Data_commentary_1.ppt
- Количество слайдов: 49

Data commentary Betül GÜLERYÜZ Osman AYDOĞAR

The type of writing that accompanies a visual display is called data commentary. • While data commentaries may be "standalone" pieces of writing, they generally occur in the Results or Discussion sections of a report or thesis. • The main purposes of a data commentary are to present the results of research, interpret these results, and to discuss the significance and implications of the results.
• Data can often be best expressed by a chart, graph, table, or other illustration. • The data should be presented analysed in logical manner; in other words you are expected to analyse and evaluate the data, not just describe it.
Why use a data commentary? • Highlight results • Assess standard theories, common beliefs, or general practices in light of the results • Compare and evaluate different data sets • Assess the reliability of data in terms of the methods that produced it

• Discuss implications of the data • Calls attention to something not directly apparent from the table, chart, or graph • Analyzes data for a reason: to support a claim which in turn helps achieve the main goal of the paper.

Structure of Data Commentary • Data commentaries usually have the following elements in the following order. 1. Location elements and/or summary statements 2. Highlighting statements 3. Discussions of implications, problems, exceptions, recommendations, etc.
Paragraph structure of a data commentary: • Topic sentence (claim) • Location elements and summaries (support) • Highlights (examples) • Implications (restatement of claim)

Highlighting Statements • The central sections of data commentaries consist of highlighting statements. • Highlighting statements are generalizations that you can draw from the details of the data display. • Highlighting statements need good judgment. They are an opportunity to show your intelligence. .

In particular, they are an opportunity for you to demonstrate • that you can spot trends or regularities in the data, • that you can separate more important findings from less important ones, and • that you can make claims of appropriate strength
So, do not • simply repeat all the details in words, • attempt to cover all the information, or • claim more than is reasonable or defensible.

Verbs for introducing highlights • Table 2 shows the most common factors are… • Figure 2. 3 illustrates the results of a study that… • Table 9 demonstrates how the use of… • …the most common are displayed in Table 3. • …details of the operation are given in Figure 4. 4. • …these qualities are suggested by Figure 9. 3. Other verbs: provide, present, summarize, reveal, indicate

Language Focus: Linking as. Clauses • These linking clauses (where as does not equal since or because) are exceptional in English grammar. In the passive, these linking clauses have no subjects. Compare the following sentences. a. As it has been proved, theory may have practical importance. b. As has been proved, theory may have practical importance. In sentence a there is a causal relationship between the asclause and the main clause. Because theory has been proved, it may have practical importance.

Some Specific ways for qualifying or moderating a claim • • 1 -Probability 2 -Distance 3 -Generalization 4 -Weaker verbs

Indicative Summary - Indicates what has been done in the work • Table 5 shows the most common modes of computer infection for U. S. businesses. • Figure 4. 2 gives the results of the second experiment.

Indicating the strengths of data results • A reduced speed limit will result in fewer accidents. • A reduced speed limit may result in fewer accidents. • A reduced speed limit could result in fewer accidents. • It is certain that… • It is almost certain that… • It is highly probable that…

• • • It is possible that… It is unlikely that… There is a strong possibility that… There is a slight possibility that… There is a remote possibility that…

Informative Summary • Provides a summary of the data. • Table 5 shows that home disks are the major source of computer viruses. • Table 4. 2 suggests that the experimental results confirm the hypothesis.

Table 5. Means of PC Infection in U. S. Businesses. Source Percentage • • Disks from home 43% Electronic bulletin board 7% Sales demonstration disk 6% Repair or service disk 6% Company, client, or consultant disk 4% Other 9% Undetermined 29%

• 1) A computer virus is a program that is specifically and maliciously designed to attack a computer system, destroying data. 2) As businesses have become increasingly dependent on computer systems, concern over the potential destructiveness of such viruses has also grown. 3) Table 5 shows the most common modes of infection for U. S. businesses. -location and indicative summary. 4) As can be seen, in the majority of cases, the source of the virus infection can be detected, with disks being brought to the workplace from home being by far the most significant (43%). 5) However, it is alarming to note that the source of nearly 30% of viruses cannot be determined. 6) While it may be possible to eliminate home-toworkplace infection by requiring computer users to run antiviral software on diskettes brought from home, businesses are still vulnerable to major data loss, especially from unidentifiable sources of infection.

Passive voice a. The most common modes of infection are shown in Table 5. b. Details of the fertilizers used are provided in Table 2. c. The results of the second experiment are given in Figure 4. 2.

Passive Verbs in Reference to a Visual • • • Shown in Illustrated in Presented in Given in Listed in Seen in Provided in Summarized in Seen from

Active voice a. Table 5 shows the most common modes of computer infections. b. Table 2 provides details of the fertilizer used. c. Figure 4. 2 gives the results of the second experiment.

Active Verbs Following Reference to a Visual • • • Shows Presents Illustrates Summarizes Demonstrates Contains Provides Depicts Lists Reports

• In order to investigate the hypothesis that 8 -year old boys are more aggressive than 8 -year old girls, 8 -year old children were observed playing in schoolyards and incidents of certain aggressive behaviors were recorded.

Aggressive Girls Boys behavior • • Pushing 21% 35% Kicking/Hitting 15% 61% Cursing 9% 30% Chasing 78% 1%

Commentary 1 • 1) In order to investigate the hypothesis that 8 year old boys are more aggressive than 8 -year old girls, 8 -year old children were observed playing in schoolyards and incidents of certain aggressive behaviors were recorded. 2)Table 1 shows that boys are more aggressive than girls. 3)The percentage of pushing is 21% of girl; on the other hand that of boys is 35%. 4)Except for chasing, the percentage of aggressive behavior is higher in boys. 5)From this data you can agree that boys are more aggressive than girls. (Rating: 73)

Commentary 2 • 1) In order to investigate the hypothesis that 8 -year old boys are more aggressive than 8 -year old girls, 8 -year old children were observed playing in schoolyards and incidents of certain aggressive behaviors were recorded. 2)As you can see in Table 1, we only considered four human aggressive behaviors in our study. 3)The most common children aggressive conduct are pushing, kicking/hitting, cursing, and chasing. 4)After several weeks of observation in different schools playground we found the percentage that appeared on table 1. 5) (See attachment 1) 6) Sixty percent (61%) of the boys like to kick and hit compared to fifteen percent (15%) of the girls. 7)This is more aggressive than chasing. 8)The chasing behavior was the only one girls were more aggressive than boys. (Rating: 77)

Commentary 3 • 1) In order to investigate the hypothesis that 8 -year old boys are more aggressive than 8 -year old girls, 8 -year old children were observed playing in schoolyards and incidents of certain aggressive behaviors were recorded. 2)It was assumed that aggressive behavior consisted of the following: i) pushing, ii) kicking and hitting, iii) cursing, and iv) chasing. 3)As can be seen from the table above, the average 8 -year old boy was more aggressive than the 8 -year old girls. 4)Chasing was the one behavior that was more pronounced for the girls. 5)This result, however, does not disprove theory since chasing seems to be a less aggressive behavior than the other behaviors that were tested. 6) The 8 -year old boys got more involved with the more aggressive behavior, which is kicking/hitting, much more than the 8 -year old girls. (Rating: 93)

Commentary 4 • 1) In order to investigate the hypothesis that 8 -year old boys are more aggressive than 8 -year old girls, 8 -year old children were observed playing in schoolyards and incidents of certain aggressive behaviors were recorded. 2)At first glance it appears that 8 -year old boys exhibit more aggressive behavior than 8 -year old girls if all four recorded behaviors are equally weighed. 3)But, this last assertion is false. 4)Since the ability to record will vary with playground size and the number of observers (not to mention the skills of the observers or accounting for children entering or leaving the playground), and that it takes a certain amount of an observers time to note the behavior, short-lived behaviors such as cursing or pushing could be under- represented. 5)Simply because more can occur during the time an observer notes another behavior. 6)Conversely, long-lived behaviors such as chasing could be over-represented because they occur over a longer period of time and thus allow more latitude for the observer marking the behavior. (Rating: 93)
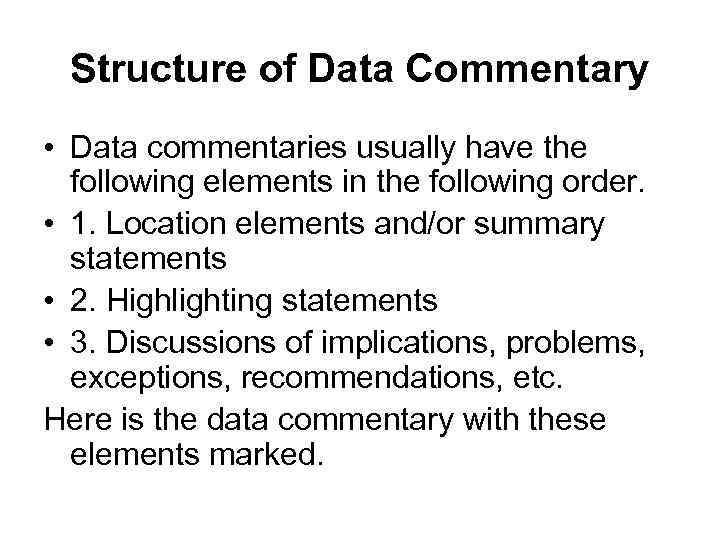
Structure of Data Commentary • Data commentaries usually have the following elements in the following order. • 1. Location elements and/or summary statements • 2. Highlighting statements • 3. Discussions of implications, problems, exceptions, recommendations, etc. Here is the data commentary with these elements marked.
![• [Location + indicative summary] Table 5 shows the most common sources of • [Location + indicative summary] Table 5 shows the most common sources of](https://present5.com/presentation/34515160_164621462/image-31.jpg)
• [Location + indicative summary] Table 5 shows the most common sources of infection for U. S. businesses. [Linking as-clause and highlight] As can be seen, in a great majority of cases, the entry point of the virus infection can be detected, with e-mail attachments being responsible for nearly 9 out of 10 viruses. [Implications] This very high percentage is increasingly alarming, especially since with a certain amount of caution such infections are largely preventable. • 0 In conseqence, e-mail users should be wary of all attachments, even those from a trusted colleague. In addition, all computers used for e-mail need to have a current version of a good antivirus program whose virus definitions are updated regularly. While it may be possible to lessen the likelihood of downloading an infected file, businesses are still vulnerable to computer virus problems because of human error and the threat of new, quickly spreading viruses that cannot be identified by antivirus software.
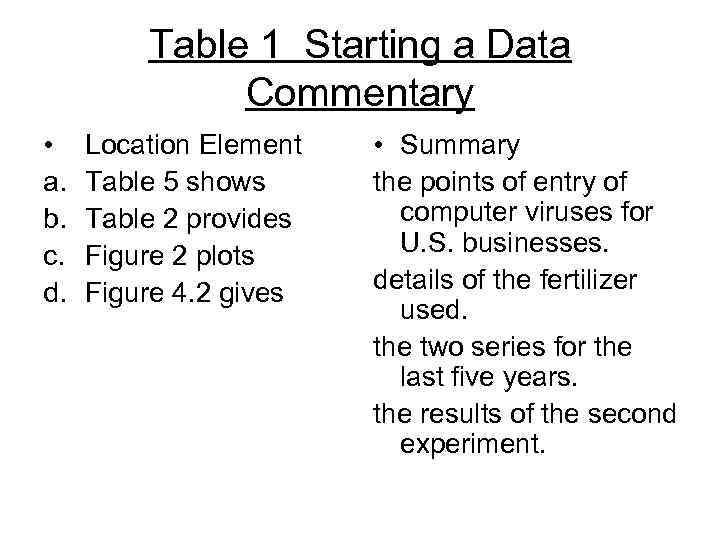
Table 1 Starting a Data Commentary • a. b. c. d. Location Element Table 5 shows Table 2 provides Figure 2 plots Figure 4. 2 gives • Summary the points of entry of computer viruses for U. S. businesses. details of the fertilizer used. the two series for the last five years. the results of the second experiment.

Table 2 Passives in Starting a Data Commentary • Summary a. The most common modes of computer infection b. The details of the fertilizer used c. The two series for the last five years d. The results of the second experiment • a. b. c. d. Location Element are shown in Table 5. are provided in Table 2. are plotted in Figure 2. are given In Figure 4. 2.

Language Focus: Linking as. Clauses A more common structure for introducing informative statements is the linking as-clause. • As shown in Fig. 1 and Fig. 2, the companies used in this survey varied significantly in geographical location, size, and method of operation. • As can be seen in Table 5, the overall rate of recall, while low, also showed considerable variation.

Using prepositions • in As shown in Table 1. . . • by As predicted by the model. . . • on As described on the previous page. . .

Highlighting Statements • Highlighting statements are generalizations that you can draw from the details of the data display.

• Highlighting statements need good judgment. They are an opportunity to show your intelligence. In particular, they are an opportunity for you to demonstrate • that you can spot trends or regularities in the data, • that you can separate more important findings from less important ones, and • that you can make claims of appropriate strength.
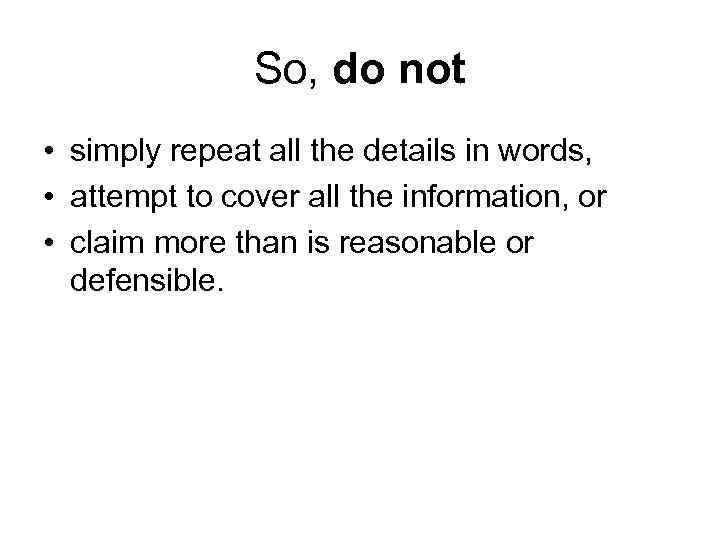
So, do not • simply repeat all the details in words, • attempt to cover all the information, or • claim more than is reasonable or defensible.
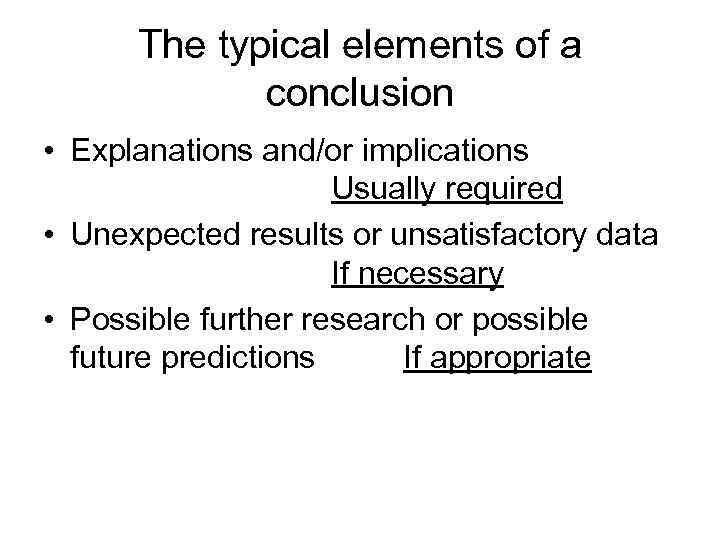
The typical elements of a conclusion • Explanations and/or implications Usually required • Unexpected results or unsatisfactory data If necessary • Possible further research or possible future predictions If appropriate

• Source: Swales, J. M. , & Feak, C. B. (2004). Academic writing for graduate students: Essential tasks and skills (2 nd ed. ). Ann Arbor, MI: The University of Michigan Press.

Describing Trends and Projections • A trend is a description of change over time. A projection is a prediction of future change. Trends and projections are usually illustrated using line graphs in which the horizontal axis represents time. Some of the language commonly used for writing about trends and projections is given below.

The graph shows that there has been a • slight • gradual • steady • marked • steep • sharp increase rise decrease fall decline drop in the number of divorces in England Wales since 1981.

Describing high and low points in figures • The number of live births outside marriage reached a peak during the second world war. • The peak age for committing a crime is 18. • Oil production peaked in 1985. • Gas production reached a (new) low in 1990.
• http: //www. phrasebank. manchester. ac. uk/t rends. htm

Referring to Literature • A considerable amount of literature has been published on X. These studies. . . • There is a large volume of published studies describing the role of …… • The first serious discussions and analyses of X emerged during the 1970 s with. . . • The generalisability of much published research on this issue is problematic. • What we know about X is largely based upon empirical studies that investigate how. . . • During the past 30 years much more information has become available on. . . • In recent years, there has been an increasing amount of literature on. . . . • A large and growing body of literature has investigated. . .

Being Critical • One question that needs to be asked, however, is whether. . . • A serious weakness with this argument, however, is that. . . • One of the limitations with this explanation is that it does not explain why. . • One criticism of much of the literature on X is that. . . • The key problem with this explanation is that. . . • The existing accounts fail to resolve the contradiction between X and Y. • However, there is an inconsistency with this argument.

Summarising the content • This paper has given an account of and the reasons for the widespread use of X. . . • This essay has argued that X is the best instrument to. . . • This assignment has explained the central importance of X in Y. • This dissertation has investigated. . .
• http: //www. monash. edu. au/lls/llonline/writi ng/information-technology/businesssystems/index. xml
• http: //www. slideshare. net/bettul 01/datacommentary
Data_commentary_1.ppt