6da41aeb692ce06bf44ace06842f6e90.ppt
- Количество слайдов: 33

Dagstuhl Workshop on Fresh Approaches for Business Process Modeling Working group on: Ki. P meets CWA Achim Brucker, Alexander Herwix, Rick Hull, Hamid Motawari, Flavia Santoro, William Wong 12 May 2016 1 IBM Confidential

Overview § On Tues/Wed we created a framework to understand Knowledge. Intensive Processes (Ki. P’s) § On Wed/Thur we asked: --- Does our Ki. P framework well with CWA ? ? ? ------ § Three ways that Ki. P’s interact with “knowledge” 4 Create a knowledge artifact, e. g. , a CWA model 4 Maintain a knowledge artifact 4 Use a knowledge artifact § This lead to 3 general observations 4 We need to understand how practitioners perform Knowledge-Intensive Work • There are different kinds of knowledge, which will affect the shape of Ki. P’s 4 Low hanging fruit: Annotate nodes in models with semantically related documents, images, etc 4 Can we make intricate models, e. g. , CWA models, “living”? 2 IBM Confidential

Many different kinds of “knowledge” that Ki. P’s might focus on § Spectrum, kind of 4 4 Lots and lots of data – e. g. , Intricate, structured models, e. g. , CWA, ITOM, BPMN schemas, … Info/knowledge gathered during an accident investigation Amorphous knowledge a CEO thinks about when making a big decision § Some “knowledge” is being captured in a machine-readable format 4 Often based on abstractions and abstraction hierarchies 4 Often with visualizations and tools 4 Often these are fairly mature, with a fairly mature & active community § Other “knowledge” may never be capture in machine-readable format 4 In that case, the role of Ki. P is to enable the humans as much as possible 4 The boundary of “machine-readable” is shifting, as new text analytics capabilities are being developed, e. g. , “cognitive computing” 3 IBM Confidential
Knowledge-enriched models 4 IBM Confidential
Making models “alive” (using CWA as example) § In general, including CWA, the model is created and used by one group… … but the actual operations are being performed by other groups § As a result, the CWA model gets out of date 4 There are few incentives to keep it up to date § How can we set up processes, incentives, fresh approaches so that these kinds of models can be kept up to date § Examples of success from other fields 4 Entity-Relationship data modeling – tools arose for mapping from ER diagrams into Relational DDL … 4 Empowerment of the end-user – eg, spreadsheets designed by, and then used by, same person • Example: shifting spreadsheet users to using Google. Doc spreadsheets 5 IBM Confidential
Directions to explore for keeping models alive Some general principles § Give to all users the “knowledge-enhanced” CWA model 4 If the see value, they will help maintain accuracy § Change detection in procedures, conditions/rules and instructions that impacts the correctness or the logic of a model 4 Instrument the operational model so that it sends update to CWA model § And, at the highest level, change recommendation techniques for keeping the models in sync with the latest changes in enterprise/environment guidelines, actors, rules/regulations, etc. 4 Incentivize the operations-level users to maintain accuracy of the CWA model 6 IBM Confidential
Directions to explore for keeping models alive An example we might try to imitate. . . 7 IBM Confidential
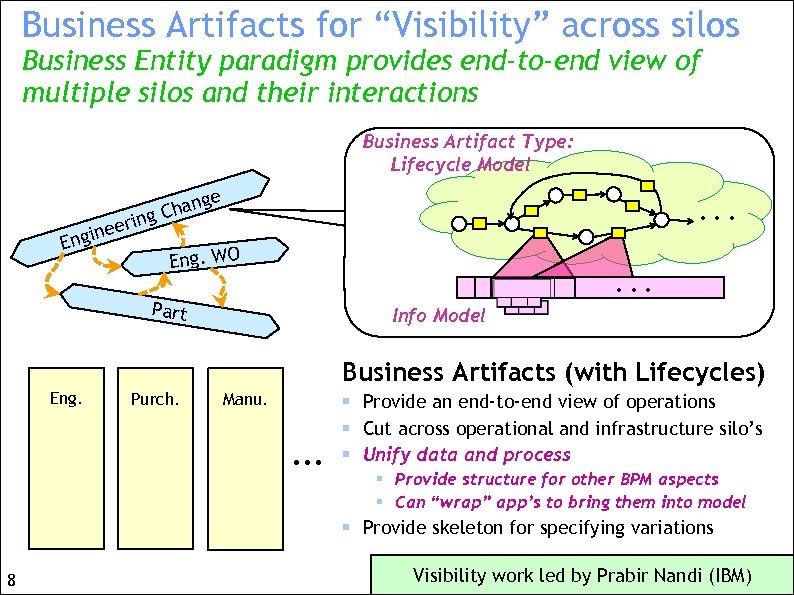
Business Artifacts for “Visibility” across silos Business Entity paradigm provides end-to-end view of multiple silos and their interactions Business Artifact Type: Lifecycle Model g Chan g erin ne Engi e . . . Eng. WO . . . Part Info Model Business Artifacts (with Lifecycles) Eng. Purch. Manu. . § Provide an end-to-end view of operations § Cut across operational and infrastructure silo’s § Unify data and process § Provide structure for other BPM aspects § Can “wrap” app’s to bring them into model § Provide skeleton for specifying variations 8 Visibility work led by Prabir Nandi (IBM)
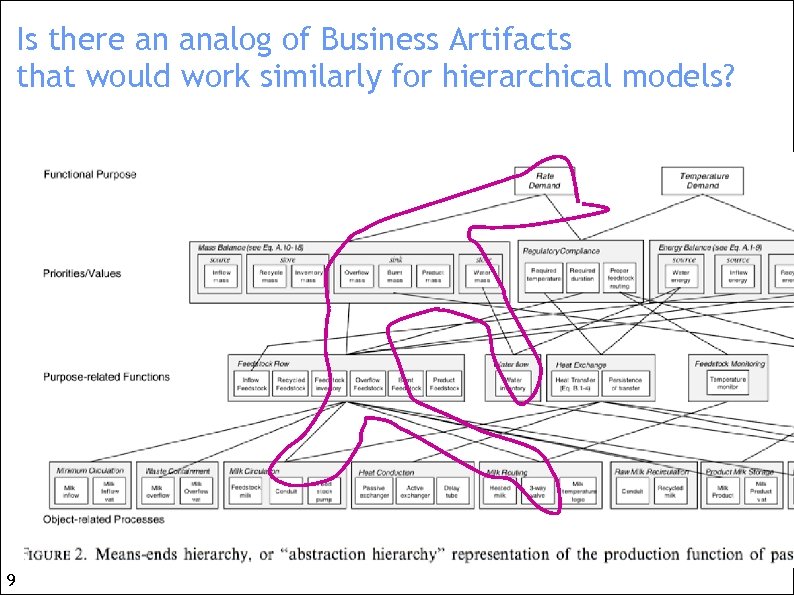
Is there an analog of Business Artifacts that would work similarly for hierarchical models? 9

10 IBM Confidential
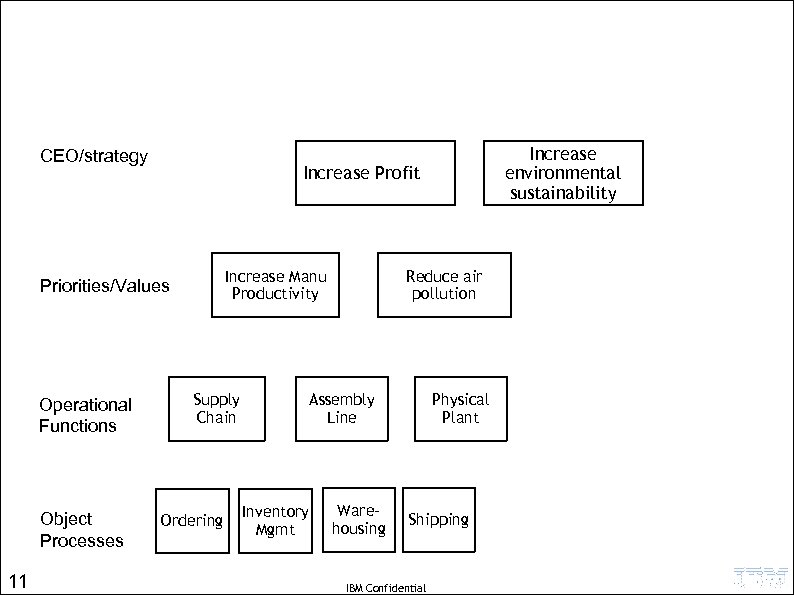
CEO/strategy • Increase Profit Increase Manu Productivity Priorities/Values Operational Functions Object Processes 11 Increase environmental sustainability Supply Chain Ordering Reduce air pollution Assembly Line Inventory Mgmt Warehousing Physical Plant Shipping IBM Confidential
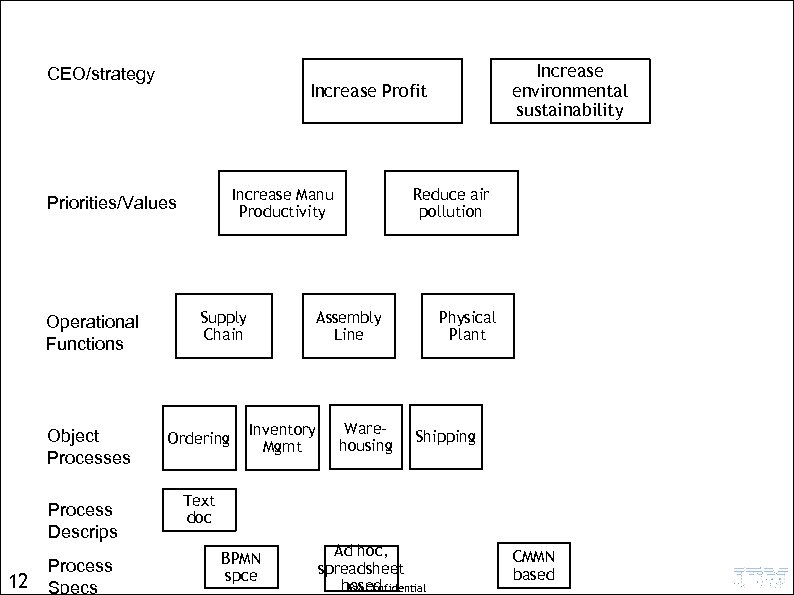
CEO/strategy • Increase Profit Increase Manu Productivity Priorities/Values Operational Functions Object Processes Process Descrips 12 Process Specs Increase environmental sustainability Supply Chain Ordering Reduce air pollution Assembly Line Inventory Mgmt Warehousing Physical Plant Shipping Text doc BPMN spce Ad hoc, spreadsheet based IBM Confidential CMMN based

Creation and Maintenance of CWA diagrams § This activity has probably been studied heavily by the Enterprise Architecture community ? ? § Historically these diagrams have been static – can we make them “alive”, and thereby give them a bigger purpose and life, so that they 13 IBM Confidential

14 IBM Confidential

15 IBM Confidential
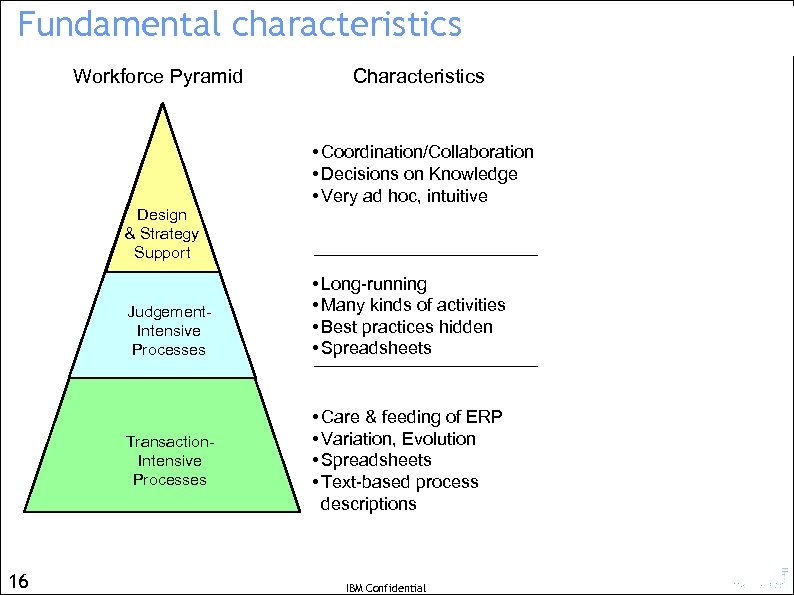
Fundamental characteristics and “centricities” Workforce Pyramid Design & Strategy Support Judgement. Intensive Processes Transaction. Intensive Processes 16 Characteristics • Coordination/Collaboration • Decisions on Knowledge • Very ad hoc, intuitive • Long-running • Many kinds of activities • Best practices hidden • Spreadsheets • Care & feeding of ERP • Variation, Evolution • Spreadsheets • Text-based process descriptions Centricity Knowledge-centric Goals-centric Data-centric However, all three aspects are relevant to all three levels IBM Confidential
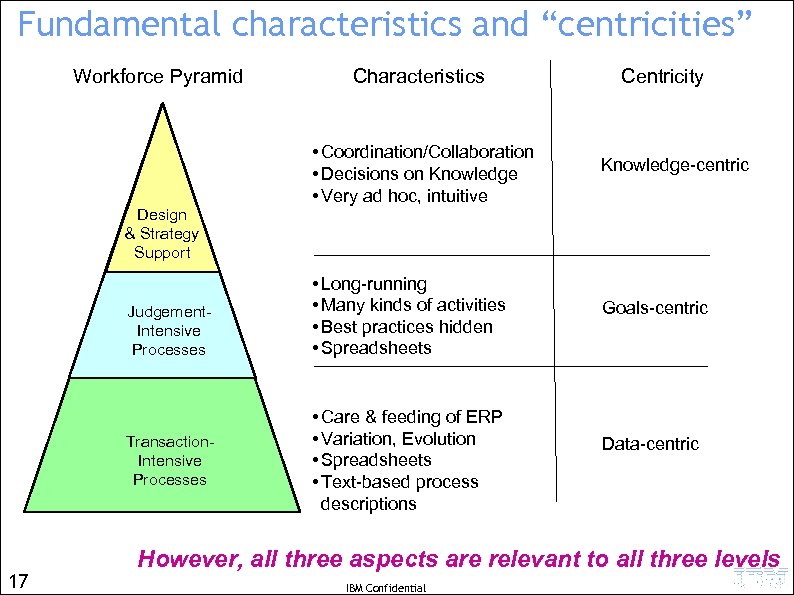
Fundamental characteristics and “centricities” Workforce Pyramid Design & Strategy Support Judgement. Intensive Processes Transaction. Intensive Processes 17 Characteristics • Coordination/Collaboration • Decisions on Knowledge • Very ad hoc, intuitive • Long-running • Many kinds of activities • Best practices hidden • Spreadsheets • Care & feeding of ERP • Variation, Evolution • Spreadsheets • Text-based process descriptions Centricity Knowledge-centric Goals-centric Data-centric However, all three aspects are relevant to all three levels IBM Confidential
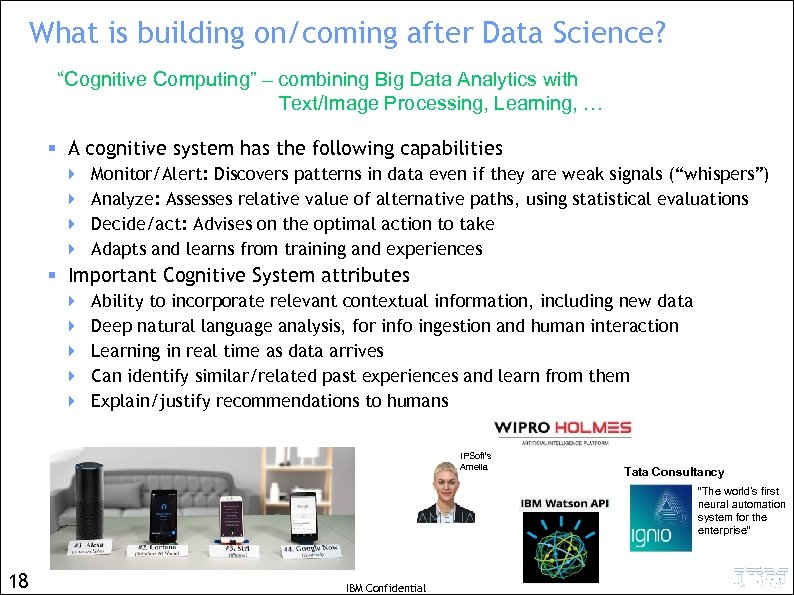
What is building on/coming after Data Science? “Cognitive Computing” – combining Big Data Analytics with Text/Image Processing, Learning, … § A cognitive system has the following capabilities 4 4 Monitor/Alert: Discovers patterns in data even if they are weak signals (“whispers”) Analyze: Assesses relative value of alternative paths, using statistical evaluations Decide/act: Advises on the optimal action to take Adapts and learns from training and experiences § Important Cognitive System attributes 4 4 4 Ability to incorporate relevant contextual information, including new data Deep natural language analysis, for info ingestion and human interaction Learning in real time as data arrives Can identify similar/related past experiences and learn from them Explain/justify recommendations to humans IPSoft’s Amelia Tata Consultancy “The world’s first neural automation system for the enterprise” 18 IBM Confidential
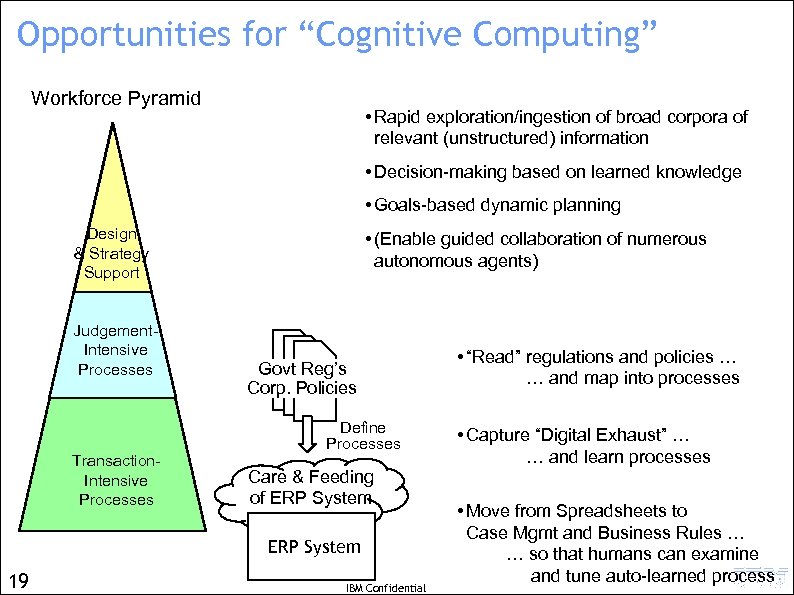
Opportunities for “Cognitive Computing” Workforce Pyramid • Rapid exploration/ingestion of broad corpora of relevant (unstructured) information • Decision-making based on learned knowledge • Goals-based dynamic planning Design & Strategy Support Judgement. Intensive Processes Transaction. Intensive Processes • (Enable guided collaboration of numerous autonomous agents) Govt Reg’s Corp. Policies Define Processes Care & Feeding of ERP System • ERP System 19 IBM Confidential • “Read” regulations and policies … … and map into processes • Capture “Digital Exhaust” … … and learn processes • Move from Spreadsheets to Case Mgmt and Business Rules … … so that humans can examine and tune auto-learned process

20 IBM Confidential
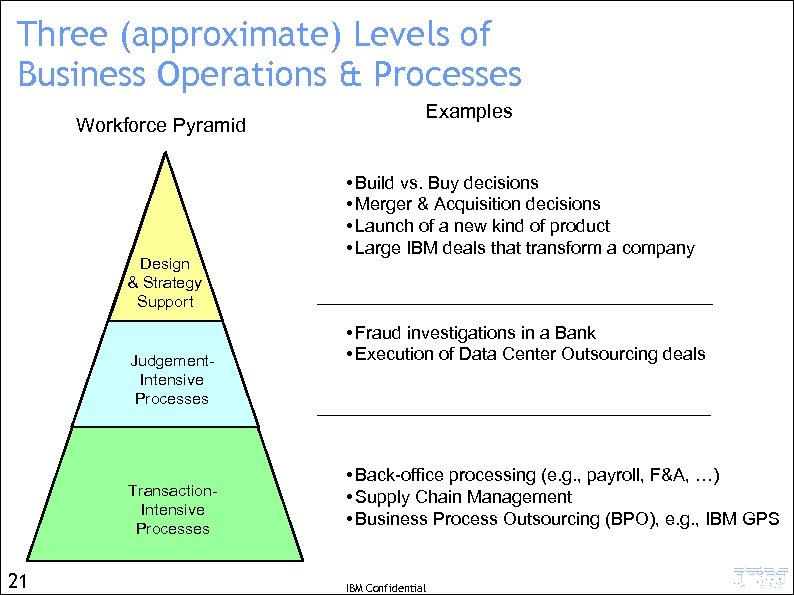
Three (approximate) Levels of Business Operations & Processes Workforce Pyramid Design & Strategy Support Judgement. Intensive Processes Transaction. Intensive Processes 21 Examples • Build vs. Buy decisions • Merger & Acquisition decisions • Launch of a new kind of product • Large IBM deals that transform a company • Fraud investigations in a Bank • Execution of Data Center Outsourcing deals • Back-office processing (e. g. , payroll, F&A, …) • Supply Chain Management • Business Process Outsourcing (BPO), e. g. , IBM GPS IBM Confidential
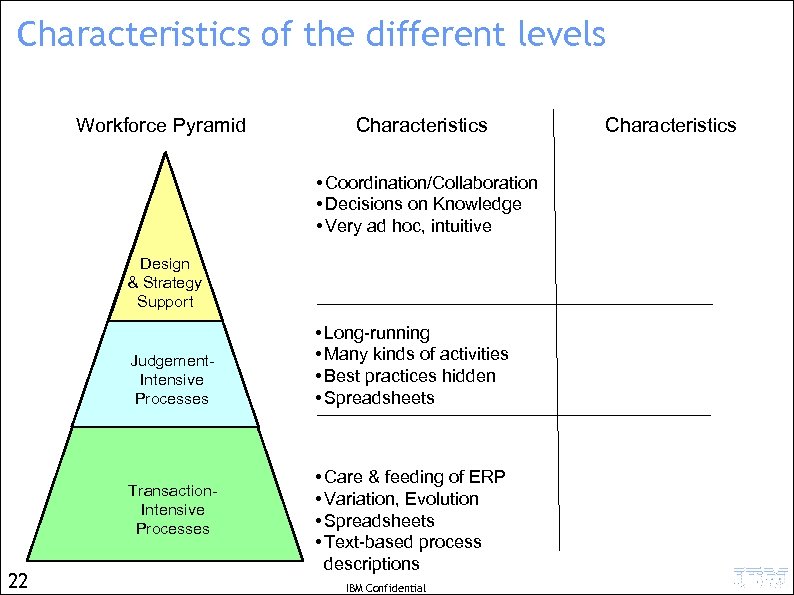
Characteristics of the different levels Workforce Pyramid Characteristics • Coordination/Collaboration • Decisions on Knowledge • Very ad hoc, intuitive Design & Strategy Support Judgement. Intensive Processes Transaction. Intensive Processes 22 • Long-running • Many kinds of activities • Best practices hidden • Spreadsheets • Care & feeding of ERP • Variation, Evolution • Spreadsheets • Text-based process descriptions IBM Confidential Characteristics
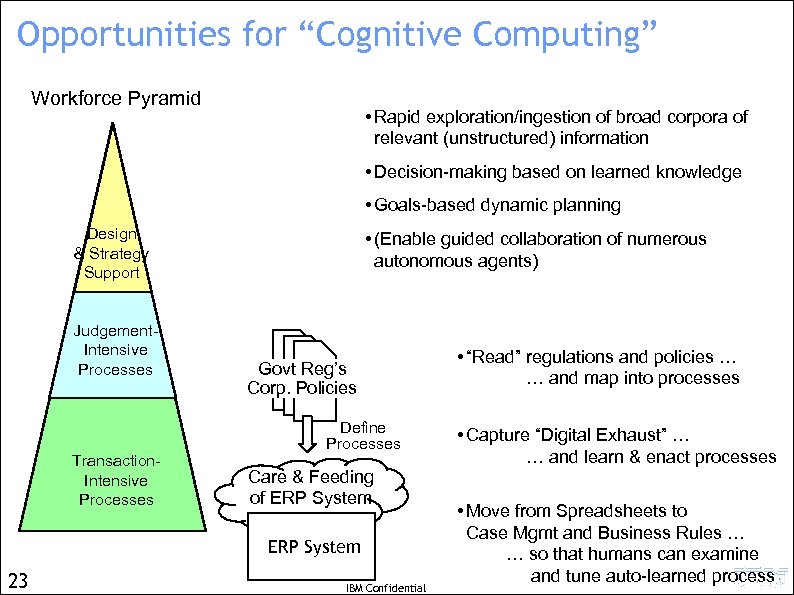
Opportunities for “Cognitive Computing” Workforce Pyramid • Rapid exploration/ingestion of broad corpora of relevant (unstructured) information • Decision-making based on learned knowledge • Goals-based dynamic planning Design & Strategy Support Judgement. Intensive Processes Transaction. Intensive Processes • (Enable guided collaboration of numerous autonomous agents) Govt Reg’s Corp. Policies Define Processes Care & Feeding of ERP System • ERP System 23 IBM Confidential • “Read” regulations and policies … … and map into processes • Capture “Digital Exhaust” … … and learn & enact processes • Move from Spreadsheets to Case Mgmt and Business Rules … … so that humans can examine and tune auto-learned process
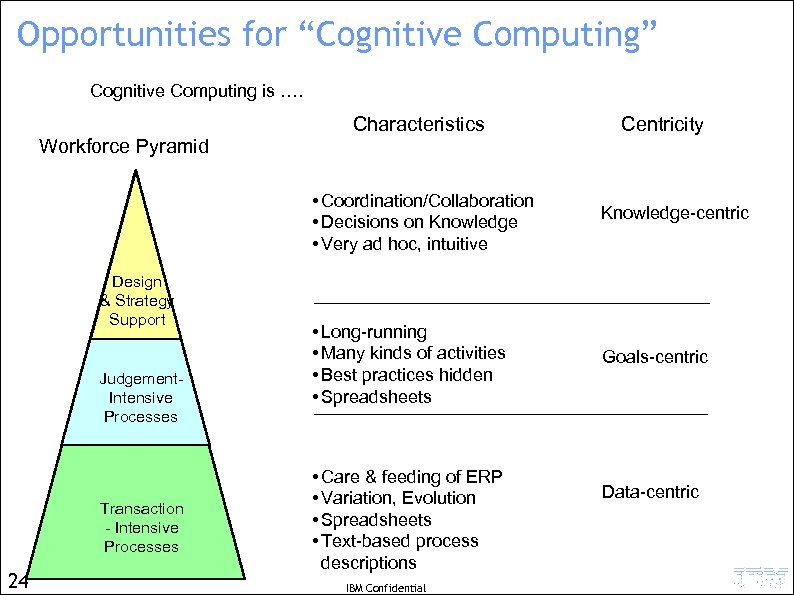
Opportunities for “Cognitive Computing” Cognitive Computing is …. Workforce Pyramid Characteristics • Coordination/Collaboration • Decisions on Knowledge • Very ad hoc, intuitive Design & Strategy Support Judgement. Intensive Processes Transaction - Intensive Processes 24 • Long-running • Many kinds of activities • Best practices hidden • Spreadsheets • Care & feeding of ERP • Variation, Evolution • Spreadsheets • Text-based process descriptions IBM Confidential Centricity Knowledge-centric Goals-centric Data-centric
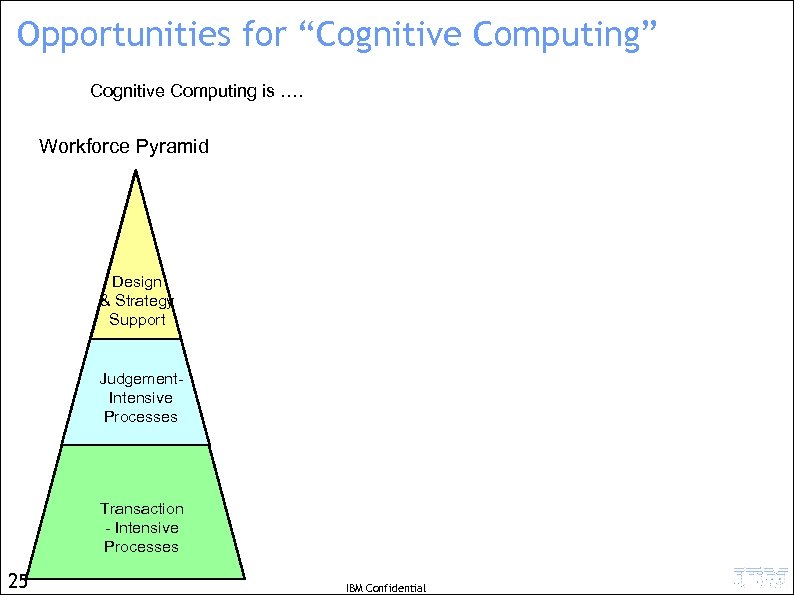
Opportunities for “Cognitive Computing” Cognitive Computing is …. Workforce Pyramid Design & Strategy Support Judgement. Intensive Processes Transaction - Intensive Processes 25 IBM Confidential
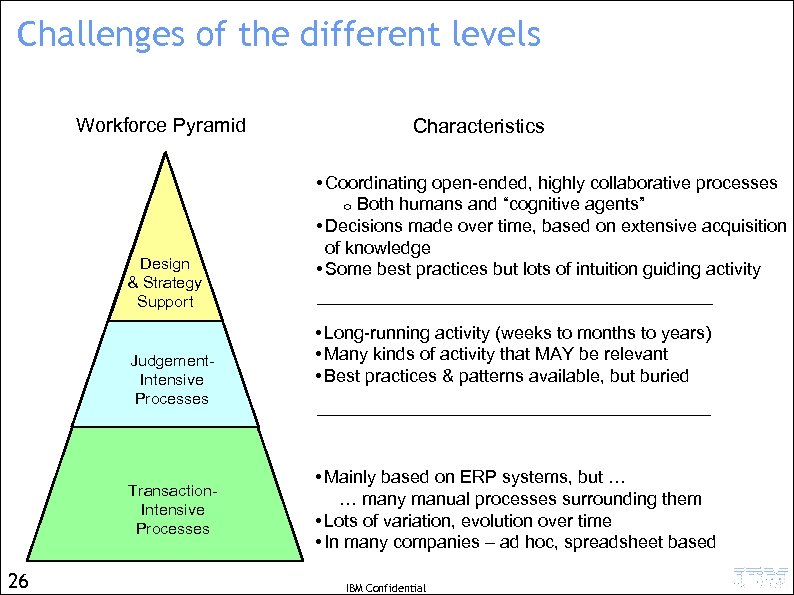
Challenges of the different levels Workforce Pyramid Design & Strategy Support Judgement. Intensive Processes Transaction. Intensive Processes 26 Characteristics • Coordinating open-ended, highly collaborative processes o Both humans and “cognitive agents” • Decisions made over time, based on extensive acquisition of knowledge • Some best practices but lots of intuition guiding activity • Long-running activity (weeks to months to years) • Many kinds of activity that MAY be relevant • Best practices & patterns available, but buried • Mainly based on ERP systems, but … … many manual processes surrounding them • Lots of variation, evolution over time • In many companies – ad hoc, spreadsheet based IBM Confidential
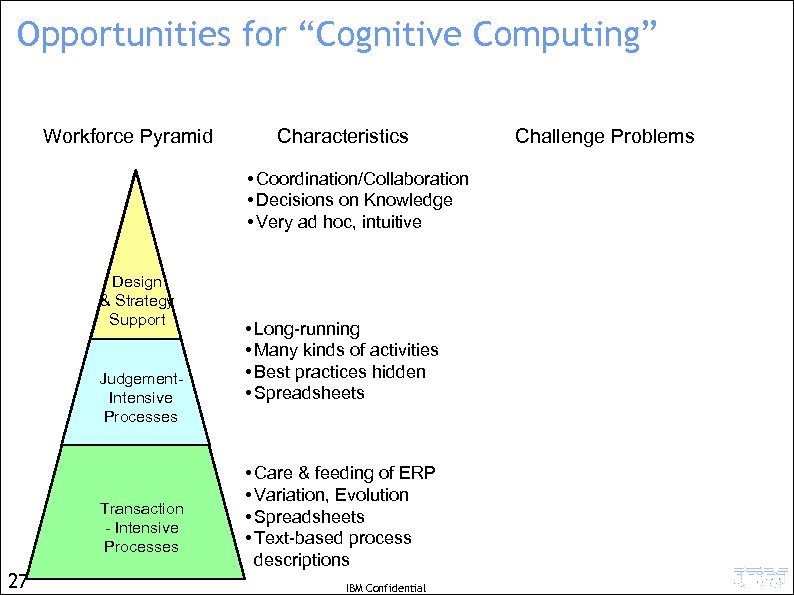
Opportunities for “Cognitive Computing” Workforce Pyramid Characteristics • Coordination/Collaboration • Decisions on Knowledge • Very ad hoc, intuitive Design & Strategy Support Judgement. Intensive Processes Transaction - Intensive Processes 27 • Long-running • Many kinds of activities • Best practices hidden • Spreadsheets • Care & feeding of ERP • Variation, Evolution • Spreadsheets • Text-based process descriptions IBM Confidential Challenge Problems
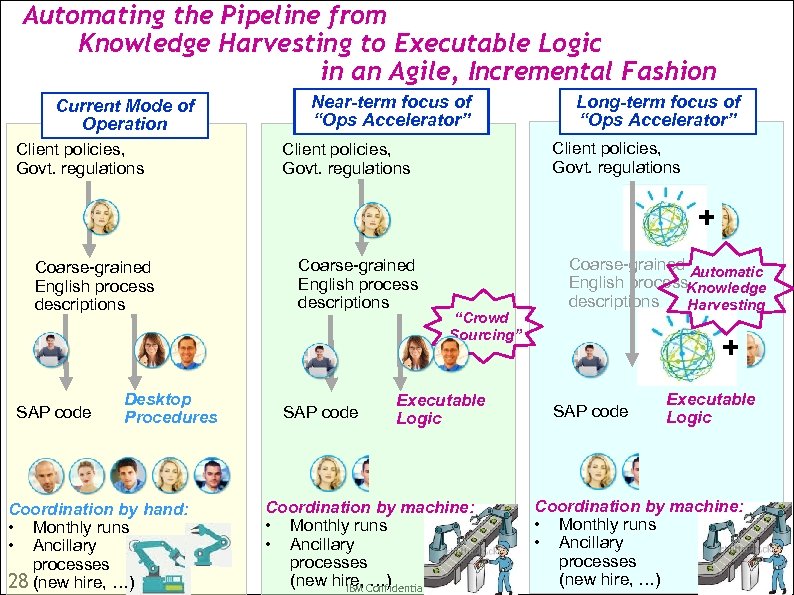
Automating the Pipeline from Knowledge Harvesting to Executable Logic in an Agile, Incremental Fashion Current Mode of Operation Client policies, Govt. regulations Near-term focus of “Ops Accelerator” Long-term focus of “Ops Accelerator” Client policies, Govt. regulations + Coarse-grained English process descriptions SAP code Desktop Procedures Coordination by hand: • Monthly runs • Ancillary processes 28 (new hire, …) Coarse-grained English process descriptions SAP code “Crowd Sourcing” Executable Logic Coordination by machine: • Monthly runs • Ancillary processes (new hire, Confidential IBM …) Coarse-grained Automatic English process. Knowledge descriptions Harvesting + SAP code Executable Logic Coordination by machine: • Monthly runs • Ancillary processes (new hire, …)

29 IBM Confidential

30 IBM Confidential

31 IBM Confidential

Backup 32 IBM Confidential
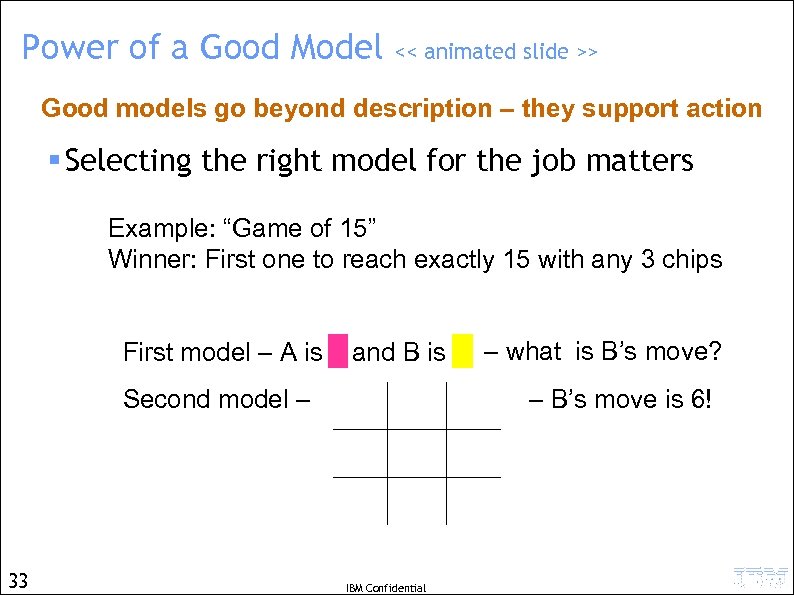
Power of a Good Model << animated slide >> Good models go beyond description – they support action § Selecting the right model for the job matters Example: “Game of 15” Winner: First one to reach exactly 15 with any 3 chips 1 2 3 First model – A is 4 5 and B is Second model – 33 6 7 8 9 – what is B’s move? – B’s move is 6! IBM Confidential
6da41aeb692ce06bf44ace06842f6e90.ppt