439c8f8ce290ce8a1043b083210b0e48.ppt
- Количество слайдов: 24
 Data and Applications Security Developments and Directions Dr. Bhavani Thuraisingham The University of Texas at Dallas Lecture #22 Secure Web Information Management and Digital Libraries March 31, 2005
Data and Applications Security Developments and Directions Dr. Bhavani Thuraisingham The University of Texas at Dallas Lecture #22 Secure Web Information Management and Digital Libraries March 31, 2005
 Outline l Web Security l Secure Web Data Management l Secure Digital Libraries
Outline l Web Security l Secure Web Data Management l Secure Digital Libraries
 Web Security l End-to-end security - Need to secure the clients, servers, networks, operating systems, transactions, data, and programming languages - The various systems when put together have to be secure l Composable properties for security l Access control rules, enforce security policies, auditing, intrusion detection l Verification and validation l Security solutions proposed by W 3 C and OMG l Java Security l Firewalls l Digital signatures and Message Digests, Cryptography
Web Security l End-to-end security - Need to secure the clients, servers, networks, operating systems, transactions, data, and programming languages - The various systems when put together have to be secure l Composable properties for security l Access control rules, enforce security policies, auditing, intrusion detection l Verification and validation l Security solutions proposed by W 3 C and OMG l Java Security l Firewalls l Digital signatures and Message Digests, Cryptography
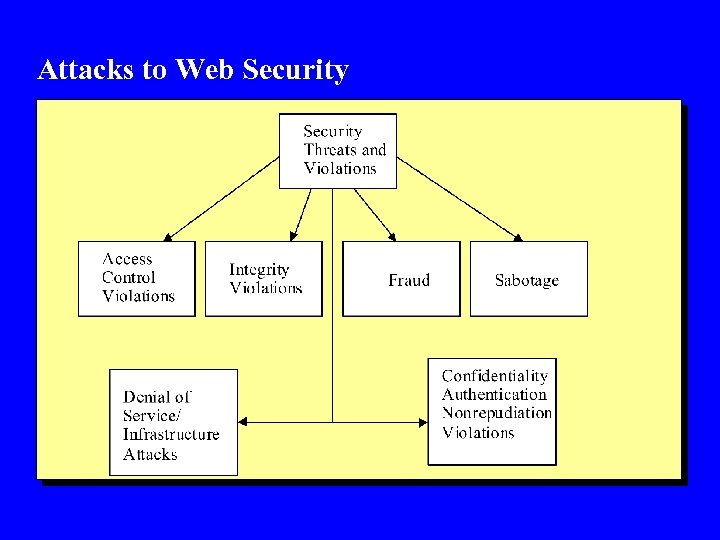 Attacks to Web Security
Attacks to Web Security
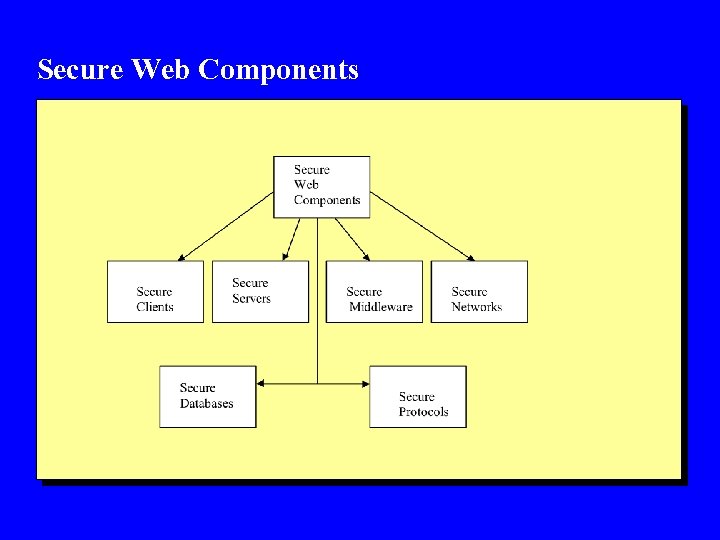 Secure Web Components
Secure Web Components
 E-Commerce Transactions l E-commerce functions are carried out as transactions - Banking and trading on the internet - Each data transaction could contain many tasks l Database transactions may be built on top of the data transaction service - Database transactions are needed for multiuser access to web databases - Need to enforce concurrency control and recovery techniques
E-Commerce Transactions l E-commerce functions are carried out as transactions - Banking and trading on the internet - Each data transaction could contain many tasks l Database transactions may be built on top of the data transaction service - Database transactions are needed for multiuser access to web databases - Need to enforce concurrency control and recovery techniques
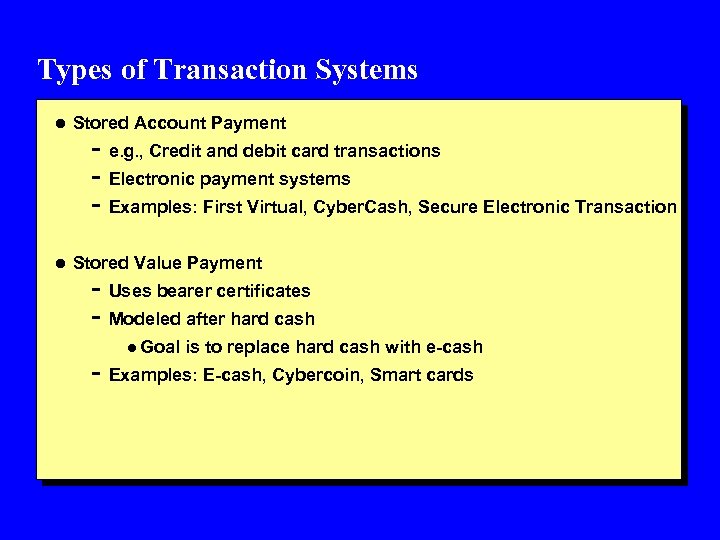 Types of Transaction Systems l Stored Account Payment - e. g. , Credit and debit card transactions - Electronic payment systems - Examples: First Virtual, Cyber. Cash, Secure Electronic Transaction l Stored Value Payment - Uses bearer certificates - Modeled after hard cash l Goal is to replace hard cash with e-cash - Examples: E-cash, Cybercoin, Smart cards
Types of Transaction Systems l Stored Account Payment - e. g. , Credit and debit card transactions - Electronic payment systems - Examples: First Virtual, Cyber. Cash, Secure Electronic Transaction l Stored Value Payment - Uses bearer certificates - Modeled after hard cash l Goal is to replace hard cash with e-cash - Examples: E-cash, Cybercoin, Smart cards
 What is E-Cash? l Electronic Cash is stored in a hardware token l Token may be loaded with money - Digital cash from the bank l Buyer can make payments to seller’s token (offline) l Buyer can pay to seller’s bank (online) l Both cases agree upon protocols l Both parties may use some sort of cryptographic key mechanism to improve security
What is E-Cash? l Electronic Cash is stored in a hardware token l Token may be loaded with money - Digital cash from the bank l Buyer can make payments to seller’s token (offline) l Buyer can pay to seller’s bank (online) l Both cases agree upon protocols l Both parties may use some sort of cryptographic key mechanism to improve security
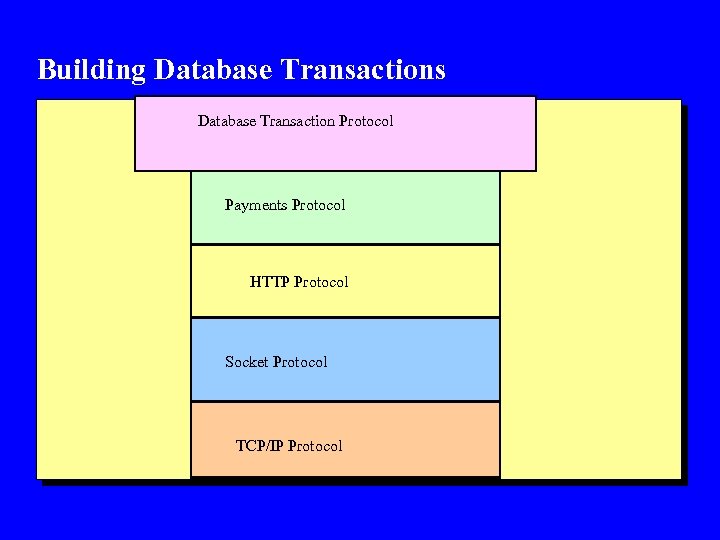 Building Database Transactions Database Transaction Protocol Payments Protocol HTTP Protocol Socket Protocol TCP/IP Protocol
Building Database Transactions Database Transaction Protocol Payments Protocol HTTP Protocol Socket Protocol TCP/IP Protocol
 Secure Web databases l Secure data models - Secure XML, RDF, - - Relational, object-oriented, text, images, video, etc. l Secure data management functions - Secure query, transactions, storage, metadata l Key components for secure digital libraries and information retrieval/browsing
Secure Web databases l Secure data models - Secure XML, RDF, - - Relational, object-oriented, text, images, video, etc. l Secure data management functions - Secure query, transactions, storage, metadata l Key components for secure digital libraries and information retrieval/browsing
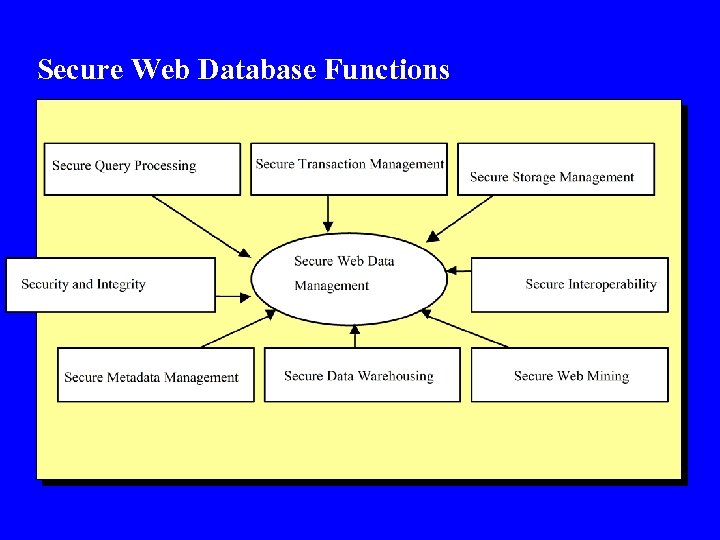 Secure Web Database Functions
Secure Web Database Functions
 Secure Query Management: Language Issues l Query language to access the databases - SQL extensions are being examined - XML-based query languages combined with SQL are emerging Example: XML-QL l XML extensions for Multimedia databases such as SMIL (Synchronized Multimedia Interface Language) - l Mappings between multiple languages l Web rules and query languages developed by W 3 C l Security should be incorporated into all aspects
Secure Query Management: Language Issues l Query language to access the databases - SQL extensions are being examined - XML-based query languages combined with SQL are emerging Example: XML-QL l XML extensions for Multimedia databases such as SMIL (Synchronized Multimedia Interface Language) - l Mappings between multiple languages l Web rules and query languages developed by W 3 C l Security should be incorporated into all aspects
 Secure Transaction Management l Example transaction on the web - Multiple users attempting to buy a product - Wait for a certain period to get the highest bid l i. e. , objects are not locked immediately l Flexible transaction models for the various types of transactions - Long duration transactions, short transactions, workflow-based transactions Electronic commerce is a major application l Concurrency control protocols Weak/strict serializability Fine grained/coarse grained locking l Cover channels analysis; E-Commerce Security -
Secure Transaction Management l Example transaction on the web - Multiple users attempting to buy a product - Wait for a certain period to get the highest bid l i. e. , objects are not locked immediately l Flexible transaction models for the various types of transactions - Long duration transactions, short transactions, workflow-based transactions Electronic commerce is a major application l Concurrency control protocols Weak/strict serializability Fine grained/coarse grained locking l Cover channels analysis; E-Commerce Security -
 Security/Integrity Management l Support for flexible security policies l Negotiations between different database administrators l Authorization and access control models such as role- based access control l Identification and authentication l Privacy Control l Copyright protection / Plagiarism l Multilevel security: Trusted Computing Base? l Maintaining the quality of the data coming from foreign sources
Security/Integrity Management l Support for flexible security policies l Negotiations between different database administrators l Authorization and access control models such as role- based access control l Identification and authentication l Privacy Control l Copyright protection / Plagiarism l Multilevel security: Trusted Computing Base? l Maintaining the quality of the data coming from foreign sources
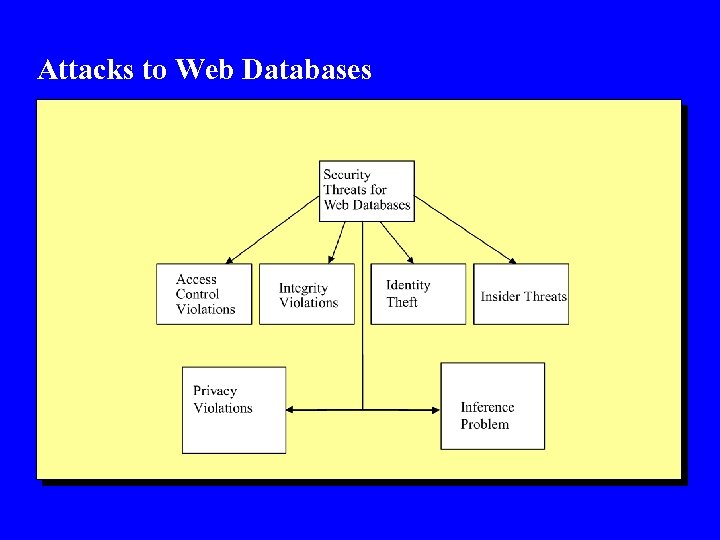 Attacks to Web Databases
Attacks to Web Databases
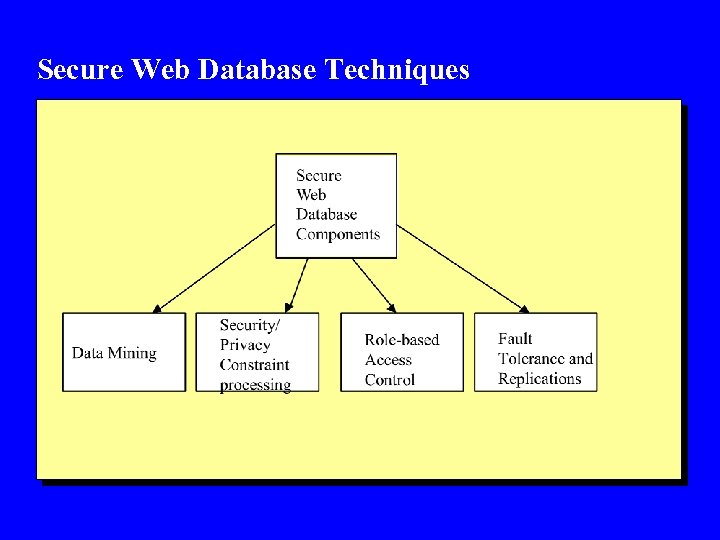 Secure Web Database Techniques
Secure Web Database Techniques
 Secure Digital Libraries l Digital libraries are e-libraries - Several communities have developed digital libraries l Medical, Social, Library of Congress l Components technologies - Web data management, Multimedia, information retrieval, indexing, browsing, -- - - l Security has to be incorporated into all aspects - Secure models for digital libraries, secure functions
Secure Digital Libraries l Digital libraries are e-libraries - Several communities have developed digital libraries l Medical, Social, Library of Congress l Components technologies - Web data management, Multimedia, information retrieval, indexing, browsing, -- - - l Security has to be incorporated into all aspects - Secure models for digital libraries, secure functions
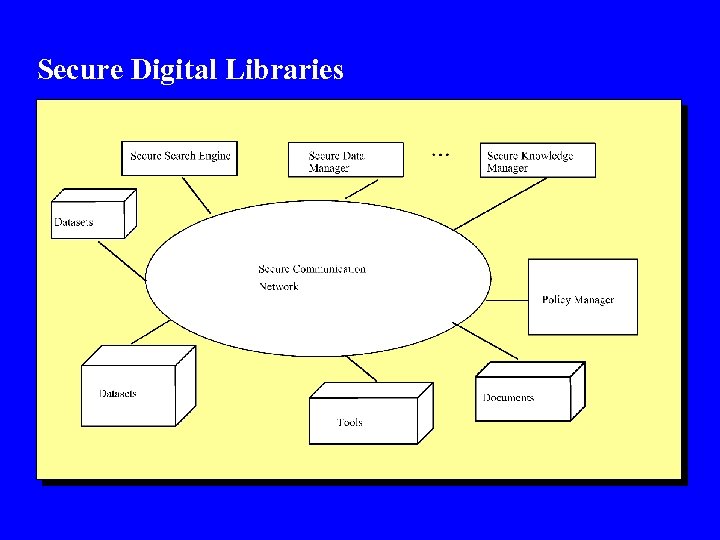 Secure Digital Libraries
Secure Digital Libraries
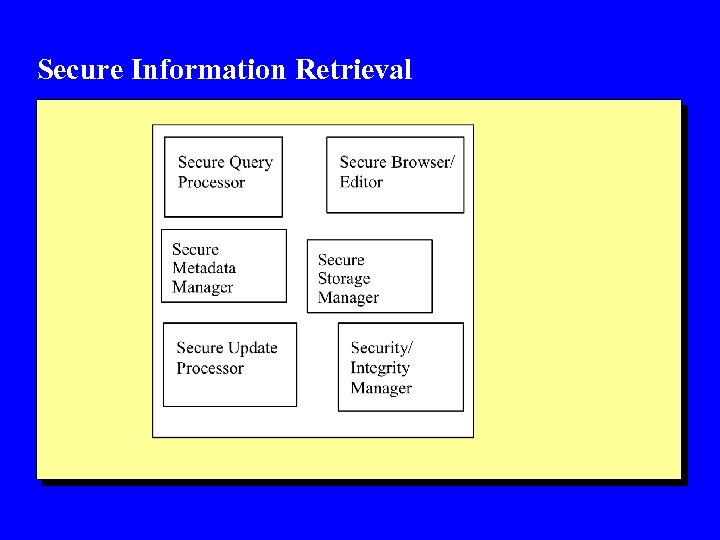 Secure Information Retrieval
Secure Information Retrieval
 Secure Browsing l Browser augments a multimedia system to develop a hypermedia system l Search space consist of nodes and links with different access control rules and/or classification levels l Can a user traverse a link or access the contents of a node? - What authorization does he/she have?
Secure Browsing l Browser augments a multimedia system to develop a hypermedia system l Search space consist of nodes and links with different access control rules and/or classification levels l Can a user traverse a link or access the contents of a node? - What authorization does he/she have?
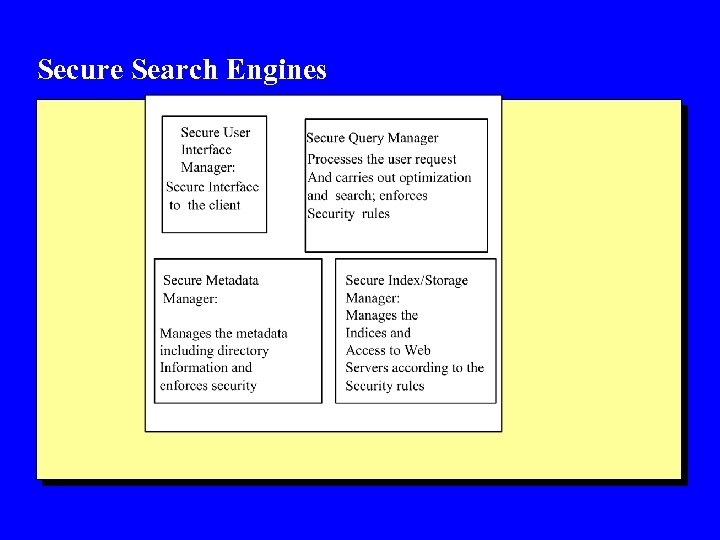 Secure Search Engines
Secure Search Engines
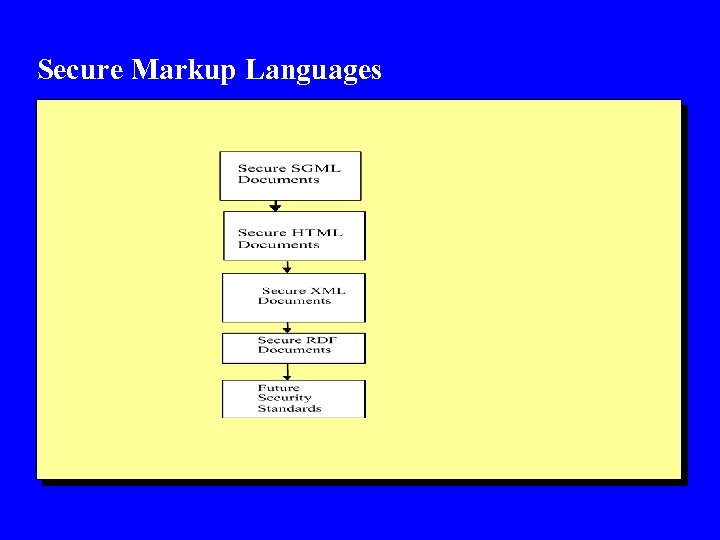 Secure Markup Languages
Secure Markup Languages
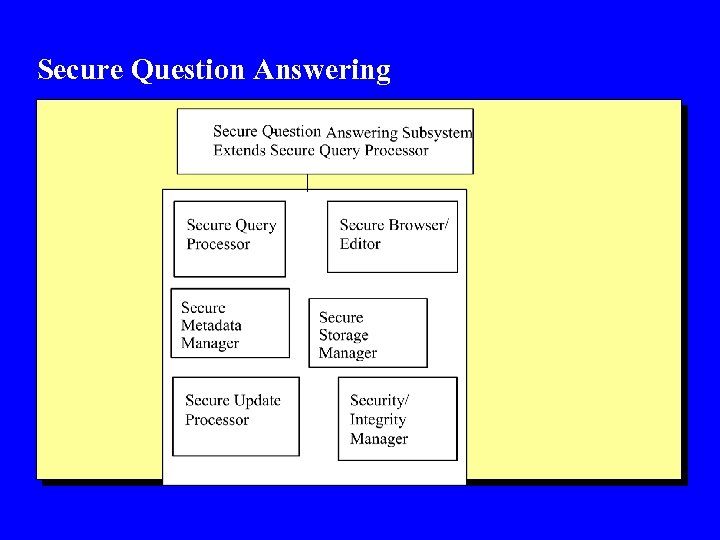 Secure Question Answering
Secure Question Answering
 Summary and Directions l End-to-end security - Secure networks, clients, servers, middleware - Secure Web databases, agents, information retrieval systems, browsers, search engines, - - l As technologies evolve, more security problems Data mining, intrusion detection, encryption are some of the technologies for security l Next steps Secure semantic web, Secure knowledge management -
Summary and Directions l End-to-end security - Secure networks, clients, servers, middleware - Secure Web databases, agents, information retrieval systems, browsers, search engines, - - l As technologies evolve, more security problems Data mining, intrusion detection, encryption are some of the technologies for security l Next steps Secure semantic web, Secure knowledge management -


