15f2a6b74943645259fc2ea87dc17030.ppt
- Количество слайдов: 53

Cybersecurity Martyn Thomas CBE FREng Livery Company Professor of Information Technology 1

Cybercrimes and cyberattacks come in many varieties • • Phishing emails Hijacked email accounts Hijacked website accounts Computer viruses Buffer overflow attacks SQL Insertion attacks (SQLi) Cross-site scripting (XSS) … … and many more 2
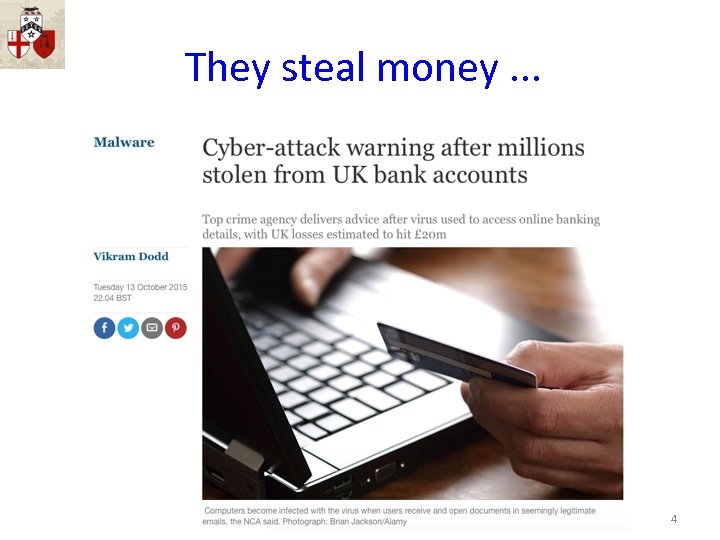
They steal money. . . www. cyberliving. uk #cyberliving 4
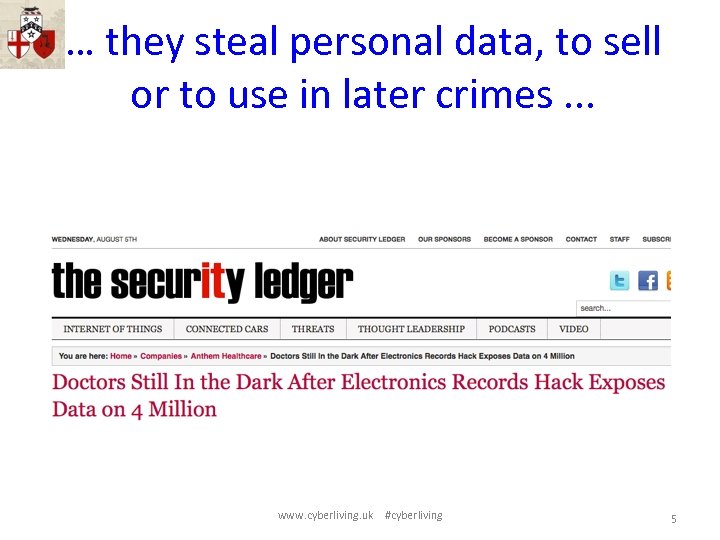
… they steal personal data, to sell or to use in later crimes. . . www. cyberliving. uk #cyberliving 5

sometimes the data is used to blackmail the victim www. cyberliving. uk #cyberliving 6
… sometimes they extort money with threats through ransomware that encrypts all your data and demands payment for the key 7
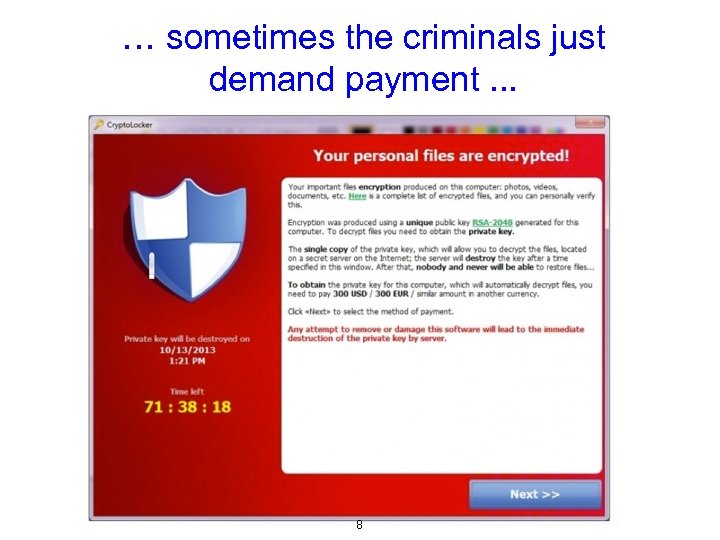
… sometimes the criminals just demand payment. . . 8
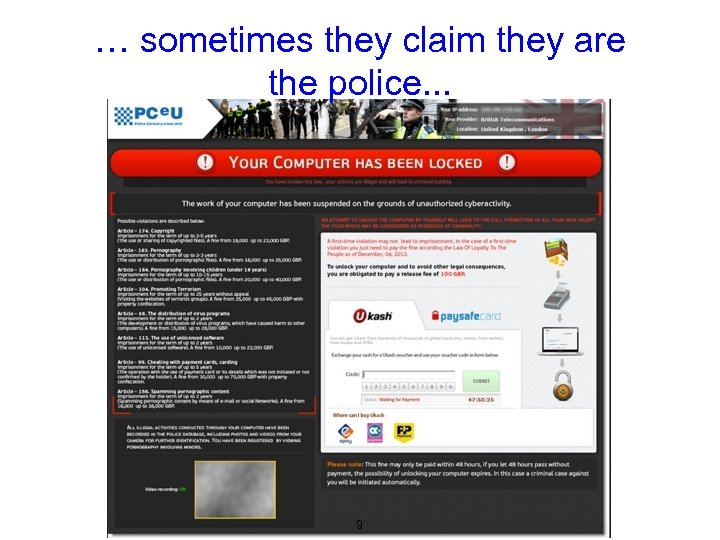
… sometimes they claim they are the police. . . 9
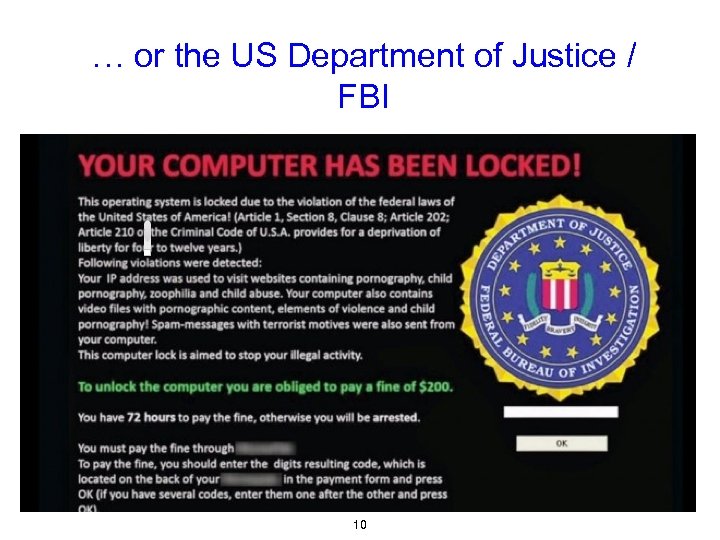
… or the US Department of Justice / FBI 10

Several US hospitals have been attacked with ransomware, disabling systems and putting patients at risk, others have had medical records stolen www. cyberliving. uk #cyberliving 11
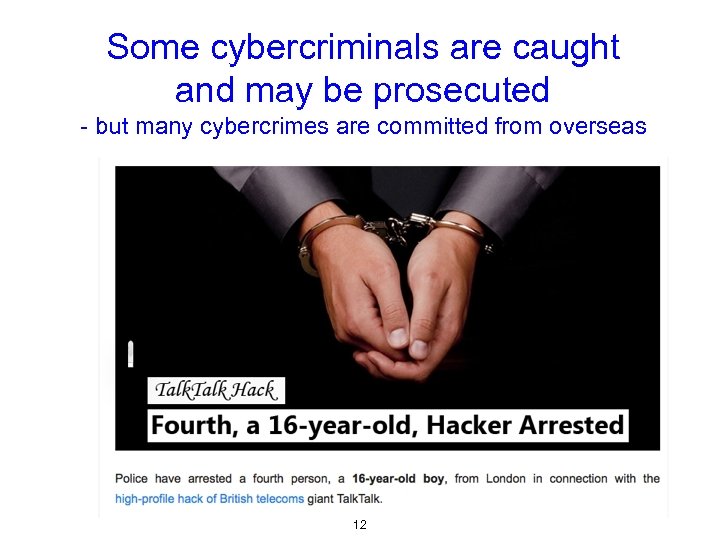
Some cybercriminals are caught and may be prosecuted - but many cybercrimes are committed from overseas 12

13

Many attacks start with Phishing and spearphishing emails to trick you into opening attachments visiting malicious websites or sending money Increasingly, phishing emails are personalised and individually targeted, using details from Facebook, Twitter, Linked. In and other social media sites 14
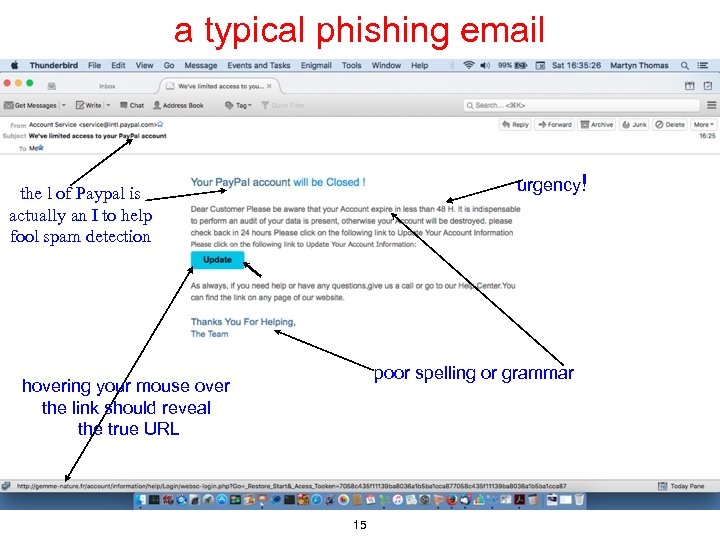
a typical phishing email urgency! the l of Paypal is actually an I to help fool spam detection poor spelling or grammar hovering your mouse over the link should reveal the true URL 15
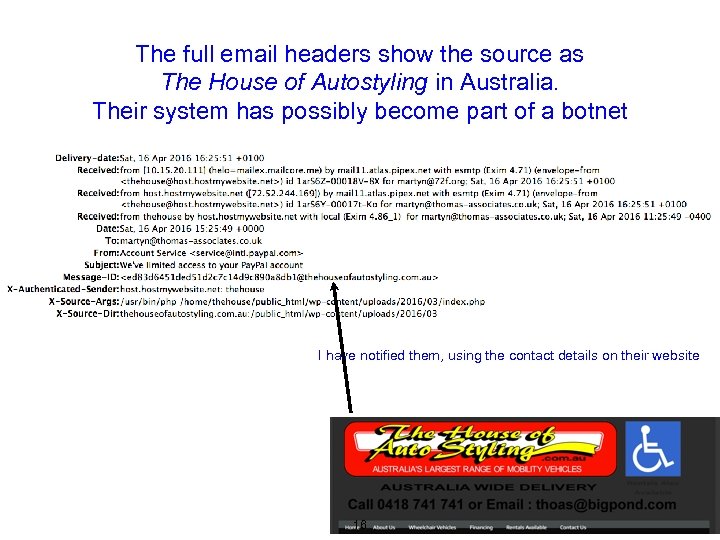
The full email headers show the source as The House of Autostyling in Australia. Their system has possibly become part of a botnet I have notified them, using the contact details on their website 16
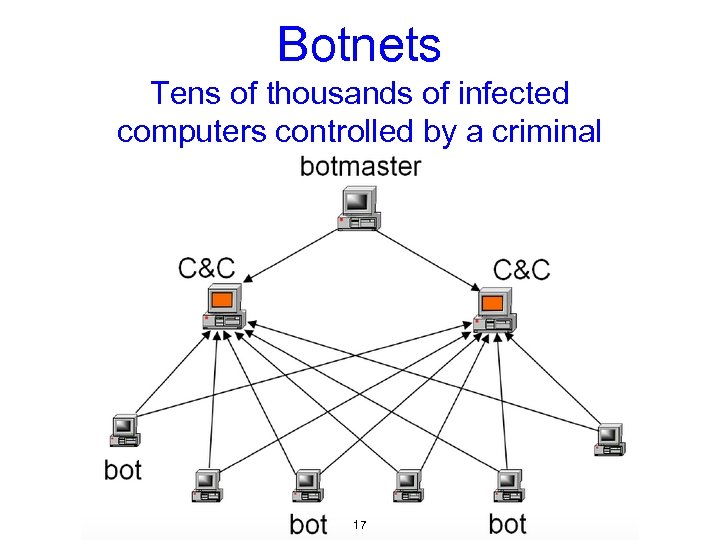
Botnets Tens of thousands of infected computers controlled by a criminal 17

What are botnets used for? • Sending spam • • • each computer may only send a few dozen a day to avoid detection Distributed Denial of Service (DDo. S) attacks • flooding the target with vast numbers of messages to disable it Click fraud • collecting fees for clicking on advertisements Proxy sites for child pornography and other crimes Bitcoin mining and other computationally intensive tasks downloading other malware etc • e. g. keyloggers to collect passwords and private data 18
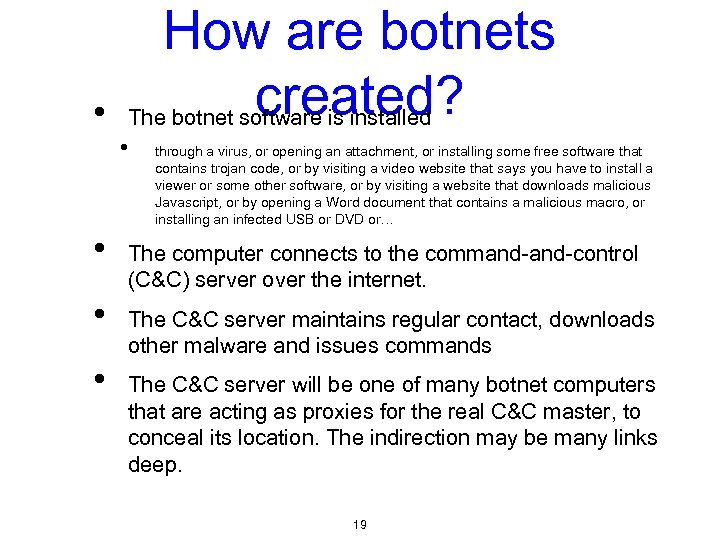
• How are botnets created? The botnet software is installed • • through a virus, or opening an attachment, or installing some free software that contains trojan code, or by visiting a video website that says you have to install a viewer or some other software, or by visiting a website that downloads malicious Javascript, or by opening a Word document that contains a malicious macro, or installing an infected USB or DVD or… The computer connects to the command-control (C&C) server over the internet. The C&C server maintains regular contact, downloads other malware and issues commands The C&C server will be one of many botnet computers that are acting as proxies for the real C&C master, to conceal its location. The indirection may be many links deep. 19

Cyberattacks often involve: Account hijacking 20
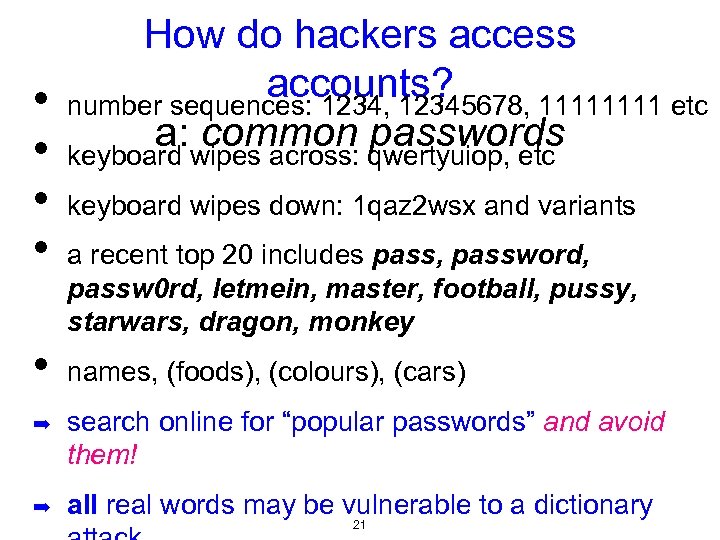
How do hackers access accounts? • number sequences: 1234, 12345678, 1111 etc a: wipes across: qwertyuiop, etc common passwords • keyboard • • • keyboard wipes down: 1 qaz 2 wsx and variants a recent top 20 includes pass, password, passw 0 rd, letmein, master, football, pussy, starwars, dragon, monkey names, (foods), (colours), (cars) ➡ search online for “popular passwords” and avoid them! ➡ all real words may be vulnerable to a dictionary 21
• How do hackers access accounts? b: stolen and re-used A popularpasswords into and the site is broken password file is stolen • or the victim logs into a site that is collecting credentials • The victim has used the same username and password on other sites 22
23

How do hackers access accounts? c: hacker creates a passwords • The intercepted“free wifi access point” in a cafe, airport or other public space. • The victim uses the network, and the hacker copies all the network traffic (using Wireshark, for example) 24

Trojan code a reason never to open email attachments or download any software without careful checking • • • Email attachments (exe files, java, macros in Word or Excel files, spoofed file types …) Free or paid-for software with hidden criminal functionality (games, browser add-ins for video viewers etc). websites that download malicious java or other software. • • malicious websites an insecure legitimate website that was compromised (eg XSS) Malicious advertising links Third-party links that are later changed … 25

An excellent source of information about common cyberattacks, how they work and how developers can protect web systems 26
27

SQL Injection (SQLi) 28

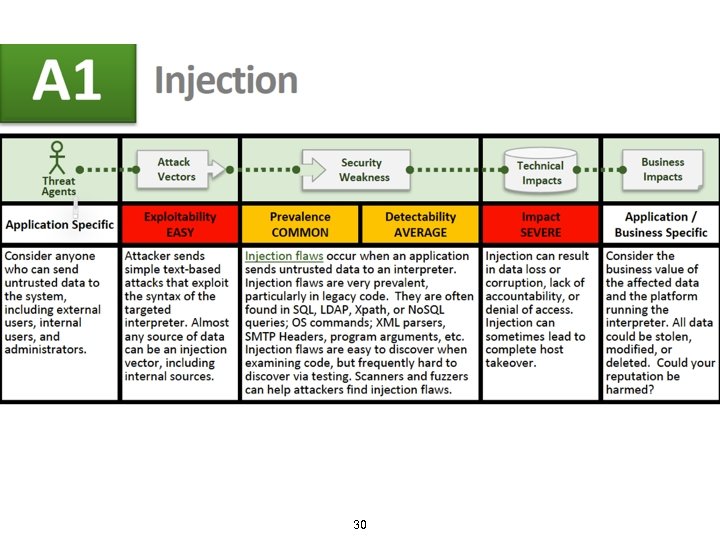
2013 -A 1 – Injection means… • Tricking an application into including unintended commands in the data sent to an interpreter Interpreters… • Take strings and interpret them as commands • SQL, OS Shell, LDAP, XPath, Hibernate, etc… SQL injection is still quite common • Many applications still susceptible (really don’t know why) • Even though it’s usually very simple to avoid Typical Impact • Usually severe. Entire database can usually be read or modified • May also allow full database schema, or account access, or even OS level access 29
30
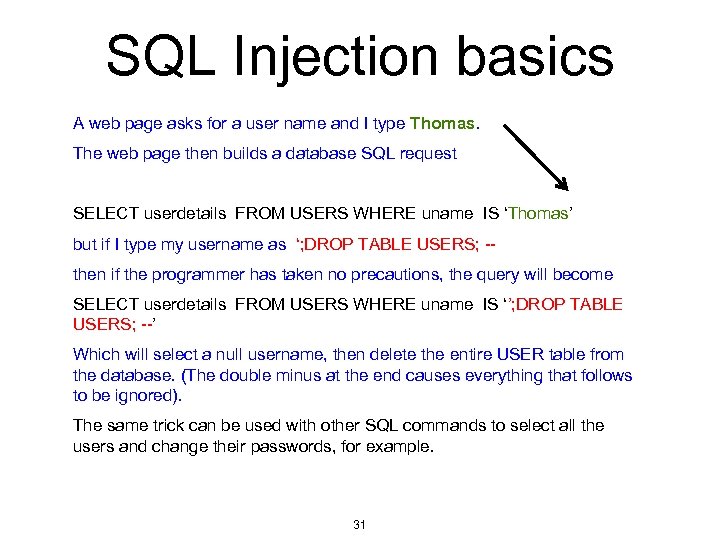
SQL Injection basics A web page asks for a user name and I type Thomas. The web page then builds a database SQL request SELECT userdetails FROM USERS WHERE uname IS ‘Thomas’ but if I type my username as ‘; DROP TABLE USERS; -then if the programmer has taken no precautions, the query will become SELECT userdetails FROM USERS WHERE uname IS ‘’; DROP TABLE USERS; --’ Which will select a null username, then delete the entire USER table from the database. (The double minus at the end causes everything that follows to be ignored). The same trick can be used with other SQL commands to select all the users and change their passwords, for example. 31
SQL Injection exploits 32

It’s so well known, it has become a joke http: //xkcd. com/327/ 33
34
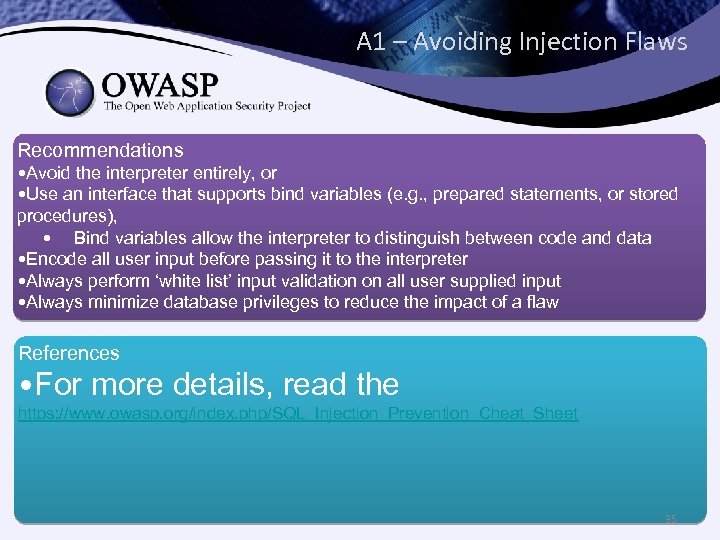
A 1 – Avoiding Injection Flaws Recommendations • Avoid the interpreter entirely, or • Use an interface that supports bind variables (e. g. , prepared statements, or stored procedures), • Bind variables allow the interpreter to distinguish between code and data • Encode all user input before passing it to the interpreter • Always perform ‘white list’ input validation on all user supplied input • Always minimize database privileges to reduce the impact of a flaw References • For more details, read the https: //www. owasp. org/index. php/SQL_Injection_Prevention_Cheat_Sheet 35

Another very common attack: Buffer overflow 36

A typical overflow: Copying a string in C/C++ strcpy char * strcpy ( char *destination, const char *source ); Copies the C string pointed by source into the array pointed by destination, including the terminating null character (and stopping at that point). To avoid overflows, the size of the array pointed by destination shall be long enough to contain the same C string as source (including the terminating null character), and should not overlap in memory with source.
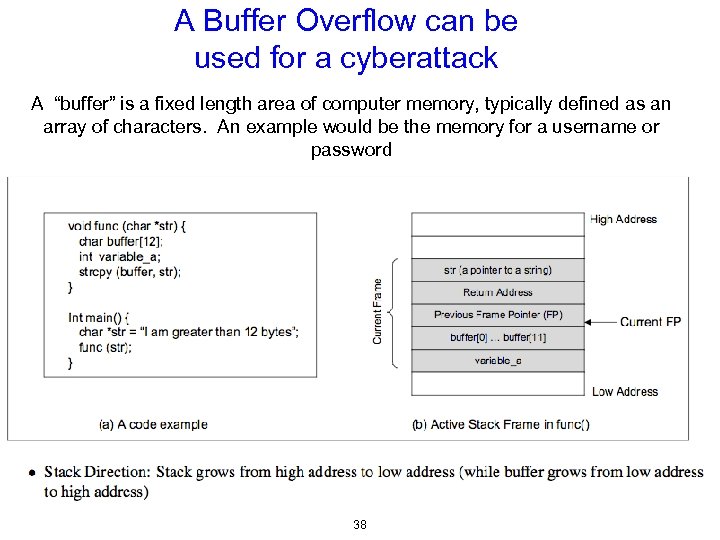
A Buffer Overflow can be used for a cyberattack A “buffer” is a fixed length area of computer memory, typically defined as an array of characters. An example would be the memory for a username or password 38
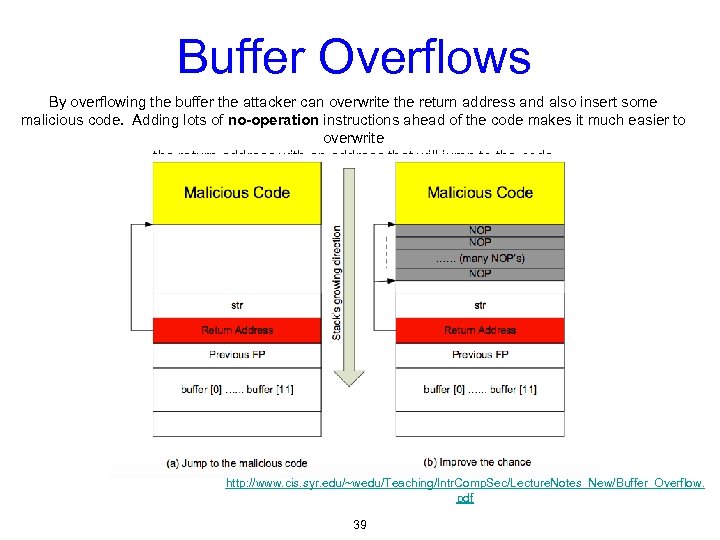
Buffer Overflows By overflowing the buffer the attacker can overwrite the return address and also insert some malicious code. Adding lots of no-operation instructions ahead of the code makes it much easier to overwrite the return address with an address that will jump to the code. http: //www. cis. syr. edu/~wedu/Teaching/Intr. Comp. Sec/Lecture. Notes_New/Buffer_Overflow. pdf 39
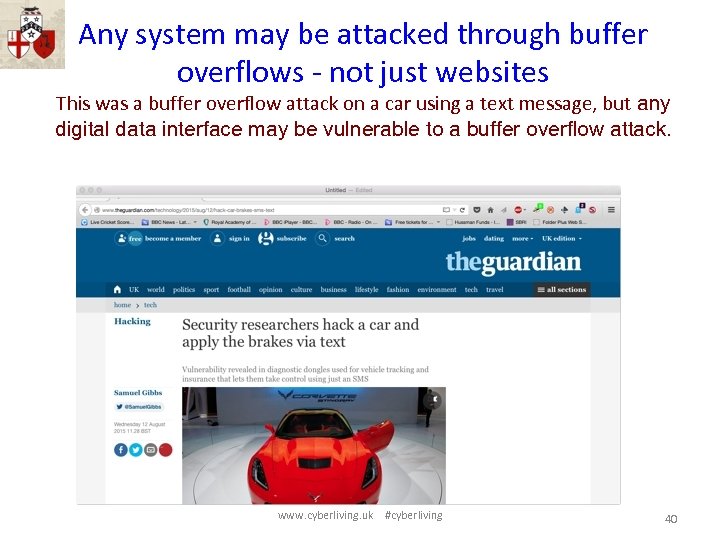
Any system may be attacked through buffer overflows - not just websites This was a buffer overflow attack on a car using a text message, but any digital data interface may be vulnerable to a buffer overflow attack. www. cyberliving. uk #cyberliving 40
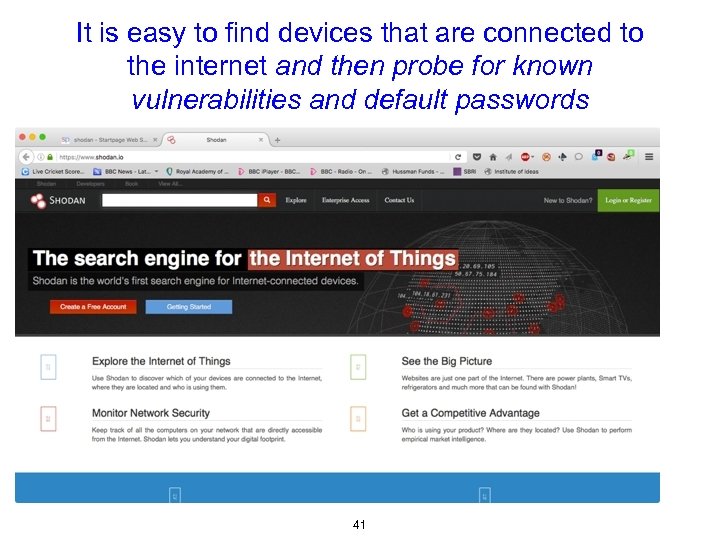
It is easy to find devices that are connected to the internet and then probe for known vulnerabilities and default passwords 41

Another Top-10 attack: Cross-site scripting The attacker enters malicious script that will be stored and displayed by other users for example, in a discussion forum or a social media site 42
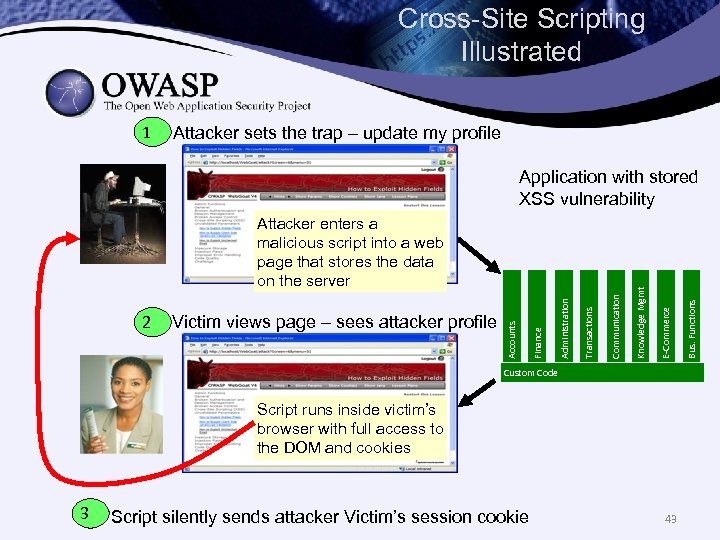
Cross-Site Scripting Illustrated 1 Attacker sets the trap – update my profile Custom Code Script runs inside victim’s browser with full access to the DOM and cookies 3 Script silently sends attacker Victim’s session cookie 43 Bus. Functions E-Commerce Communication Transactions Administration Victim views page – sees attacker profile Finance 2 Accounts Attacker enters a malicious script into a web page that stores the data on the server Knowledge Mgmt Application with stored XSS vulnerability

2013 -A 3 – Cross-Site Scripting (XSS) Occurs any time… • Raw data from attacker is sent to an innocent user’s browser Raw data… • Stored in database • Reflected from web input (form field, hidden field, URL, etc…) • Sent directly into rich Java. Script client Virtually every web application has this problem • Try this in your browser – javascript: alert(document. cookie) Typical Impact • Steal user’s session, steal sensitive data, rewrite web page, redirect user to phishing or malware site • Most Severe: Install XSS proxy which allows attacker to observe and direct all user’s behavior on vulnerable site and force user to other sites 44
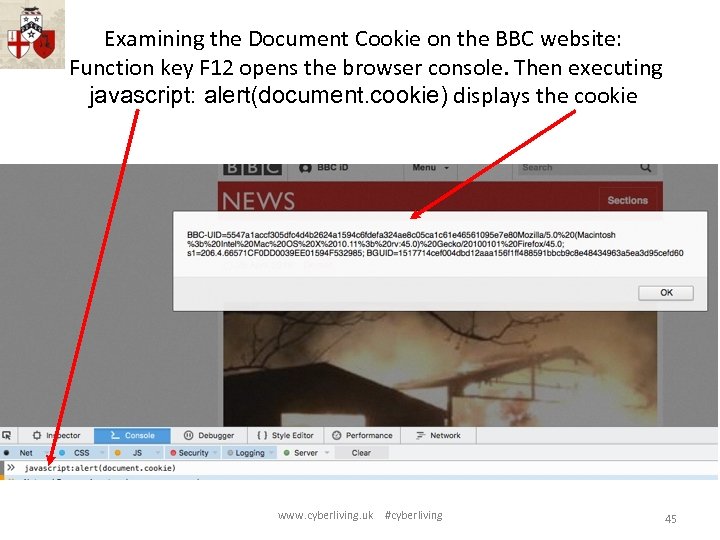
Examining the Document Cookie on the BBC website: Function key F 12 opens the browser console. Then executing javascript: alert(document. cookie) displays the cookie www. cyberliving. uk #cyberliving 45

The most common way to reduce the vulnerability to cyberattack is through test-and fix • • Testing for cyber vulnerabilities is called Penetration Testing or pen testing It has the same weakness as other forms of testing: it may show the presence of defects but it cannot show the absence of defects. Pen testers may run large numbers of known attacks against systems, using special testing tools and databases of known exploits. . . … but so may attackers 46
Metasploit is a popular and powerful tool for penetration testing with a library of known exploits 47
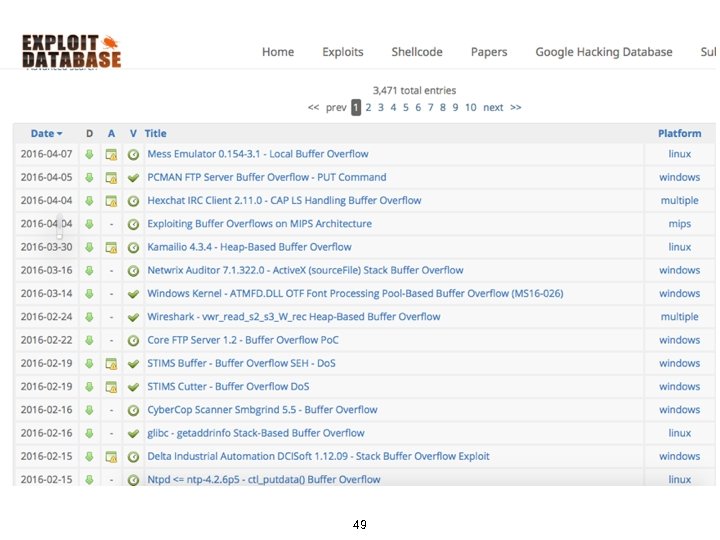
https: //www. exploit-db. com/ An archive of tens of thousands of reported and verified vulnerabilities, vulnerable applications and exploits, available for download 48
49

How can you protect yourself? • • Use strong passwords Use software that helps to protect you : I use • • Thunderbird for emails, Firefox as a browser with the No. Script addon (it’s inconvenient but powerful) Startpage as a search engine with the Startpage proxy links to visit pages ad-blockers and tracker blockers 50

Cybersecurity Advice 51
Cybersecurity Advice 52
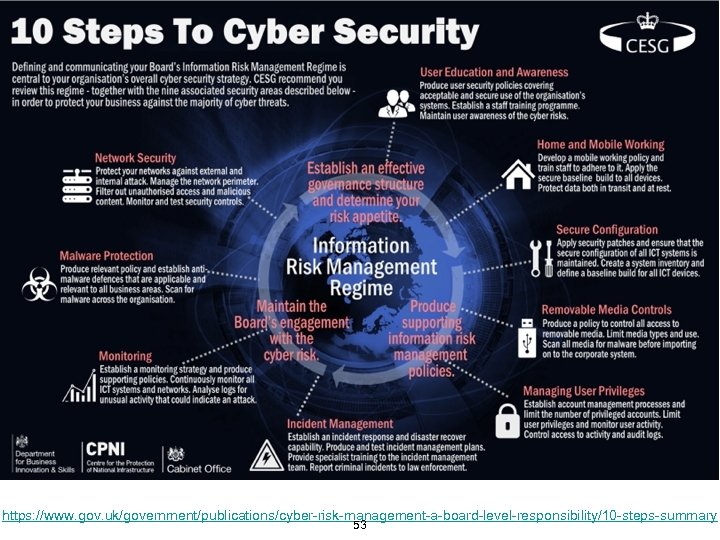
https: //www. gov. uk/government/publications/cyber-risk-management-a-board-level-responsibility/10 -steps-summary 53

Join the discussions … • Visit and discuss cybersecurity at http: www. cyberliving. uk • Share your knowledge and experience • Ask questions - I’ll do my best to answer them. www. cyberliving. uk #cyberliving 54
15f2a6b74943645259fc2ea87dc17030.ppt