12b99002a34475fa7182ed0569d6eb3f.ppt
- Количество слайдов: 91
 Data Link Layer Services and Protocols Arzad A. Kherani (alam@cse. iitd. ac. in) Dept. of Computer Sc. And Engg. Indian Institute of Technology Delhi Topics in Networking 1
Data Link Layer Services and Protocols Arzad A. Kherani (alam@cse. iitd. ac. in) Dept. of Computer Sc. And Engg. Indian Institute of Technology Delhi Topics in Networking 1
 Outline Frame encoding l Error detection and recovery l Data Link Protocols l Protocol analysis l – Performance – Verification for correctness Topics in Networking 2
Outline Frame encoding l Error detection and recovery l Data Link Protocols l Protocol analysis l – Performance – Verification for correctness Topics in Networking 2
 Data link services Operates between two neighboring devices l Provides a capability for higher-layer entities to send “packets” l – A packet is a sequence of bits, with well-identified “start” and “end” l The packet is itself encapsulated into a “frame”, adding to it “header” and “trailer” Topics in Networking 3
Data link services Operates between two neighboring devices l Provides a capability for higher-layer entities to send “packets” l – A packet is a sequence of bits, with well-identified “start” and “end” l The packet is itself encapsulated into a “frame”, adding to it “header” and “trailer” Topics in Networking 3
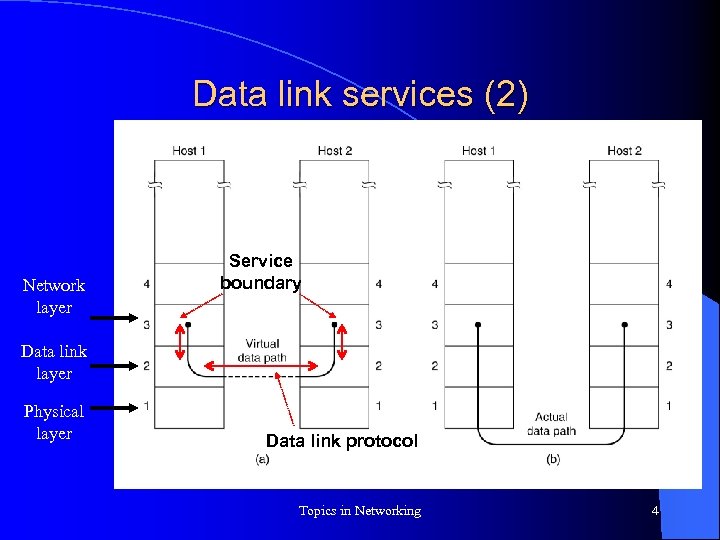 Data link services (2) Network layer Service boundary Data link layer Physical layer Data link protocol Topics in Networking 4
Data link services (2) Network layer Service boundary Data link layer Physical layer Data link protocol Topics in Networking 4
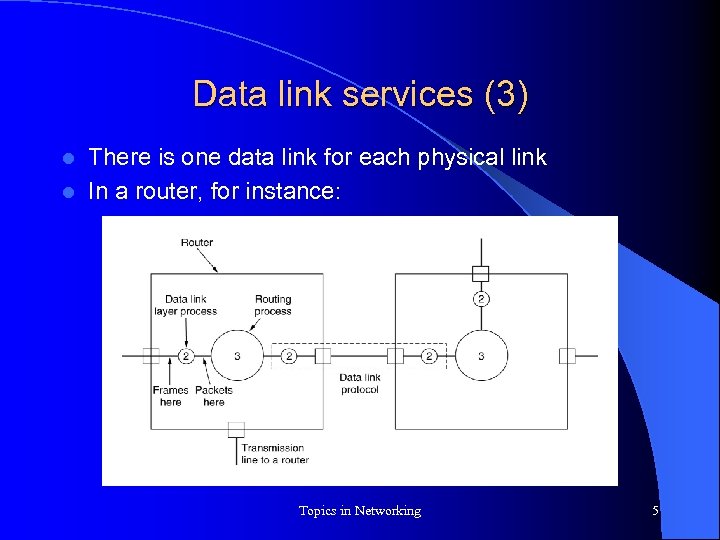 Data link services (3) There is one data link for each physical link l In a router, for instance: l Topics in Networking 5
Data link services (3) There is one data link for each physical link l In a router, for instance: l Topics in Networking 5
 Data link services l Connection-less service – Un-acknowledged service l Useful in case of low errors, and for real-time applications – Acknowledged service l l l Used in wire-less networks Frames that are not acked may be re-sent Connection-oriented service – acknowledged l Ensures delivery of frames Topics in Networking 6
Data link services l Connection-less service – Un-acknowledged service l Useful in case of low errors, and for real-time applications – Acknowledged service l l l Used in wire-less networks Frames that are not acked may be re-sent Connection-oriented service – acknowledged l Ensures delivery of frames Topics in Networking 6
 Framing l Link layer packet = frame l Problem: how to recognize beginning and end of frame? l Three methods – byte counting (DDCMP) – bit stuffing (X. 25 Level 2, 802. x) – byte stuffing (BISYNCH, IMP-IMP) Topics in Networking 7
Framing l Link layer packet = frame l Problem: how to recognize beginning and end of frame? l Three methods – byte counting (DDCMP) – bit stuffing (X. 25 Level 2, 802. x) – byte stuffing (BISYNCH, IMP-IMP) Topics in Networking 7
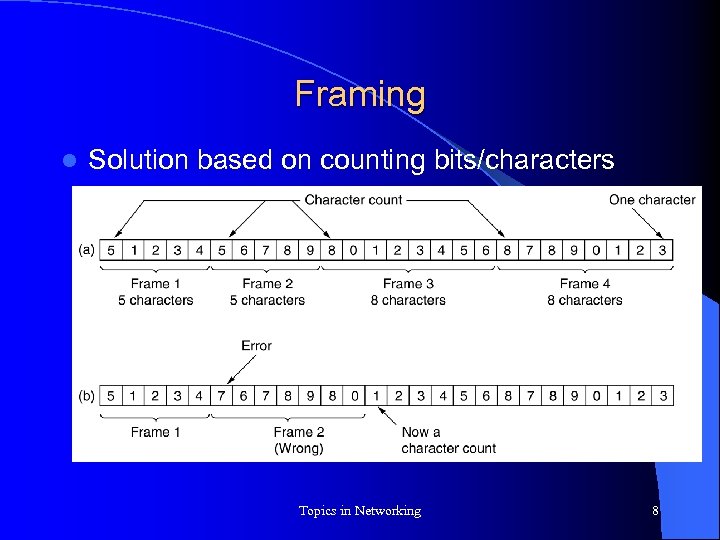 Framing l Solution based on counting bits/characters Topics in Networking 8
Framing l Solution based on counting bits/characters Topics in Networking 8
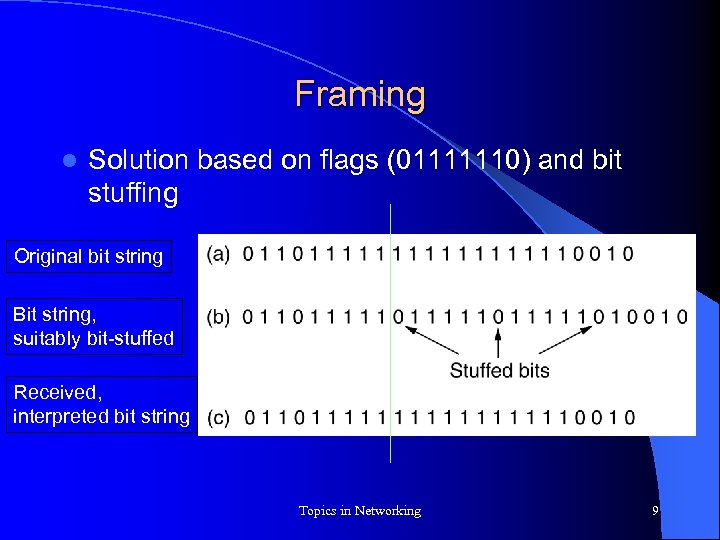 Framing l Solution based on flags (01111110) and bit stuffing Original bit string Bit string, suitably bit-stuffed Received, interpreted bit string Topics in Networking 9
Framing l Solution based on flags (01111110) and bit stuffing Original bit string Bit string, suitably bit-stuffed Received, interpreted bit string Topics in Networking 9
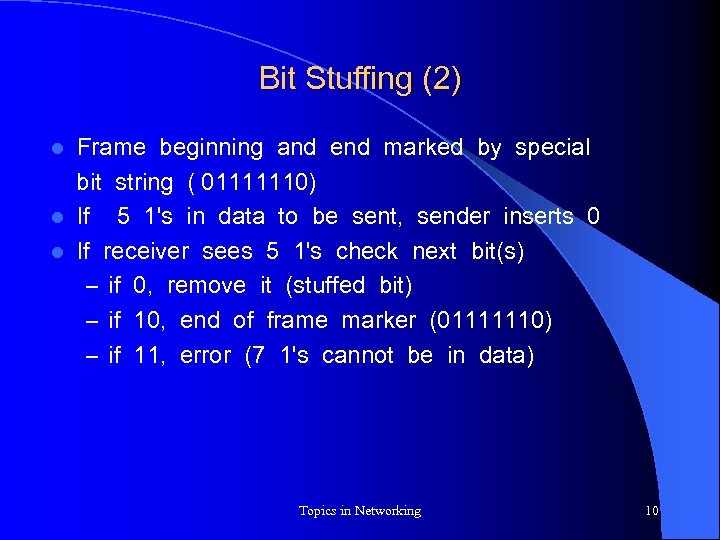 Bit Stuffing (2) Frame beginning and end marked by special bit string ( 01111110) l If 5 1's in data to be sent, sender inserts 0 l If receiver sees 5 1's check next bit(s) – if 0, remove it (stuffed bit) – if 10, end of frame marker (01111110) – if 11, error (7 1's cannot be in data) l Topics in Networking 10
Bit Stuffing (2) Frame beginning and end marked by special bit string ( 01111110) l If 5 1's in data to be sent, sender inserts 0 l If receiver sees 5 1's check next bit(s) – if 0, remove it (stuffed bit) – if 10, end of frame marker (01111110) – if 11, error (7 1's cannot be in data) l Topics in Networking 10
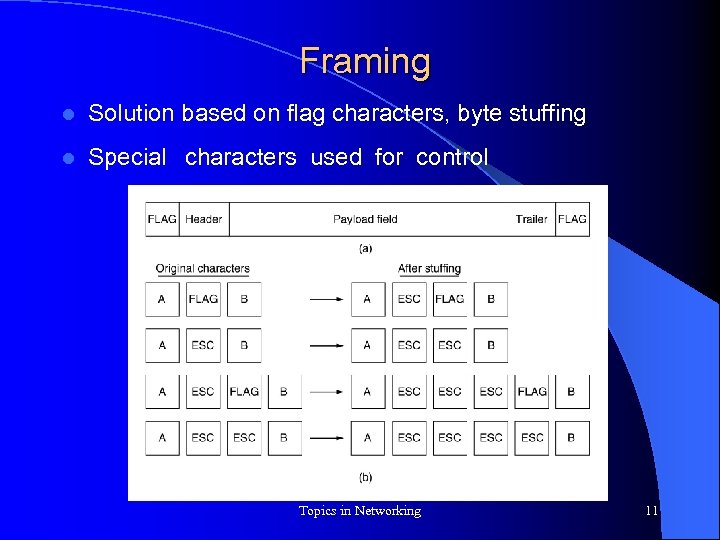 Framing l Solution based on flag characters, byte stuffing l Special characters used for control Topics in Networking 11
Framing l Solution based on flag characters, byte stuffing l Special characters used for control Topics in Networking 11
 Byte Stuffing Problems l Dependence on fixed character set Must examine every byte of data on sending and receiving (insert / remove DLE) l l Was used widely in IBM bisynch (at 9600 bps) Topics in Networking 12
Byte Stuffing Problems l Dependence on fixed character set Must examine every byte of data on sending and receiving (insert / remove DLE) l l Was used widely in IBM bisynch (at 9600 bps) Topics in Networking 12
 Error detection and recovery l Two approaches: – error correction codes l quick, but ineffective in several cases: – temporary dislocation – frame size is large, and error rate is high – burst errors l expensive – error detection and recovery using re-transmission l the preferred solution today – efficient Topics in Networking 13
Error detection and recovery l Two approaches: – error correction codes l quick, but ineffective in several cases: – temporary dislocation – frame size is large, and error rate is high – burst errors l expensive – error detection and recovery using re-transmission l the preferred solution today – efficient Topics in Networking 13
 Error detection l Hamming distance between pair of codes let message of length m 2 m distinct messages with r redundant bits, codeword is of length n = m + r hamming distance between codes x, y = no. of bits in which x and y differ l Hamming distance for a code consider n dimension space, with 2 m codewords hamming distance for code (or coding scheme) = minx, y (no. of bits in which x and y differ) Topics in Networking 14
Error detection l Hamming distance between pair of codes let message of length m 2 m distinct messages with r redundant bits, codeword is of length n = m + r hamming distance between codes x, y = no. of bits in which x and y differ l Hamming distance for a code consider n dimension space, with 2 m codewords hamming distance for code (or coding scheme) = minx, y (no. of bits in which x and y differ) Topics in Networking 14
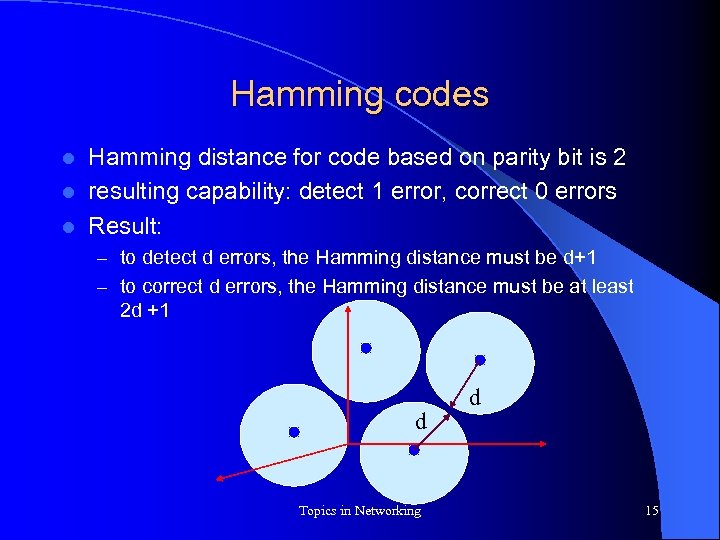 Hamming codes Hamming distance for code based on parity bit is 2 l resulting capability: detect 1 error, correct 0 errors l Result: l – to detect d errors, the Hamming distance must be d+1 – to correct d errors, the Hamming distance must be at least 2 d +1 d Topics in Networking d 15
Hamming codes Hamming distance for code based on parity bit is 2 l resulting capability: detect 1 error, correct 0 errors l Result: l – to detect d errors, the Hamming distance must be d+1 – to correct d errors, the Hamming distance must be at least 2 d +1 d Topics in Networking d 15
 Hamming codes (2) Consider 7 bit data, 4 redundancy bits, codeword is 11 bits l message bits are numbered 3, 5, 6, 7, 9, 10, 11 l redundancy bits are numbered 1, 2, 4, 8 l check bit 1 checks error in bits 1, 3, 5, 7, 9, 11 check bit 2 checks error in bits 2, 3, 6, 7, 10, 11 check bit 4 checks error in bits 4, 5, 6, 7 check bit 8 checks error in bits 8, 9, 10, 11 or (it should be) 0 = b 1 + b 3 + b 5 + b 7 + b 9 + b 11 0 = b 2 + b 3 + b 6 + b 7 + b 10 + b 11 0 = b 4 + b 5 + b 6 + b 7 0 = b 8 + b 9 + b 10 + b 11 Topics in Networking 16
Hamming codes (2) Consider 7 bit data, 4 redundancy bits, codeword is 11 bits l message bits are numbered 3, 5, 6, 7, 9, 10, 11 l redundancy bits are numbered 1, 2, 4, 8 l check bit 1 checks error in bits 1, 3, 5, 7, 9, 11 check bit 2 checks error in bits 2, 3, 6, 7, 10, 11 check bit 4 checks error in bits 4, 5, 6, 7 check bit 8 checks error in bits 8, 9, 10, 11 or (it should be) 0 = b 1 + b 3 + b 5 + b 7 + b 9 + b 11 0 = b 2 + b 3 + b 6 + b 7 + b 10 + b 11 0 = b 4 + b 5 + b 6 + b 7 0 = b 8 + b 9 + b 10 + b 11 Topics in Networking 16
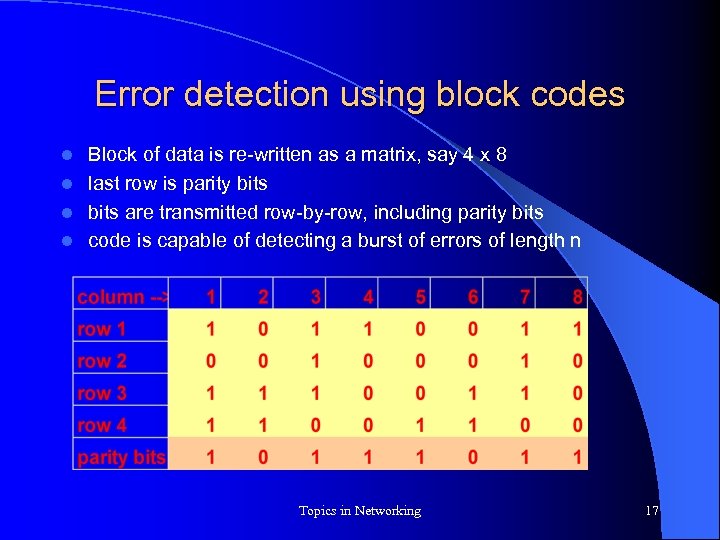 Error detection using block codes Block of data is re-written as a matrix, say 4 x 8 l last row is parity bits l bits are transmitted row-by-row, including parity bits l code is capable of detecting a burst of errors of length n l Topics in Networking 17
Error detection using block codes Block of data is re-written as a matrix, say 4 x 8 l last row is parity bits l bits are transmitted row-by-row, including parity bits l code is capable of detecting a burst of errors of length n l Topics in Networking 17
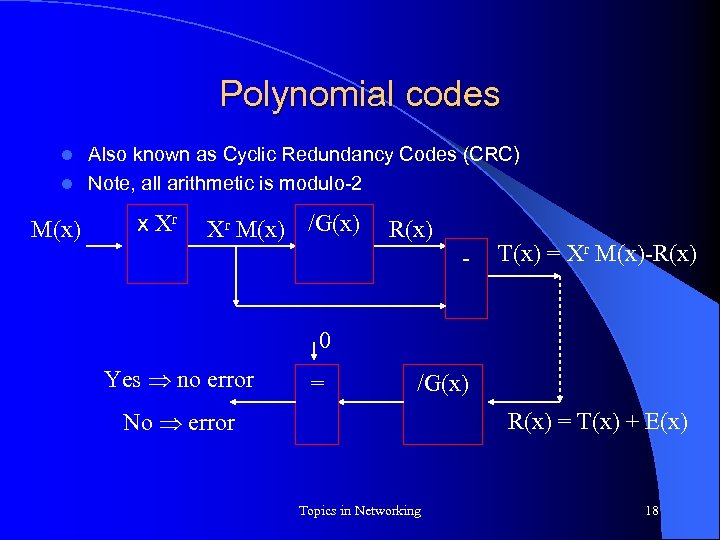 Polynomial codes Also known as Cyclic Redundancy Codes (CRC) l Note, all arithmetic is modulo-2 l M(x) x Xr Xr M(x) /G(x) R(x) - T(x) = Xr M(x)-R(x) 0 Yes no error = /G(x) R(x) = T(x) + E(x) No error Topics in Networking 18
Polynomial codes Also known as Cyclic Redundancy Codes (CRC) l Note, all arithmetic is modulo-2 l M(x) x Xr Xr M(x) /G(x) R(x) - T(x) = Xr M(x)-R(x) 0 Yes no error = /G(x) R(x) = T(x) + E(x) No error Topics in Networking 18
 Polynomial codes (2) l l l Error detection capability depends upon G(x) 1 bit error R(x) = T(x) + xi R(x)/G(x) = 0 iff E(x)/G(x) = 0 E(x)/G(x) 0 if G(x) has 2 or more terms single errors can always be detected Similarly, two errors can always be detected if G(x) does not divide xk + 1 Again, if G(x) is divisible by x+1 then an odd number of errors can be detected Polynomial codes with r CRC bits will detect all bursts of length r or less etc. , etc. Topics in Networking 19
Polynomial codes (2) l l l Error detection capability depends upon G(x) 1 bit error R(x) = T(x) + xi R(x)/G(x) = 0 iff E(x)/G(x) = 0 E(x)/G(x) 0 if G(x) has 2 or more terms single errors can always be detected Similarly, two errors can always be detected if G(x) does not divide xk + 1 Again, if G(x) is divisible by x+1 then an odd number of errors can be detected Polynomial codes with r CRC bits will detect all bursts of length r or less etc. , etc. Topics in Networking 19
 Polynomial codes (3) International, IEEE standards l IEEE 802 standard G(x) = x 32 + x 26 + x 23 + x 22 + x 16 + x 12 + x 11 + x 10 + x 8 + x 7 + x 5 + x 4 + x 2 + x 1 + 1 it is capable of detecting bursts of length up to 32, and all odd number of errors, and even no of error with high probability l Topics in Networking 20
Polynomial codes (3) International, IEEE standards l IEEE 802 standard G(x) = x 32 + x 26 + x 23 + x 22 + x 16 + x 12 + x 11 + x 10 + x 8 + x 7 + x 5 + x 4 + x 2 + x 1 + 1 it is capable of detecting bursts of length up to 32, and all odd number of errors, and even no of error with high probability l Topics in Networking 20
 Error recovery Error detection, followed by re-transmissions, etc. l Efficient l Simultaneously address problem of “flow control” l Topics in Networking 21
Error recovery Error detection, followed by re-transmissions, etc. l Efficient l Simultaneously address problem of “flow control” l Topics in Networking 21
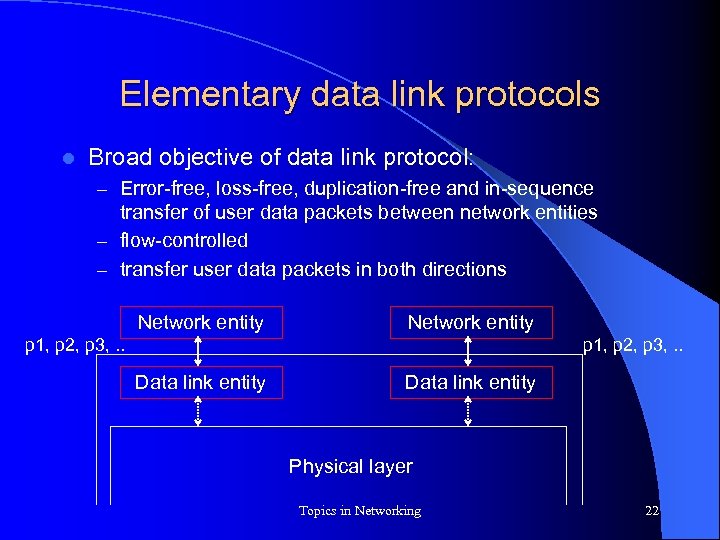 Elementary data link protocols l Broad objective of data link protocol: – Error-free, loss-free, duplication-free and in-sequence transfer of user data packets between network entities – flow-controlled – transfer user data packets in both directions Network entity p 1, p 2, p 3, . . Data link entity Physical layer Topics in Networking 22
Elementary data link protocols l Broad objective of data link protocol: – Error-free, loss-free, duplication-free and in-sequence transfer of user data packets between network entities – flow-controlled – transfer user data packets in both directions Network entity p 1, p 2, p 3, . . Data link entity Physical layer Topics in Networking 22
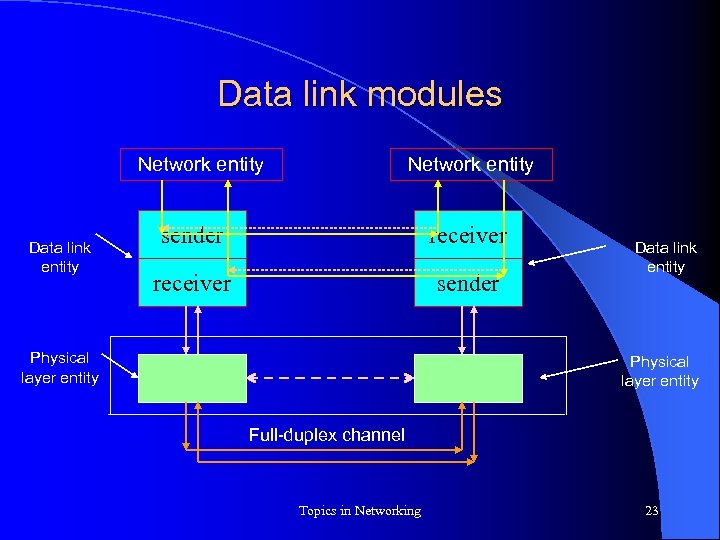 Data link modules Network entity Data link entity Network entity sender receiver sender Physical layer entity Data link entity Physical layer entity Full-duplex channel Topics in Networking 23
Data link modules Network entity Data link entity Network entity sender receiver sender Physical layer entity Data link entity Physical layer entity Full-duplex channel Topics in Networking 23
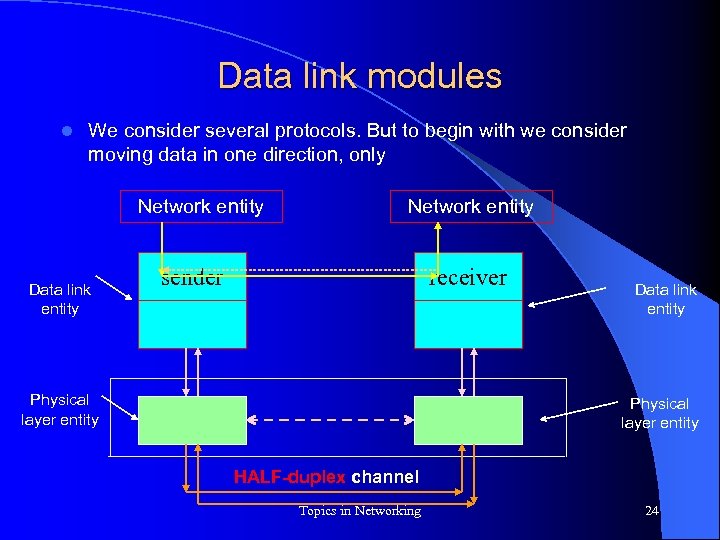 Data link modules l We consider several protocols. But to begin with we consider moving data in one direction, only Network entity Data link entity Network entity sender receiver Physical layer entity Data link entity Physical layer entity HALF-duplex channel Topics in Networking 24
Data link modules l We consider several protocols. But to begin with we consider moving data in one direction, only Network entity Data link entity Network entity sender receiver Physical layer entity Data link entity Physical layer entity HALF-duplex channel Topics in Networking 24
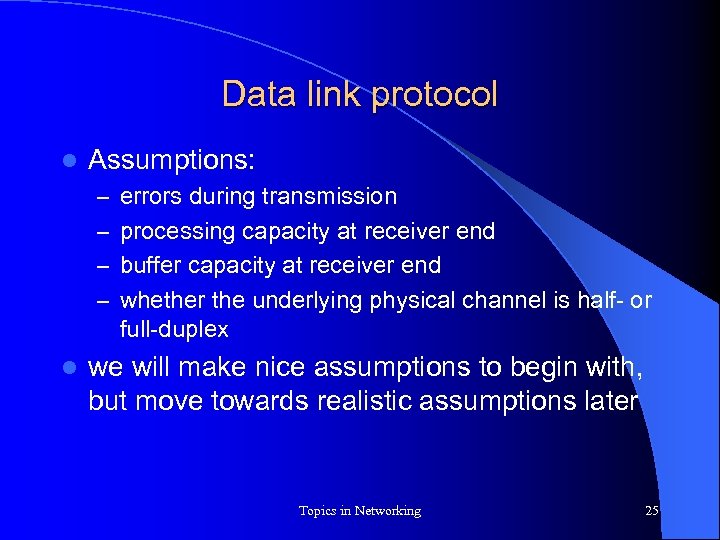 Data link protocol l Assumptions: – errors during transmission – processing capacity at receiver end – buffer capacity at receiver end – whether the underlying physical channel is half- or full-duplex l we will make nice assumptions to begin with, but move towards realistic assumptions later Topics in Networking 25
Data link protocol l Assumptions: – errors during transmission – processing capacity at receiver end – buffer capacity at receiver end – whether the underlying physical channel is half- or full-duplex l we will make nice assumptions to begin with, but move towards realistic assumptions later Topics in Networking 25
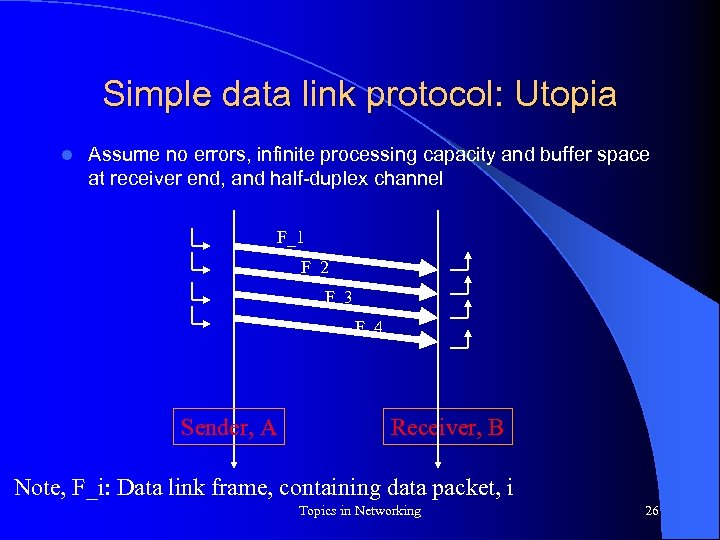 Simple data link protocol: Utopia l Assume no errors, infinite processing capacity and buffer space at receiver end, and half-duplex channel F_1 F_2 F_3 F_4 Sender, A Receiver, B Note, F_i: Data link frame, containing data packet, i Topics in Networking 26
Simple data link protocol: Utopia l Assume no errors, infinite processing capacity and buffer space at receiver end, and half-duplex channel F_1 F_2 F_3 F_4 Sender, A Receiver, B Note, F_i: Data link frame, containing data packet, i Topics in Networking 26
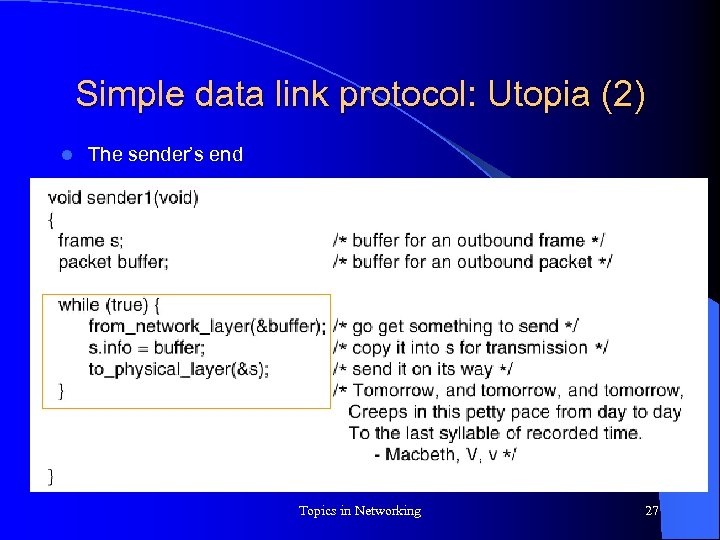 Simple data link protocol: Utopia (2) l The sender’s end Topics in Networking 27
Simple data link protocol: Utopia (2) l The sender’s end Topics in Networking 27
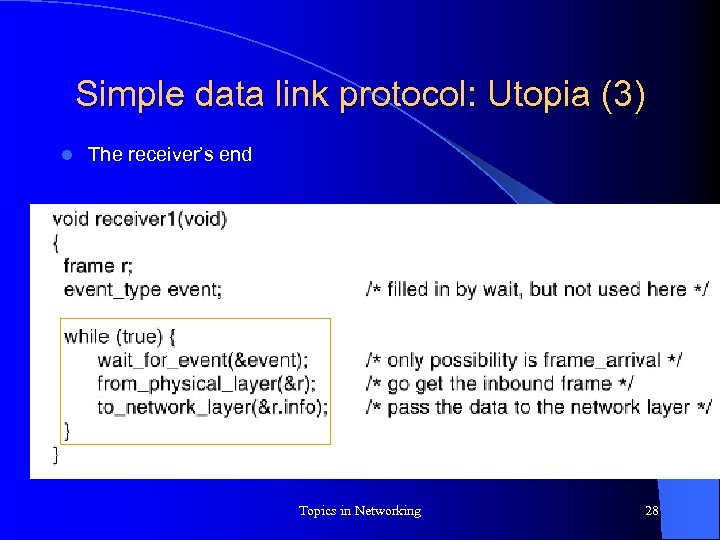 Simple data link protocol: Utopia (3) l The receiver’s end Topics in Networking 28
Simple data link protocol: Utopia (3) l The receiver’s end Topics in Networking 28
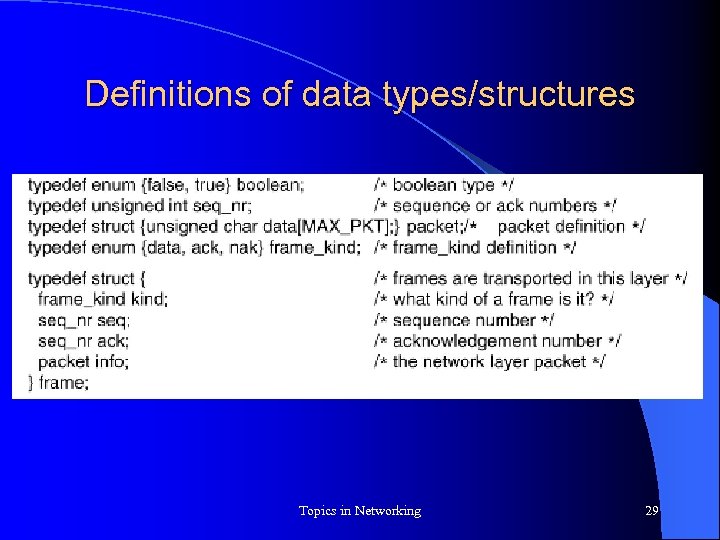 Definitions of data types/structures Topics in Networking 29
Definitions of data types/structures Topics in Networking 29
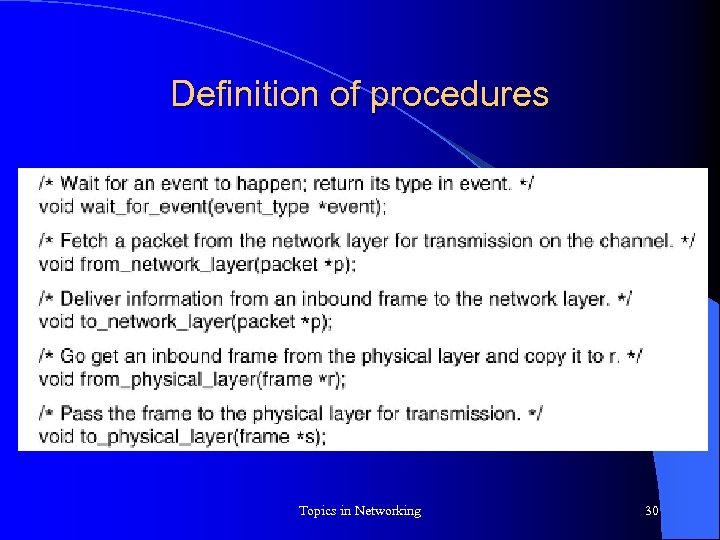 Definition of procedures Topics in Networking 30
Definition of procedures Topics in Networking 30
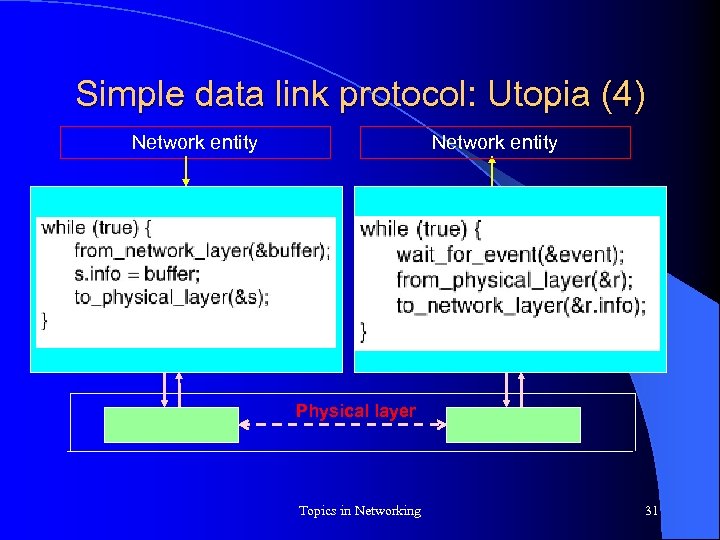 Simple data link protocol: Utopia (4) Network entity Physical layer Topics in Networking 31
Simple data link protocol: Utopia (4) Network entity Physical layer Topics in Networking 31
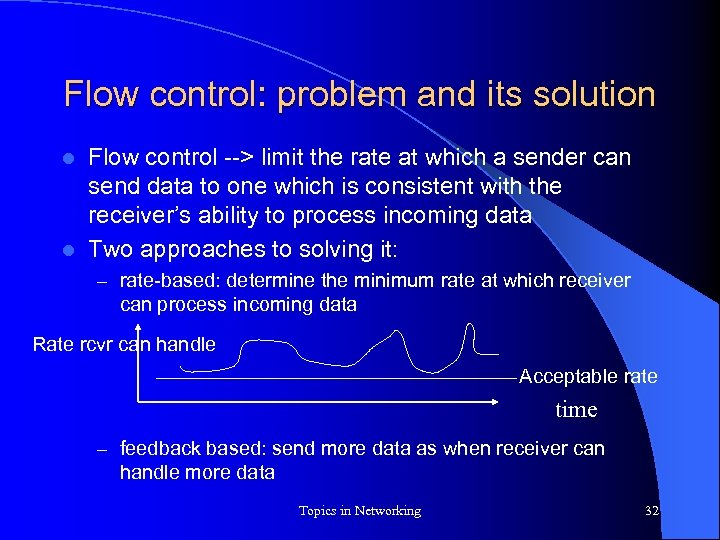 Flow control: problem and its solution Flow control --> limit the rate at which a sender can send data to one which is consistent with the receiver’s ability to process incoming data l Two approaches to solving it: l – rate-based: determine the minimum rate at which receiver can process incoming data Rate rcvr can handle Acceptable rate time – feedback based: send more data as when receiver can handle more data Topics in Networking 32
Flow control: problem and its solution Flow control --> limit the rate at which a sender can send data to one which is consistent with the receiver’s ability to process incoming data l Two approaches to solving it: l – rate-based: determine the minimum rate at which receiver can process incoming data Rate rcvr can handle Acceptable rate time – feedback based: send more data as when receiver can handle more data Topics in Networking 32
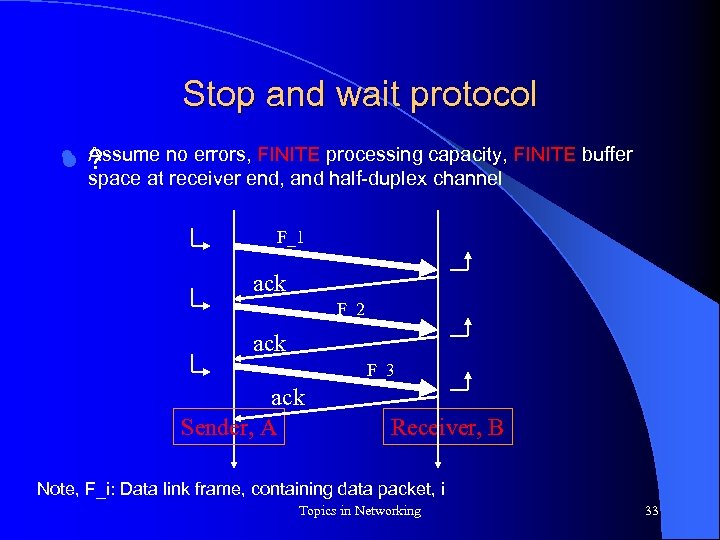 Stop and wait protocol l l Assume no errors, FINITE processing capacity, FINITE buffer ? space at receiver end, and half-duplex channel F_1 ack F_2 ack F_3 ack Sender, A Receiver, B Note, F_i: Data link frame, containing data packet, i Topics in Networking 33
Stop and wait protocol l l Assume no errors, FINITE processing capacity, FINITE buffer ? space at receiver end, and half-duplex channel F_1 ack F_2 ack F_3 ack Sender, A Receiver, B Note, F_i: Data link frame, containing data packet, i Topics in Networking 33
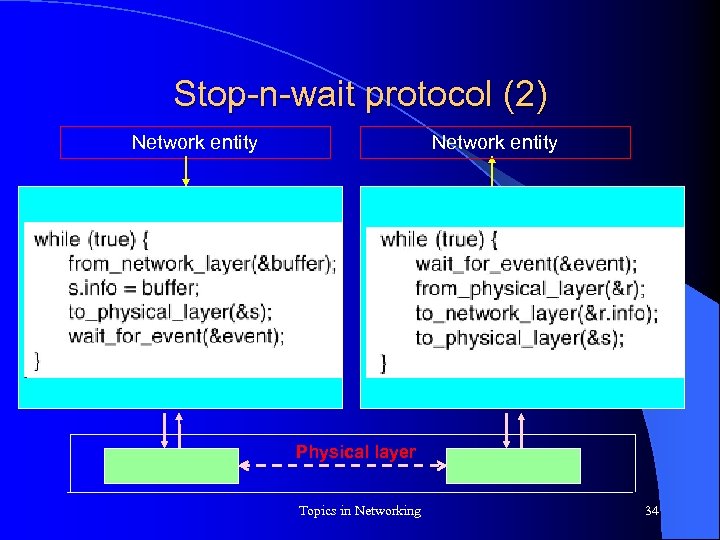 Stop-n-wait protocol (2) Network entity Physical layer Topics in Networking 34
Stop-n-wait protocol (2) Network entity Physical layer Topics in Networking 34
 PAR protocol for noisy channels l PAR protocol addresses: – flow control – noisy channel l based on “positive acks” and re-transmissions Topics in Networking 35
PAR protocol for noisy channels l PAR protocol addresses: – flow control – noisy channel l based on “positive acks” and re-transmissions Topics in Networking 35
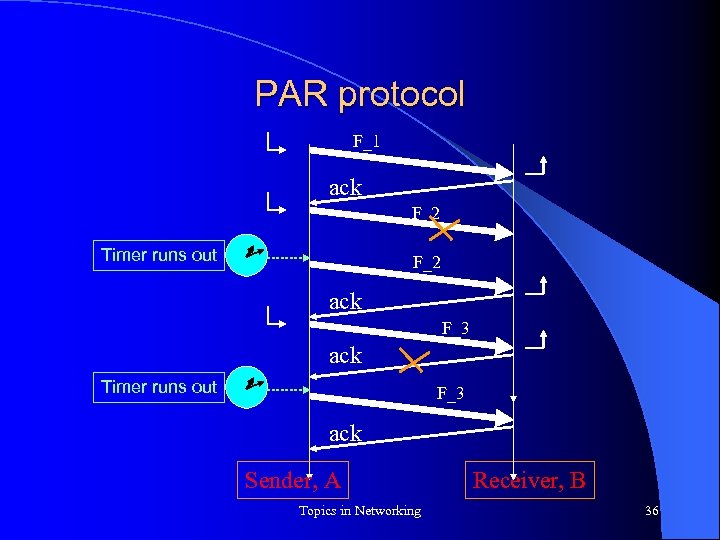 PAR protocol F_1 ack F_2 Timer runs out F_2 ack F_3 ack Timer runs out F_3 ack Sender, A Topics in Networking Receiver, B 36
PAR protocol F_1 ack F_2 Timer runs out F_2 ack F_3 ack Timer runs out F_3 ack Sender, A Topics in Networking Receiver, B 36
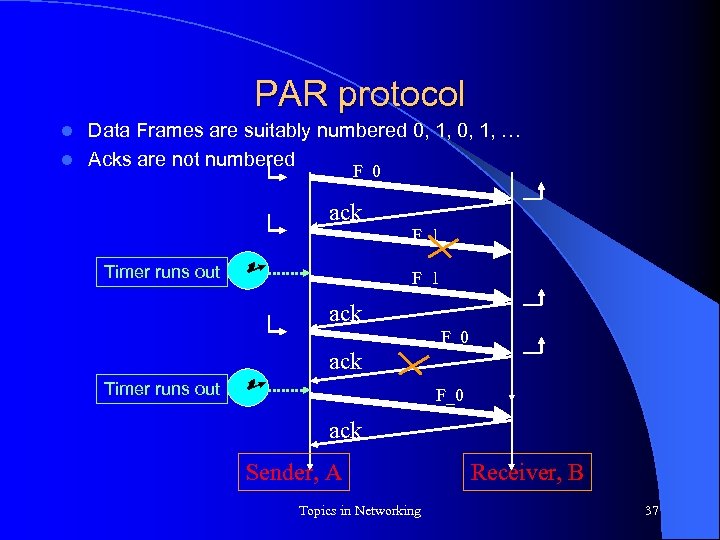 PAR protocol Data Frames are suitably numbered 0, 1, … l Acks are not numbered l F_0 ack Timer runs out F_1 ack F_0 ack Timer runs out F_0 ack Sender, A Topics in Networking Receiver, B 37
PAR protocol Data Frames are suitably numbered 0, 1, … l Acks are not numbered l F_0 ack Timer runs out F_1 ack F_0 ack Timer runs out F_0 ack Sender, A Topics in Networking Receiver, B 37
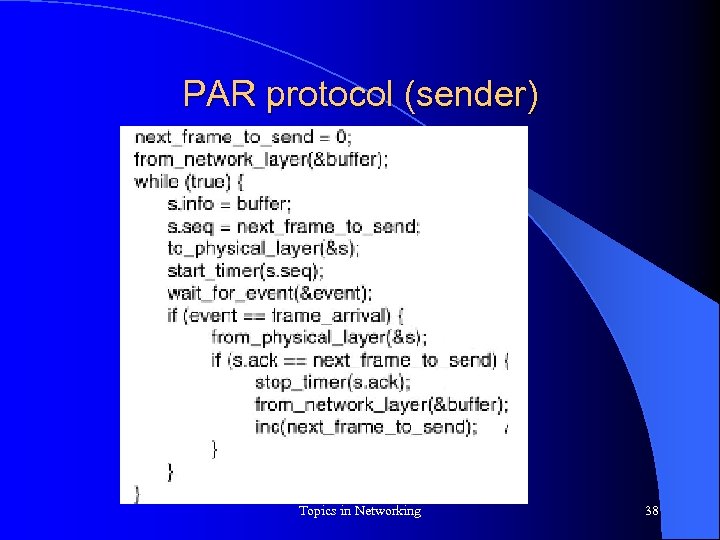 PAR protocol (sender) Topics in Networking 38
PAR protocol (sender) Topics in Networking 38
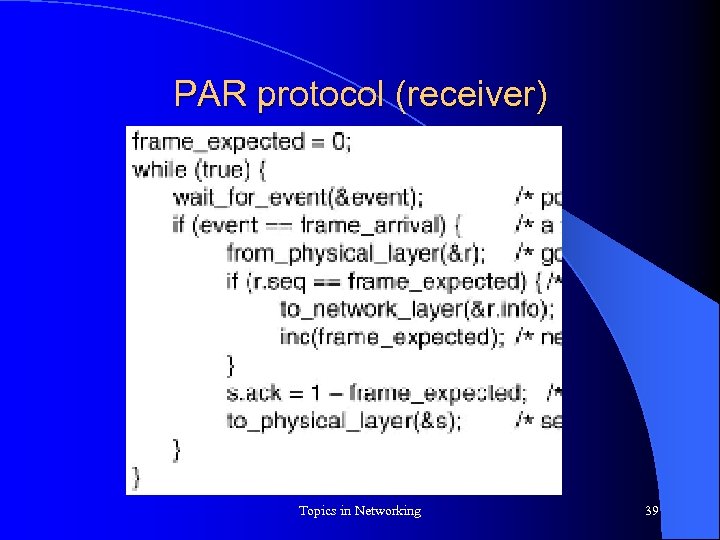 PAR protocol (receiver) Topics in Networking 39
PAR protocol (receiver) Topics in Networking 39
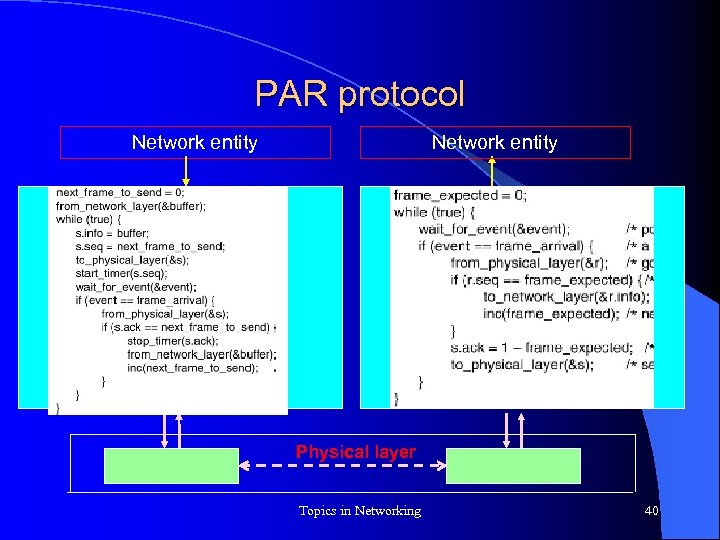 PAR protocol Network entity Physical layer Topics in Networking 40
PAR protocol Network entity Physical layer Topics in Networking 40
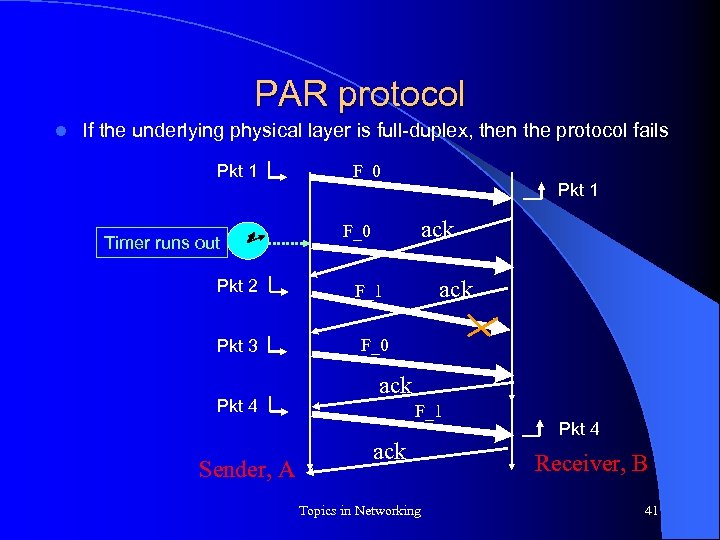 PAR protocol l If the underlying physical layer is full-duplex, then the protocol fails Pkt 1 Timer runs out Pkt 2 Pkt 3 Pkt 4 Sender, A F_0 Pkt 1 ack F_0 ack F_1 ack Topics in Networking Pkt 4 Receiver, B 41
PAR protocol l If the underlying physical layer is full-duplex, then the protocol fails Pkt 1 Timer runs out Pkt 2 Pkt 3 Pkt 4 Sender, A F_0 Pkt 1 ack F_0 ack F_1 ack Topics in Networking Pkt 4 Receiver, B 41
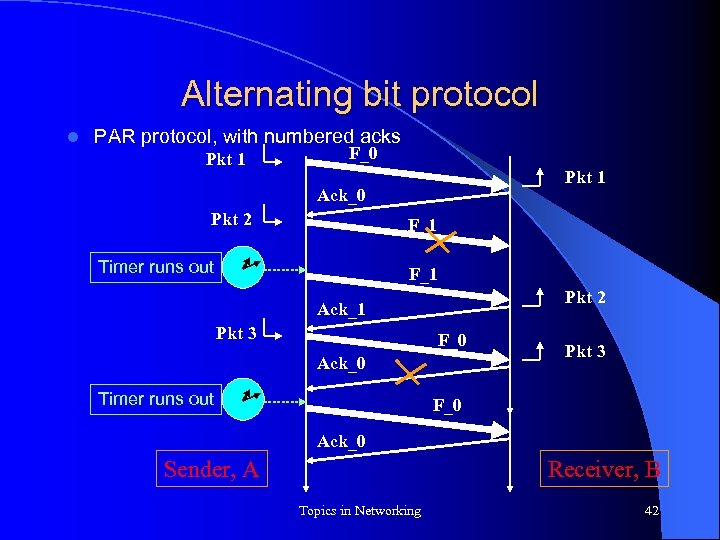 Alternating bit protocol l PAR protocol, with numbered acks Pkt 1 F_0 Pkt 1 Ack_0 Pkt 2 F_1 Timer runs out F_1 Pkt 2 Ack_1 Pkt 3 F_0 Ack_0 Timer runs out Pkt 3 F_0 Ack_0 Sender, A Receiver, B Topics in Networking 42
Alternating bit protocol l PAR protocol, with numbered acks Pkt 1 F_0 Pkt 1 Ack_0 Pkt 2 F_1 Timer runs out F_1 Pkt 2 Ack_1 Pkt 3 F_0 Ack_0 Timer runs out Pkt 3 F_0 Ack_0 Sender, A Receiver, B Topics in Networking 42
 Alternating bit protocol Topics in Networking 43
Alternating bit protocol Topics in Networking 43
 Alternating bit protocol Topics in Networking 44
Alternating bit protocol Topics in Networking 44
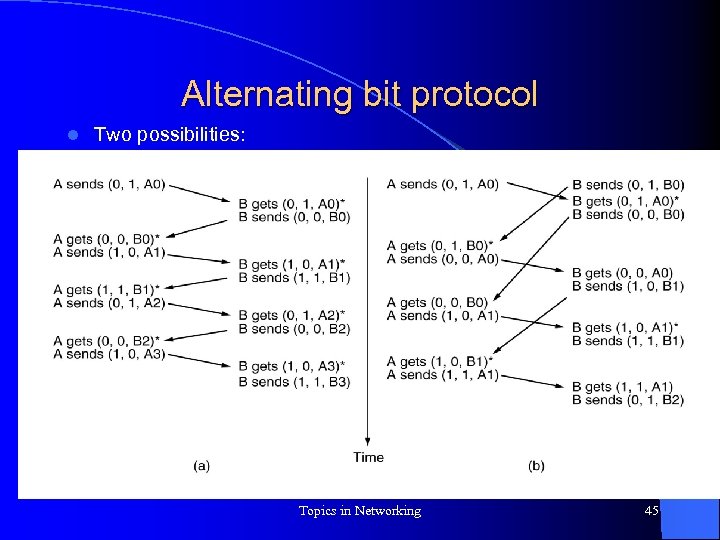 Alternating bit protocol l Two possibilities: Topics in Networking 45
Alternating bit protocol l Two possibilities: Topics in Networking 45
 Alternating bit protocol l l l Use link A B to carry data from A to B, and acks from B to A and use link B A to carry data from B to A, and acks from A to B Piggyback acks onto data frames, if one has data to send Else, just an ack Redundant acks are OK An ack takes the form “I am waiting to receive data frame no. X” Introduce a field for frame type, “data frame” or “ack frame” Topics in Networking 46
Alternating bit protocol l l l Use link A B to carry data from A to B, and acks from B to A and use link B A to carry data from B to A, and acks from A to B Piggyback acks onto data frames, if one has data to send Else, just an ack Redundant acks are OK An ack takes the form “I am waiting to receive data frame no. X” Introduce a field for frame type, “data frame” or “ack frame” Topics in Networking 46
 Performance of PAR protocol Link utilization Utilization = L / (L+b*R), where L = size of data frame b = data rate R is round-trip delay l For a satellite channel, let L = 10 K bits, b = 100 Kbps, R=500 ms Utilization is 10 K / (10 K + 50 K) = 1/6 l For a fibre-optic channel, let L = 10 K bits, b = 100 Mbps, R = 1 ms Utilization is 10 K / (10 K + 100 K) = 1/11 l Delay=BW product is the key l Let sender send many data frames before it receives an ack l Topics in Networking 47
Performance of PAR protocol Link utilization Utilization = L / (L+b*R), where L = size of data frame b = data rate R is round-trip delay l For a satellite channel, let L = 10 K bits, b = 100 Kbps, R=500 ms Utilization is 10 K / (10 K + 50 K) = 1/6 l For a fibre-optic channel, let L = 10 K bits, b = 100 Mbps, R = 1 ms Utilization is 10 K / (10 K + 100 K) = 1/11 l Delay=BW product is the key l Let sender send many data frames before it receives an ack l Topics in Networking 47
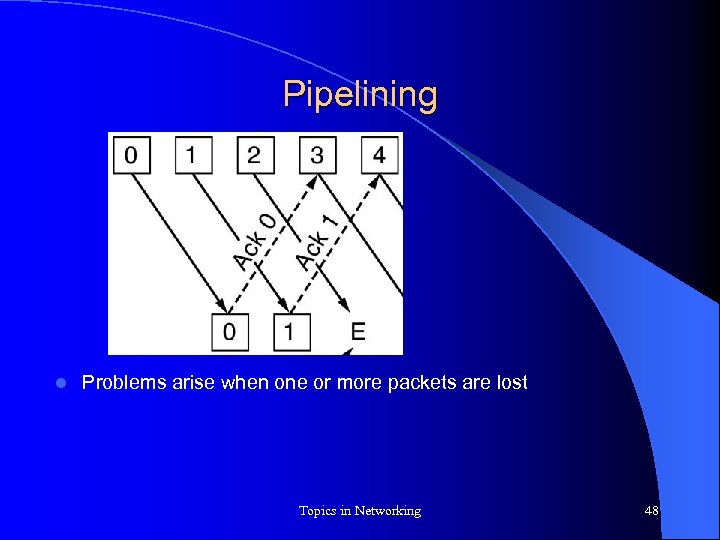 Pipelining l Problems arise when one or more packets are lost Topics in Networking 48
Pipelining l Problems arise when one or more packets are lost Topics in Networking 48
 Pipelining, with error recovery l Two approaches to recover from loss of data frame: – go-back n – selective repeat Topics in Networking 49
Pipelining, with error recovery l Two approaches to recover from loss of data frame: – go-back n – selective repeat Topics in Networking 49
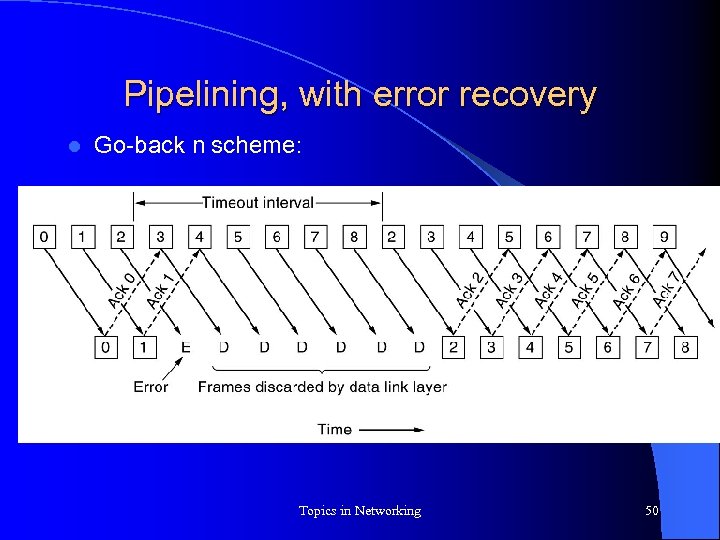 Pipelining, with error recovery l Go-back n scheme: Topics in Networking 50
Pipelining, with error recovery l Go-back n scheme: Topics in Networking 50
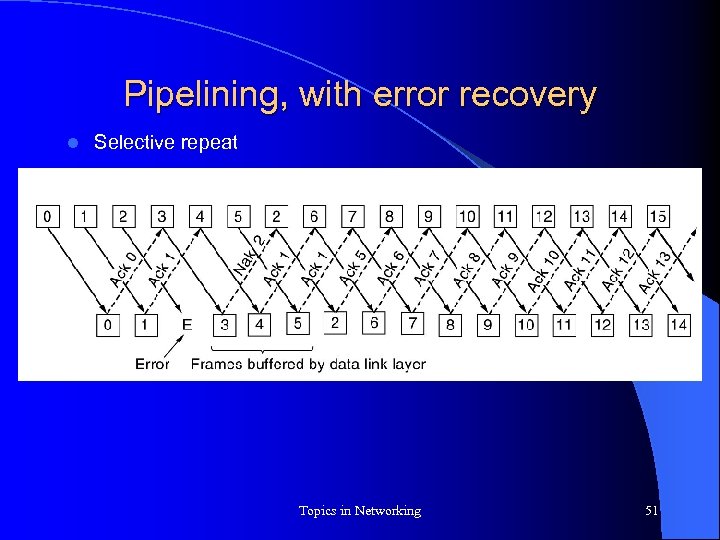 Pipelining, with error recovery l Selective repeat Topics in Networking 51
Pipelining, with error recovery l Selective repeat Topics in Networking 51
 Sliding window protocols Each data frame is sequentially numbered 0 through 2 n-1 l Sender maintains “transmit window” indicating: l – which data frames can be sent – which data frames have been sent l receiver maintains a “Receive window” – which data frames can it receive – which data frames have been received Topics in Networking 52
Sliding window protocols Each data frame is sequentially numbered 0 through 2 n-1 l Sender maintains “transmit window” indicating: l – which data frames can be sent – which data frames have been sent l receiver maintains a “Receive window” – which data frames can it receive – which data frames have been received Topics in Networking 52
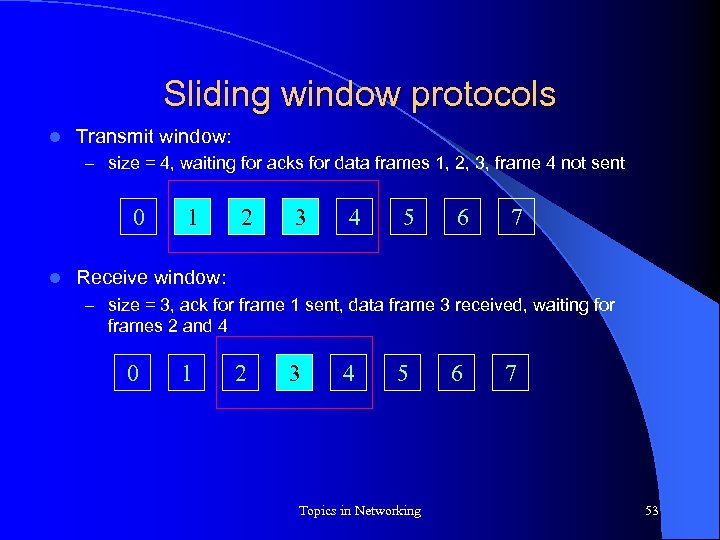 Sliding window protocols l Transmit window: – size = 4, waiting for acks for data frames 1, 2, 3, frame 4 not sent 0 l 1 2 3 4 5 6 7 Receive window: – size = 3, ack for frame 1 sent, data frame 3 received, waiting for frames 2 and 4 0 1 2 3 4 5 Topics in Networking 6 7 53
Sliding window protocols l Transmit window: – size = 4, waiting for acks for data frames 1, 2, 3, frame 4 not sent 0 l 1 2 3 4 5 6 7 Receive window: – size = 3, ack for frame 1 sent, data frame 3 received, waiting for frames 2 and 4 0 1 2 3 4 5 Topics in Networking 6 7 53
 Sliding window protocols l Assuming sequence numbering 0. . 7 – Go back n protocol: l l Transmit window is size, say 7 receive window is size 1 – selective repeat protocol: l l transmit window is size 4 receive window is size 4 Topics in Networking 54
Sliding window protocols l Assuming sequence numbering 0. . 7 – Go back n protocol: l l Transmit window is size, say 7 receive window is size 1 – selective repeat protocol: l l transmit window is size 4 receive window is size 4 Topics in Networking 54
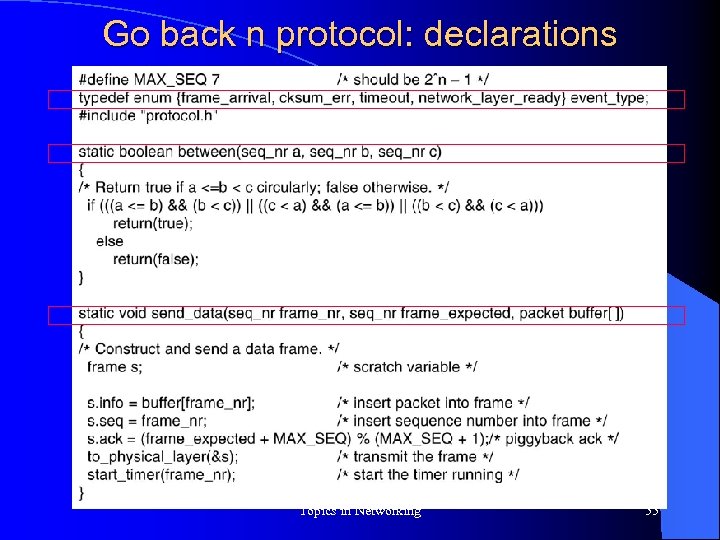 Go back n protocol: declarations Topics in Networking 55
Go back n protocol: declarations Topics in Networking 55
 Go back n protocol: more declrations Topics in Networking 56
Go back n protocol: more declrations Topics in Networking 56
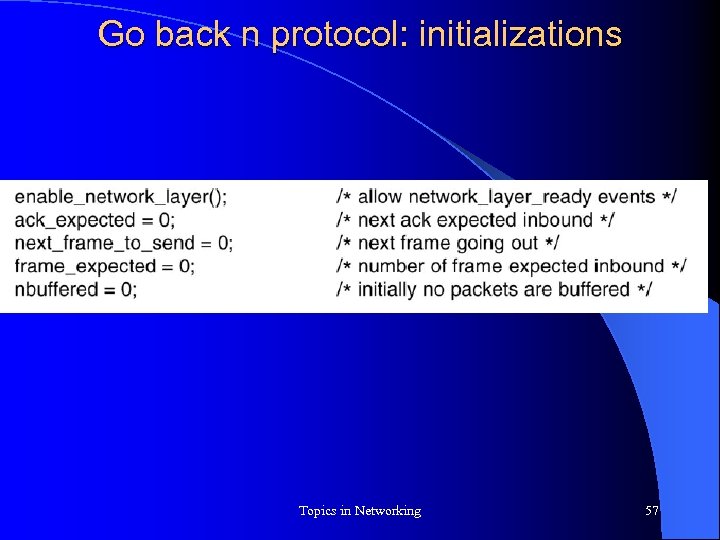 Go back n protocol: initializations Topics in Networking 57
Go back n protocol: initializations Topics in Networking 57
 Go back n protocol (loop) Topics in Networking 58
Go back n protocol (loop) Topics in Networking 58
 Go back n protocol: event processing Topics in Networking 59
Go back n protocol: event processing Topics in Networking 59
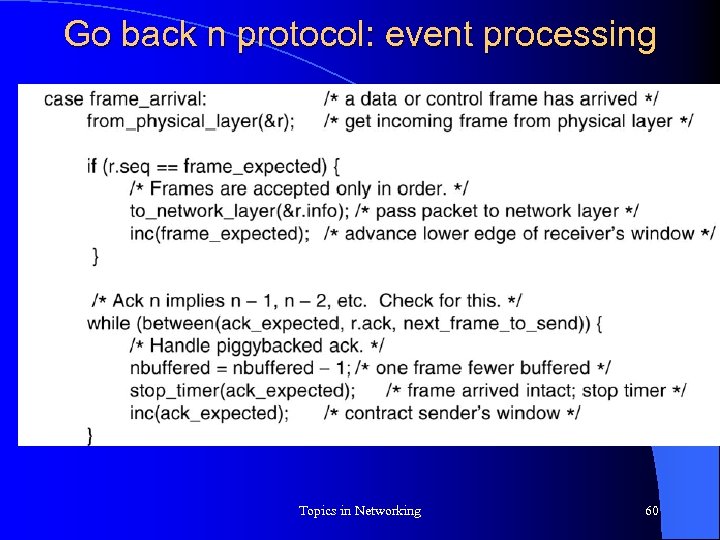 Go back n protocol: event processing Topics in Networking 60
Go back n protocol: event processing Topics in Networking 60
 Go back n protocol: event processing Topics in Networking 61
Go back n protocol: event processing Topics in Networking 61
 Go back n protocol l Buffer requirements – at sender’s end: N-1, where seq no is 0. . N-1 – at receiver’s end: 1 l Go-back n works well when error are infrequent – Because several frames need to be re-transmitted when an error occurs Topics in Networking 62
Go back n protocol l Buffer requirements – at sender’s end: N-1, where seq no is 0. . N-1 – at receiver’s end: 1 l Go-back n works well when error are infrequent – Because several frames need to be re-transmitted when an error occurs Topics in Networking 62
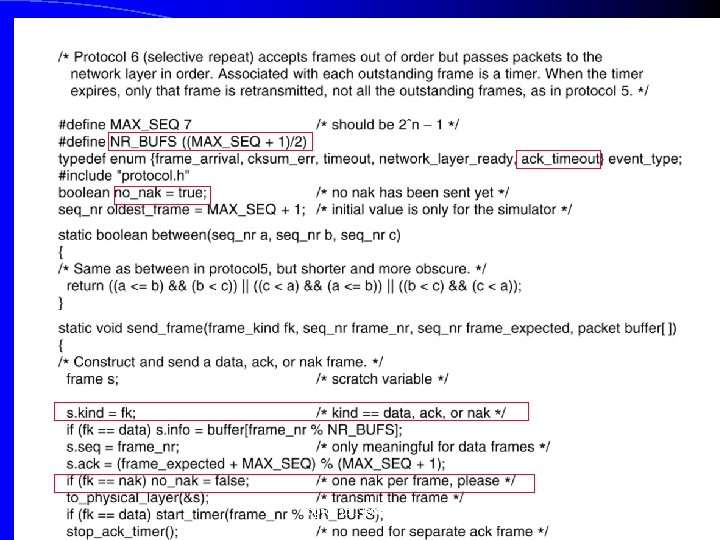
 Select Repeat Protocol Sequence numbering: 0 through n-1 l Transmit window size is n/2 l Receiver buffers each correctly recd data frame, but does not deliver it to the layer 3 l Receiver sends a NACK frame when it suspects loss of a data frame l – But makes sure that a NACK is not repeated Topics in Networking 63
Select Repeat Protocol Sequence numbering: 0 through n-1 l Transmit window size is n/2 l Receiver buffers each correctly recd data frame, but does not deliver it to the layer 3 l Receiver sends a NACK frame when it suspects loss of a data frame l – But makes sure that a NACK is not repeated Topics in Networking 63
 Select Repeat Protocol Topics in Networking 64
Select Repeat Protocol Topics in Networking 64
 Select Repeat Protocol Topics in Networking 65
Select Repeat Protocol Topics in Networking 65
 Select Repeat Protocol Topics in Networking 66
Select Repeat Protocol Topics in Networking 66
 Select Repeat Protocol Topics in Networking 67
Select Repeat Protocol Topics in Networking 67
 Protocol Analysis Performance l Verification l Topics in Networking 68
Protocol Analysis Performance l Verification l Topics in Networking 68
 Protocol Performance – Delay – Efficient use of available bandwidth Topics in Networking 69
Protocol Performance – Delay – Efficient use of available bandwidth Topics in Networking 69
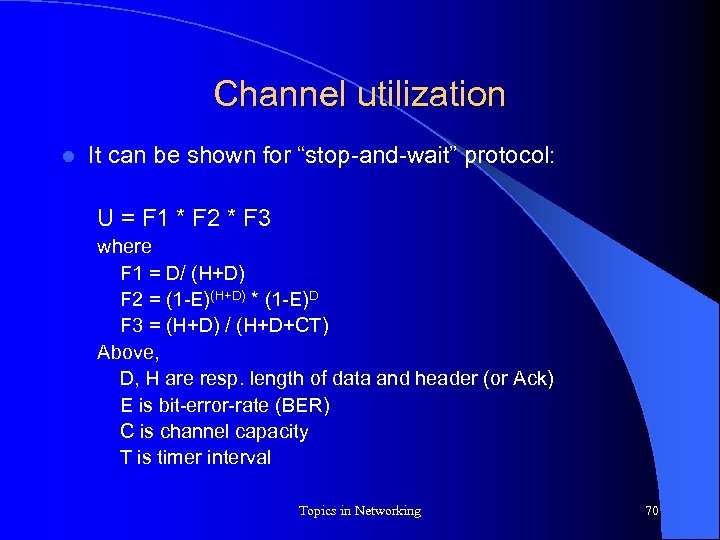 Channel utilization l It can be shown for “stop-and-wait” protocol: U = F 1 * F 2 * F 3 where F 1 = D/ (H+D) F 2 = (1 -E)(H+D) * (1 -E)D F 3 = (H+D) / (H+D+CT) Above, D, H are resp. length of data and header (or Ack) E is bit-error-rate (BER) C is channel capacity T is timer interval Topics in Networking 70
Channel utilization l It can be shown for “stop-and-wait” protocol: U = F 1 * F 2 * F 3 where F 1 = D/ (H+D) F 2 = (1 -E)(H+D) * (1 -E)D F 3 = (H+D) / (H+D+CT) Above, D, H are resp. length of data and header (or Ack) E is bit-error-rate (BER) C is channel capacity T is timer interval Topics in Networking 70
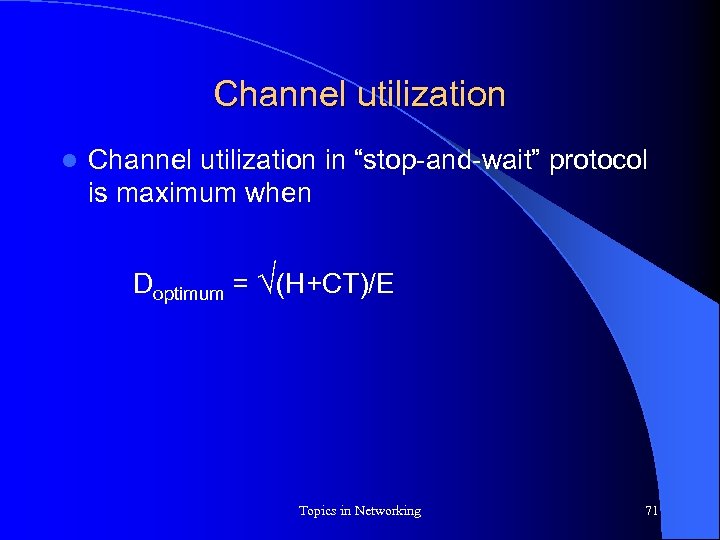 Channel utilization l Channel utilization in “stop-and-wait” protocol is maximum when Doptimum = (H+CT)/E Topics in Networking 71
Channel utilization l Channel utilization in “stop-and-wait” protocol is maximum when Doptimum = (H+CT)/E Topics in Networking 71
 Channel utilization l Channel utilization in “sliding-window” protocols is complex. Consider: – No error, large Tx window – No error, small Tx window – With possibility of errors, large Tx window – With possibility of errors, small Tx window Topics in Networking 72
Channel utilization l Channel utilization in “sliding-window” protocols is complex. Consider: – No error, large Tx window – No error, small Tx window – With possibility of errors, large Tx window – With possibility of errors, small Tx window Topics in Networking 72
 Channel utilization l What is a large enough window size? W > 1 + 2 C I / (D+H) where I = propagation delay + interrupt handling time Topics in Networking 73
Channel utilization l What is a large enough window size? W > 1 + 2 C I / (D+H) where I = propagation delay + interrupt handling time Topics in Networking 73
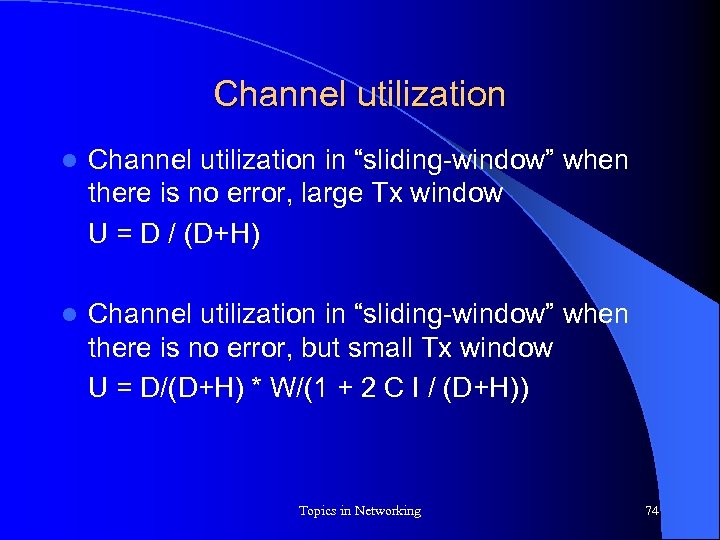 Channel utilization l Channel utilization in “sliding-window” when there is no error, large Tx window U = D / (D+H) l Channel utilization in “sliding-window” when there is no error, but small Tx window U = D/(D+H) * W/(1 + 2 C I / (D+H)) Topics in Networking 74
Channel utilization l Channel utilization in “sliding-window” when there is no error, large Tx window U = D / (D+H) l Channel utilization in “sliding-window” when there is no error, but small Tx window U = D/(D+H) * W/(1 + 2 C I / (D+H)) Topics in Networking 74
 Channel utilization l Channel utilization in “sliding-window” when there may be errors, but Tx window is small U = D/(D+H) * (1 -L) where L is the probability that a frame or an ack to it is lost l Channel utilization in “sliding-window” when there may be errors, but Tx window is small U = D/(D+H) * (1 -L) * W/(1 + 2 C I / (D+H)) Topics in Networking 75
Channel utilization l Channel utilization in “sliding-window” when there may be errors, but Tx window is small U = D/(D+H) * (1 -L) where L is the probability that a frame or an ack to it is lost l Channel utilization in “sliding-window” when there may be errors, but Tx window is small U = D/(D+H) * (1 -L) * W/(1 + 2 C I / (D+H)) Topics in Networking 75
 Channel utilization C*I is also the “delay-BW product”, l And CI/F is the delay-BW product in terms of no of frames l Channel util. Increasing delay-BW prod. Window size Topics in Networking 76
Channel utilization C*I is also the “delay-BW product”, l And CI/F is the delay-BW product in terms of no of frames l Channel util. Increasing delay-BW prod. Window size Topics in Networking 76
 Protocol Verification – Formal specification – Verification of protocol design – Conformance of an implementation to a given design Topics in Networking 77
Protocol Verification – Formal specification – Verification of protocol design – Conformance of an implementation to a given design Topics in Networking 77
 Protocol Verification l Two parts: – protocol modeling – verification Look upon the communicating entities as ONE finite state machine l Use two different, although equivalent, ways to model the machines: l – State transition diagrams – Petrinet based model Topics in Networking 78
Protocol Verification l Two parts: – protocol modeling – verification Look upon the communicating entities as ONE finite state machine l Use two different, although equivalent, ways to model the machines: l – State transition diagrams – Petrinet based model Topics in Networking 78
 Protocol verification: model using state transitions l Consider an example: stop-n-wait protocol – Consider the sender-receiver pair, together with channels as ONE single system – Focus on significant states, not intermediate states encountered while executing commands or program instructions Topics in Networking 79
Protocol verification: model using state transitions l Consider an example: stop-n-wait protocol – Consider the sender-receiver pair, together with channels as ONE single system – Focus on significant states, not intermediate states encountered while executing commands or program instructions Topics in Networking 79
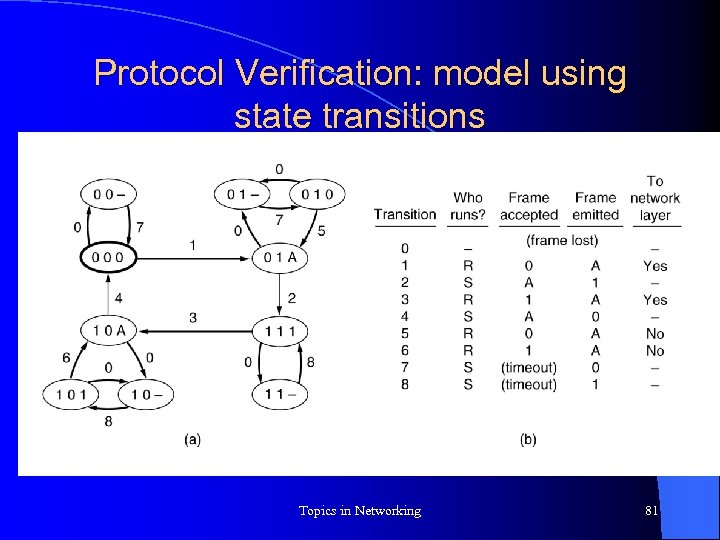
 Protocol Verification: model using state transitions l Stop-n-wait protocol components, and their states – Sender: “sending” 0 or 1 – Receiver: receiving 0 or 1 – Half-duplex channel: carrying frame 0 or 1, or Ack, or “-” – Acks are not numbered l Total no of states is 16, of which 6 are unreachable – These are states that correspond to sender and receiver waiting for next event to occur l Further, – Consider initial state – Any enabled transition may take place next – Transitions take place at any time Topics in Networking 80
Protocol Verification: model using state transitions l Stop-n-wait protocol components, and their states – Sender: “sending” 0 or 1 – Receiver: receiving 0 or 1 – Half-duplex channel: carrying frame 0 or 1, or Ack, or “-” – Acks are not numbered l Total no of states is 16, of which 6 are unreachable – These are states that correspond to sender and receiver waiting for next event to occur l Further, – Consider initial state – Any enabled transition may take place next – Transitions take place at any time Topics in Networking 80
 Protocol Verification: model using state transitions Topics in Networking 81
Protocol Verification: model using state transitions Topics in Networking 81
 Protocol Verification l Can a protocol drop a user packet? – Protocol never delivers packets in two data frames, numbered 0, without delivering packet contained in a data frame numbered 1 – Or, machine does not make two transitions numbered “ 1”, without an intervening transition “ 3” – There does not a path with two edges corresponding to “transition 1” without an intervening edge “transition 3” Topics in Networking 82
Protocol Verification l Can a protocol drop a user packet? – Protocol never delivers packets in two data frames, numbered 0, without delivering packet contained in a data frame numbered 1 – Or, machine does not make two transitions numbered “ 1”, without an intervening transition “ 3” – There does not a path with two edges corresponding to “transition 1” without an intervening edge “transition 3” Topics in Networking 82
 Protocol Verification l Can a protocol drop a sequence of two user packets? – Or, sender should not state 1 twice while receiver does not change its state in between Topics in Networking 83
Protocol Verification l Can a protocol drop a sequence of two user packets? – Or, sender should not state 1 twice while receiver does not change its state in between Topics in Networking 83
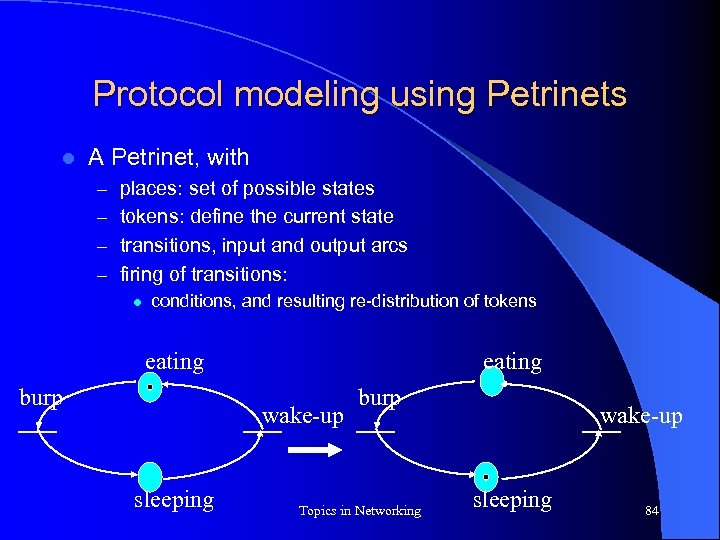 Protocol modeling using Petrinets l A Petrinet, with – places: set of possible states – tokens: define the current state – transitions, input and output arcs – firing of transitions: l conditions, and resulting re-distribution of tokens eating burp eating wake-up sleeping burp Topics in Networking wake-up sleeping 84
Protocol modeling using Petrinets l A Petrinet, with – places: set of possible states – tokens: define the current state – transitions, input and output arcs – firing of transitions: l conditions, and resulting re-distribution of tokens eating burp eating wake-up sleeping burp Topics in Networking wake-up sleeping 84
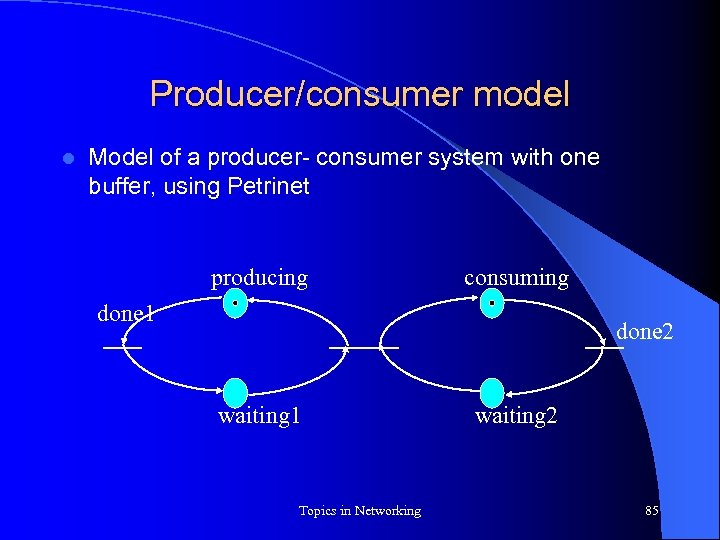 Producer/consumer model l Model of a producer- consumer system with one buffer, using Petrinet producing consuming done 1 done 2 waiting 1 Topics in Networking waiting 2 85
Producer/consumer model l Model of a producer- consumer system with one buffer, using Petrinet producing consuming done 1 done 2 waiting 1 Topics in Networking waiting 2 85
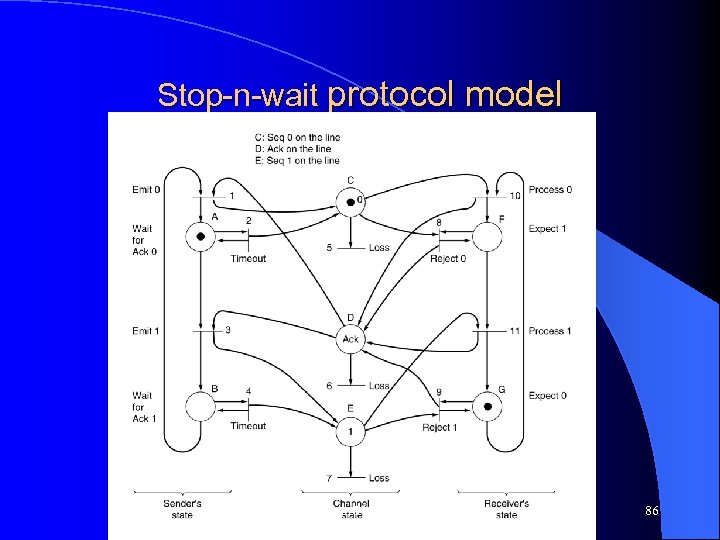 Stop-n-wait protocol model Topics in Networking 86
Stop-n-wait protocol model Topics in Networking 86
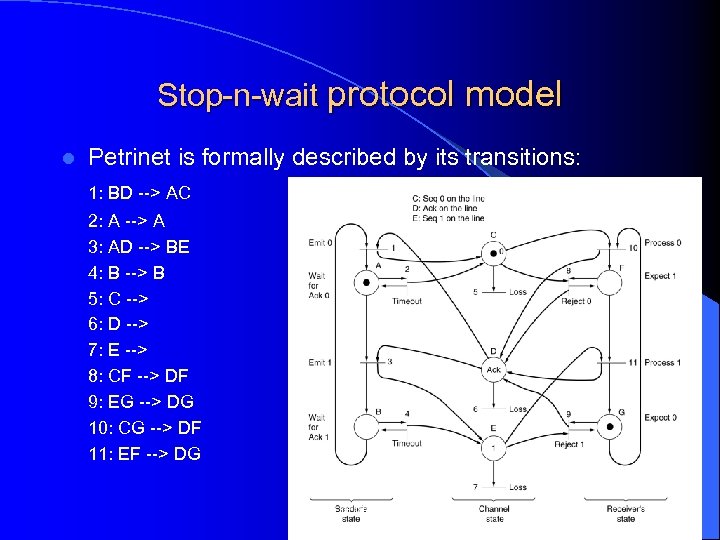 Stop-n-wait protocol model l Petrinet is formally described by its transitions: 1: BD --> AC 2: A --> A 3: AD --> BE 4: B --> B 5: C --> 6: D --> 7: E --> 8: CF --> DF 9: EG --> DG 10: CG --> DF 11: EF --> DG Topics in Networking 87
Stop-n-wait protocol model l Petrinet is formally described by its transitions: 1: BD --> AC 2: A --> A 3: AD --> BE 4: B --> B 5: C --> 6: D --> 7: E --> 8: CF --> DF 9: EG --> DG 10: CG --> DF 11: EF --> DG Topics in Networking 87
 Stop-n-wait protocol model l Using the formal specs one can formally argue about properties that are (are not) satisfied: – e. g. consider all possible sequences of transitions. Then are there two “ 10” transitions without an intervening transition “ 11”? – How would ensure that two consecutive packets are not lost Topics in Networking 88
Stop-n-wait protocol model l Using the formal specs one can formally argue about properties that are (are not) satisfied: – e. g. consider all possible sequences of transitions. Then are there two “ 10” transitions without an intervening transition “ 11”? – How would ensure that two consecutive packets are not lost Topics in Networking 88
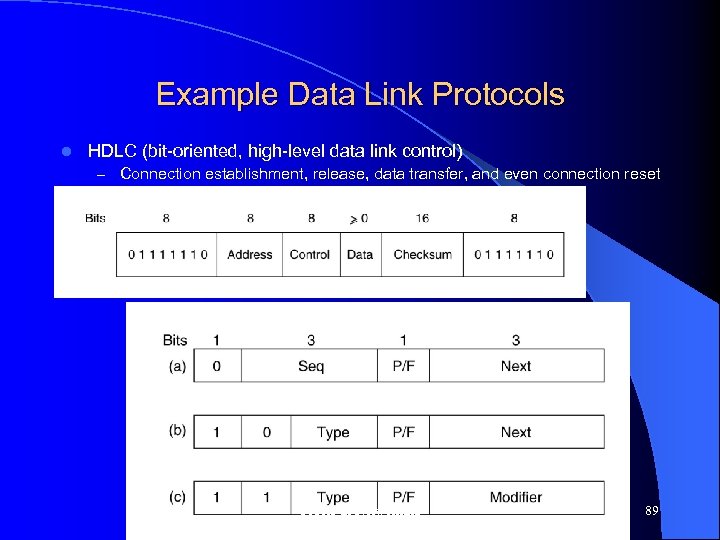 Example Data Link Protocols l HDLC (bit-oriented, high-level data link control) – Connection establishment, release, data transfer, and even connection reset Topics in Networking 89
Example Data Link Protocols l HDLC (bit-oriented, high-level data link control) – Connection establishment, release, data transfer, and even connection reset Topics in Networking 89
 Example Data Link Protocols l PPP (point-to-point protocol) – Mainly used router-to-router and dial-up connections – Connection establishment and release a data link, data transfer, and even connection reset – Help establish network layer (IP) addresses l Over LANs, the protocol is typically Ethernet Topics in Networking 90
Example Data Link Protocols l PPP (point-to-point protocol) – Mainly used router-to-router and dial-up connections – Connection establishment and release a data link, data transfer, and even connection reset – Help establish network layer (IP) addresses l Over LANs, the protocol is typically Ethernet Topics in Networking 90
 Thanks Topics in Networking 91
Thanks Topics in Networking 91


