fd91d93be45a6e2a640a69970d06c957.ppt
- Количество слайдов: 24
 Data and Applications Security Developments and Directions Dr. Bhavani Thuraisingham The University of Texas at Dallas Lecture #13 Secure Distributed Object Systems February 22, 2005
Data and Applications Security Developments and Directions Dr. Bhavani Thuraisingham The University of Texas at Dallas Lecture #13 Secure Distributed Object Systems February 22, 2005
 Outline l Background l Object Request Brokers l Secure Object Request Brokers l Dependable Object Request Brokers l Directions
Outline l Background l Object Request Brokers l Secure Object Request Brokers l Dependable Object Request Brokers l Directions
 Object Model: Review l Objects- every entity is an object - Example: Book, Film, Employee, Car l Class - Objects with common attributes are grouped into a class l Attributes or Instance Variables - Properties of an object class inherited by the object instances l Class Hierarchy - Parent-Child class hierarchy l Composite objects - Book object with paragraphs, sections etc. l Methods - Functions associated with a class
Object Model: Review l Objects- every entity is an object - Example: Book, Film, Employee, Car l Class - Objects with common attributes are grouped into a class l Attributes or Instance Variables - Properties of an object class inherited by the object instances l Class Hierarchy - Parent-Child class hierarchy l Composite objects - Book object with paragraphs, sections etc. l Methods - Functions associated with a class
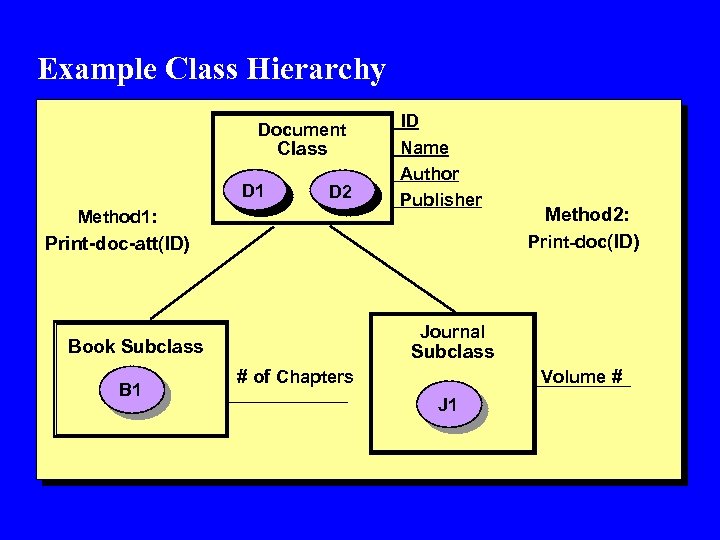 Example Class Hierarchy Document Class D 1 D 2 Method 1: ID Name Author Publisher Print-doc-att(ID) Journal Book Subclass B 1 Method 2: Print-doc(ID) Subclass Volume # # of Chapters J 1
Example Class Hierarchy Document Class D 1 D 2 Method 1: ID Name Author Publisher Print-doc-att(ID) Journal Book Subclass B 1 Method 2: Print-doc(ID) Subclass Volume # # of Chapters J 1
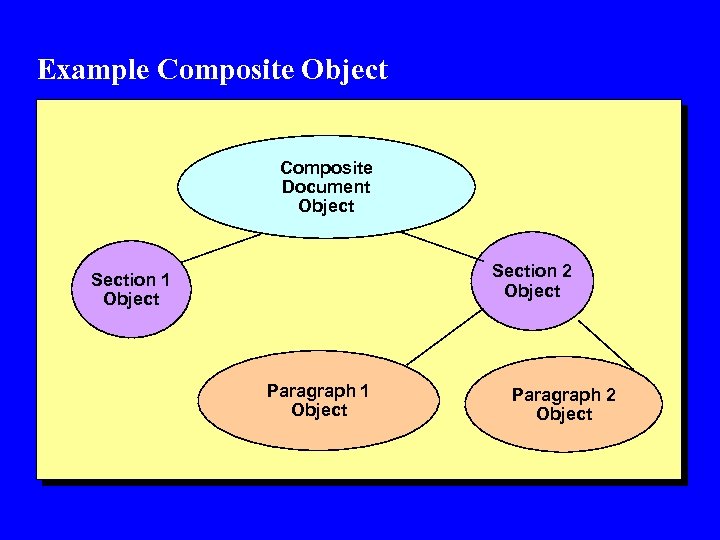 Example Composite Object Composite Document Object Section 2 Object Section 1 Object Paragraph 2 Object
Example Composite Object Composite Document Object Section 2 Object Section 1 Object Paragraph 2 Object
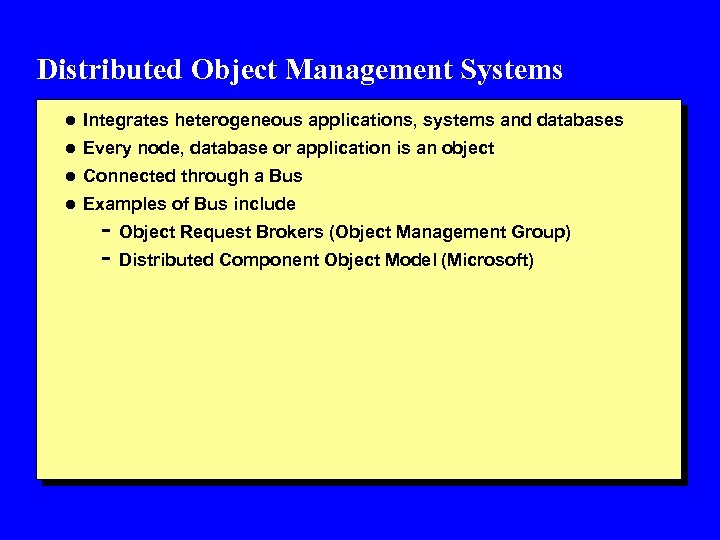 Distributed Object Management Systems l Integrates heterogeneous applications, systems and databases l Every node, database or application is an object l Connected through a Bus l Examples of Bus include - Object Request Brokers (Object Management Group) - Distributed Component Object Model (Microsoft)
Distributed Object Management Systems l Integrates heterogeneous applications, systems and databases l Every node, database or application is an object l Connected through a Bus l Examples of Bus include - Object Request Brokers (Object Management Group) - Distributed Component Object Model (Microsoft)
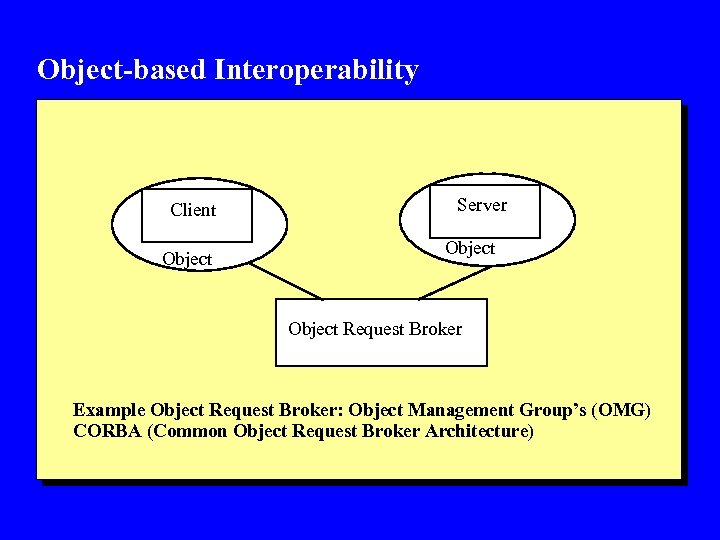 Object-based Interoperability Client Object Server Object Request Broker Example Object Request Broker: Object Management Group’s (OMG) CORBA (Common Object Request Broker Architecture)
Object-based Interoperability Client Object Server Object Request Broker Example Object Request Broker: Object Management Group’s (OMG) CORBA (Common Object Request Broker Architecture)
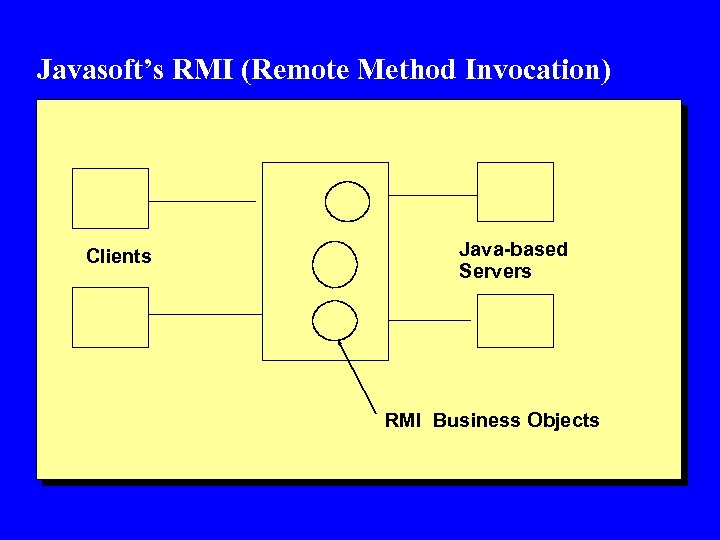 Javasoft’s RMI (Remote Method Invocation) Clients Java-based Servers RMI Business Objects
Javasoft’s RMI (Remote Method Invocation) Clients Java-based Servers RMI Business Objects
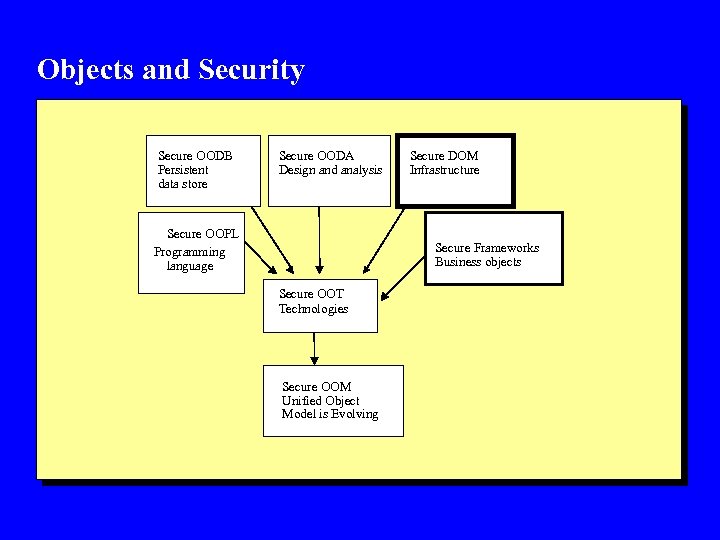 Objects and Security Secure OODB Persistent data store Secure OODA Design and analysis Secure OOPL Programming language Secure DOM Infrastructure Secure Frameworks Business objects Secure OOT Technologies Secure OOM Unified Object Model is Evolving
Objects and Security Secure OODB Persistent data store Secure OODA Design and analysis Secure OOPL Programming language Secure DOM Infrastructure Secure Frameworks Business objects Secure OOT Technologies Secure OOM Unified Object Model is Evolving
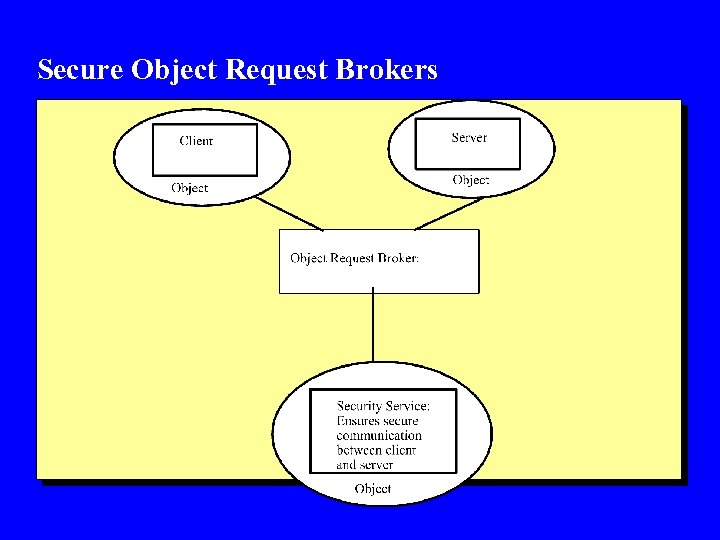 Secure Object Request Brokers
Secure Object Request Brokers
 CORBA (Common Object Request Broker Architecture) Security l Security Service provides the following: - Confidentiality - Integrity - Accountability - Availability l URLs - http: //www. javaolympus. com/J 2 SE/NETWORKING/CORBA/COR BASecurity. jsp - http: //student. cosy. sbg. ac. at/~amayer/projects/corbasec/sec_ov erview. html - www. omg. org
CORBA (Common Object Request Broker Architecture) Security l Security Service provides the following: - Confidentiality - Integrity - Accountability - Availability l URLs - http: //www. javaolympus. com/J 2 SE/NETWORKING/CORBA/COR BASecurity. jsp - http: //student. cosy. sbg. ac. at/~amayer/projects/corbasec/sec_ov erview. html - www. omg. org
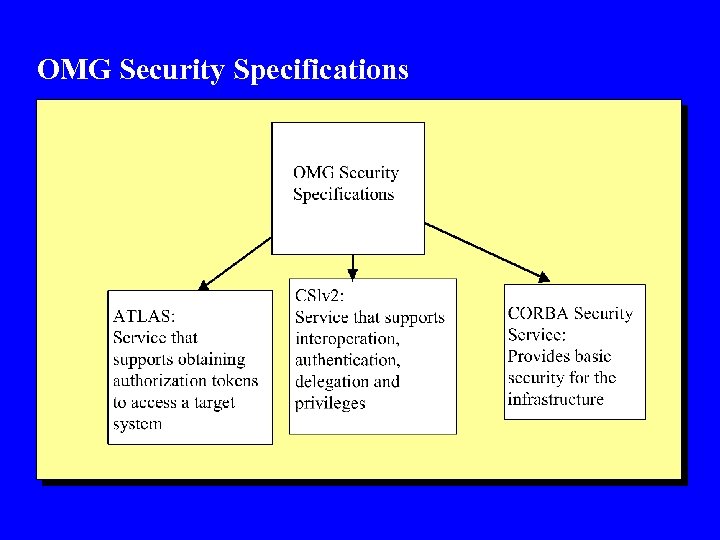 OMG Security Specifications
OMG Security Specifications
 CORBA (Common Object Request Broker Architecture) Security l Security Service provides the following: - Confidentiality - Integrity - Accountability - Availability l URLs - http: //www. javaolympus. com/J 2 SE/NETWORKING/CORBA/COR BASecurity. jsp - http: //student. cosy. sbg. ac. at/~amayer/projects/corbasec/sec_ov erview. html - www. omg. org
CORBA (Common Object Request Broker Architecture) Security l Security Service provides the following: - Confidentiality - Integrity - Accountability - Availability l URLs - http: //www. javaolympus. com/J 2 SE/NETWORKING/CORBA/COR BASecurity. jsp - http: //student. cosy. sbg. ac. at/~amayer/projects/corbasec/sec_ov erview. html - www. omg. org
 CORBA (Common Object Request Broker Architecture) Security - 2 l Identification and Authentication of Principles l Authorization and Access Control l Security Auditing l Security of communications l Administration of security information l Non repudiation
CORBA (Common Object Request Broker Architecture) Security - 2 l Identification and Authentication of Principles l Authorization and Access Control l Security Auditing l Security of communications l Administration of security information l Non repudiation
 CORBA (Common Object Request Broker Architecture) Security - 2 l Identification and Authentication of Principles l Authorization and Access Control l Security Auditing l Security of communications l Administration of security information l Non repudiation
CORBA (Common Object Request Broker Architecture) Security - 2 l Identification and Authentication of Principles l Authorization and Access Control l Security Auditing l Security of communications l Administration of security information l Non repudiation
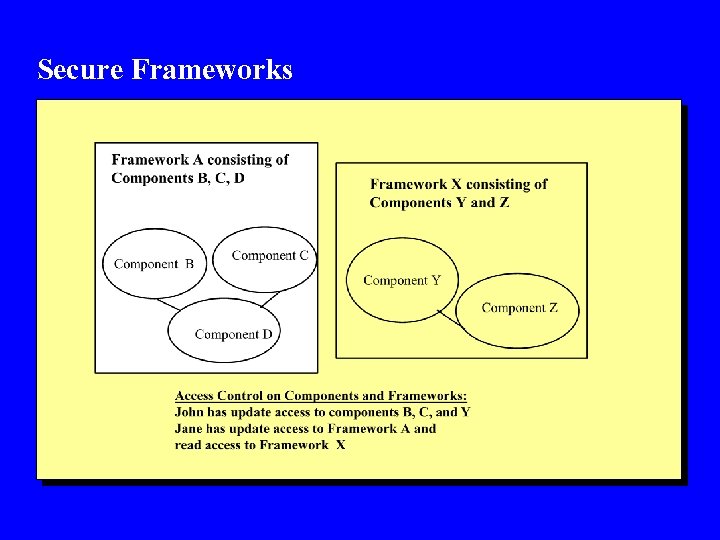 Secure Frameworks
Secure Frameworks
 Overview: Migrating Legacy Systems l Many of the current systems and applications may become obsolete l Need an approach to migrate these systems to new architectures l Evolutionary approach: incremental transition of today's systems into more flexible systems l Extensible system architecture ultimately replaces today's hardware and software architecture l Open systems approach, standards l Security has to be considered throughout the migration processes
Overview: Migrating Legacy Systems l Many of the current systems and applications may become obsolete l Need an approach to migrate these systems to new architectures l Evolutionary approach: incremental transition of today's systems into more flexible systems l Extensible system architecture ultimately replaces today's hardware and software architecture l Open systems approach, standards l Security has to be considered throughout the migration processes
 Migrating Legacy Database and Applications l Build business model in a sub-domain and relate data to existing databases and systems. l Wrap existing systems to provide access as needed. l Incorporate middle tier services and begin migrating workflow. l Gradually migrate business logic and rely on business objects for end-user systems. l Security policies must be enforced by the old and migrated systems
Migrating Legacy Database and Applications l Build business model in a sub-domain and relate data to existing databases and systems. l Wrap existing systems to provide access as needed. l Incorporate middle tier services and begin migrating workflow. l Gradually migrate business logic and rely on business objects for end-user systems. l Security policies must be enforced by the old and migrated systems
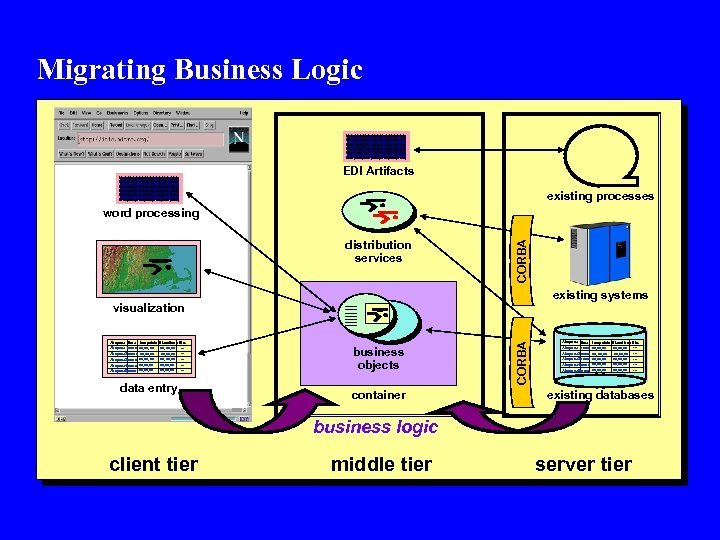 Migrating Business Logic blah, blah, blah, blah, blah, blah, blah, blah, blah, blah, blah, blah, blah, blah, blah, blah, blah, blah, blah, blah, blah, EDI Artifacts existing processes distribution services CORBA word processing existing systems Airspace time turnpoints Airspace nn: nn xx, xx Airspace 2 nn: nn xx, xx Airspace 3 nn: nn xx, xx Airspace 4 nn: nn xx, xx Airspace 5 nn: nn xx, xx Elevations Etc. . . . xx, xx, xx. . . data entry business objects container CORBA visualization Airspace time turnpoints Airspace nn: nn xx, xx Airspace 2 nn: nn xx, xx Airspace 3 nn: nn xx, xx Airspace 4 nn: nn xx, xx Airspace 5 nn: nn xx, xx Elevations Etc. . . . xx, xx, xx. . . existing databases business logic client tier middle tier server tier
Migrating Business Logic blah, blah, blah, blah, blah, blah, blah, blah, blah, blah, blah, blah, blah, blah, blah, blah, blah, blah, blah, blah, blah, EDI Artifacts existing processes distribution services CORBA word processing existing systems Airspace time turnpoints Airspace nn: nn xx, xx Airspace 2 nn: nn xx, xx Airspace 3 nn: nn xx, xx Airspace 4 nn: nn xx, xx Airspace 5 nn: nn xx, xx Elevations Etc. . . . xx, xx, xx. . . data entry business objects container CORBA visualization Airspace time turnpoints Airspace nn: nn xx, xx Airspace 2 nn: nn xx, xx Airspace 3 nn: nn xx, xx Airspace 4 nn: nn xx, xx Airspace 5 nn: nn xx, xx Elevations Etc. . . . xx, xx, xx. . . existing databases business logic client tier middle tier server tier
 Application vs. Database Migration l Extract schema from the legacy code - Use reengineering tools l Extract metadata associated with the data l Deal with incomplete data and fill in the gaps l Build schemas in the target system from the extracted schema l Build the database l Enforce the security policies
Application vs. Database Migration l Extract schema from the legacy code - Use reengineering tools l Extract metadata associated with the data l Deal with incomplete data and fill in the gaps l Build schemas in the target system from the extracted schema l Build the database l Enforce the security policies
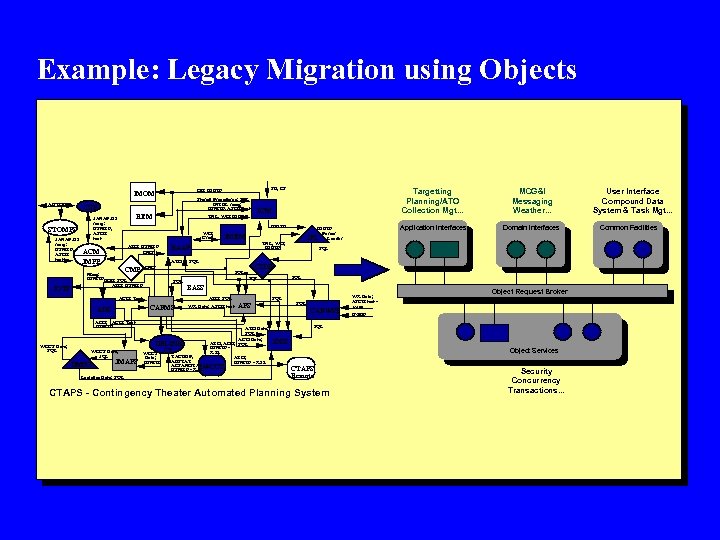 Example: Legacy Migration using Objects AUTODIN STOMPS JANAP 128 mesg: USMTF, ASCII text TNL, WO; IDBTF REM ATO; USMTF CMS ACM JMPP CMS Mesg: USMTF EOB; SQL ATO; USMTF ATO ACO; Text USMTF WCCS Data; JQL UMSG JMAPS Logistics Data; SQL UFLINK CI WCCS Data; USMTF SQL CIDB SQL BASS ATO; SQL CAFMS ADS SQL WX Data; ASCII text APS ATO Data; SQL ACO Data; ATO, ACO; SQL USMTF X. 25 ATO; USMTF - X. 25 TACREP, ABSTAT ACSAMSTAT; USMTF - X. 25 WCCS Domain Interfaces IPL TNL, WO; IDBTF SQL IDBTF Parser Loader JMEM MCG&I Messaging Weather. . . Application Interfaces ICM RAAP ACO; Text WCCS Data; SQL Targetting Planning/ATO Collection Mgt. . . IDBTF WO; Cmd CMP JOTS Stored Procedures; SQL INTEL mesg; USMTF, ASCII text CSP JANAP 128 mesg: USMTF, ASCII text SB, CS OB; IDBTF IMOM SQL CAFWSP WX Data; ASCII text AWN UGDF Object Request Broker SQL JDSS Object Services CTAPS Remote CTAPS - Contingency Theater Automated Planning System Security Concurrency Transactions. . . User Interface Compound Data System & Task Mgt. . . Common Facilities
Example: Legacy Migration using Objects AUTODIN STOMPS JANAP 128 mesg: USMTF, ASCII text TNL, WO; IDBTF REM ATO; USMTF CMS ACM JMPP CMS Mesg: USMTF EOB; SQL ATO; USMTF ATO ACO; Text USMTF WCCS Data; JQL UMSG JMAPS Logistics Data; SQL UFLINK CI WCCS Data; USMTF SQL CIDB SQL BASS ATO; SQL CAFMS ADS SQL WX Data; ASCII text APS ATO Data; SQL ACO Data; ATO, ACO; SQL USMTF X. 25 ATO; USMTF - X. 25 TACREP, ABSTAT ACSAMSTAT; USMTF - X. 25 WCCS Domain Interfaces IPL TNL, WO; IDBTF SQL IDBTF Parser Loader JMEM MCG&I Messaging Weather. . . Application Interfaces ICM RAAP ACO; Text WCCS Data; SQL Targetting Planning/ATO Collection Mgt. . . IDBTF WO; Cmd CMP JOTS Stored Procedures; SQL INTEL mesg; USMTF, ASCII text CSP JANAP 128 mesg: USMTF, ASCII text SB, CS OB; IDBTF IMOM SQL CAFWSP WX Data; ASCII text AWN UGDF Object Request Broker SQL JDSS Object Services CTAPS Remote CTAPS - Contingency Theater Automated Planning System Security Concurrency Transactions. . . User Interface Compound Data System & Task Mgt. . . Common Facilities
 What does CORBA provide? l CORBA provides an evolvable system integration platform l CORBA provides a path for legacy migration - Applications can be coarsely wrapped as CORBA objects, providing 100% reuse l Wrapping is a relatively straight forward technique l Need to dig to uncover hidden dependencies l Does not address duplication of common functions - Applications can be reengineered to replace duplicated functions with CORBA based common services l Substantially more difficult than coarse wrapping
What does CORBA provide? l CORBA provides an evolvable system integration platform l CORBA provides a path for legacy migration - Applications can be coarsely wrapped as CORBA objects, providing 100% reuse l Wrapping is a relatively straight forward technique l Need to dig to uncover hidden dependencies l Does not address duplication of common functions - Applications can be reengineered to replace duplicated functions with CORBA based common services l Substantially more difficult than coarse wrapping
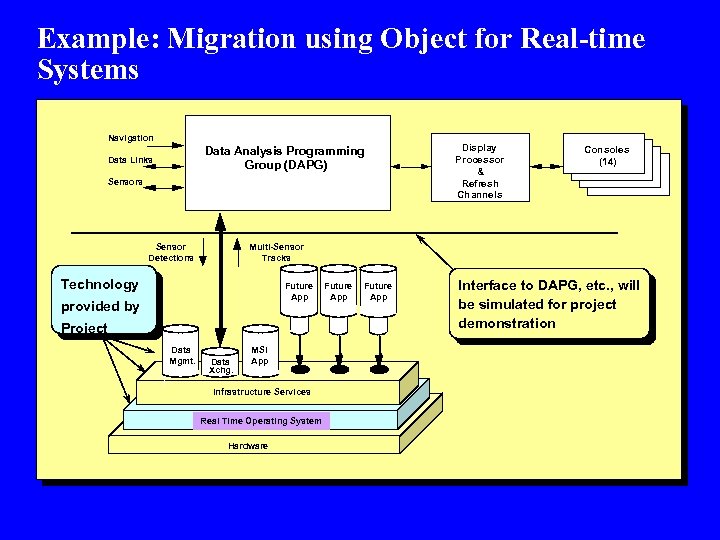 Example: Migration using Object for Real-time Systems Navigation Data Analysis Programming Group (DAPG) Data Links Sensor Detections Consoles (14) Multi-Sensor Tracks Technology Future App provided by Project Data Mgmt. Display Processor & Refresh Channels Data Xchg. MSI App Infrastructure Services Real Time Operating System Hardware Future App Interface to DAPG, etc. , will be simulated for project demonstration
Example: Migration using Object for Real-time Systems Navigation Data Analysis Programming Group (DAPG) Data Links Sensor Detections Consoles (14) Multi-Sensor Tracks Technology Future App provided by Project Data Mgmt. Display Processor & Refresh Channels Data Xchg. MSI App Infrastructure Services Real Time Operating System Hardware Future App Interface to DAPG, etc. , will be simulated for project demonstration
 Directions l Security cannot be an afterthought for object-based interoperability l Use ORBs that have implemented security services l Trends are moving towards Java based interoperability and Enterprise Application Integration (EAI) l Examples of EAI products are Web Sphere (IBM) and Web Logic (BEA) l Security has to be incorporated into EAI products
Directions l Security cannot be an afterthought for object-based interoperability l Use ORBs that have implemented security services l Trends are moving towards Java based interoperability and Enterprise Application Integration (EAI) l Examples of EAI products are Web Sphere (IBM) and Web Logic (BEA) l Security has to be incorporated into EAI products


