633d438076c07d9a5696ae751f1861ab.ppt
- Количество слайдов: 25
 Data and Applications Security Developments and Directions Dr. Bhavani Thuraisingham The University of Texas at Dallas Trustworthy Semantic Webs March 25, 2011
Data and Applications Security Developments and Directions Dr. Bhavani Thuraisingham The University of Texas at Dallas Trustworthy Semantic Webs March 25, 2011
 Outline l Semantic web l XML security l RDF security l Ontologies and Security l Rules and Security l Reference: - Building trustworthy semantic web, Thuraisingham, CRC Press, 2007
Outline l Semantic web l XML security l RDF security l Ontologies and Security l Rules and Security l Reference: - Building trustworthy semantic web, Thuraisingham, CRC Press, 2007
 From Today’s Web to Semantic web l Today’s web - High recall, low precision: Too many web pages resulting in searches, many not relevant - Sometimes low recall - Results sensitive to vocabulary: Different words even if they mean the same thing do not results in same web pages - Results are single web pages not linked web pages l Semantic web - Machine understandable web pages - Activities on the web such as searching with little or no human intervention - Technologies for knowledge management, e-commerce, interoperability - Solutions to the problems faced by today’s web
From Today’s Web to Semantic web l Today’s web - High recall, low precision: Too many web pages resulting in searches, many not relevant - Sometimes low recall - Results sensitive to vocabulary: Different words even if they mean the same thing do not results in same web pages - Results are single web pages not linked web pages l Semantic web - Machine understandable web pages - Activities on the web such as searching with little or no human intervention - Technologies for knowledge management, e-commerce, interoperability - Solutions to the problems faced by today’s web
 Knowledge Management and Personal Agents l Knowledge Management - Corporation Need: Searching, extracting and maintaining information, uncovering hidden dependencies, viewing information - Semantic web for knowledge management: Organizing knowledge, automated tools for maintaining knowledge, question answering, querying multiple documents, controlling access to documents l Personal Agent - John is a president of a company. He needs to have a surgery for a serious but not a critical illness. With current web he has to check each web page for relevant information, make decisions depending on the information provided - With the semantic web, the agent will retrieve all the relevant information, synthesize the information, ask John if needed, and then present the various options and makes recommendations
Knowledge Management and Personal Agents l Knowledge Management - Corporation Need: Searching, extracting and maintaining information, uncovering hidden dependencies, viewing information - Semantic web for knowledge management: Organizing knowledge, automated tools for maintaining knowledge, question answering, querying multiple documents, controlling access to documents l Personal Agent - John is a president of a company. He needs to have a surgery for a serious but not a critical illness. With current web he has to check each web page for relevant information, make decisions depending on the information provided - With the semantic web, the agent will retrieve all the relevant information, synthesize the information, ask John if needed, and then present the various options and makes recommendations
 E-Commerce l Business to Consumer - Users shopping on the web; wrapper technology is used to extract information about user preferences etc. and display the products to the user - Use of semantic web: Develop software agents that can interpret privacy requirements, pricing and product information and display timely and correct information to the use; also provides information about the reputation of shops l Business to Business - Organizations work together and carrying out transactions such as collaborating on a product, supply chains etc. With today’s web lack of standards for data exchange - Use of semantic web: XML is a big improvement, but need to agree on vocabulary. Future will be the use of ontologies to agree on meanings and interpretations
E-Commerce l Business to Consumer - Users shopping on the web; wrapper technology is used to extract information about user preferences etc. and display the products to the user - Use of semantic web: Develop software agents that can interpret privacy requirements, pricing and product information and display timely and correct information to the use; also provides information about the reputation of shops l Business to Business - Organizations work together and carrying out transactions such as collaborating on a product, supply chains etc. With today’s web lack of standards for data exchange - Use of semantic web: XML is a big improvement, but need to agree on vocabulary. Future will be the use of ontologies to agree on meanings and interpretations
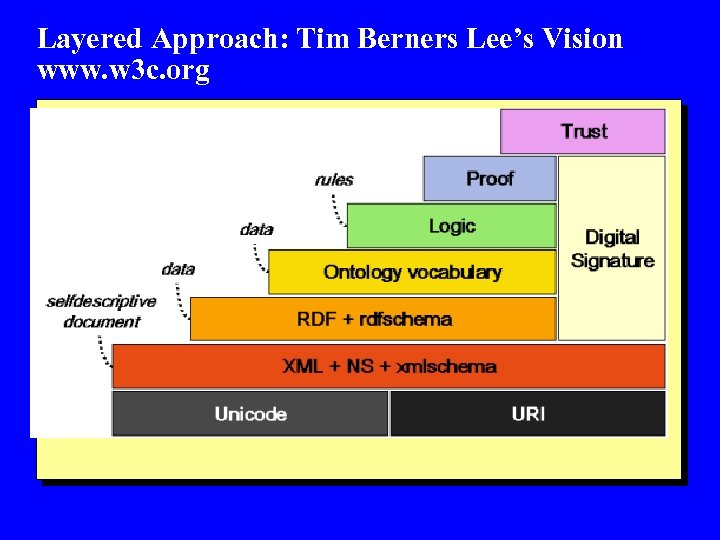 Layered Approach: Tim Berners Lee’s Vision www. w 3 c. org
Layered Approach: Tim Berners Lee’s Vision www. w 3 c. org
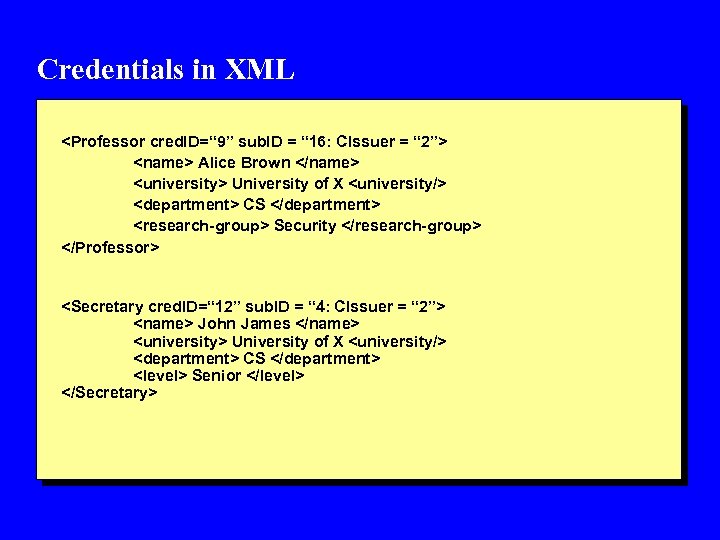 Credentials in XML
Credentials in XML
 Policies in XML
Policies in XML
 Access Control Strategy l Subjects request access to XML documents under two modes: Browsing and authoring - With browsing access subject can read/navigate documents Authoring access is needed to modify, delete, append documents l Access control module checks the policy based and applies policy specs l Views of the document are created based on credentials and policy specs l In case of conflict, least access privilege rule is enforced l Works for Push/Pull modes
Access Control Strategy l Subjects request access to XML documents under two modes: Browsing and authoring - With browsing access subject can read/navigate documents Authoring access is needed to modify, delete, append documents l Access control module checks the policy based and applies policy specs l Views of the document are created based on credentials and policy specs l In case of conflict, least access privilege rule is enforced l Works for Push/Pull modes
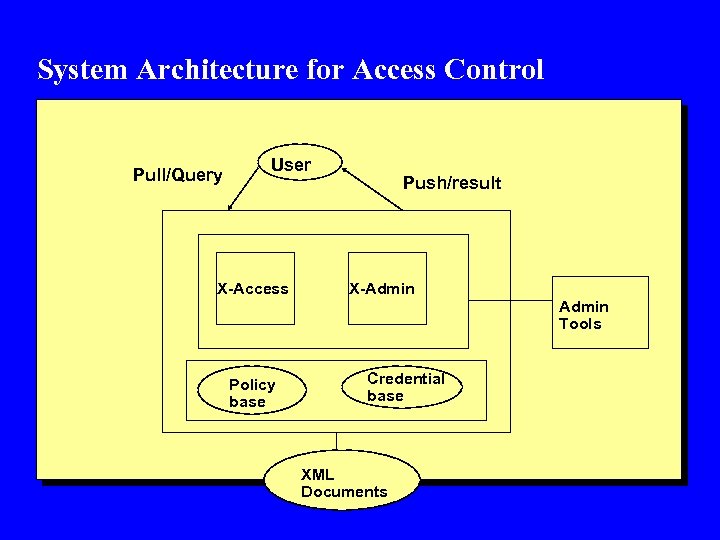 System Architecture for Access Control Pull/Query User X-Access Push/result X-Admin Tools Policy base Credential base XML Documents
System Architecture for Access Control Pull/Query User X-Access Push/result X-Admin Tools Policy base Credential base XML Documents
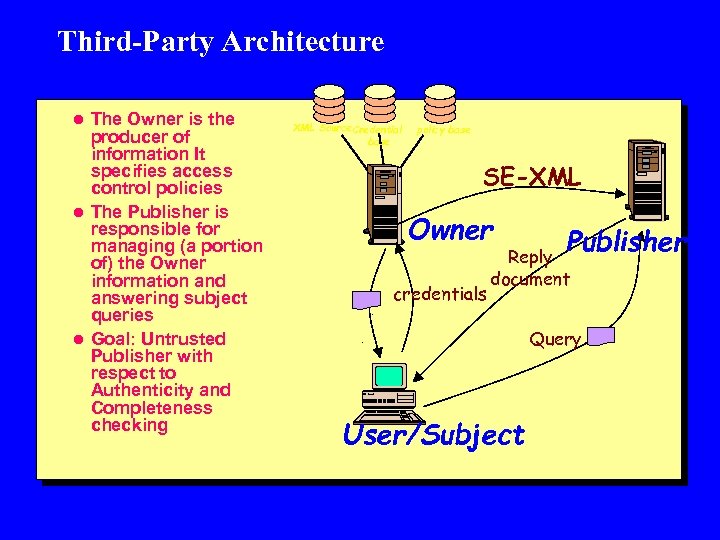 Third-Party Architecture l The Owner is the producer of information It specifies access control policies l The Publisher is responsible for managing (a portion of) the Owner information and answering subject queries l Goal: Untrusted Publisher with respect to Authenticity and Completeness checking XML Source Credential base policy base SE-XML Owner credentials Publisher Reply document Query User/Subject
Third-Party Architecture l The Owner is the producer of information It specifies access control policies l The Publisher is responsible for managing (a portion of) the Owner information and answering subject queries l Goal: Untrusted Publisher with respect to Authenticity and Completeness checking XML Source Credential base policy base SE-XML Owner credentials Publisher Reply document Query User/Subject
 XML Databases l Data is presented as XML documents l Query language: XML-QL l Query optimization l Managing transactions on XML documents l Metadata management: XML schemas/DTDs l Access methods and index strategies l XML security and integrity management
XML Databases l Data is presented as XML documents l Query language: XML-QL l Query optimization l Managing transactions on XML documents l Metadata management: XML schemas/DTDs l Access methods and index strategies l XML security and integrity management
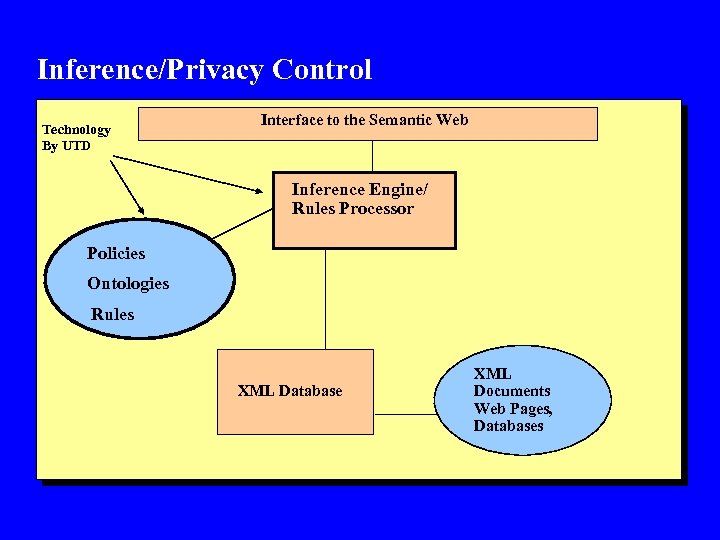 Inference/Privacy Control Technology By UTD Interface to the Semantic Web Inference Engine/ Rules Processor Policies Ontologies Rules XML Database XML Documents Web Pages, Databases
Inference/Privacy Control Technology By UTD Interface to the Semantic Web Inference Engine/ Rules Processor Policies Ontologies Rules XML Database XML Documents Web Pages, Databases
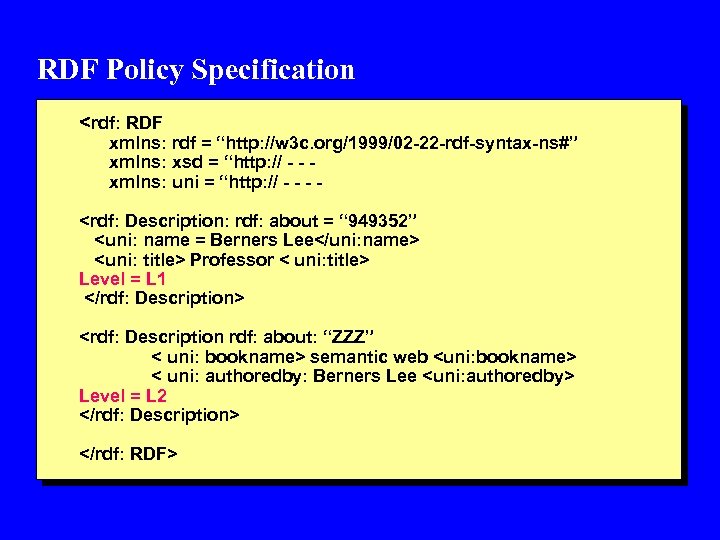 RDF Policy Specification
RDF Policy Specification
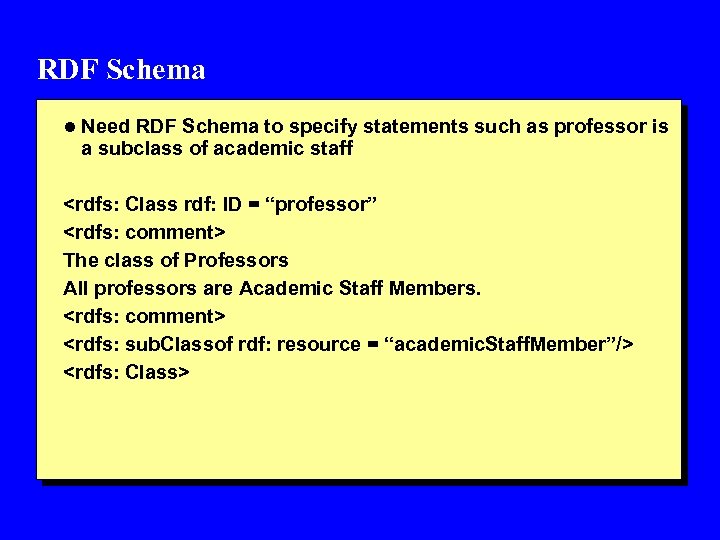 RDF Schema l Need RDF Schema to specify statements such as professor is a subclass of academic staff
RDF Schema l Need RDF Schema to specify statements such as professor is a subclass of academic staff
 RDF Schema: Security Policies l How can security policies be specified?
RDF Schema: Security Policies l How can security policies be specified?
 RDF Inferencing l While first order logic provides a proof system, it will be computationally infeasible l As a result horn clause logic was developed for logic programming; this is still computationally expensive l RDF uses If then Rules l IF E contains the triples (? u, rdfs: sub. Classof, ? v) and (? v, rdfs: sub. Classof ? w) THEN E also contains the triple (? u, rdfs: sub. Class. Of, ? w) That is, if u is a subclass of v, and v is a subclass of w, then u is a subclass of w
RDF Inferencing l While first order logic provides a proof system, it will be computationally infeasible l As a result horn clause logic was developed for logic programming; this is still computationally expensive l RDF uses If then Rules l IF E contains the triples (? u, rdfs: sub. Classof, ? v) and (? v, rdfs: sub. Classof ? w) THEN E also contains the triple (? u, rdfs: sub. Class. Of, ? w) That is, if u is a subclass of v, and v is a subclass of w, then u is a subclass of w
 RDF Query l One can query RDF using XML, but this will be very difficult as RDF is much richer than XML l Is there an analogy between say XQuery and a query language for RDF? l RQL – an SQL-like language has been developed for RDF l Select from “RDF document” where some “condition”
RDF Query l One can query RDF using XML, but this will be very difficult as RDF is much richer than XML l Is there an analogy between say XQuery and a query language for RDF? l RQL – an SQL-like language has been developed for RDF l Select from “RDF document” where some “condition”
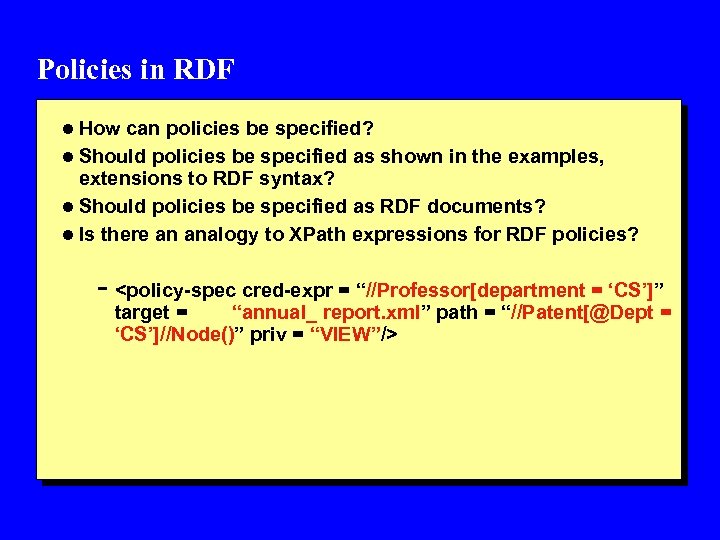 Policies in RDF l How can policies be specified? l Should policies be specified as shown in the examples, extensions to RDF syntax? l Should policies be specified as RDF documents? l Is there an analogy to XPath expressions for RDF policies? -
Policies in RDF l How can policies be specified? l Should policies be specified as shown in the examples, extensions to RDF syntax? l Should policies be specified as RDF documents? l Is there an analogy to XPath expressions for RDF policies? -
 Security and Ontology l Ontologies used to specify security policies - Example: OWL to specify security policies - Choice between XML, RDF, OWL, Rules ML, etc. l Security for Ontologies - Access control on Ontologies l Give access to certain parts of the Ontology
Security and Ontology l Ontologies used to specify security policies - Example: OWL to specify security policies - Choice between XML, RDF, OWL, Rules ML, etc. l Security for Ontologies - Access control on Ontologies l Give access to certain parts of the Ontology
 Policies in OWL l How can policies be specified? l Should policies be specified as shown in the examples, extensions to OWL syntax? l Should policies be specified as OWL documents? l Is there an analogy to XPath expressions for OWL policies? -
Policies in OWL l How can policies be specified? l Should policies be specified as shown in the examples, extensions to OWL syntax? l Should policies be specified as OWL documents? l Is there an analogy to XPath expressions for OWL policies? -
 Policies in OWL: Example < owl: Class rdf: about = “#associate. Professor”>
Policies in OWL: Example < owl: Class rdf: about = “#associate. Professor”>
 Logic and Inference l First order predicate logic l High level language to express knowledge l Well understood semantics l Logical consequence - inference l Proof systems exist l Sound and complete l OWL is based on a subset of logic – descriptive logic
Logic and Inference l First order predicate logic l High level language to express knowledge l Well understood semantics l Logical consequence - inference l Proof systems exist l Sound and complete l OWL is based on a subset of logic – descriptive logic
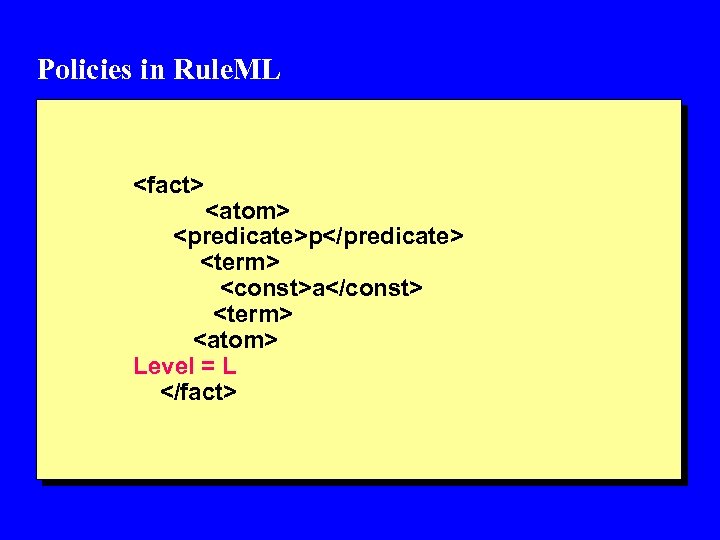 Policies in Rule. ML
Policies in Rule. ML
 Common Threads and Challenges l Common Threads - Building Ontologies for Semantics - XML for Syntax l Challenges - Scalability, Resolvability - Security policy specification, Securing the documents and ontologies - Developing applications for secure semantic web technologies - Automated tools for ontology management l Creating, maintaining, evolving and querying ontologies
Common Threads and Challenges l Common Threads - Building Ontologies for Semantics - XML for Syntax l Challenges - Scalability, Resolvability - Security policy specification, Securing the documents and ontologies - Developing applications for secure semantic web technologies - Automated tools for ontology management l Creating, maintaining, evolving and querying ontologies


