41476a3d77f717ea5cc27d62b453a69f.ppt
- Количество слайдов: 29
![DACODA [Crandall et al. ; CCS 2005] n DAvis mal. CODe n Analyzer Discover DACODA [Crandall et al. ; CCS 2005] n DAvis mal. CODe n Analyzer Discover](https://present5.com/presentation/41476a3d77f717ea5cc27d62b453a69f/image-1.jpg) DACODA [Crandall et al. ; CCS 2005] n DAvis mal. CODe n Analyzer Discover invariants in the exploit vector (ε) ¨ Symbolic execution on the system trace during attacks that Minos catches n Used for an empirical analysis of polymorphism and metamorphism ¨ Quantify and understand the limits 1
DACODA [Crandall et al. ; CCS 2005] n DAvis mal. CODe n Analyzer Discover invariants in the exploit vector (ε) ¨ Symbolic execution on the system trace during attacks that Minos catches n Used for an empirical analysis of polymorphism and metamorphism ¨ Quantify and understand the limits 1
 Worm Polymorphism and Metamorphism n Viruses: Defender has time to pick apart the attacker’s techniques ¨ e. g. n Algorithmic scanners, emulation Worms: Attacker has time to pick apart the deployed network defense techniques ¨ What can defenders do to evaluate the robustness of defenses against attacks that don’t exist yet? 2
Worm Polymorphism and Metamorphism n Viruses: Defender has time to pick apart the attacker’s techniques ¨ e. g. n Algorithmic scanners, emulation Worms: Attacker has time to pick apart the deployed network defense techniques ¨ What can defenders do to evaluate the robustness of defenses against attacks that don’t exist yet? 2
![Measuring Poly/metamorphism n [Ma et al. ; IMC 2006] ¨ Found wild” n relatively Measuring Poly/metamorphism n [Ma et al. ; IMC 2006] ¨ Found wild” n relatively](https://present5.com/presentation/41476a3d77f717ea5cc27d62b453a69f/image-3.jpg) Measuring Poly/metamorphism n [Ma et al. ; IMC 2006] ¨ Found wild” n relatively little polymorphism “in the Worm defense designers don’t have samples of the poly/metamorphic techniques attackers will use on their defenses ¨ (Have to build the defense first) 3
Measuring Poly/metamorphism n [Ma et al. ; IMC 2006] ¨ Found wild” n relatively little polymorphism “in the Worm defense designers don’t have samples of the poly/metamorphic techniques attackers will use on their defenses ¨ (Have to build the defense first) 3
 How DACODA Works “Information only has meaning in that it is subject to interpretation. ” [Cohen, 1984] n Gives each byte of network data a unique label n Tracks these through the entire system n Discovers predicates about how the host under attack interprets the network bytes n 4
How DACODA Works “Information only has meaning in that it is subject to interpretation. ” [Cohen, 1984] n Gives each byte of network data a unique label n Tracks these through the entire system n Discovers predicates about how the host under attack interprets the network bytes n 4
![mov al, [Address. With. Label 1832] ; AL. expr <= (Label 1832) add al, mov al, [Address. With. Label 1832] ; AL. expr <= (Label 1832) add al,](https://present5.com/presentation/41476a3d77f717ea5cc27d62b453a69f/image-5.jpg) mov al, [Address. With. Label 1832] ; AL. expr <= (Label 1832) add al, 4 ; AL. expr <= (ADD AL. Expr 4) ; /* AL. expr == (ADD (LABEL 1832) 4) */ cmp al, 10 ; ZFLAG. left <= AL. expr ; /* ZFLAG. left == (ADD (Label 1832) 4) */ ; ZFLAG. right <= 10 je Jump. Target. If. Equal. To. Ten ; P <= new Predicate(EQUAL ZFLAG. Left ZFLAG. Right) ; /* P == (EQUAL (ADD (Label 1832) 4) 10) */ ; Add. To. Set. Of. Known. Predicates(P) 5
mov al, [Address. With. Label 1832] ; AL. expr <= (Label 1832) add al, 4 ; AL. expr <= (ADD AL. Expr 4) ; /* AL. expr == (ADD (LABEL 1832) 4) */ cmp al, 10 ; ZFLAG. left <= AL. expr ; /* ZFLAG. left == (ADD (Label 1832) 4) */ ; ZFLAG. right <= 10 je Jump. Target. If. Equal. To. Ten ; P <= new Predicate(EQUAL ZFLAG. Left ZFLAG. Right) ; /* P == (EQUAL (ADD (Label 1832) 4) 10) */ ; Add. To. Set. Of. Known. Predicates(P) 5
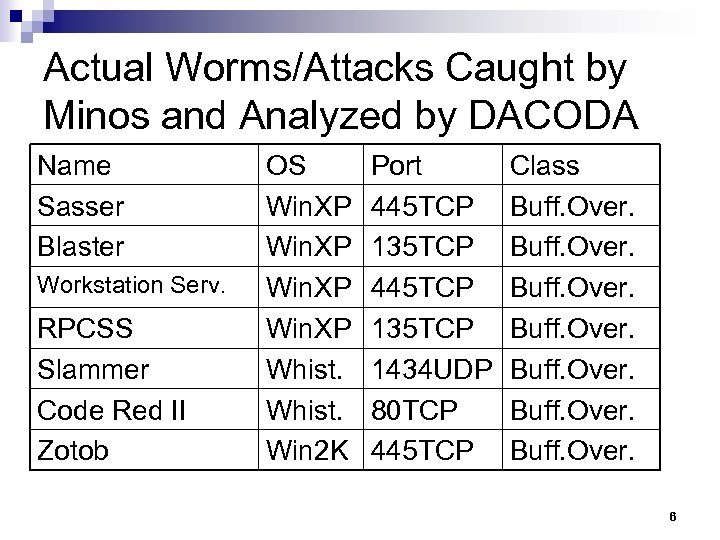 Actual Worms/Attacks Caught by Minos and Analyzed by DACODA Name Sasser Blaster Workstation Serv. RPCSS Slammer Code Red II Zotob OS Win. XP Whist. Win 2 K Port 445 TCP 135 TCP 1434 UDP 80 TCP 445 TCP Class Buff. Over. 6
Actual Worms/Attacks Caught by Minos and Analyzed by DACODA Name Sasser Blaster Workstation Serv. RPCSS Slammer Code Red II Zotob OS Win. XP Whist. Win 2 K Port 445 TCP 135 TCP 1434 UDP 80 TCP 445 TCP Class Buff. Over. 6
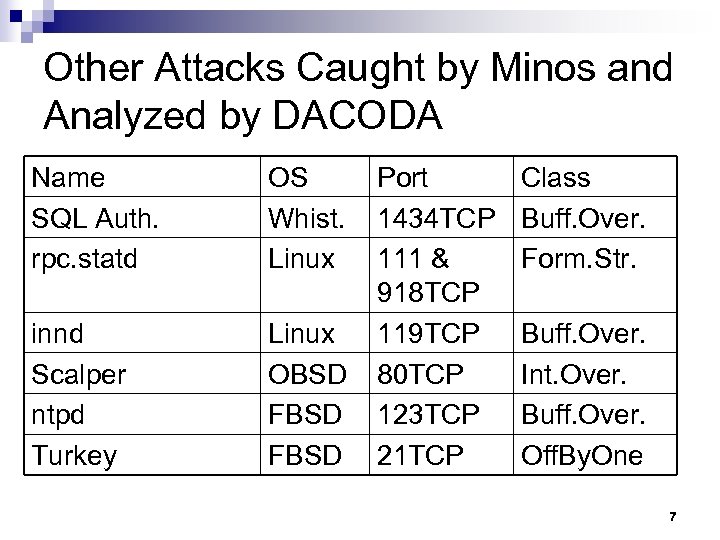 Other Attacks Caught by Minos and Analyzed by DACODA Name SQL Auth. rpc. statd OS Whist. Linux innd Scalper ntpd Turkey Linux OBSD FBSD Port 1434 TCP 111 & 918 TCP 119 TCP 80 TCP 123 TCP 21 TCP Class Buff. Over. Form. Str. Buff. Over. Int. Over. Buff. Over. Off. By. One 7
Other Attacks Caught by Minos and Analyzed by DACODA Name SQL Auth. rpc. statd OS Whist. Linux innd Scalper ntpd Turkey Linux OBSD FBSD Port 1434 TCP 111 & 918 TCP 119 TCP 80 TCP 123 TCP 21 TCP Class Buff. Over. Form. Str. Buff. Over. Int. Over. Buff. Over. Off. By. One 7
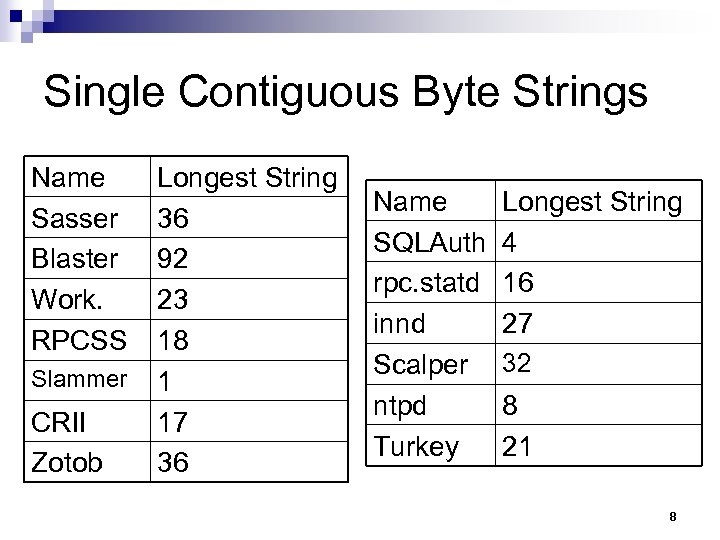 Single Contiguous Byte Strings Name Sasser Blaster Work. RPCSS Slammer CRII Zotob Longest String 36 92 23 18 1 17 36 Name SQLAuth rpc. statd innd Scalper ntpd Turkey Longest String 4 16 27 32 8 21 8
Single Contiguous Byte Strings Name Sasser Blaster Work. RPCSS Slammer CRII Zotob Longest String 36 92 23 18 1 17 36 Name SQLAuth rpc. statd innd Scalper ntpd Turkey Longest String 4 16 27 32 8 21 8
![Single Contiguous Signatures n n Autograph [Kim and Karp; USENIX Security 2004] and Early. Single Contiguous Signatures n n Autograph [Kim and Karp; USENIX Security 2004] and Early.](https://present5.com/presentation/41476a3d77f717ea5cc27d62b453a69f/image-9.jpg) Single Contiguous Signatures n n Autograph [Kim and Karp; USENIX Security 2004] and Early. Bird [Singh et al. ; OSDI 2004] both demonstrated good results at about 40 bytes for the signature length [Newsome et al. ; IEEE S&P 2005] came to the same conclusion as we did and proposed sets of smaller byte strings called tokens 9
Single Contiguous Signatures n n Autograph [Kim and Karp; USENIX Security 2004] and Early. Bird [Singh et al. ; OSDI 2004] both demonstrated good results at about 40 bytes for the signature length [Newsome et al. ; IEEE S&P 2005] came to the same conclusion as we did and proposed sets of smaller byte strings called tokens 9
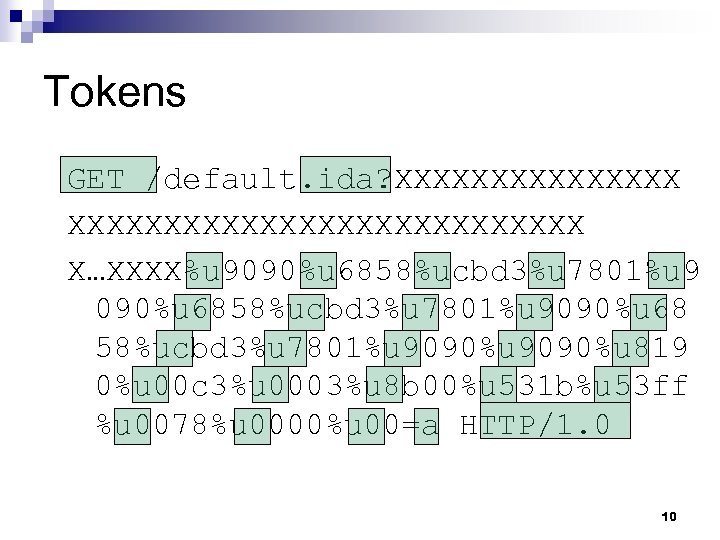 Tokens GET /default. ida? XXXXXXXXXXXXXXXXXXXXX X…XXXX%u 9090%u 6858%ucbd 3%u 7801%u 9090%u 68 58%ucbd 3%u 7801%u 9090%u 819 0%u 00 c 3%u 0003%u 8 b 00%u 531 b%u 53 ff %u 0078%u 0000%u 00=a HTTP/1. 0 10
Tokens GET /default. ida? XXXXXXXXXXXXXXXXXXXXX X…XXXX%u 9090%u 6858%ucbd 3%u 7801%u 9090%u 68 58%ucbd 3%u 7801%u 9090%u 819 0%u 00 c 3%u 0003%u 8 b 00%u 531 b%u 53 ff %u 0078%u 0000%u 00=a HTTP/1. 0 10
 Where do These Tokens Come From? n Scalper “Transfer-Encoding: chunked” ¨ Same n applies to most of these vulnerabilities “The Horns of a Dilemma” ¨ Use protocol framing as a signature ¨ Be very precise 11
Where do These Tokens Come From? n Scalper “Transfer-Encoding: chunked” ¨ Same n applies to most of these vulnerabilities “The Horns of a Dilemma” ¨ Use protocol framing as a signature ¨ Be very precise 11
 Conclusions from DACODA Whole system analysis is important n New focus on more semantic signatures n ¨ How to understand the semantics of the vulnerability? n We can learn a lot about emerging malware threats by studying existing malware samples and their interactions with the systems they run on 12
Conclusions from DACODA Whole system analysis is important n New focus on more semantic signatures n ¨ How to understand the semantics of the vulnerability? n We can learn a lot about emerging malware threats by studying existing malware samples and their interactions with the systems they run on 12
![Temporal Search [Crandall et al. ; ASPLOS 2006] n Automated discovery of timebomb attacks Temporal Search [Crandall et al. ; ASPLOS 2006] n Automated discovery of timebomb attacks](https://present5.com/presentation/41476a3d77f717ea5cc27d62b453a69f/image-13.jpg) Temporal Search [Crandall et al. ; ASPLOS 2006] n Automated discovery of timebomb attacks ¨ Analysis n in the π stage Prototype of behavior-based analysis ¨ Proposed a framework for a problem space nobody has looked at before ¨ Implemented parts of it ¨ Identified the remaining challenges n By testing real worms with timebombs on our prototype 13
Temporal Search [Crandall et al. ; ASPLOS 2006] n Automated discovery of timebomb attacks ¨ Analysis n in the π stage Prototype of behavior-based analysis ¨ Proposed a framework for a problem space nobody has looked at before ¨ Implemented parts of it ¨ Identified the remaining challenges n By testing real worms with timebombs on our prototype 13
 You as an antivirus professional catch a new worm… n n Unpack it Polymorphism/ metamorphism? Anti-debugger tricks? Any behaviors predicated on time? ¨ How it gets the time? ¨ UTC/Local? ¨ Conversions between formats? 14
You as an antivirus professional catch a new worm… n n Unpack it Polymorphism/ metamorphism? Anti-debugger tricks? Any behaviors predicated on time? ¨ How it gets the time? ¨ UTC/Local? ¨ Conversions between formats? 14
 With Temporal Search… n n n Infect a VM Automated, behavior-based Temporal Search Respond 15
With Temporal Search… n n n Infect a VM Automated, behavior-based Temporal Search Respond 15
 How to respond? n Sober. X – 6 and 7 January 2006 ¨ URLs n Kama Sutra – 3 rd of the month ¨ Users n blocked removed infections Code Red – 20 th of the month ¨ White House IP address changed What if we have just hours or even minutes, not days? 16
How to respond? n Sober. X – 6 and 7 January 2006 ¨ URLs n Kama Sutra – 3 rd of the month ¨ Users n blocked removed infections Code Red – 20 th of the month ¨ White House IP address changed What if we have just hours or even minutes, not days? 16
![Behavior-based Analysis [Cohen, 1984] defined behavior-based detection as a question of “defining what is Behavior-based Analysis [Cohen, 1984] defined behavior-based detection as a question of “defining what is](https://present5.com/presentation/41476a3d77f717ea5cc27d62b453a69f/image-17.jpg) Behavior-based Analysis [Cohen, 1984] defined behavior-based detection as a question of “defining what is and is not a legitimate use of a service, and finding a means of detecting the difference. ” n Behavior-based analysis is similar n ¨ Assume the system is infected with malware ¨ Analyze its use of a service such as the PIT 17
Behavior-based Analysis [Cohen, 1984] defined behavior-based detection as a question of “defining what is and is not a legitimate use of a service, and finding a means of detecting the difference. ” n Behavior-based analysis is similar n ¨ Assume the system is infected with malware ¨ Analyze its use of a service such as the PIT 17
 Why not just speed up the clock? n Dramatic time perturbation would be easy to detect ¨ Also not easy to do for a busy system (effectively lowers perceived performance) n May miss some behaviors ¨ Kama n Sutra Will not be able to explain behaviors it does elicit 18
Why not just speed up the clock? n Dramatic time perturbation would be easy to detect ¨ Also not easy to do for a busy system (effectively lowers perceived performance) n May miss some behaviors ¨ Kama n Sutra Will not be able to explain behaviors it does elicit 18
 Basic Idea n Find timers ¨ Run time the PIT at different rates of perceived System performance stays the same n Correlate between PIT and memory writes n n Symbolic execution ¨ e. g. n with DACODA Weakest precondition calculation 19
Basic Idea n Find timers ¨ Run time the PIT at different rates of perceived System performance stays the same n Correlate between PIT and memory writes n n Symbolic execution ¨ e. g. n with DACODA Weakest precondition calculation 19
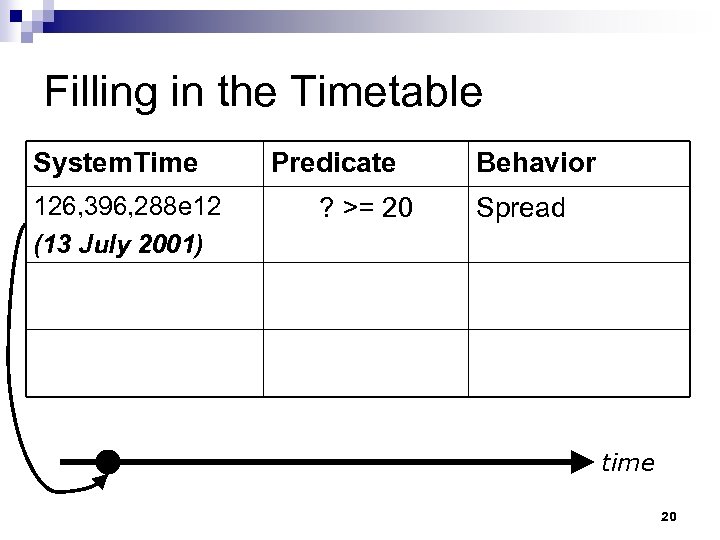 Filling in the Timetable System. Time 126, 396, 288 e 12 (13 July 2001) Predicate ? >= 20 Behavior Spread time 20
Filling in the Timetable System. Time 126, 396, 288 e 12 (13 July 2001) Predicate ? >= 20 Behavior Spread time 20
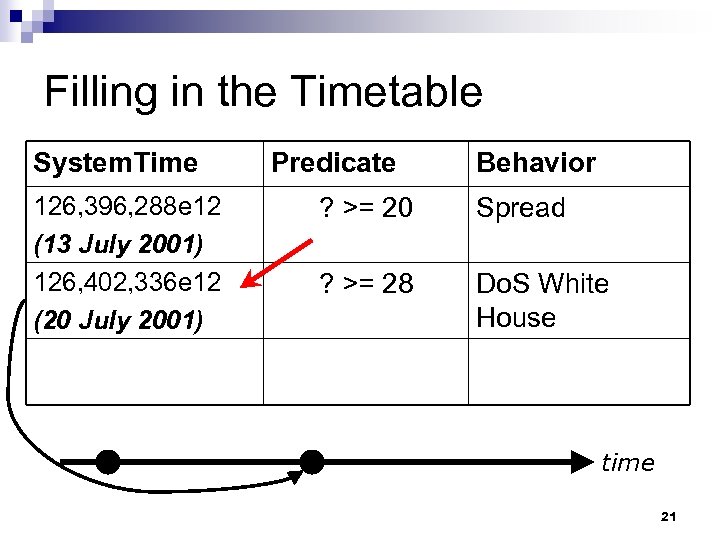 Filling in the Timetable System. Time 126, 396, 288 e 12 (13 July 2001) 126, 402, 336 e 12 (20 July 2001) Predicate Behavior ? >= 20 Spread ? >= 28 Do. S White House time 21
Filling in the Timetable System. Time 126, 396, 288 e 12 (13 July 2001) 126, 402, 336 e 12 (20 July 2001) Predicate Behavior ? >= 20 Spread ? >= 28 Do. S White House time 21
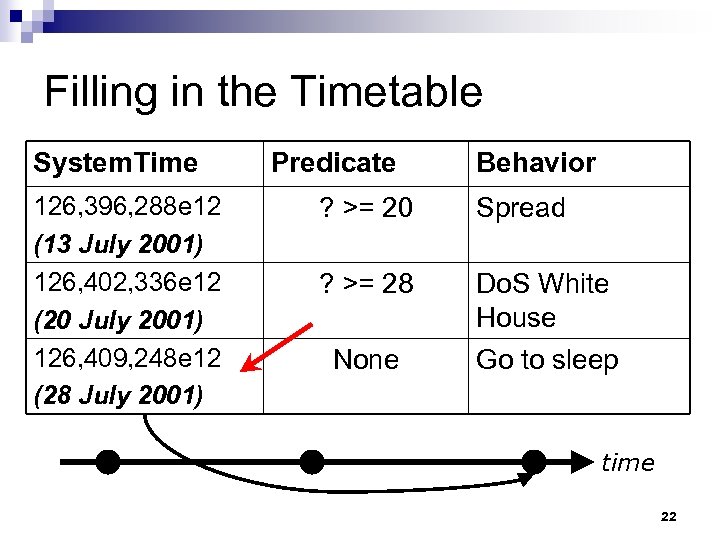 Filling in the Timetable System. Time 126, 396, 288 e 12 (13 July 2001) 126, 402, 336 e 12 (20 July 2001) 126, 409, 248 e 12 (28 July 2001) Predicate Behavior ? >= 20 Spread ? >= 28 Do. S White House None Go to sleep time 22
Filling in the Timetable System. Time 126, 396, 288 e 12 (13 July 2001) 126, 402, 336 e 12 (20 July 2001) 126, 409, 248 e 12 (28 July 2001) Predicate Behavior ? >= 20 Spread ? >= 28 Do. S White House None Go to sleep time 22
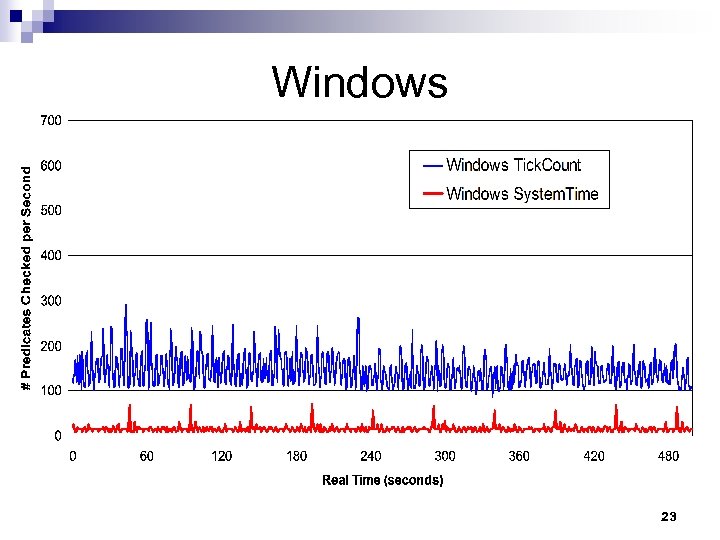 Windows 23
Windows 23
 Manual Analysis n Many different library calls, APIs for date and time Get. System. Time(), Get. Local. Time(), Get. Time. Zone. Information(), Diff. Date(), Get. Date. Format(), etc. ¨ System call not really necessary ¨ n Conversions back and forth between various represenations (e. g. My. Party. A, Blaster. E) ¨ ¨ ¨ UTC vs. Local 1600 vs. 1970 32 - vs 64 -bit integers for day, month, year, etc. strings n Not always done with standard library functions Have to unpack it first, anti-debugging tricks n All of this is simply dataflow from System. Time timer n 24
Manual Analysis n Many different library calls, APIs for date and time Get. System. Time(), Get. Local. Time(), Get. Time. Zone. Information(), Diff. Date(), Get. Date. Format(), etc. ¨ System call not really necessary ¨ n Conversions back and forth between various represenations (e. g. My. Party. A, Blaster. E) ¨ ¨ ¨ UTC vs. Local 1600 vs. 1970 32 - vs 64 -bit integers for day, month, year, etc. strings n Not always done with standard library functions Have to unpack it first, anti-debugging tricks n All of this is simply dataflow from System. Time timer n 24
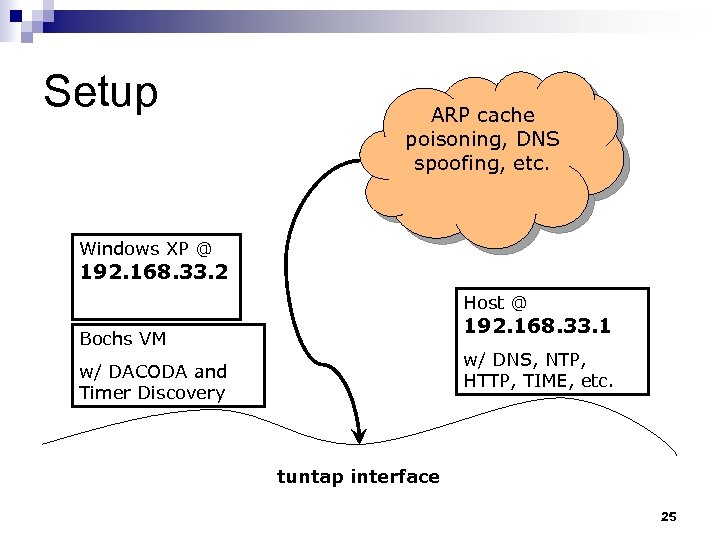 Setup ARP cache poisoning, DNS spoofing, etc. Windows XP @ 192. 168. 33. 2 Host @ 192. 168. 33. 1 Bochs VM w/ DNS, NTP, HTTP, TIME, etc. w/ DACODA and Timer Discovery tuntap interface 25
Setup ARP cache poisoning, DNS spoofing, etc. Windows XP @ 192. 168. 33. 2 Host @ 192. 168. 33. 1 Bochs VM w/ DNS, NTP, HTTP, TIME, etc. w/ DACODA and Timer Discovery tuntap interface 25
 Temporal Search n Symbolic Execution (DACODA) ¨ Cod n n Red, Blaster. E, My. Party. A, Klez. A Discovers predicates on day, hour, minute, etc. on a real time trace Control-flow sensitivity within loops ¨ Cod Red, Blaster. E, My. Party. A, Klez. A, Sober. X Kama Sutra n Month and year 26
Temporal Search n Symbolic Execution (DACODA) ¨ Cod n n Red, Blaster. E, My. Party. A, Klez. A Discovers predicates on day, hour, minute, etc. on a real time trace Control-flow sensitivity within loops ¨ Cod Red, Blaster. E, My. Party. A, Klez. A, Sober. X Kama Sutra n Month and year 26
 Adversarial Analysis n For any technique, being applicable to every possible virus or worm is not a requirement ¨AV companies collect intelligence n More details in the paper on this 27
Adversarial Analysis n For any technique, being applicable to every possible virus or worm is not a requirement ¨AV companies collect intelligence n More details in the paper on this 27
 Conclusions from Temporal Search n Manual analysis is tricky and time-consuming ¨ Temporal Search can dramatically improve response time n n n Behavior-based analysis is all about the environment Malware does not follow a linear timetable Gregorian calendar poses its own challenges 28
Conclusions from Temporal Search n Manual analysis is tricky and time-consuming ¨ Temporal Search can dramatically improve response time n n n Behavior-based analysis is all about the environment Malware does not follow a linear timetable Gregorian calendar poses its own challenges 28
 Why Behavior-Based Analysis? “An ant, viewed as a behaving system, is quite simple. The apparent complexity of its behavior over time is largely a reflection of the complexity of the environment in which it finds itself. ” –Herbert Simon 29
Why Behavior-Based Analysis? “An ant, viewed as a behaving system, is quite simple. The apparent complexity of its behavior over time is largely a reflection of the complexity of the environment in which it finds itself. ” –Herbert Simon 29


