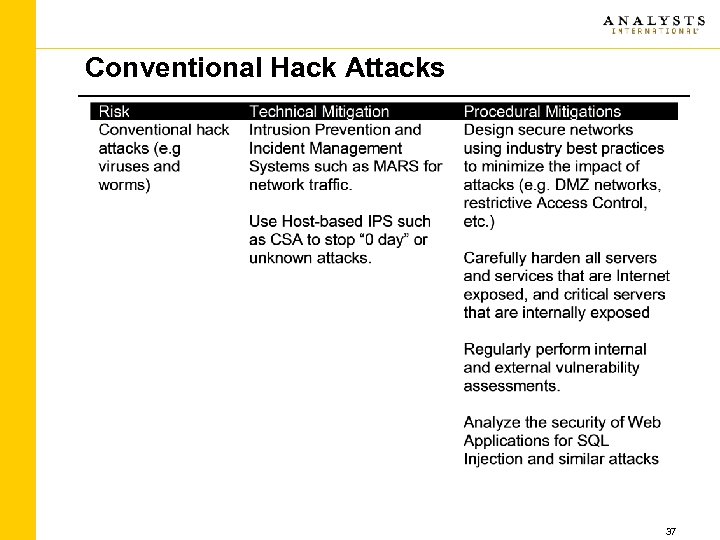 Conventional Hack Attacks 37
Conventional Hack Attacks 37
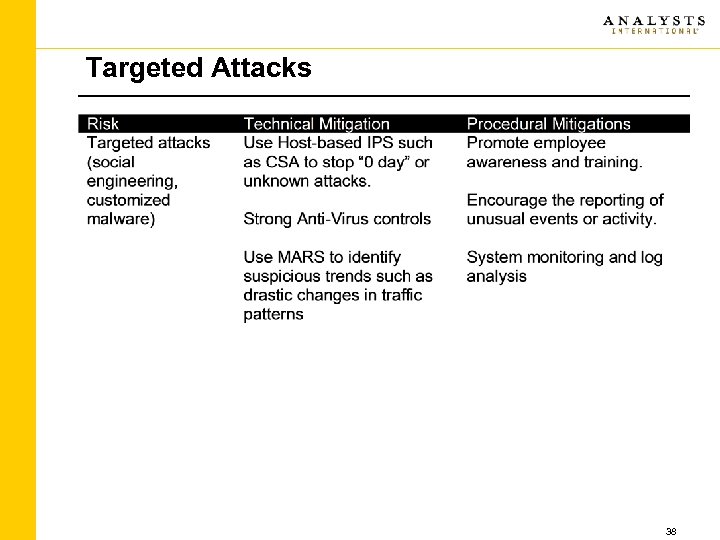 Targeted Attacks 38
Targeted Attacks 38
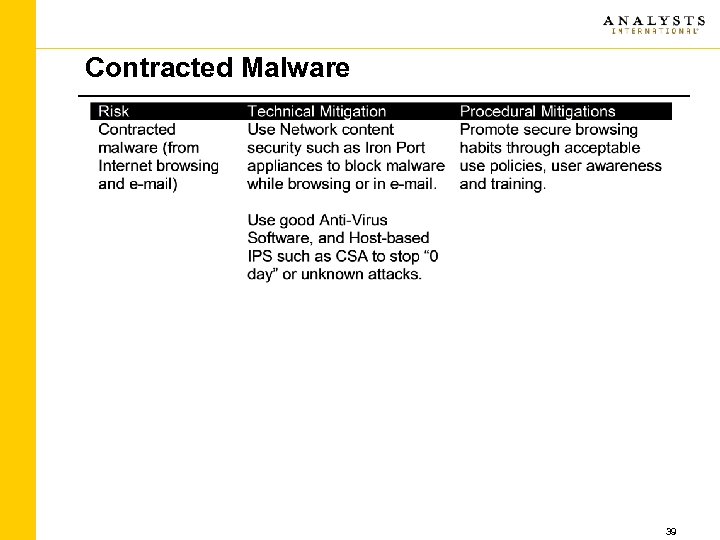 Contracted Malware 39
Contracted Malware 39
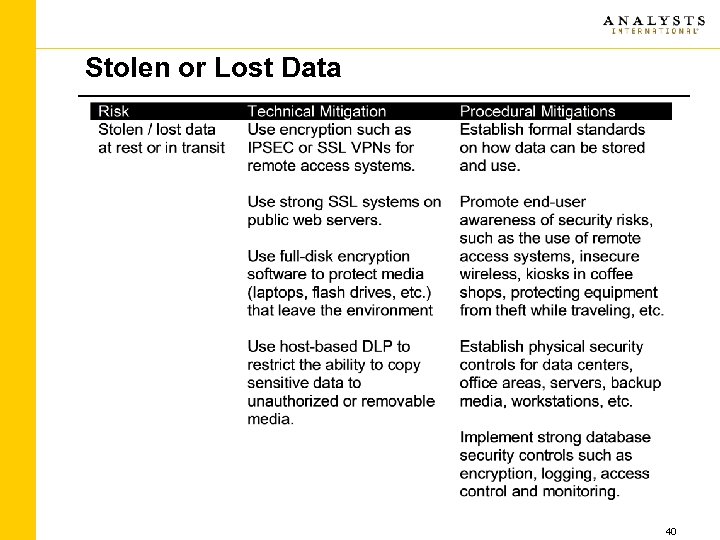 Stolen or Lost Data 40
Stolen or Lost Data 40
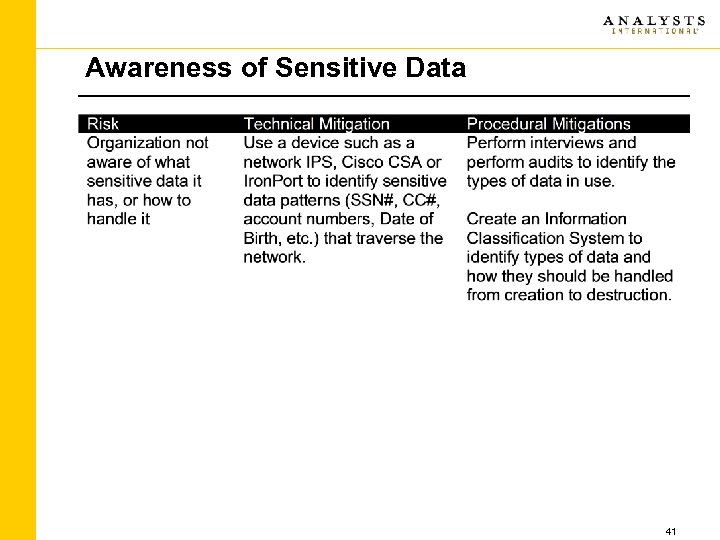 Awareness of Sensitive Data 41
Awareness of Sensitive Data 41
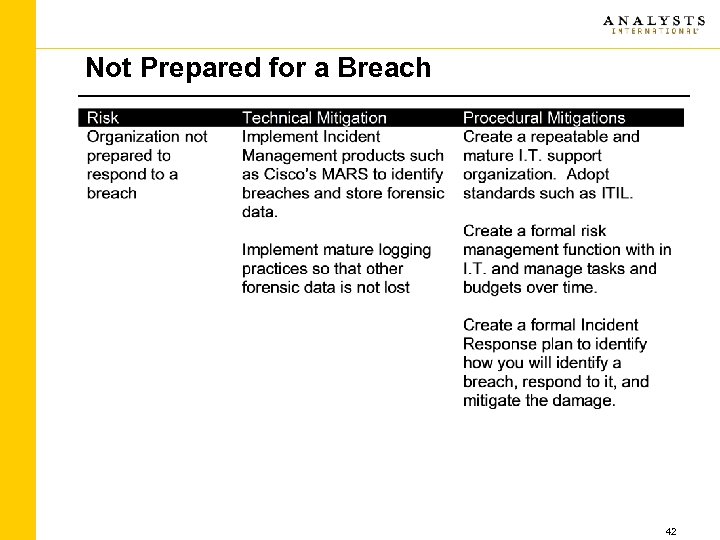 Not Prepared for a Breach 42
Not Prepared for a Breach 42
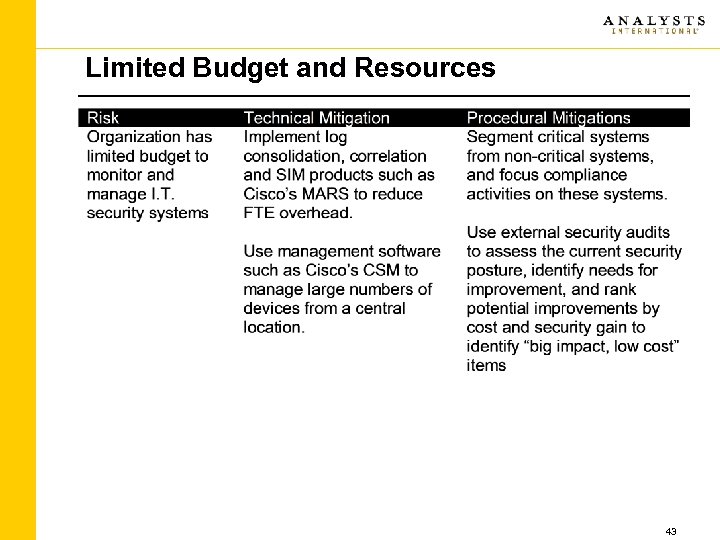 Limited Budget and Resources 43
Limited Budget and Resources 43
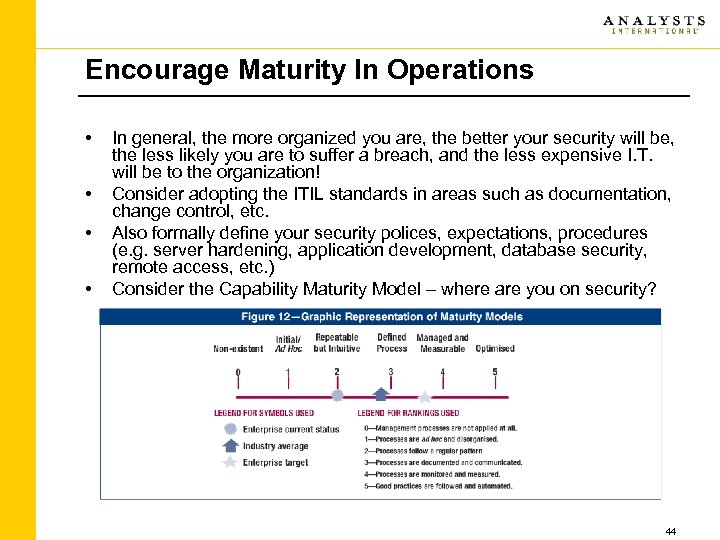 Encourage Maturity In Operations • • In general, the more organized you are, the better your security will be, the less likely you are to suffer a breach, and the less expensive I. T. will be to the organization! Consider adopting the ITIL standards in areas such as documentation, change control, etc. Also formally define your security polices, expectations, procedures (e. g. server hardening, application development, database security, remote access, etc. ) Consider the Capability Maturity Model – where are you on security? 44
Encourage Maturity In Operations • • In general, the more organized you are, the better your security will be, the less likely you are to suffer a breach, and the less expensive I. T. will be to the organization! Consider adopting the ITIL standards in areas such as documentation, change control, etc. Also formally define your security polices, expectations, procedures (e. g. server hardening, application development, database security, remote access, etc. ) Consider the Capability Maturity Model – where are you on security? 44
 Manage Employees • Do regular background checks of applicants • Have strong, documented linkages between H. R. and I. T. • Require sign-off on Acceptable Use Policies (AUP) and Non-Disclosure Agreements (NDA) • Provide training and awareness on security issues, recommended at 1 week/year per I. T. employee, less for end users • Regularly monitor employee activity 45
Manage Employees • Do regular background checks of applicants • Have strong, documented linkages between H. R. and I. T. • Require sign-off on Acceptable Use Policies (AUP) and Non-Disclosure Agreements (NDA) • Provide training and awareness on security issues, recommended at 1 week/year per I. T. employee, less for end users • Regularly monitor employee activity 45
 Formalize Risk Management • I. T. Risk Management should be a formal process in your organization • Consider creating a workgroup tasked with managing security that is responsible for: – Promoting awareness of Information Security issues within the organization – Identifying and managing strategic, operational and financial I. T. risks – Identifying and managing I. T. regulatory compliance requirements and controls – Identify security needs, budgetary and staffing requirements, etc. – Act as an interface to other departments within the organization to provide guidance and assistance on information security issues 46
Formalize Risk Management • I. T. Risk Management should be a formal process in your organization • Consider creating a workgroup tasked with managing security that is responsible for: – Promoting awareness of Information Security issues within the organization – Identifying and managing strategic, operational and financial I. T. risks – Identifying and managing I. T. regulatory compliance requirements and controls – Identify security needs, budgetary and staffing requirements, etc. – Act as an interface to other departments within the organization to provide guidance and assistance on information security issues 46
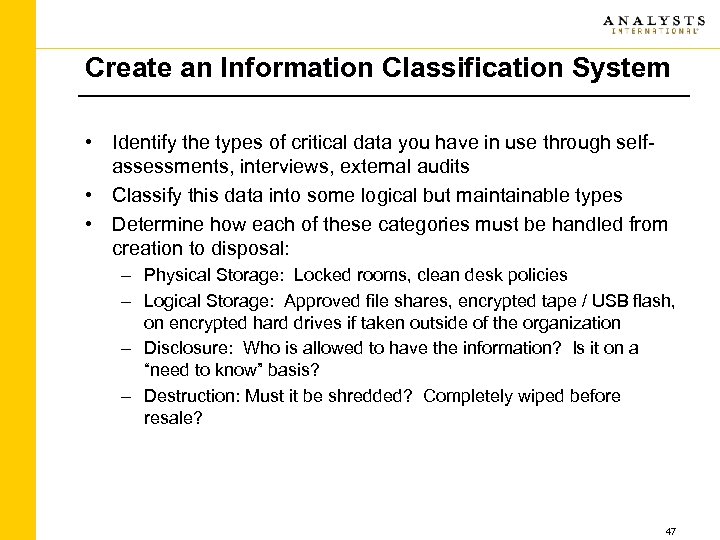 Create an Information Classification System • Identify the types of critical data you have in use through selfassessments, interviews, external audits • Classify this data into some logical but maintainable types • Determine how each of these categories must be handled from creation to disposal: – Physical Storage: Locked rooms, clean desk policies – Logical Storage: Approved file shares, encrypted tape / USB flash, on encrypted hard drives if taken outside of the organization – Disclosure: Who is allowed to have the information? Is it on a “need to know” basis? – Destruction: Must it be shredded? Completely wiped before resale? 47
Create an Information Classification System • Identify the types of critical data you have in use through selfassessments, interviews, external audits • Classify this data into some logical but maintainable types • Determine how each of these categories must be handled from creation to disposal: – Physical Storage: Locked rooms, clean desk policies – Logical Storage: Approved file shares, encrypted tape / USB flash, on encrypted hard drives if taken outside of the organization – Disclosure: Who is allowed to have the information? Is it on a “need to know” basis? – Destruction: Must it be shredded? Completely wiped before resale? 47
 Create an Incident Response Plan • Have a formal plan, that people are aware of and can use, on how to respond to an incident • Consider items such as: – How will you identify a breach? – What is the appropriate response, based on the type of information? – What information will you record about the incident? – Who is allowed to talk to whom? – What types of incidents will require an “oops letter” to go out? Who makes the call on this? – Will you have to file a Suspicious Activity Report (SAR) with an oversight agency? 48
Create an Incident Response Plan • Have a formal plan, that people are aware of and can use, on how to respond to an incident • Consider items such as: – How will you identify a breach? – What is the appropriate response, based on the type of information? – What information will you record about the incident? – Who is allowed to talk to whom? – What types of incidents will require an “oops letter” to go out? Who makes the call on this? – Will you have to file a Suspicious Activity Report (SAR) with an oversight agency? 48
 Forensic Readiness • Forensic readiness is related to incident response, but focuses on taking steps to accumulate forensic data before an incident happens • Do you have log files from all of your network devices? Servers? Would they be available if the device was wiped? • Do you have the ability to do log analysis with software such as Sawmill in an ad-hoc basis for data mining? • Do you have processes, procedures and tools to analyze and preserve data? • Do you know who to call if you are out of your depth? • Do you have legal help? • Are you covering your data retention requirements? 49
Forensic Readiness • Forensic readiness is related to incident response, but focuses on taking steps to accumulate forensic data before an incident happens • Do you have log files from all of your network devices? Servers? Would they be available if the device was wiped? • Do you have the ability to do log analysis with software such as Sawmill in an ad-hoc basis for data mining? • Do you have processes, procedures and tools to analyze and preserve data? • Do you know who to call if you are out of your depth? • Do you have legal help? • Are you covering your data retention requirements? 49
 Privacy Policy • Do you have a written privacy policy? • Does it match the regulatory requirements that you may be subject to? • Does it align with your information classification and incident response procedures? • Has your lawyer reviewed it? 50
Privacy Policy • Do you have a written privacy policy? • Does it match the regulatory requirements that you may be subject to? • Does it align with your information classification and incident response procedures? • Has your lawyer reviewed it? 50
 Section 3 – Managing Data Loss - Cisco Solutions Bret Straffon, bstraffo@cisco. com PSS Security Lansing, MI July 15 th, 2008
Section 3 – Managing Data Loss - Cisco Solutions Bret Straffon, bstraffo@cisco. com PSS Security Lansing, MI July 15 th, 2008
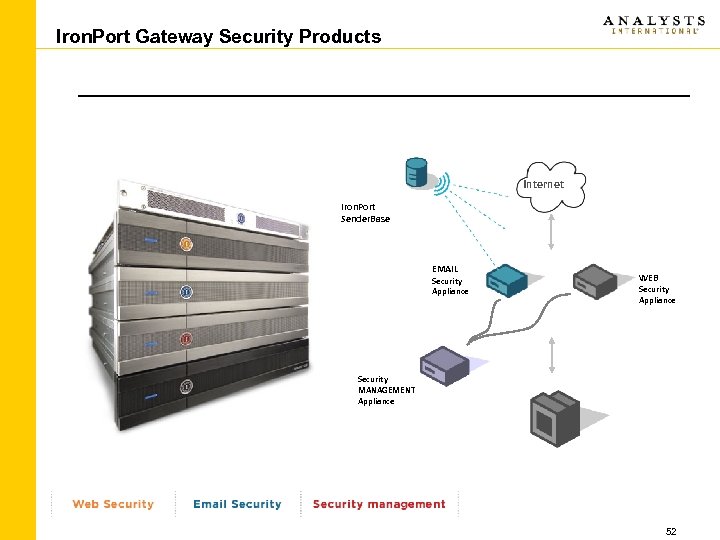 Iron. Port Gateway Security Products Internet Iron. Port Sender. Base EMAIL Security Appliance WEB Security Appliance Security MANAGEMENT Appliance 52
Iron. Port Gateway Security Products Internet Iron. Port Sender. Base EMAIL Security Appliance WEB Security Appliance Security MANAGEMENT Appliance 52
 Iron. Port – Gateway Solutions E-Mail Security (C-Series) Web Security (S-Series) • • Protection from External Attacks – – – • Spam Virus Denial of Service Phishing Directory Harvesting Misdirected Bounces Protection of Internal Property – – – Compliance Data Leakage Encryption Brand Protection Email Authentication Control Web Traffic – – • High performance web proxy Web Policy & URL Filtering Fully integrated complete content inspection L 4 traffic monitor protects all network ports Protect from Web Threats – – – – Adware Virus Phishing Browser Hijackers Keyloggers Trojans and more 53
Iron. Port – Gateway Solutions E-Mail Security (C-Series) Web Security (S-Series) • • Protection from External Attacks – – – • Spam Virus Denial of Service Phishing Directory Harvesting Misdirected Bounces Protection of Internal Property – – – Compliance Data Leakage Encryption Brand Protection Email Authentication Control Web Traffic – – • High performance web proxy Web Policy & URL Filtering Fully integrated complete content inspection L 4 traffic monitor protects all network ports Protect from Web Threats – – – – Adware Virus Phishing Browser Hijackers Keyloggers Trojans and more 53
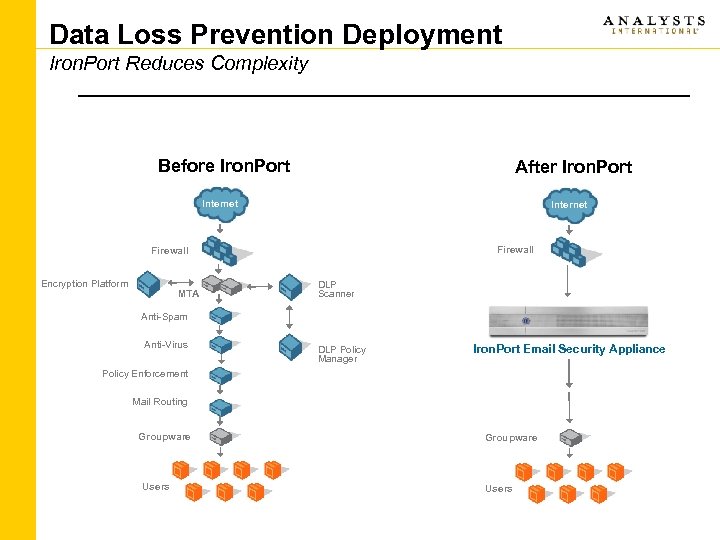 Data Loss Prevention Deployment Iron. Port Reduces Complexity Before Iron. Port After Iron. Port Internet Firewall Encryption Platform MTA DLP Scanner Anti-Spam Anti-Virus DLP Policy Manager Iron. Port Email Security Appliance Policy Enforcement Mail Routing Groupware Users
Data Loss Prevention Deployment Iron. Port Reduces Complexity Before Iron. Port After Iron. Port Internet Firewall Encryption Platform MTA DLP Scanner Anti-Spam Anti-Virus DLP Policy Manager Iron. Port Email Security Appliance Policy Enforcement Mail Routing Groupware Users
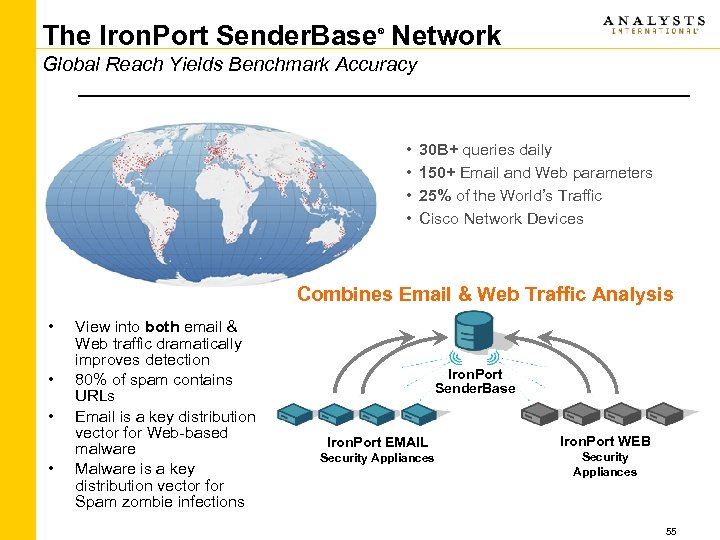 The Iron. Port Sender. Base Network ® Global Reach Yields Benchmark Accuracy • • 30 B+ queries daily 150+ Email and Web parameters 25% of the World’s Traffic Cisco Network Devices Combines Email & Web Traffic Analysis • • View into both email & Web traffic dramatically improves detection 80% of spam contains URLs Email is a key distribution vector for Web-based malware Malware is a key distribution vector for Spam zombie infections Iron. Port Sender. Base Iron. Port EMAIL Iron. Port WEB Security Appliances 55
The Iron. Port Sender. Base Network ® Global Reach Yields Benchmark Accuracy • • 30 B+ queries daily 150+ Email and Web parameters 25% of the World’s Traffic Cisco Network Devices Combines Email & Web Traffic Analysis • • View into both email & Web traffic dramatically improves detection 80% of spam contains URLs Email is a key distribution vector for Web-based malware Malware is a key distribution vector for Spam zombie infections Iron. Port Sender. Base Iron. Port EMAIL Iron. Port WEB Security Appliances 55
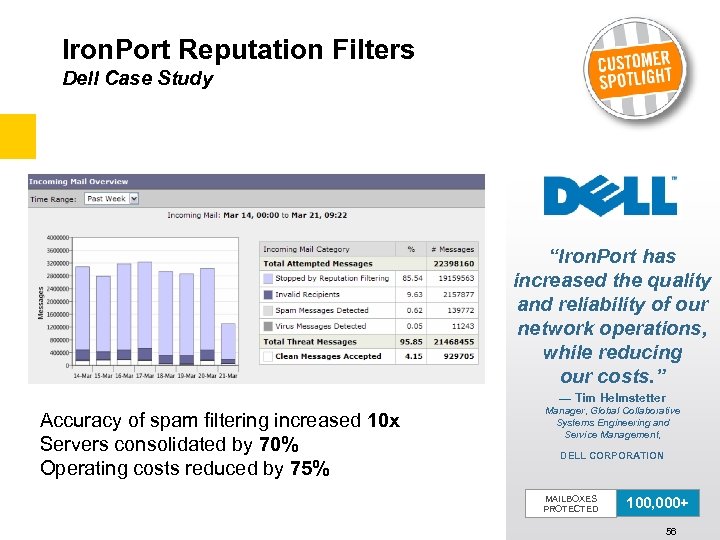 Iron. Port Reputation Filters Dell Case Study • Dell’s challenge: – Dell currently receives 26 million messages per day – Only 1. 5 million are legitimate messages – 68 existing gateways running Spam Assassin were not accurate • Iron. Port’s solution: – Iron. Port Reputation Filters block over 19 million messages per day – 5. 5 million messages per day scanned by Iron. Port Anti-Spam – Replaced 68 servers with 8 Iron. Port appliances Accuracy of spam filtering increased 10 x Servers consolidated by 70% Operating costs reduced by 75% “Iron. Port has increased the quality and reliability of our network operations, while reducing our costs. ” — Tim Helmstetter Manager, Global Collaborative Systems Engineering and Service Management, DELL CORPORATION MAILBOXES PROTECTED 100, 000+ 56
Iron. Port Reputation Filters Dell Case Study • Dell’s challenge: – Dell currently receives 26 million messages per day – Only 1. 5 million are legitimate messages – 68 existing gateways running Spam Assassin were not accurate • Iron. Port’s solution: – Iron. Port Reputation Filters block over 19 million messages per day – 5. 5 million messages per day scanned by Iron. Port Anti-Spam – Replaced 68 servers with 8 Iron. Port appliances Accuracy of spam filtering increased 10 x Servers consolidated by 70% Operating costs reduced by 75% “Iron. Port has increased the quality and reliability of our network operations, while reducing our costs. ” — Tim Helmstetter Manager, Global Collaborative Systems Engineering and Service Management, DELL CORPORATION MAILBOXES PROTECTED 100, 000+ 56
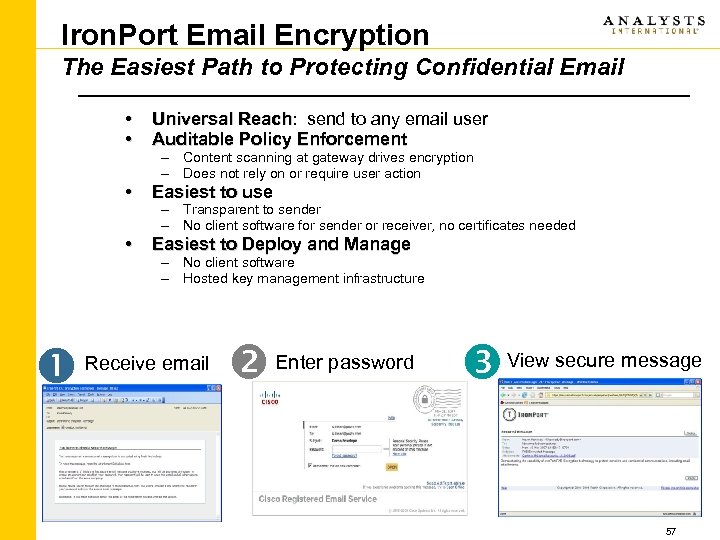 Iron. Port Email Encryption The Easiest Path to Protecting Confidential Email • • • Easiest to use • Universal Reach: send to any email user Reach Auditable Policy Enforcement Easiest to Deploy and Manage – Content scanning at gateway drives encryption – Does not rely on or require user action – Transparent to sender – No client software for sender or receiver, no certificates needed – No client software – Hosted key management infrastructure Receive email Enter password View secure message 57
Iron. Port Email Encryption The Easiest Path to Protecting Confidential Email • • • Easiest to use • Universal Reach: send to any email user Reach Auditable Policy Enforcement Easiest to Deploy and Manage – Content scanning at gateway drives encryption – Does not rely on or require user action – Transparent to sender – No client software for sender or receiver, no certificates needed – No client software – Hosted key management infrastructure Receive email Enter password View secure message 57
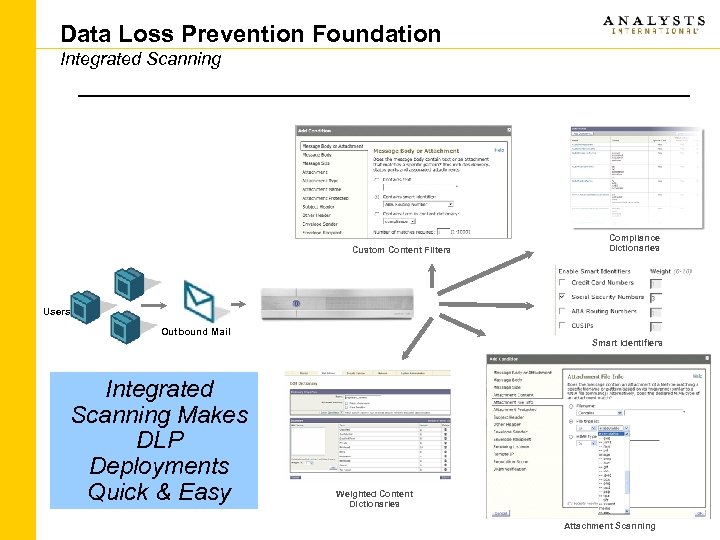 Data Loss Prevention Foundation Integrated Scanning Custom Content Filters Compliance Dictionaries Users Outbound Mail Smart Identifiers Integrated Scanning Makes DLP Deployments Quick & Easy Weighted Content Dictionaries Attachment Scanning
Data Loss Prevention Foundation Integrated Scanning Custom Content Filters Compliance Dictionaries Users Outbound Mail Smart Identifiers Integrated Scanning Makes DLP Deployments Quick & Easy Weighted Content Dictionaries Attachment Scanning
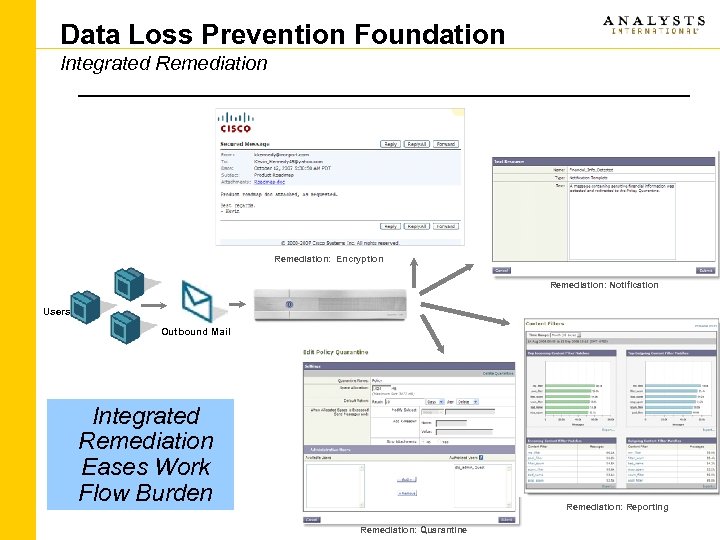 Data Loss Prevention Foundation Integrated Remediation: Encryption Remediation: Notification Users Outbound Mail Integrated Remediation Eases Work Flow Burden Remediation: Reporting Remediation: Quarantine
Data Loss Prevention Foundation Integrated Remediation: Encryption Remediation: Notification Users Outbound Mail Integrated Remediation Eases Work Flow Burden Remediation: Reporting Remediation: Quarantine
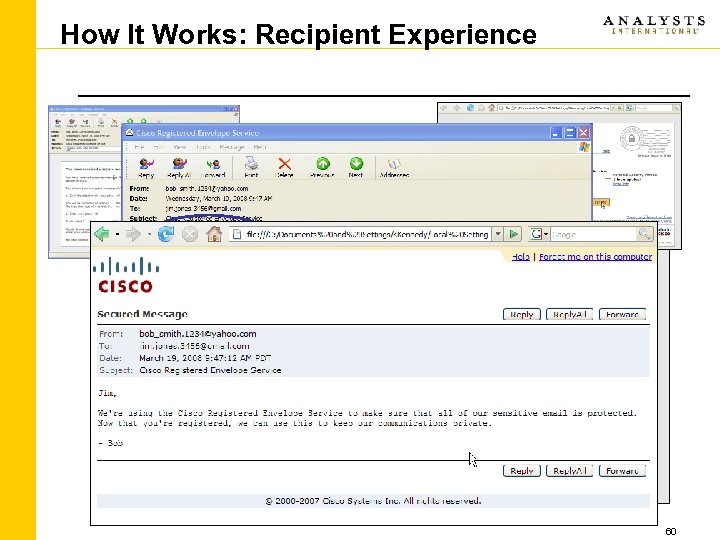 How It Works: Recipient Experience on ti N ot a ic if pe o el nv E 60
How It Works: Recipient Experience on ti N ot a ic if pe o el nv E 60
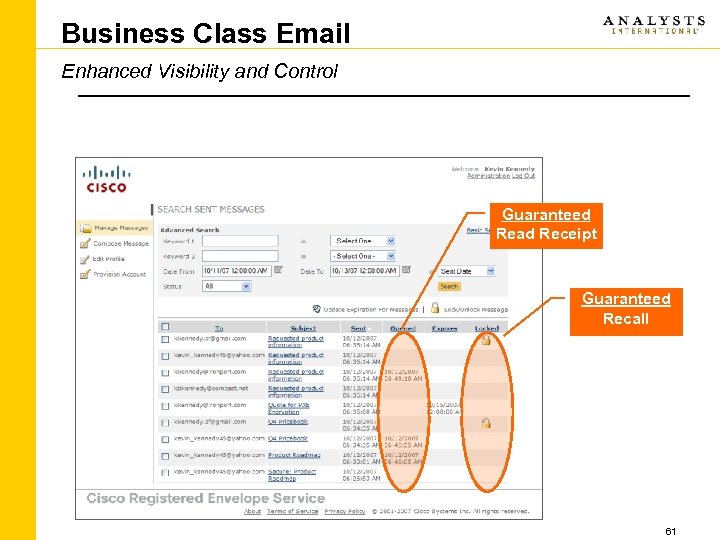 Business Class Email Enhanced Visibility and Control Guaranteed Read Receipt Guaranteed Recall 61
Business Class Email Enhanced Visibility and Control Guaranteed Read Receipt Guaranteed Recall 61
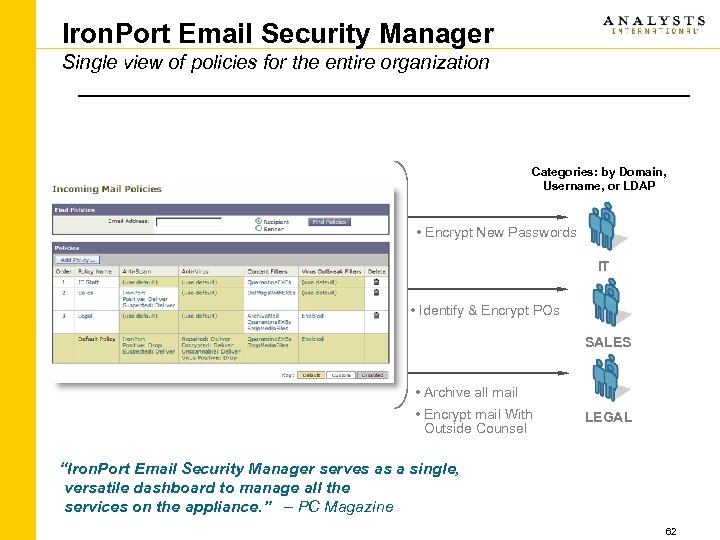 Iron. Port Email Security Manager Single view of policies for the entire organization Categories: by Domain, Username, or LDAP • Encrypt New Passwords IT • Identify & Encrypt POs SALES • Archive all mail • Encrypt mail With Outside Counsel LEGAL “Iron. Port Email Security Manager serves as a single, versatile dashboard to manage all the services on the appliance. ” – PC Magazine 62
Iron. Port Email Security Manager Single view of policies for the entire organization Categories: by Domain, Username, or LDAP • Encrypt New Passwords IT • Identify & Encrypt POs SALES • Archive all mail • Encrypt mail With Outside Counsel LEGAL “Iron. Port Email Security Manager serves as a single, versatile dashboard to manage all the services on the appliance. ” – PC Magazine 62
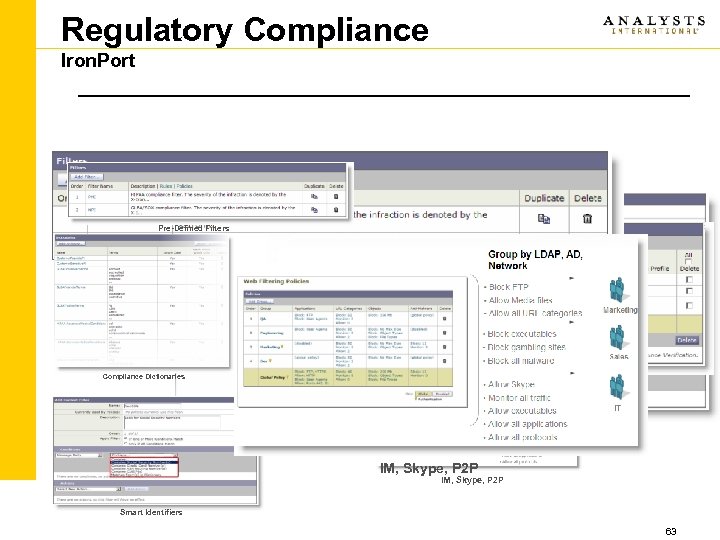 Regulatory Compliance Iron. Port Pre-Defined Filters Encryption (Message Based & TLS) Compliance Dictionaries Smart Identifiers IM, Skype, P 2 P Smart Identifiers 63
Regulatory Compliance Iron. Port Pre-Defined Filters Encryption (Message Based & TLS) Compliance Dictionaries Smart Identifiers IM, Skype, P 2 P Smart Identifiers 63
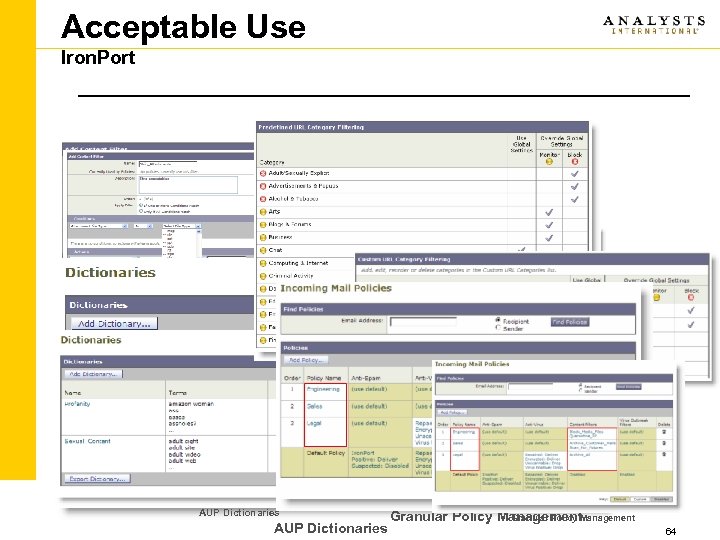 Acceptable Use Iron. Port Custom Filter Creation URL Filtering / Webmail Control Custom Filter Creation AUP Dictionaries Granular Policy Management 64
Acceptable Use Iron. Port Custom Filter Creation URL Filtering / Webmail Control Custom Filter Creation AUP Dictionaries Granular Policy Management 64
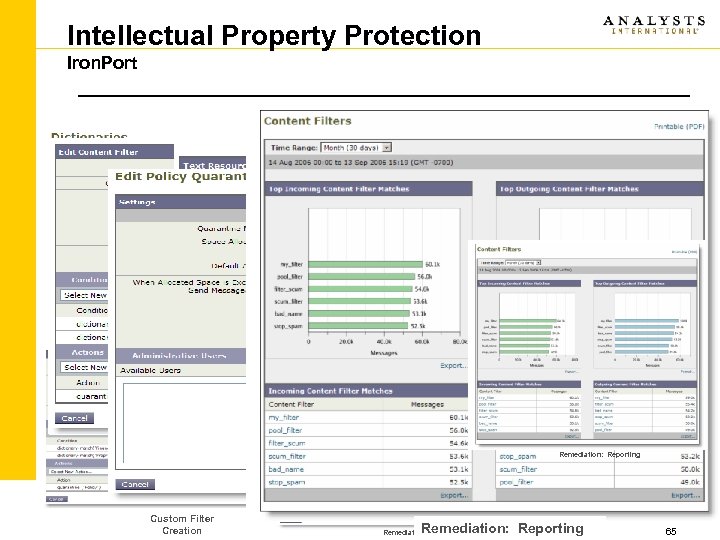 Intellectual Property Protection Iron. Port Data Leakage Dictionaries Remediation: Notification Custom Filter Creation Remediation: Reporting Remediation: Quarantine 65
Intellectual Property Protection Iron. Port Data Leakage Dictionaries Remediation: Notification Custom Filter Creation Remediation: Reporting Remediation: Quarantine 65
 CA Dept. of Alcohol & Drug Programs Data Loss Prevention via Iron. Port’s Email Security Appliances • ADP’s Challenge: – – – • The Iron. Port Solution: – – • State mandated outbound content filtering Encryption to meet HIPAA and similar regulations Prevent accidental disclosures of state data, including patient records and SSNs Secure messaging with outside partners Other needs: phishing protection, easy message retention, improved system management Iron. Port C-Series email security appliance Email Encryption Envelope Server, Iron. Port Anti-Spam, Iron. Port Virus Outbreak Filters, Sophos Anti-virus Iron. Port Results: – – Rapid deployment of Data Loss Prevention technology Ensures compliance with state and federal laws Set and forget management; little to no administrative intervention Industry leading anti-spam and anti-virus protection at the network perimeter, providing a first line of defense for Exchange servers “The selection of the Iron. Port email and encryption system fulfilled the need for a secure electronic messaging system as the department requires a secure transmission method to meet HIPAA guidelines as well as other administrative requirements. . . ” — Gary Hummel, CISSP Information Security Officer Dept. of Alcohol & Drug Programs 66
CA Dept. of Alcohol & Drug Programs Data Loss Prevention via Iron. Port’s Email Security Appliances • ADP’s Challenge: – – – • The Iron. Port Solution: – – • State mandated outbound content filtering Encryption to meet HIPAA and similar regulations Prevent accidental disclosures of state data, including patient records and SSNs Secure messaging with outside partners Other needs: phishing protection, easy message retention, improved system management Iron. Port C-Series email security appliance Email Encryption Envelope Server, Iron. Port Anti-Spam, Iron. Port Virus Outbreak Filters, Sophos Anti-virus Iron. Port Results: – – Rapid deployment of Data Loss Prevention technology Ensures compliance with state and federal laws Set and forget management; little to no administrative intervention Industry leading anti-spam and anti-virus protection at the network perimeter, providing a first line of defense for Exchange servers “The selection of the Iron. Port email and encryption system fulfilled the need for a secure electronic messaging system as the department requires a secure transmission method to meet HIPAA guidelines as well as other administrative requirements. . . ” — Gary Hummel, CISSP Information Security Officer Dept. of Alcohol & Drug Programs 66
 Iron. Port Encryption Use Cases Government q q Tax forms Land registry Defense procurement Benefit statements Header One Health Care q q q Patient Appointments Invoices Prescriptions Treatment plans Benefit statements Test results Pharmaceutical q Drug research collaboration q Test results q FDA Submissions Financial Services q q q q Trade Confirmations Broker/Agent Networks Insurance Policies Bank Statements Credit Card Statements Account Service Requests Loan/Account Applications General Operations / Finance q Order confirmations q Invoices q Purchase Orders q Payment details q PCI Compliance Legal q Contracts q Patents q Attorney-Client Privilege IT q Password seeding q Live password resets q Voicemail transcription HR q Benefits statements q Offer / pay letters q Stock option grants q Time cards q Pay slips Sales q Quotes q Product Presentations Marketing q Product roadmaps q Price lists q Promotion codes Business Development q M&A discussions q Deal negotiation Engineering / R&D q Design collaboration q Patents Copyright © 2000 -2007 Cisco Systems, Inc. All rights reserved. Iron. Port, the Iron. Port logo and Sender. Base are registered trademarks of Cisco Systems, Inc. All other trademarks are the property of Cisco Systems, Inc. or their respective owners. While every effort is made to ensure the information given is accurate, Cisco does not accept liability for any errors or mistakes which may arise. Specifications and other information in this document may be subject to change without notice. 67
Iron. Port Encryption Use Cases Government q q Tax forms Land registry Defense procurement Benefit statements Header One Health Care q q q Patient Appointments Invoices Prescriptions Treatment plans Benefit statements Test results Pharmaceutical q Drug research collaboration q Test results q FDA Submissions Financial Services q q q q Trade Confirmations Broker/Agent Networks Insurance Policies Bank Statements Credit Card Statements Account Service Requests Loan/Account Applications General Operations / Finance q Order confirmations q Invoices q Purchase Orders q Payment details q PCI Compliance Legal q Contracts q Patents q Attorney-Client Privilege IT q Password seeding q Live password resets q Voicemail transcription HR q Benefits statements q Offer / pay letters q Stock option grants q Time cards q Pay slips Sales q Quotes q Product Presentations Marketing q Product roadmaps q Price lists q Promotion codes Business Development q M&A discussions q Deal negotiation Engineering / R&D q Design collaboration q Patents Copyright © 2000 -2007 Cisco Systems, Inc. All rights reserved. Iron. Port, the Iron. Port logo and Sender. Base are registered trademarks of Cisco Systems, Inc. All other trademarks are the property of Cisco Systems, Inc. or their respective owners. While every effort is made to ensure the information given is accurate, Cisco does not accept liability for any errors or mistakes which may arise. Specifications and other information in this document may be subject to change without notice. 67
 Iron. Port Security Appliances Integrated Security Appliances For The Network Perimeter • • L 4 traffic monitor inspects all traffic Web reputation for preventive filtering Integrated complete content inspection Data Loss Prevention Iron. Port S-Series WEB SECURITY APPLIANCE • • + Multi Layer Spam Protection Industry Leading Virus Protection Data Loss Prevention Unmatched Performance Iron. Port C-Series EMAIL SECURITY APPLIANCE 68
Iron. Port Security Appliances Integrated Security Appliances For The Network Perimeter • • L 4 traffic monitor inspects all traffic Web reputation for preventive filtering Integrated complete content inspection Data Loss Prevention Iron. Port S-Series WEB SECURITY APPLIANCE • • + Multi Layer Spam Protection Industry Leading Virus Protection Data Loss Prevention Unmatched Performance Iron. Port C-Series EMAIL SECURITY APPLIANCE 68
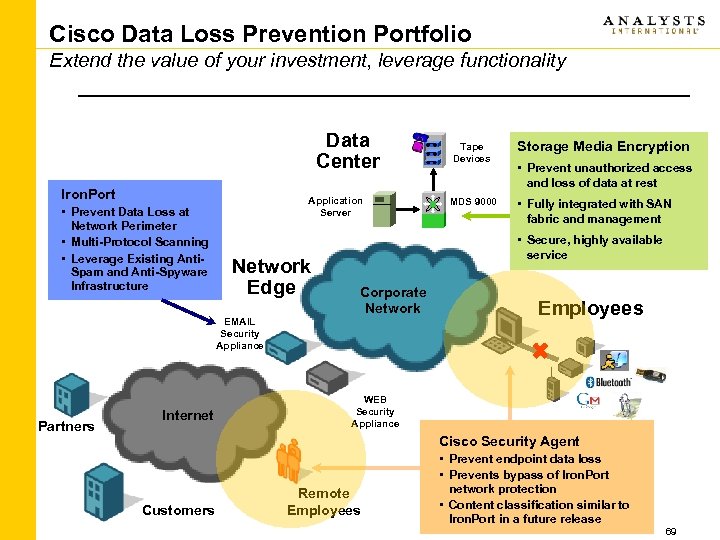 Cisco Data Loss Prevention Portfolio Extend the value of your investment, leverage functionality Data Center Iron. Port • Prevent Data Loss at Network Perimeter • Multi-Protocol Scanning • Leverage Existing Anti. Spam and Anti-Spyware Infrastructure Application Server Network Edge Internet Storage Media Encryption MDS 9000 • Fully integrated with SAN fabric and management • Prevent unauthorized access and loss of data at rest • Secure, highly available service Corporate Network EMAIL Security Appliance Partners Tape Devices Employees WEB Security Appliance Cisco Security Agent Customers Remote Employees • Prevent endpoint data loss • Prevents bypass of Iron. Port network protection • Content classification similar to Iron. Port in a future release 69
Cisco Data Loss Prevention Portfolio Extend the value of your investment, leverage functionality Data Center Iron. Port • Prevent Data Loss at Network Perimeter • Multi-Protocol Scanning • Leverage Existing Anti. Spam and Anti-Spyware Infrastructure Application Server Network Edge Internet Storage Media Encryption MDS 9000 • Fully integrated with SAN fabric and management • Prevent unauthorized access and loss of data at rest • Secure, highly available service Corporate Network EMAIL Security Appliance Partners Tape Devices Employees WEB Security Appliance Cisco Security Agent Customers Remote Employees • Prevent endpoint data loss • Prevents bypass of Iron. Port network protection • Content classification similar to Iron. Port in a future release 69
 Concern: Endpoint Data is Mobile • How is data mobile? – USB, Floppy, CD Burner – SSL encrypted transfers – Webmail, p 2 p, IM – Cut and Paste – Dial-up modem, Bluetooth, IRDA interfaces • What’s the concern? – Protecting Intellectual Property stored on the endpoint – Demonstrating that regulated data is properly controlled – Auditing and enforcing corporate use policies for data on laptops 70
Concern: Endpoint Data is Mobile • How is data mobile? – USB, Floppy, CD Burner – SSL encrypted transfers – Webmail, p 2 p, IM – Cut and Paste – Dial-up modem, Bluetooth, IRDA interfaces • What’s the concern? – Protecting Intellectual Property stored on the endpoint – Demonstrating that regulated data is properly controlled – Auditing and enforcing corporate use policies for data on laptops 70
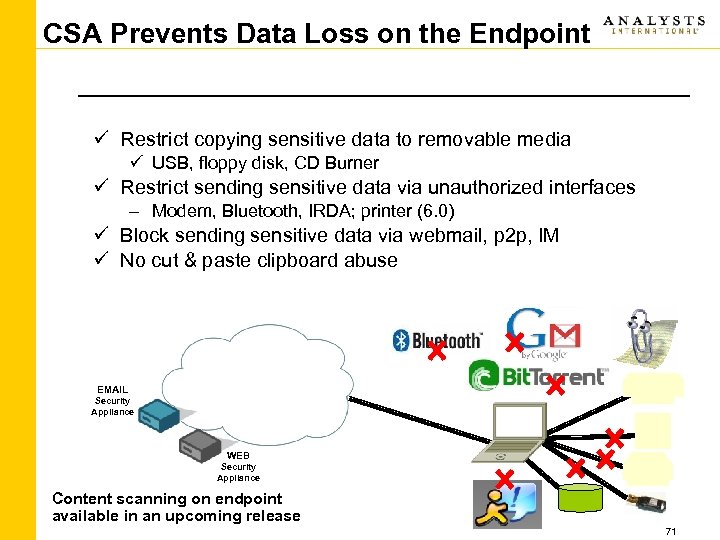 CSA Prevents Data Loss on the Endpoint ü Restrict copying sensitive data to removable media ü USB, floppy disk, CD Burner ü Restrict sending sensitive data via unauthorized interfaces – Modem, Bluetooth, IRDA; printer (6. 0) ü Block sending sensitive data via webmail, p 2 p, IM ü No cut & paste clipboard abuse EMAIL Security Appliance WEB Security Appliance Content scanning on endpoint available in an upcoming release 71
CSA Prevents Data Loss on the Endpoint ü Restrict copying sensitive data to removable media ü USB, floppy disk, CD Burner ü Restrict sending sensitive data via unauthorized interfaces – Modem, Bluetooth, IRDA; printer (6. 0) ü Block sending sensitive data via webmail, p 2 p, IM ü No cut & paste clipboard abuse EMAIL Security Appliance WEB Security Appliance Content scanning on endpoint available in an upcoming release 71
 Removable Media Controls • • • Controls for USB drives, CD, i. Pod Monitor usage Confidential file controls Authorized user controls Location-based controls End user Business Justification for audits Consolidated event reporting of USB usage 72
Removable Media Controls • • • Controls for USB drives, CD, i. Pod Monitor usage Confidential file controls Authorized user controls Location-based controls End user Business Justification for audits Consolidated event reporting of USB usage 72
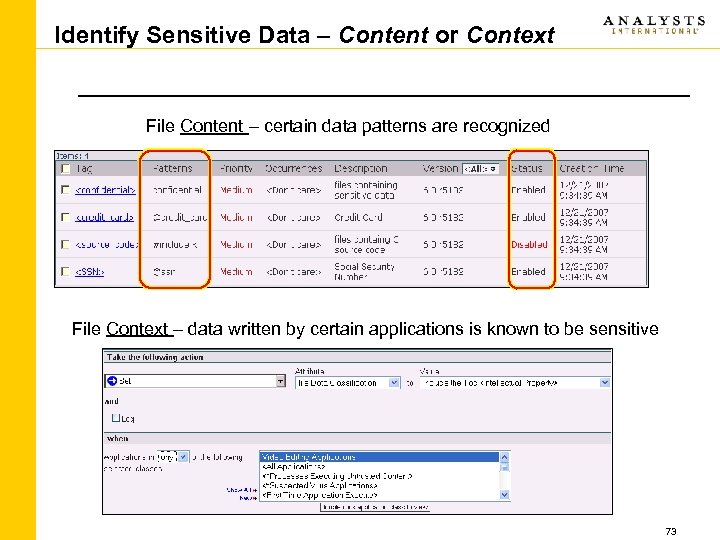 Identify Sensitive Data – Content or Context File Content – certain data patterns are recognized File Context – data written by certain applications is known to be sensitive 73
Identify Sensitive Data – Content or Context File Content – certain data patterns are recognized File Context – data written by certain applications is known to be sensitive 73
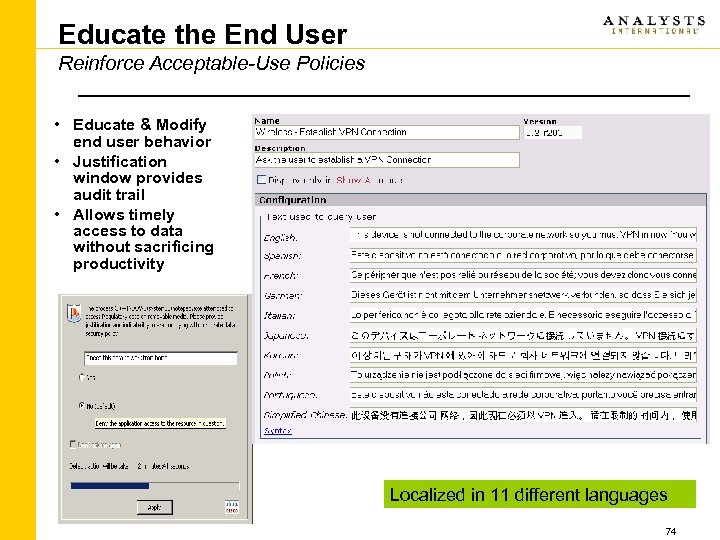 Educate the End User Reinforce Acceptable-Use Policies • Educate & Modify end user behavior • Justification window provides audit trail • Allows timely access to data without sacrificing productivity Localized in 11 different languages 74
Educate the End User Reinforce Acceptable-Use Policies • Educate & Modify end user behavior • Justification window provides audit trail • Allows timely access to data without sacrificing productivity Localized in 11 different languages 74
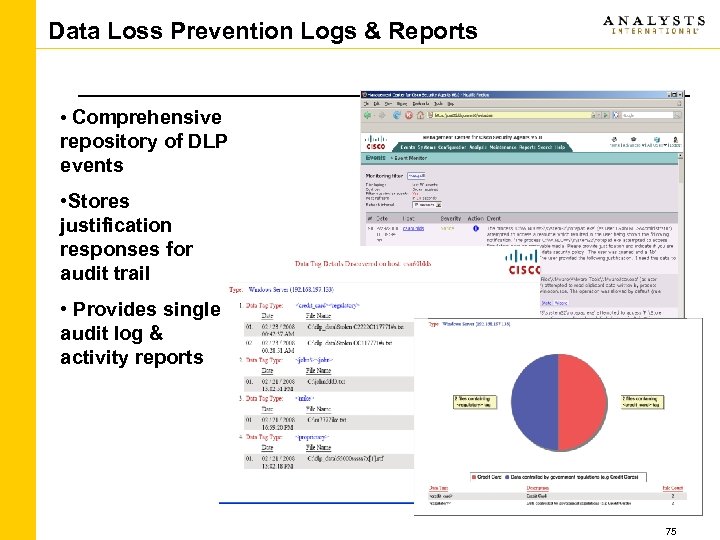 Data Loss Prevention Logs & Reports • Comprehensive repository of DLP events • Stores justification responses for audit trail • Provides single audit log & activity reports 75
Data Loss Prevention Logs & Reports • Comprehensive repository of DLP events • Stores justification responses for audit trail • Provides single audit log & activity reports 75
 Concern: Endpoint Users are Mobile • When are users mobile? – Working from home – During trips at hotels and business partners – Daily with public and retail hotspots • What’s the concern? – Continuity of data mobility controls when not in the office – Ensuring corporate network data security protections cannot be bypassed 76
Concern: Endpoint Users are Mobile • When are users mobile? – Working from home – During trips at hotels and business partners – Daily with public and retail hotspots • What’s the concern? – Continuity of data mobility controls when not in the office – Ensuring corporate network data security protections cannot be bypassed 76
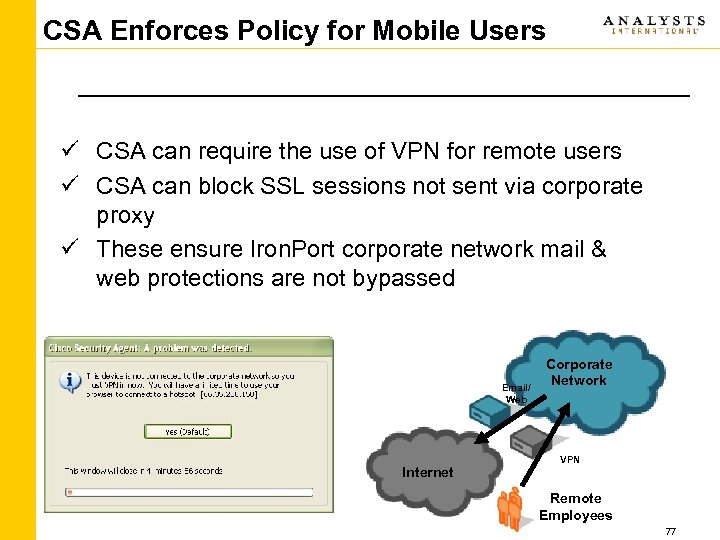 CSA Enforces Policy for Mobile Users ü CSA can require the use of VPN for remote users ü CSA can block SSL sessions not sent via corporate proxy ü These ensure Iron. Port corporate network mail & web protections are not bypassed Email/ Web Internet Corporate Network VPN Remote Employees 77
CSA Enforces Policy for Mobile Users ü CSA can require the use of VPN for remote users ü CSA can block SSL sessions not sent via corporate proxy ü These ensure Iron. Port corporate network mail & web protections are not bypassed Email/ Web Internet Corporate Network VPN Remote Employees 77
 Colorado State Employees Credit Union Data Loss Prevention via Cisco Security Agent • Colorado State’s Challenge: – Concerned about Data Loss Prevention – Needed a way to secure employee laptops, disk drives, USB flash drives and CD-ROMs • The Cisco Security Agent Solution: – Cisco Security Agent deployed on their endpoints – Cisco Security Agent disables the usage of USB ports – Cisco Security Agent allows only authorized users such as IT to write to flash drives – Cisco Security Agent mandates that all file storage must be done in secure encrypted partitions • Cisco Security Agent Results: – Mandates compliance to Colorado State’s established security policy – Ensures compliance to State and federal laws for credit unions “USB ports are disabled using the Cisco Security Agent, so only certain people such as IT can write to flash drives. We usually don’t encrypt the entire drive on users’ laptops, but do provide secure storage areas so that end users can just save the files to that location and they will always be encrypted. ” — Tom Gonzales, Senior Network Administrator Colorado State Employees Credit Union 78
Colorado State Employees Credit Union Data Loss Prevention via Cisco Security Agent • Colorado State’s Challenge: – Concerned about Data Loss Prevention – Needed a way to secure employee laptops, disk drives, USB flash drives and CD-ROMs • The Cisco Security Agent Solution: – Cisco Security Agent deployed on their endpoints – Cisco Security Agent disables the usage of USB ports – Cisco Security Agent allows only authorized users such as IT to write to flash drives – Cisco Security Agent mandates that all file storage must be done in secure encrypted partitions • Cisco Security Agent Results: – Mandates compliance to Colorado State’s established security policy – Ensures compliance to State and federal laws for credit unions “USB ports are disabled using the Cisco Security Agent, so only certain people such as IT can write to flash drives. We usually don’t encrypt the entire drive on users’ laptops, but do provide secure storage areas so that end users can just save the files to that location and they will always be encrypted. ” — Tom Gonzales, Senior Network Administrator Colorado State Employees Credit Union 78
 Intrusion Prevention “Zero Update” Track Record • CSA has a proven track record of stopping brand new exploits, botnets, targeted attacks, worms, and viruses over past 7 years: 2001 – Code Red, Nimda (all 5 exploits), Pentagone (Gonner) 2002 – Sircam, Debploit, SQL Snake, Bugbear, 2003 – SQL Slammer, So Big, Blaster/Welchia, Fizzer 2004 – My. Doom, Bagle, Sasser, JPEG browser exploit (MS 04 -028), RPCDCOM exploit (MS 03 -039), Buffer Overflow in Workstation service (MS 03049) 2005 – Internet Explorer Command Execution Vulnerability, Zotob 2006 – USB Hacksaw, IE VML exploit, WMF, IE Textrange, RDS Dataspace 2007 – Rinbot, Storm Trojan, Big Yellow, Word(MS 07 -014), MS ANI 0 Day, MS DNS 0 Day No signatures, or configuration updates required 79
Intrusion Prevention “Zero Update” Track Record • CSA has a proven track record of stopping brand new exploits, botnets, targeted attacks, worms, and viruses over past 7 years: 2001 – Code Red, Nimda (all 5 exploits), Pentagone (Gonner) 2002 – Sircam, Debploit, SQL Snake, Bugbear, 2003 – SQL Slammer, So Big, Blaster/Welchia, Fizzer 2004 – My. Doom, Bagle, Sasser, JPEG browser exploit (MS 04 -028), RPCDCOM exploit (MS 03 -039), Buffer Overflow in Workstation service (MS 03049) 2005 – Internet Explorer Command Execution Vulnerability, Zotob 2006 – USB Hacksaw, IE VML exploit, WMF, IE Textrange, RDS Dataspace 2007 – Rinbot, Storm Trojan, Big Yellow, Word(MS 07 -014), MS ANI 0 Day, MS DNS 0 Day No signatures, or configuration updates required 79
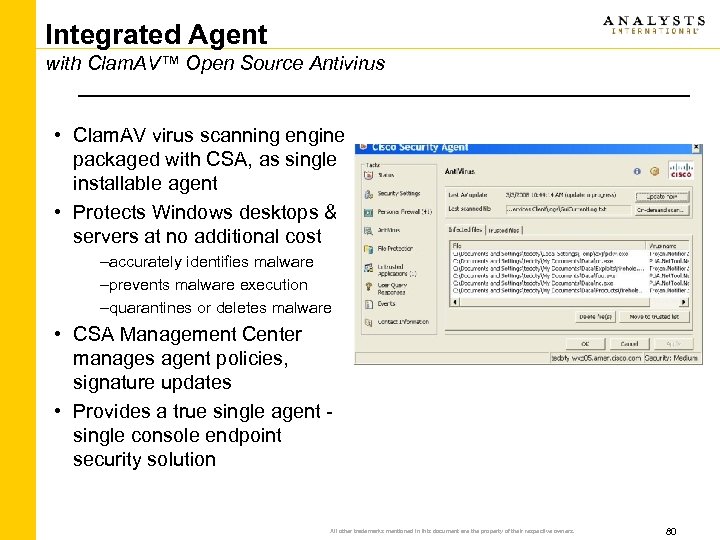 Integrated Agent with Clam. AV™ Open Source Antivirus • Clam. AV virus scanning engine packaged with CSA, as single installable agent • Protects Windows desktops & servers at no additional cost –accurately identifies malware –prevents malware execution –quarantines or deletes malware • CSA Management Center manages agent policies, signature updates • Provides a true single agent single console endpoint security solution All other trademarks mentioned in this document are the property of their respective owners. 80
Integrated Agent with Clam. AV™ Open Source Antivirus • Clam. AV virus scanning engine packaged with CSA, as single installable agent • Protects Windows desktops & servers at no additional cost –accurately identifies malware –prevents malware execution –quarantines or deletes malware • CSA Management Center manages agent policies, signature updates • Provides a true single agent single console endpoint security solution All other trademarks mentioned in this document are the property of their respective owners. 80
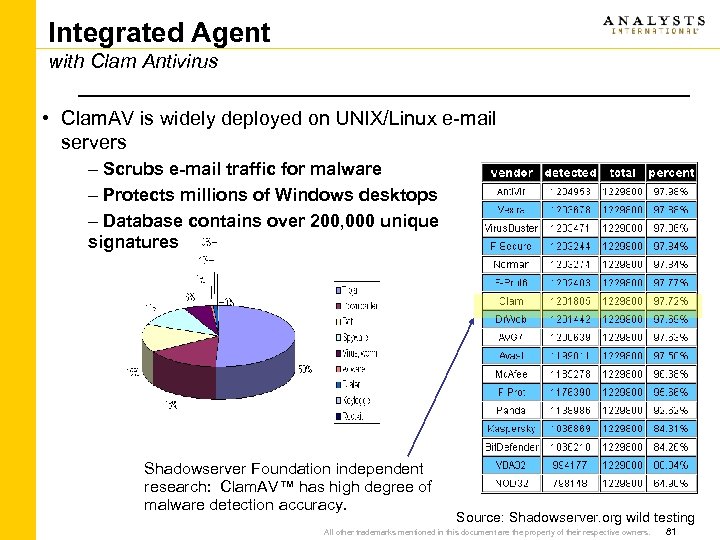 Integrated Agent with Clam Antivirus • Clam. AV is widely deployed on UNIX/Linux e-mail servers – Scrubs e-mail traffic for malware – Protects millions of Windows desktops – Database contains over 200, 000 unique signatures Shadowserver Foundation independent research: Clam. AV™ has high degree of malware detection accuracy. Source: Shadowserver. org wild testing All other trademarks mentioned in this document are the property of their respective owners. 81
Integrated Agent with Clam Antivirus • Clam. AV is widely deployed on UNIX/Linux e-mail servers – Scrubs e-mail traffic for malware – Protects millions of Windows desktops – Database contains over 200, 000 unique signatures Shadowserver Foundation independent research: Clam. AV™ has high degree of malware detection accuracy. Source: Shadowserver. org wild testing All other trademarks mentioned in this document are the property of their respective owners. 81
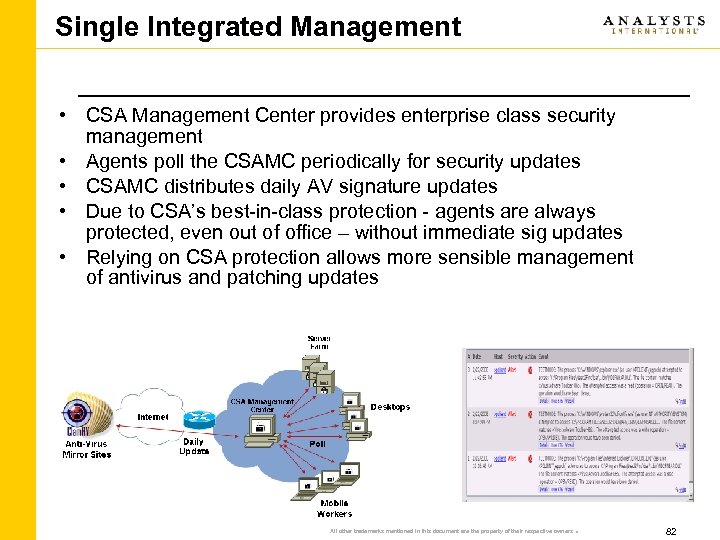 Single Integrated Management • CSA Management Center provides enterprise class security management • Agents poll the CSAMC periodically for security updates • CSAMC distributes daily AV signature updates • Due to CSA’s best-in-class protection - agents are always protected, even out of office – without immediate sig updates • Relying on CSA protection allows more sensible management of antivirus and patching updates All other trademarks mentioned in this document are the property of their respective owners . 82
Single Integrated Management • CSA Management Center provides enterprise class security management • Agents poll the CSAMC periodically for security updates • CSAMC distributes daily AV signature updates • Due to CSA’s best-in-class protection - agents are always protected, even out of office – without immediate sig updates • Relying on CSA protection allows more sensible management of antivirus and patching updates All other trademarks mentioned in this document are the property of their respective owners . 82
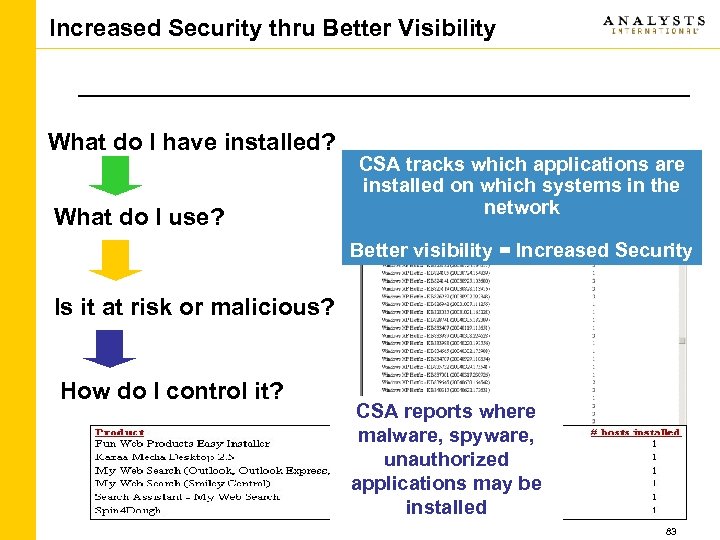 Increased Security thru Better Visibility What do I have installed? What do I use? CSA tracks which applications are installed on which systems in the network Better visibility = Increased Security Is it at risk or malicious? How do I control it? CSA reports where malware, spyware, unauthorized applications may be installed 83
Increased Security thru Better Visibility What do I have installed? What do I use? CSA tracks which applications are installed on which systems in the network Better visibility = Increased Security Is it at risk or malicious? How do I control it? CSA reports where malware, spyware, unauthorized applications may be installed 83
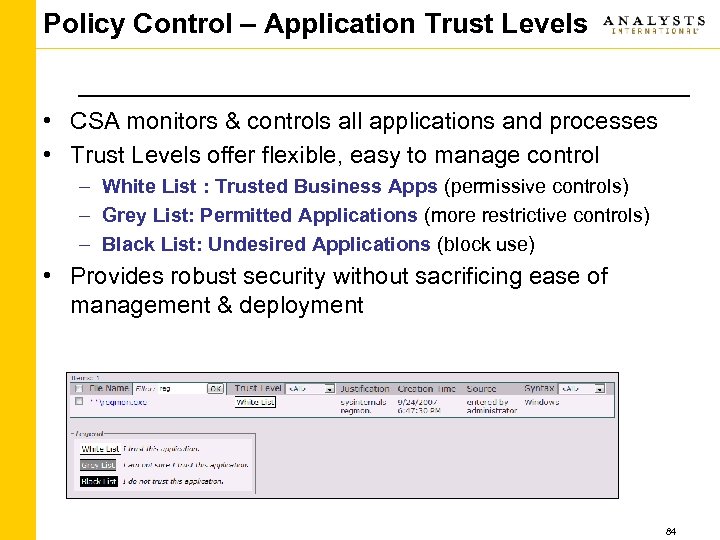 Policy Control – Application Trust Levels • CSA monitors & controls all applications and processes • Trust Levels offer flexible, easy to manage control – White List : Trusted Business Apps (permissive controls) – Grey List: Permitted Applications (more restrictive controls) – Black List: Undesired Applications (block use) • Provides robust security without sacrificing ease of management & deployment 84
Policy Control – Application Trust Levels • CSA monitors & controls all applications and processes • Trust Levels offer flexible, easy to manage control – White List : Trusted Business Apps (permissive controls) – Grey List: Permitted Applications (more restrictive controls) – Black List: Undesired Applications (block use) • Provides robust security without sacrificing ease of management & deployment 84
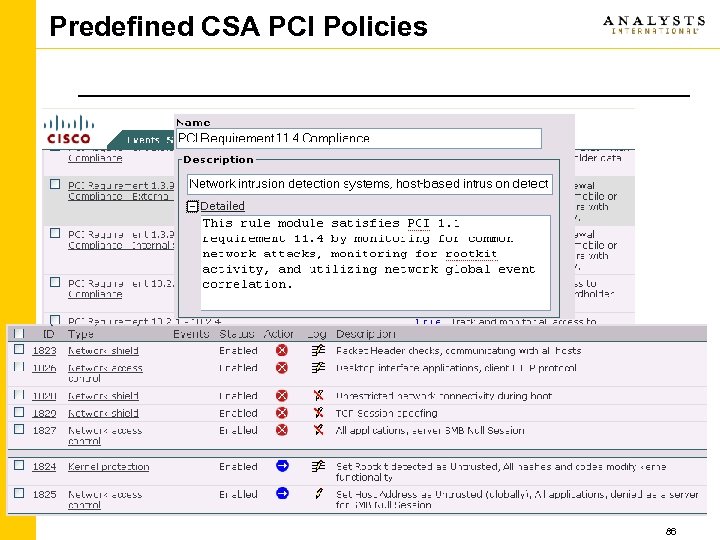
 Regulatory Compliance Benefits for PCI Compliance • Provides compliance solution for 9 out of 12 PCI requirements • Predefined PCI Policies offer ease of management & audit – 26 Rule Modules, 150 rules • Validated by Cybertrust (official PCI auditor) • Runs on Servers, Point-Of-Sale terminals, desktops and laptops • CSA can be customized for other compliance mandates http: //www. cisco. com/go/retail 85
Regulatory Compliance Benefits for PCI Compliance • Provides compliance solution for 9 out of 12 PCI requirements • Predefined PCI Policies offer ease of management & audit – 26 Rule Modules, 150 rules • Validated by Cybertrust (official PCI auditor) • Runs on Servers, Point-Of-Sale terminals, desktops and laptops • CSA can be customized for other compliance mandates http: //www. cisco. com/go/retail 85
 Predefined CSA PCI Policies 86
Predefined CSA PCI Policies 86
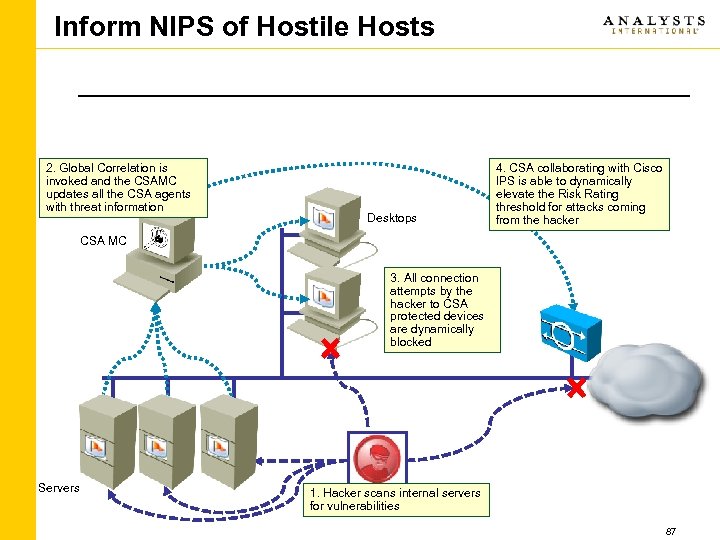 Inform NIPS of Hostile Hosts 2. Global Correlation is invoked and the CSAMC updates all the CSA agents with threat information Desktops 4. CSA collaborating with Cisco IPS is able to dynamically elevate the Risk Rating threshold for attacks coming from the hacker CSA MC 3. All connection attempts by the hacker to CSA protected devices are dynamically blocked Servers 1. Hacker scans internal servers for vulnerabilities 87
Inform NIPS of Hostile Hosts 2. Global Correlation is invoked and the CSAMC updates all the CSA agents with threat information Desktops 4. CSA collaborating with Cisco IPS is able to dynamically elevate the Risk Rating threshold for attacks coming from the hacker CSA MC 3. All connection attempts by the hacker to CSA protected devices are dynamically blocked Servers 1. Hacker scans internal servers for vulnerabilities 87
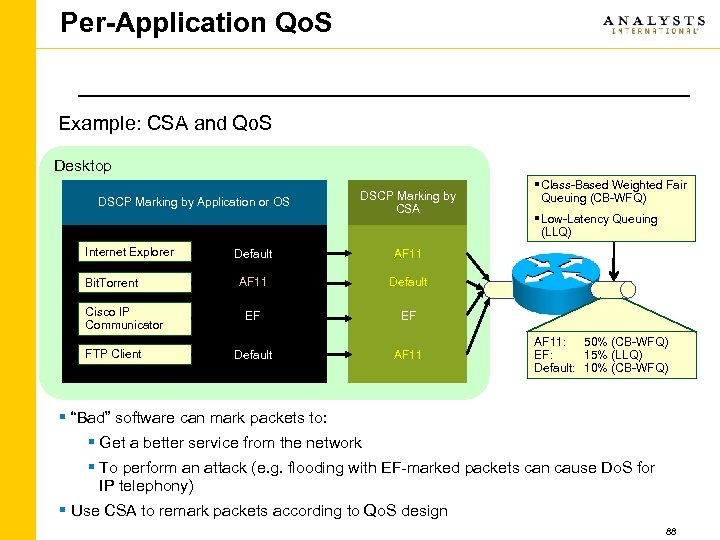 Per-Application Qo. S Example: CSA and Qo. S Desktop DSCP Marking by Application or OS Internet Explorer Bit. Torrent Cisco IP Communicator FTP Client DSCP Marking by CSA Default EF EF Default AF 11 § Low-Latency Queuing (LLQ) AF 11 § Class-Based Weighted Fair Queuing (CB-WFQ) AF 11: 50% (CB-WFQ) EF: 15% (LLQ) Default: 10% (CB-WFQ) § “Bad” software can mark packets to: § Get a better service from the network § To perform an attack (e. g. flooding with EF-marked packets can cause Do. S for IP telephony) § Use CSA to remark packets according to Qo. S design 88
Per-Application Qo. S Example: CSA and Qo. S Desktop DSCP Marking by Application or OS Internet Explorer Bit. Torrent Cisco IP Communicator FTP Client DSCP Marking by CSA Default EF EF Default AF 11 § Low-Latency Queuing (LLQ) AF 11 § Class-Based Weighted Fair Queuing (CB-WFQ) AF 11: 50% (CB-WFQ) EF: 15% (LLQ) Default: 10% (CB-WFQ) § “Bad” software can mark packets to: § Get a better service from the network § To perform an attack (e. g. flooding with EF-marked packets can cause Do. S for IP telephony) § Use CSA to remark packets according to Qo. S design 88
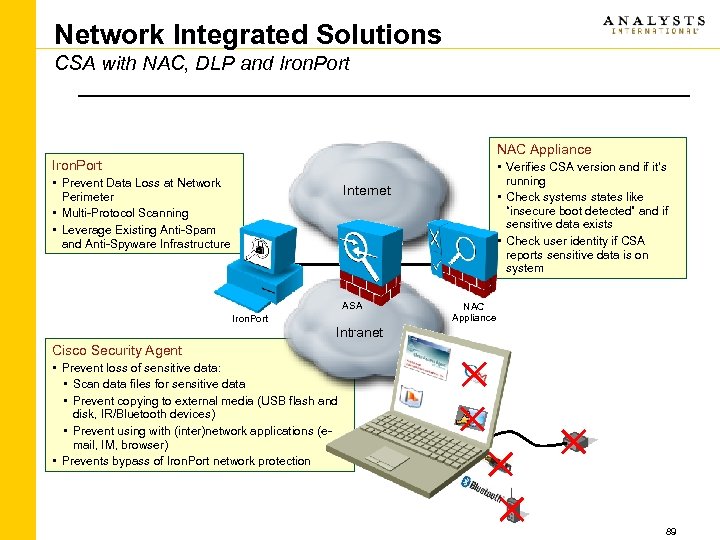 Network Integrated Solutions CSA with NAC, DLP and Iron. Port NAC Appliance Iron. Port • Prevent Data Loss at Network Perimeter • Multi-Protocol Scanning • Leverage Existing Anti-Spam and Anti-Spyware Infrastructure • Verifies CSA version and if it’s running • Check systems states like “insecure boot detected” and if sensitive data exists • Check user identity if CSA reports sensitive data is on system Internet ASA Iron. Port NAC Appliance Intranet Cisco Security Agent • Prevent loss of sensitive data: • Scan data files for sensitive data • Prevent copying to external media (USB flash and disk, IR/Bluetooth devices) • Prevent using with (inter)network applications (email, IM, browser) • Prevents bypass of Iron. Port network protection 89
Network Integrated Solutions CSA with NAC, DLP and Iron. Port NAC Appliance Iron. Port • Prevent Data Loss at Network Perimeter • Multi-Protocol Scanning • Leverage Existing Anti-Spam and Anti-Spyware Infrastructure • Verifies CSA version and if it’s running • Check systems states like “insecure boot detected” and if sensitive data exists • Check user identity if CSA reports sensitive data is on system Internet ASA Iron. Port NAC Appliance Intranet Cisco Security Agent • Prevent loss of sensitive data: • Scan data files for sensitive data • Prevent copying to external media (USB flash and disk, IR/Bluetooth devices) • Prevent using with (inter)network applications (email, IM, browser) • Prevents bypass of Iron. Port network protection 89
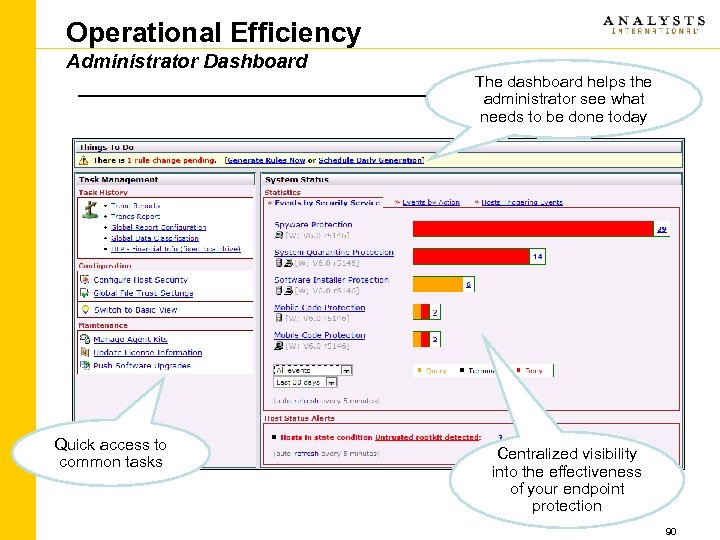 Operational Efficiency Administrator Dashboard The dashboard helps the administrator see what needs to be done today Quick access to common tasks Centralized visibility into the effectiveness of your endpoint protection 90
Operational Efficiency Administrator Dashboard The dashboard helps the administrator see what needs to be done today Quick access to common tasks Centralized visibility into the effectiveness of your endpoint protection 90
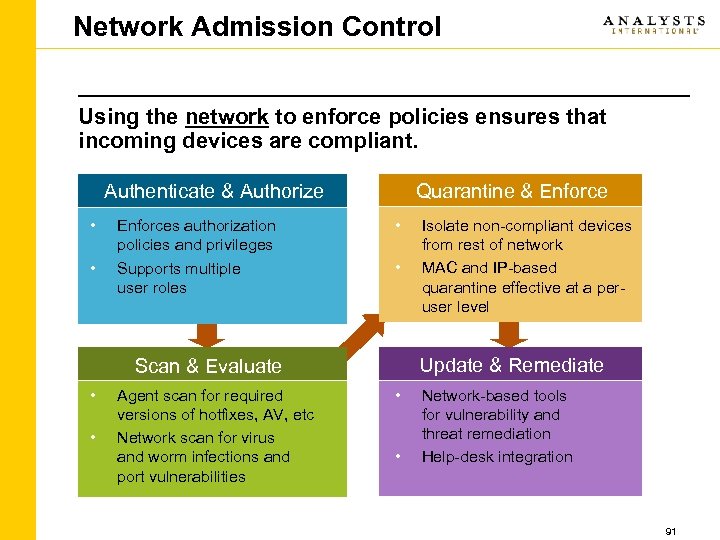 Network Admission Control Using the network to enforce policies ensures that incoming devices are compliant. Authenticate & Authorize • • Enforces authorization policies and privileges Supports multiple user roles Quarantine & Enforce • • Update & Remediate Scan & Evaluate • • Agent scan for required versions of hotfixes, AV, etc Network scan for virus and worm infections and port vulnerabilities Isolate non-compliant devices from rest of network MAC and IP-based quarantine effective at a peruser level • • Network-based tools for vulnerability and threat remediation Help-desk integration 91
Network Admission Control Using the network to enforce policies ensures that incoming devices are compliant. Authenticate & Authorize • • Enforces authorization policies and privileges Supports multiple user roles Quarantine & Enforce • • Update & Remediate Scan & Evaluate • • Agent scan for required versions of hotfixes, AV, etc Network scan for virus and worm infections and port vulnerabilities Isolate non-compliant devices from rest of network MAC and IP-based quarantine effective at a peruser level • • Network-based tools for vulnerability and threat remediation Help-desk integration 91
 Cisco NAC Partnerships Cisco NAC is committed to protecting customer’s investments in partner applications Cisco NAC Supports Policies for 300+ Applications, Including these Vendors: 92
Cisco NAC Partnerships Cisco NAC is committed to protecting customer’s investments in partner applications Cisco NAC Supports Policies for 300+ Applications, Including these Vendors: 92
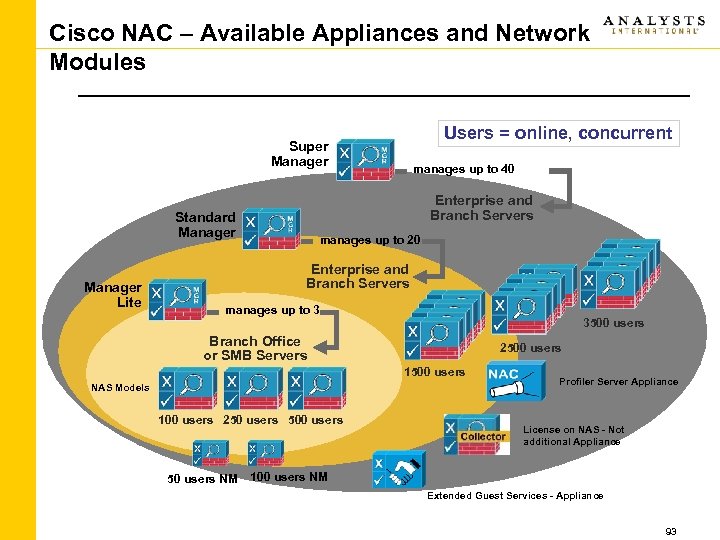 Cisco NAC – Available Appliances and Network Modules Users = online, concurrent Super Manager Enterprise and Branch Servers Standard Manager Lite manages up to 40 manages up to 20 Enterprise and Branch Servers manages up to 3 3500 users Branch Office or SMB Servers 2500 users 1500 users NAS Models 100 users 250 users NM Profiler Server Appliance License on NAS - Not additional Appliance 100 users NM Extended Guest Services - Appliance 93
Cisco NAC – Available Appliances and Network Modules Users = online, concurrent Super Manager Enterprise and Branch Servers Standard Manager Lite manages up to 40 manages up to 20 Enterprise and Branch Servers manages up to 3 3500 users Branch Office or SMB Servers 2500 users 1500 users NAS Models 100 users 250 users NM Profiler Server Appliance License on NAS - Not additional Appliance 100 users NM Extended Guest Services - Appliance 93
 Section 4 – Managing Data Loss – Analysts Solutions Mark Lachniet, Solutions Architect – Analysts International Lansing, MI July 15 th, 2008
Section 4 – Managing Data Loss – Analysts Solutions Mark Lachniet, Solutions Architect – Analysts International Lansing, MI July 15 th, 2008
 Analysts International Security Services • Analysts International staffs engineers and consultants dedicated entirely to security services • This includes a wide range of functions including policy development, incident response/forensics, security assessments, hardware and software installation and configuration, etc. • Includes both preventative and reactive services, should they be necessary • Analysts International’s security engineers/consultants specialize in various compliance areas such as PCI, HIPPA, GLBA and DIACAP 95
Analysts International Security Services • Analysts International staffs engineers and consultants dedicated entirely to security services • This includes a wide range of functions including policy development, incident response/forensics, security assessments, hardware and software installation and configuration, etc. • Includes both preventative and reactive services, should they be necessary • Analysts International’s security engineers/consultants specialize in various compliance areas such as PCI, HIPPA, GLBA and DIACAP 95
 Policy and Procedure Development • If you are interested in getting help with developing your policies, practices and procedures, Analysts can assign a consultant who can work with you to help • Every organization is different, and one size does not fit all • We have helped other organizations create the same procedures (e. g. Information Classification, Incident Response, Log Review) that are discussed in this seminar • In addition, we have worked with many organizations to create security policies such as: – – – Acceptable Use Policies Remote access policies Security device minimum standards / baseline configs Wireless security policies And many more 96
Policy and Procedure Development • If you are interested in getting help with developing your policies, practices and procedures, Analysts can assign a consultant who can work with you to help • Every organization is different, and one size does not fit all • We have helped other organizations create the same procedures (e. g. Information Classification, Incident Response, Log Review) that are discussed in this seminar • In addition, we have worked with many organizations to create security policies such as: – – – Acceptable Use Policies Remote access policies Security device minimum standards / baseline configs Wireless security policies And many more 96
 Incident Response Services • In the unfortunate event that you suspect you have been hacked or had a breach, Analysts can help you to determine the scope of an incident and its possible ramifications • Tracking attacks through multiple firewalls, routers, Windows and UNIX servers, databases and applications is time consuming and technically demanding • We can assist you with to: – – – Minimize the disruption to your organization Find out what happened Identify short-term recovery and mitigation strategies Create reports on the scope and nature of the incident Identify long-term improvements that will reduce future risk Interface with Law enforcement and legal counsel as needed 97
Incident Response Services • In the unfortunate event that you suspect you have been hacked or had a breach, Analysts can help you to determine the scope of an incident and its possible ramifications • Tracking attacks through multiple firewalls, routers, Windows and UNIX servers, databases and applications is time consuming and technically demanding • We can assist you with to: – – – Minimize the disruption to your organization Find out what happened Identify short-term recovery and mitigation strategies Create reports on the scope and nature of the incident Identify long-term improvements that will reduce future risk Interface with Law enforcement and legal counsel as needed 97
 Administrator Termination Services • In the event that you need to terminate an I. T. employee with significant levels of access • Often used in “hostile” departures such as employees being fired • Also used by organizations as a best practice to create a reusable termination procedure in low-risk departures • Analysts’ staff will work with you to: – – – Evaluate the risk posed by the departing employee Participate in exit interviews if desired Identify physical and intellectual property to be retrieved Identify systems that the individual may have had access to Create a list of tasks that will need to be performed such as changing passwords, contacting vendors and partners, updating software, etc. – Analyze systems for “time bombs” or other evidence of abuse – Change passwords on servers, network devices, remote access systems, telephony systems, etc. 98
Administrator Termination Services • In the event that you need to terminate an I. T. employee with significant levels of access • Often used in “hostile” departures such as employees being fired • Also used by organizations as a best practice to create a reusable termination procedure in low-risk departures • Analysts’ staff will work with you to: – – – Evaluate the risk posed by the departing employee Participate in exit interviews if desired Identify physical and intellectual property to be retrieved Identify systems that the individual may have had access to Create a list of tasks that will need to be performed such as changing passwords, contacting vendors and partners, updating software, etc. – Analyze systems for “time bombs” or other evidence of abuse – Change passwords on servers, network devices, remote access systems, telephony systems, etc. 98
 Vulnerability Assessments • Internet Security Assessment Service (ISAS) used to scan Internet-accessible servers for security flaws that could be used to breach security • On-Site Assessment Service (OSAS) used to scan Internal servers for security flaws that could be used by a malicious employee or partner, or exploited by automated systems such as worms • Web Application Security Assessment (WASA) used to analyze web applications for security flaws that could lead to a hack of sensitive back-end databases or trusted systems • Customized assessments of products and systems such as security appliances, Citrix systems, wireless devices, etc. can also be performed as needed 99
Vulnerability Assessments • Internet Security Assessment Service (ISAS) used to scan Internet-accessible servers for security flaws that could be used to breach security • On-Site Assessment Service (OSAS) used to scan Internal servers for security flaws that could be used by a malicious employee or partner, or exploited by automated systems such as worms • Web Application Security Assessment (WASA) used to analyze web applications for security flaws that could lead to a hack of sensitive back-end databases or trusted systems • Customized assessments of products and systems such as security appliances, Citrix systems, wireless devices, etc. can also be performed as needed 99
 Security Needs Assessment Service (SNAS) • The SNAS process is intended to be a wide-ranging review of security practices and procedures • Primarily based on discussions and reviews of documentation • Often used when an organization wants to get a “check up” on their current posture, or wants to identify the most important areas to focus on for security • Yearly third-party security audits are frequently required by financial auditors • Often customized to address specific concerns such as compliance with a specific regulation such as GLBA, NCUA, Michigan Gaming Control Board, etc. • Provides a detailed deliverable with a security ranking matrix that maps each recommendation on a cost vs. gain matrix, so you can quickly identify the “low hanging fruit” 100
Security Needs Assessment Service (SNAS) • The SNAS process is intended to be a wide-ranging review of security practices and procedures • Primarily based on discussions and reviews of documentation • Often used when an organization wants to get a “check up” on their current posture, or wants to identify the most important areas to focus on for security • Yearly third-party security audits are frequently required by financial auditors • Often customized to address specific concerns such as compliance with a specific regulation such as GLBA, NCUA, Michigan Gaming Control Board, etc. • Provides a detailed deliverable with a security ranking matrix that maps each recommendation on a cost vs. gain matrix, so you can quickly identify the “low hanging fruit” 100
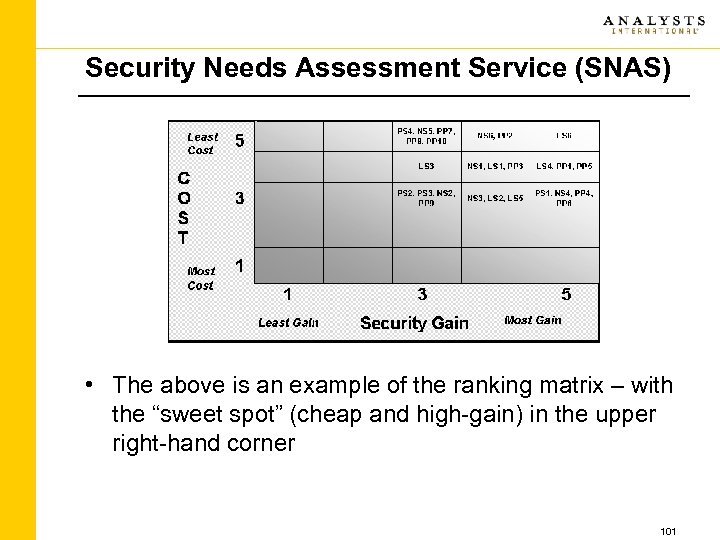 Security Needs Assessment Service (SNAS) • The above is an example of the ranking matrix – with the “sweet spot” (cheap and high-gain) in the upper right-hand corner 101
Security Needs Assessment Service (SNAS) • The above is an example of the ranking matrix – with the “sweet spot” (cheap and high-gain) in the upper right-hand corner 101
 Questions, Comments and Discussion Contacts Analysts International Cisco Systems Mark Lachniet Solutions Architect mlachniet@analysts. com (517) 336 -1004 (office) Bret Straffon PSS - Security bstraffo@cisco. com (248) 455 -1737 (office) Lance Miller Security Practice Director lmiller@analysts. com (248) 232 -5322 (office) Scott Maxwell CAM – Cisco Channel scmaxwel@cisco. com (614) 718 2784 (office) 102
Questions, Comments and Discussion Contacts Analysts International Cisco Systems Mark Lachniet Solutions Architect mlachniet@analysts. com (517) 336 -1004 (office) Bret Straffon PSS - Security bstraffo@cisco. com (248) 455 -1737 (office) Lance Miller Security Practice Director lmiller@analysts. com (248) 232 -5322 (office) Scott Maxwell CAM – Cisco Channel scmaxwel@cisco. com (614) 718 2784 (office) 102


